Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER
- Discover all devices on the network.
- Display their IP address.
- Display their MAC address.
Write the Python code using the scapy.all module.
Refer to: https://scapy.readthedocs.io/en/latest/installation.html
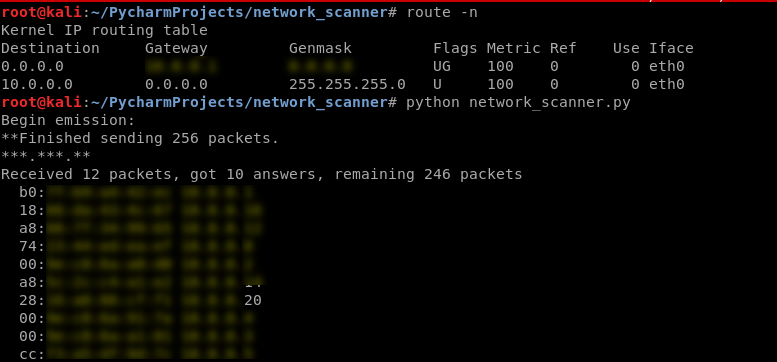
#!/usr/bin/env python import scapy.all as scapy def scan(ip):
scapy.arping(ip) scan("10.0.0.1/24")
ALGORITHM
Goal -> Discover clients on the network.
Steps:
1. Create arp request directed to broadcast MAC asking for IP.
Two main parts:
-> Use ARP to ask who has target IP.
-> Set destination MAC to broadcast MAC.
2. Send packet and receive a response.
3. Parse the response.
4. Print result.
Use the scapy module in this program.
https://scapy.readthedocs.io/en/latest/usage.html
EX: Python Script to discover the clients on the network.
#!/usr/bin/env python import scapy.all as scapy def scan(ip):
arp_request = scapy.ARP(pdst=ip)
broadcast = scapy.Ether(dst="ff:ff:ff:ff:ff:ff")
arp_request_broadcast = broadcast/arp_request
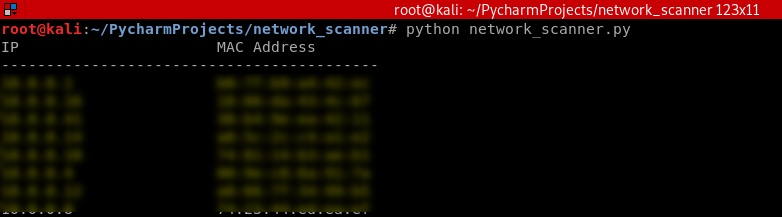
answered_list = scapy.srp(arp_request_broadcast, timeout=1, verbose=False)[0] print("IP\t\t\tMAC Address\n------------------------------------------")
for element in answered_list:
print(element[1].psrc + "\t\t" + element[1].hwsrc) scan("10.0.0.1/24")
Execute the script and show the result.
Python Ethical Hacking - NETWORK_SCANNER(1)的更多相关文章
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - MAC Address & How to Change(3)
SIMPLE ALGORITHM Goal -> Check if MAC address was changed. Steps: 1. Execute and read ifconfig. ...
- Python Ethical Hacking - MAC Address & How to Change(2)
FUNCTIONS Set of instructions to carry out a task. Can take input, and return a result. Make the cod ...
- Python Ethical Hacking - MAC Address & How to Change(1)
MAC ADDRESS Media Access Control Permanent Physical Unique Assigned by manufacturer WHY CHANGE THE M ...
- Python Ethical Hacking - The Lab and Needed Software
The Lab and Needed Software Attacker Machine - Kali Linux https://www.kali.org/ 1. Install the softw ...
- Python Ethical Hacking - Basic Concetion
What is Hacking? Gaining unauthorized access. Hackers? 1.Black-hat Hackers 2.White-hat Hackers 3.Gre ...
- Python Ethical Hacking - VULNERABILITY SCANNER(9)
Automatically Discovering Vulnerabilities Using the Vulnerability Scanner 1. Modify the run_scanner ...
随机推荐
- 小白的mapbox学习之路-显示地图
刚接触mapbox,只是简单记下自己的学习之路,如有错误,欢迎大神指正 1-头部引入链接 2-body中定义一个div块,用来显示地图 3-在script中创建一个map对象,并设置相关参数 mapb ...
- winxp系统连接服务器丢包解决方法
winxp系统连接服务器丢包解决方法 MFC编写一个打开网页的程序,发生异常没有获取到数据. 分析步骤: 1. 用getLastError()获取到的信息,(2)- 系统找不到指定的文件. 2. 用浏 ...
- <用户输入url按下回车,一直到用户看到界面,这期间经历了什么>
用户输入url按下回车,一直到用户看到界面,这期间都经历什么? 一. DNS解析缓存: 1. 找到浏览器缓存解析域名: 2. 找到和 DNS 缓存 ; 3. 找到路由器 DNS 缓存: 4. 找到查 ...
- C++ vector迭代器访问二维数组
#include<iostream> #include<vector> int main(){ std::vector<int> arr(); // 创建一维数组 ...
- Python3-socket模块-低级网络接口
Python3中的socket模块提供了对访问套接字(socket)的接口 socket可以理解为是一个管道,通过这个管道可以使两个不同的程序通过网络进行通信,在Python中的scoket()函数可 ...
- 九、深度优先 && 广度优先
原文地址 一.什么是"搜索"算法? 算法是作用于具体数据结构之上的,深度优先搜索算法和广度优先搜索算法都是基于"图"这种数据结构的. 因为图这种数据结构的表达能 ...
- Codeforces Round #651 (Div. 2)
感觉自己无可救药了. A题:找到小于等于n的两个不同的数的gcd最大是多少,显然是floort(n/2).设这两数是a * gcd, b * gcd然后gcd(a,b) = 1,那么gcd要尽量大,不 ...
- Github仓库如何选择开源许可证
Github仓库如何选择开源许可证 目录 Github仓库如何选择开源许可证 为什么需要开源许可证? 不使用开源许可证对于开发者有何影响? 不使用开源许可证对于项目的使用者有何影响? Github的开 ...
- python变量拷贝
写python代码时候,如:A = 0,B = A,B = 1, 有时候会发现A变成了1,那么怎么办呢? 以下是伪代码: import copy ... X_ = copy.copy(X) ... 这 ...
- VS2017 快捷键
VS2017注释:先CTRL+K 然后CTRL+C (ctrl按住不松,松开k按c) 取消注释:先CTRL+K,然后CTRL+U (ctrl按住不松,松开k按c)
