Lab 1-4
Analyze the file Lab01-04.exe.
Questions and Short Answers
Upload the Lab01-04.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
A: As of this writing, 16 of 43 antivirus engines identify this as malicious code that downloads and/or drops additional malware onto a system.
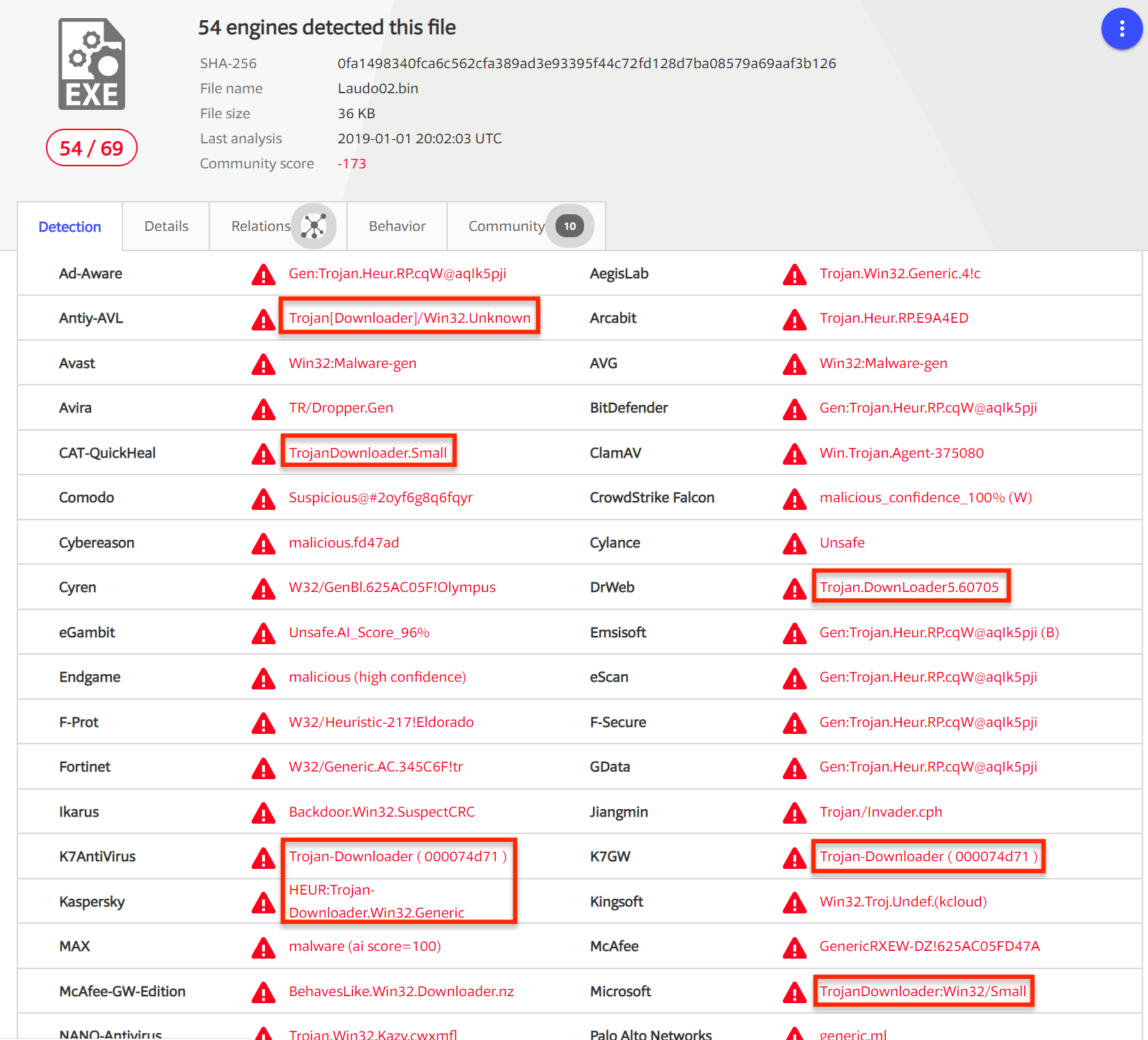
注:在写这篇博客时的数据是 69 反病毒引擎里面 54 个是反病毒签名。
Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
A: There are no indications that the file is packed or obfuscated.
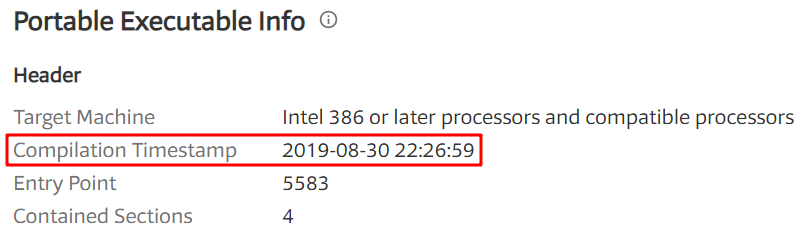
When was this program compiled?
A: According to the file header, this program was compiled in August 2019. Clearly, the compile time is faked, and we can’t determine when the file was compiled.
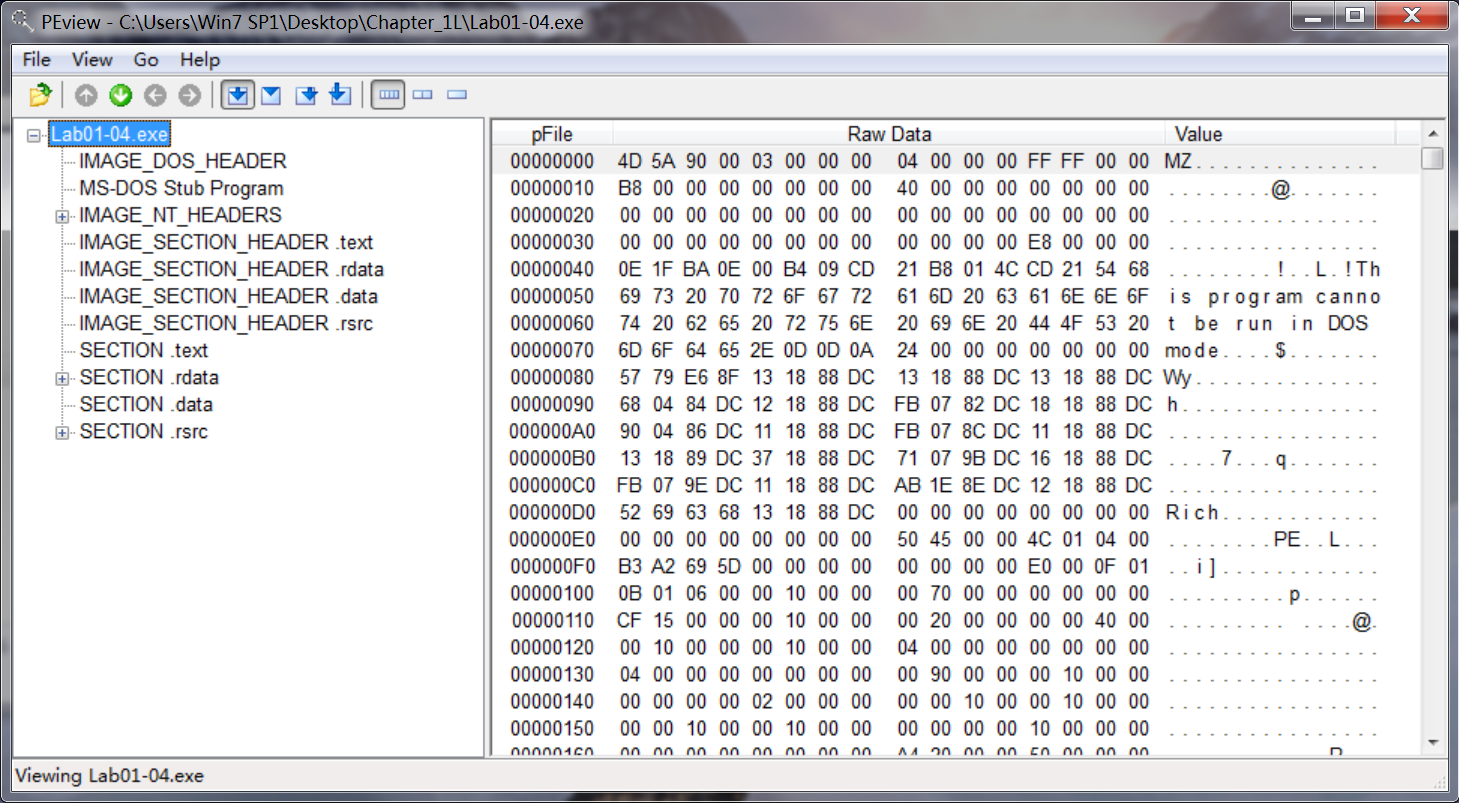
PEview 查看的结果如下:
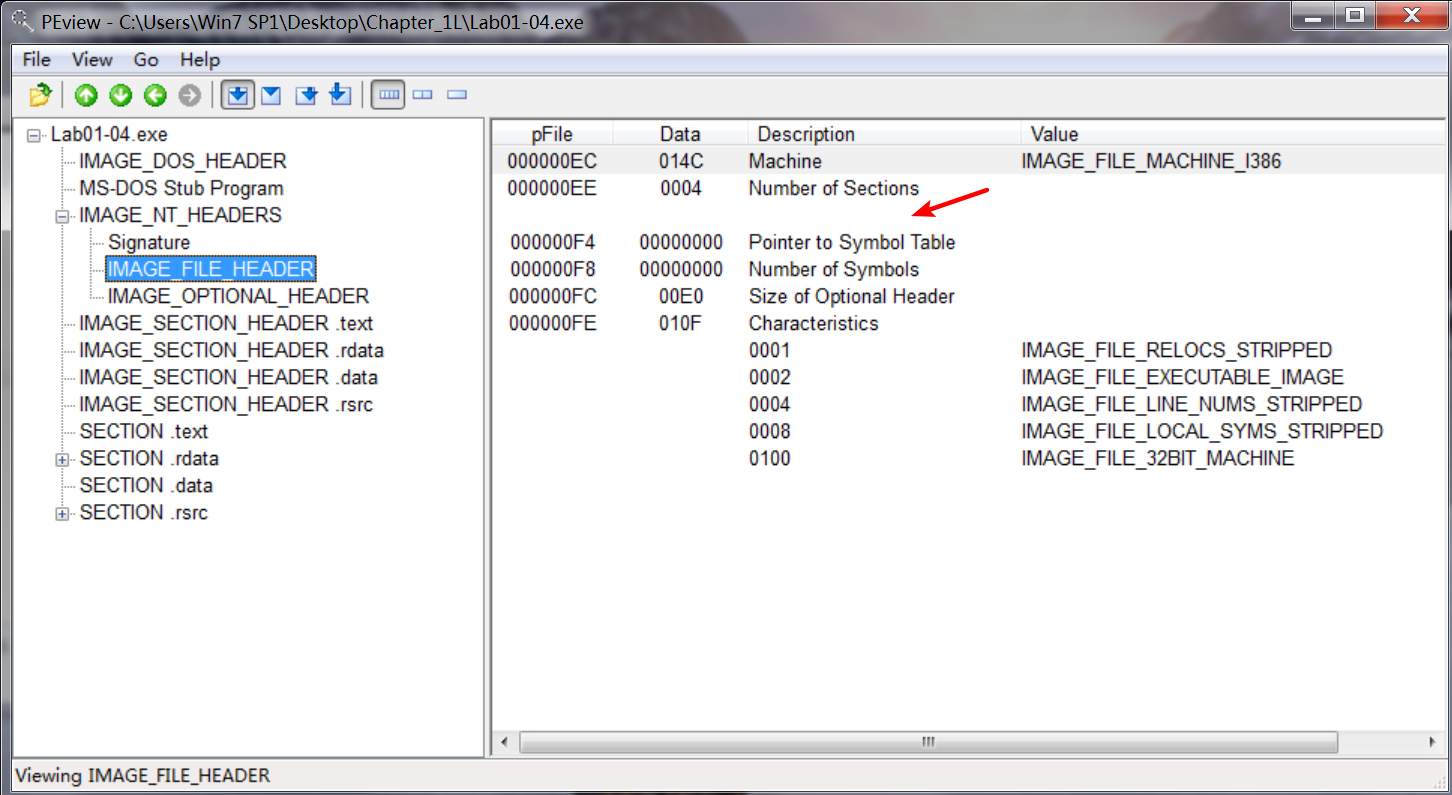
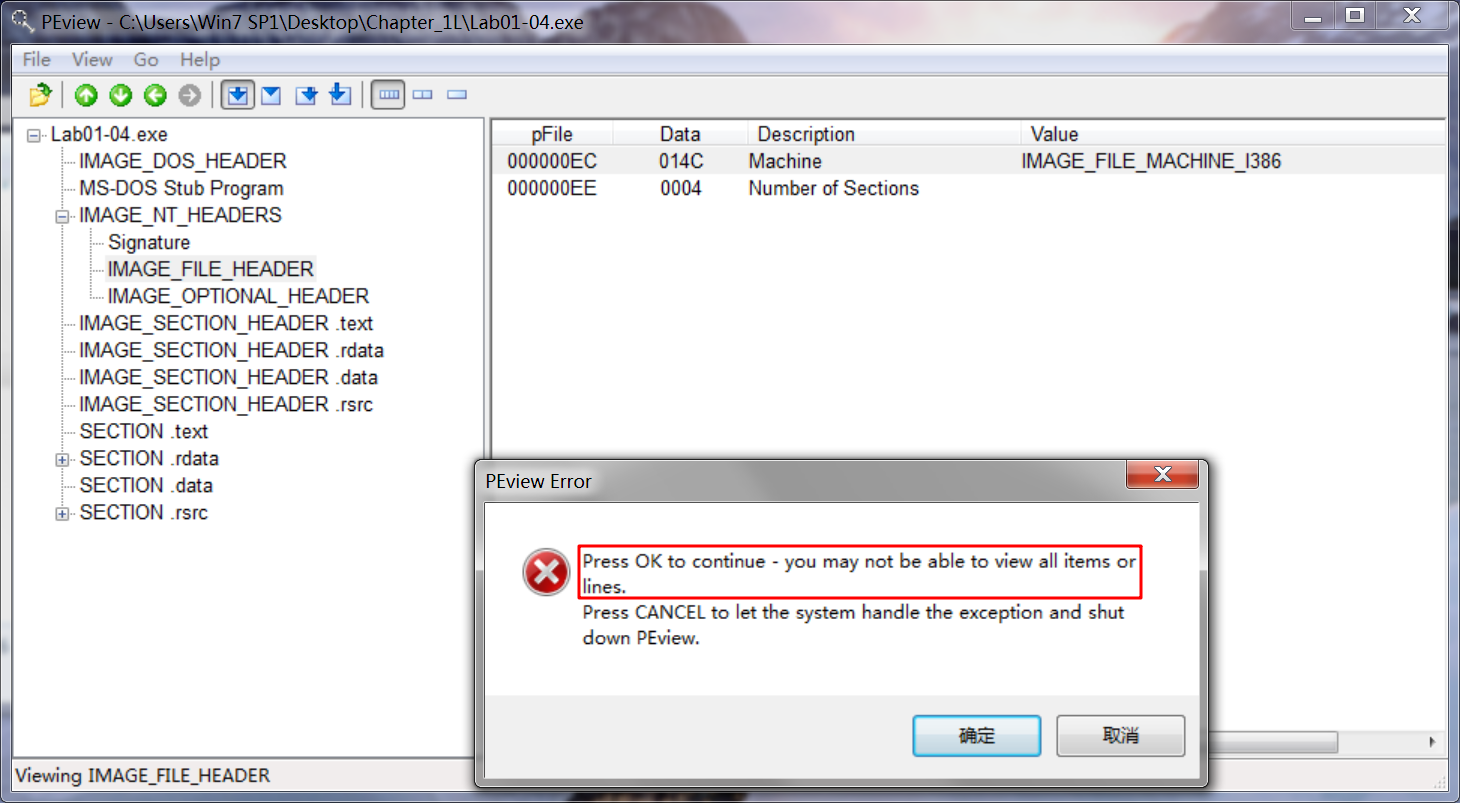
本该在箭头处显示,却为空。(应该是我的软件版本自身的问题,因为要打开 IMAGE_FILE_HEADER 时,会弹出警告:可能会出现有些条目不能显示。)
在 VT(http://www.VirusTotal.com/)中查看的结果如下:
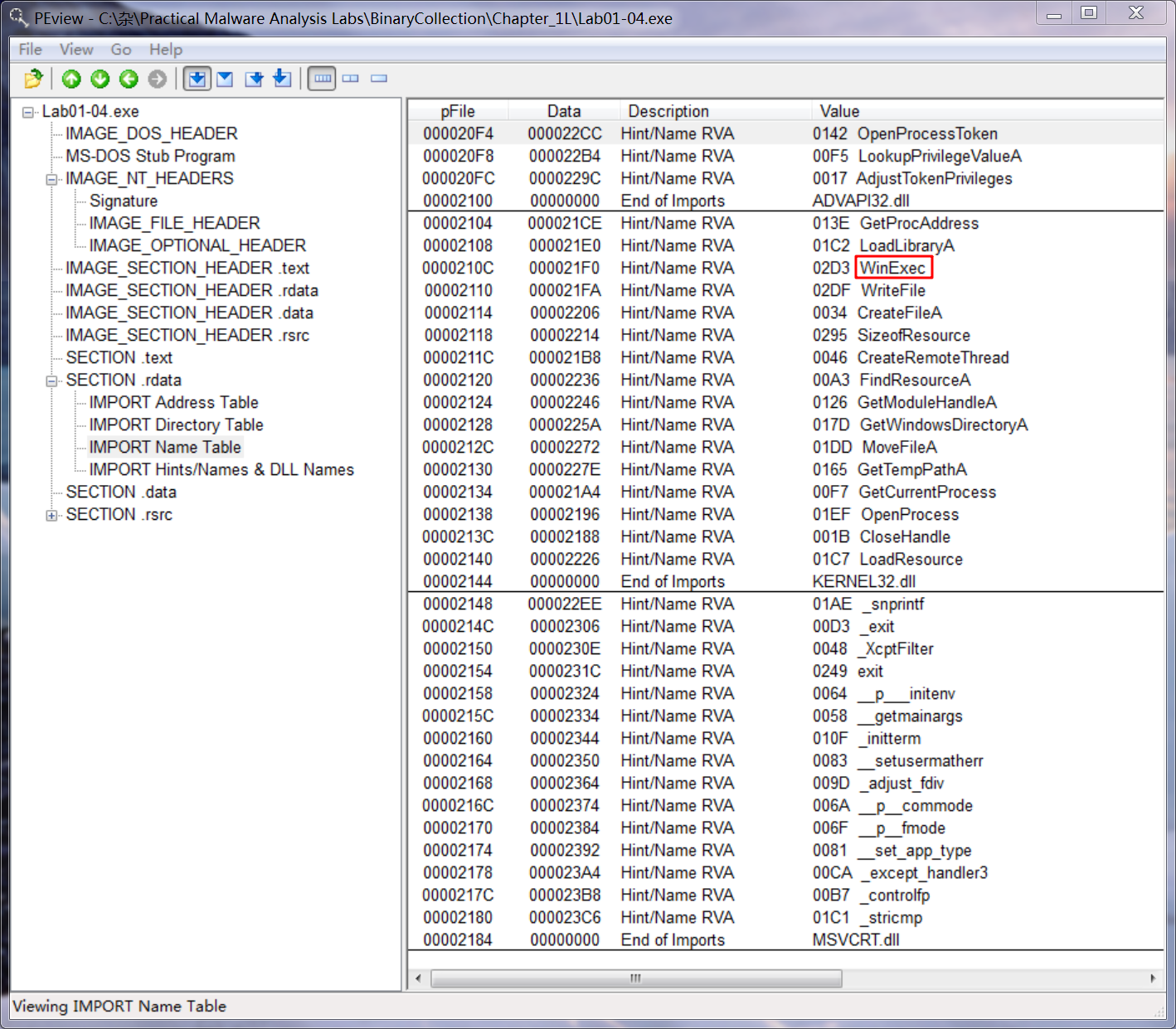
Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
A: The imports from advapi32.dll indicate that the program is doing something with permissions. The imports from WinExec and WriteFile, along with the results from VirusTotal.com, tell us that the program writes a file to disk and then executes it. There are also imports for reading information from the resource section of the file.
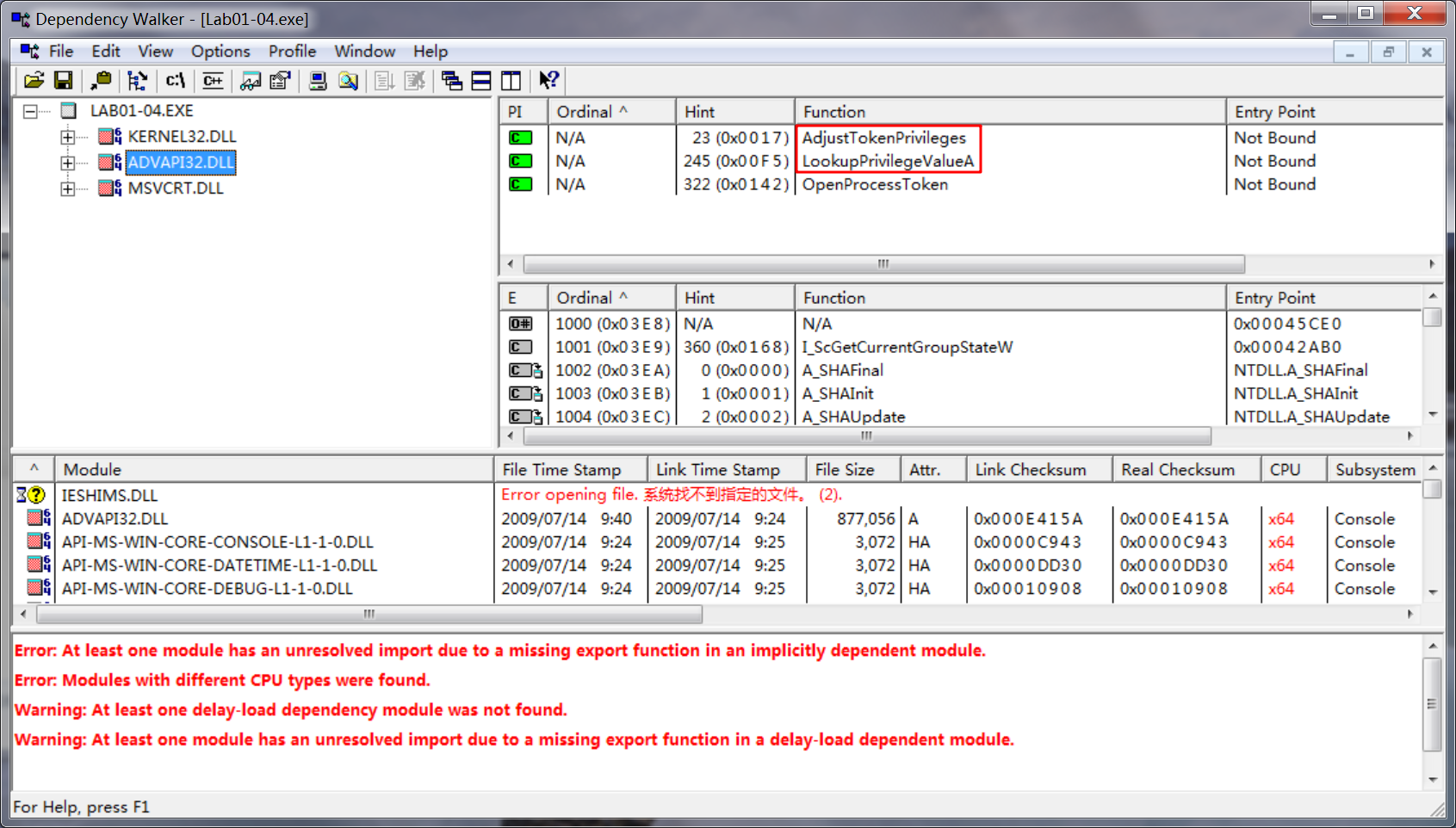
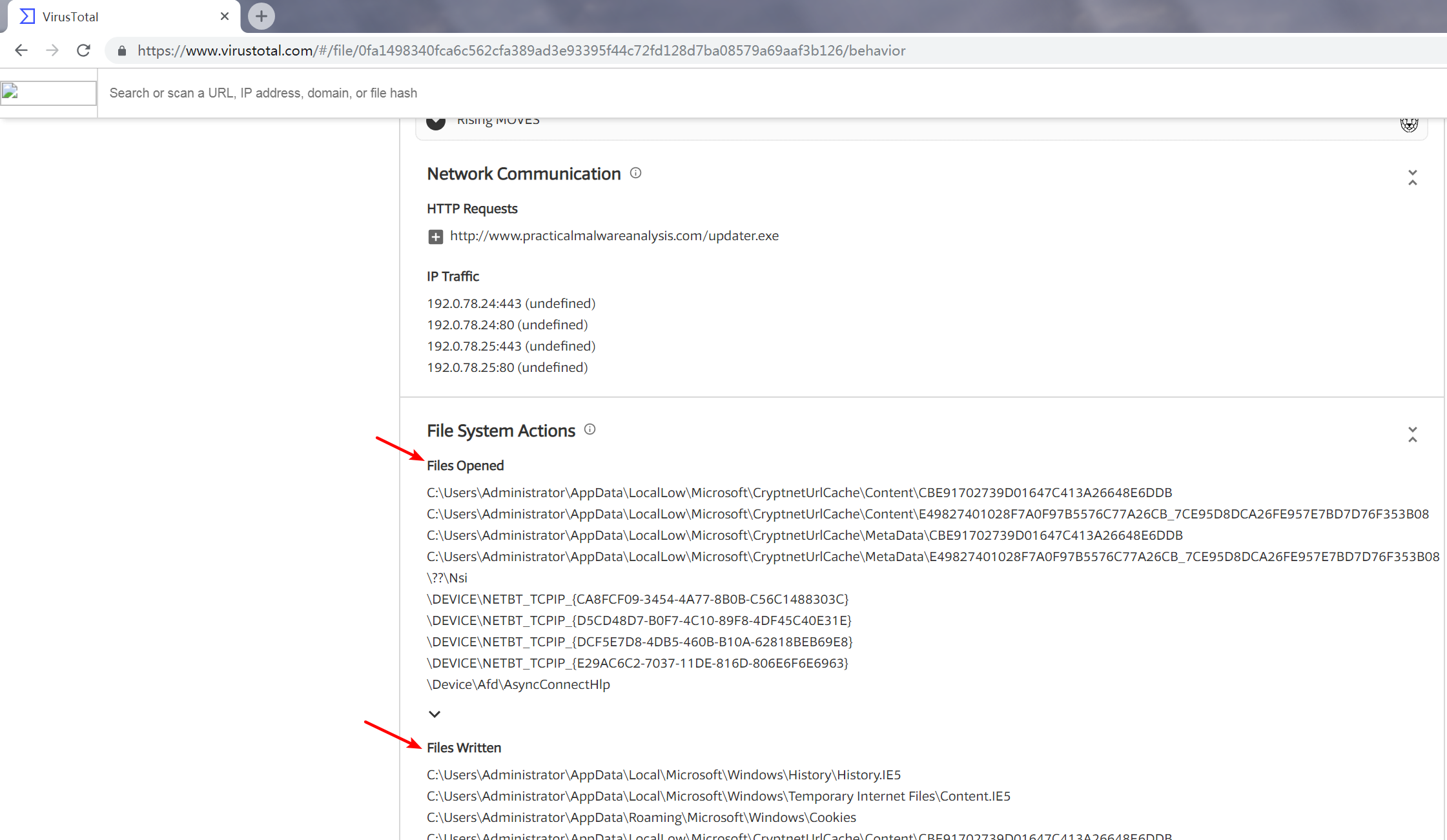
What host- or network-based indicators could be used to identify this malware on infected machines?
A: The string \system32\wupdmgr.exe indicates that this program could create or modify a file at that location. The string www.malwareanalysisbook.com/ updater.exe probably indicates where additional malware is stored, ready for download.
注:利用 IDA -> View -> Opensubviews -> Strings 没有找到要查找的线索。但是书中的方法可以找到。
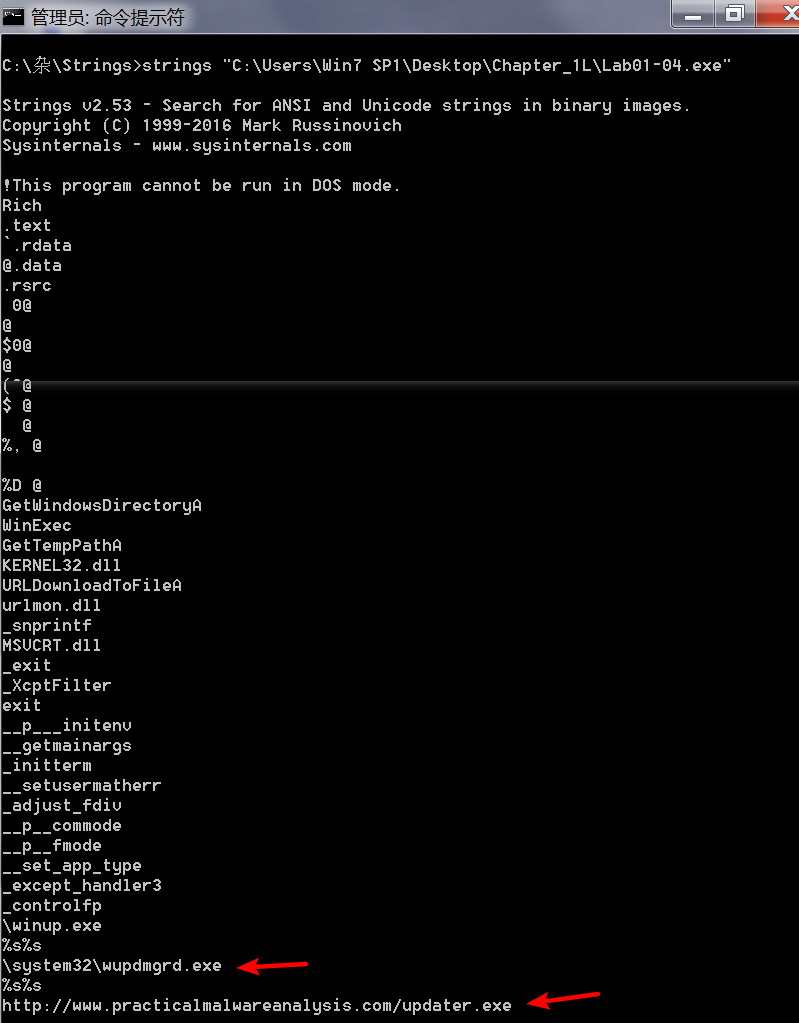
注:翻译版书1.3 查找字符串(英文版书,Part 1: Basic Analysis -> Finding Strings)
步骤:
- 下载Strings(英文原版书提供的链接好使,翻译版失效。)
- cmd -> 进入下载的strings.exe可执行文件所在文件夹 -> 使用 strings 命令查看
This file has one resource in the resource section. Use Resource Hacker to examine that resource, and then use it to extract the resource. What can you learn from the resource?
A: The resource section contains another PE executable. Use Resource Hacker to save the resource as binary data, and then analyze the binary file as you would analyze any executable. The executable in the resource section is a downloader program that downloads additional malware.
Detailed Analysis
For the Lab01-04.exe file, the results from VirusTotal.com suggest a program related to a downloader. PEview gives no indication that the file is packed or obfuscated.

注:在写这篇博客时的数据是 68 反病毒引擎里面 56 个是反病毒签名。分析结果显示很大部分的引擎显示这很可能是一个木马下载后门软件。
The imports from advapi32.dll tell us that program does something with permissions, and we can assume that it tries to access protected files using special permissions. The imports from kernel32.dll tell us that the program loads data from the resource section (LoadResource, FindResource, and SizeOfResource), writes a file to disk (CreateFile and WriteFile), and executes a file on the disk (WinExec). We can also guess that the program writes files to the system directory because of the calls to GetWindowsDirectory.
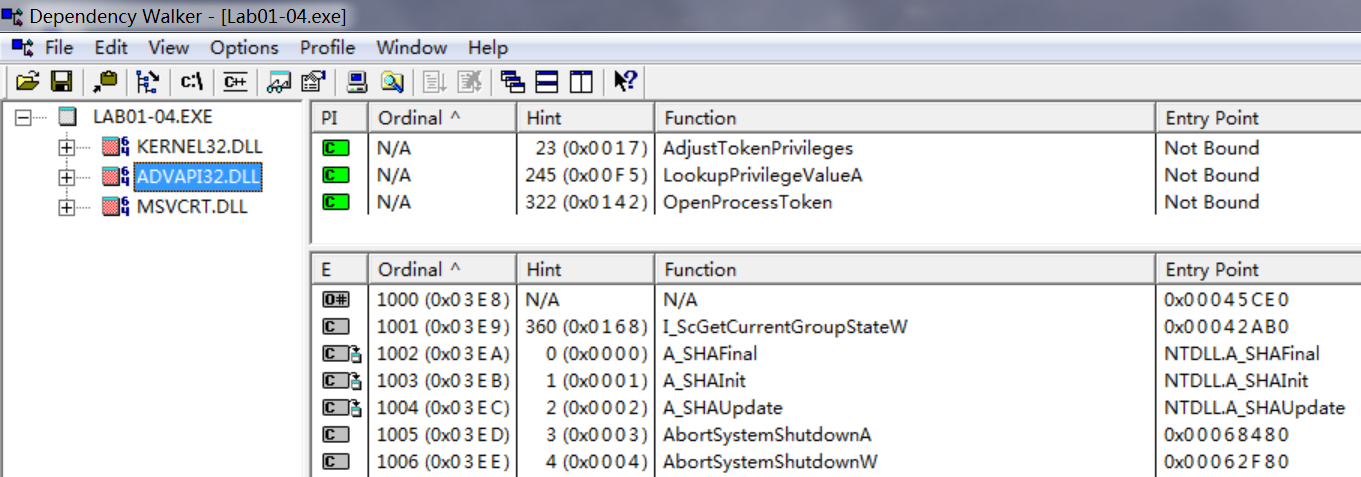
AdjustTokenPrivileges说明这个函数可以通过令牌的方式确保只运行一个进程在系统中;
LookupPrigilegeValueA说明这个程序可以去查找用户的登录信息等系统敏感信息。
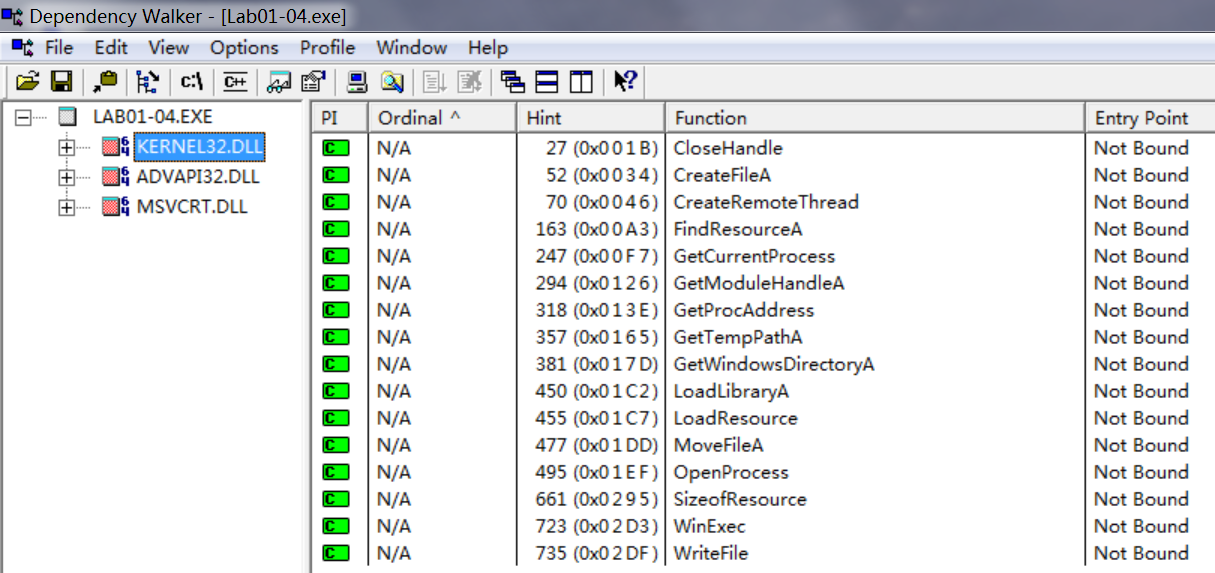
KERNEL32.DLL导入了CreateFileA和MoveFileA这个函数,说明它可以创建一个文件和移动一个文件;
还有CreateRemoteThread说明这个函数会在一个远程进程(Remote Process)里面创建一个自己的远程线程(Remote Thread)来运行恶意代码;
还有FindResourceA、LoadResource和SizeofResourse这个函数,说明它在查找资源节的内容;
GetCurrentProcess和OpenProcess这个是获得想要获得进程的文件描述符,也是为了操作远程的进程;
值得注意的是GetTempPathA这个函数,这说明这恶意代码可能会使用Temp目录。
WinExec说明这个程序可以运行另一个程序代码。
Examining the strings, we see www.malwareanalysisbok.com/updater.exe, which is probably the location that holds the malicious code for download. We also see the string \system32\wupdmgr.exe, which, in combination with the call to GetWindowsDirectory, suggests that a file in C:\Windows\System32 wupdmgr.exe is created or edited by this malware.
We now know with some confidence that this malicious file downloads new malware. We know where it downloads the malware from, and we can guess where it stores the downloaded malware. The only thing that’s odd is that the program doesn’t appear to access any network functions.
The most interesting part of this malware is the resource section. When we open this malware in Resource Hacker, we see one resource. Resource Hacker identifies the type of the resource as binary, meaning arbitrary binary data, and when we look at the data, most of it is meaningless. But notice the string !This program cannot be run in DOS mode. This string is the error message included in the DOS header at the beginning of all PE files. We can therefore conclude that this resource is an additional executable file stored in the resource section of Lab01-04.exe. This is a fairly common technique used in malware.
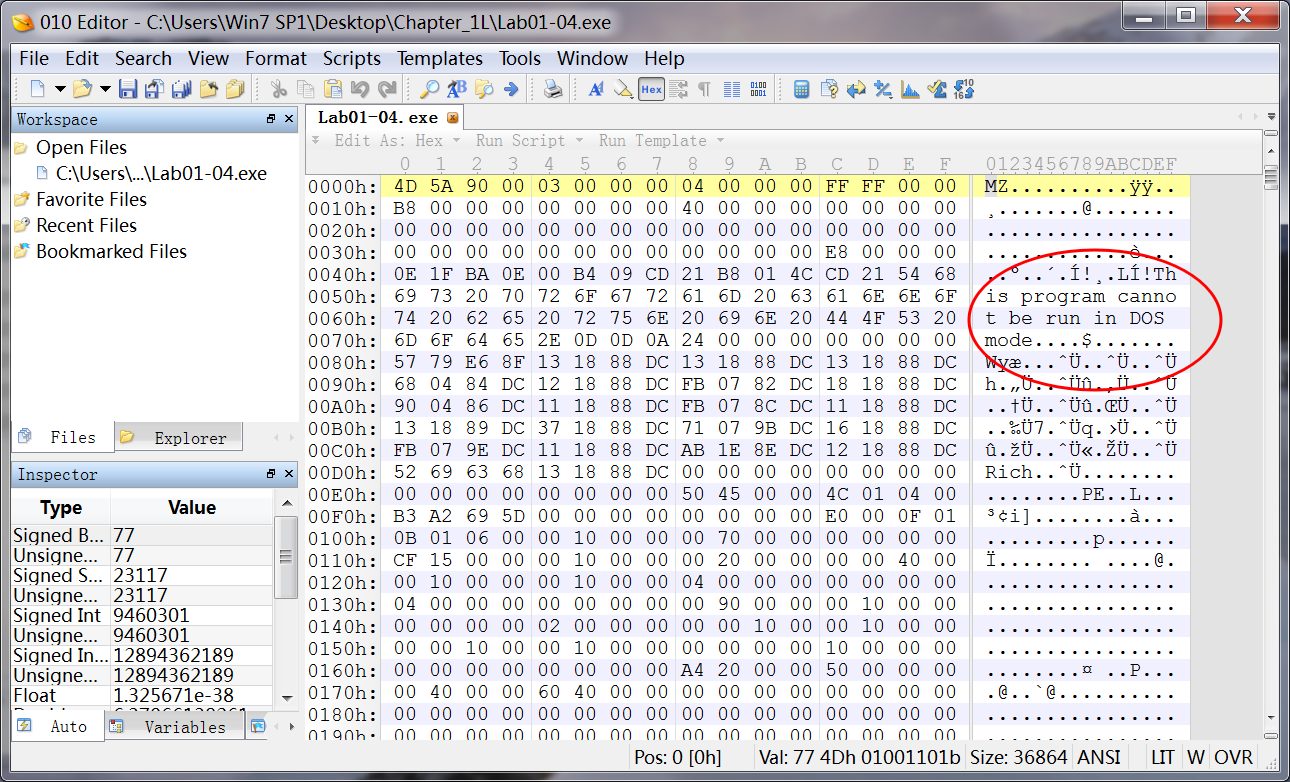
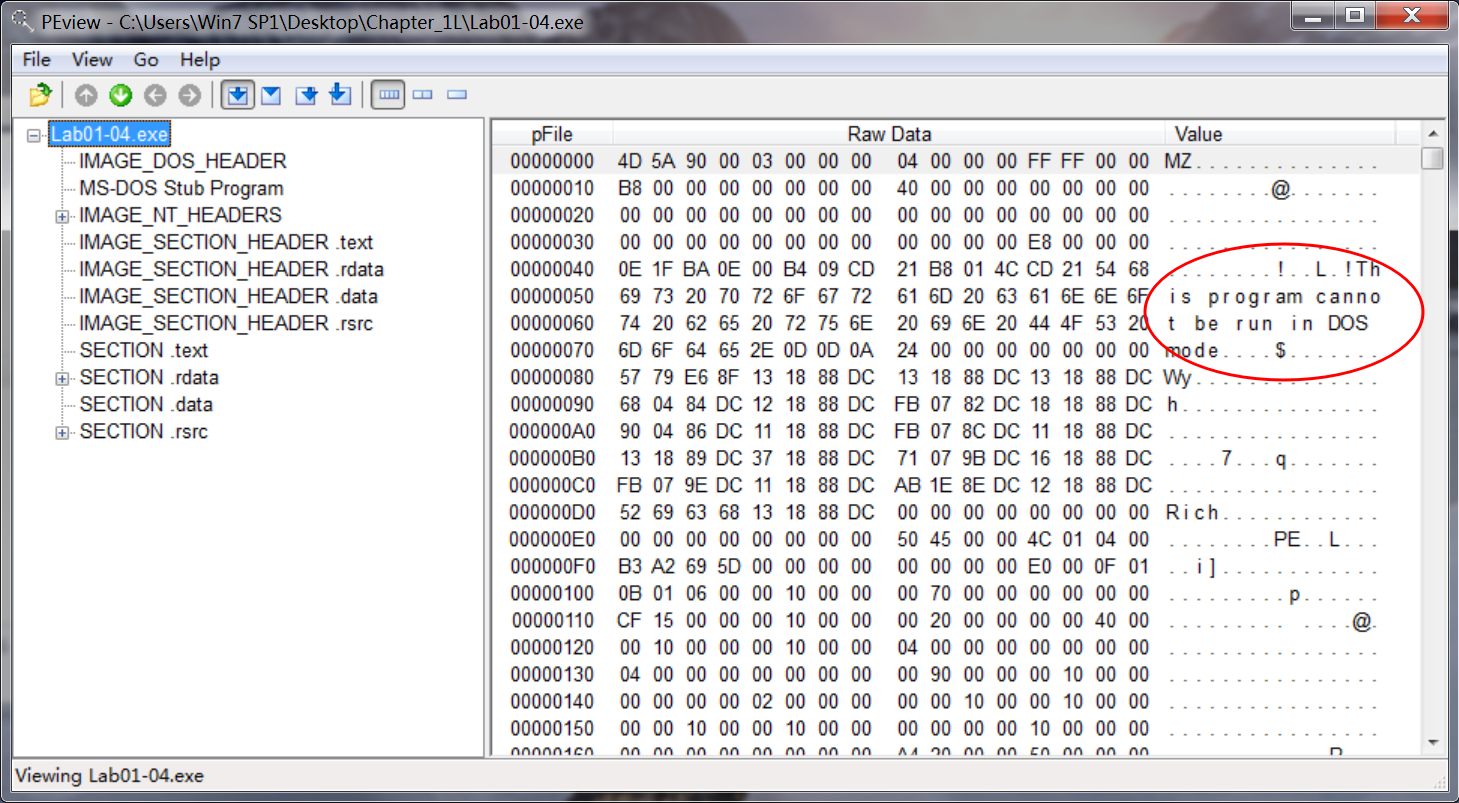
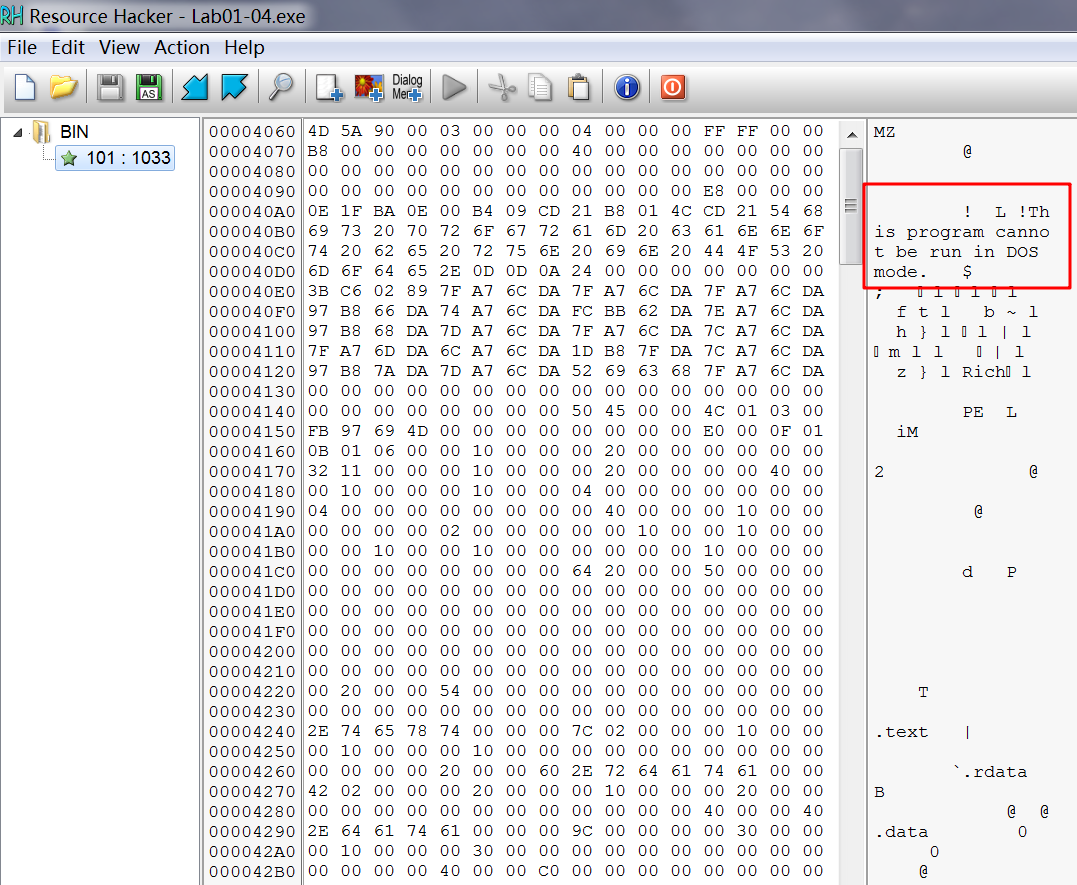
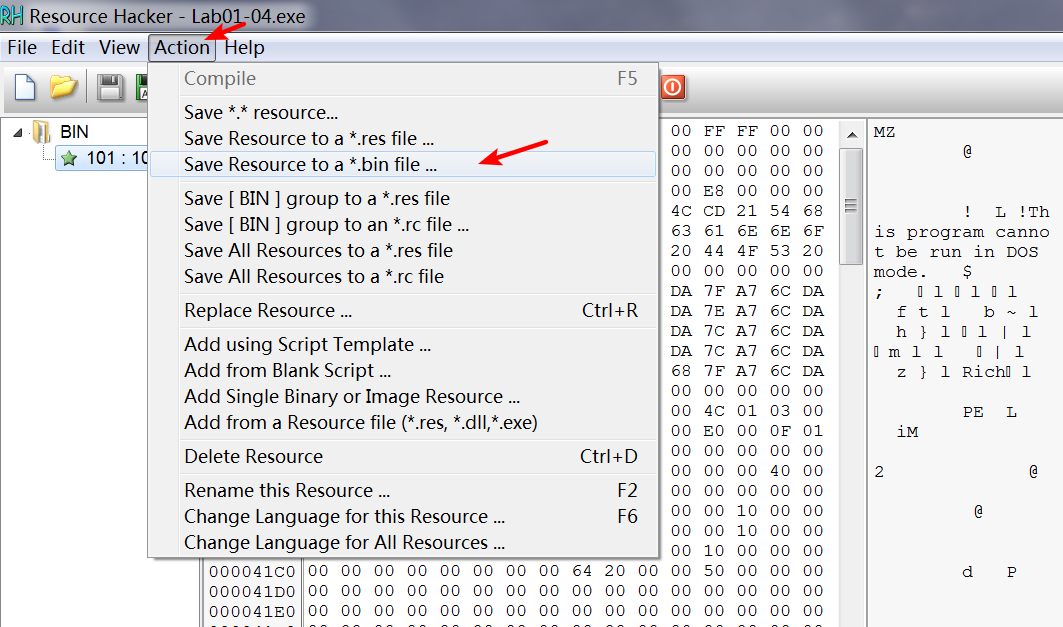
To continue analyzing this file with Resource Hacker, we click Action -> Save resource as binary file. After saving the resource, we open the file in PEview to analyze the file embedded within it. Looking at the imports, we see that the embedded file is the one that accesses the network functions. It calls URLDownloadToFile, a function commonly used by malicious downloaders. It also calls WinExec, which probably executes the downloaded file.
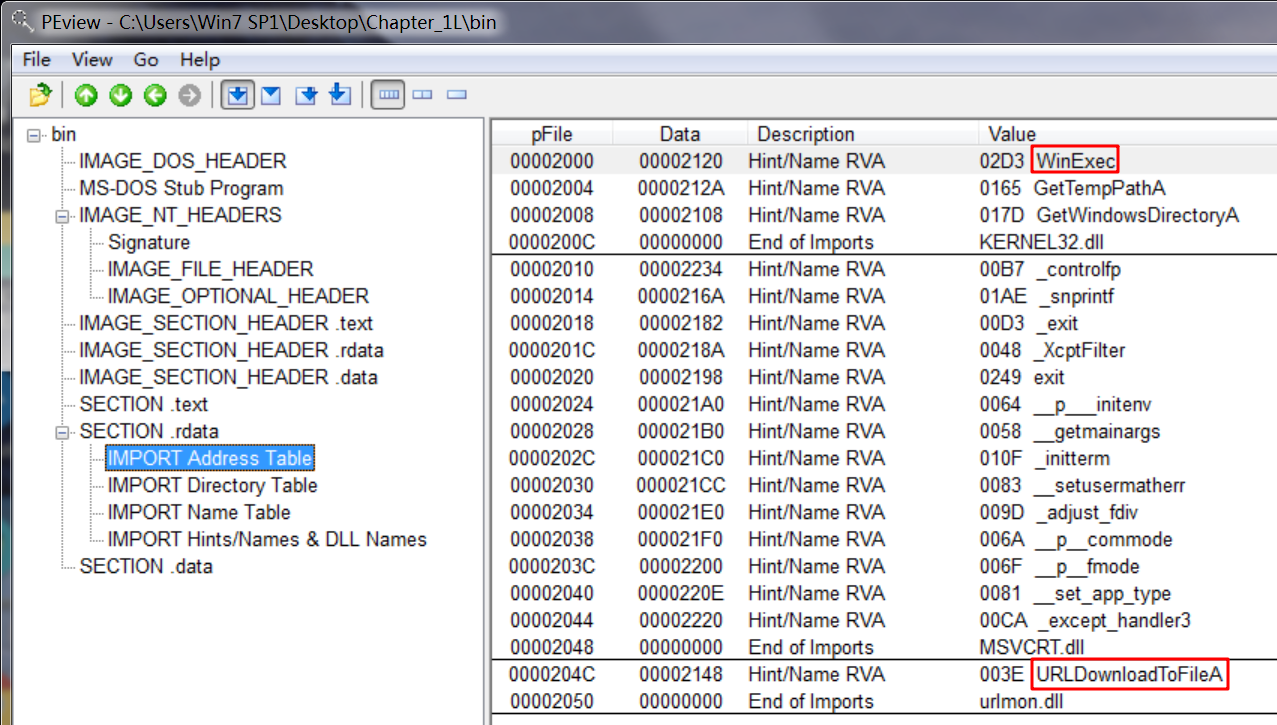
注:未经过 Resource Hacker 处理,使用 PEview 没有看到 URLDownloadToFileA 函数,urlmon.dll 库也没有显示。
Preference
Lab 1-4的更多相关文章
- MIT 6.828 JOS学习笔记18. Lab 3.2 Part B: Page Faults, Breakpoints Exceptions, and System Calls
现在你的操作系统内核已经具备一定的异常处理能力了,在这部分实验中,我们将会进一步完善它,使它能够处理不同类型的中断/异常. Handling Page Fault 缺页中断是一个非常重要的中断,因为我 ...
- MIT 6.828 JOS学习笔记17. Lab 3.1 Part A User Environments
Introduction 在这个实验中,我们将实现操作系统的一些基本功能,来实现用户环境下的进程的正常运行.你将会加强JOS内核的功能,为它增添一些重要的数据结构,用来记录用户进程环境的一些信息:创建 ...
- MIT 6.828 JOS学习笔记16. Lab 2.2
Part 3 Kernel Address Space JOS把32位线性地址虚拟空间划分成两个部分.其中用户环境(进程运行环境)通常占据低地址的那部分,叫用户地址空间.而操作系统内核总是占据高地址的 ...
- MIT 6.828 JOS学习笔记15. Lab 2.1
Lab 2: Memory Management lab2中多出来的几个文件: inc/memlayout.h kern/pmap.c kern/pmap.h kern/kclock.h kern/k ...
- MIT 6.828 JOS学习笔记10. Lab 1 Part 3: The kernel
Lab 1 Part 3: The kernel 现在我们将开始具体讨论一下JOS内核了.就像boot loader一样,内核开始的时候也是一些汇编语句,用于设置一些东西,来保证C语言的程序能够正确的 ...
- MIT 6.828 JOS学习笔记7. Lab 1 Part 2.2: The Boot Loader
Lab 1 Part 2 The Boot Loader Loading the Kernel 我们现在可以进一步的讨论一下boot loader中的C语言的部分,即boot/main.c.但是在我们 ...
- python opencv 利用Lab空间把春天的场景改为秋天
前一段时间实现了Reinhard颜色迁移算法,感觉挺有意思的,然后在代码上随意做了一些更改,有了一些发现,把Lab通道的a通道值改为127左右,可以将绿色改为黄色,而对其他颜色的改动非常小,因此可以将 ...
- Acadia Lab 228 + Lab 222
又是一对串烧实验,布好线后非常方便就可以一起完成. 连线方案一模一样: Lab 228 数码管骰子 核心代码如下: def loop() : global cnt global btn_read,se ...
- Acadia Lab 203 + Lab 231
在做完 Lab 6 之后,惊觉选做实验缺口很大,于是遍历了一遍夏任务,找到了一条最省力的路线. 做完 Lab 6 的连线不用拆,可以接下来做以下两个实验: Lab 203 网络时钟 核心代码如下: v ...
- GJM : 【技术干货】给The Lab Renderer for Unity中地形添加阴影
感谢您的阅读.喜欢的.有用的就请大哥大嫂们高抬贵手"推荐一下"吧!你的精神支持是博主强大的写作动力以及转载收藏动力.欢迎转载! 版权声明:本文原创发表于 [请点击连接前往] ,未经 ...
随机推荐
- topcoder srm 480 div1
problem1 link 直接模拟即可. problem2 link 首先,网关一定是安装在client与server之间的链路上.而不会安装在client与client之间的链路上.对于一条路径c ...
- Python3 tkinter基础 Entry state 不可写 可以选 可复制的输入框
Python : 3.7.0 OS : Ubuntu 18.04.1 LTS IDE : PyCharm 2018.2.4 Conda ...
- Linux内核中的netlink是什么?
答: 是一种内核与用户应用间的双向数据传输方式,用户态使用传统的socketAPI即可使用netlink提供的功能,但是内核态需要使用专门的api来使用netlink.
- SpringBoot 整合使用dubbo
这里主要是按照teaey作者的spring-boot-starter-dubbo框架进行一些变化的使用 依赖包: <dependency> <groupId>com.aliba ...
- HDU 4918 Query on the subtree(动态点分治+树状数组)
题意 给定一棵 \(n\) 个节点的树,每个节点有点权.完成 \(q\) 个操作--操作分两种:修改点 \(x\) 的点权.查询与 \(x\) 距离小于等于 \(d\) 的权值总和. \(1 \leq ...
- Docker Builders:Builder pattern vs. Multi-stage builds in Docker
原文链接 Builder pattern vs. Multi-stage builds in Docker This post looks at two new PRs from the Docker ...
- Kubernetes之容器
Images You create your Docker image and push it to a registry before referring to it in a Kubernetes ...
- Win10远程桌面可能是由于CredSSP加密Oracle修正
win10更新1083之后,远程桌面就会连接失败,显示如下: 根据微软官方的说法是更改了安全策略: https://support.microsoft.com/zh-cn/help/4093492/c ...
- Android 4.0之后的日历控件拥挤的解决办法
本意是想做成这个样子的控件: 发现使用datepicker之后,效果完全不同,把整个日历都显示出来了.非常拥挤. 在datepicker中加入android:calendarViewShown=&qu ...
- java根据地址获取百度API经纬度
java根据地址获取百度API经纬度(详细文档) public void getLarLng(String address) throws Exception { String ak = " ...
