Lab 7-1
Analyze the malware found in the file Lab07-01.exe.
Questions and Short Answers
How does this program ensure that it continues running (achieves persistence) when the computer is restarted?
A: This program creates the service MalService to ensure that it runs every time the computer is started.
Why does this program use a mutex?
A: The program uses a mutex to ensure that only one copy of the program is running at a time.
What is a good host-based signature to use for detecting this program?
A: We could search for a mutex named HGL345 and for the service MalService.
What is a good network-based signature for detecting this malware?
A: The malware uses the user-agent Internet Explorer 8.0 and communicates with www.malwareanalysisbook.com.
What is the purpose of this program?
A: This program waits until midnight on January 1, 2100, and then sends many requests to http://www.malwareanalysisbook.com/, presumably to conduct a distributed denial-of-service (DDoS) attack against the site.
When will this program finish executing?
A: This program will never finish. It waits on a timer until the year 2100, and then creates 20 threads, each of which runs in an infinite loop.
Detailed Analysis
The first step in analyzing this malware in depth is to open it with IDA Pro or a similar tool to examine the imported function list. Many functions in the list provide little information because they are commonly imported by all Windows executables, but a few stand out. Specifically OpenSCManager and CreateService indicate that this malware probably creates a service to ensure that it will run when the computer is restarted.
The import of StartServiceCtrlDispatcherA hints that this file actually is a service. The calls to InternetOpen and InternetOpenUrl tell us that this program might connect to a URL to download content.
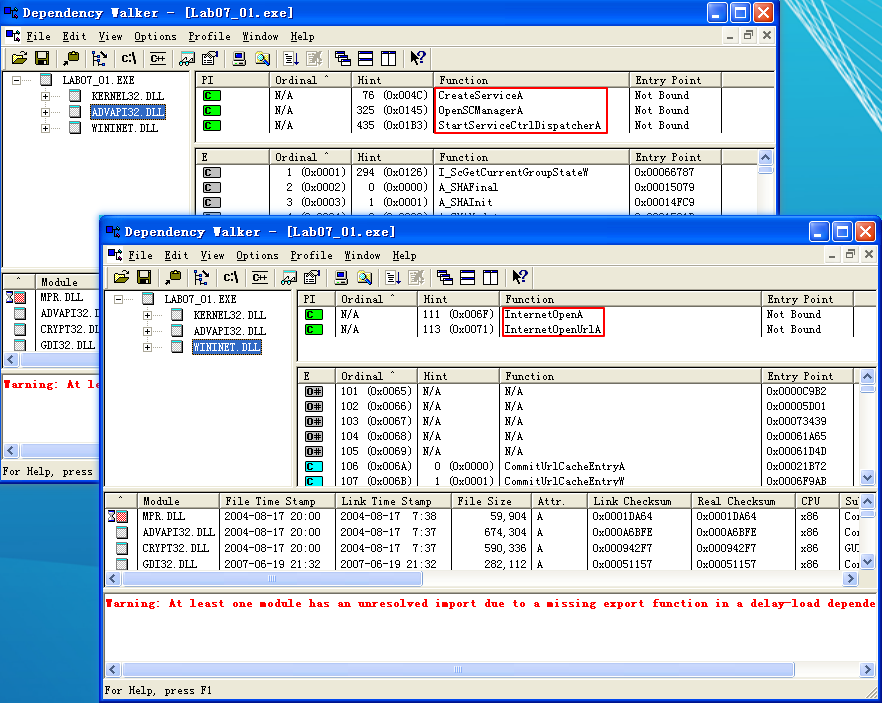
Next, we jump to the main function, which IDA Pro has identified and labeled *_wmain* at location 0x401000. A quick glance at the code shows that it’s short enough to analyze completely. The *_wmain* function calls only one other function, as shown in the following listing. If the code were longer, we would need to focus on only the most interesting function calls based on our review of the import table.
This code begins with a call to StartServiceCtrlDispatcherA at \({\color{red} 2 }\). According to the MSDN documentation, this function is used by a program to implement a service, and it is usually called immediately. The function specifies the service control function that the service control manager will call. Here, it specifies sub_401040 at \({\color{red} 1}\), which will be called after the call to StartServiceCtrlDispatcherA.
This first portion of code, including the call to StartServiceCtrlDispatcherA, is bookkeeping code that is necessary for programs that are run as services. It doesn’t tell us what the program is doing, but it does tell us that it expects to be run as a service.
Next, we examine the sub_401040 function, as shown in the following listing.
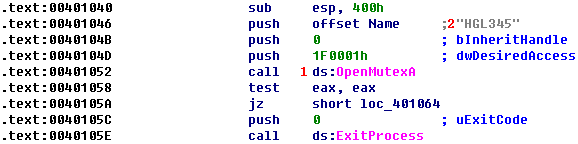
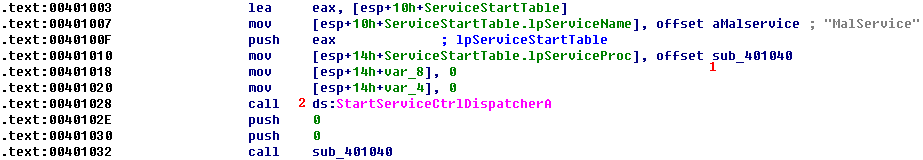
The first function call is to OpenMutexA at \({\color{red} 1}\). The only thing of note is that this call is attempting to obtain a handle to the named mutex HGL345 at \({\color{red}2}\). If the call fails, the program exits.
The next call is shown in the following listing.

This code creates a mutex at \({\color{red}1}\) named HGL345 \({\color{red} 2 }\). The combination of these two mutex calls is designed to ensure that only one copy of this executable is running on a system at any given time. If a copy was already running, then the first call to OpenMutexA would have been successful, and the program would have exited.
Next, the code calls OpenSCManager, which opens a handle to the service control manager so that the program can add or modify services. The next call is to the GetModuleFileName function, which returns the full pathname to the currently running executable or a loaded DLL. The first parameter(hModule) is a handle to the module for which the name should be retrieved, or it is NULL to get the full pathname of the executable.
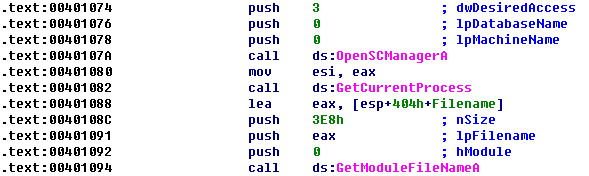
The full pathname is used by CreateServiceA to create a new service. The CreateServiceA call has many parameters, but the key ones are noted in the following listing.

The key CreateServiceA parameters are BinaryPathName at \({\color{red}1}\), dwStartType at \({\color{red}2}\), and dwServiceType at \({\color{red}3}\). The binary path to the executable is the same as the path to the currently running executable retrieved by the GetModuleFileName call. The GetModuleFileName call is needed because the malware may not know its directory or filename. By dynamically obtaining this information, it can install the service no matter which executable is called or where it is stored.
The MSDN documentation lists valid entries for the dwServiceType and dwStartType parameters. For dwStartType, the possibilities are SERVICE_BOOT_START (0x00), SERVICE_SYSTEM_START (0x01), SERVICE_AUTO_START (0x02), SERVICE_DEMAND_START (0x03), and SERVICE_DISABLED (0x04). The malware passed 0x02, which corresponds to SERVICE_AUTO_START, indicating that the service runs automatically on system startup.
A lot of code manipulates time-related structures. IDA Pro has labeled a structure to be a SYSTEMTIME structure, which is one of several Windows time structures. According to MSDN, the SYSTEMTIME structure has separate fields for the second, minute, hour, day, and so on, for use in specifying time. In this case, all values are first set to 0, and then the value for the year is set to 0x0834 at \({\color{red}1}\), or 2100 in decimal. This time represents midnight on January 1, 2100. The program then calls SystemTimeToFileTime between time formats.
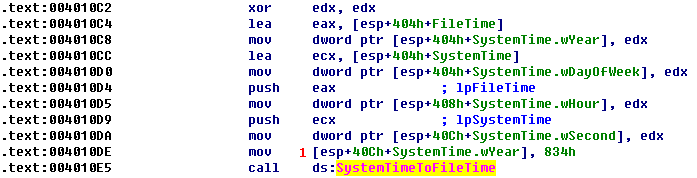
注:我们可以通过 IDA 的 Imports 找到 SystemTimeToFileTime,然后使用下图方法定位到上图:

Next, the program calls CreateWaitableTimer, SetWaitableTimer, and WaitForSingleObject. The most important argument for our purposes is the lpDueTime argument to SetWaitableTimer. The argument is the FileTime returned by SystemTimeToFileTime, as shown in the preceding listing. The code then uses WaitForSingleObject to wait until January 1, 2100.
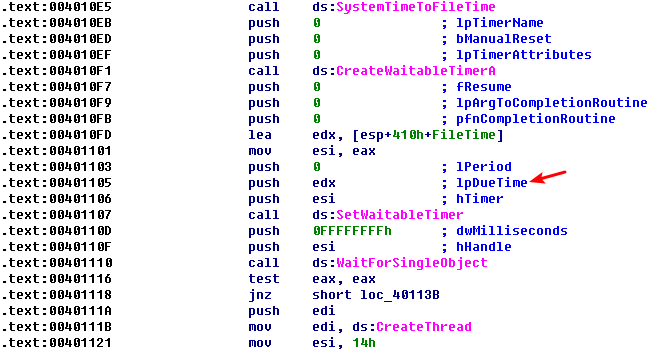
The code then loops 20 (0x14) times, as shown in the following listing.
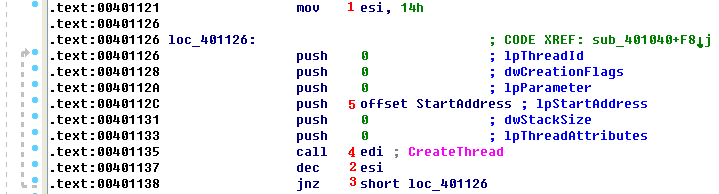
Here, ESI is set at \({\color{red}1}\) as the counter to 0x14 (20 in decimal). At the end of the loop, ESI is decremented at \({\color{red}2}\), and when it hits zero at \({\color{red}3}\), the loop exits. A call to CreateThread at \({\color{red}4}\) has several parameters, but only one is important to us. The lpStartAddress parameter at \({\color{red}5}\) tells us which function will be used as the start address for the thread—labeled StartAddress in this case.
We double-click StartAddress. We see that this function calls InternetOpen to initialize a connection to the Internet, and then calls InternetOpenUrlA from within a loop, which is shown in the following code.
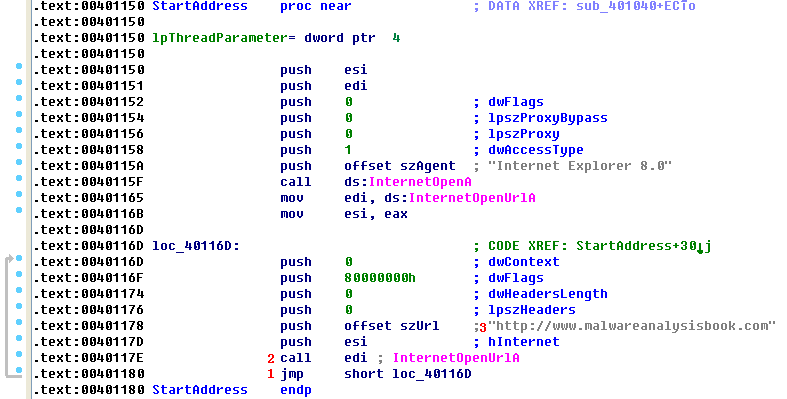
The jmp instruction at the end of the loop at \({\color{red} 1 }\) is an unconditional jump, which means that the code will never end; it will call InternetOpenUrlA \({\color{red}2}\) and download the home page of www.malwareanalysisbook.com \({\color{red}3}\) forever. And because CreateThread is called 20 times, 20 threads will call InternetOpenUrlA forever. Clearly, this malware is designed to launch a DDoS attack by installing itself on many machines. If all of the infected machines connect to the server at the same time (January 1, 2100), they may overload the server and make it impossible to access the site.
In summary, this malware uses mutexes to ensure that only one copy is running at a time, creates a service to ensure that it runs again when the system reboots, waits until January 1, 2100, and then continues to download www.malwareanalysisbook.com indefinitely.
Note that this malware doesn’t perform all of the functions required of a service. Normally, a service must implement functions to be stopped or paused, and it must change its status to let the user and OS know that the service has started. Because this malware does none of this, its service’s status will always display START_PENDING, and the service cannot be stopped while it is running. Malware often implements just enough functionality to achieve the author’s goals, without bothering to implement the entire functionality required by the specification.
NOTE
If you ran this lab without a virtual machine, remove the malware by entering
sc delete Malserviceat the command line, and then deleting the file itself.
Preference
Lab 7-1的更多相关文章
- MIT 6.828 JOS学习笔记18. Lab 3.2 Part B: Page Faults, Breakpoints Exceptions, and System Calls
现在你的操作系统内核已经具备一定的异常处理能力了,在这部分实验中,我们将会进一步完善它,使它能够处理不同类型的中断/异常. Handling Page Fault 缺页中断是一个非常重要的中断,因为我 ...
- MIT 6.828 JOS学习笔记17. Lab 3.1 Part A User Environments
Introduction 在这个实验中,我们将实现操作系统的一些基本功能,来实现用户环境下的进程的正常运行.你将会加强JOS内核的功能,为它增添一些重要的数据结构,用来记录用户进程环境的一些信息:创建 ...
- MIT 6.828 JOS学习笔记16. Lab 2.2
Part 3 Kernel Address Space JOS把32位线性地址虚拟空间划分成两个部分.其中用户环境(进程运行环境)通常占据低地址的那部分,叫用户地址空间.而操作系统内核总是占据高地址的 ...
- MIT 6.828 JOS学习笔记15. Lab 2.1
Lab 2: Memory Management lab2中多出来的几个文件: inc/memlayout.h kern/pmap.c kern/pmap.h kern/kclock.h kern/k ...
- MIT 6.828 JOS学习笔记10. Lab 1 Part 3: The kernel
Lab 1 Part 3: The kernel 现在我们将开始具体讨论一下JOS内核了.就像boot loader一样,内核开始的时候也是一些汇编语句,用于设置一些东西,来保证C语言的程序能够正确的 ...
- MIT 6.828 JOS学习笔记7. Lab 1 Part 2.2: The Boot Loader
Lab 1 Part 2 The Boot Loader Loading the Kernel 我们现在可以进一步的讨论一下boot loader中的C语言的部分,即boot/main.c.但是在我们 ...
- python opencv 利用Lab空间把春天的场景改为秋天
前一段时间实现了Reinhard颜色迁移算法,感觉挺有意思的,然后在代码上随意做了一些更改,有了一些发现,把Lab通道的a通道值改为127左右,可以将绿色改为黄色,而对其他颜色的改动非常小,因此可以将 ...
- Acadia Lab 228 + Lab 222
又是一对串烧实验,布好线后非常方便就可以一起完成. 连线方案一模一样: Lab 228 数码管骰子 核心代码如下: def loop() : global cnt global btn_read,se ...
- Acadia Lab 203 + Lab 231
在做完 Lab 6 之后,惊觉选做实验缺口很大,于是遍历了一遍夏任务,找到了一条最省力的路线. 做完 Lab 6 的连线不用拆,可以接下来做以下两个实验: Lab 203 网络时钟 核心代码如下: v ...
- GJM : 【技术干货】给The Lab Renderer for Unity中地形添加阴影
感谢您的阅读.喜欢的.有用的就请大哥大嫂们高抬贵手"推荐一下"吧!你的精神支持是博主强大的写作动力以及转载收藏动力.欢迎转载! 版权声明:本文原创发表于 [请点击连接前往] ,未经 ...
随机推荐
- linux 通过pid 寻找程序路径的最简单命令(pwdx)
在linux实际操作命令中,查看pid的方式有很多种,通过pid找程序路径的方式也有好几个,但是可能大家都忽略的一个很简单也是很实用的命令:pwdx. 比如要查找某个java编写的程序运行情况可通过j ...
- Numpy float64和Python float是一样的
>>> numpy.float64(5.9975).hex() # 函数用于将10进制整数转换成16进制,以字符串形式表示. '0x1.7fd70a3d70a3dp+2' >& ...
- [js]nodejs初探http/url/fs模块
难怪我没学会, 因为我的套路有问题. 错误点, 1,大而全 2,不注重思路 学习要领: 1, 小而精 2, 重思路(总结) nodejs特点: 1.node提供了js的运行环境, 一般将node运行在 ...
- 9个用来爬取网络站点的 Python 库
上期入口:10个不到500行代码的超牛Python练手项目 1️⃣Scrapy 一个开源和协作框架,用于从网站中提取所需的数据. 以快速,简单,可扩展的方式. 官网:https://scrapy.or ...
- [LeetCode] 236. Lowest Common Ancestor of a Binary Tree_ Medium tag: DFS, Divide and conquer
Given a binary tree, find the lowest common ancestor (LCA) of two given nodes in the tree. According ...
- 对stm32寄存器的理解(个人理解,大神轻喷)
学习了stm32有一年了,今天想来写写自己对寄存器的理解,帮助那些有志学习stm32的朋友们少走一些弯路. ---------------------------------------------- ...
- iPhone IOS10安装APP没提示连接网络(无法联网)的解决办法
iPhone升级ios10之后,遇到如标题所述问题时: 1.退出APP,设置-蜂窝移动网络-无线局域网助理-开启 2.进入APP,这时候就回提示连接网络了. 提醒: 数据流量有限的朋友,平时请关闭&q ...
- mysql----------mysql5.7.11导入sql文件时报错This function has none of DETERMINISTIC, NO SQL, or READS SQL DATA in its declaration and binary logging is enabled
1.导入sql文件出现如下错误. [Err] 1418 - This function has none of DETERMINISTIC, NO SQL, or READS SQL DATA in ...
- 雾霾天出行,如何精确避开“雷区”?2016 SODA数据侠十强
(2016年参加了上海 SODA 竞赛,进入前十,最终获得上海市的两个奖项.) ▍跟踪雾霾,仅靠零星的监测点数据怎么行? 如果雾霾短期内没有办法彻底根治,我们可以做什么,把环境污染物对人的影响尽可能降 ...
- U-boot2010.06移植--阶段一
2011-02-24 23:14:57 我今天的移植将分如下3步.加上写记录文档,预计时间3小时. 一,不改变源码,完成编译. 二,修改源码,搭建一个U-boot的框架,完成编译. 三,修改源码,完成 ...
