Referenced:http://www.petenetlive.com/KB/Article/0000869
Problem
I had to set this up for a client this week, I’ve setup a DMZ on a 5505 before and I’ve setup other VLANs to do other jobs, e.g. visitor Internet access. But this client needed a secondary VLAN setting up for IP Phones. In addition I needed to route traffic between both the internal VLANs.
I did an internet search and tried to find some configs I could reverse engineer, the few I found were old (Pre version 8.3) ones and the little info I got were more people in forums asking why theirs did not work. So I built a firewall with 8.2 code, then worked out how to do it, then upgraded the firewall to version 9.1. Finally I picked out the relevant parts of the upgraded config.
Here's the scenario I'm going to use for this example.
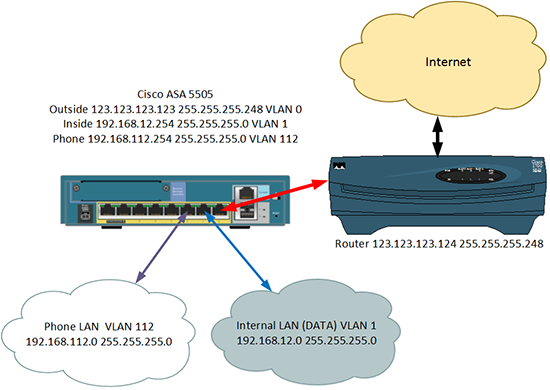
Solution
Before we start, yes I know the ASA is a firewall not a router! A better solution would be to have either a router behind the firewall or, (as is more common) a switch that is layer 3 capable, i.e it can route.
Your ASA MUST have a Security Plus licence to be able to do this. Check your license version.
The commands you use will be different if your firewall is running an operating system earlier than 8.3, check your ASA version and proceed to the correct set of commands.
For Firewalls running an Operating System OLDER than 8.3 go here
How to Setup VLAN Routing on an ASA 5505 (Version 8.3 and Newer)
1. Connect to the firewall, go to enable mode, then go to configure terminal mode.
User Access Verification
Password: Type help or '?' for a list of available commands. Petes-ASA> enable Password: ******** Petes-ASA# configure terminal Petes-ASA(config)#
2. As in the diagram (above) I have three VLANs, VLAN 0 is outside and will be connected to Ethernet 0/0. VLAN 1 is inside and will be connected to Ethernet 0/1. VLAN 112 is for my phones and will be connected to Ethernet 0/2. Here I setup the IP addresses, and add the VLANs to the physical interfaces.
Note: I don't need to Add VLAN 1 to Ethernet 0/1, because all ports are in VLAN 1 by default.
Petes-ASA(config)# interface Ethernet0/0 Petes-ASA(config-if)# switchport access vlan 2 Petes-ASA(config-if)# interface Ethernet0/2 Petes-ASA(config-if)# switchport access vlan 112 Petes-ASA(config-if)# interface Vlan1 Petes-ASA(config-if)# nameif inside Petes-ASA(config-if)# security-level 100 Petes-ASA(config-if)# ip address 192.168.12.254 255.255.255.0 Petes-ASA(config-if)# interface Vlan2 Petes-ASA(config-if)# nameif outside Petes-ASA(config-if)# security-level 0 Petes-ASA(config-if)# ip address 123.123.123.123 255.255.255.248 Petes-ASA(config-if)# interface Vlan112 Petes-ASA(config-if)# nameif PHONE_VLAN_112 Petes-ASA(config-if)# security-level 100 Petes-ASA(config-if)# ip address 192.168.112.254 255.255.255.0
3. To get traffic working to the internet you will need to specify a 'route' to your outside router.
Petes-ASA(config)# route outside 0.0.0.0 0.0.0.0 123.123.123.124
4. Turn on 'Hair Pinning' (the ability to route traffic back out of the same interface it came in through) and allow traffic to pass between interfaces.
Petes-ASA(config)# same-security-traffic permit inter-interface Petes-ASA(config)# same-security-traffic permit intra-interface
5. Out of the box, if you have not configured any access-lists then you can skip this step, as traffic will flow from a more secure interface (the inside and the phone one) to a less secure interface (the outside one). Here I'm going to use an ACL and allow all traffic anyway.
Petes-ASA(config)# access-list VLAN112_outbound extended permit ip 192.168.112.0 255.255.255.0 any Petes-ASA(config)# access-list outbound extended permit ip 192.168.12.0 255.255.255.0 any Petes-ASA(config)# access-group outbound in interface inside Petes-ASA(config)# access-group VLAN112_outbound in interface PHONE_VLAN_112
6. Now setup 'dynamic' NAT so that all traffic leaving both the inside VLAN and the Phone VLAN network get NATTEDto the public IP address.
Petes-ASA(config)# object network obj_any Petes-ASA(config-network-object)# subnet 0.0.0.0 0.0.0.0 Petes-ASA(config-network-object)# nat (inside,outside) dynamic interface Petes-ASA(config-network-object)# object network obj_any-01 Petes-ASA(config-network-object)# subnet 0.0.0.0 0.0.0.0 Petes-ASA(config-network-object)# nat (PHONE_VLAN_112,outside) dynamic interface
7. Now setup 'static' NAT so that traffic travelling between the inside VLAN and the phone VLAN does NOT getNATTED.
Petes-ASA(config)# object network obj-192.168.12.0 Petes-ASA(config-network-object)# subnet 192.168.12.0 255.255.255.0 Petes-ASA(config-network-object)# nat (inside,PHONE_VLAN_112) static 192.168.112.0 Petes-ASA(config-network-object)# object network obj-192.168.112.0 Petes-ASA(config-network-object)# subnet 192.168.112.0 255.255.255.0 Petes-ASA(config-network-object)# nat (PHONE_VLAN_112,inside) static 192.168.112.0
8. Enable routing, and set the MTU for all three VLANs.
Petes-ASA(config)# router eigrp 500 Petes-ASA(config-router)# network 192.168.12.0 255.255.255.0 Petes-ASA(config-router)# network 192.168.112.0 255.255.255.0 Petes-ASA(config-router)# passive-interface outside Petes-ASA(config-router)# exit Petes-ASA(config)# mtu inside 1500 Petes-ASA(config)# mtu outside 1500 Petes-ASA(config)# mtu PHONE_VLAN_112 1500
9. Save the changes, and give it a test.
Petes-ASA(config)# write memory Building configuration... Cryptochecksum: aab5e5a2 c707770d f7350728 d9ac34de [OK] Petes-ASA(config)#
Full Config for you to Copy and Paste;
interface Ethernet0/0 switchport access vlan 2 ! interface Ethernet0/1 ! interface Ethernet0/2 switchport access vlan 112 ! interface Vlan1 nameif inside security-level 100 ip address 192.168.12.254 255.255.255.0 ! interface Vlan2 nameif outside security-level 0 ip address 123.123.123.123 255.255.255.248 ! interface Vlan112 nameif PHONE_VLAN_112 security-level 100 ip address 192.168.112.254 255.255.255.0 ! same-security-traffic permit inter-interface same-security-traffic permit intra-interface ! access-list VLAN112_outbound extended permit ip 192.168.112.0 255.255.255.0 any access-list outbound extended permit ip 192.168.12.0 255.255.255.0 any ! object network obj-192.168.12.0 subnet 192.168.12.0 255.255.255.0 nat (inside,PHONE_VLAN_112) static 192.168.112.0 object network obj-192.168.112.0 subnet 192.168.112.0 255.255.255.0 nat (PHONE_VLAN_112,inside) static 192.168.112.0 object network obj_any subnet 0.0.0.0 0.0.0.0 nat (inside,outside) dynamic interface object network obj_any-01 subnet 0.0.0.0 0.0.0.0 nat (PHONE_VLAN_112,outside) dynamic interface ! mtu inside 1500 mtu outside 1500 mtu PHONE_VLAN_112 1500 ! access-group outbound in interface inside access-group VLAN112_outbound in interface PHONE_VLAN_112 ! router eigrp 500 network 192.168.12.0 255.255.255.0 network 192.168.112.0 255.255.255.0 passive-interface outside ! route outside 0.0.0.0 0.0.0.0 123.123.123.124
How to Setup VLAN Routing on an ASA 5505 (Pre Version 8.3)
1. Connect to the firewall, go to enable mode, then go to configure terminal mode.
User Access Verification
Password: Type help or '?' for a list of available commands. Petes-ASA> enable Password: ******** Petes-ASA# configure terminal Petes-ASA(config)#
2. 2. As in the diagram (above) I have three VLANs, VLAN 0 is outside and will be connected to Ethernet 0/0. VLAN 1 is inside and will be connected to Ethernet 0/1. VLAN 112 is for my phones and will be connected to Ethernet 0/2. Here I setup the IP addresses, and add the VLANs to the physical interfaces.
Note: I don't need to Add VLAN 1 to Ethernet 0/1 because all ports are in VLAN 1 by default.
Petes-ASA(config)# interface Ethernet0/0 Petes-ASA(config-if)# switchport access vlan 2 Petes-ASA(config-if)# interface Ethernet0/2 Petes-ASA(config-if)# switchport access vlan 112 Petes-ASA(config-if)# interface Vlan1 Petes-ASA(config-if)# nameif inside Petes-ASA(config-if)# security-level 100 Petes-ASA(config-if)# ip address 192.168.12.254 255.255.255.0 Petes-ASA(config-if)# interface Vlan2 Petes-ASA(config-if)# nameif outside Petes-ASA(config-if)# security-level 0 Petes-ASA(config-if)# ip address 123.123.123.123 255.255.255.248 Petes-ASA(config-if)# interface Vlan112 Petes-ASA(config-if)# nameif PHONE_VLAN_112 Petes-ASA(config-if)# security-level 100 Petes-ASA(config-if)# ip address 192.168.112.254 255.255.255.0
3. To get traffic working to the internet you will need to specify a 'route' to your outside router.
Petes-ASA(config)# route outside 0.0.0.0 0.0.0.0 123.123.123.124
4. Turn on 'Hair Pinning' (the ability to route traffic back out of the same interface it came in through). and allow traffic to pass between interfaces.
Petes-ASA(config)# same-security-traffic permit inter-interface Petes-ASA(config)# same-security-traffic permit intra-interface
5. Out of the box, if you have not configured any access-lists then you can skip this step, as traffic will flow from a more secure interface (the inside and the phone one) to a less secure interface (the outside one). Here I'm going to use an ACL and allow all traffic anyway.
Petes-ASA(config)# access-list VLAN112_outbound extended permit ip 192.168.112.0 255.255.255.0 any Petes-ASA(config)# access-list outbound extended permit ip 192.168.12.0 255.255.255.0 any Petes-ASA(config)# access-group outbound in interface inside Petes-ASA(config)# access-group VLAN112_outbound in interface PHONE_VLAN_112
6. Enable NAT so that all traffic leaving both the inside VLAN and the Phone VLAN network get NATTED to the publicIP address.
Petes-ASA(config)# global (outside) 1 interface Petes-ASA(config)# nat (inside) 1 0.0.0.0 0.0.0.0 Petes-ASA(config)# nat (PHONE_VLAN_112) 1 0.0.0.0 0.0.0.0
7. Now setup 'static' NAT so that traffic travelling between the inside VLAN and the phone VLAN does NOT getNATTED.
Petes-ASA(config)# static (inside,PHONE_VLAN_112) 192.168.112.0 192.168.12.0 netmask 255.255.255.0 Petes-ASA(config)# static (PHONE_VLAN_112,inside) 192.168.112.0 192.168.112.0 netmask 255.255.255.0
8. Enable routing, and set the MTU for all three VLANs.
Petes-ASA(config)# router eigrp 500 Petes-ASA(config-router)# network 192.168.12.0 255.255.255.0 Petes-ASA(config-router)# network 192.168.112.0 255.255.255.0 Petes-ASA(config-router)# passive-interface outside Petes-ASA(config-router)# exit Petes-ASA(config)# mtu inside 1500 Petes-ASA(config)# mtu outside 1500 Petes-ASA(config)# mtu PHONE_VLAN_112 1500
9. Save the changes, and give it a test.
Petes-ASA(config)# write memory Building configuration... Cryptochecksum: aab5e5a2 c707770d f7350728 d9ac34de [OK] Petes-ASA(config)#
Full Config for you to Copy and Paste;
interface Vlan1 nameif inside security-level 100 ip address 192.168.12.254 255.255.255.0 ! interface Vlan2 nameif outside security-level 0 ip address 123.123.123.123 255.255.255.248 ! interface Vlan112 nameif PHONE_VLAN_112 security-level 100 ip address 192.168.112.254 255.255.255.0 ! interface Ethernet0/0 switchport access vlan 2 ! interface Ethernet0/1 ! interface Ethernet0/2 switchport access vlan 112 ! same-security-traffic permit inter-interface same-security-traffic permit intra-interface ! access-list VLAN112_outbound extended permit ip 192.168.112.0 255.255.255.0 any access-list outbound extended permit ip 192.168.12.0 255.255.255.0 any ! mtu inside 1500 mtu outside 1500 mtu PHONE_VLAN_112 1500 ! global (outside) 1 interface nat (inside) 1 0.0.0.0 0.0.0.0 nat (PHONE_VLAN_112) 1 0.0.0.0 0.0.0.0 ! static (inside,PHONE_VLAN_112) 192.168.112.0 192.168.12.0 netmask 255.255.255.0 static (PHONE_VLAN_112,inside) 192.168.112.0 192.168.112.0 netmask 255.255.255.0 ! access-group outbound in interface inside access-group VLAN112_outbound in interface PHONE_VLAN_112 ! router eigrp 500 network 192.168.12.0 255.255.255.0 network 192.168.112.0 255.255.255.0 passive-interface outside ! route outside 0.0.0.0 0.0.0.0 123.123.123.124
- CISCO ASA 5505 经典配置案例
nterface Vlan2 nameif outside ----------------------------------------对端口命名外端口 security-level 0 -- ...
- Cisco ASA 5505配置详解(v8.3之前版本)
在配ASA 5505时用到的命令 2009-11-22 22:49 nat-control命令 在6.3的时候只要是穿越防火墙都需要创建转换项,比如:nat:static等等,没有转换项是不能穿越防火 ...
- Cisco ASA intra-interface routing
LAN1和LAN2的默认路由指向各自的ASA,各ASA中设置对方LAN的静态路由指向ROUTER,打开ASA的intra-interface traffic,关闭LAN1和LAN2地址互相访问的NAT ...
- Cisco ASA 配置案例---anyconnect拨通后所有流量从服务器端出去
一.目的: 1.Cisco ASA之Lan端能正常上网. 2.anyconnect端所有流量从Cisco ASA的Outside出去. 3.anyconnect端能访问Cisco ASA的Inside ...
- Cisco ASA使用证书加密
使用ASDM配置HTTPS证书加密anyconnect连接 一.在没有使用证书的情况下每次连接VPN都会出现如下提示 ASA Version: 8.4.(1) ASDM Version: 6.4.(7 ...
- Cisco ASA端口映射
Cisco ASA 端口映射设置 1.使用ASDM进入到配置页面,点开NAT Rules,然后新增Network Object,NAT选项如下图所示设定. 下图设定外网IP映射到内网IP地址192.1 ...
- Cisco ASA 高级配置
Cisco ASA 高级配置 一.防范IP分片攻击 1.Ip分片的原理: 2.Ip分片的安全问题: 3.防范Ip分片. 这三个问题在之前已经详细介绍过了,在此就不多介绍了.详细介绍请查看上一篇文章:I ...
- Cisco asa 5510升级IOS和ASDM
asa asa(config)# dir ...
- cisco ASA ios升级或恢复
cisco ASA ios升级或恢复 一.升级前准备工作 1.准备好所要升级的IOS文件及对应的ASDM文件 2.在一台电脑上架设好tftp,设置好目录,与防火墙进行连接(假设电脑IP为192.168 ...
随机推荐
- Codeforces Round #308 (Div. 2)----C. Vanya and Scales
C. Vanya and Scales time limit per test 1 second memory limit per test 256 megabytes input standard ...
- VBA SQLServer 基本操作
读取MS SQL Server数据表数据,并将它保存到excel工作表中 Sub ReturnSQLrecord() 'sht 为excel工作表对象变量,指向某一工作表 Dim i As Int ...
- mysql 索引长度限制
MyISAM存储引擎引键的长度综合不能超过1000字节 InnoDB单列索引长度不能超过767bytes,联合索引还有一个限制是3072
- PHP Mongodb 基本操作
<?php include "config/config.inc.php";$host = $config['host'];$port = $config['port']; ...
- mongodb的监控与性能优化
一.mongodb的监控 mongodb可以通过profile来监控数据,进行优化. 查看当前是否开启profile功能用命令 db.getProfilingLevel() 返回level等级,值为 ...
- Octopus系列之开发过程各个技术点
自定义了页面周期 使用唯一的一个VelocityEngine全局的静态实例,优化了小泥鳅blog中每次请求都要创建VelocityEngine实例对象,减少了对象的开销 通过UA判断请求来自的设备,从 ...
- Qml一些技巧
1.从ListView中获取当前选中项 myList.currentItem.children[0].text 可以获取ListView的选择项的一个个元素.注意children的使用.
- ubuntu 设置静态ip
1. 为网卡配置静态IP地址 编辑文件/etc/network/interfaces: sudo vi /etc/network/interfaces 并用下面的行来替换有关eth0的行: # The ...
- Js练习题之字数判断
目标:控制某个栏目里每行字数,当字数超出时,以省略号显示 $("元素").each(function(){ var maxlength=9; //最大字数 if($(this).t ...
- C 记录
为什么调用 sqrt 函数报错显示未定义 一.调用此函数时,要先引用头文件:#include <math.h>二.linux gcc 编译时,如果用到了 math中的函数,要手工加入函数库 ...

