Ethical Hacking - NETWORK PENETRATION TESTING(3)
Change MAC Address using macchanger.
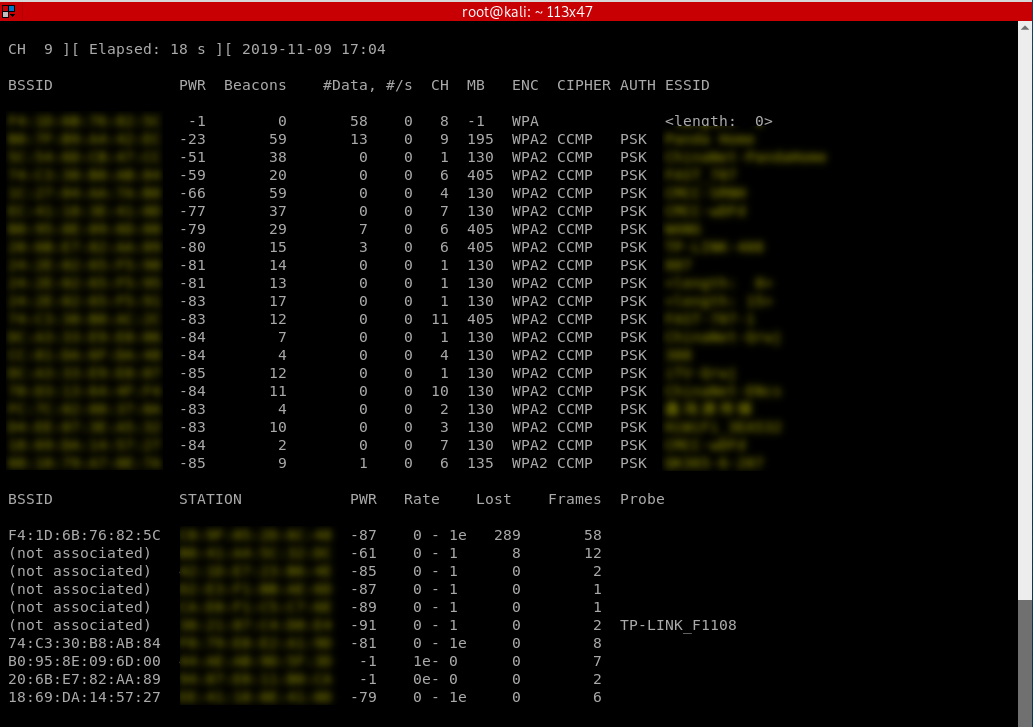
Packet Sniffing Basics Airodump-ng
airodump-ng is a program part of the aircrack-ng package, it's a packet sniffer that allows us to capture all the packets that are in our wifi card range. We can also use it to just scan all wifi networks around us and gather info about them.
Using Airodump-ng:
1. Enable monitor mode
airmon-ng start [interface]
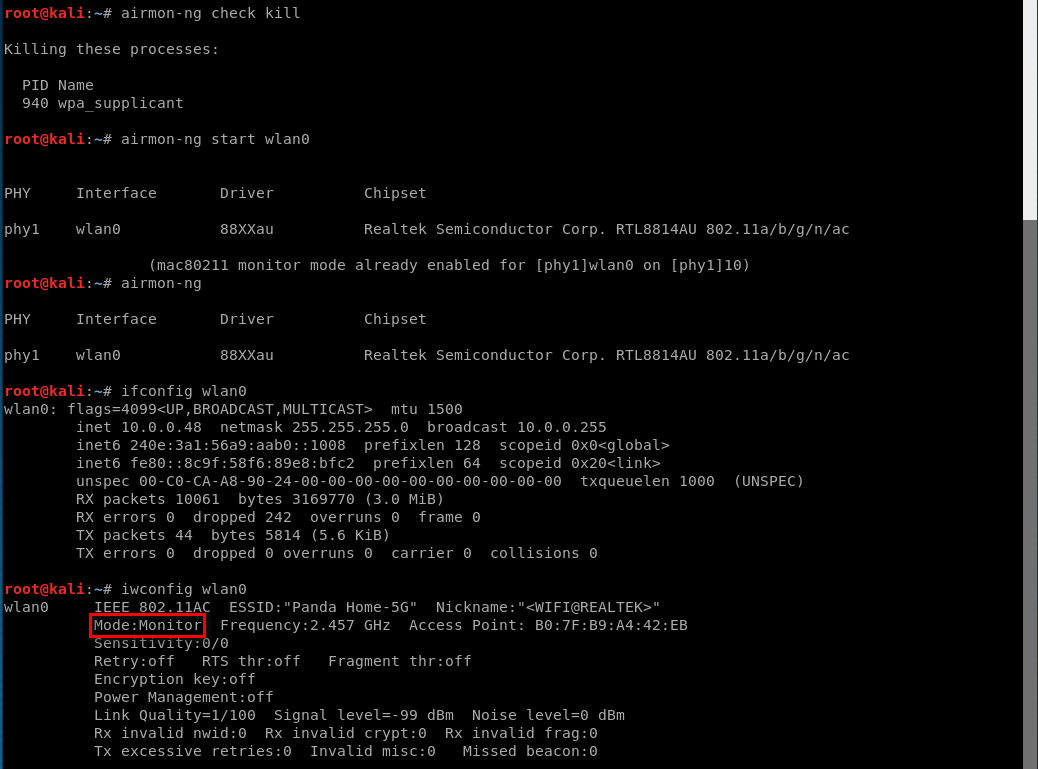
Enabling Monitor Mode Manually.
iwconfig [interface] mode monitor
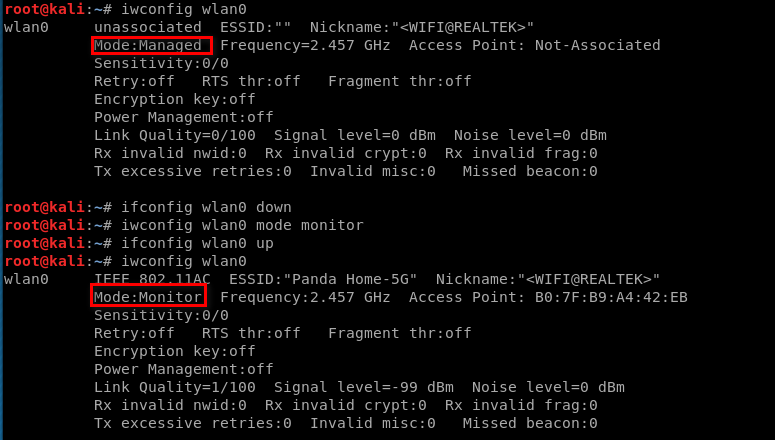
Enabling Monitor Mode Using airmon-ng
airmon-ng check kill
airmon-ng start [interface]
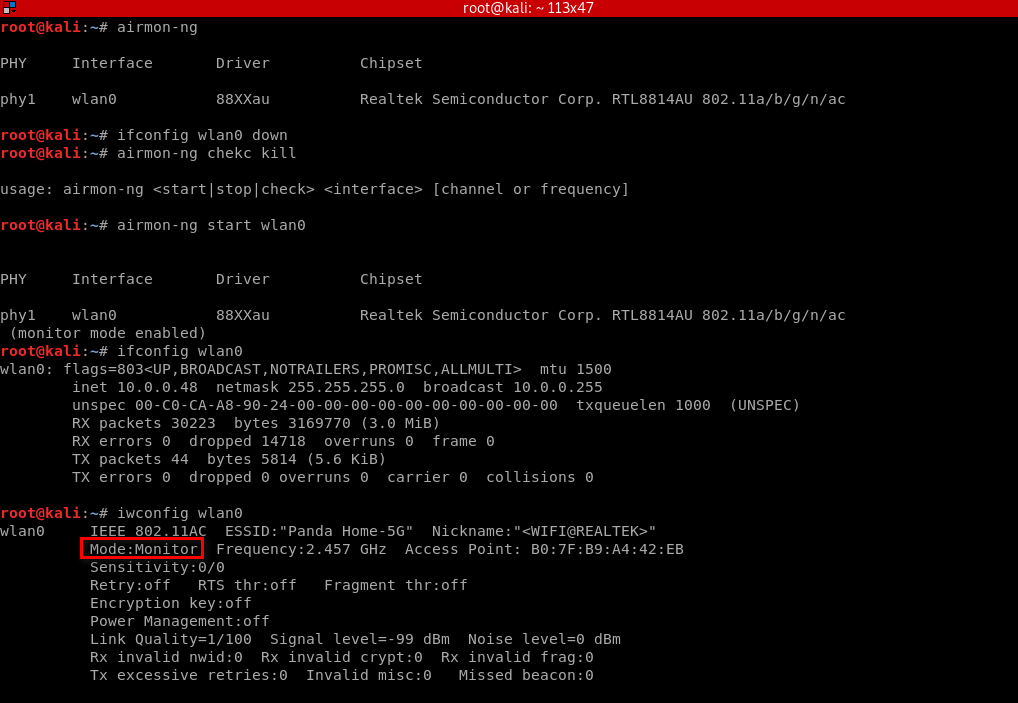
2. Start airodump-ng
airodump-ng [interface]
Ethical Hacking - NETWORK PENETRATION TESTING(3)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
- Ethical Hacking - NETWORK PENETRATION TESTING(5)
Deauthentication Attacks Theory This attack is used to disconnect any device from any network within ...
随机推荐
- ImportError: cannot import name _remove_dead_weakref
出现这个错误, 和python环境有关. 电脑有多个版本造成的. python3 有这个_remove_dead_weakref python 2.7.10 并没有_remove_dead_weakr ...
- Java 多线程基础(八)线程让步
Java 多线程基础(八)线程让步 yield 一.yield 介绍 yield()的作用是让步.它能让当前线程由“运行状态”进入到“就绪状态”,从而让其它具有相同优先级的等待线程获取执行权:但是,并 ...
- python 函数式编程 高阶函数 装饰器
# -*- coding:gb2312 -*- #coding=utf-8 # 高阶函数 import math def is_sqr(x): y = int(math.sqrt(x)) return ...
- AndroidStudio 编译失败;Caused by: org.gradle.api.resources.ResourceException: Could not get resource..
错误信息: Caused by: org.gradle.api.resources.ResourceException: Could not get resource 'https://jcenter ...
- 39 _ 队列5 _ 循环队列需要几个参数来确定 及其含义的讲解.swf
上面讲解都是循环队列,如果是链表实现的话就很简单,队列只有循环队列才比较复杂 此时队列中只存储一个有效元素3,当在删除一个元素的时候,队列为空,pFont向上移动,pFont等于pRear,但是此时p ...
- junit配合catubuter统计单元测试的代码覆盖率
1.视频参考孔浩老师ant视频笔记 对应的build-junit.xml脚步如下所示: <?xml version="1.0" encoding="UTF-8&qu ...
- disruptor架构一
Disruptor是一个高性能的异步处理框架,或者可以认为是最快的消息框架(轻量的JMS),也可以认为是一个观察者模式的实现,或者事件监听模式的实现. 在使用之前,首先说明disruptor主要功能加 ...
- trollcave解题
这是第一次完整地进行模拟渗透,前前后后一共花了一天时间,花了点时间写了个writeup. 博主是个菜鸡,如果有大神看到,请轻喷...... writeup下载:https://hrbeueducn-m ...
- 深度学习“四大名著”发布!Python、TensorFlow、机器学习、深度学习四件套!
Python 程序员深度学习的"四大名著": 这四本书着实很不错!我们都知道现在机器学习.深度学习的资料太多了,面对海量资源,往往陷入到"无从下手"的困惑出境. ...
- vue基础入门(2.2)
2.2.基础指令 2.2.1.什么是指令 指令 (Directives) 是带有 v- 前缀的特殊特性,指令特性的值预期是单个 JavaScript 表达式,指令的职责是,当表达式的值改变时,将其产生 ...
