Ethical Hacking - NETWORK PENETRATION TESTING(24)
Detecting suspicious activities using Wireshark
You can use make the MAC address of the router to static on the ARP table to prevent ARP attack. But it is not effective and useful for big companys .
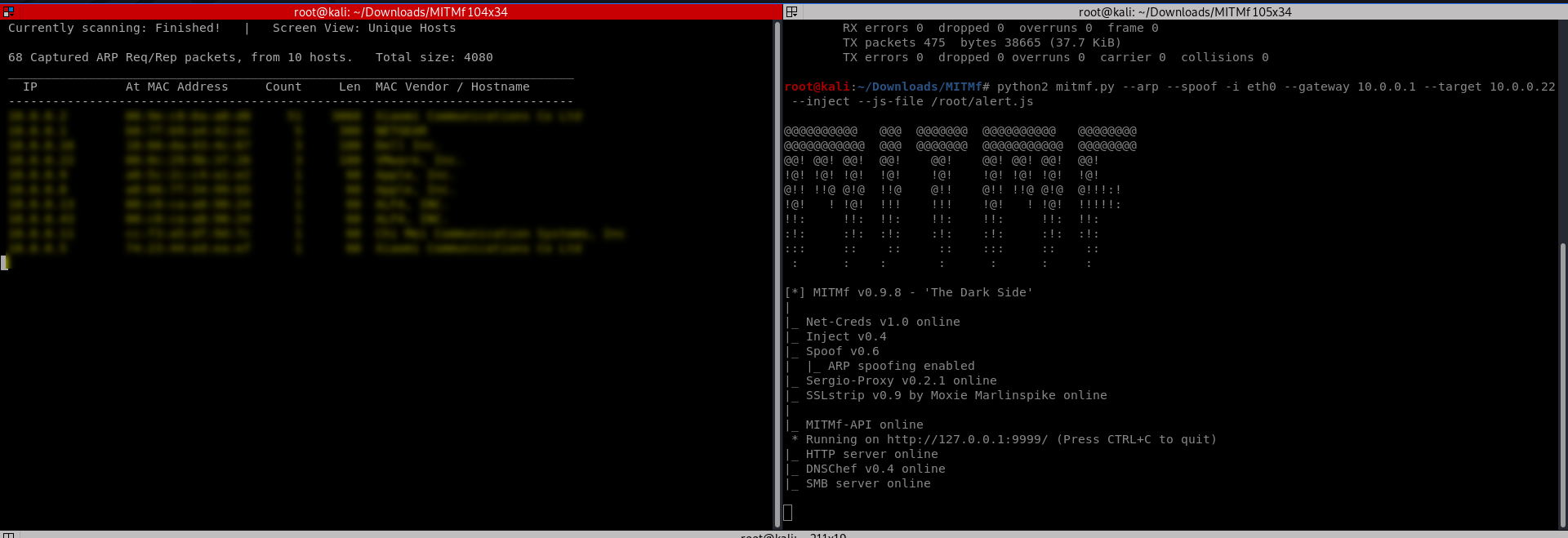
Start the attacks from the Kali Linux.
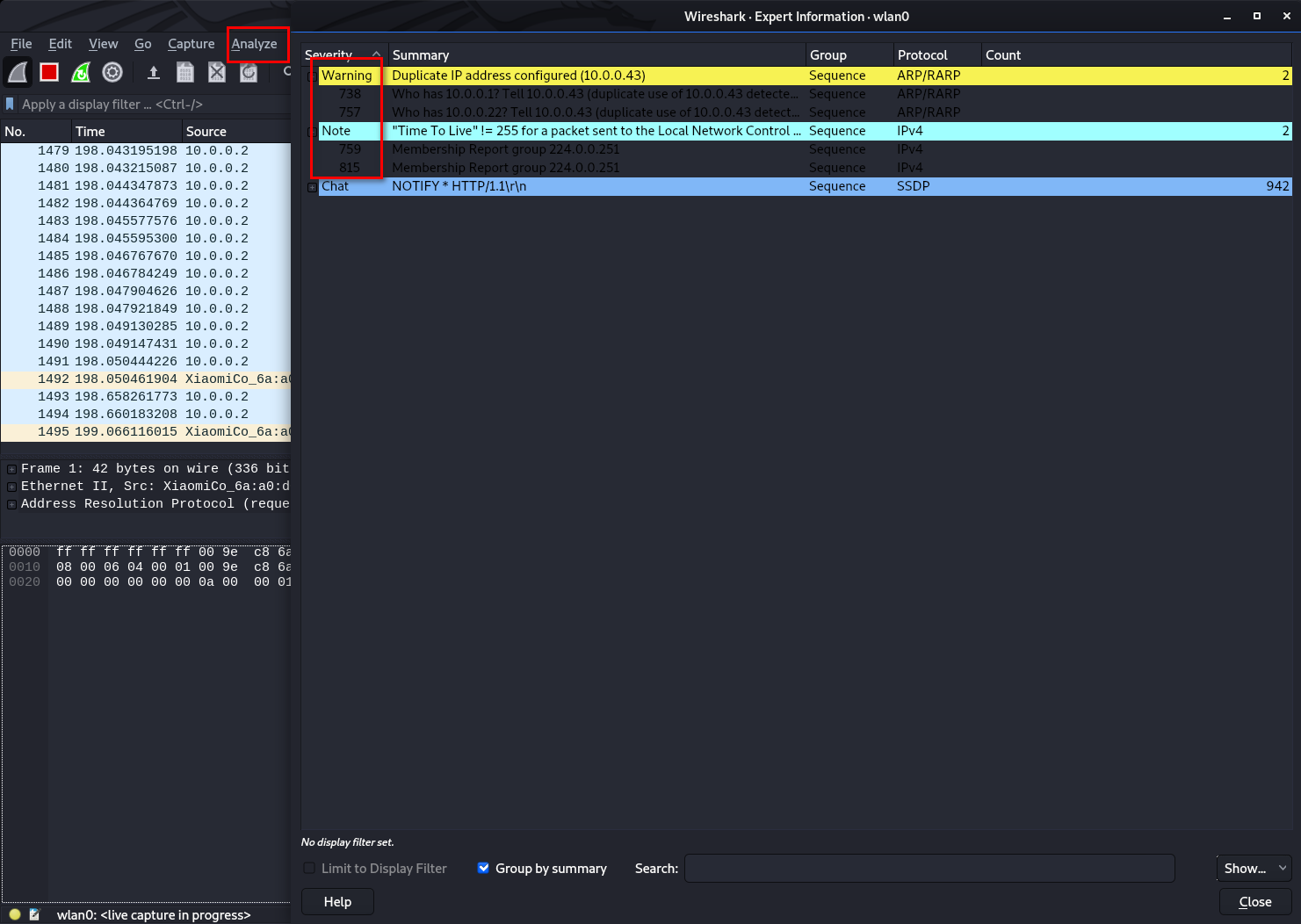
Analyze the packages from expert information.
Ethical Hacking - NETWORK PENETRATION TESTING(24)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- cb02a_c++_数据结构_顺序容器_STL_list类_双向链表
/*cb02a_c++_数据结构_顺序容器_STL_list类_双向链表实例化std::list对象在list开头插入元素在list末尾插入元素在list中间插入元素,插入时间恒定,非常快.数组:中间 ...
- 测试人员遇到Android APP崩溃和无响应手足无措?
这2天,在测APP兼容性时,遇到APP奔溃闪退的情况.将问题反馈给开发后,开发自己调试后,没有复现.由于又是远程,base地不在一块,我总不能把手机寄过去吧,那也太费事了. 所以就想到,提供明确的报错 ...
- 1169A+B问题终结版(高精度计算)
描述 给定两个整数A和B,输出A+B的值.A和B的值可能会很大很大,甚至达到100位.现在请你解决这一问题. 输入 两行,分别是两个整数A,B,换行隔开.A和B会很大很大. 输出 一个整数,即A+B的 ...
- 定时任务Cron
Linux系统中的定时任务cron,一个很实际很有效很简单的一个工作,在日常的生产环境中,会被广泛使用的一个组件.通过设置时间.执行的脚本等内容,能够让系统自动的执行相关任务,很是方便. cron定时 ...
- Java 根据地图定位坐标推荐附近的目标地址(直线距离)
这两天需要在公众号上面做一个关于根据地图当前定位与目标地址直线距离远近推荐的查询,一开始摸不着头脑,现已解决,mark一下 现有的材料:当前用户手机端的通过微信定位的经纬度坐标.数据表中保存有场地的定 ...
- 流媒体学习计划表——pr
参考教程 视频:b站oeasy 书籍:<adobe premiere pro cc 2018经典教程> 学习教训 一定要多做--实践是检验真理的唯一标准 书籍补充理论知识,视频讲究实操(理 ...
- 动态自动配置Bean
概览 接口Condition 用于基于条件的自动配置,和注解@Conditional配合使用,可实现JavaBean的动态自动配置 自定义实现动态配置Bean 定义一个接口和两个实现类 定义两个Con ...
- 一不小心,我就上传了 279674 字的 MySQL 学习资料到 github 上了
自从2019年11月我们出版了<千金良方--MySQL 性能优化金字塔法则>一书之后,持续不断有人来询问我MySQL 4 个系统字典库相关的问题,因为篇幅原因,书中并没有完整收录4个字典库 ...
- slow SQL
一.介绍 慢查询日志可用于查找需要很长时间才能执行的查询,因此是优化的候选者.但是,检查长慢的查询日志可能是一项耗时的任务. 二.配置 # 查看: slow_query_log 慢SQL开关 slow ...
- xshell界面变成半透明的怎么办?
在工具——选项查看选项卡去掉使窗口透明的前的勾就可以了
