Hashcat使用指南
Hashcat使用指南
免责声明:
本文章仅供学习和研究使用,严禁使用该文章内容对互联网其他应用进行非法操作,若将其用于非法目的,所造成的后果由您自行承担,产生的一切风险与本文作者无关,如继续阅读该文章即表明您默认遵守该内容。
0×01 Hashcat破解linux shadow的密码-首先了解shadow文件到底是什么?
登录Linux会要求输入用户名和密码。通常本地文件中会存储一份用户密码,并与用户输入对比,如果相同就允许用户登录。起初用户密码存储与/etc/passwd中,但由于/etc/passwd必须供所有用户读取,因此为了避免密码破译,unix系统将加密后的密码存储于/etc/shadow中,仅供超级用户可读。
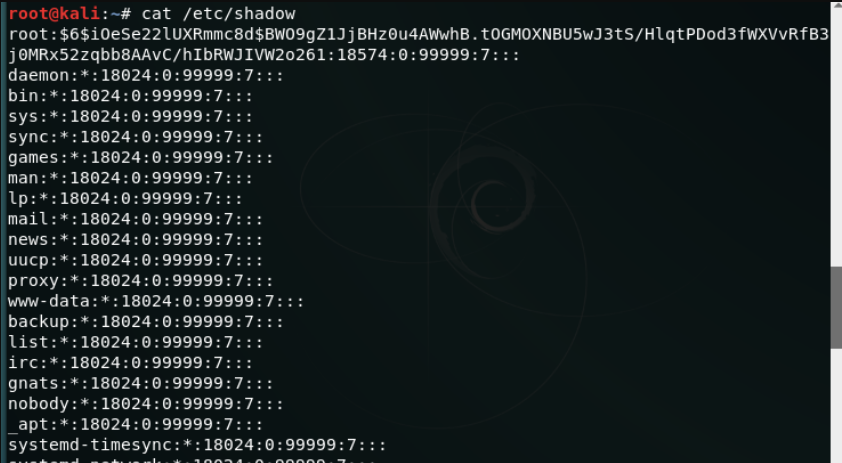
/etc/shadow中密码格式:
$id$salt$encrypted
id表示hash算法。起初密码用DES算法加密,单随着DES加密破解难度的降低,已用其他加密算法替代DES。在shadow文件中,密码字段如果以“$”打头,则表示非DES加密。
如:$1$2eWq10AC$NaQqalCk3
即表示非DES加密密码,而1表示使用了基于MD5的加密算法。
$2a$04$NZJWn7W2skvQRC5lW3H7q.ZTE8bz4xbC 2a表示Blowfish算法。
常见的标识与算法:
| ID | 算法 |
|---|---|
| 1 | MD5 |
| 2a | Blowfish |
| 5 | SHA-256 |
| 6 | SHA-512 |
0×02 hashcat的使用
hashcat是世界上最快和最先进的密码恢复实用程序,支持超过 300 种高度优化的哈希算法的五种独特的攻击模式。hashcat 目前支持 Linux、Windows 和 macOS 上的 CPU、GPU 和其他硬件加速器,并具有帮助实现分布式密码破解的工具。
使用Hashcat破解(hash值比对,查表)linux登录密码时,并不需要一条完整的/etc/shadow记录,只需要留下加密类型,Salt值,hash值就可以了,写成一行保存到文件中即可。
linux /etc/shadow中hash算法包括缺省的DES经典算法、MD5哈希算法($1)、Blowfish加密算法($2或$2a)和SHA哈希算法($5或$6)。因此利用hashcat进行破解的参数也不同,比如MD5哈希算法($1),使用hashcat -m 500参数;SHA哈希算法($5或$6),使用hashcat -m 1800 参数。
使用方法如下
hashcat -m 1800 -a 0 -o success.txt check.hash password.txt
-m参数是告诉hashcat解密的Hash类型,1800则是指SHA-512(Unix)类型密码;
-a参数是指定攻击模式,0代表Straight模式,使用字典进行破解尝试;
-o参数是指输出结果文件,输出到found.txt文件中;
check.hash放入shadow文件的hash值
password.txt放入密码
success.txt成功破解到的放入这个文件
创建一个用户,密码为123456
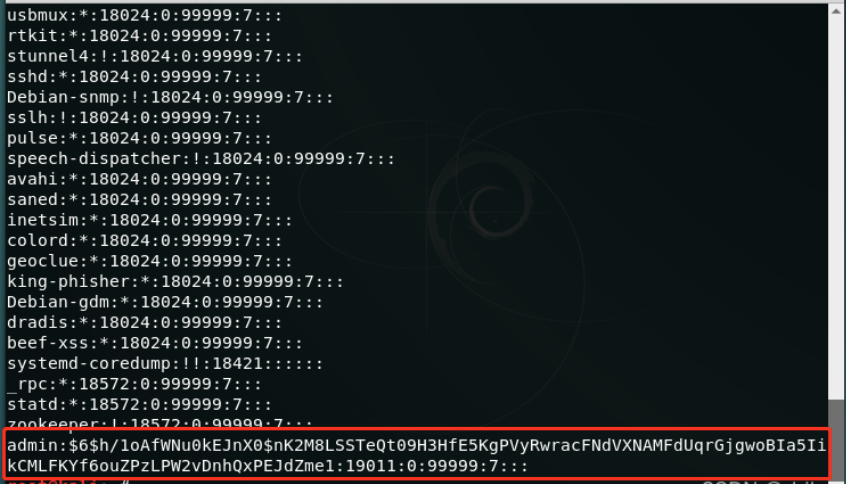
开始破解
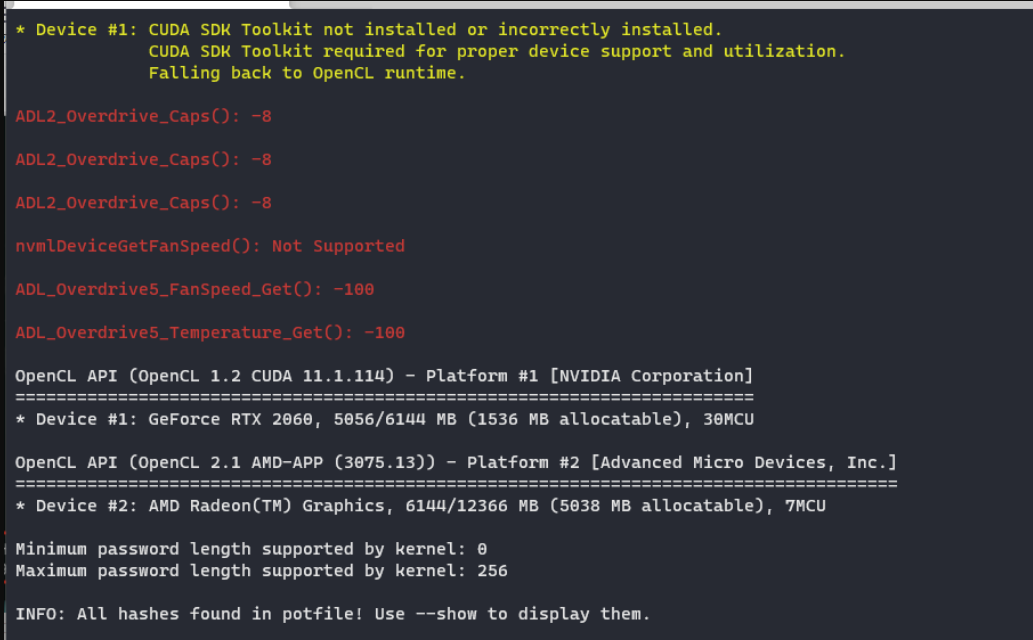
成功破解
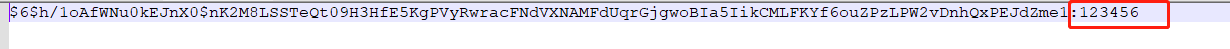
如果报错hipFuncGetAttribute is missing from HIP shared library.可以尝试使用--show命令或者--force命令
参数补充:
-m 参数
# | Name | Category
======+=====================================================+======================================
900 | MD4 | Raw Hash
0 | MD5 | Raw Hash
100 | SHA1 | Raw Hash
1300 | SHA2-224 | Raw Hash
1400 | SHA2-256 | Raw Hash
10800 | SHA2-384 | Raw Hash
1700 | SHA2-512 | Raw Hash
17300 | SHA3-224 | Raw Hash
17400 | SHA3-256 | Raw Hash
17500 | SHA3-384 | Raw Hash
17600 | SHA3-512 | Raw Hash
6000 | RIPEMD-160 | Raw Hash
600 | BLAKE2b-512 | Raw Hash
11700 | GOST R 34.11-2012 (Streebog) 256-bit, big-endian | Raw Hash
11800 | GOST R 34.11-2012 (Streebog) 512-bit, big-endian | Raw Hash
6900 | GOST R 34.11-94 | Raw Hash
17010 | GPG (AES-128/AES-256 (SHA-1($pass))) | Raw Hash
5100 | Half MD5 | Raw Hash
17700 | Keccak-224 | Raw Hash
17800 | Keccak-256 | Raw Hash
17900 | Keccak-384 | Raw Hash
18000 | Keccak-512 | Raw Hash
6100 | Whirlpool | Raw Hash
10100 | SipHash | Raw Hash
70 | md5(utf16le($pass)) | Raw Hash
170 | sha1(utf16le($pass)) | Raw Hash
1470 | sha256(utf16le($pass)) | Raw Hash
10870 | sha384(utf16le($pass)) | Raw Hash
1770 | sha512(utf16le($pass)) | Raw Hash
10 | md5($pass.$salt) | Raw Hash salted and/or iterated
20 | md5($salt.$pass) | Raw Hash salted and/or iterated
3800 | md5($salt.$pass.$salt) | Raw Hash salted and/or iterated
3710 | md5($salt.md5($pass)) | Raw Hash salted and/or iterated
4110 | md5($salt.md5($pass.$salt)) | Raw Hash salted and/or iterated
4010 | md5($salt.md5($salt.$pass)) | Raw Hash salted and/or iterated
21300 | md5($salt.sha1($salt.$pass)) | Raw Hash salted and/or iterated
40 | md5($salt.utf16le($pass)) | Raw Hash salted and/or iterated
2600 | md5(md5($pass)) | Raw Hash salted and/or iterated
3910 | md5(md5($pass).md5($salt)) | Raw Hash salted and/or iterated
3500 | md5(md5(md5($pass))) | Raw Hash salted and/or iterated
4400 | md5(sha1($pass)) | Raw Hash salted and/or iterated
20900 | md5(sha1($pass).md5($pass).sha1($pass)) | Raw Hash salted and/or iterated
21200 | md5(sha1($salt).md5($pass)) | Raw Hash salted and/or iterated
4300 | md5(strtoupper(md5($pass))) | Raw Hash salted and/or iterated
30 | md5(utf16le($pass).$salt) | Raw Hash salted and/or iterated
110 | sha1($pass.$salt) | Raw Hash salted and/or iterated
120 | sha1($salt.$pass) | Raw Hash salted and/or iterated
4900 | sha1($salt.$pass.$salt) | Raw Hash salted and/or iterated
4520 | sha1($salt.sha1($pass)) | Raw Hash salted and/or iterated
24300 | sha1($salt.sha1($pass.$salt)) | Raw Hash salted and/or iterated
140 | sha1($salt.utf16le($pass)) | Raw Hash salted and/or iterated
19300 | sha1($salt1.$pass.$salt2) | Raw Hash salted and/or iterated
14400 | sha1(CX) | Raw Hash salted and/or iterated
4700 | sha1(md5($pass)) | Raw Hash salted and/or iterated
4710 | sha1(md5($pass).$salt) | Raw Hash salted and/or iterated
21100 | sha1(md5($pass.$salt)) | Raw Hash salted and/or iterated
18500 | sha1(md5(md5($pass))) | Raw Hash salted and/or iterated
4500 | sha1(sha1($pass)) | Raw Hash salted and/or iterated
4510 | sha1(sha1($pass).$salt) | Raw Hash salted and/or iterated
5000 | sha1(sha1($salt.$pass.$salt)) | Raw Hash salted and/or iterated
130 | sha1(utf16le($pass).$salt) | Raw Hash salted and/or iterated
1410 | sha256($pass.$salt) | Raw Hash salted and/or iterated
1420 | sha256($salt.$pass) | Raw Hash salted and/or iterated
22300 | sha256($salt.$pass.$salt) | Raw Hash salted and/or iterated
20720 | sha256($salt.sha256($pass)) | Raw Hash salted and/or iterated
1440 | sha256($salt.utf16le($pass)) | Raw Hash salted and/or iterated
20800 | sha256(md5($pass)) | Raw Hash salted and/or iterated
20710 | sha256(sha256($pass).$salt) | Raw Hash salted and/or iterated
21400 | sha256(sha256_bin($pass)) | Raw Hash salted and/or iterated
1430 | sha256(utf16le($pass).$salt) | Raw Hash salted and/or iterated
10810 | sha384($pass.$salt) | Raw Hash salted and/or iterated
10820 | sha384($salt.$pass) | Raw Hash salted and/or iterated
10840 | sha384($salt.utf16le($pass)) | Raw Hash salted and/or iterated
10830 | sha384(utf16le($pass).$salt) | Raw Hash salted and/or iterated
1710 | sha512($pass.$salt) | Raw Hash salted and/or iterated
1720 | sha512($salt.$pass) | Raw Hash salted and/or iterated
1740 | sha512($salt.utf16le($pass)) | Raw Hash salted and/or iterated
1730 | sha512(utf16le($pass).$salt) | Raw Hash salted and/or iterated
50 | HMAC-MD5 (key = $pass) | Raw Hash authenticated
60 | HMAC-MD5 (key = $salt) | Raw Hash authenticated
150 | HMAC-SHA1 (key = $pass) | Raw Hash authenticated
160 | HMAC-SHA1 (key = $salt) | Raw Hash authenticated
1450 | HMAC-SHA256 (key = $pass) | Raw Hash authenticated
1460 | HMAC-SHA256 (key = $salt) | Raw Hash authenticated
1750 | HMAC-SHA512 (key = $pass) | Raw Hash authenticated
1760 | HMAC-SHA512 (key = $salt) | Raw Hash authenticated
11750 | HMAC-Streebog-256 (key = $pass), big-endian | Raw Hash authenticated
11760 | HMAC-Streebog-256 (key = $salt), big-endian | Raw Hash authenticated
11850 | HMAC-Streebog-512 (key = $pass), big-endian | Raw Hash authenticated
11860 | HMAC-Streebog-512 (key = $salt), big-endian | Raw Hash authenticated
11500 | CRC32 | Raw Checksum
27900 | CRC32C | Raw Checksum
28000 | CRC64Jones | Raw Checksum
18700 | Java Object hashCode() | Raw Checksum
25700 | MurmurHash | Raw Checksum
27800 | MurmurHash3 | Raw Checksum
14100 | 3DES (PT = $salt, key = $pass) | Raw Cipher, Known-plaintext attack
14000 | DES (PT = $salt, key = $pass) | Raw Cipher, Known-plaintext attack
26401 | AES-128-ECB NOKDF (PT = $salt, key = $pass) | Raw Cipher, Known-plaintext attack
26402 | AES-192-ECB NOKDF (PT = $salt, key = $pass) | Raw Cipher, Known-plaintext attack
26403 | AES-256-ECB NOKDF (PT = $salt, key = $pass) | Raw Cipher, Known-plaintext attack
15400 | ChaCha20 | Raw Cipher, Known-plaintext attack
14500 | Linux Kernel Crypto API (2.4) | Raw Cipher, Known-plaintext attack
14900 | Skip32 (PT = $salt, key = $pass) | Raw Cipher, Known-plaintext attack
11900 | PBKDF2-HMAC-MD5 | Generic KDF
12000 | PBKDF2-HMAC-SHA1 | Generic KDF
10900 | PBKDF2-HMAC-SHA256 | Generic KDF
12100 | PBKDF2-HMAC-SHA512 | Generic KDF
8900 | scrypt | Generic KDF
400 | phpass | Generic KDF
16100 | TACACS+ | Network Protocol
11400 | SIP digest authentication (MD5) | Network Protocol
5300 | IKE-PSK MD5 | Network Protocol
5400 | IKE-PSK SHA1 | Network Protocol
25100 | SNMPv3 HMAC-MD5-96 | Network Protocol
25000 | SNMPv3 HMAC-MD5-96/HMAC-SHA1-96 | Network Protocol
25200 | SNMPv3 HMAC-SHA1-96 | Network Protocol
26700 | SNMPv3 HMAC-SHA224-128 | Network Protocol
26800 | SNMPv3 HMAC-SHA256-192 | Network Protocol
26900 | SNMPv3 HMAC-SHA384-256 | Network Protocol
27300 | SNMPv3 HMAC-SHA512-384 | Network Protocol
2500 | WPA-EAPOL-PBKDF2 | Network Protocol
2501 | WPA-EAPOL-PMK | Network Protocol
22000 | WPA-PBKDF2-PMKID+EAPOL | Network Protocol
22001 | WPA-PMK-PMKID+EAPOL | Network Protocol
16800 | WPA-PMKID-PBKDF2 | Network Protocol
16801 | WPA-PMKID-PMK | Network Protocol
7300 | IPMI2 RAKP HMAC-SHA1 | Network Protocol
10200 | CRAM-MD5 | Network Protocol
16500 | JWT (JSON Web Token) | Network Protocol
19600 | Kerberos 5, etype 17, TGS-REP | Network Protocol
19800 | Kerberos 5, etype 17, Pre-Auth | Network Protocol
19700 | Kerberos 5, etype 18, TGS-REP | Network Protocol
19900 | Kerberos 5, etype 18, Pre-Auth | Network Protocol
7500 | Kerberos 5, etype 23, AS-REQ Pre-Auth | Network Protocol
13100 | Kerberos 5, etype 23, TGS-REP | Network Protocol
18200 | Kerberos 5, etype 23, AS-REP | Network Protocol
5500 | NetNTLMv1 / NetNTLMv1+ESS | Network Protocol
27000 | NetNTLMv1 / NetNTLMv1+ESS (NT) | Network Protocol
5600 | NetNTLMv2 | Network Protocol
27100 | NetNTLMv2 (NT) | Network Protocol
4800 | iSCSI CHAP authentication, MD5(CHAP) | Network Protocol
8500 | RACF | Operating System
6300 | AIX {smd5} | Operating System
6700 | AIX {ssha1} | Operating System
6400 | AIX {ssha256} | Operating System
6500 | AIX {ssha512} | Operating System
3000 | LM | Operating System
19000 | QNX /etc/shadow (MD5) | Operating System
19100 | QNX /etc/shadow (SHA256) | Operating System
19200 | QNX /etc/shadow (SHA512) | Operating System
15300 | DPAPI masterkey file v1 | Operating System
15900 | DPAPI masterkey file v2 | Operating System
7200 | GRUB 2 | Operating System
12800 | MS-AzureSync PBKDF2-HMAC-SHA256 | Operating System
12400 | BSDi Crypt, Extended DES | Operating System
1000 | NTLM | Operating System
9900 | Radmin2 | Operating System
5800 | Samsung Android Password/PIN | Operating System
28100 | Windows Hello PIN/Password | Operating System
13800 | Windows Phone 8+ PIN/password | Operating System
2410 | Cisco-ASA MD5 | Operating System
9200 | Cisco-IOS $8$ (PBKDF2-SHA256) | Operating System
9300 | Cisco-IOS $9$ (scrypt) | Operating System
5700 | Cisco-IOS type 4 (SHA256) | Operating System
2400 | Cisco-PIX MD5 | Operating System
8100 | Citrix NetScaler (SHA1) | Operating System
22200 | Citrix NetScaler (SHA512) | Operating System
1100 | Domain Cached Credentials (DCC), MS Cache | Operating System
2100 | Domain Cached Credentials 2 (DCC2), MS Cache 2 | Operating System
7000 | FortiGate (FortiOS) | Operating System
26300 | FortiGate256 (FortiOS256) | Operating System
125 | ArubaOS | Operating System
501 | Juniper IVE | Operating System
22 | Juniper NetScreen/SSG (ScreenOS) | Operating System
15100 | Juniper/NetBSD sha1crypt | Operating System
26500 | iPhone passcode (UID key + System Keybag) | Operating System
122 | macOS v10.4, macOS v10.5, macOS v10.6 | Operating System
1722 | macOS v10.7 | Operating System
7100 | macOS v10.8+ (PBKDF2-SHA512) | Operating System
3200 | bcrypt $2*$, Blowfish (Unix) | Operating System
500 | md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5) | Operating System
1500 | descrypt, DES (Unix), Traditional DES | Operating System
7400 | sha256crypt $5$, SHA256 (Unix) | Operating System
1800 | sha512crypt $6$, SHA512 (Unix) | Operating System
24600 | SQLCipher | Database Server
131 | MSSQL (2000) | Database Server
132 | MSSQL (2005) | Database Server
1731 | MSSQL (2012, 2014) | Database Server
24100 | MongoDB ServerKey SCRAM-SHA-1 | Database Server
24200 | MongoDB ServerKey SCRAM-SHA-256 | Database Server
12 | PostgreSQL | Database Server
11100 | PostgreSQL CRAM (MD5) | Database Server
3100 | Oracle H: Type (Oracle 7+) | Database Server
112 | Oracle S: Type (Oracle 11+) | Database Server
12300 | Oracle T: Type (Oracle 12+) | Database Server
7401 | MySQL $A$ (sha256crypt) | Database Server
11200 | MySQL CRAM (SHA1) | Database Server
200 | MySQL323 | Database Server
300 | MySQL4.1/MySQL5 | Database Server
8000 | Sybase ASE | Database Server
8300 | DNSSEC (NSEC3) | FTP, HTTP, SMTP, LDAP Server
25900 | KNX IP Secure - Device Authentication Code | FTP, HTTP, SMTP, LDAP Server
16400 | CRAM-MD5 Dovecot | FTP, HTTP, SMTP, LDAP Server
1411 | SSHA-256(Base64), LDAP {SSHA256} | FTP, HTTP, SMTP, LDAP Server
1711 | SSHA-512(Base64), LDAP {SSHA512} | FTP, HTTP, SMTP, LDAP Server
24900 | Dahua Authentication MD5 | FTP, HTTP, SMTP, LDAP Server
10901 | RedHat 389-DS LDAP (PBKDF2-HMAC-SHA256) | FTP, HTTP, SMTP, LDAP Server
15000 | FileZilla Server >= 0.9.55 | FTP, HTTP, SMTP, LDAP Server
12600 | ColdFusion 10+ | FTP, HTTP, SMTP, LDAP Server
1600 | Apache $apr1$ MD5, md5apr1, MD5 (APR) | FTP, HTTP, SMTP, LDAP Server
141 | Episerver 6.x < .NET 4 | FTP, HTTP, SMTP, LDAP Server
1441 | Episerver 6.x >= .NET 4 | FTP, HTTP, SMTP, LDAP Server
1421 | hMailServer | FTP, HTTP, SMTP, LDAP Server
101 | nsldap, SHA-1(Base64), Netscape LDAP SHA | FTP, HTTP, SMTP, LDAP Server
111 | nsldaps, SSHA-1(Base64), Netscape LDAP SSHA | FTP, HTTP, SMTP, LDAP Server
7700 | SAP CODVN B (BCODE) | Enterprise Application Software (EAS)
7701 | SAP CODVN B (BCODE) from RFC_READ_TABLE | Enterprise Application Software (EAS)
7800 | SAP CODVN F/G (PASSCODE) | Enterprise Application Software (EAS)
7801 | SAP CODVN F/G (PASSCODE) from RFC_READ_TABLE | Enterprise Application Software (EAS)
10300 | SAP CODVN H (PWDSALTEDHASH) iSSHA-1 | Enterprise Application Software (EAS)
133 | PeopleSoft | Enterprise Application Software (EAS)
13500 | PeopleSoft PS_TOKEN | Enterprise Application Software (EAS)
21500 | SolarWinds Orion | Enterprise Application Software (EAS)
21501 | SolarWinds Orion v2 | Enterprise Application Software (EAS)
24 | SolarWinds Serv-U | Enterprise Application Software (EAS)
8600 | Lotus Notes/Domino 5 | Enterprise Application Software (EAS)
8700 | Lotus Notes/Domino 6 | Enterprise Application Software (EAS)
9100 | Lotus Notes/Domino 8 | Enterprise Application Software (EAS)
26200 | OpenEdge Progress Encode | Enterprise Application Software (EAS)
20600 | Oracle Transportation Management (SHA256) | Enterprise Application Software (EAS)
4711 | Huawei sha1(md5($pass).$salt) | Enterprise Application Software (EAS)
20711 | AuthMe sha256 | Enterprise Application Software (EAS)
22400 | AES Crypt (SHA256) | Full-Disk Encryption (FDE)
27400 | VMware VMX (PBKDF2-HMAC-SHA1 + AES-256-CBC) | Full-Disk Encryption (FDE)
14600 | LUKS | Full-Disk Encryption (FDE)
13711 | VeraCrypt RIPEMD160 + XTS 512 bit | Full-Disk Encryption (FDE)
13712 | VeraCrypt RIPEMD160 + XTS 1024 bit | Full-Disk Encryption (FDE)
13713 | VeraCrypt RIPEMD160 + XTS 1536 bit | Full-Disk Encryption (FDE)
13741 | VeraCrypt RIPEMD160 + XTS 512 bit + boot-mode | Full-Disk Encryption (FDE)
13742 | VeraCrypt RIPEMD160 + XTS 1024 bit + boot-mode | Full-Disk Encryption (FDE)
13743 | VeraCrypt RIPEMD160 + XTS 1536 bit + boot-mode | Full-Disk Encryption (FDE)
13751 | VeraCrypt SHA256 + XTS 512 bit | Full-Disk Encryption (FDE)
13752 | VeraCrypt SHA256 + XTS 1024 bit | Full-Disk Encryption (FDE)
13753 | VeraCrypt SHA256 + XTS 1536 bit | Full-Disk Encryption (FDE)
13761 | VeraCrypt SHA256 + XTS 512 bit + boot-mode | Full-Disk Encryption (FDE)
13762 | VeraCrypt SHA256 + XTS 1024 bit + boot-mode | Full-Disk Encryption (FDE)
13763 | VeraCrypt SHA256 + XTS 1536 bit + boot-mode | Full-Disk Encryption (FDE)
13721 | VeraCrypt SHA512 + XTS 512 bit | Full-Disk Encryption (FDE)
13722 | VeraCrypt SHA512 + XTS 1024 bit | Full-Disk Encryption (FDE)
13723 | VeraCrypt SHA512 + XTS 1536 bit | Full-Disk Encryption (FDE)
13771 | VeraCrypt Streebog-512 + XTS 512 bit | Full-Disk Encryption (FDE)
13772 | VeraCrypt Streebog-512 + XTS 1024 bit | Full-Disk Encryption (FDE)
13773 | VeraCrypt Streebog-512 + XTS 1536 bit | Full-Disk Encryption (FDE)
13781 | VeraCrypt Streebog-512 + XTS 512 bit + boot-mode | Full-Disk Encryption (FDE)
13782 | VeraCrypt Streebog-512 + XTS 1024 bit + boot-mode | Full-Disk Encryption (FDE)
13783 | VeraCrypt Streebog-512 + XTS 1536 bit + boot-mode | Full-Disk Encryption (FDE)
13731 | VeraCrypt Whirlpool + XTS 512 bit | Full-Disk Encryption (FDE)
13732 | VeraCrypt Whirlpool + XTS 1024 bit | Full-Disk Encryption (FDE)
13733 | VeraCrypt Whirlpool + XTS 1536 bit | Full-Disk Encryption (FDE)
23900 | BestCrypt v3 Volume Encryption | Full-Disk Encryption (FDE)
16700 | FileVault 2 | Full-Disk Encryption (FDE)
27500 | VirtualBox (PBKDF2-HMAC-SHA256 & AES-128-XTS) | Full-Disk Encryption (FDE)
27600 | VirtualBox (PBKDF2-HMAC-SHA256 & AES-256-XTS) | Full-Disk Encryption (FDE)
20011 | DiskCryptor SHA512 + XTS 512 bit | Full-Disk Encryption (FDE)
20012 | DiskCryptor SHA512 + XTS 1024 bit | Full-Disk Encryption (FDE)
20013 | DiskCryptor SHA512 + XTS 1536 bit | Full-Disk Encryption (FDE)
22100 | BitLocker | Full-Disk Encryption (FDE)
12900 | Android FDE (Samsung DEK) | Full-Disk Encryption (FDE)
8800 | Android FDE <= 4.3 | Full-Disk Encryption (FDE)
18300 | Apple File System (APFS) | Full-Disk Encryption (FDE)
6211 | TrueCrypt RIPEMD160 + XTS 512 bit | Full-Disk Encryption (FDE)
6212 | TrueCrypt RIPEMD160 + XTS 1024 bit | Full-Disk Encryption (FDE)
6213 | TrueCrypt RIPEMD160 + XTS 1536 bit | Full-Disk Encryption (FDE)
6241 | TrueCrypt RIPEMD160 + XTS 512 bit + boot-mode | Full-Disk Encryption (FDE)
6242 | TrueCrypt RIPEMD160 + XTS 1024 bit + boot-mode | Full-Disk Encryption (FDE)
6243 | TrueCrypt RIPEMD160 + XTS 1536 bit + boot-mode | Full-Disk Encryption (FDE)
6221 | TrueCrypt SHA512 + XTS 512 bit | Full-Disk Encryption (FDE)
6222 | TrueCrypt SHA512 + XTS 1024 bit | Full-Disk Encryption (FDE)
6223 | TrueCrypt SHA512 + XTS 1536 bit | Full-Disk Encryption (FDE)
6231 | TrueCrypt Whirlpool + XTS 512 bit | Full-Disk Encryption (FDE)
6232 | TrueCrypt Whirlpool + XTS 1024 bit | Full-Disk Encryption (FDE)
6233 | TrueCrypt Whirlpool + XTS 1536 bit | Full-Disk Encryption (FDE)
12200 | eCryptfs | Full-Disk Encryption (FDE)
10400 | PDF 1.1 - 1.3 (Acrobat 2 - 4) | Document
10410 | PDF 1.1 - 1.3 (Acrobat 2 - 4), collider #1 | Document
10420 | PDF 1.1 - 1.3 (Acrobat 2 - 4), collider #2 | Document
10500 | PDF 1.4 - 1.6 (Acrobat 5 - 8) | Document
25400 | PDF 1.4 - 1.6 (Acrobat 5 - 8) - user and owner pass | Document
10600 | PDF 1.7 Level 3 (Acrobat 9) | Document
10700 | PDF 1.7 Level 8 (Acrobat 10 - 11) | Document
9400 | MS Office 2007 | Document
9500 | MS Office 2010 | Document
9600 | MS Office 2013 | Document
25300 | MS Office 2016 - SheetProtection | Document
9700 | MS Office <= 2003 $0/$1, MD5 + RC4 | Document
9710 | MS Office <= 2003 $0/$1, MD5 + RC4, collider #1 | Document
9720 | MS Office <= 2003 $0/$1, MD5 + RC4, collider #2 | Document
9810 | MS Office <= 2003 $3, SHA1 + RC4, collider #1 | Document
9820 | MS Office <= 2003 $3, SHA1 + RC4, collider #2 | Document
9800 | MS Office <= 2003 $3/$4, SHA1 + RC4 | Document
18400 | Open Document Format (ODF) 1.2 (SHA-256, AES) | Document
18600 | Open Document Format (ODF) 1.1 (SHA-1, Blowfish) | Document
16200 | Apple Secure Notes | Document
23300 | Apple iWork | Document
6600 | 1Password, agilekeychain | Password Manager
8200 | 1Password, cloudkeychain | Password Manager
9000 | Password Safe v2 | Password Manager
5200 | Password Safe v3 | Password Manager
6800 | LastPass + LastPass sniffed | Password Manager
13400 | KeePass 1 (AES/Twofish) and KeePass 2 (AES) | Password Manager
23400 | Bitwarden | Password Manager
16900 | Ansible Vault | Password Manager
26000 | Mozilla key3.db | Password Manager
26100 | Mozilla key4.db | Password Manager
23100 | Apple Keychain | Password Manager
11600 | 7-Zip | Archive
12500 | RAR3-hp | Archive
23800 | RAR3-p (Compressed) | Archive
23700 | RAR3-p (Uncompressed) | Archive
13000 | RAR5 | Archive
17220 | PKZIP (Compressed Multi-File) | Archive
17200 | PKZIP (Compressed) | Archive
17225 | PKZIP (Mixed Multi-File) | Archive
17230 | PKZIP (Mixed Multi-File Checksum-Only) | Archive
17210 | PKZIP (Uncompressed) | Archive
20500 | PKZIP Master Key | Archive
20510 | PKZIP Master Key (6 byte optimization) | Archive
23001 | SecureZIP AES-128 | Archive
23002 | SecureZIP AES-192 | Archive
23003 | SecureZIP AES-256 | Archive
13600 | WinZip | Archive
18900 | Android Backup | Archive
24700 | Stuffit5 | Archive
13200 | AxCrypt 1 | Archive
13300 | AxCrypt 1 in-memory SHA1 | Archive
23500 | AxCrypt 2 AES-128 | Archive
23600 | AxCrypt 2 AES-256 | Archive
14700 | iTunes backup < 10.0 | Archive
14800 | iTunes backup >= 10.0 | Archive
8400 | WBB3 (Woltlab Burning Board) | Forums, CMS, E-Commerce
2612 | PHPS | Forums, CMS, E-Commerce
121 | SMF (Simple Machines Forum) > v1.1 | Forums, CMS, E-Commerce
3711 | MediaWiki B type | Forums, CMS, E-Commerce
4521 | Redmine | Forums, CMS, E-Commerce
24800 | Umbraco HMAC-SHA1 | Forums, CMS, E-Commerce
11 | Joomla < 2.5.18 | Forums, CMS, E-Commerce
13900 | OpenCart | Forums, CMS, E-Commerce
11000 | PrestaShop | Forums, CMS, E-Commerce
16000 | Tripcode | Forums, CMS, E-Commerce
7900 | Drupal7 | Forums, CMS, E-Commerce
4522 | PunBB | Forums, CMS, E-Commerce
2811 | MyBB 1.2+, IPB2+ (Invision Power Board) | Forums, CMS, E-Commerce
2611 | vBulletin < v3.8.5 | Forums, CMS, E-Commerce
2711 | vBulletin >= v3.8.5 | Forums, CMS, E-Commerce
25600 | bcrypt(md5($pass)) / bcryptmd5 | Forums, CMS, E-Commerce
25800 | bcrypt(sha1($pass)) / bcryptsha1 | Forums, CMS, E-Commerce
21 | osCommerce, xt:Commerce | Forums, CMS, E-Commerce
18100 | TOTP (HMAC-SHA1) | One-Time Password
2000 | STDOUT | Plaintext
99999 | Plaintext | Plaintext
21600 | Web2py pbkdf2-sha512 | Framework
10000 | Django (PBKDF2-SHA256) | Framework
124 | Django (SHA-1) | Framework
12001 | Atlassian (PBKDF2-HMAC-SHA1) | Framework
19500 | Ruby on Rails Restful-Authentication | Framework
27200 | Ruby on Rails Restful Auth (one round, no sitekey) | Framework
20200 | Python passlib pbkdf2-sha512 | Framework
20300 | Python passlib pbkdf2-sha256 | Framework
20400 | Python passlib pbkdf2-sha1 | Framework
24410 | PKCS#8 Private Keys (PBKDF2-HMAC-SHA1 + 3DES/AES) | Private Key
24420 | PKCS#8 Private Keys (PBKDF2-HMAC-SHA256 + 3DES/AES) | Private Key
15500 | JKS Java Key Store Private Keys (SHA1) | Private Key
22911 | RSA/DSA/EC/OpenSSH Private Keys ($0$) | Private Key
22921 | RSA/DSA/EC/OpenSSH Private Keys ($6$) | Private Key
22931 | RSA/DSA/EC/OpenSSH Private Keys ($1, $3$) | Private Key
22941 | RSA/DSA/EC/OpenSSH Private Keys ($4$) | Private Key
22951 | RSA/DSA/EC/OpenSSH Private Keys ($5$) | Private Key
23200 | XMPP SCRAM PBKDF2-SHA1 | Instant Messaging Service
22600 | Telegram Desktop < v2.1.14 (PBKDF2-HMAC-SHA1) | Instant Messaging Service
24500 | Telegram Desktop >= v2.1.14 (PBKDF2-HMAC-SHA512) | Instant Messaging Service
22301 | Telegram Mobile App Passcode (SHA256) | Instant Messaging Service
23 | Skype | Instant Messaging Service
26600 | MetaMask Wallet | Cryptocurrency Wallet
21000 | BitShares v0.x - sha512(sha512_bin(pass)) | Cryptocurrency Wallet
11300 | Bitcoin/Litecoin wallet.dat | Cryptocurrency Wallet
16600 | Electrum Wallet (Salt-Type 1-3) | Cryptocurrency Wallet
21700 | Electrum Wallet (Salt-Type 4) | Cryptocurrency Wallet
21800 | Electrum Wallet (Salt-Type 5) | Cryptocurrency Wallet
12700 | Blockchain, My Wallet | Cryptocurrency Wallet
15200 | Blockchain, My Wallet, V2 | Cryptocurrency Wallet
18800 | Blockchain, My Wallet, Second Password (SHA256) | Cryptocurrency Wallet
25500 | Stargazer Stellar Wallet XLM | Cryptocurrency Wallet
16300 | Ethereum Pre-Sale Wallet, PBKDF2-HMAC-SHA256 | Cryptocurrency Wallet
15600 | Ethereum Wallet, PBKDF2-HMAC-SHA256 | Cryptocurrency Wallet
15700 | Ethereum Wallet, SCRYPT | Cryptocurrency Wallet
22500 | MultiBit Classic .key (MD5) | Cryptocurrency Wallet
27700 | MultiBit Classic .wallet (scrypt) | Cryptocurrency Wallet
22700 | MultiBit HD (scrypt) | Cryptocurrency Wallet
-a 参数
- [ Attack Modes ] -
# | Mode
===+======
0 Straight(字典破解)
1 Combination(组合破解)
3 Brute-force(掩码暴力破解)
6 Hybrid dict + mask(混合字典+掩码)
7 Hybrid mask + dict(混合掩码+字典)
其他参数
–increment
启用增量破解模式,让 hashcat 在指定的密码长度范围内执行破解
–increment-min
密码最小长度,后面直接等于一个整数即可,配置 increment 模式一起使用
–increment-max
密码最大长度,后面直接等于一个整数即可,配置 increment 模式一起使用
–force
忽略破解过程中的警告信息
–remove
删除已被破解成功的 hash
–username
忽略 hash 文件中的指定的用户名,在破解 Linux 系统用户密码 hash 会用到
–potfile-disable
不在 potfile 中记录破解成功的 hash
-I
--opencl-info显示有关检测到的 OpenCL 平台/设备的信息,如果有一块好的显卡的话破解速度会快很多。
-o
--outfile 指定破解成功后的 hash 及所对应的明文密码的存放位置
-O
--optimized-kernel-enable 启用优化的内核(限制密码长度)
-d
--opencl-devices指定 opencl 的设备
内置字符集
===+============+============+==============+==============+
l | abcdefghijklmnopqrstuvwxyz # 小写字母 a-z
u | ABCDEFGHIJKLMNOPQRSTUVWXYZ # 大写字母 A-Z
d | 0123456789 # 数字 0-9
h | 0123456789abcdef # 数字 + abcdef
H | 0123456789ABCDEF # 数字 + ABCDEF
s | !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~ # 特殊字符
a | ?l?u?d?s # 键盘上所有可见的字符
b | 0x00 - 0xff # 可能是用来匹配像空格这种密码的
===+============+============+==============+==============+
使用场景补充
使用hashcat破解md5
1、首先用pass@word生成一个md5
1f579f72a6a8ce1033afca7c94c132b0
使用hashcat
hashcat -m 0 -a 0 -o success.txt check.hash password.txt
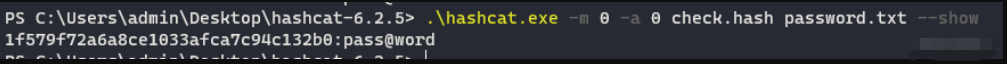
成功破解。
如果使用字典破解,那么破解速度就取决于你的字典大小。
2、再用54789654八位数纯数字生成一个md5
af8430e2c9c4bc3dc3f1a1dc69bbcc82
使用字符集破解模式
.\hashcat.exe -m 0 -a 3 .\check.hash ?d?d?d?d?d?d?d?d
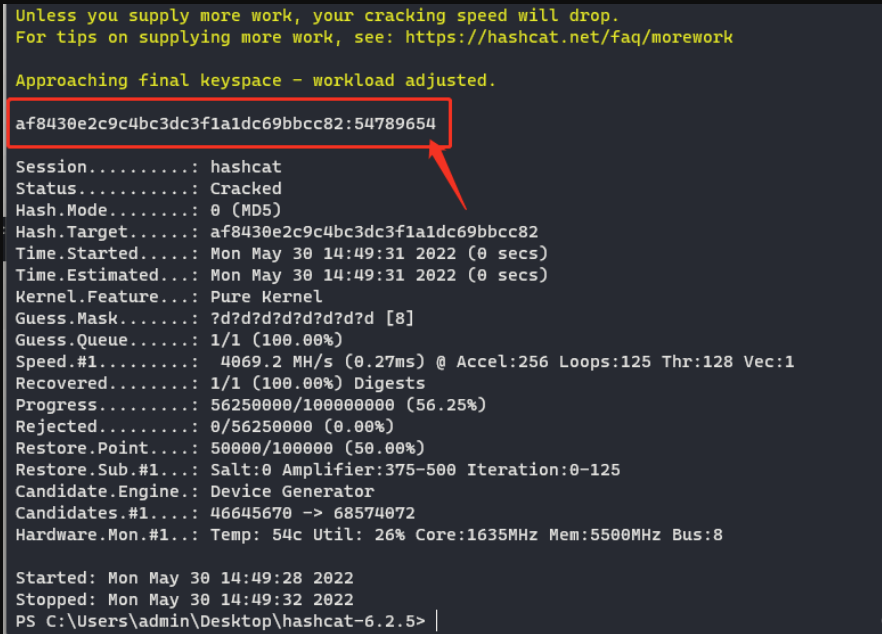
可以看到,这种简单的纯数字密码几秒钟就能破解。
如果使用内置字符集破解,那么破解速度取决于你的CPU或GPU的运算力。
使用hashcat破解加盐md5
找一个加盐hash
9393dc56f0c683b7bba9b3751d0f6a46:OTD6v4c8I3Zid2AL
使用hashcat
.\hashcat.exe -m 10 -a 0 .\check.hash .\password.txt
成功破解

如果想使用GPU来跑的话,可以参考上面操作步骤。
参考
https://www.sqlsec.com/2019/10/hashcat.html#toc-heading-22
Hashcat使用指南的更多相关文章
- JavaScript权威指南 - 函数
函数本身就是一段JavaScript代码,定义一次但可能被调用任意次.如果函数挂载在一个对象上,作为对象的一个属性,通常这种函数被称作对象的方法.用于初始化一个新创建的对象的函数被称作构造函数. 相对 ...
- UE4新手之编程指南
虚幻引擎4为程序员提供了两套工具集,可共同使用来加速开发的工作流程. 新的游戏类.Slate和Canvas用户接口元素以及编辑器功能可以使用C++语言来编写,并且在使用Visual Studio 或 ...
- JavaScript权威指南 - 对象
JavaScript对象可以看作是属性的无序集合,每个属性就是一个键值对,可增可删. JavaScript中的所有事物都是对象:字符串.数字.数组.日期,等等. JavaScript对象除了可以保持自 ...
- JavaScript权威指南 - 数组
JavaScript数组是一种特殊类型的对象. JavaScript数组元素可以为任意类型,最大容纳232-1个元素. JavaScript数组是动态的,有新元素添加时,自动更新length属性. J ...
- const extern static 终极指南
const extern static 终极指南 不管是从事哪种语言的开发工作,const extern static 这三个关键字的用法和原理都是我们必须明白的.本文将对此做出非常详细的讲解. co ...
- Atitit.研发管理软件公司的软资产列表指南
Atitit.研发管理软件公司的软资产列表指南 1. Isv模型下的软资产1 2. 实现层面implet1 3. 规范spec层1 4. 法则定律等val层的总结2 1. Isv模型下的软资产 Sof ...
- HA 高可用软件系统保养指南
又过了一年 618,六月是公司一年一度的大促月,一般提前一个月各系统就会减少需求和功能的开发,转而更多去关注系统可用性.稳定性和管控性等方面的非功能需求.大促前的准备工作一般叫作「备战」,可以把线上运 ...
- 第六代智能英特尔® 酷睿™ 处理器图形 API 开发人员指南
欢迎查看第六代智能英特尔® 酷睿™ 处理器图形 API 开发人员指南,该处理器可为开发人员和最终用户提供领先的 CPU 和图形性能增强.各种新特性和功能以及显著提高的性能. 本指南旨在帮助软件开发人员 ...
- Visual Studio Code 配置指南
Visual Studio Code (简称 VS Code)是由微软研发的一款免费.开源的跨平台文本(代码)编辑器.在我看来它是「一款完美的编辑器」. 本文是有关 VS Code 的特性介绍与配置指 ...
- Web API 入门指南 - 闲话安全
Web API入门指南有些朋友回复问了些安全方面的问题,安全方面可以写的东西实在太多了,这里尽量围绕着Web API的安全性来展开,介绍一些安全的基本概念,常见安全隐患.相关的防御技巧以及Web AP ...
随机推荐
- 100 个常见错误「GitHub 热点速览 v.22.35」
本周的特推非常得延续上周的特点--会玩,向别人家的女朋友发送早安.这个错误是如何发生的呢?如何有效避免呢?自己用 daily_morning 免部署.定制一个早安小助手给女友吧. 除了生活中的错误,工 ...
- 存储更弹性,详解 Fluid “ECI 环境数据访问” 新功能
近期,Fluid 支持了阿里云 ECI 应用,并将 JuiceFS Runtime Controller 设置为默认安装:JuiceFS 也就此功能与 Fluid 完成了集成和测试工作. 用户可以在 ...
- Redux(mvc、flux、react-redux)
其他章节请看: react实战 系列 Redux 关于状态管理,在 Vue 中我们已经使用过 Vuex,在 spug 项目中我们使用了 mobx,接下来我们学习 Redux. 本篇以较为易懂的方式讲解 ...
- .NET 6当中的Web API版本控制
大家好,我是张飞洪,感谢您的阅读,我会不定期和你分享学习心得,希望我的文章能成为你成长路上的垫脚石,让我们一起精进. 为了了解ASP.NET Core Web API的版本控制,我们必须了解API中的 ...
- Chrome 浏览器缓存的问题
浏览器缓存的问题 Chrome 在浏览器中设置: 1 Ctrl + Shift + Delete 2 Ctrl + F5 强制刷新 3 F12 打开控制台 ---> Network ---> ...
- nginx中 location正则的理解
文章转载自:https://blog.csdn.net/wzj_110/article/details/110142902 正则表达式在线测试工具:https://tool.lu/regex loca ...
- Kubernetes 监控:Prometheus Adpater =》自定义指标扩缩容
使用 Kubernetes 进行容器编排的主要优点之一是,它可以非常轻松地对我们的应用程序进行水平扩展.Pod 水平自动缩放(HPA)可以根据 CPU 和内存使用量来扩展应用,前面讲解的 HPA 章节 ...
- 安装krew
地址:https://krew.sigs.k8s.io/docs/user-guide/setup/install/ macOS/Linux Bash or ZSH shells 确保已安装git 2 ...
- Elastic:应用程序性能监控/管理(APM)实践
在今天的文章里,我们将介绍Elastic的一个重要的应用:应用程序性能管理(Application Performance Monitoring/Management),简称APM.那么到底什么是AP ...
- ingress-nginx自带认证功能【nginx自带】
问题:通过nginx可以给某些web网站设置登录使用的用户名和密码,现在网站部署到k8s中,通过配置nginx-ingress->service->pod来访问的,怎么给这个网站再配置上访 ...
