Kubernetes 部署 Kubernetes-Dashboard v2.0.0 尝鲜
目录
· . 一、简介
· . 二、兼容性
· . 三、部署 Kubernetes Dashboard
· . 1、Dashboard RBAC
· . 2、创建 ConfigMap、Secret
· . 3、kubernetes-dashboard
· . 4、创建 kubernetes-metrics-scraper
· . 5、创建访问的 ServiceAccount
· . 四、登录新版本 Dashboard 查看
· . 五、部署 Metrics Server 为 Dashboard 提供指标数据
参考地址:
部署文件 Github 地址:https://github.com/my-dlq/blog-example/tree/master/kubernetes/kubernetes-dashboard2.0.0-deploy
系统环境:
Kubernetes 版本:1.17.4
kubernetes-dashboard 版本:v2.0.0
一、简介
Kubernetes Dashboard 是 Kubernetes 集群的基于 Web 的通用 UI。它允许用户管理在群集中运行的应用程序并对其进行故障排除,以及管理群集本身。这个项目在 Github 已经有半年多不更新了,最近推出了 v2.0.0 版本,这里在 Kubernetes 中部署一下,尝试看看新版本咋样。
二、兼容性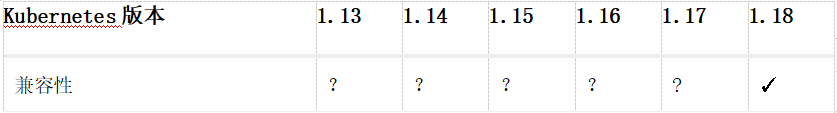
✕不支持的版本范围。
✓ 完全支持的版本范围。
? 由于Kubernetes API版本之间的重大更改,某些功能可能无法在仪表板中正常运行。
三、部署 Kubernetes Dashboard
注意:如果“kube-system”命名空间已经存在 Kubernetes-Dashboard 相关资源,请换成别的 Namespace。
完整部署文件 Github 地址:https://github.com/my-dlq/blog-example/tree/master/kubernetes/kubernetes-dashboard2.0.0-deploy
1、Dashboard RBAC
创建 Dashboard RBAC 部署文件
k8s-dashboard-rbac.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
rules:
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"]
verbs: ["get", "update", "delete"]
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster", "dashboard-metrics-scraper"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"]
verbs: ["get"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
rules:
- apiGroups: ["metrics.k8s.io"]
resources: ["pods", "nodes"]
verbs: ["get", "list", "watch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system
部署 Dashboard RBAC
$ kubectl apply -f k8s-dashboard-rbac.yaml
2、创建 ConfigMap、Secret
创建 Dashboard Config & Secret 部署文件
k8s-dashboard-configmap-secret.yaml
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-csrf
namespace: kube-system
type: Opaque
data:
csrf: ""
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-key-holder
namespace: kube-system
type: Opaque
---
kind: ConfigMap
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-settings
namespace: kube-system
部署 Dashboard Config & Secret
$ kubectl apply -f k8s-dashboard-configmap-secret.yaml
3、kubernetes-dashboard
创建 Dashboard Deploy 部署文件
k8s-dashboard-deploy.yaml
## Dashboard Service
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
type: NodePort
ports:
- port: 443
nodePort: 30001
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
---
## Dashboard Deployment
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
serviceAccountName: kubernetes-dashboard
containers:
- name: kubernetes-dashboard
image: kubernetesui/dashboard:v2.0.3
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
- --namespace=kube-system #设置为当前部署的Namespace
resources:
limits:
cpu: 1000m
memory: 512Mi
requests:
cpu: 1000m
memory: 512Mi
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
- name: tmp-volume
mountPath: /tmp
- name: localtime
readOnly: true
mountPath: /etc/localtime
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
- name: localtime
hostPath:
type: File
path: /etc/localtime
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
部署 Dashboard Deploy
$ kubectl apply -f k8s-dashboard-deploy.yaml
4、创建 kubernetes-metrics-scraper
创建 Dashboard Metrics 部署文件
k8s-dashboard-metrics.yaml
## Dashboard Metrics Service
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kube-system
spec:
ports:
- port: 8000
targetPort: 8000
selector:
k8s-app: dashboard-metrics-scraper
---
## Dashboard Metrics Deployment
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kube-system
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: dashboard-metrics-scraper
template:
metadata:
labels:
k8s-app: dashboard-metrics-scraper
annotations:
seccomp.security.alpha.kubernetes.io/pod: 'runtime/default'
spec:
serviceAccountName: kubernetes-dashboard
containers:
- name: dashboard-metrics-scraper
image: kubernetesui/metrics-scraper:v1.0.4
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
ports:
- containerPort: 8000
protocol: TCP
resources:
limits:
cpu: 1000m
memory: 512Mi
requests:
cpu: 1000m
memory: 512Mi
livenessProbe:
httpGet:
scheme: HTTP
path: /
port: 8000
initialDelaySeconds: 30
timeoutSeconds: 30
volumeMounts:
- mountPath: /tmp
name: tmp-volume
- name: localtime
readOnly: true
mountPath: /etc/localtime
volumes:
- name: tmp-volume
emptyDir: {}
- name: localtime
hostPath:
type: File
path: /etc/localtime
nodeSelector:
"beta.kubernetes.io/os": linux
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
部署 Dashboard Metrics
$ kubectl apply -f k8s-dashboard-metrics.yaml
5、创建访问的 ServiceAccount
创建一个绑定 admin 权限的 ServiceAccount,获取其 Token 用于访问看板。
创建 Dashboard ServiceAccount 部署文件
k8s-dashboard-token.yaml
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: admin
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
roleRef:
kind: ClusterRole
name: cluster-admin
apiGroup: rbac.authorization.k8s.io
subjects:
- kind: ServiceAccount
name: admin
namespace: kube-system
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin
namespace: kube-system
labels:
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
部署访问的 ServiceAccount
$ kubectl apply -f k8s-dashboard-token.yaml
获取 Token
$ kubectl describe secret/$(kubectl get secret -n kube-system |grep admin|awk '{print $1}') -n kube-system
token:
eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi10b2tlbi1iNGo0aCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjkwMTQzMWYxLTVmNGItMTFlOS05Mjg3LTAwMGMyOWQ5ODY5NyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTphZG1pbiJ9.iwE1UdhB78FgXZJh4ByyOZVNh7M1l2CmOOevihOrY9tl_Z5sf3i_04CA33xA2LAMg7WNVYPjGB7vszBlkQyDGw0H5kJzIfL1YnR0JeLQkNk3v9TLyRqKJA2n8pxmJQIJP1xq0OPRGOfcA_n_c5qESs9QFHejVc5vABim8VBGX-pefKoJVXgu3r4w8gr1ORn4l5-LtHdQjSz3Dys7HwZo71fX2aLQR5bOPurkFKXqymcUoBYpWVsf-0cyN7hLRO-x-Z1i-uVpdM8ClpYSHv49eoDJePrcWpRp-Ryq6SNpGhiqCjjifEQAVHbr36QSAx8I1aamqLcpA0Da2qnunw52JA
四、登录新版本 Dashboard 查看
本人的 Kubernetes 集群地址为”192.168.2.11”并且在 Service 中设置了 NodePort 端口为 30001 和类型为 NodePort 方式访问 Dashboard ,所以访问地址:https://192.168.2.11:30001 进入 Kubernetes Dashboard 页面,然后输入上一步中创建的 ServiceAccount 的 Token 进入 Dashboard,可以看到新的 Dashboard。
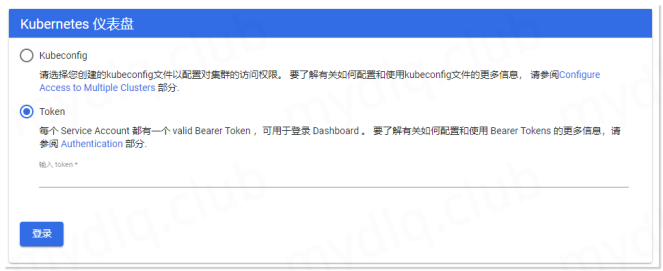
跟上一个版本比较,整体风格更加简洁,并且,可以感受到的是这个页面比以前访问速度更加快速(估计是加了缓存),除了之外还增加了:
新增黑色主题
新增对CRD的管理
新增对集群角色的编辑
新增对 kubernetes 对象以 yaml 格式进行编辑
修改集群资源指标的监控监控信息以及看板样式
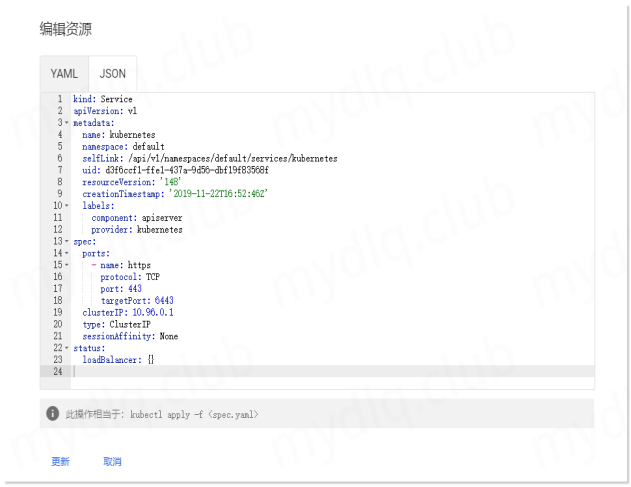
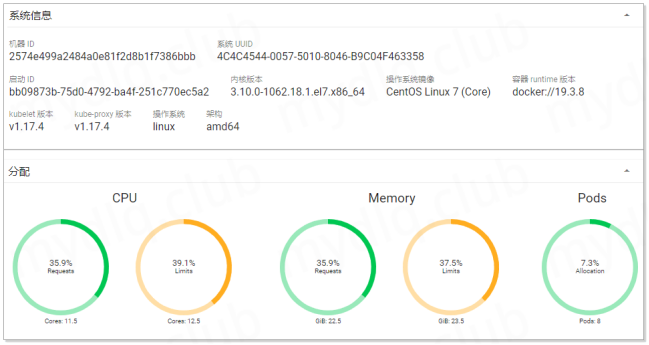
五、部署 Metrics Server 为 Dashboard 提供指标数据
Dashboard 已经部署完成,不过登录 Dashboard 后可以看到:
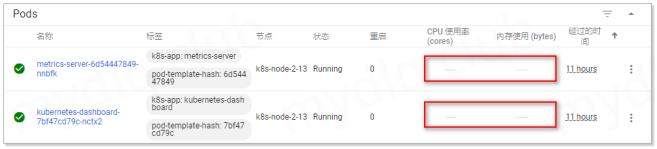
这些栏数据显示都是空,这是由于 Dashboard 的指标部署需要从 Metrics Server 中获取,Dashboard 该版本另一个组件 kubernetes-metrics-scraper 就是用于从 Metrics Server 获取指标的适配器。之前我们已经部署 kubernetes-metrics-scraper 组件,接下来只要再部署 Metrics Server 组件就能获取系统指标数据,供 Dashboard 绘制图形,部署 Metrics Server 可以参考:
Kubernetes 部署 Metrics Server 获取集群指标数据
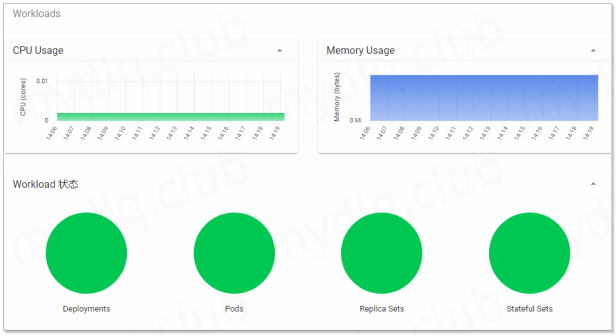
当按照上面部署完成后,等一段时间,再刷新 Dashboard 界面,可以观察到如下界面:
–END–
Kubernetes 部署 Kubernetes-Dashboard v2.0.0 尝鲜的更多相关文章
- R︱Rstudio 1.0版本尝鲜(R notebook、下载链接、sparkR、代码时间测试profile)
每每以为攀得众山小,可.每每又切实来到起点,大牛们,缓缓脚步来俺笔记葩分享一下吧,please~ --------------------------- 2016年11月1日,RStudio 1.0版 ...
- Kubernetes V1.16.2部署Dashboard V2.0(beta5)
Kubernetes V1.16.2部署Dashboard V2.0(beta5) 在Master上部署Dashboard 集群安装部署请看安装Kubernetes V1.16.2 kubectl g ...
- Kubespray部署Kubernetes 1.13.0(使用本地镜像仓库)
1. 下载kubespray # git clone https://github.com/kubernetes-sigs/kubespray.git # cd kubespray # pip ins ...
- 使用离线包部署kubernetes 1.9.0、kubernetes-dashboard 1.8
=============================================== 2018/3/22_第2次修改 ccb_warlock 更新 ...
- 二进制方式部署Kubernetes 1.6.0集群(开启TLS)
本节内容: Kubernetes简介 环境信息 创建TLS加密通信的证书和密钥 下载和配置 kubectl(kubecontrol) 命令行工具 创建 kubeconfig 文件 创建高可用 etcd ...
- 2、kubeadm快速部署kubernetes(v1.15.0)集群190623
一.网络规划 节点网络:192.168.100.0/24 Service网络:10.96.0.0/12 Pod网络(默认):10.244.0.0/16 二.组件分布及节点规划 master(192.1 ...
- Helm 安装部署Kubernetes的dashboard
Kubernetes Dashboard 是 k8s集群的一个 WEB UI管理工具,代码托管在 github 上,地址:https://github.com/kubernetes/dashboard ...
- 二进制搭建Kubernetes集群(最新v1.16.0版本)
目录 1.生产环境k8s平台架构 2.官方提供三种部署方式 3.服务器规划 4.系统初始化 5.Etcd集群部署 5.1.安装cfssl工具 5.2.生成etcd证书 5.2.1 创建用来生成 CA ...
- 一文吃透如何部署kubernetes之Dashboard
kubernetes Dashboard是什么? Dashboard是kubernetes的Web GUI,可用于在kubernetes集群上部署容器化应用,应用排错,管理集群本身及其附加的资源等,它 ...
随机推荐
- 使用Lock接口来解决线程安全的问题
package cn.itcast.demo16.Demo09.Lock;import java.util.concurrent.locks.Lock;import java.util.concurr ...
- VectorCAST软件自动化测试方案
VectorCAST 是主要用于对C/C++/Ada程序进行软件自动化测试,并能够在Windows和Linux等多种开发环境下运行.其主要功能包含自动化的单元测试.集 成测试.覆盖率分析.回归测试.代 ...
- 如何使用cURL获得请求/响应具体耗时?
如何使用cURL一次测量请求和响应时间? cURL支持格式化输出请求的详细信息(请参阅cURL手册页的-w.–write out<format>获取更多信息). 如题,我们将只关注如何知晓 ...
- 3、Spring的DI依赖注入
一.DI介绍 1.DI介绍 依赖注入,应用程序运行依赖的资源由Spring为其提供,资源进入应用程序的方式称为注入. Spring容器管理容器中Bean之间的依赖关系,Spring使用一种被称为&qu ...
- 代码仓库gogs的基本配置使用
目录 一.基本功能介绍 主板说明 页面说明 用户设置 二.仓库 新建仓库 迁移仓库 仓库介绍 三.组织和团队 创建新组织 创建团队 一.基本功能介绍 主板说明 图中1表示自己个人账户下的仓库(所有权属 ...
- iOS开发——密码存储之keychain的使用
iOS的keychain服务提供了一种安全的保存私密信息(密码,序列号,证书等)的方式.每个ios程序都有一个独立的keychain存储.从ios 3.0开始,跨程序分享keychain变得可行. 下 ...
- RabbitMQ,RocketMQ,Kafka 消息模型对比分析
消息模型 消息队列的演进 消息队列模型 发布订阅模型 RabbitMQ的消息模型 交换器的类型 direct topic fanout headers Kafka的消息模型 RocketMQ的消息模型 ...
- python selenium表单定位
在Web应用中经常会遇到frame/iframe 表单嵌套页面的应用,WebDriver 只能在一个页面上对元素识别与定位,对于frame/iframe 表单内嵌页面上的元素无法直接定位.这时就需要通 ...
- int i=i++;和i=++i;和i++
1.int i=i++; 2.i=++i; 3.i++
- 使用.NET 6开发TodoList应用(1)——系列背景
前言 想到要写这样一个系列博客,初衷有两个:一是希望通过一个实践项目,将.NET 6 WebAPI开发的基础知识串联起来,帮助那些想要入门.NET 6服务端开发的朋友们快速上手,对使用.NET 6开发 ...
