hdu 4119 Isabella's Message
Isabella's Message
Time Limit: 2000/1000 MS (Java/Others) Memory Limit: 32768/32768 K (Java/Others)
Total Submission(s): 1365 Accepted Submission(s): 400
The encrypted message is an N * N matrix, and each grid contains a character.
Steve uses a special mask to work as a key. The mask is N * N(where N is an even number) matrix with N*N/4 holes of size 1 * 1 on it.
The decrypt process consist of the following steps:
1. Put the mask on the encrypted message matrix
2. Write down the characters you can see through the holes, from top to down, then from left to right.
3. Rotate the mask by 90 degrees clockwise.
4. Go to step 2, unless you have wrote down all the N*N characters in the message matrix.
5. Erase all the redundant white spaces in the message.
For example, you got a message shown in figure 1, and you have a mask looks like figure 2. The decryption process is shown in figure 3, and finally you may get a message "good morning".
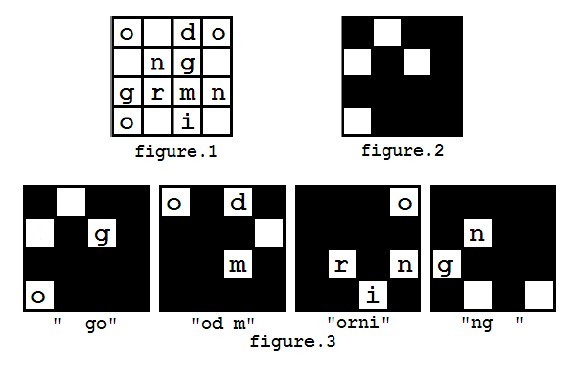
You can assume that the mask is always carefully chosen that each character in the encrypted message will appear exactly once during decryption.
However, in the first step of decryption, there are several ways to put the mask on the message matrix, because the mask can be rotated (but not flipped). So you may get different results such as "od morning go" (as showed in figure 4), and you may also get other messages like "orning good m", "ng good morni".
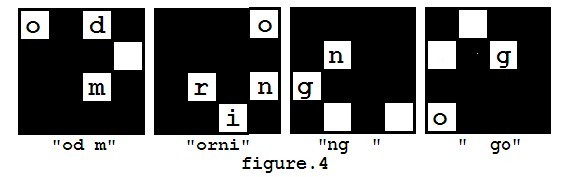
Steve didn't know which direction of the mask should be chosen at the beginning, but after he tried all possibilities, he found that the message "good morning" is the only one he wanted because he couldn't recognize some words in the other messages. So he will always consider the message he can understand the correct one. Whether he can understand a message depends whether he knows all the words in the message. If there are more than one ways to decrypt the message into an understandable one, he will choose the lexicographically smallest one. The way to compare two messages is to compare the words of two messages one by one, and the first pair of different words in the two messages will determine the lexicographic order of them.
Isabella sends letters to Steve almost every day. As decrypting Isabella's message takes a lot of time, and Steve can wait no longer to know the content of the message, he asked you for help. Now you are given the message he received, the mask, and the list of words he already knew, can you write a program to help him decrypt it?
Each test case contains several lines.
The first line contains an even integer N(2 <= N <= 50), indicating the size of the matrix.
The following N lines each contains exactly N characters, reresenting the message matrix. The message only contains lowercase letters and periods('.'), where periods represent the white spaces.
You can assume the matrix contains at least one letter.
The followingN lines each containsN characters, representing the mask matrix. The asterisk('*') represents a hole, and period('.') otherwise. The next line contains an integer M(1 <= M <= 100), the number of words he knew.
Then the following M lines each contains a string represents a word. The words only contain lowercase letters, and its length will not exceed 20.
If Steve cannot understand the message, just print the Y as "FAIL TO DECRYPT".
4
o.do
.ng.
grmn
o.i.
.*..
*.*.
....
*...
2
good
morning
4
..lf
eoyv
oeou
vrer
..*.
.*..
....
*.*.
5
i
you
the
love
forever
4
.sle
s.c.
e.fs
..uu
*...
.*..
...*
..*.
1
successful
Case #2: love you forever
Case #3: FAIL TO DECRYPT
- #include <iostream>
- #include <stdio.h>
- #include <string.h>
- using namespace std;
- #define MAXN 55
- struct node {
- char map[MAXN][MAXN];
- };
- int n,kk;char str[4][10000],lib[10000][25],anss[10000],stemp[10000];int strnum[4];
- bool strflag[4];
- node change(node a)
- {
- int i,j,ii,k;node b;
- for(i=0,ii=0;i<n;i++,ii++)
- {
- for(j=n-1,k=0;j>=0;j--,k++)
- {
- b.map[ii][k]=a.map[j][i];
- }
- }
- return b;
- }
- bool find(char str[])
- {
- int i;
- for(i=0;i<kk;i++)
- {
- if(strcmp(str,lib[i])==0)
- return true;
- }
- return false;
- }
- int main()
- {
- int tcase,i,j,i2,space,tt=1;
- node a,b;
- scanf("%d",&tcase);
- while(tcase--)
- {
- memset(strnum,0,sizeof(strnum));
- memset(strflag,true,sizeof(strflag));
- for(i=0;i<4;i++)
- {
- memset(str[i],0,sizeof(str[i]));
- }
- scanf("%d",&n);
- gets(stemp);
- for(i=0;i<n;i++)
- {
- for(j=0;j<n;j++)
- {
- char c=getchar();
- a.map[i][j]=c;
- }
- gets(stemp);
- }
- for(i=0;i<n;i++)
- {
- for(j=0;j<n;j++)
- {
- char c=getchar();
- b.map[i][j]=c;
- }
- gets(stemp);
- }
- scanf("%d",&kk);
- gets(stemp);
- for(i=0;i<kk;i++)
- {
- scanf("%s",lib[i]);
- }
- memset(stemp,0,sizeof(stemp));
- int space=0;node primeb=b;
- for(i=0;i<4;i++)
- {
- bool flag=true;space=0;b=primeb;
- for(j=0;j<4&&flag;j++)
- {
- for(int ii=0;ii<n&&flag;ii++)
- for(int jj=0;jj<n&&flag;jj++)
- {
- if(b.map[ii][jj]=='*')
- {
- if(a.map[ii][jj]=='.'&&space>0)
- {
- stemp[space++]='\0';
- if(!find(stemp))
- {
- flag=false;
- strflag[i]=false;
- }
- else
- {
- str[i][strnum[i]++]=' ';
- for(i2=0;i2<=space-2;i2++)
- {
- str[i][strnum[i]++]=stemp[i2];
- }
- }
- space=0;
- }
- if(a.map[ii][jj]!='.')
- {
- stemp[space++]=a.map[ii][jj];
- }
- }
- }
- b=change(b);
- }
- if(space>0&&flag)
- {
- stemp[space++]='\0';
- if(!find(stemp))
- {
- flag=false;
- strflag[i]=false;
- }
- else
- {
- str[i][strnum[i]++]=' ';
- for(i2=0;i2<=space-2;i2++)
- {
- str[i][strnum[i]++]=stemp[i2];
- }
- }
- space=0;
- }
- primeb=change(primeb);
- }
- bool flag=true;
- for(i=0;i<4;i++)
- {
- if(strflag[i])
- {
- str[i][strnum[i]++]='\0';
- if(flag)
- {
- strcpy(anss,str[i]);
- flag=false;
- }
- if(strcmp(anss,str[i])>0)
- strcpy(anss,str[i]);
- }
- }
- if(!flag)
- printf("Case #%d:%s\n",tt++,anss);
- else
- printf("Case #%d: FAIL TO DECRYPT\n",tt++);
- }
- return 0;
- }
hdu 4119 Isabella's Message的更多相关文章
- hdu 4119 Isabella's Message 模拟题
Isabella's Message Time Limit: 20 Sec Memory Limit: 256 MB 题目连接 http://acm.hdu.edu.cn/showproblem.p ...
- hdu 3410 Passing the Message(单调队列)
题目链接:hdu 3410 Passing the Message 题意: 说那么多,其实就是对于每个a[i],让你找他的从左边(右边)开始找a[j]<a[i]并且a[j]=max(a[j])( ...
- hdu 4300 Clairewd’s message KMP应用
Clairewd’s message 题意:先一个转换表S,表示第i个拉丁字母转换为s[i],即a -> s[1];(a为明文,s[i]为密文).之后给你一串长度为n<= 100000的前 ...
- hdu 4300 Clairewd’s message(具体解释,扩展KMP)
题目链接:http://acm.hdu.edu.cn/showproblem.php?pid=4300 Problem Description Clairewd is a member of FBI. ...
- hdu 4300 Clairewd’s message(扩展kmp)
Problem Description Clairewd is a member of FBI. After several years concealing in BUPT, she interce ...
- HDU 4300 Clairewd’s message(KMP+思维)
题目链接:http://acm.hdu.edu.cn/showproblem.php?pid=4300 题目大意:题目大意就是给以一段字符xxxxzzz前面x部分是密文z部分是明文,但是我们不知道是从 ...
- 【HDU 4300 Clairewd’s message】
Clairewd is a member of FBI. After several years concealing in BUPT, she intercepted some important ...
- HDU - 3410 Passing the Message 单调递减栈
Passing the Message What a sunny day! Let’s go picnic and have barbecue! Today, all kids in “Sun Flo ...
- hdu 4300 Clairewd’s message 字符串哈希
Clairewd’s message Time Limit: 2000/1000 MS (Java/Others) Memory Limit: 32768/32768 K (Java/Other ...
随机推荐
- Css元素布局定位
<!DOCTYPE HTML> <html lang="zh-cn"> <head> <meta charset="UTF-8& ...
- intellj idea 如何设置类头注释和方法注释
intellj idea 如何设置类头注释和方法注释 intellj idea的强大之处就不多说了,相信每个用过它的人都会体会到,但是我们也会被他的复杂搞的晕头转向,尤其刚从ecl ...
- 在View中使用CGridCtrl时出现系统异常
一.简介 我的程序是单文档程序,我的View视图需要使用CGridCtrl,于是我把CGridCtrl作为子窗口嵌入到View中覆盖住整个View.由于不能像gridctrl_demo227那样直接在 ...
- HDU 4498 Function Curve (分段, simpson)
转载请注明出处,谢谢http://blog.csdn.net/ACM_cxlove?viewmode=contents by---cxlove 最近太逗了...感觉成都要打铁了...只能给队友端 ...
- 关于微信浏览不能URL传参,URL中的问号被删除
关于微信浏览不能URL传参,URL中的问号被删除. 尼玛难道没有人遇到过这个问题?看了微信支付SDK3.0的代码,看到urlencode 看到了几次.实际上 在微信浏览器下 header('locat ...
- php-Eclipse对php中的namespace关键字报语法错误的问题
namespace是php5.3以上才支持的, 解决办法:升级IDE 切换Eclipse中的php版本 Window > Preferences > PHP > PHP Int ...
- hdu 2471 简单DP
题目链接:http://acm.hdu.edu.cn/showproblem.php?pid=2571 简单dp, dp[n][m] +=( dp[n-1][m],dp[n][m-1],d[i][k ...
- VC++或QT下 高精度 多媒体定时器
在VC编程中,用SetTimer可以定义一个定时器,到时间了,就响应OnTimer消息,但这种定时器精度太低了.如果需要精度更高一些的定时器(精 确到1ms),可以使用下面的高精度多媒体定时器进行代码 ...
- RIA Service 的 SOAP EndPoint
原文 www.cyqdata.com/cnblogs/article-detail-39983-english 越来越多的朋友都在使用Silverlight开发应用程序,其中我们常用的还会有一个特殊的 ...
- GitHub Android 最火开源项目Top20 GitHub 上的开源项目不胜枚举,越来越多的开源项目正在迁移到GitHub平台上。基于不要重复造轮子的原则,了解当下比较流行的Android与iOS开源项目很是必要。利用这些项目,有时能够让你达到事半功倍的效果。
1. ActionBarSherlock(推荐) ActionBarSherlock应该算得上是GitHub上最火的Android开源项目了,它是一个独立的库,通过一个API和主题,开发者就可以很方便 ...
