poj1523 求割点 tarjan
| Time Limit: 1000MS | Memory Limit: 10000K | |
| Total Submissions: 7678 | Accepted: 3489 |
Description
Node 3 is therefore a Single Point of Failure (SPF) for this network. Strictly, an SPF will be defined as any node that, if unavailable, would prevent at least one pair of available nodes from being able to communicate on what was previously a fully connected network. Note that the network on the right has no such node; there is no SPF in the network. At least two machines must fail before there are any pairs of available nodes which cannot communicate. 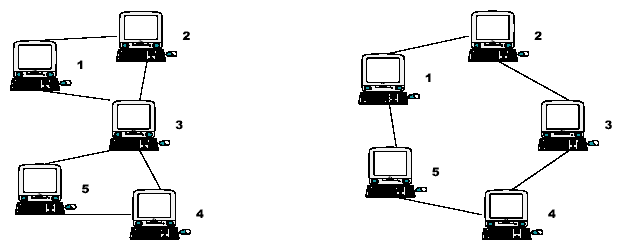
Input
Output
The first network in the file should be identified as "Network #1", the second as "Network #2", etc. For each SPF node, output a line, formatted as shown in the examples below, that identifies the node and the number of fully connected subnets that remain when that node fails. If the network has no SPF nodes, simply output the text "No SPF nodes" instead of a list of SPF nodes.
Sample Input
- 1 2
- 5 4
- 3 1
- 3 2
- 3 4
- 3 5
- 0
- 1 2
- 2 3
- 3 4
- 4 5
- 5 1
- 0
- 1 2
- 2 3
- 3 4
- 4 6
- 6 3
- 2 5
- 5 1
- 0
- 0
Sample Output
- Network #1
- SPF node 3 leaves 2 subnets
- Network #2
- No SPF nodes
- Network #3
- SPF node 2 leaves 2 subnets
- SPF node 3 leaves 2 subnets
题意: 求割点 同时求出删除当前点后,分成几个连通分量。
思路:
tarjan算法求割点。 tarjan处理强连通 其实都是基于dfs的。同时维护2个数组。 dfn[] 和 low[] 分别表示第i点时的深度,和通过能够到达的祖先的深度。
求强连通的时候,如果low[i] == dfn[i] 说明栈内当前点以上的点 都是强连通块里面的。也就是说i的子树中不能到达i的祖先。
在求割点的时候,如果low[v] > dfn[u](v是u的子节点)说明v不能到达u的祖先 说明删除u后 v的子树从原图中分离。
- #include<set>
- #include<map>
- #include<queue>
- #include<stack>
- #include<cmath>
- #include<string>
- #include<vector>
- #include<cstdio>
- #include<cstring>
- #include<iostream>
- #include<algorithm>
- #define INF 1000000001
- #define MOD 1000000007
- #define ll long long
- #define lson l,m,rt<<1
- #define rson m+1,r,rt<<1|1
- #define pi acos(-1.0)
- using namespace std;
- const int MAXN = ;
- struct node
- {
- int to;
- int next;
- }edge[MAXN*];
- int ind,pre[MAXN],dfn[MAXN],low[MAXN],num[MAXN],n,vis[MAXN];
- void add(int x,int y)
- {
- edge[ind].to = y;
- edge[ind].next = pre[x];
- pre[x] = ind ++;
- }
- void dfs(int rt,int d)
- {
- vis[rt] = ;
- dfn[rt] = low[rt] = d;
- for(int i = pre[rt]; i != -; i = edge[i].next){
- int t = edge[i].to;
- if(!vis[t]){
- dfs(t,d + );
- low[rt] = min(low[rt],low[t]);
- if(low[t] >= dfn[rt]){
- num[rt] ++;
- }
- }
- else {
- low[rt] = min(low[rt],dfn[t]);
- }
- }
- }
- int main()
- {
- int x,y,ff = ;
- while(){
- n = ;
- scanf("%d",&x);
- if(!x)break;
- scanf("%d",&y);
- ind = , memset(pre,-,sizeof(pre));
- add(x,y), add(y,x);
- n = max(x,y);
- while(){
- scanf("%d",&x);
- if(!x)break;
- scanf("%d",&y);
- n = max(n,x);
- n = max(n,y);
- add(x,y), add(y,x);
- }
- memset(vis,,sizeof(vis));
- memset(dfn,,sizeof(dfn));
- memset(low,,sizeof(low));
- memset(num,,sizeof(num));
- dfs(,);
- int flag = ;
- if(ff >= )printf("\n");
- printf("Network #%d\n",++ff);
- num[] = num[] ? num[] - : ;
- for(int i = ; i <= n; i++){
- if(num[i]){
- flag = ;
- printf(" SPF node %d leaves %d subnets\n",i,num[i] + );
- }
- }
- if(!flag){
- printf(" No SPF nodes\n");
- }
- }
- return ;
- }
poj1523 求割点 tarjan的更多相关文章
- poj1523求割点以及割后连通分量数tarjan算法应用
无向图,双向通道即可,tarjan算法简单应用.点u是割点,条件1:u是dfs树根,则u至少有2个孩子结点.||条件2:u不是根,dfn[u]=<low[v],v是u的孩子结点,而且每个这样的v ...
- zoj 1119 / poj 1523 SPF (典型例题 求割点 Tarjan 算法)
poj : http://poj.org/problem?id=1523 如果无向图中一个点 u 为割点 则u 或者是具有两个及以上子女的深度优先生成树的根,或者虽然不是一个根,但是它有一个子女 w, ...
- uva 315 Network(无向图求割点)
https://uva.onlinejudge.org/index.php?option=com_onlinejudge&Itemid=8&page=show_problem& ...
- poj 1523 SPF(tarjan求割点)
本文出自 http://blog.csdn.net/shuangde800 ------------------------------------------------------------ ...
- Tarjan求割点和桥
by szTom 前置知识 邻接表存储及遍历图 tarjan求强连通分量 割点 割点的定义 在一个无向图中,如果有一个顶点集合,删除这个顶点集合以及这个集合中所有顶点相关联的边以后,图的连通分量增多, ...
- Tarjan应用:求割点/桥/缩点/强连通分量/双连通分量/LCA(最近公共祖先)【转】【修改】
一.基本概念: 1.割点:若删掉某点后,原连通图分裂为多个子图,则称该点为割点. 2.割点集合:在一个无向连通图中,如果有一个顶点集合,删除这个顶点集合,以及这个集合中所有顶点相关联的边以后,原图变成 ...
- [学习笔记]tarjan求割点
都口胡了求割边,就顺便口胡求割点好了QAQ 的定义同求有向图强连通分量. 枚举当前点的所有邻接点: 1.如果某个邻接点未被访问过,则访问,并在回溯后更新 2.如果某个邻接点已被访问过,则更新 对于当前 ...
- tarjan算法求割点cojs 8
tarjan求割点:cojs 8. 备用交换机 ★★ 输入文件:gd.in 输出文件:gd.out 简单对比时间限制:1 s 内存限制:128 MB [问题描述] n个城市之间有通讯网 ...
- UESTC 900 方老师炸弹 --Tarjan求割点及删点后连通分量数
Tarjan算法. 1.若u为根,且度大于1,则为割点 2.若u不为根,如果low[v]>=dfn[u],则u为割点(出现重边时可能导致等号,要判重边) 3.若low[v]>dfn[u], ...
随机推荐
- POJ3013 Big Christmas Tree[转换 最短路]
Big Christmas Tree Time Limit: 3000MS Memory Limit: 131072K Total Submissions: 23387 Accepted: 5 ...
- USACO1.1Broken Necklace[环状DP作死]
题目描述 你有一条由N个红色的,白色的,或蓝色的珠子组成的项链(3<=N<=350),珠子是随意安排的. 这里是 n=29 的二个例子: 第一和第二个珠子在图片中已经被作记号. 图片 A ...
- Carcraft
魔兽登录系统 创建魔兽系统相关窗体: 登录窗体(frmLogin) 注册窗体(frmRegister) 主窗体 (frmMain) 实现魔兽登录系统: 登录的界面如下 实现思路: 1.创建一个 ...
- 社交化分享SDK for Unity
前言 社交化分享,即分享到社交网络. 本文主要记录的是在Unity集成社交化分享SDK,现主流的分享SDK有如下: 1.友盟社交化分享 for unity 2.ShareSDK分享 for unity ...
- 关于OAUTH2.0的极品好文
Web Server Flow: web ServerFlow是把oauth1.0的三个步骤缩略为两个步骤 首先这个是适合有server的第三方使用的. 1客户端http请求authorize 2服务 ...
- WAMP中phpMyAdmin登陆不了问题的解决方法
WAMP中phpMyAdmin登陆不了问题的解决方法
- S2结业考试的第一次测验
错题分析: 1:java中的错误处理是通过异常处理模型来实现的,那么异常处理模块能处理的错误是: A:运行时错误 B:逻辑错误 C:语法错误 D:内部错误 正确答案是:A 解析:运行时异常都是Runt ...
- ConcurrentHashMap是如何提高并发时的吞吐性能
为并发吞吐性能所做的优化 ConcurrentHashMap使用了一些技巧来获取高的并发性能,同时避免了锁.这些技巧包括: 为不同的Hash bucket(所谓hash bucket即不同范围的key ...
- 隐写技巧——利用JPEG文件格式隐藏payload
0x00 前言 继续对图片隐写技巧的学习,这次是对JPEG文件格式的学习和理解.同PNG文件的格式对比,JPEG文件相对简单,读取其中隐藏payload的方式大同小异,两者区别在于文件格式不同,可供利 ...
- StringBuffer and StringBuilder
As of release JDK 5, this class has been supplemented with an equivalent class designed for use by a ...
