jsencrypt加密
在登录时,前台页面的用户名、密码都是明文传输到后台的,漏洞扫描认为这样子不安全,就想到了前台js加密,后台解密的方法,要用到jsencrypt.js,具体代码如下:
前台页面:
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<title></title>
<script src="Scripts/jquery-1.4.1.min.js" type="text/javascript"></script>
<script src="Scripts/jsencrypt.min.js" type="text/javascript"></script>
<script type="text/javascript">
function subData() {
var encrypt = new JSEncrypt();
var publicKey = $("#pubkey").val();
encrypt.setPublicKey(publicKey); var userdata = {};
userdata.Username = encodeURI(encrypt.encrypt($("#tUsername").val()));
userdata.Password = encodeURI(encrypt.encrypt($("#tPassword").val())); $.post("Handler1.ashx", userdata, function (r) {
alert(r);
});
}
</script>
</head>
<body>
用户名:<input type="text" id="tUsername" /><br />
密码:<input type="password" id="tPassword" /><br />
<input type="button" onclick="subData()" value="登录" />
<textarea id="pubkey" rows="15" cols="65" style="display:none">
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDZpm0555ciZabX/1uVDI07cJUI
66mcK2yf5FDB+KOKUrFyWY/xYS8csRDSN1vDfNnmdN45vGr+IMrEeZVqri/tvEL6
3N1JEWlKkvXolLpA6DHc/OKjXR9oQ93MDpftswOSdD5tQxplEDDemBeY2/Qh3RTB
MGKsFuPoYKRxSQP7xwIDAQAB
</textarea>
</body>
</html>
后台处理程序:
using System;
using System.Collections.Generic;
using System.Web;
using System.Security.Cryptography;
using System.Text;
using System.IO; namespace WebApplication1
{
/// <summary>
/// Handler1 的摘要说明
/// </summary>
public class Handler1 : IHttpHandler
{
private const string privateKey = @"MIICXwIBAAKBgQDZpm0555ciZabX/1uVDI07cJUI66mcK2yf5FDB+KOKUrFyWY/x
YS8csRDSN1vDfNnmdN45vGr+IMrEeZVqri/tvEL63N1JEWlKkvXolLpA6DHc/OKj
XR9oQ93MDpftswOSdD5tQxplEDDemBeY2/Qh3RTBMGKsFuPoYKRxSQP7xwIDAQAB
AoGBAMAchXbB84YaAZ3QOQ8jyBm6MuJv2QMO1U+AoMPF6txyR0xuv35I0OPbasSS
tn2j21XuvCRsKmhrm262/uruG0B0jclwruCs/HejvyH9l6/taIMms8UepJqt860b
YbmKcECYKacjPe6+j2OyMCQiG1I+E0NbEe0kq2kbWSyqEuHJAkEA4tfWaC5o2caM
oedrn6u3QuWNvDqtzvJHYzGg3D6hQMSabbxXt0UOebnEegWPeGdR+0fmNCy7SQdO
vfkThb6rswJBAPWgGPp9eQeA8kIwj5pbtyyqsGUhkmM+/PnMe7V9S7O7A7l6NJvq
Sdg7RMEYtpm+B9F0aRlHxRh4/0Rw7GmFFZ0CQQCMl00RYMInRwFeTvnLCjgYxAEm
Sg/zFQHdnqKeHkr+w1sa7AJJWglwtAvrvIqBCzgqTxOD/r1Ms7S/1SGeYOA1AkEA
6ikcZwDjNuIZEjzVSiSRdgWrcF4W/oJ4DXSBoz21w7xQCqyUJueuSnQGUcfLnLnr
HiVKZI1lOrVvNcIpv1beiQJBAKEIKyZrqqdlM7PaHIyqdSMnjNrJ5ixTek6y5OCW
GZ+Tph2YwU3ffpyugfKRxE/FMFlK2x6Mxp7UOtAWkfXaHEE="; private const string publicKey = @"MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDZpm0555ciZabX/1uVDI07cJUI
66mcK2yf5FDB+KOKUrFyWY/xYS8csRDSN1vDfNnmdN45vGr+IMrEeZVqri/tvEL6
3N1JEWlKkvXolLpA6DHc/OKjXR9oQ93MDpftswOSdD5tQxplEDDemBeY2/Qh3RTB
MGKsFuPoYKRxSQP7xwIDAQAB"; public void ProcessRequest(HttpContext context)
{
context.Response.ContentType = "text/plain";
string Username = context.Request["Username"];
string Password = context.Request["Password"]; //解密
RSACryptoService rsa = new RSACryptoService(privateKey, publicKey); Username = rsa.Decrypt(Username);
Password = rsa.Decrypt(Password); context.Response.Write("ok");
} public bool IsReusable
{
get
{
return false;
}
}
} /// <summary>
/// RSA类
/// </summary>
public class RSACryptoService
{
private RSACryptoServiceProvider _privateKeyRsaProvider;
private RSACryptoServiceProvider _publicKeyRsaProvider; public RSACryptoService(string privateKey, string publicKey = null)
{
if (!string.IsNullOrEmpty(privateKey))
{
_privateKeyRsaProvider = CreateRsaProviderFromPrivateKey(privateKey);
} if (!string.IsNullOrEmpty(publicKey))
{
_publicKeyRsaProvider = CreateRsaProviderFromPublicKey(publicKey);
}
} public string Decrypt(string cipherText)
{
if (_privateKeyRsaProvider == null)
{
throw new Exception("_privateKeyRsaProvider is null");
}
return Encoding.UTF8.GetString(_privateKeyRsaProvider.Decrypt(System.Convert.FromBase64String(cipherText), false));
} public string Encrypt(string text)
{
if (_publicKeyRsaProvider == null)
{
throw new Exception("_publicKeyRsaProvider is null");
}
return Convert.ToBase64String(_publicKeyRsaProvider.Encrypt(Encoding.UTF8.GetBytes(text), false));
} private RSACryptoServiceProvider CreateRsaProviderFromPrivateKey(string privateKey)
{
var privateKeyBits = System.Convert.FromBase64String(privateKey); var RSA = new RSACryptoServiceProvider();
var RSAparams = new RSAParameters(); using (BinaryReader binr = new BinaryReader(new MemoryStream(privateKeyBits)))
{
byte bt = ;
ushort twobytes = ;
twobytes = binr.ReadUInt16();
if (twobytes == 0x8130)
binr.ReadByte();
else if (twobytes == 0x8230)
binr.ReadInt16();
else
throw new Exception("Unexpected value read binr.ReadUInt16()"); twobytes = binr.ReadUInt16();
if (twobytes != 0x0102)
throw new Exception("Unexpected version"); bt = binr.ReadByte();
if (bt != 0x00)
throw new Exception("Unexpected value read binr.ReadByte()"); RSAparams.Modulus = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.Exponent = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.D = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.P = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.Q = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.DP = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.DQ = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.InverseQ = binr.ReadBytes(GetIntegerSize(binr));
} RSA.ImportParameters(RSAparams);
return RSA;
} private int GetIntegerSize(BinaryReader binr)
{
byte bt = ;
byte lowbyte = 0x00;
byte highbyte = 0x00;
int count = ;
bt = binr.ReadByte();
if (bt != 0x02)
return ;
bt = binr.ReadByte(); if (bt == 0x81)
count = binr.ReadByte();
else
if (bt == 0x82)
{
highbyte = binr.ReadByte();
lowbyte = binr.ReadByte();
byte[] modint = { lowbyte, highbyte, 0x00, 0x00 };
count = BitConverter.ToInt32(modint, );
}
else
{
count = bt;
} while (binr.ReadByte() == 0x00)
{
count -= ;
}
binr.BaseStream.Seek(-, SeekOrigin.Current);
return count;
} private RSACryptoServiceProvider CreateRsaProviderFromPublicKey(string publicKeyString)
{
// encoded OID sequence for PKCS #1 rsaEncryption szOID_RSA_RSA = "1.2.840.113549.1.1.1"
byte[] SeqOID = { 0x30, 0x0D, 0x06, 0x09, 0x2A, 0x86, 0x48, 0x86, 0xF7, 0x0D, 0x01, 0x01, 0x01, 0x05, 0x00 };
byte[] x509key;
byte[] seq = new byte[];
int x509size; x509key = Convert.FromBase64String(publicKeyString);
x509size = x509key.Length; // --------- Set up stream to read the asn.1 encoded SubjectPublicKeyInfo blob ------
using (MemoryStream mem = new MemoryStream(x509key))
{
using (BinaryReader binr = new BinaryReader(mem)) //wrap Memory Stream with BinaryReader for easy reading
{
byte bt = ;
ushort twobytes = ; twobytes = binr.ReadUInt16();
if (twobytes == 0x8130) //data read as little endian order (actual data order for Sequence is 30 81)
binr.ReadByte(); //advance 1 byte
else if (twobytes == 0x8230)
binr.ReadInt16(); //advance 2 bytes
else
return null; seq = binr.ReadBytes(); //read the Sequence OID
if (!CompareBytearrays(seq, SeqOID)) //make sure Sequence for OID is correct
return null; twobytes = binr.ReadUInt16();
if (twobytes == 0x8103) //data read as little endian order (actual data order for Bit String is 03 81)
binr.ReadByte(); //advance 1 byte
else if (twobytes == 0x8203)
binr.ReadInt16(); //advance 2 bytes
else
return null; bt = binr.ReadByte();
if (bt != 0x00) //expect null byte next
return null; twobytes = binr.ReadUInt16();
if (twobytes == 0x8130) //data read as little endian order (actual data order for Sequence is 30 81)
binr.ReadByte(); //advance 1 byte
else if (twobytes == 0x8230)
binr.ReadInt16(); //advance 2 bytes
else
return null; twobytes = binr.ReadUInt16();
byte lowbyte = 0x00;
byte highbyte = 0x00; if (twobytes == 0x8102) //data read as little endian order (actual data order for Integer is 02 81)
lowbyte = binr.ReadByte(); // read next bytes which is bytes in modulus
else if (twobytes == 0x8202)
{
highbyte = binr.ReadByte(); //advance 2 bytes
lowbyte = binr.ReadByte();
}
else
return null;
byte[] modint = { lowbyte, highbyte, 0x00, 0x00 }; //reverse byte order since asn.1 key uses big endian order
int modsize = BitConverter.ToInt32(modint, ); int firstbyte = binr.PeekChar();
if (firstbyte == 0x00)
{ //if first byte (highest order) of modulus is zero, don't include it
binr.ReadByte(); //skip this null byte
modsize -= ; //reduce modulus buffer size by 1
} byte[] modulus = binr.ReadBytes(modsize); //read the modulus bytes if (binr.ReadByte() != 0x02) //expect an Integer for the exponent data
return null;
int expbytes = (int)binr.ReadByte(); // should only need one byte for actual exponent data (for all useful values)
byte[] exponent = binr.ReadBytes(expbytes); // ------- create RSACryptoServiceProvider instance and initialize with public key -----
RSACryptoServiceProvider RSA = new RSACryptoServiceProvider();
RSAParameters RSAKeyInfo = new RSAParameters();
RSAKeyInfo.Modulus = modulus;
RSAKeyInfo.Exponent = exponent;
RSA.ImportParameters(RSAKeyInfo); return RSA;
} }
} private bool CompareBytearrays(byte[] a, byte[] b)
{
if (a.Length != b.Length)
return false;
int i = ;
foreach (byte c in a)
{
if (c != b[i])
return false;
i++;
}
return true;
}
}
}
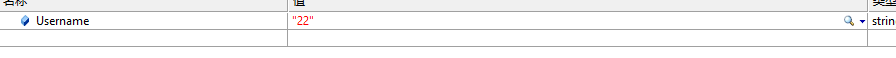
效果如下:
加密后的数据:
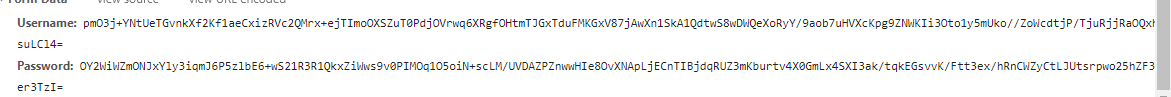
后台解密:

jsencrypt加密的更多相关文章
- vue使用JSEncrypt实现rsa加密及挂载方法
挂载全局方法 使用jsencrypt进行rsa加密 原文链接:Js参数RSA加密传输,jsencrypt.js的使用 - CSDN博客* https://blog.csdn.net/p31201115 ...
- PHP的学习--RSA加密解密
PHP服务端与客户端交互或者提供开放API时,通常需要对敏感的数据进行加密,这时候rsa非对称加密就能派上用处了. 举个通俗易懂的例子,假设我们再登录一个网站,发送账号和密码,请求被拦截了. 密码没加 ...
- 我用Django搭网站(3)-表单RSA加密
之前开发项目时因为种种原因一直使用明文提交,表单直接明文提交非常不安全,只要稍加操作就能轻易获取用户的信息.在众里寻他千百度之后决定使用RSA加密方式,简单可靠. 项目准备 一.安装PyCrypto库 ...
- 关于RSA汇总
写在前面 安全测试需要, 后台数据需要签名, 前台验签, 于是有了这篇hao123. 正文 jsrsasign https://github.com/kjur/jsrsasign jsrsasign使 ...
- jsencrypt参数前端加密c#解密
写程序时一般是通过form表单或者ajax方式将参数提交到服务器进行验证,如何防止提交的请求不被抓包后串改,虽然无法说绝对安全却给非法提交提高了难度,本篇采用jsencypt在前端进行加密的并且用C# ...
- rsa加密算法及js的JSEncrypt实现前端加密
最近的项目中用到了rsa加密算法,在实现了相关功能之后,我去了解了一下rsa相关原理,于是就写了这篇博客啦. 首先介绍一下什么是rsa加密算法: 作为非对称加密算法的老大,rsa号称是地球上最安全的加 ...
- 使用jsencrypt(rsa加密方式)给js加密防被刷
加密步骤 1.需要加密的参数 * * ).toISOString().replace(/T/g, }Z/, ''); //使用本地时间,然后转换格式 2.js中引用jsencrypt.js文件,然后实 ...
- js加密php解密---jsencrypt
原理:javascript加密PHP解密: 完全依赖openssl: 一. openssl 是干嘛的 它集成了众多密码算法及实用工具 rsa加密流程:(今天只讲众多加密方式中的一种) 1. 在当前文件 ...
- javascript加密PHP解密---jsencrypt
今天偶然发现jsencrypt这玩意,之前做"直播室聊天"时 数据传输明文问题没解决; 一直苦苦寻找技术解决方案今天勉强找了个: 原理:javascript加密PHP解密: 完全依 ...
随机推荐
- linux中使用Crontab定时执行java的jar包无法使用环境变量的问题
1.crontab简单使用 cmd 其实就是5个星星的事情,随便百度一下吧 5个时间标签用来标注执行的设定.比如每5分钟执行一次/5 * * * cmd 要特别注意 2.有些命令在命令行里执行很好,到 ...
- ASP.NET MVC应用程序播放AVI视频
前面Insus.NET实现一系列在MVC应用程序播放SWF, FLV, WMV, RM, RMVB视频.每篇使用不同的方法方式,大同小异.这篇中,为了MVC应用程序播放AVI视频,用纯M, V, C来 ...
- Mysql系统知识梳理
1 数据库分类 MySQL Oracle redis 2 MySQL 存储引擎有哪些 ENGINE=InnoDB 提供事务安全表,支持外键. MyISAM Memory数据存入内存中,如果内存出现异常 ...
- Mysql添加字段.md
alter table td_user add gender bit DEFAULT 0 COMMENT '性别';
- Android-View的绘制源码学习总结
##前言 算是第一篇正式的github博文,回顾了一下之前看过的view源码解析,做一个对目前为止View学习小的总结. 我觉得对于源码的解析和学习,把所有流程记下来意义并不是很大,最关键的是: 1. ...
- BZOJ4806(SummerTrainingDay03-K dp)
炮 Time Limit: 10 Sec Memory Limit: 128 MBSubmit: 464 Solved: 243[Submit][Status][Discuss] Descript ...
- layui 三级菜单
<!DOCTYPE html> <html> <head> <meta charset="utf-8"> <meta name ...
- (三)MongoDB数据库注意
1.数据库名 数据库也通过名字来标识.数据库名可以是满足以下条件的任意UTF-8字符串. 不能是空字符串(""). 不得含有' '(空格)...$./.\和\0 (空字符). 应全 ...
- 【代码笔记】iOS-NSFileManager
一,代码. #import "ViewController.h" @interface ViewController () @end @implementation ViewCon ...
- html基础标签下
1.1 单标签 ◆注释标签 ctrl+/ ◆水平线标签 <hr> ◆换行标签 <br> 1.2 双标签 ◆段落标签 <p></p> ◆ ...
