Model Inversion Attack Paper Indexpage
Paper [1]:
White-box neural network attack, adversaries have full access to the model. Using Gradient Descent going back to update the input so that reconstructing the original training data.
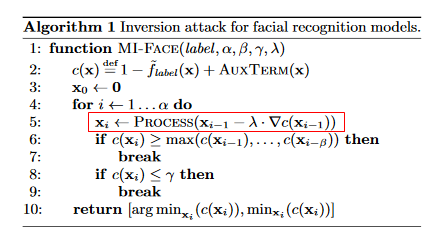
About black-box attack, they mentioned using numeric gradient approximation.
Question: If the model does not overfit the dataset, cannot recover the training data.
Paper [2]:
Proposed black-box attack via online ML-as-a-S platform, targeting to extract parameters from simple structures by solving equations. Condifence values is the key to solve these equations.
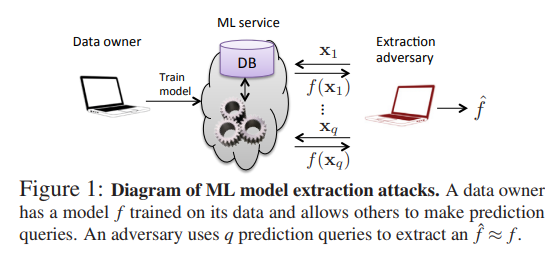
Question: However, this method seems like brute force, and it would be tough when the type and structure of model are unknown or really complex. Ex. they query 10,000 times to steal a neural network, which will be identified as hacking activity in real environment. (or too expensive to query online service)
[1] M. Fredrikson, S. Jha and T. Ristenpart, "Model inversion attacks that exploit confidence information and basic countermeasures," in 2015, . DOI: 10.1145/2810103.2813677.
[2] Florian Tramer, Fan Zhang, Ari Juels, Michael K. Reiter, and Thomas Ristenpart. Stealing machine learning models via prediction apis. In 25th USENIX Security Symposium, USENIX Security 16, Austin, TX, USA, August 10-12, 2016., pages 601-618, 2016. Presentation: https://www.youtube.com/watch?time_continue=26&v=qGjzmEzPkiI
Model Inversion Attack Paper Indexpage的更多相关文章
- Summary on Visual Tracking: Paper List, Benchmarks and Top Groups
Summary on Visual Tracking: Paper List, Benchmarks and Top Groups 2018-07-26 10:32:15 This blog is c ...
- 【Paper】智能家居
From: http://liudongdong1.github.io keyword: Human-centered computing , LoRa Paper: WIDESEE WIDESEE: ...
- Attention and Augmented Recurrent Neural Networks
Attention and Augmented Recurrent Neural Networks CHRIS OLAHGoogle Brain SHAN CARTERGoogle Brain Sep ...
- linux 并发 RCU
What is RCU, Fundamentally? https://lwn.net/Articles/262464/ If you can fill the unforgiving secondw ...
- [笔记]Practical Lessons from Predicting Clicks on Ads at Facebook
ABSTRACT 这篇paper中作者结合GBDT和LR,取得了很好的效果,比单个模型的效果高出3%.随后作者研究了对整体预测系统产生影响的几个因素,发现Feature+Model的贡献程度最大,而其 ...
- 用Caffe生成对抗样本
同步自我的知乎专栏:https://zhuanlan.zhihu.com/p/26122612 上篇文章 瞎谈CNN:通过优化求解输入图像 - 知乎专栏 中提到过对抗样本,这篇算是针对对抗样本的一个小 ...
- Unity文档阅读 第二章 依赖注入
Introduction 介绍Chapter 1 outlines how you can address some of the most common requirements in enterp ...
- Unity Rain Ai 插件基本使用(二)
前言 在前面的教程中我们已经基本实现了路径导航和障碍物规避. 但是这样我们并没有让我们的角色学会思考,他只是机械的去完成一些步骤,这并不能体现Rain插件的智能. 一个角色他应该有多个不同的状态,待机 ...
- 机器学习算法GBDT
http://www-personal.umich.edu/~jizhu/jizhu/wuke/Friedman-AoS01.pdf https://www.cnblogs.com/bentuwuyi ...
随机推荐
- linux下解压缩.tar.bz2到某目录下
1\可先进入要解压的目的目录,然后使用tar命令 比如我要将桌面的a.tar.bz2解压到/var/b cd /var/b tar -xjf /root/Desktop/a.tar.bz2 ...
- ARM Cortex-M底层技术(1)—程序在Flash和SRAM的空间分配
1. keil编译介绍 当使用keil进行单片机的开发时,运行一段程序后,在output输出框会看到如下图的结果. 图1 keil 的output框 其中,Compiler编译器,使用的版本是 V5. ...
- 爱奇艺免费vip观看地址
本人qq群也有许多的技术文档,希望可以为你提供一些帮助(非技术的勿加). QQ群: 281442983 (点击链接加入群:http://jq.qq.com/?_wv=1027&k=29Lo ...
- Tomcat与jdk在Linux上的安装与配置
本人qq群也有许多的技术文档,希望可以为你提供一些帮助(非技术的勿加). QQ群: 281442983 (点击链接加入群:http://jq.qq.com/?_wv=1027&k=29Lo ...
- layui数据表格分页加载动画,自己定义加载动画,"加载中..."
记录思路,仅供参考 在表格渲染完成后,在done回调函数中给分页动态加点击事件, 关闭"加载中..."动画也是在 done回调函数中关闭 这是我实现的思路,记录给大家参考. , d ...
- Centos logrotate截断tomcat日志文件
1. 设置logrotate轮转日志文件 tomcat日志目录:/usr/local/tomcat/apache-tomcat-8.5.34/logs /etc/logrotate.d/目录下创建to ...
- handy源码阅读(四):Channel类
通道,封装了可以进行epoll的一个fd. struct Channel: private noncopyable { Channel(EventBase* base, int fd, int eve ...
- 6392. 【NOIP2019模拟2019.10.26】僵尸
题目描述 题解 吼题但题解怎么这么迷 考虑一种和题解不同的做法(理解) 先把僵尸离散化,h相同的钦(ying)点一个大小 (可以发现这样每种情况只会被算正好一次) 计算完全被占领的方案,然后1-方案/ ...
- React 之React.createContext
使用Context,可以跨越组件进行数据传递 import React from 'react'; import ReactDOM from 'react-dom'; const ThemeConte ...
- 170826-关于spring的知识点及练习
1.Spring作用: 1.生态体系庞大,全能型选手![springmvc是其一个子模块,jdbcTemplate能直接操作数据库!] 2.将其他组件粘合在一起 3.IOC容器和AOP[Aspect ...
