Hash Tables and Hash Functions
Reference: Compuer science
Introduction:
This computer science video describes the fundamental principles of the hash table data structure which allows for very fast insertion and retrieval of data. It covers commonly used hash algorithms for numeric and alphanumeric keys and summarises the objectives of a good hash function. Collision resolution is described, including open addressing techniques such as linear and quadratic probing, and closed addressing techniques such as chaining with a linked list.

Consider a list:

Find Ada
You can use linearly search, which costs the time of O(n)
Or you happend to know the index of ada(8), you can look up the value very quickly.
this costs you the time of O(1)
Can help wondering that what if we encode the name into index would the look-up process become O(1).?
Absolutely!
we can turn the key(i.e. the name) into a number(index) with a hash function.
Let's say take each letter of the word get its ascii code,add them up,divided by the length of the array,get the remainder.

Namely , the hash function here is :
we can serve the properties of a person as the value,the name as key.
So that we can look up the profile of a person by the key(i.e.name)

Notes:

So far you aquire the ability to transform a key into index, you can look up very information by hash table.
Needless to say, that is unrealistic.

Have you ever consider the case that two different key are truned into a same index number?
That is collisions.
Let's look a example.
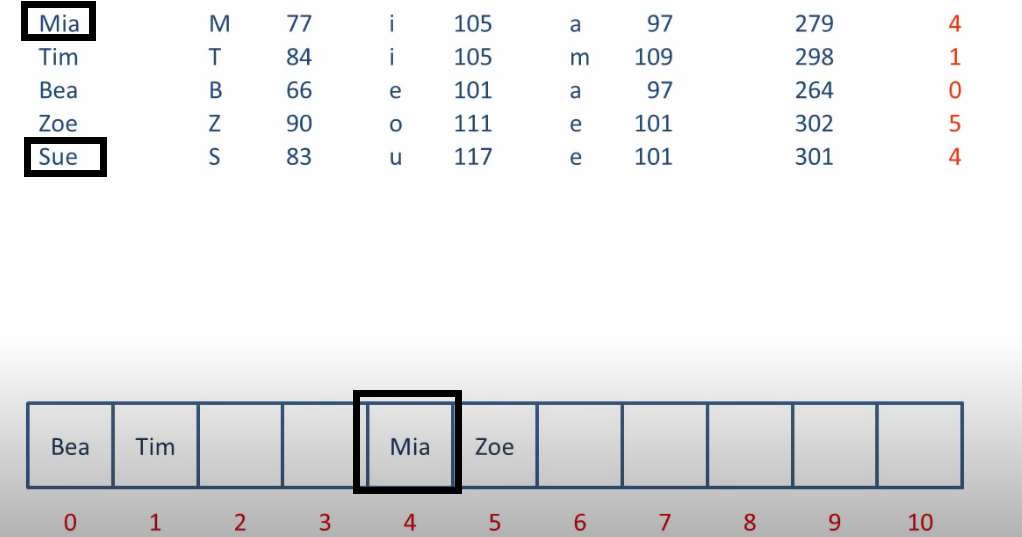
How to solve collisions?
we can put sue into the next place index5 which is empty.
Basically we can put the one that causes collision into the next empty place.
this is linear probing.
put the element somewhere other than the caculated adress is call open adressing.
because every location is open to every elements.
we can use a varity of techniques to decide where to palce.
If we get to the end of the array still can't find a empty place,
it may cycle around to the start of the array.
As you can image , the indexing process is also involved linear probing.(linear search)
In the worse case scenario, it takes O(n) to store and search a key.
Need to mention:

Another way to deal with collisions is called chaining. (close addressing)
we add a linked list in the collision index.
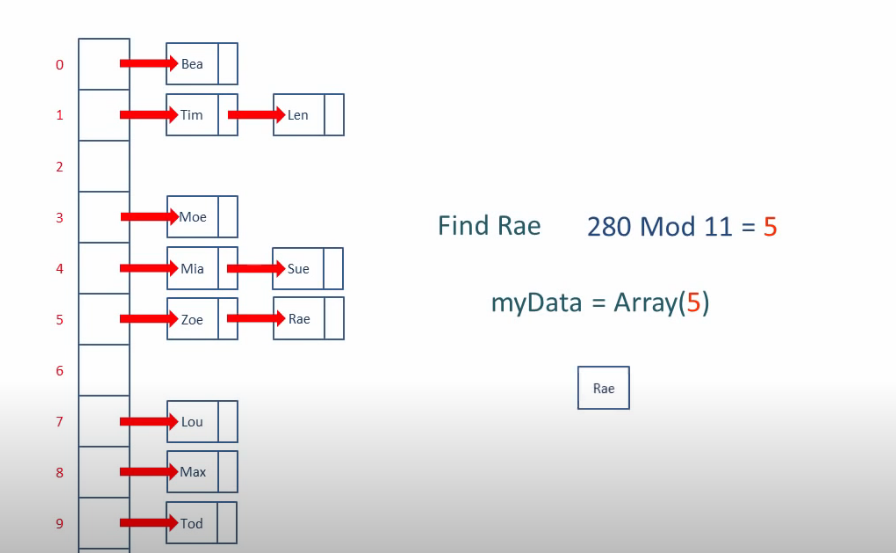
traverse the linked list also takes time.
Summary:



Hash Tables and Hash Functions的更多相关文章
- 11 Hash tables
11 Hash tables Many applications require a dynamic set that supports only the dictionary operatio ...
- 查询计划Hash和查询Hash
查询计划hash和查询hash 在SQL Server 2008中引入的围绕执行计划和缓冲的新功能被称为查询计划hash和查询hash.这是使用针对查询或查询计划的算法来生成二进制hash值的二进制对 ...
- 14.4.3 Adaptive Hash Index 自适应hash index
14.4.3 Adaptive Hash Index 自适应hash index 自适应hash index(AHI) 让InnoDB 执行更像内存数据库在系统使用合适的负载组合和足够的内存用于Buf ...
- 14.2.5.6 Adaptive Hash Indexes 自适应Hash Indexes
14.2.5.6 Adaptive Hash Indexes 自适应Hash Indexes adaptive hash index(AHI) 让InnoDB 执行更加像在一个内存数据库里在, 在不牺 ...
- Hash::make与Hash::check
调用方法之前要先去引用: use Illuminate\Support\Facades\Hash; 可以调用 Hash 门面上的 make 方法对存储密码进行哈希: $pwd = Hash::make ...
- 转载:字符串hash总结(hash是一门优雅的暴力!)
转载自:远航休息栈 字符串Hash总结 Hash是什么意思呢?某度翻译告诉我们: hash 英[hæʃ] 美[hæʃ]n. 剁碎的食物; #号; 蔬菜肉丁;vt. 把…弄乱; 切碎; 反复推敲; 搞糟 ...
- cdoj1092-韩爷的梦 (字符串hash)【hash】
http://acm.uestc.edu.cn/#/problem/show/1092 韩爷的梦 Time Limit: 200/100MS (Java/Others) Memory Limi ...
- Hash表及hash算法的分析
Hash表中的一些原理/概念,及根据这些原理/概念: 一. Hash表概念 二. Hash构造函数的方法,及适用范围 三. Hash处理冲突方法,各自特征 四. ...
- Cuckoo Hash和多级Hash的粗浅认识
通过对Cuckoo Hash.多级Hash和BloomFilter的粗浅了解,感觉它们三者存在类似之处,算是近亲(暂且把普通的Hash称作远亲). Cuckoo Hash的思想非常简单,冲突时,重Ha ...
随机推荐
- 题解-CF436E Cardboard Box
题面 CF436E Cardboard Box \(n\) 个关卡,对每个关卡可以花 \(a_i\) 时间得到 \(1\) 颗星,或花 \(b_i\) 时间得到 \(2\) 颗星,或不玩.问获得 \( ...
- 一个最简单的typescript工程
初级: 1.新建一个文件夹~/a/ 2.cd ~/a/ 3.npm init -y 生成package.json 4.新建index.ts,内容:console.log(" ...
- 在RAC上部署OGG并配置OGG高可用
目录 简介 环境信息 安装OGG 配置数据库 开启数据库级别日志补充 在dbdc1为OGG单独创建TNS 创建OGG管理用户及其表空间 配置OGG 设置OGG全局参数 Source端,OGG设置, 配 ...
- 面试 11-00.JavaScript高级面试
11-00.JavaScript高级面试 #前言 一.基础知识: ES 6常用语法:class .module.Promise等 原型高级应用:结合 jQuery 和 zepto 源码 异步全面讲解: ...
- [日常摸鱼]bzoj2463 [中山市选2009]谁能赢呢?
题意:两个人在$n*n$的棋盘上玩游戏,一开始棋子在左上角,可以上下左右的走到没有走过的地方,最后不能走的那个输,两个人都采取最优决策问哪个赢 猜结论!$n$为偶数则先手赢,否则后手赢. 考虑用$1* ...
- DVWA-文件包含-目录遍历学习笔记
参考文献资料: https://www.cnblogs.com/s0ky1xd/p/5823685.html https://www.cnblogs.com/yuzly/p/10799486.html ...
- 一文让你彻底了解什么是CI/CD
转载自: https://linux.cn/article-9926-1.html CI/CD简介 在软件开发中经常会提到持续集成Continuous Integration(CI)和 持续交付Con ...
- Centos7 根目录存储空间扩展方法
Centos7 根目录存储空间扩展方法 一.首先通过 df -hl 命令查看磁盘占用情况,其中根目录已经被占满,此时需要对其进行扩容 二.针对虚拟机环境的centos7系统根存储空间扩容,可利 ...
- ajax上传单个文件
jsp页面 <%@ page language="java" pageEncoding="UTF-8"%> <!DOCTYPE HTML> ...
- MySQL为Null会导致5个问题,个个致命!
在正式开始之前,我们先来看下 MySQL 服务器的配置和版本号信息,如下图所示: "兵马未动粮草先行",看完了相关的配置之后,我们先来创建一张测试表和一些测试数据. -- 如果存在 ...
