SElinux测试及排错
一、修改SElinux的状态
#sestatus --查看状态
#setenforce --临时修改
#setenforce
#getenforce #vim /etc/selinux/config --通过配置文件修改
SELINUX=Enforcing
#systemctl reboot --重启生效
#getenforce
二、文件的上下文
#setenforce 1
#yum install -y httpd
#mkdir /local
#echo lxjtest > /local/index.html
#ln -s /local/ /var/www/html/soft
[root@rhel1 html]# ll -Z /local/index.html
-rw-r--r--. root root unconfined_u:object_r:default_t:s0 /local/index.html
[root@rhel1 html]# ll -Z /var/www/
drwxr-xr-x. root root system_u:object_r:httpd_sys_script_exec_t:s0 cgi-bin
drwxr-xr-x. root root system_u:object_r:httpd_sys_content_t:s0 html
修改文件上下文的三种方法:
方法1:修改/local目录的的fcontext为httpd_sys_content_t
#semanage fcontext -l | grep http
#chcon -R -t httpd_sys_content_t /local/
方法2:
修改/local目录的的fcontext为跟/var/www目录一致
#chcon -R --reference /var/www/ /local/
方法3:
#semanage fcontext -a -t httpd_sys_content_t '/local(/.*)?'
#restorecon -FRv /local
# man semanage fcontext
#推荐使用第3钟方法,文件夹上下文类型将写入内核
在RHEL2上访问测试:
#setenforce 1
http://192.168.100.1/soft #未在RHEL1修改上下文,访问会被Forbidden,修改正确后可访问
实验一、端口的上下文
#查看端口的上下文
#semanage port -l | grep http
#添加端口的上下文
#semanage port -a -t http_port_t -p tcp 8899
#删除端口的上下文
#semanage port -d -t http_port_t -p tcp 8899
#修改端口的上下文
#semanage port -m -t http_port_t -p tcp 8899
#修改防火墙
#firewall-cmd --permanent --add-port=8899/tcp
#firewall-cmd --reload
#修改httpd配置文件,以监听8899端口
#vim /etc/httpd/conf/httpd.conf
Listen 8899 #增加
#mkdir /var/www/8899
#echo 8899 > /var/www/8899/index.html
#vim /etc/httpd/conf.d/0.conf
< VirtualHost 192.168.100.1:>
DocumentRoot "/var/www/html"
ServerName 192.168.100.1
< /VirtualHost>
< VirtualHost 192.168.100.1:>
DocumentRoot "/var/www/8899"
ServerName 192.168.100.1
< /VirtualHost>
#systemctl restart httpd
在rhel1和rhel2上访问测试:
http://192.168.100.1
http://192.168.100.1:8899
实验二、布尔值
使用SElinux图形画界面来配置selinux
#yum provides system-config-selinux
#yum install -y policycoreutils-gui-2.2.5-11.el7.x86_64
#system-config-selinux 打开SElinux图形界面
例:
#yum install -y samba
#getsebool -a
#getsebool -a | grep samba
#setsebool -P samba_enable_home_dir on
#setsebool -P samba_export_all_rw on
-a 列出
-P 永久生效permanent
实验三、SElinux在网络各服务中的配置
man selinux
常见有一些服务的SElinux配置
===ftp===
//If you want to share files anonymously <如果你想把这个共享给匿名的话,需要开启以下>
chcon -R -t public_content_t /var/ftp
//If you want to setup a directory where you can upload files
<如果你想让你设置的FTP目录可以上传文件的话,SELINUX需要设置>
chcon -t public_content_rw_t /var/ftp/incoming
//You must also turn on the boolean allow_ftpd_anon_write <允许匿名用户写入权限>
setsebool -P allow_ftpd_anon_write=1
//If you are setting up this machine as a ftpd server and wish to allow users to access their home directorories<如果你希望你的FTP用户可以访问自己的家目录的话,需要开启>
setsebool -P ftp_home_dir 1
//If you want to run ftpd as a daemon<如果你希望将vsftpd以daemon的方式运行的话,需要开启>
setsebool -P ftpd_is_daemon 1
//You can disable SELinux protection for the ftpd daemon<你可以让SElinux停止保护vsftpd的daemon方式动行>
setsebool -P ftpd_disable_trans 1
===httpd===
//If you want a particular domain to write to the public_content_rw_t domain
< 如果希望具体个doman具有可写权限的话,需要设置>
setsebool -P allow_httpd_anon_write=1
or
setsebool -P allow_httpd_sys__anon_write=1
//httpd can be setup to allow cgi s to be executed <HTTP被设置允许cgi的设置>
setsebool -P httpd_enable_cgi 1
//If you want to allow access to users home directories<允许用户HHTP访问其家目录,该设定限仅于用户的家目录主页>
setsebool -P httpd_enable_homedirs 1
chcon -R -t httpd_sys_content_t ~user/public_html
//httpd is allowed access to the controling terminal<允许httpd访问终端>
setsebool -P httpd_tty_comm 1
//such that one httpd service can not interfere with another
setsebool -P httpd_unified 0
//loadable modules run under the same context as httpd
setsebool -P httpd_builtin_ing 0
//httpd s are allowed to connect out to the network
setsebool -P httpd_can_network_connect 1
// You can disable suexec transition
setsebool -P httpd_suexec_disable_trans 1
//You can disable SELinux protection for the httpd daemon by executing <关闭Selinux的关于httpd进程守护的保护>
setsebool -P httpd_disable_trans 1
service httpd restart
===named===
//If you want to have named update the master zone files <关于named,master更新selinux设定>
setsebool -P named_write_master_zones 1
//You can disable SELinux protection for the named daemon by executing
< 关闭named的进程守护保护>
setsebool -P named_disable_trans 1
service named restart
===nfs===
//If you want to setup this machine to share nfs partitions read only
< Selinux将本机的NFS共享设置成只读>
setsebool -P nfs_export_all_ro 1
//If you want to share files read/write<Selinux将本机的NFS共享设置成可读可写>
setsebool -P nfs_export_all_rw 1
//If you want to use a remote NFS server for the home directories on this machine
<如果你想要将远程NFS的家目录共享到本机,需要开启>
setsebool -P use_nfs_home_dirs 1
===samba===
//If you want to share files other than home directorie
< 如果你希望将目录共享给其他用户,你需要设置>
chcon -t samba_share_t /directory
//If you want to share files with multiple domains
如果samba服务器共享目录给多个域,则需要:
setsebool -P allow_smbd_anon_write=1
//If you are setting up this machine as a Samba server and wish to share the home directories
samba服务器要共享家目录时:
setsebool -P samba_enable_home_dirs 1
//If you want to use a remote Samba server for the home directories on this machine
如果你需在本机上使用远程samba服务器的家目录
setsebool -P use_samba_home_dirs 1
//You can disable SELinux protection for the samba daemon by executing
关闭selinux关于samba的进程守护的保护
setsebool -P smbd_disable_trans 1
service smb restart
===rsync===
//If you want to share files using the rsync daemon
共享rsync目录时:
chcon -t public_content_t /directories
//If you want to share files with multiple domains
允许其他用户写入时
setsebool -P allow_rsync_anon_write=1
//You can disable SELinux protection for the rsync daemon by executing
停止rsync的进程保护
setsebool -P rsync_disable_trans 1
===kerberos===
//allow your system to work properly in a Kerberos environment
允许系统使用kerberos
setsebool -P allow_kerberos 1
//If you are running Kerberos daemons kadmind or krb5kdc
setsebool -P krb5kdc_disable_trans 1
service krb5kdc restart
setsebool -P kadmind_disable_trans 1
service kadmind restart
===nis===
Allow your system to work properly in a NIS environment
系统工作在nis环境时
setsebool -P allow_ypbind 1
实验四、selinux的troubleshoot
关闭SElinux问题直接解决说明很可能是SElinux的问题
方法一
如果SElinux阻止了某项服务,可以先设置SElinux为permissive模式,然后查看日志
方法二
#service auditd restart
#tail -f /var/log/message
Nov :: rhel2 setroubleshoot: SELinux is preventing /usr/sbin/httpd from name_bind access on the tcp_socket port .
For complete SELinux messages run: sealert -l 477211dd-4f0a-4c46-a295-7eef08bf545b
Nov :: rhel2 python: SELinux is preventing /usr/sbin/httpd from name_bind access on the tcp_socket port .##*****
Plugin bind_ports (92.2 confidence) suggests ************************##012If you want to allow /usr/sbin/httpd to bind to network port 8899
#012Then you need to modify the port type.#012Do## semanage port -a -t PORT_TYPE -p tcp #
where PORT_TYPE is one of the following: http_cache_port_t, http_port_t, jboss_management_port_t, jboss_messaging_port_t, ntop_port_t, puppet_port_t.
##***** Plugin catchall_boolean (7.83 confidence) suggests ******************##012If you want to allow nis to enabled
#012Then you must tell SELinux about this by enabling the 'nis_enabled' boolean.#012You can read 'None' man page for more details.
#012Do#012setsebool -P nis_enabled ##***** Plugin catchall (1.41 confidence) suggests **************************
##012If you believe that httpd should be allowed name_bind access on the port tcp_socket by default.
#012Then you should report this as a bug.#012You can generate a local policy module to allow this access.
#012Do#012allow this access for now by executing:## ausearch -c 'httpd' --raw | audit2allow -M my-httpd#012
# semodule -i my-httpd.pp#
#sealert -l 477211dd-4f0a-4c46-a295-7eef08bf545b
[root@rhel2 ~]# sealert -l 477211dd-4f0a-4c46-a295-7eef08bf545b
SELinux is preventing /usr/sbin/httpd from name_bind access on the tcp_socket port . ***** Plugin bind_ports (92.2 confidence) suggests ************************ If you want to allow /usr/sbin/httpd to bind to network port
Then you need to modify the port type.
Do
# semanage port -a -t PORT_TYPE -p tcp
where PORT_TYPE is one of the following: http_cache_port_t, http_port_t, jboss_management_port_t, jboss_messaging_port_t, ntop_port_t, puppet_port_t. ***** Plugin catchall_boolean (7.83 confidence) suggests ****************** If you want to allow system to run with NIS
Then you must tell SELinux about this by enabling the 'nis_enabled' boolean.
You can read 'None' man page for more details.
Do
setsebool -P nis_enabled ***** Plugin catchall (1.41 confidence) suggests ************************** If you believe that httpd should be allowed name_bind access on the port tcp_socket by default.
Then you should report this as a bug.
You can generate a local policy module to allow this access.
Do
allow this access for now by executing:
# ausearch -c 'httpd' --raw | audit2allow -M my-httpd
# semodule -i my-httpd.pp Additional Information:
Source Context system_u:system_r:httpd_t:s0
Target Context system_u:object_r:unreserved_port_t:s0
Target Objects port [ tcp_socket ]
Source httpd
Source Path /usr/sbin/httpd
Port
Host rhel2.rusky.com
Source RPM Packages httpd-2.4.-.el7.x86_64
Target RPM Packages
Policy RPM selinux-policy-3.13.-.el7.noarch
Selinux Enabled True
Policy Type targeted
Enforcing Mode Enforcing
Host Name rhel2.rusky.com
Platform Linux rhel2.rusky.com 3.10.-.el7.x86_64 # SMP
Thu Jul :: EDT x86_64 x86_64
Alert Count
First Seen -- :: CST
Last Seen -- :: CST
Local ID 477211dd-4f0a-4c46-a295-7eef08bf545b Raw Audit Messages
type=AVC msg=audit(1510304292.2:): avc: denied { name_bind } for pid= comm="httpd" src= scontext=system_u:system_r:httpd_t:s0 tcontext=system_u:object_r:unreserved_port_t:s0 tclass=tcp_socket type=SYSCALL msg=audit(1510304292.2:): arch=x86_64 syscall=bind success=no exit=EACCES a0= a1=55cf7ca992e8 a2= a3=7ffca3c9125c items= ppid= pid= auid= uid= gid= euid= suid= fsuid= egid= sgid= fsgid= tty=(none) ses= comm=httpd exe=/usr/sbin/httpd subj=system_u:system_r:httpd_t:s0 key=(null) Hash: httpd,httpd_t,unreserved_port_t,tcp_socket,name_bind
#sealert -b --通过图形化界面troubleshooting
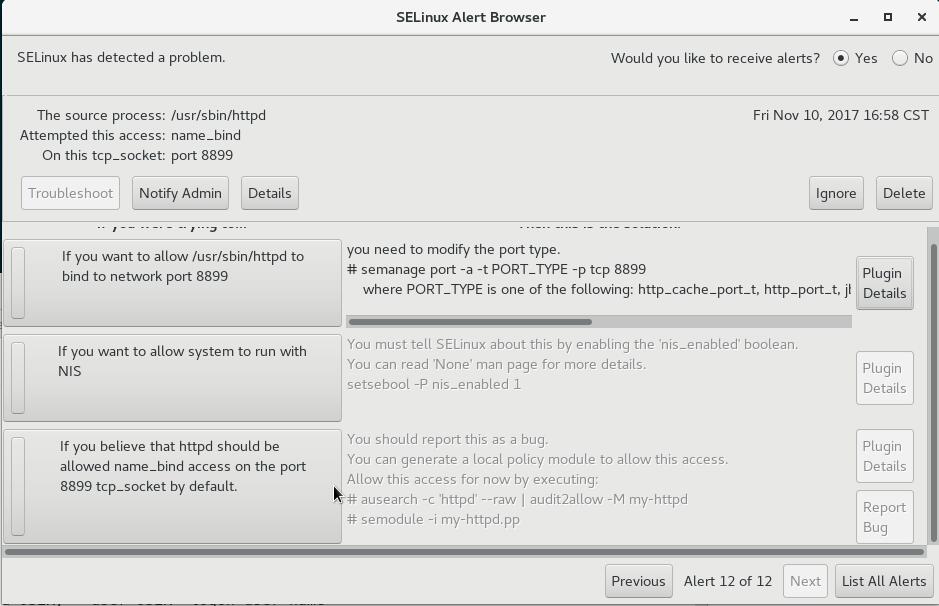
方法三
audit2why < /var/log/audit/audit.log
audit2allow < /var/log/audit/audit.log
SElinux测试及排错的更多相关文章
- Testing - 测试基础 - 方法
选择和使用测试方法和工具 按照测试需求用途(或测试技巧)选择 在软件开发生命周期和软件测试流程中适当地选择 按照测试人员实际技能选择 选择可提供的和可执行的 测试方法 类别及技巧 目标 使用方法 举例 ...
- SELINUX配置
今天试着将centos7的ssh默认端口改成1234,但改了后,SSHD服务竟然启动不了了.后来关了selinux测试,果然可以了.但这是运行环境,不能关,所以不得不配置semanage! 一.安装s ...
- 没有15k薪资都不会了解的测试内幕
软件测试的工程师阶层是指随着行业的飞速发展,测试人员犹如身在洪流之中“逆水行舟不进则退”.知其然已经无法满足当今的测试人员,还要知其所以然.所以测试人员不仅仅要关注系统外部结构,还得了解系统内部的逻辑 ...
- 技术实战:基于 MHA 方式实现 MySQL 的高可用(转)
转自:http://os.51cto.com/art/201307/401702_all.htm MHA故障转移可以很好的帮我们解决从库数据的一致性问题,同时最大化挽回故障发生后的数据.本文分享了基于 ...
- Windows Server 2008 R2 配置AD(Active Directory)域控制器
实施过程: 一.安装Windows Server2008 R2操作系统 (过程略) 二.安装域控制器 1. 修改电脑名称 2.修改电脑DNS 三.配置AD 1.在"服务器管理器"- ...
- 【转】SQLServerDBA十大必备工具---让生活轻松点
曾经和一些DBA和数据库开发人员交流时,问他们都用过一些什么样的DB方面的工具,大部分人除了SSMS和Profile之外,基本就没有使用过其他工具了: 诚然,SSMS和Profile足够强大,工作的大 ...
- 解决 LINUX mysql不能通过IP连接 只能localhost 权限没问题情况下
最近朋友的一个服务器出现了一个奇怪的问题,弄了两个星期没有解决,在哥坚持不懈的努力下,终于解决了问题.发出来给需要的朋友. 问题:php程序连接mysql只能使用localhost,不能使用127.0 ...
- SQLServerDBA十大必备工具---让生活轻松点(转)
曾经和一些DBA和数据库开发人员交流时,问他们都用过一些什么样的DB方面的工具,大部分人除了SSMS和Profile之外,基本就没有使用过其他工具了: 诚然,SSMS和Profile足够强大,工作的大 ...
- PHP程序开发人员要掌握的知识
文件目录处理函数包80%以上的函数的功能的灵活运用. 日期时间函数中的80%以上的函数的功能的灵活运用 数学函数库中的100%的内容. 网络库中的60%以上的内容,对各个函数的功能比较熟悉. 字符串处 ...
随机推荐
- react常用模块介绍
react各个模块: 1.node.js自带的模块(原生模块):https://www.jianshu.com/p/abc72267abfc原生模块的api文档地址:http://nodejs.cn/ ...
- 也给我的E420拆机清清灰尘
用了两年,天气燥热,是得拆开清理下了,E430清理非常方便,拆开后面挡板就行,E420就麻烦很多,需要全部拆下,关于E420的拆机网上已经有非常详细的教程了,我这里做一些补充,有兴趣的同学欢迎参考. ...
- 浅谈Hybrid技术的设计与实现【转】
https://www.cnblogs.com/yexiaochai/p/4921635.html 前言 浅谈Hybrid技术的设计与实现 浅谈Hybrid技术的设计与实现第二弹 浅谈Hybrid技术 ...
- ZooKeeper 了解
- [Go] Returning Multiple Values from a Function in Go
Returning multiple values from a function is a common idiom in Go, most often used for returning val ...
- 10.2.1itools导入不了歌曲
首先下载iTools 4抢先版,下载地址:http://update2.itools.hk/api/v1/redirect?p=itools4&c=pc_Thinksky 点击电脑桌面左下方“ ...
- Unity3D for Mac 破解
每次版本更新又忘记怎么搞了.干脆记下来! 1安装Unity 2安装成功后打开Applecation>Unity>Unity(右击显示包内容)>contents>MacOS 3用 ...
- poj 3042 Grazing on the Run
这个题目原型应该是吃完所有的草丛的最小时间,现在变成了每个草丛被吃的时间和,貌似如果还是按照原来的dp方法dp[i][j]表示吃完i到j的草丛的花掉的时间的话,有两个因素会影响后面的决策,一个是花掉的 ...
- Windows服务安装与控制
Windows服务安装与控制 1.建立服务 (1)定义一个ServiceInstaller using System; using System.Collections.Generic; using ...
- app_offline.htm
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.1//EN" "http://www.w3.org/TR/xhtml11/DT ...
