HTTPS双向认证+USB硬件加密锁(加密狗)配置
环境: Ubuntu14.04,apache2.4.7, openssl1.0.1f
安装apache2
apt-get install apache2 -y
一般openssl默认已经安装
开启apache的ssl模块和ssl站点
a2enmod ssl
a2ensite default-ssl.conf
创建证书目录
mkdir /etc/apache2/certs
进入目录创建证书和秘钥
cd /etc/apache2/certs
/usr/lib/ssl/misc/CA.sh -newca
root@bogon:/etc/apache2/certs# /usr/lib/ssl/misc/CA.sh -newca
CA certificate filename (or enter to create)
Making CA certificate ...
Generating a 2048 bit RSA private key
.............................................................................................+++
..+++
writing new private key to './demoCA/private/./cakey.pem'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or aDN.
There are quite a few fields but you can leave some blank
For some fields there will be a defaultvalue,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:Beijing
Locality Name (eg, city) []:Beijing
OrganizationName (eg, company) [Internet Widgits Pty Ltd]:PWRD
Organizational Unit Name (eg, section) []:OPS
Common Name (e.g. server FQDN or YOUR name) []:10.1.1.128
Email Address []:jailman@sina.com
Please enter the following 'extra' attributes
to be sent with your certificate request
Achallenge password []:111111
An optional company name []:pwrd
Using configuration from /usr/lib/ssl/openssl.cnf
Enter pass phrase for ./demoCA/private/./cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 14695213526817228816 (0xcbefe2d81474c810)
Validity
Not Before: Jan 5 05:30:34 2017 GMT
Not After : Jan 5 05:30:34 2020 GMT
Subject:
countryName = CN
stateOrProvinceName = Beijing
organizationName = PWRD
organizationalUnitName = OPS
commonName = 10.1.1.128
emailAddress = jailman@sina.com
X509v3 extensions:
X509v3 Subject Key Identifier:
50:CA:37:3C:45:11:0E:E1:BA:E7:80:74:66:D0:98:B9:21:8E:13:BD
X509v3 Authority KeyIdentifier:
keyid:50:CA:37:3C:45:11:0E:E1:BA:E7:80:74:66:D0:98:B9:21:8E:13:BD
X509v3 Basic Constraints:
CA:TRUE
Certificate is to be certified until Jan 5 05:30:34 2020 GMT (1095 days)
Write out database with 1 new entries
Data Base Updated
tree命令查看一下
root@bogon:/etc/apache2/certs# tree
.
└── demoCA
├── cacert.pem
├── careq.pem
├── certs
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.old
├── newcerts
│ └── CBEFE2D81474C810.pem
├── private
│ └── cakey.pem
└── serial
5directories, 8 files
生成服务器证书(密码全部设置为111111)
a) 生成私钥: openssl genrsa -des3 -out server.key2048
b) 生成csr文件: openssl req -new -keyserver.key -out server.csr
c) 生成证书&签名: openssl ca -in server.csr-out server.crt
#遇到下列不成功时修改vim demoCA/index.txt.attr中unique_subject =no
failed to update database
TXT_DB error number 2
上述执行结果
root@bogon:/etc/apache2/certs# openssl genrsa -des3 -out server.key 2048
Generating RSA private key, 2048 bit long modulus
........................................+++
............................+++
eis 65537 (0x10001)
Enter pass phrase for server.key:
Verifying - Enter pass phrase for server.key:
root@bogon:/etc/apache2/certs# openssl req -new -key server.key -outserver.csr
Enter pass phrase for server.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or aDN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:Beijing
Locality Name (eg, city) []:Beijing
Organization Name (eg, company) [Internet Widgits Pty Ltd]:PWRD
Organizational Unit Name (eg, section) []:OPS
Common Name (e.g. server FQDN or YOUR name) []:10.1.1.128
Email Address []:jailman@sina.com
Please enter the following 'extra' attributes
to be sent with your certificate request
Achallenge password []:111111
An optional company name []:pwrd
root@bogon:/etc/apache2/certs# openssl ca -in server.csr -out server.crt
Using configuration from /usr/lib/ssl/openssl.cnf
Enter pass phrase for ./demoCA/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 14695213526817228817 (0xcbefe2d81474c811)
Validity
Not Before: Jan 5 05:39:32 2017 GMT
Not After : Jan 5 05:39:32 2018 GMT
Subject:
countryName = CN
stateOrProvinceName = Beijing
organizationName = PWRD
organizationalUnitName = OPS
commonName = 10.1.1.128
emailAddress = jailman@sina.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL GeneratedCertificate
X509v3 Subject Key Identifier:
FB:32:4F:A6:6D:01:D3:00:98:00:BF:0A:2E:E5:E6:90:CC:E0:E4:8B
X509v3 Authority KeyIdentifier:
keyid:50:CA:37:3C:45:11:0E:E1:BA:E7:80:74:66:D0:98:B9:21:8E:13:BD
Certificate is to be certified until Jan 5 05:39:32 2018 GMT (365 days)
Sign the certificate? [y/n]:y
1out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
生成客户端证书(密码全部设置为111111)
a) 生成私钥: openssl genrsa -des3 -out client.key2048
b) 生成csr文件: openssl req -new -keyclient.key -out client.csr
c) 生成证书&签名: openssl ca -in client.csr-out client.crt
上述命令执行结果:
root@bogon:/etc/apache2/certs# openssl genrsa -des3 -out client.key 2048
Generating RSA private key, 2048 bit long modulus
...........................................................................................+++
............................+++
eis 65537 (0x10001)
Enter pass phrase for client.key:
Verifying - Enter pass phrase for client.key:
root@bogon:/etc/apache2/certs# openssl req -new -key client.key -outclient.csr
Enter pass phrase for client.key:
You are about to be asked to enter information that will be incorporated
intoyour certificate request.
What you are about to enter is what is called a Distinguished Name or aDN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:Beijing
Locality Name (eg, city) []:Beijing
Organization Name (eg, company) [Internet Widgits Pty Ltd]:PWRD
Organizational Unit Name (eg, section) []:OPS
Common Name (e.g. server FQDN or YOUR name) []:10.1.1.128
Email Address []:jailman@sina.com
Please enter the following 'extra' attributes
to be sent with your certificate request
Achallenge password []:111111
An optional company name []:pwrd
root@bogon:/etc/apache2/certs# openssl ca -in client.csr -out client.crt
Using configuration from /usr/lib/ssl/openssl.cnf
Enter pass phrase for ./demoCA/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 14695213526817228818 (0xcbefe2d81474c812)
Validity
Not Before: Jan 5 05:43:35 2017 GMT
Not After : Jan 5 05:43:35 2018 GMT
Subject:
countryName = CN
stateOrProvinceName = Beijing
organizationName = PWRD
organizationalUnitName = OPS
commonName = 10.1.1.128
emailAddress = jailman@sina.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL GeneratedCertificate
X509v3 Subject Key Identifier:
78:4C:B0:9E:BA:EE:BD:E2:88:55:F4:06:B4:57:5E:74:71:E0:1B:2D
X509v3 Authority KeyIdentifier:
keyid:50:CA:37:3C:45:11:0E:E1:BA:E7:80:74:66:D0:98:B9:21:8E:13:BD
Certificate is to be certified until Jan 5 05:43:35 2018 GMT (365 days)
Sign the certificate? [y/n]:y
1out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
查看上述两步生成的证书和秘钥
root@bogon:/etc/apache2/certs# ls
client.crt client.key server.crt server.key
client.csr demoCA server.csr
*生成浏览器支持的.pfx(.p12)证书
a) openssl pkcs12 -export -clcerts -in client.crt -inkey client.key -outclient.p12
执行结果
root@bogon:/etc/apache2/certs# openssl pkcs12 -export -clcerts -inclient.crt -inkey client.key -out client.p12
Enterpass phrase for client.key:
EnterExport Password:
Verifying- Enter Export Password:
生成不带密码验证的client/server.key.unsecure
如果你想要把数字证书用于Nginx、Apache等Web服务器,你会发现启动nginx服务器时会要求你输入数字证书密码,
这是因为在设置私钥key时将密码写入了key文件,导致Nginx/Apache等系列服务器在启动时要求Enter PEM pass phrase。
我们需要做的是剥离这个密码,利用如下OpenSSL命令生成server.key.unsecure文件
openssl rsa -in server.key -outserver.key.unsecure
最终的结果:
root@bogon:/etc/apache2/certs# tree
.
├──client.crt
├──client.csr
├──client.key
├──client.p12
├──demoCA
│??├── cacert.pem
│??├── careq.pem
│??├── certs
│??├── crl
│??├── index.txt
│??├── index.txt.attr
│??├── index.txt.attr.old
│??├── index.txt.old
│??├── newcerts
│??│?? ├── CBEFE2D81474C810.pem
│??│?? ├── CBEFE2D81474C811.pem
│??│?? └── CBEFE2D81474C812.pem
│??├── private
│??│?? └── cakey.pem
│??├── serial
│??└── serial.old
├──server.crt
├──server.csr
└──server.key
5directories, 19 files
配置apache2 https
vim/etc/apache2/sites-enabled/default-ssl.conf
<IfModule mod_ssl.c>
<VirtualHost_default_:443>
ServerAdminwebmaster@localhost
DocumentRoot/var/www/html
ErrorLog${APACHE_LOG_DIR}/error.log
CustomLog${APACHE_LOG_DIR}/access.log combined
SSLEngineon
SSLCertificateFile /etc/apache2/certs/server.crt
SSLCertificateKeyFile/etc/apache2/certs/server.key
SSLCACertificateFile/etc/apache2/certs/demoCA/cacert.pem
SSLVerifyClientrequire
SSLVerifyDepth 10
<FilesMatch"\.(cgi|shtml|phtml|php)$">
SSLOptions+StdEnvVars
</FilesMatch>
<Directory/usr/lib/cgi-bin>
SSLOptions+StdEnvVars
</Directory>
BrowserMatch"MSIE [2-6]" \
nokeepalivessl-unclean-shutdown \
downgrade-1.0force-response-1.0
BrowserMatch"MSIE [17-9]" ssl-unclean-shutdown
</VirtualHost>
</IfModule>
serviceapache2 restart
root@bogon:/etc/apache2/sites-enabled#service apache2 restart
*Restarting web server apache2 Apache needs to decrypt your SSL Keys for bogon.localdomain:443 (RSA)
Pleaseenter passphrase:
输入密码启动
证书导出到本地准备写入加密锁
root@bogon:/etc/apache2/certs# szclient.p12
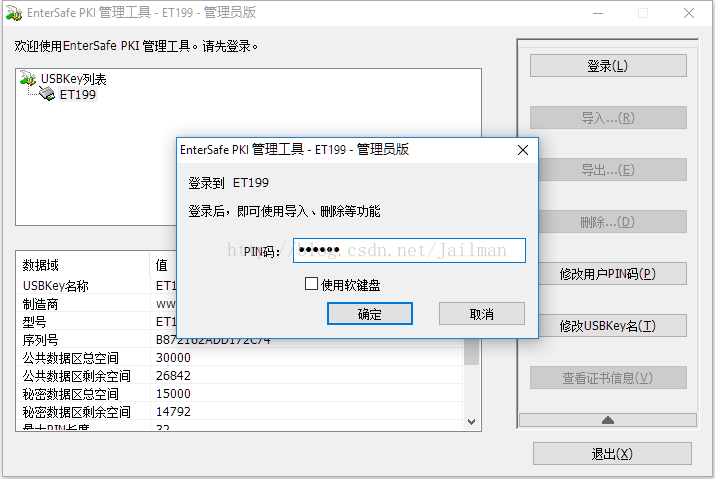
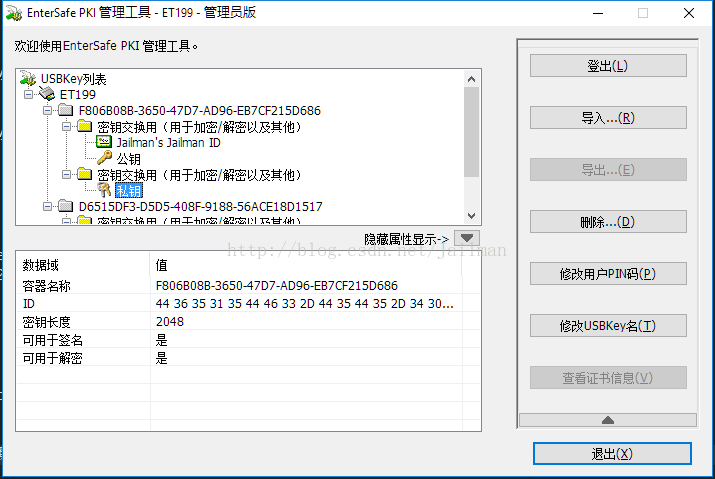
打开USB锁管理软件
输入PIN登录
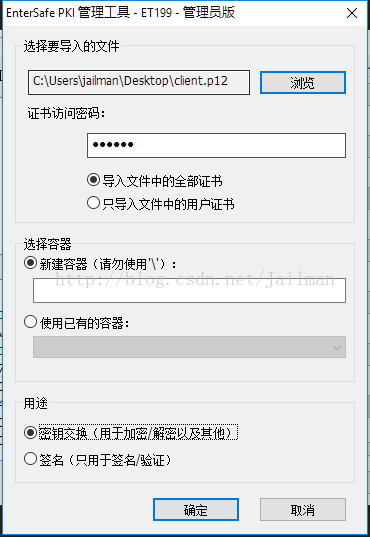
这里实际上我们已经提前将加密锁初始化为了PKI锁
点击导入,选择证书,输入证书密码,其他默认
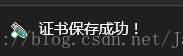
Win10提示导入成功
导入后的效果
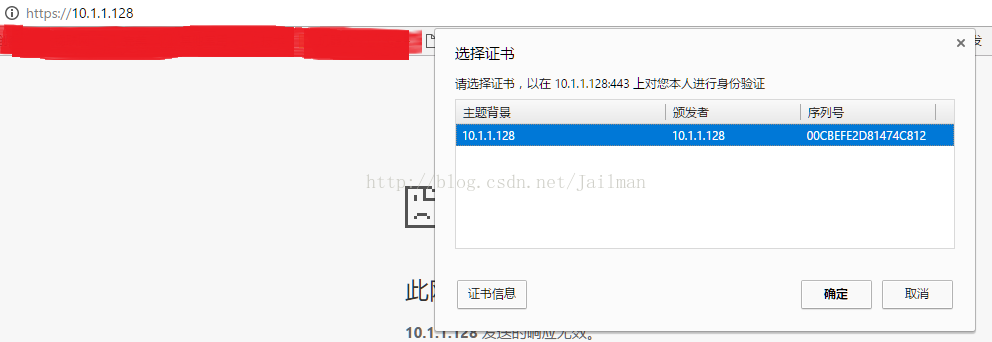
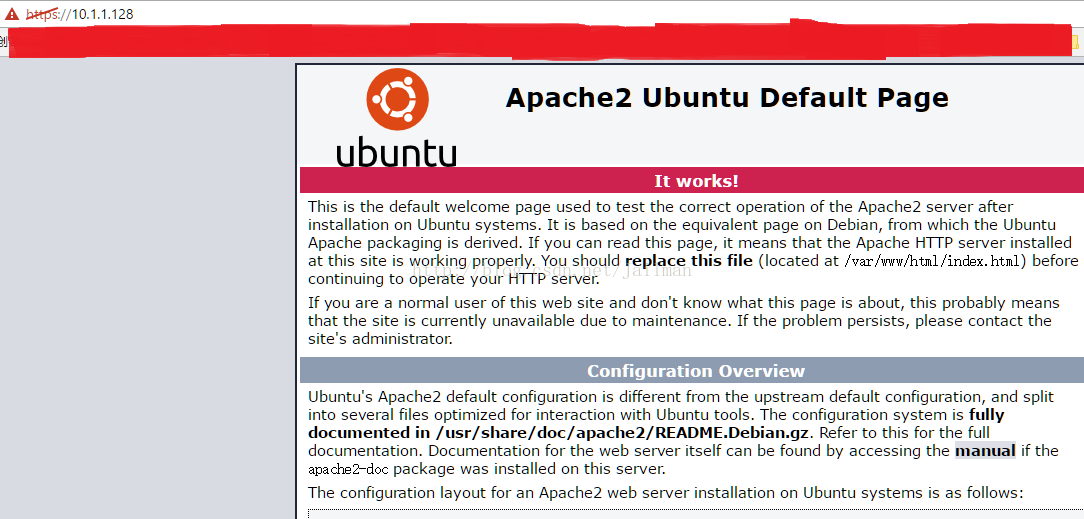
USB加密锁保持插入,访问测试站点https://10.1.1.128,有证书提示
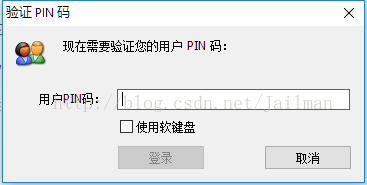
点击确定输入PIN码
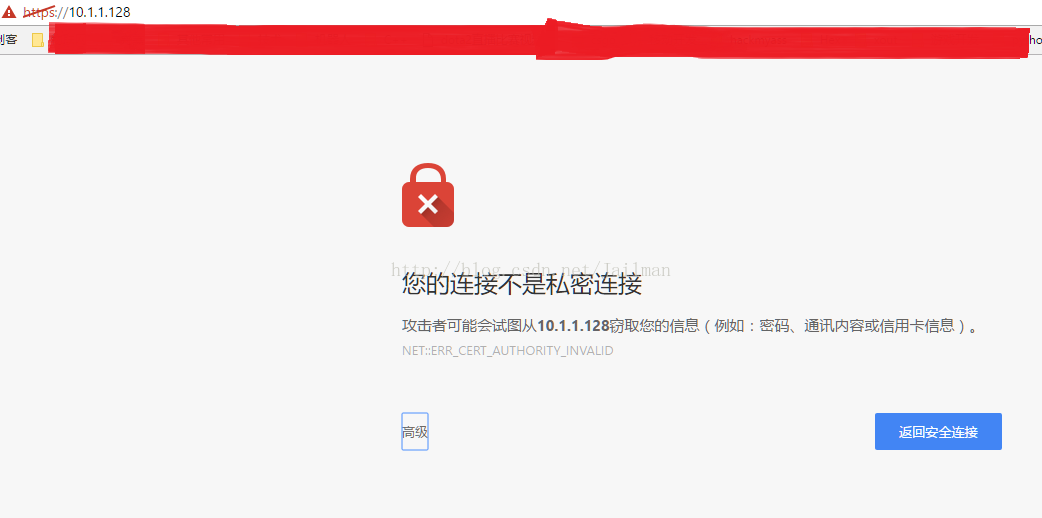
忽略安全提示
成功访问
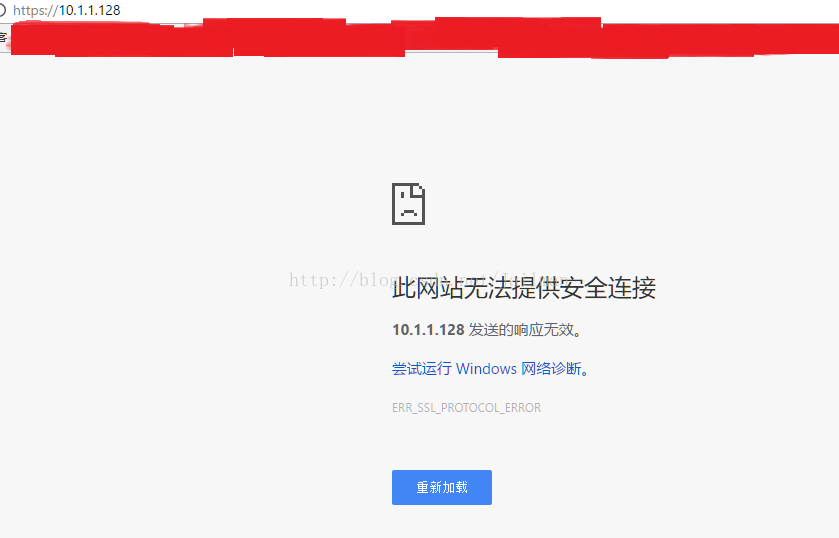
不插key的情况下访问结果
我使用的是ET199加密锁,加上运费一共花了29元
HTTPS双向认证+USB硬件加密锁(加密狗)配置的更多相关文章
- httpd设置HTTPS双向认证
去年用tomcat.jboss配置过HTTPS双向认证,那时候主要用的是JDK自带的keytool工具.这次是用httpd + openssl,区别比较大 在网上搜索了很多文章,发现全面介绍的不多,或 ...
- Android Https双向认证 + GRPC
keywords:android https 双向认证android GRPC https 双向认证 ManagedChannel channel = OkHttpChannelBuilder.for ...
- https双向认证訪问管理后台,採用USBKEY进行系统訪问的身份鉴别,KEY的证书长度大于128位,使用USBKEY登录
近期项目需求,须要实现用USBKEY识别用户登录,採用https双向认证訪问管理后台管理界面,期间碰到过一些小问题,写出来给大家參考下. 1:前期准备工作 USBKEY 硬件:我买的是飞天诚信 epa ...
- Keytool配置 Tomcat的HTTPS双向认证
Keytool配置 Tomcat的HTTPS双向认证 证书生成 keytool 简介 Keytool是一个Java数据证书的管理工具, Keytool将密钥(key)和证书(certificates) ...
- HTTPS 双向认证构建移动设备安全体系
HTTPS 双向认证构建移动设备安全体系 对于一些高安全性要求的企业内项目,我们有时希望能够对客户端进行验证.这个时候我们可以使用Https的双向认证机制来实现这个功能. 单向认证:保证server是 ...
- Tomcat 配置 HTTPS双向认证
Tomcat 配置 HTTPS 双向认证指引说明: � 本文档仅提供 Linux 操作系统下的指引 � 在阅读本指引前请您在 Linux 部署 JDK 和 Tomcatserver为了 Tomcat ...
- Https双向认证Android客户端配置
Https .cer证书转换为BKS证书 公式https://blog.csdn.net/zww986736788/article/details/81708967 keytool -importce ...
- 双向认证 HTTPS双向认证
[微信支付]微信小程序支付开发者文档 https://pay.weixin.qq.com/wiki/doc/api/wxa/wxa_api.php?chapter=4_3 HTTPS双向认证使用说明 ...
- nodejs之https双向认证
说在前面 之前我们总结了https的相关知识,如果不懂可以看我另一篇文章:白话理解https 有关证书生成可以参考:自签证书生成 正题 今天使用nodejs来实现https双向认证 话不多说,直接进入 ...
随机推荐
- HDU - 4436sam裸题
题意:给你多个数字串,求本质不同的子串和(去掉前导零) 题解:建广义sam,刚开始一直想的是用l来计算,发现前导零对l的影响根本消不掉,所以不会做= =,原来应该是直接用一个新的数组表示到当前有多少个 ...
- Spring Boot常用注解
SpringBoot注解大全 一.注解(annotations)列表 @SpringBootApplication:包含了@ComponentScan.@Configuration和@Enable ...
- PAT 1031 Hello World for U
1031 Hello World for U (20 分) Given any string of N (≥) characters, you are asked to form the char ...
- WebView中JS调用Android Method 遇到的坑整理
WebView是android中常用的一个组件,其作用是展示网页,并让网页和android app进行一些业务逻辑上的交互. 其坑无数,相信用过的都知道,一个一个来解决吧. 1.怎么互调: <! ...
- Oracle Log Block Size
Although the size of redo entries is measured in bytes, LGWR writes the redo to the log files on dis ...
- ActiveMQ queue和topic,持久订阅和非持久订阅
消息的 destination 分为 queue 和 topic,而消费者称为 subscriber(订阅者).queue 中的消息只会发送给一个订阅者,而 topic 的消息,会发送给每一个订阅者. ...
- vmware自定义网段
vmware会自动随机给分配192.168下的一个C段作为虚拟网卡(如VMnet8)的网段. 有时我们可能不想使用随机分配的网段而想使用指定网段 注意:配置成新网段后VMware会认为所有IP都没分配 ...
- Talend 从Excel导入Saleforce数据(二) TMAP是精髓
TMap LookUp 经过测试的结果: ------------------------------------------ LookUp最好从CSV读数据,这样是最快了(20万记录1s).从Sal ...
- Sql server中 如何用sql语句创建视图
1.视图的作用 视图的作用: 第一点:使用视图,可以定制用户数据,聚焦特定的数据. 解释: 在实际过程中,公司有不同角色的工作人员,我们以销售公司为例的话, 采购人员,可以需要一些与其有关的数据,而与 ...
- TCP/IP报文 三次握手 四次挥手
1.TCP报文格式 TCP/IP协议的详细信息参看<TCP/IP协议详解>三卷本.下面是TCP报文格式图:图1 TCP报文格式 上图中有几个字段需要重点介绍下: (1)序号:Seq序 ...