【译】x86程序员手册19-6.3.2数据访问的约束
6.3.2 Restricting Access to Data 数据访问的约束
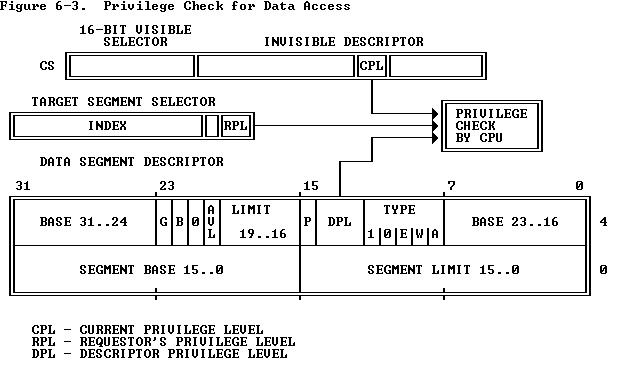
To address operands in memory, an 80386 program must load the selector of a data segment into a data-segment register (DS, ES, FS, GS, SS). The processor automatically evaluates access to a data segment by comparing privilege levels. The evaluation is performed at the time a selector for the descriptor of the target segment is loaded into the data-segment register. As Figure 6-3 shows, three different privilege levels enter into this type of privilege check:
对于内存的地址操作,80386的程序必须将一个数据段的选择子装入数据段寄存器(DS、ES、FS、GS、SS)。处理器通过比较特权级别自动评估对数据段的访问。当目的段的选择子被装入到数据段寄存器时评估被执行。正如图6-3所示,三个不同的特权级别参与这种特权检验:
- The CPL (current privilege level). 当前特权级别(CPL)
- The RPL (requestor's privilege level) of the selector used to specify the target segment.
用来指定目的段的选择子的需求特权级别(RPL)。
- The DPL of the descriptor of the target segment.
目的段描述符的特权级别(DPL)。
Instructions may load a data-segment register (and subsequently use the target segment) only if the DPL of the target segment is numerically greater than or equal to the maximum of the CPL and the selector's RPL. In other words, a procedure can only access data that is at the same or less privileged level.
仅当目的段的DPL数值大于或等于CPL和RPL中的最大值时,指令才能装入数据段寄存器。换句话说,一个程序仅可以访问同级或低特权级的数据。
The addressable domain of a task varies as CPL changes. When CPL is zero, data segments at all privilege levels are accessible; when CPL is one, only data segments at privilege levels one through three are accessible; when CPL is three, only data segments at privilege level three are accessible. This property of the 80386 can be used, for example, to prevent applications procedures from reading or changing tables of the operating system.
当CPL被修改后,任务的可寻址域也跟着变化。当CPL是0时,所有特权级的数据段都可访问;当CPL是1时,仅特权级别为1到3的数据段可访问;当CPL是3时,仅有特权级别是3的数据段可访问。80386的这些属性可以在如下情况中使用,例如,阻止应用程序读取或修改操作系统。
6.3.2.1 Accessing Data in Code Segments 访问代码段数据
Less common than the use of data segments is the use of code segments to store data. Code segments may legitimately hold constants; it is not possible to write to a segment described as a code segment.
相比使用数据段而言,很少使用代码段存储数据。代码段包含静态变量是合理的;向代码段写入数值是不可能的。
The following methods of accessing data in code segments are possible:
下面访问代码段的方法是可能的:
- Load a data-segment register with a selector of a nonconforming, readable, executable segment.
使用一个非一致性、可读的、可执行的段的选择子装入数据段寄存器。
- Load a data-segment register with a selector of a conforming, readable, executable segment.
使用一致的、可读的、可执行的段的选择子装入数据段寄存器。
- Use a CS override prefix to read a readable, executable segment whose selector is already loaded in the CS register.
使用CS做为段前缀来读一个可读的、可执行的段(其选择子已被装入CS寄存器)。
The same rules as for access to data segments apply to case 1. Case 2 is always valid because the privilege level of a segment whose conforming bit is set is effectively the same as CPL regardless of its DPL. Case 3 always valid because the DPL of the code segment in CS is, by definition, equal to CPL.
访问数据段时使用与场景1所示的相同规则。场景2总是有效的,因为这些一致性位被设置段,它的特权级别和作为CPL和它的DPL是有效的。场景3总是有效的,因为CS寄存器中的代码段DPL等于CPL。
6.3.3 Restricting Control Transfers 控制转移约束
With the 80386, control transfers are accomplished by the instructions JMP, CALL, RET, INT, and IRET, as well as by the exception and interrupt mechanisms . Exceptions and interrupts are special cases that Chapter 9 covers. This chapter discusses only JMP, CALL, and RET instructions.
对于80386而言,控制转移通过以下指令实现:JMP、CALL、RET、INT和IRET,此外异常和中断机制也会转移。异常和中断是特殊的场景,会在第9章涉及。本章仅讨论JMP、CALL和RET指令。
The "near" forms of JMP, CALL, and RET transfer within the current code segment, and therefore are subject only to limit checking. The processor ensures that the destination of the JMP, CALL, or RET instruction does not exceed the limit of the current executable segment. This limit is cached in the CS register; therefore, protection checks for near transfers require no extra clock cycles.
短JMP、CALL和RET的转移是在当前代码段内,因此仅需要对限长进行检验。处理器确保JMP、CALL或RET目的地不超出当前执行段的限长。限长被缓存在CS寄存器中;因此,对于近转移而言保护检查无需额外的时钟周期。
The operands of the "far" forms of JMP and CALL refer to other segments; therefore, the processor performs privilege checking. There are two ways a JMP or CALL can refer to another segment:
长转移操作数由引用其他段的JMP和CALL构成;因此,处理器要执行特权检验。JMP或CALL可以有两种方式来引用另一个段:
- The operand selects the descriptor of another executable segment.
操作数选择了另一个可执行段的描述符。
- The operand selects a call gate descriptor. This gated form of transfer is discussed in a later section on call gates.
操作数选择了一个调用门描述符。门调用转移在后面调用门的部分讨论。
As Figure 6-4 shows, two different privilege levels enter into a privilege check for a control transfer that does not use a call gate:
正如图6-4所示,对于不涉及调用门的控制转移时的特权检验,可以使用两个不同的特权级别:
- The CPL (current privilege level).
- The DPL of the descriptor of the target segment.
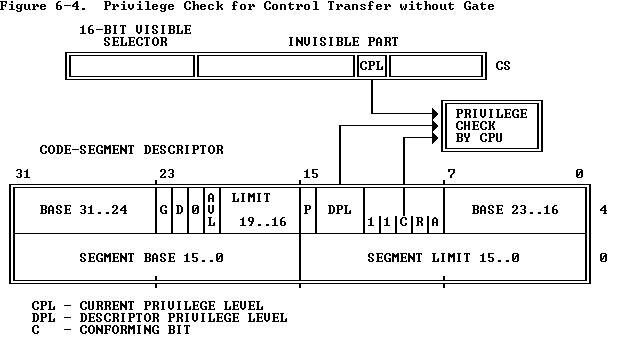
Normally the CPL is equal to the DPL of the segment that the processor is currently executing. CPL may, however, be greater than DPL if the conforming bit is set in the descriptor of the current executable segment. The processor keeps a record of the CPL cached in the CS register; this value can be different from the DPL in the descriptor of the code segment.
通常CPL等于当前处理器正在执行的段的DPL。然而,如果当前执行段描述符的一致性位被设置,CPL大于DPL。处理器在CS寄存器中缓存CPL;其值可以与代码段描述符的DPL不同。
The processor permits a JMP or CALL directly to another segment only if one of the following privilege rules is satisfied:
仅当下列特权级别被满足时,处理器允许JMP或CALL直接访问另一个段。
- DPL of the target is equal to CPL. 目标DPL等于CPL。
- The conforming bit of the target code-segment descriptor is set, and the DPL of the target is less than or equal to CPL.
目标代码段描述符的一致性位被置位,目的DPL小于或等于CPL。
An executable segment whose descriptor has the conforming bit set is called a conforming segment. The conforming-segment mechanism permits sharing of procedures that may be called from various privilege levels but should execute at the privilege level of the calling procedure. Examples of such procedures include math libraries and some exception handlers. When control is transferred to a conforming segment, the CPL does not change. This is the only case when CPL may be unequal to the DPL of the current executable segment.
描述符一致性位被置位的可执行代码段叫一致性段。一致性段机制允许共享程序,这些程序可以被不同特权级调用,但执行时以调用程序的特权级别进行。这样的程序例子包括数学库和一些异常处理例程。当控制权转移到一段性段时,CPL不修改。这是唯一的场景,CPL可以不等于当前执行段的DPL。
Most code segments are not conforming. The basic rules of privilege above mean that, for nonconforming segments, control can be transferred without a gate only to executable segments at the same level of privilege. There is a need, however, to transfer control to (numerically) smaller privilege levels; this need is met by theCALL instruction when used with call-gate descriptors, which are explained in the next section. The JMP instruction may never transfer control to a nonconforming segment whose DPL does not equal CPL.
大部分代码段不是一致性的。上面的特权规则意味着,对于非一致性段,不使用门进行控制转移时,仅可以执行相同特权级别的段代码。然而,将控制权转移到数值更小的特权级别是需要的;当使用调用门描述符来进行CALL指令时会遇到这种需求,这将在下面部分解释。当DPL不等于CPL时,JMP指令永远不会转移控制到一个非一致性段中。
【译】x86程序员手册19-6.3.2数据访问的约束的更多相关文章
- 【译】x86程序员手册01
Intel 80386 Reference Programmer's Manual 80386程序员参考手册 Chapter 1 -- Introduction to the 80386 第1章 - ...
- 【译】x86程序员手册03 - 2.1内存组织和分段
2.1 Memory Organization and Segmentation 内存组织和分段 The physical memory of an 80386 system is organized ...
- 【译】x86程序员手册00 - 翻译起因
从上一次学习MIT的操作系统课程又过去了一年.上次学习并没有坚持下去.想来虽有种种原因,其还在自身无法坚持罢了.故此次再鼓起勇气重新学习,发现课程都已由2014改版为2016了.但大部分内容并没有改变 ...
- 【译】x86程序员手册38-10.2实在址模式下的软件初始化
10.2 Software Initialization for Real-Address Mode 实地址模式的软件初始化 In real-address mode a few structur ...
- 【译】x86程序员手册09-第3章程序指令集
注:觉得本章内容与理解操作系统不直接相关,所以本章并未看完,也就没有翻译完,放在这里中是为了保证手册的完整.有兴趣的人可以去原址查看. https://pdos.csail.mit.edu/6.828 ...
- 【译】x86程序员手册02 - 基本的程序模式
Chapter 2 -- Basic Programming Model: 基本的程序模式 Introduces the models of memory organization. Defines ...
- 【译】x86程序员手册40-10.5初始化的例子
10.5 Initialization Example初始化的例子 译注:本来想把这个例子全部注释完,但由于对intel汇编实不熟悉,有太多的伪指令,本人也是免强看懂,所以就不再做翻译了. $TITL ...
- 【译】x86程序员手册39-10.3切换到保护模式
10.3 Switching to Protected Mode 切换到保护模式 Setting the PE bit of the MSW in CR0 causes the 80386 to b ...
- 【译】x86程序员手册37-第10章 初始化
Chapter 10 Initialization 第10章 初始化 After a signal on the RESET pin, certain registers of the 80386 a ...
随机推荐
- rpm 命令的使用
rpm -ivh xv-3.10a-13.i386.rpm 在Terminal中,基本的安装指令如下: rpm -i xv-3.10a-13.i386.rpm 如果你的连网速度足够快,也可 ...
- vijos 1237 隐形的翅膀
隐形的翅膀 背景 小杉终于进入了天堂.他看到每个人都带着一双隐形翅膀,他也想要. (小杉是怎么看到的?……) 描述 天使告诉小杉,每只翅膀都有长度,两只翅膀的长度之比越接近黄金分割比例,就越完美. 现 ...
- 1.4-动态路由协议OSPF①
r2#sh ip ospf border-routers 查看ABR 修改OSPF接口优先级 r1(config)#int e 0 r1(config-if)#ip ospf priority 100 ...
- 小议C#错误调试和异常处理
在程序设计中不可避免地会出现各种各样的错误,在编写代码时须要尽量避免. 在处理错误时,首先应该分析错 误的类型,找出出错的原因才干解决错误. 错误的分类 watermark/2/text/aHR0cD ...
- Android学习之仿QQ側滑功能的实现
如今项目越来越多的应用了滑动删除的功能,Android本来遵循的是长按删除,IOS定制的是滑动删除,不可否认滑动删除确实在客户体验上要好一点,所以看了非常多关于仿QQ滑动删除的样例,还是感觉代码家的A ...
- P1830 轰炸III
P1830 轰炸III 84通过 145提交 题目提供者wanglichao1121 标签模拟矩阵洛谷原创 难度普及/提高- 提交该题 讨论 题解 记录 最新讨论 暂时没有讨论 题目背景 一个大小为N ...
- ios11--播放音效
// // ViewController.m // 10-iOS中播放音效 // // Created by xiaomage on 15/12/26. // Copyright © 2015年 小码 ...
- had been doing 和had been done有什么差别
had been doing 和had been done有什么差别 浏览 37114 次 1个回答 最佳答案 21Doreen 来自科学教育类芝麻团 推荐于2017-10-15 1.首先要区分h ...
- [HNOI2011]XOR与路径
https://zybuluo.com/mdeditor#1094266 标签(空格分隔): 高斯消元 期望 题面 从 1 号节点开始,以相等的概率,随机选择与当前节点相关联的某条边,并沿这条边走到下 ...
- Linux 文件和目录操作 - cd - 切换目录
命令详解 重要星级: ★★★★★ 功能说明: cd 命令是 "change directory" 中每个单词的首字母缩写,其功能是从当前工作目录切换到指定工作目录. 语法格式: c ...
