IDA断点和搜索
一、断点
调试很重要一点是下断点,看看IDA提供的功能,本来已经和WinDbg一样强了。
官方文档的变化
Edit breakpoint
Action name: BreakpointEdit
Condition(6.5及之前版本)
This IDC expression will be evaluated each time the breakpoint
is reached. If the expression returns true, the debugger will execute the
selected actions. Please note that you can use the register names in the
IDC scripts when the debugger is active. Tests like this would be ok,
for example: EAX == EBX+5 or Dword(ESP+0x10) == 34
Condition(6.6版本开始)
This IDC expression will be evaluated each time the breakpoint
is reached. If the expression returns true (non-zero), the debugger will execute the
selected actions. Please note that you can use the register names in the
IDC scripts when the debugger is active. Tests like this are allowed,
for example: EAX == EBX+5 or Dword(ESP+0x10) == 34
You can also use the "..." button to enter a multiline condition, or specify
another scripting language to use. See here for
more info.
Breakpoint conditions |
You can use the "Condition" field of the breakpoint properties to enter an expression which is evaluated when the breakpoint is hit. It can be either an actual condition or just any valid code in IDC or another supported scripting language syntax. By using the "..." button, you can open a multi-line editor for the condtition and switch the scripting language used for evaluating it.
Expressions
If you enter an expression, the result will be used to determine whether
the selected actions are exectuted. Some examples of IDC expressions:
Check if EAX is equal to 5:
EAX==5
Check if the first argument to the function is 1:
Dword(ESP)==1
Interpret the second argument to the function as a pointer to Unicode string, print it,
and return 0 (so that the execution continues immediately):
Message("Filename: %s\n", GetString(Dword(ESP+4), -1, ASCSTR_UNICODE)), 0
Set EAX to 0 and continue:
EAX=0,0
Statements
You can enter several statements in the multi-line editor. If the last one is a 'return' statement,
it is used as the result of the condition. Otherwise the condition is assumed to return 0.
可以看出新变化,支持多行编辑了,更好更方便更加强大。举得例子也让我想起逗号表示式了,也就是不断点打印日志可以使用这种方式。
逗号表达式表达式1,表达式2,表达式3,...... ,表达式n逗号表达式的要领:(1) 逗号表达式的运算过程为:从左往右逐个计算表达式。(2) 逗号表达式作为一个整体,它的值为最后一个表达式(也即表达式n)的值。(3) 逗号运算符的优先级别在所有运算符中最低。如:(3+5,6+8)的值是14,(a=3*5,a*4)的值是60。
官方网站更新介绍:https://www.hex-rays.com/products/ida/6.6/,里面有许多改变,这里看编辑条件断点。
Multiline breakpoint conditions
Python users will love this: now it is possible to write a multiline condition right in the 'edit breakpoint' dialog box. IDA even accepts function definitions there!

以前的
1、断点:
参考:自带文档,调试菜单(Debugger submenu)-断点子菜单(Breakpoints submenu)-编辑断点(Edit breakpoint)章节和IDC之表达式(IDC: Expressions)一章
条件断点,可以输入一个IDC表达式,如果在调试状态下可以使用寄存器名字。
Condition
This IDC expression will be evaluated each time the breakpoint
is reached. If the expression returns true, the debugger will execute the
selected actions. Please note that you can use the register names in the
IDC scripts when the debugger is active. Tests like this would be ok,
for example: EAX == EBX+5 or Dword(ESP+0x10) == 34
案例1:自定义打印跟踪执行某条语句时的各种值。
Alphabetical list of IDC functions
The following conventions are used in the function descriptions:
'ea' is a linear address
'success' is 0 if a function fails, 1 otherwise
'void' means that function returns no meaningful value (always 0)
'anyvalue' means that function may return value of any type
一个永远返回假的条件表达式:0 * Message("%s = %d\n", atoa(Dword(R2+0x10)), R2+0x20)
这里我试过,需要与0相乘,确保假。
远程调试,字符串指针R2+0x10的值是"crack"的表达式
'c' == DbgByte(DbgDword(R2+0x10)) && 'r' == DbgByte(1+DbgDword(R2+0x10)) && 'a' == DbgByte(2+DbgDword(R2+0x10)) && 'c' == DbgByte(3+DbgDword(R2+0x10)) && 'k' == DbgByte(4+DbgDword(R2+0x10))
案例2:根据前一条语句的某些值来对某语句下条件断点。

CODE:00234EC8 loc_234EC8: ; CODE XREF: sub_234DD8+CB↑j
CODE:00234EC8 mov eax, edi
CODE:00234ECA call sub_193ED4
CODE:00234ECF push eax ; hWnd
CODE:00234ED0 call GetWindowTextLengthW
CODE:00234ED5 mov edx, eax
CODE:00234ED7 inc edx
CODE:00234ED8 mov eax, esi
CODE:00234EDA call sub_E48AC
CODE:00234EDF mov eax, [esi]
CODE:00234EE1 call sub_E4544
CODE:00234EE6 push eax ; nMaxCount
CODE:00234EE7 mov eax, [esi]
CODE:00234EE9 call sub_E4534
CODE:00234EEE push eax ; lpString 压入第二参数,缓冲区指针地址,可利用条件断点保存EAX值
CODE:00234EEF mov eax, edi
CODE:00234EF1 call sub_193ED4
CODE:00234EF6 push eax ; hWnd
CODE:00234EF7 call GetWindowTextW
CODE:00234EFC mov eax, [esi] ; 执行完GetWindowTextW后在这里利用条件断点查看缓冲区
CODE:00234EFE call sub_E4544
CODE:00234F03 mov edx, eax
CODE:00234F05 dec edx
CODE:00234F06 mov eax, esi
CODE:00234F08 call sub_E48AC
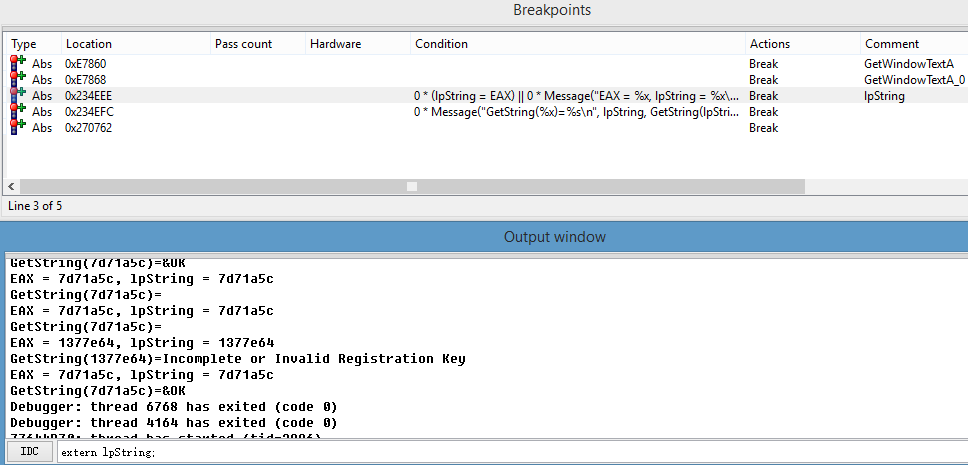
在执行完GetWindowTextW想看里的内容或者根据lpString来下条件断点。可以这样:
1、在IDA底部的IDC命令行声明一个全局变量:extern lpString;
2、在CODE:00234EEE处下表达式始终为假的条件断点:0 * (lpString = EAX) || 0 * Message("EAX = %x, lpString = %x\n", EAX, lpString)
3、在CODE:00234EFC处下条件断点,表达式为:0 * Message("GetString(Address_%x)=%s\n", lpString, GetString(Dword(lpString),-1, ASCSTR_UNICODE))
结果打印类似如下:
EAX = 7d71a5c, lpString = 7d71a5c
GetString(Address_7d71a5c)=
EAX = 7d5ebb4, lpString = 7d5ebb4
GetString(Address_7d5ebb4)=
在IDA底部的IDC命令行输入lpString执行,查看lpString,嗯起作用了
IDC>lpString
131460020. 7D5EBB4h 765365664o 00000111110101011110101110110100b '措'
在CODE:00234EFC处下条件断点,表达式为:
0 * Message("GetString(%x)=%s\n", lpString, GetString(lpString,-1, ASCSTR_UNICODE))
EAX = 7d71a5c, lpString = 7d71a5c
GetString(7d71a5c)=
EAX = 1377e64, lpString = 1377e64
GetString(1377e64)=Incomplete or Invalid Registration Key
EAX = 7d71a5c, lpString = 7d71a5c
GetString(7d71a5c)=&OK
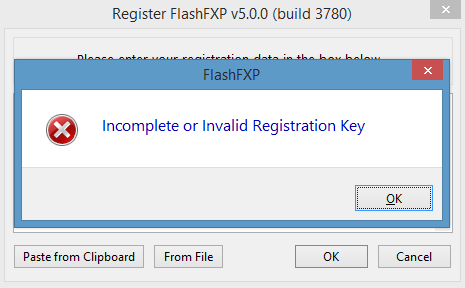
字符串比较断点:
断点地址 User32.dll BOOL SetWindowText(HWND hwnd,LPCTSTR lpString);
断点条件 0*Message("wchar(%x)=%s\n", Dword(ESP+8), GetString(Dword(ESP+8),-1, ASCSTR_UNICODE)) || GetString(Dword(ESP+8),-1, ASCSTR_UNICODE) == "Incomplete or Invalid Registration Key"
其中,逻辑||前为打印调用的历史记录。
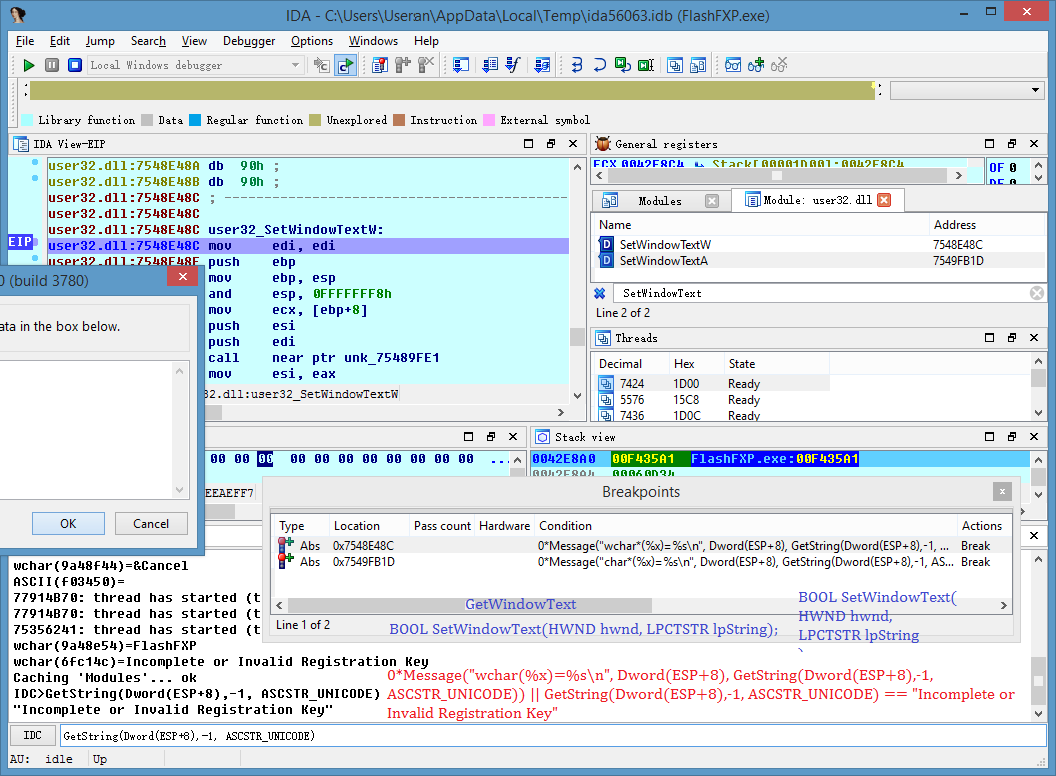
2、程式化下条件断点
见文档Breakpoint handling functions一章
// Set breakpoint condition
// address - any address in the breakpoint range
// cnd - breakpoint condition
// is_lowcnd- 0:regular condition,1:low level condition
// Returns: success success SetBptCndEx(long ea, string cnd, long is_lowcnd);
#define SetBptCnd(ea, cnd) SetBptCndEx(ea, cnd, 0)
Debugger: control
***********************************************
Execute one instruction in the current thread.
Other threads are kept suspended.
//
NOTE
You must call GetDebuggerEvent() after this call
in order to find out what happened. Normally you will
get the STEP event but other events are possible (for example,
an exception might occur or the process might exit).
This remark applies to all execution control functions.
The event codes depend on the issued command.
returns: successsuccess StepInto(void);
IDA 5.2持调试器除了支持以往的事件的模型,还允许设计一个顺序
执行(线性模型)的IDC 脚本来控制调试器。以往的基于事件的模型依然可用,同时也可通过使
用 get_debugger_event()这个函数来支持简单的线性模型。这个函数暂停插件(或脚本)
的执行直到一个新的调试器时间发生。使用者可以指定他是只对进程挂起事件感兴趣或是对
所有事件。也可以进行定时设置,如果没有其它事件发生,超时后程序可以继续执行。
#include <idc.idc> //--------------------------------------------------------------------------
static main()
{
auto code, bptea_some_addrese; AppBpt(bptea_some_addrese); // 在某地址下断点
StartDebugger("","",""); // 调试start debugger with default params
code = GetDebuggerEvent(WFNE_SUSP, -); // 等待断点发生... and wait for bpt
if ( code <= )
return Failed(code); Message ("Stopped at %a, event code is %x\n", GetEventEA(), GetEventId()); // 打印消息 StepInto(); // 扮演跟进行动 request a single step
GetDebuggerEvent(WFNE_SUSP, -); // ... and wait for app to execute
StepInto(); // request a single step
GetDebuggerEvent(WFNE_SUSP, -); // ... and wait for app to execute
DelBpt(bptea);
}
//-------------------------------------------------------------------------- // Print an failure message
static Failed(code)
{
Warning("Failed, sorry (code %d)", code);
return ;
}
UUNP 解压器插件的核心功能
http://blog.csdn.net/eqera/article/details/8239505
#include <idc.idc> //--------------------------------------------------------------------------
static main()
{
auto ea, bptea, tea1, tea2, code, minea, maxea;
auto r_esp, r_eip, caller, funcname; // Calculate the target IP range. It is the first segment.
// As soon as the EIP register points to this range, we assume that
// the unpacker has finished its work.
tea1 = FirstSeg();
tea2 = SegEnd(tea1); // Calculate the current module boundaries. Any calls to GetProcAddress
// outside of these boundaries will be ignored.
minea = MinEA();
maxea = MaxEA(); // Launch the debugger and run until the entry point
if ( !RunTo(BeginEA()) )
return Failed(-); // Wait for the process to stop at the entry point
code = GetDebuggerEvent(WFNE_SUSP, -);
if ( code <= )
return Failed(code); // Set a breakpoint at GetProcAddress
bptea = LocByName("kernel32_GetProcAddress");
if ( bptea == BADADDR )
return Warning("Could not locate GetProcAddress");
AddBpt(bptea); while ( )
{
// resume the execution and wait until the unpacker calls GetProcAddress
code = GetDebuggerEvent(WFNE_SUSP|WFNE_CONT, -);
if ( code <= )
return Failed(code); // check the caller, it must be from our module
r_esp = GetRegValue("ESP");
caller = Dword(r_esp);
if ( caller < minea || caller >= maxea )
continue; // if the function name passed to GetProcAddress is not in the ignore-list,
// then switch to the trace mode
funcname = GetString(Dword(r_esp+), -, ASCSTR_C);
// ignore some api calls because they might be used by the unpacker
if ( funcname == "VirtualAlloc" )
continue;
if ( funcname == "VirtualFree" )
continue; // A call to GetProcAddress() probably means that the program has been
// unpacked in the memory and now is setting up its import table
break;
} // trace the program in the single step mode until we jump to
// the area with the original entry point.
DelBpt(bptea);
EnableTracing(TRACE_STEP, );
for ( code = GetDebuggerEvent(WFNE_ANY|WFNE_CONT, -); // resume
code > ;
code = GetDebuggerEvent(WFNE_ANY, -) )
{
r_eip = GetEventEa();
if ( r_eip >= tea1 && r_eip < tea2 )
break;
}
if ( code <= )
return Failed(code); // as soon as the current ip belongs OEP area, suspend the execution and
// inform the user
PauseProcess();
code = GetDebuggerEvent(WFNE_SUSP, -);
if ( code <= )
return Failed(code); EnableTracing(TRACE_STEP, ); // Clean up the disassembly so it looks nicer
MakeUnknown(tea1, tea2-tea1, DOUNK_EXPAND|DOUNK_DELNAMES);
MakeCode(r_eip);
AutoMark2(tea1, tea2, AU_USED);
AutoMark2(tea1, tea2, AU_FINAL);
TakeMemorySnapshot();
MakeName(r_eip, "real_start");
Warning("Successfully traced to the completion of the unpacker code\n"
"Please rebuild the import table using renimp.idc\n"
"before stopping the debugger");
}
//--------------------------------------------------------------------------
// Print an failure message
static Failed(code)
{
Warning("Failed to unpack the file, sorry (code %d)", code);
return ;
}
二、搜索
addr = FindBinary(, SEARCH_DOWN, "31 32 33 34 35 36 37 38 39"); #ea = FindText(ea, SEARCH_NEXT | SEARCH_REGEX, , , "test *[a-zA-Z]*, +[a-zA-Z]*") MinEA() 等价于 GetLongPrm(INF_MIN_EA)
而INF_MIN_EA // int32; The lowest address used // in the program //
IDC>auto ea_result = FindText(MinEA() ,SEARCH_DOWN|SEARCH_NEXT, , , ""); Message("%s %x\n", BADADDR == ea_result ? "bad" : "ok", ea_result);
bad ffffffff //查找mov dword ptr [eax+1Ch], offset sub_11010类似这种形式的指令
IDC>auto ea = ; ea = FindText(ea, SEARCH_DOWN |SEARCH_NEXT | SEARCH_REGEX, , , "mov +dword ptr \\[[a-zA-Z]+\\+[a-zA-Z0-9_ ]+h\\],[a-zA-Z0-9_ ]*"); Message("Find in %x\n", ea); if(BADADDR != ea) {auto op2_addr = GetOperandValue(ea,); Message("op2 address is %x\n", op2_addr);}
Find in //双击这里自动定位代码
op2 address is
IDA断点和搜索的更多相关文章
- UVA - 11212 Editing a Book(IDA*算法+状态空间搜索)
题意:通过剪切粘贴操作,将n个自然段组成的文章,排列成1,2,……,n.剪贴板只有一个,问需要完成多少次剪切粘贴操作可以使文章自然段有序排列. 分析: 1.IDA*搜索:maxn是dfs的层数上限,若 ...
- HDU 1560 DNA sequence (IDA* 迭代加深 搜索)
题目地址:http://acm.hdu.edu.cn/showproblem.php?pid=1560 BFS题解:http://www.cnblogs.com/crazyapple/p/321810 ...
- uva 11212 - Editing a Book(迭代加深搜索 IDA*) 迭代加深搜索
迭代加深搜索 自己看的时候第一遍更本就看不懂..是非常水,但智商捉急也是没有办法的事情. 好在有几个同学已经是做过了这道题而且对迭代加深搜索的思路有了一定的了解,所以在某些不理解的地方询问了一下他们的 ...
- POJ2286 The Rotation Game[IDA*迭代加深搜索]
The Rotation Game Time Limit: 15000MS Memory Limit: 150000K Total Submissions: 6325 Accepted: 21 ...
- IDA Pro 权威指南学习笔记(九) - 数据搜索
Search -> Next Code 命令将光标移动到下一个包含指令的位置 Jump -> Jump to Function 命令可以打开所有函数,可以迅速选择一个函数并导航到该函数所在 ...
- codevs2495 水叮当的舞步 IDA*
我打暴力不对,于是就看看题解,,,,,,IDA*就是限制搜索深度而已,这句话给那些会A*但不知道IDA*是什么玩意的小朋友 看题解请点击这里 上方题解没看懂的看看这:把左上角的一团相同颜色的范围,那个 ...
- 15 Puzzle (4乘4谜题) IDA*(DFS策略与曼哈顿距离启发) 的C语言实现
大家好!这是我的第一篇博客,由于之前没有撰写博客的经验,并且也是初入计算机和人工智能领域,可能有些表述或者理解不当,还请大家多多指教. 一.撰写目的 由于这个学期在上算法与数据结构课程的时候,其中一个 ...
- POJ3460 Booksort(IDA*)
POJ3460 Booksort 题意:给定一个长度为n的序列,每次可以取出其中的一段数,插入任意一个位置,问最少需要几次操作才能使整个序列变为1~n 思路:IDA*+迭代加深搜索 小技巧:将一段数插 ...
- CISCN 2019 writeup
划水做了两个pwn和两个逆向...... 二进制题目备份 Re easyGO Go语言,输入有Please字样,ida搜索sequence of bytes搜please的hex值找到字符串变量,交叉 ...
随机推荐
- C++中使用Curl和JsonCpp调用有道翻译API实现在线翻译
使用C++开发一个在线翻译工具,这个想法在我大脑中过了好几遍了,所以就搜了下资料,得知网络上有很多翻译API,这里我选择我平时使用较多的有道翻译API进行在线翻译工具开发的练习.翻译API返回的结果常 ...
- Mysql 数值类型
Mysql数值类型 整数型 小数型(浮点数) 日期时间型
- Linux服务器的安装
命令:1. mount /mnt/cdrom/回车 安装光驱2. cd /mnt/cdrom/ 进入光驱目录3. cd /mnt/cdrom/RedHat/RPMS/ 进入RPMS目录4. rpm - ...
- net4:MultiView(view)行为中的commmandname与commmandargument,ListBox的使用及移动操作
原文发布时间为:2008-07-29 -- 来源于本人的百度文章 [由搬家工具导入] using System;using System.Data;using System.Configuration ...
- 查看公网IP信息的方法
有时候我们想知道自己的外网ip,推荐几个好用的方法 windows 用百度搜索“ip”就会显示 用浏览器访问getip.name 或者 ifconfig.me linux 使用curl命令 curl ...
- [转]常用iOS图片处理方法
自:http://blog.sina.com.cn/s/blog_8988732e0100xcx1.html ========== (one) UIImage 图像 等比例缩放=========== ...
- LeetCode OJ——Longest Valid Parentheses
http://oj.leetcode.com/problems/longest-valid-parentheses/ 最大括号匹配长度,括号是可以嵌套的 #include <string> ...
- 让网站永久拥有HTTPS - 申请免费SSL证书并自动续期
https://blog.csdn.net/xs18952904/article/details/79262646 https://freessl.org/
- iOS内购总结
内购流程: 1. 用户先拿到购买产品的单子, 2. 拿着单子去苹果那里交钱,交完钱让苹果在单子上盖个章 3.拿着盖了章的单子传给自己的服务器来验证是否真的支付成功,服务器是跟苹果验证(我们客户端也是可 ...
- ping++微信渠道,第二次拉起不能进行支付返回订单号重复问题
项目中用到了支付功能,采用的是ping++实现的,上线运行一年多都很正常,但是最近突然出现有买家反映说不能进行支付的情况 通过了解和沟通之后发现发现是重复拉起失败,然后我们对问题进行了排查. 测试过程 ...
