攻防世界 reverse 进阶 1-4
1.dmd-50 suctf-2016
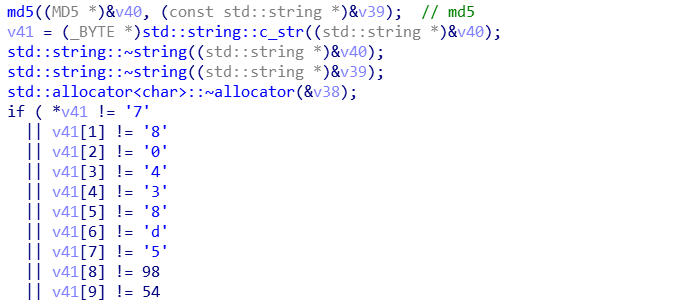
md5后比较,在线解md5得到:
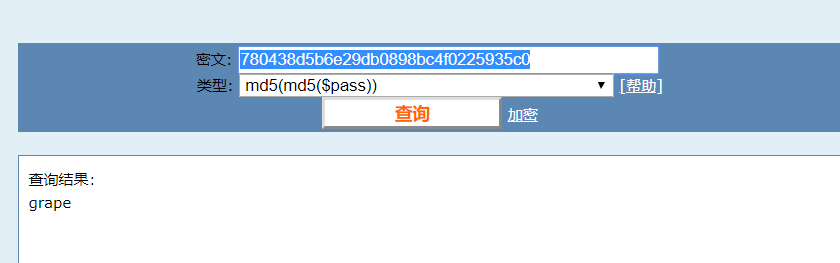
md5(md5($pass)),所以将grape再进行MD5

b781cbb29054db12f88f08c6e161c199
2.Shuffle SECCON-CTF-2014

硬编码:
SECCON{Welcome to the SECCON 2014 CTF!}
3.re2-cpp-is-awesome alexctf-2017
1 __int64 __fastcall main(int a1, char **a2, char **a3)
2 {
3 char *v3; // rbx
4 __int64 v4; // rax
5 __int64 v5; // rdx
6 __int64 v6; // rax
7 __int64 v7; // rdx
8 __int64 v8; // rdx
9 __int64 char_1; // rdx
10 __int64 s_char; // [rsp+10h] [rbp-60h]
11 char v12; // [rsp+20h] [rbp-50h]
12 char v13; // [rsp+4Fh] [rbp-21h]
13 __int64 v14; // [rsp+50h] [rbp-20h]
14 int k; // [rsp+5Ch] [rbp-14h]
15
16 if ( a1 != 2 )
17 {
18 v3 = *a2;
19 v4 = std::operator<<<std::char_traits<char>>(&std::cout, "Usage: ", a3);
20 v6 = std::operator<<<std::char_traits<char>>(v4, v3, v5);
21 std::operator<<<std::char_traits<char>>(v6, " flag\n", v7);
22 exit(0);
23 }
24 std::allocator<char>::allocator(&v13, a2, a3);
25 std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::basic_string(&v12, a2[1], &v13);
26 std::allocator<char>::~allocator(&v13);
27 k = 0;
28 for ( s_char = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::begin(&v12);
29 ;
30 sub_400D7A(&s_char) )
31 {
32 v14 = std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::end(&v12);
33 if ( !cmp_400D3D((__int64)&s_char, (__int64)&v14) )
34 break;
35 char_1 = *(unsigned __int8 *)sub_400D9A((__int64)&s_char);
36 if ( (_BYTE)char_1 != str_6020A0[dword_6020C0[k]] )// 关键比较处
37 error_400B56((__int64)&s_char, (__int64)&v14, char_1);// 输出失败
38 ++k;
39 }
40 success_400B73((__int64)&s_char, (__int64)&v14, v8);// 成功
41 std::__cxx11::basic_string<char,std::char_traits<char>,std::allocator<char>>::~basic_string(&v12);
42 return 0LL;
43 }
关键处,在一个字符串中取特定顺序的字符进行与输入比较
1 x='L3t_ME_T3ll_Y0u_S0m3th1ng_1mp0rtant_A_{FL4G}_W0nt_b3_3X4ctly_th4t_345y_t0_c4ptur3_H0wev3r_1T_w1ll_b3_C00l_1F_Y0u_g0t_1t'
2 x=list(x)
3 y=[ 36,
4 0,
5 5,
6 54,
7 101,
8 7,
9 39,
10 38,
11 45,
12 1,
13 3,
14 0,
15 13,
16 86,
17 1,
18 3,
19 101,
20 3,
21 45,
22 22,
23 2,
24 21,
25 3,
26 101,
27 0,
28 41,
29 68,
30 68,
31 1,
32 68,
33 43]
34 t=[]
35 for i in range(len(y)):
36 t.append(x[y[i]])
37
38 print(''.join(t))
ALEXCTF{W3_L0v3_C_W1th_CL45535}
4.crackme SHCTF-2017
查壳:
脱壳:
esp脱壳法:
单步执行pushfd后,转到esp
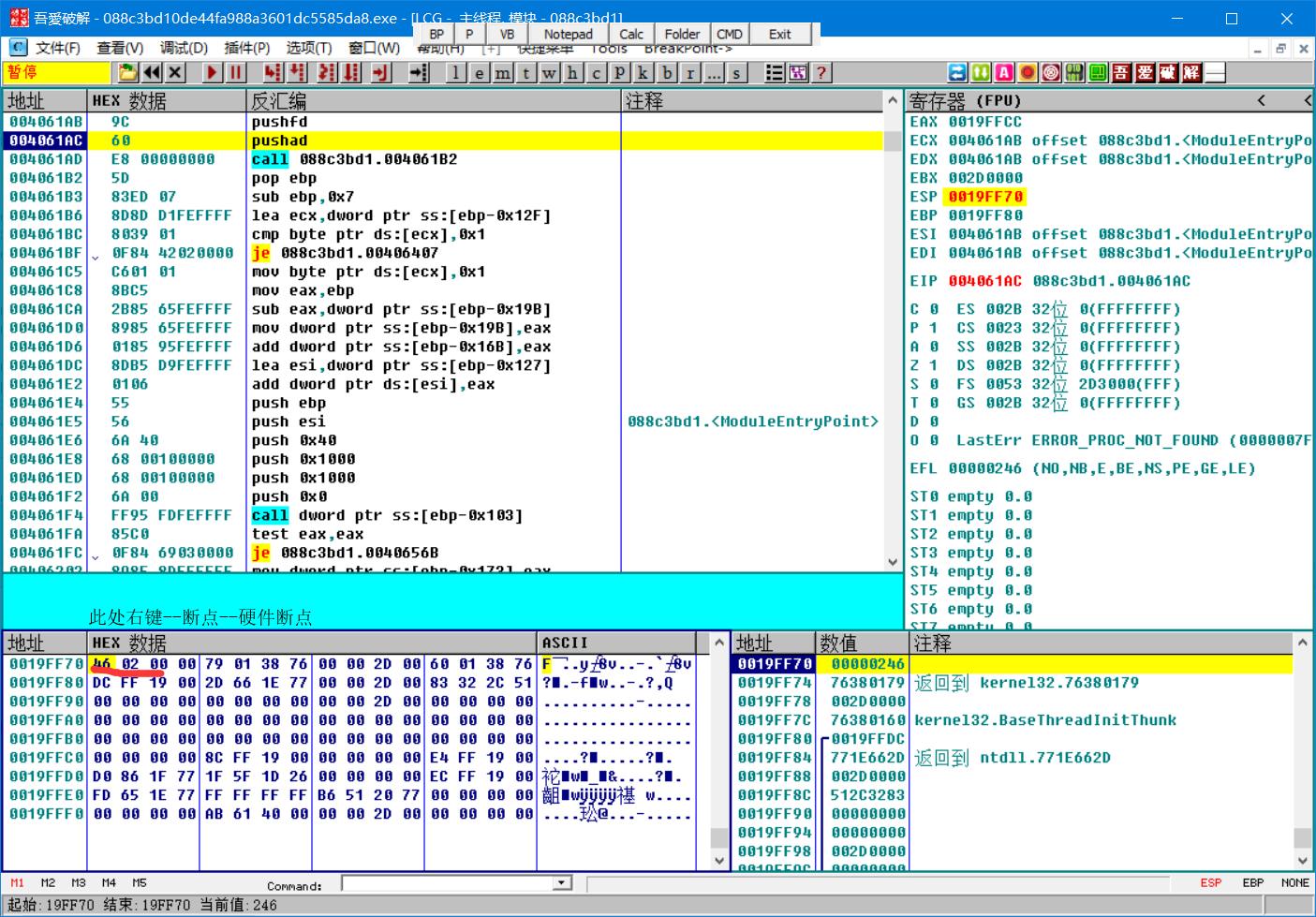
运行,断在一jmp处,单步来到一call,来到oep,在此处脱壳

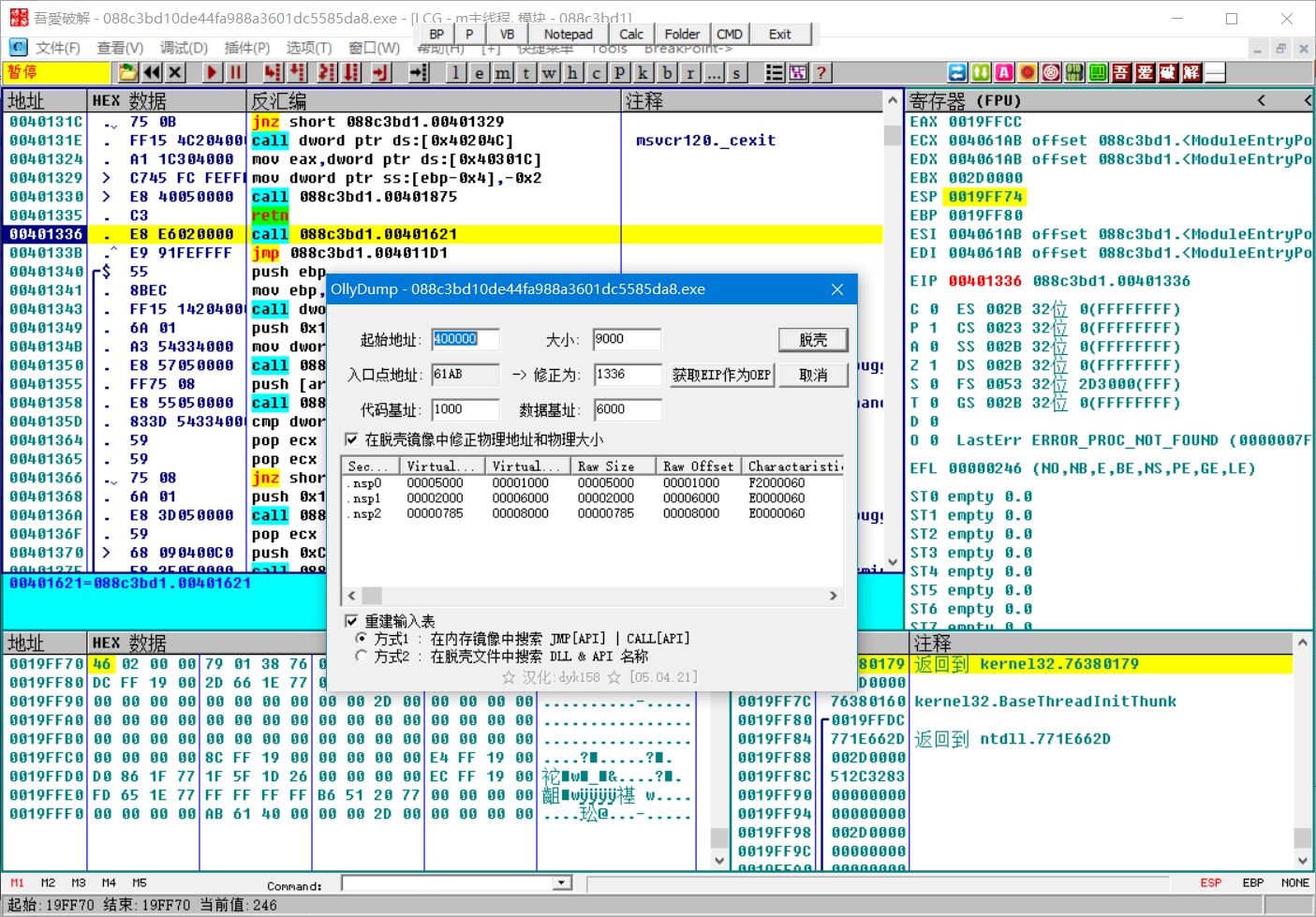
脱壳成功,可以在ida中直接分析,这里我直接在od中跟一下程序,通过定位提示字符串,发现程序流程很简单,就是一个简单的异或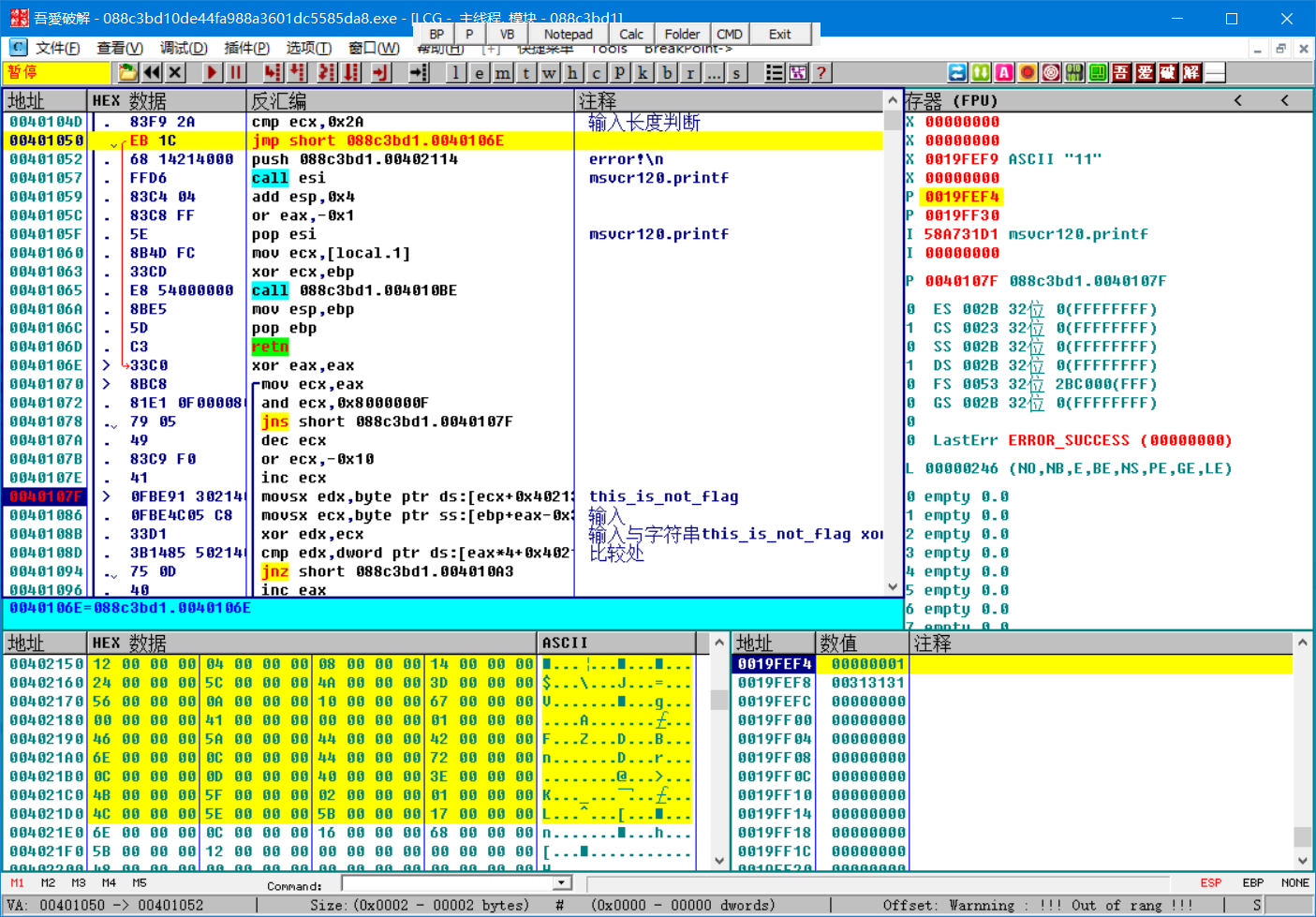
脚本:
1 x=[18,
2 4,
3 8,
4 20,
5 36,
6 92,
7 74,
8 61,
9 86,
10 10,
11 16,
12 103,
13 0,
14 65,
15 0,
16 1,
17 70,
18 90,
19 68,
20 66,
21 110,
22 12,
23 68,
24 114,
25 12,
26 13,
27 64,
28 62,
29 75,
30 95,
31 2,
32 1,
33 76,
34 94,
35 91,
36 23,
37 110,
38 12,
39 22,
40 104,
41 91,
42 18]
43 s=list('this_is_not_flag')
44 t=[]
45 for i in range(42):
46 t.append(chr(ord(s[i%16])^x[i]))
47 print(''.join(t))
flag{59b8ed8f-af22-11e7-bb4a-3cf862d1ee75}
攻防世界 reverse 进阶 1-4的更多相关文章
- 攻防世界 reverse 进阶 APK-逆向2
APK-逆向2 Hack-you-2014 (看名以为是安卓逆向呢0.0,搞错了吧) 程序是.net写的,直接祭出神器dnSpy 1 using System; 2 using System.Diag ...
- 攻防世界 reverse 进阶 10 Reverse Box
攻防世界中此题信息未给全,题目来源为[TWCTF-2016:Reverse] Reverse Box 网上有很多wp是使用gdb脚本,这里找到一个本地还原关键算法,然后再爆破的 https://www ...
- 攻防世界 reverse 进阶 9-re1-100
9.re1-100 1 if ( numRead ) 2 { 3 if ( childCheckDebugResult() ) 4 { 5 responseFalse(); 6 } 7 else if ...
- 攻防世界 reverse 进阶 8-The_Maya_Society Hack.lu-2017
8.The_Maya_Society Hack.lu-2017 在linux下将时间调整为2012-12-21,运行即可得到flag. 下面进行分析 1 signed __int64 __fastca ...
- 攻防世界 reverse 进阶 notsequence
notsequence RCTF-2015 关键就是两个check函数 1 signed int __cdecl check1_80486CD(int a1[]) 2 { 3 signed int ...
- 攻防世界 reverse 进阶 easyre-153
easyre-153 查壳: upx壳 脱壳: 1 int __cdecl main(int argc, const char **argv, const char **envp) 2 { 3 int ...
- 攻防世界 reverse 进阶 -gametime
19.gametime csaw-ctf-2016-quals 这是一个小游戏,挺有意思的 's'-->' ' 'x'-->'x' 'm'-->'m' 观察流程,发现检验函 ...
- 攻防世界 reverse 进阶 16-zorropub
16.zorropub nullcon-hackim-2016 (linux平台以后整理) https://github.com/ctfs/write-ups-2016/tree/master/nu ...
- 攻防世界 reverse 进阶 15-Reversing-x64Elf-100
15.Reversing-x64Elf-100 这题非常简单, 1 signed __int64 __fastcall sub_4006FD(__int64 a1) 2 { 3 signed int ...
- 攻防世界 reverse 进阶 12 ReverseMe-120
程序流程很清晰 1 int __cdecl main(int argc, const char **argv, const char **envp) 2 { 3 unsigned int v3; // ...
随机推荐
- IPC$入侵
一 唠叨一下: 网上关于ipc$入侵的文章可谓多如牛毛,而且也不乏优秀之作,攻击步骤甚至可以说已经成为经典的模式,因此也没人愿意再把这已经成为定式的东西拿出来摆弄. 二 什么是ipc$ IPC$(In ...
- Spring框架整合Mybatis项目
第一步:导入相关依赖jar包 <dependency> <groupId>org.mybatis</groupId> <artifactId>mybat ...
- Python+argparse+notebook
argparse"应用"于jupyter-notebook中 args.xx =======================>> args["xx" ...
- 关于Google Chrome的使用小技巧!
1 1 http://www.runoob.com/w3cnote/chrome-skip.html Chrome是Google公司开发的一个现代化的网页浏览器,作为三大浏览器之一 它搭载了被称为V8 ...
- How to build a sortable table in native js?
How to build a sortable table in native/vanilla js? H5 DnD https://developer.mozilla.org/zh-CN/docs/ ...
- React & Didact
React & Didact A DIY guide to build your own React https://github.com/pomber/didact https://gith ...
- array group by key javascript
array group by key javascript calendar Array.reduce https://developer.mozilla.org/en-US/docs/Web/Jav ...
- uniapp 创建简单的tabs
tabs组件 <template> <view class="tabs"> <view class="bar" :style=&q ...
- DeFi 热潮下,NGK将成为下一个财富密码
区块链正在脱虚向实,处于大规模落地,赋能实体产业的前夜,而在这个关键的关口,一个万亿市场的蓝海正在缓缓生成,成为区块链落地的急先锋,这个先锋便是DeFi. DeFi,即Decentralized Fi ...
- 你真的知道typeof null的结果为什么是‘object‘吗?
到目前为止,ECMAScript 标准中定义了8种数据类型,它们分别是Undefined.Null.Number.Boolean.String.Symbol.BigInt.Object. 为了判断变量 ...
