Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库之后的切换到指定的工作空间
不多说,直接上干货!
为什么要这么做?
答: 方便我们将扫描不同的目标或目标的不同段,进行归类。为了更好的后续工作!
前期博客
Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库
注意啦:
我这里,是已经切换到了自定义的PostgreSQL数据库postgres,不是默认的PostgreSQL数据库msf。
那么,工作空间是属于数据库里的。
也就是说,下面,我是在自定义数据库postgres里操作的。
可以看到,默认的工作空间是default
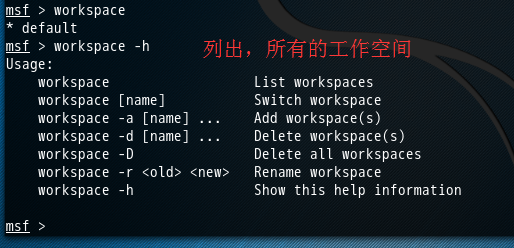
msf > workspace
* default ( 默认的)
msf > workspace -h
Usage:
workspace List workspaces
workspace [name] Switch workspace
workspace -a [name] ... Add workspace(s) (创建)
workspace -d [name] ... Delete workspace(s) (删除)
workspace -D Delete all workspaces
workspace -r <old> <new> Rename workspace (重命名)
workspace -h Show this help information msf >
好的,然后呢,我现在带领大家,来创建自定义的工作空间,
然后,再Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库之后的切换到指定的工作空间
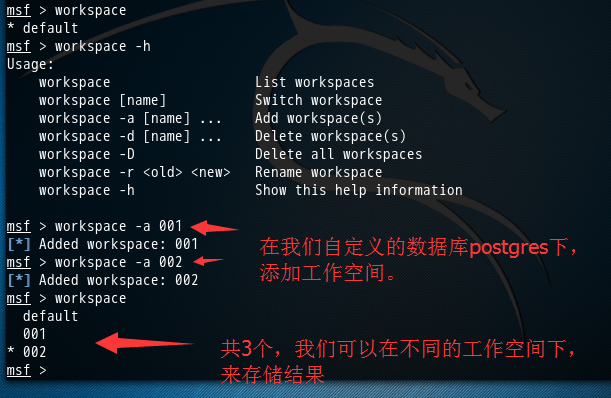
msf > workspace
* default
msf > workspace -h
Usage:
workspace List workspaces
workspace [name] Switch workspace
workspace -a [name] ... Add workspace(s)
workspace -d [name] ... Delete workspace(s)
workspace -D Delete all workspaces
workspace -r <old> <new> Rename workspace
workspace -h Show this help information msf > workspace -a
[*] Added workspace:
msf > workspace -a
[*] Added workspace:
msf > workspace
default *
msf >

msf > workspace
default *
msf > workspace
[*] Workspace:
msf >
成功链接到我们刚自定义创建好的数据库postgres后,可以用db_nmap命令,这个命令能够在MSF终端中运行db_nmap,并自动将扫描后的结果,存储到对应的数据库下的工作空间下。(我这里是存储在自定义数据库postgres的工作空间001下)
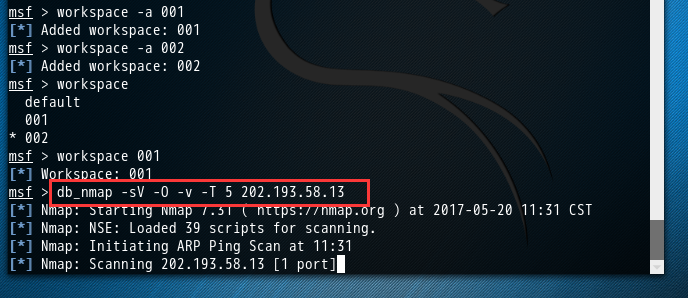
msf > workspace 001
[*] Workspace: 001
msf > db_nmap -sV -O -v -T 5 202.193.58.13
[*] Nmap: Starting Nmap 7.31 ( https://nmap.org ) at 2017-05-20 11:31 CST
[*] Nmap: NSE: Loaded 39 scripts for scanning.
[*] Nmap: Initiating ARP Ping Scan at 11:31
[*] Nmap: Scanning 202.193.58.13 [1 port]
[*] Nmap: Completed ARP Ping Scan at 11:31, 0.01s elapsed (1 total hosts)
[*] Nmap: Initiating Parallel DNS resolution of 1 host. at 11:31
[*] Nmap: Completed Parallel DNS resolution of 1 host. at 11:31, 0.02s elapsed
[*] Nmap: Initiating SYN Stealth Scan at 11:31
[*] Nmap: Scanning 13.58.193.202.in-addr.arpa (202.193.58.13) [1000 ports]
[*] Nmap: Discovered open port 139/tcp on 202.193.58.13
[*] Nmap: Discovered open port 22/tcp on 202.193.58.13
[*] Nmap: Discovered open port 21/tcp on 202.193.58.13
[*] Nmap: Discovered open port 445/tcp on 202.193.58.13
[*] Nmap: Discovered open port 23/tcp on 202.193.58.13
[*] Nmap: Discovered open port 80/tcp on 202.193.58.13
[*] Nmap: Discovered open port 5900/tcp on 202.193.58.13
[*] Nmap: Discovered open port 3306/tcp on 202.193.58.13
[*] Nmap: Discovered open port 25/tcp on 202.193.58.13
[*] Nmap: Discovered open port 53/tcp on 202.193.58.13
[*] Nmap: Discovered open port 111/tcp on 202.193.58.13
[*] Nmap: Discovered open port 8180/tcp on 202.193.58.13
[*] Nmap: Discovered open port 5432/tcp on 202.193.58.13
[*] Nmap: Discovered open port 512/tcp on 202.193.58.13
[*] Nmap: Discovered open port 8009/tcp on 202.193.58.13
[*] Nmap: Discovered open port 514/tcp on 202.193.58.13
[*] Nmap: Discovered open port 2121/tcp on 202.193.58.13
[*] Nmap: Discovered open port 6000/tcp on 202.193.58.13
[*] Nmap: Discovered open port 6667/tcp on 202.193.58.13
[*] Nmap: Discovered open port 513/tcp on 202.193.58.13
[*] Nmap: Discovered open port 1099/tcp on 202.193.58.13
[*] Nmap: Discovered open port 2049/tcp on 202.193.58.13
[*] Nmap: Discovered open port 1524/tcp on 202.193.58.13
[*] Nmap: Completed SYN Stealth Scan at 11:31, 0.99s elapsed (1000 total ports)
[*] Nmap: Initiating Service scan at 11:31
[*] Nmap: Scanning 23 services on 13.58.193.202.in-addr.arpa (202.193.58.13)
[*] Nmap: Completed Service scan at 11:32, 16.06s elapsed (23 services on 1 host)
[*] Nmap: Initiating OS detection (try #1) against 13.58.193.202.in-addr.arpa (202.193.58.13)
[*] Nmap: Retrying OS detection (try #2) against 13.58.193.202.in-addr.arpa (202.193.58.13)
[*] Nmap: NSE: Script scanning 202.193.58.13.
[*] Nmap: Initiating NSE at 11:32
[*] Nmap: Completed NSE at 11:32, 2.43s elapsed
[*] Nmap: Initiating NSE at 11:32
[*] Nmap: Completed NSE at 11:32, 1.13s elapsed
[*] Nmap: Nmap scan report for 13.58.193.202.in-addr.arpa (202.193.58.13)
[*] Nmap: Host is up (0.0022s latency).
[*] Nmap: Not shown: 977 closed ports
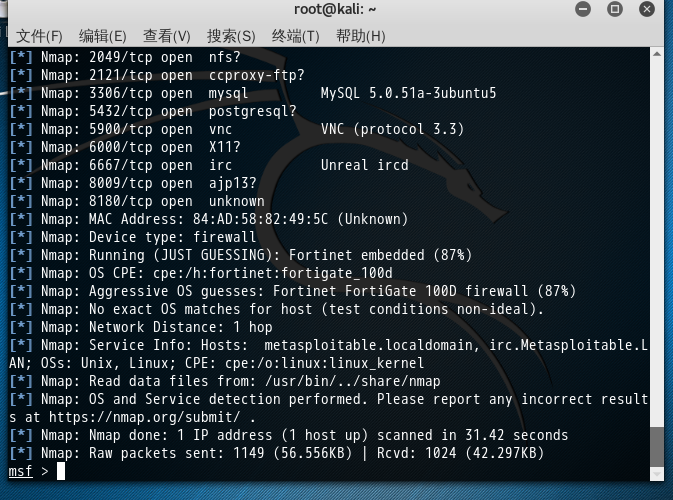
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 21/tcp open ftp vsftpd 2.3.4
[*] Nmap: 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
[*] Nmap: 23/tcp open telnet Linux telnetd
[*] Nmap: 25/tcp open smtp Postfix smtpd
[*] Nmap: 53/tcp open domain?
[*] Nmap: 80/tcp open http?
[*] Nmap: 111/tcp open rpcbind?
[*] Nmap: 139/tcp open netbios-ssn?
[*] Nmap: 445/tcp open microsoft-ds?
[*] Nmap: 512/tcp open exec netkit-rsh rexecd
[*] Nmap: 513/tcp open login?
[*] Nmap: 514/tcp open shell Netkit rshd
[*] Nmap: 1099/tcp open rmiregistry?
[*] Nmap: 1524/tcp open shell Metasploitable root shell
[*] Nmap: 2049/tcp open nfs?
[*] Nmap: 2121/tcp open ccproxy-ftp?
[*] Nmap: 3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
[*] Nmap: 5432/tcp open postgresql?
[*] Nmap: 5900/tcp open vnc VNC (protocol 3.3)
[*] Nmap: 6000/tcp open X11?
[*] Nmap: 6667/tcp open irc Unreal ircd
[*] Nmap: 8009/tcp open ajp13?
[*] Nmap: 8180/tcp open unknown
[*] Nmap: MAC Address: 84:AD:58:82:49:5C (Unknown)
[*] Nmap: Device type: firewall
[*] Nmap: Running (JUST GUESSING): Fortinet embedded (87%)
[*] Nmap: OS CPE: cpe:/h:fortinet:fortigate_100d
[*] Nmap: Aggressive OS guesses: Fortinet FortiGate 100D firewall (87%)
[*] Nmap: No exact OS matches for host (test conditions non-ideal).
[*] Nmap: Network Distance: 1 hop
[*] Nmap: Service Info: Hosts: metasploitable.localdomain, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
[*] Nmap: Read data files from: /usr/bin/../share/nmap
[*] Nmap: OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 31.42 seconds
[*] Nmap: Raw packets sent: 1149 (56.556KB) | Rcvd: 1024 (42.297KB)
msf >
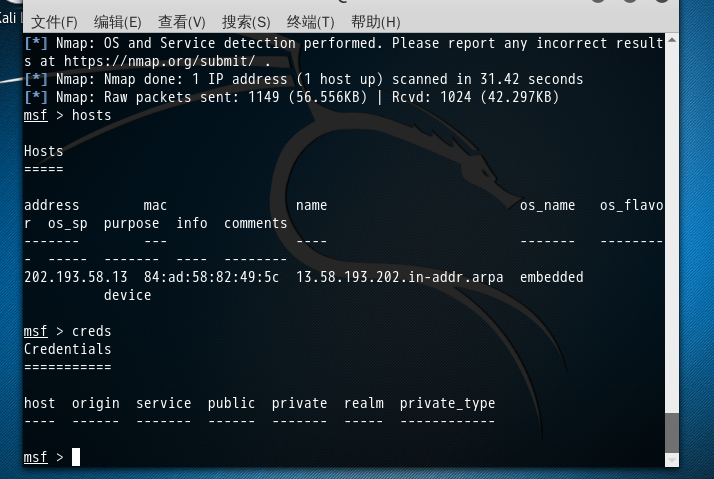
msf > hosts Hosts
===== address mac name os_name os_flavor os_sp purpose info comments
------- --- ---- ------- --------- ----- ------- ---- --------
202.193.58.13 84:ad:58:82:49:5c 13.58.193.202.in-addr.arpa embedded device msf > creds
Credentials
=========== host origin service public private realm private_type
---- ------ ------- ------ ------- ----- ------------ msf >
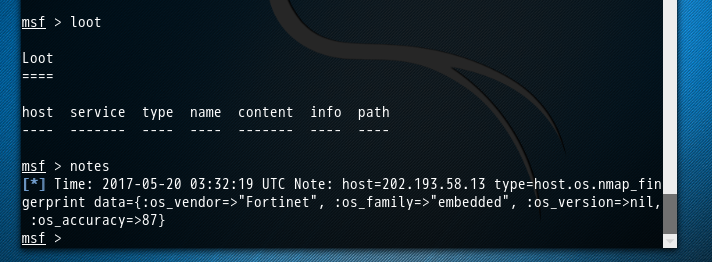
msf > loot Loot
==== host service type name content info path
---- ------- ---- ---- ------- ---- ---- msf > notes
[*] Time: 2017-05-20 03:32:19 UTC Note: host=202.193.58.13 type=host.os.nmap_fingerprint data={:os_vendor=>"Fortinet", :os_family=>"embedded", :os_version=>nil, :os_accuracy=>87}
msf >
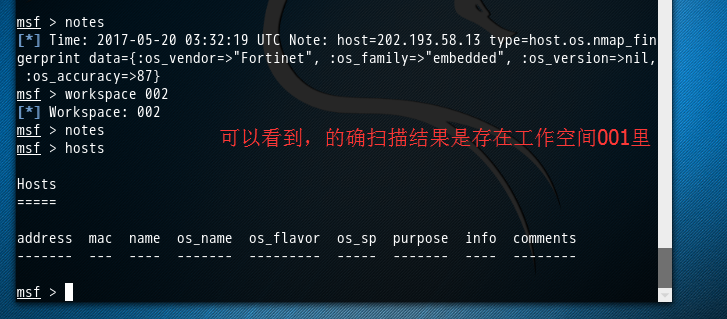
msf > notes
[*] Time: -- :: UTC Note: host=202.193.58.13 type=host.os.nmap_fingerprint data={:os_vendor=>"Fortinet", :os_family=>"embedded", :os_version=>nil, :os_accuracy=>}
msf > workspace
[*] Workspace:
msf > notes
msf > hosts Hosts
===== address mac name os_name os_flavor os_sp purpose info comments
------- --- ---- ------- --------- ----- ------- ---- -------- msf >
Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库之后的切换到指定的工作空间的更多相关文章
- MetaSploit攻击实例讲解------工具Meterpreter常用功能介绍(kali linux 2016.2(rolling))(详细)
不多说,直接上干货! 说在前面的话 注意啦:Meterpreter的命令非常之多,本篇博客下面给出了所有,大家可以去看看.给出了详细的中文 由于篇幅原因,我只使用如下较常用的命令. 这篇博客,利用下面 ...
- MetaSploit攻击实例讲解------Metasploit自动化攻击(包括kali linux 2016.2(rolling) 和 BT5)
不多说,直接上干货! 前期博客 Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库 Kali linux 2016.2(Ro ...
- MetaSploit攻击实例讲解------终端下PostgreSQL数据库的使用(包括kali linux 2016.2(rolling) 和 BT5)
不多说,直接上干货! 配置msf连接postgresql数据库 我这里是使用kali linux 2016.2(rolling) 用过的博友们都知道,已经预安装好了PostgreSQL. 1. p ...
- MetaSploit攻击实例讲解------社会工程学set攻击(kali linux 2016.2(rolling))(详细)
不多说,直接上干货! 首先,如果你是用的BT5,则set的配置文件是在 /pentest/exploits/set/set_config下. APACHE_SERVER=ONSELF_SIGNED_A ...
- MetaSploit攻击实例讲解------攻击445端口漏洞(kali linux 2016.2(rolling))(详细)
不多说,直接上干货! 大家,相信最近的这个事件,对于445端口已经是非常的小心了.勒索病毒 445端口是一个毁誉参半的端口,有了它我们可以在局域网中轻松访问各种共享文件夹或共享打印机,但也正是因为有了 ...
- Kali linux 2016.2 的 plyload模块之meterpreter plyload详解
不多说,直接上干货! 前期博客 Kali linux 2016.2(Rolling)中的payloads模块详解 当利用成功后尝试运行一个进程,它将在系统进程列表里显示,即使在木马中尝试执行系统命令, ...
- Kali linux 2016.2(Rolling)里Metasploit的数据库
为什么要在Metasploit里提及到数据库? 大家都知道,这么多信息,我怎样才能把它们整理好并保存起来?怎么展现给老大看,最后怎么体现在要提交的渗透测试报告中呢? 你的担忧真的很有必要,因为啊, ...
- Kali linux 2016.2(Rolling)里安装OpenVAS
不多说,直接上干货! 本博文,是在Kali 2.0 linux里,安装OpenVAS. 前言 OpenVAS是一款开放式的漏洞评估工具,主要用来检测目标网络或主机的安全性.与安全焦点的X-Scan工具 ...
- Kali linux 2016.2(Rolling)中的Metasploit如何更新与目录结构初步认识
如何更新MSF 1.Windows平台 方法1: 运行msfupdate.bat 在msfconsole里执行命令svn update 或者 方法2: 2.unix/linux平台 方法1: 运行m ...
随机推荐
- FZU_Problem 2168 防守阵地 I
Problem 2168 防守阵地 I Accept: 128 Submit: 392 Time Limit: 3000 mSec Memory Limit : 32768 KB Problem De ...
- linux高级技巧:heartbeat+lvs(三)
之前我们把LVS和heartbeat都单独进行了測试,是时候进行合并了 1.LVS+heartbeat: 首先显示我们的控制台: 让这两个 ...
- Git-删除本地文件夹的repository(本地仓库)
安装git软件后.有些文件夹里会出现带有?的图标,右键菜单上会有"Git-Sync"或者"Git-Commit"等命令:正常的应该是"Git-Clon ...
- [jzoj 6084] [GDOI2019模拟2019.3.25] 礼物 [luogu 4916] 魔力环 解题报告(莫比乌斯反演+生成函数)
题目链接: https://jzoj.net/senior/#main/show/6084 https://www.luogu.org/problemnew/show/P4916 题目: 题解: 注: ...
- shiro什么时候会进入doGetAuthorizationInfo(PrincipalCollection principals)
shiro会进入授权方法一共有三种情况!(注解.标签.代码) 1.subject.hasRole(“admin”) 或 subject.isPermitted(“admin”):自己去调用这个是否有什 ...
- etxjs
序言 编辑 功能丰富,无人能出其右. 无论是界面之美,还是功能之强,ext的表格控件都高居榜首. 单选行,多选行,高亮显示选中的行,拖拽改变列宽度,按列排序,这些基本功能ExtJS轻量级实现. 自动生 ...
- SparkShuffle调优原理和最佳实践
在网络层,互联网提供所有应用程序都要使用的两种类型的服务,尽管目前理解这些服务的细节并不重要,但在所有TCP/IP概述中,都不能忽略他们: 无连接分组交付服务(Connectionless Packe ...
- layui(弹出层)
首先引入文件 layui.css jquery.min.js layui.js 弹出层 data-method 后面的属性控制是什么弹窗,在js中写方法 <div class="sit ...
- 「JavaSE 重新出发」02.02 引用数据类型
引用(复合)数据类型 1. 枚举类型 例: 枚举类型 Size 的声明: enum Size { SMALL, MEDIUM, LARGE, EXTRA_LARGE }; 声明 Size 类型变量: ...
- 百度蜘蛛IP地址到底代表什么含义?
百度蜘蛛IP地址到底代表什么含义,是不是不同的ip地址所代表的含义不一样呢?对权重和抓取是否有影响?哪些是无效的蜘蛛,哪些是站长工具的蜘蛛,那些又是百度自己真正的蜘蛛?百度蜘蛛,是百度搜索引擎的一个自 ...
