Python Ethical Hacking - Malware Packaging(4)
Converting Python Programs to Linux Executables
Note: You can not execute the program on Linux by double click.
Install the PyInstaller.
pip3 install PyInstaller
Covert the Python Program to Linux executable.
pyinstaller --onefile --noconsole reverse_backdoor.py
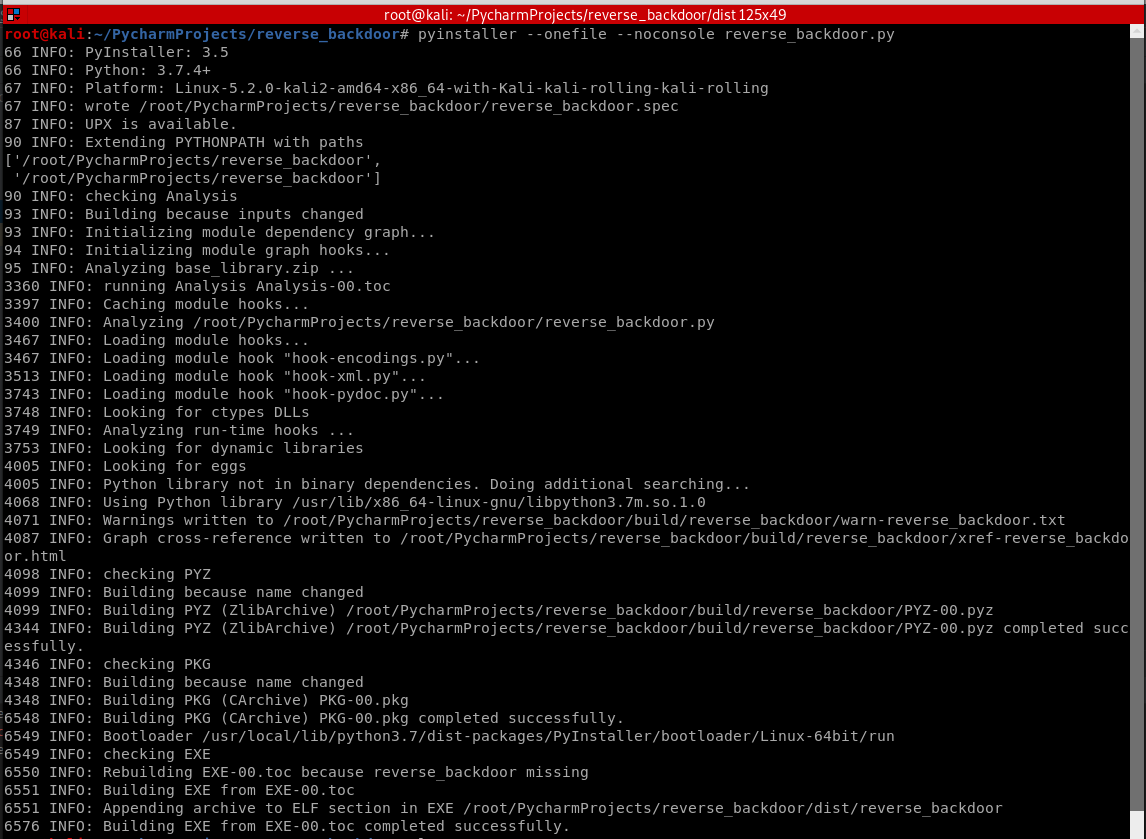
The executable file in Linux has no extension.
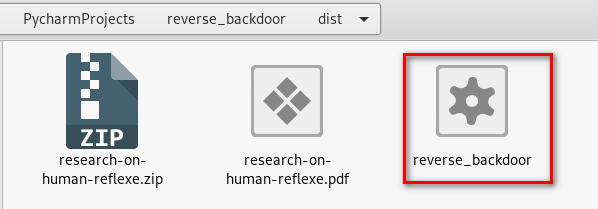
Move the executable to DebianBuster and run this program.
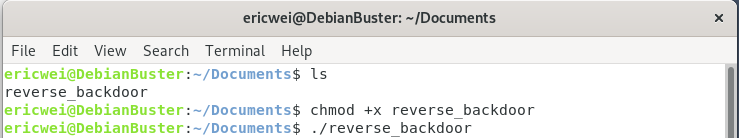
The connection is established successfully.
Python Ethical Hacking - Malware Packaging(4)的更多相关文章
- Python Ethical Hacking - Malware Packaging(2)
PACKAGING FOR WINDOWS FROM LINUX For best results package the program from the same OS as the target ...
- Python Ethical Hacking - Malware Packaging(1)
PACKAGING Convert python program into an executable that: Packages all program files into a single e ...
- Python Ethical Hacking - Malware Packaging(3)
Convert Python Programs to OS X Executables https://files.pythonhosted.org/packages/4a/08/6ca123073a ...
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - Malware Analysis(4)
DOWNLOAD_FILE Download files on a system. Once packaged properly will work on all operating systems. ...
- Python Ethical Hacking - Malware Analysis(3)
Stealing WiFi Password Saved on a Computer #!/usr/bin/env python import smtplib import subprocess im ...
- Python Ethical Hacking - Malware Analysis(2)
Filtering Command Output using Regex #!/usr/bin/env python import smtplib import subprocess import r ...
- Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD A generic executable that downloads & executes files. Disadvantag ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- VUE+ELEMENT-UI的后台项目封装组件--查询form的封装
最近项目打算重构,项目的模块几乎都是以后台查询展示的传统的增删改差模式,所以卑微的我想要自己封装一下查询form,先上效果图 子组件页面: <template> <div class ...
- vue 入门, todoList
# 实现逻辑: > * 技术栈> 1. 生命周期,creatd( 创建后执行)> 2. methods': 调用事件方法,结果不会缓存> 3. Watch : 监听器,监听输 ...
- Java并发编程-深入探讨synchronized实现原理
synchronized这个关键字对应Java程序猿来说是非常的熟悉,只要遇到要解决线程安全问题的地方都会使用这个关键字.接下来一起来探讨一下synchronized到底时怎么实现线程同步,使用syn ...
- springboot自动装配原理
最近开始学习spring源码,看各种文章的时候看到了springboot自动装配实现原理.用自己的话简单概括下. 首先打开一个基本的springboot项目,点进去@SpringBootApplica ...
- Python3-shutil模块-高级文件操作
Python3中的shutil模块提供了对文件和容器文件的一些高级操作 shutil.copy(src, dst) 拷贝文件,src和dst为路径的字符串表示,copy()会复制文件数据和文件权限,但 ...
- 学习oracle的SQL语句 练习
--1.查询emp表,显示薪水大于2000,且工作类别是MANAGER的雇员信息 select * from emp where sal > 2000and job = 'MANAGER'; - ...
- autocomplete 之 ASP.NET
<link href="CSS/jquery.autocomplete.css" rel="stylesheet" type="text/css ...
- QT Creator配置环境和安装
原文链接:https://blog.csdn.net/qq_33154343/java/article/details/78587699 补充下其中缺少的步骤:安装后缺少QT GUI Applicat ...
- DBMS_METADATA.GET_DDL查出不存在的列SYS_C00014_20070116:47:09$
DBMS_METADATA.GET_DDL查出不存在的列SYS_C00014_20070116:47:09$ 前言 很久很久以前,有多久呢? 有多久了,等等我看下截图的日期(溜︿( ̄︶ ̄)︿). 哦, ...
- Spring Cloud系列教程第九篇-Eureka自我保护机制
Spring Cloud系列教程第九篇-Eureka自我保护机制 本文主要内容: 1:自我保护介绍 2:导致原因分析 3:怎么禁止自我保护 本文是由凯哥(凯哥Java:kagejava)发布的< ...
