8 Best DDoS Attack Tools (Free DDoS Tool Of The Year 2019)
#1) HULK
Description:
HULK stands for HTTP Unbearable Load King. It is a DoS attack tool for the web server. It is created for research purposes.
Features:
- It can bypass the cache engine.
- It can generate unique and obscure traffic.
- It generates a great volume of traffic at the web server.

https://packetstormsecurity.com/files/download/112856/hulk.zip
#2) Tor’s Hammer
Description:
This tool is created for testing purposes. It is for slow post attack.
Features:
- If you run it through Tor network then you will remain unidentified.
- In order to run it through Tor, use 127.0.0.1:9050.
- With this tool, the attack can be made on Apache and IIS servers.

https://sourceforge.net/projects/torshammer/files/Torshammer/1.0/
#3) Slowloris
Features:
- It sends authorized HTTP traffic to the server.
- It doesn’t affect other services and ports on the target network.
- This attack tries to keep the maximum connection engaged with those that are open.
- It achieves this by sending a partial request.
- It tries to hold the connections as long as possible.
- As the server keeps the false connection open, this will overflow the connection pool and will deny the request to the true connections.

https://github.com/gkbrk/slowloris
#4) LOIC
Description: LOIC stands for Low Orbit Ion Cannon. It is a free and popular tool that is available for the DDoS attack.
Features:9
- It is easy to use.
- It sends UDP, TCP, and HTTP requests to the server.
- It can do the attack based on the URL or IP address of the server.
- Within seconds, the website will be down and it will stop responding to the actual requests.
- It will NOT HIDE your IP address. Even using the proxy server will not work. Because in that case, it will make the proxy server a target.

https://sourceforge.net/projects/loic/
#5) Xoic
Description: It is a DDoS attacking tool. With the help of this tool, the attack can be made on small websites.
Features:
- It is easy to use.
- It provides three modes to attack.
- Testing mode.
- Normal DoS attack mode.
- DoS attack with TCP or HTTP or UDP or ICMP message.

https://sourceforge.net/directory/os:mac/?q=xoic
#6) DDOSIM
Description: DDOSIM stands for DDoS Simulator. This tool is for simulating the real DDoS attack. It can attack on the website as well as on the network.
Features:
- It attacks the server by reproducing many Zombie hosts.
- These hosts create a complete TCP connection with the server.
- It can do HTTP DDoS attack using valid requests.
- It can do DDoS attack using invalid requests.
- It can make an attack on the application layer

https://sourceforge.net/projects/ddosim/files/ddosim-0.2.tar.gz/download
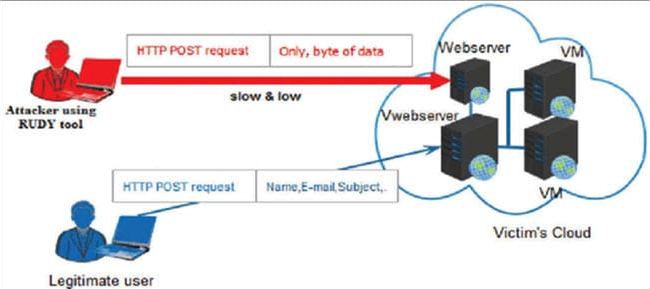
#7) RUDY
Description: RUDY stands for R-U-Dead-Yet. This tool makes the attack using a long form field submission through POST method.
Features:
- Interactive console menu.
- You can select the forms from the URL, for the POST-based DDoS attack.
- It identifies the form fields for data submission. Then injects the long content length data to this form, at a very slow rate.
https://sourceforge.net/projects/r-u-dead-yet/
#8) PyLoris
Description:
This tool is created for testing. To make a DoS attack on the server, this tool uses SOCKS proxies and SSL connections.
Features:
- The attack can be made on HTTP, FTP, SMTP, IMAP, and Telnet.
- It has an easy to use GUI.
- It directly makes an attack on service.
https://sourceforge.net/projects/pyloris/
8 Best DDoS Attack Tools (Free DDoS Tool Of The Year 2019)的更多相关文章
- DDoS ATTACK PROCESSING APPARATUS AND METHOD IN OPENFLOW SWITCH
An OpenFlow switch in an OpenFlow environment includes an attack determination module to collect sta ...
- Identifying a distributed denial of service (DDOS) attack within a network and defending against such an attack
The invention provides methods, apparatus and systems for detecting distributed denial of service (D ...
- 使用DDOS deflate抵御少量DDOS攻击
DDoS-Deflate是一款非常小巧的防御和减轻DDoS攻击的工具,它可以通过监测netstat来跟踪来创建大量互联网连接的IP地址信息,通过APF或IPTABLES禁止或阻档这些非常IP地址. 工 ...
- f5 ddos cc——Mitigating DDoS Attacks with F5 Technology
摘自:https://f5.com/resources/white-papers/mitigating-ddos-attacks-with-f5-technology Mitigating Appli ...
- 国外DDoS产品的一些调研—— Akamai Arbor Networks Cloudflare DOSarrest F5 Fastly Imperva Link11 Neustar Nexusguard Oracle (Dyn) Radware Verisign
Global DDoS Threat LandscapeQ4 2017 https://www.incapsula.com/ddos-report/ddos-report-q4-2017.html,D ...
- Varnish简介
Varnish介绍: Varnish是一个反向HTTP代理,有时也被称为HTTP的加速器或网络加速器:它存在于真实服务器的前面(可能有多级代理),将来自于客户端的请求中的部分内容存储在自身的内存中,以 ...
- 知名黑客组织Anonymous(匿名者)的装备库
原文出处: infosecinstitute 译文出处:freebuf 欢迎分享原创到伯乐头条 本文关注的是世界著名的黑客组织Anonymous(匿名者).“我将描述他们的攻击方法和方式的计划 ...
- Azure上Linux VM DDOS攻击预防: 慢速攻击
在上篇博客(http://www.cnblogs.com/cloudapps/p/4996046.html)中,介绍了如何使用Apache的模块mod_evasive进行反DDOS攻击的设置,在这种模 ...
- DDoS
Distributed Denial of Service (DDoS) Attacks/tools https://staff.washington.edu/dittrich/misc/ddos/ ...
随机推荐
- python的gRPC示例
参考URL: https://segmentfault.com/a/1190000015220713?utm_source=channel-hottest gRPC 是一个高性能.开源和通用的 RPC ...
- 【洛谷P4148】简单题(kd-tree)
传送门 题意: 给出一个\(n*n\)的棋盘,现在有两种操作:一种是某个格子里的数字加上\(A\),另一种是询问矩阵和. 空间限制:\(20MB\),强制在线. 思路: 直接\(kd-tree\)来搞 ...
- python获取某路径下,某种特定类型的文件名称,os.walk(路径)生成器;os.listdir(路径),os.path.splitext(名称),os.path.join(路径,名称),os.path.isdir(路径\名称)
#获取某文件夹下制定类型文件# import os# def filep(fp):# l=[]# a=os.walk(fp) #生成器# for nowp,sonp,oth in a: #当前目录,子 ...
- CF1252J Tiling Terrace
CF1252J Tiling Terrace 洛谷评测传送门 题目描述 Talia has just bought an abandoned house in the outskirt of Jaka ...
- 消息队列的使用<二>:ActiveMQ的基本使用(Java)
目录 ActiveMQ 介绍 下载.安装和初次运行 Java上初次使用activeMQ 设置请求属性: 可靠性机制 事务 消息消费方式 receive 监听器: 消息类型 发布/订阅模式 非持久订阅 ...
- 【转】pywinauto教程
一.环境安装 1.命令行安装方法 pip install pywinauto==0.6.7 2.手动安装方法 安装包下载链接:pyWin32: python调用windows api的库https:/ ...
- 响应国家号召 1+X 证书 Web 前端开发考试模拟题
1+x证书Web前端开发初级理论考试样题2019 http://blog.zh66.club/index.php/archives/149/ 1+x证书Web前端开发初级实操考试样题2019 http ...
- LeetCode 142:环形链表 II Linked List Cycle II
给定一个链表,返回链表开始入环的第一个节点. 如果链表无环,则返回 null. 为了表示给定链表中的环,我们使用整数 pos 来表示链表尾连接到链表中的位置(索引从 0 开始). 如果 pos 是 - ...
- 【测试方法】Web测试中bug定位基本方法
知识总结:Web测试中bug定位基本方法 涉及知识点:测试方法 在web测试过程中,经常会遇到页面中内容或数据显示错误,甚至不显示,第一反应就是BUG,没错,确实是BUG.进一步了解这个BUG的问题出 ...
- WPF ToggleButton Style
<Style x:Key="ArrowToggleStyle" TargetType="ToggleButton"> <Setter Prop ...
