Lab 6-1
LABS
The goal of the labs for this chapter is to help you to understand the overall functionality of a program by analyzing code constructs. Each lab will guide you through discovering and analyzing a new code construct. Each lab builds on the previous one, thus creating a single, complicated piece of malware with four constructs. Once you’ve finished working through the labs, you should be able to more easily recognize these individual constructs when you encounter them in malware.
Lab 6-1
In this lab, you will analyze the malware found in the file Lab06-01.exe.
Questions and Short Answers
What is the major code construct found in the only subroutine called by main?
A: The major code construct is an
ifstatement located at 0x401000.What is the subroutine located at 0x40105F?
A:
printfis the subroutine located at 0x40105F.What is the purpose of this program?
A: The program checks for an active Internet connection. If an active connection is found, it prints “Success: Internet Connection.” If a connection is not found, it prints “Error 1.1: No Internet.” This program can be used by malware to check for a connection before attempting to connect to the Internet.
Detailed Analysis
We begin by performing basic static analysis on this executable. Looking at the imports, we see that the DLL WININET.dll and the function InternetGetConnectedState are imported. The Windows Internet (WinINet) API enables applications to interact with HTTP protocols to access Internet resources.
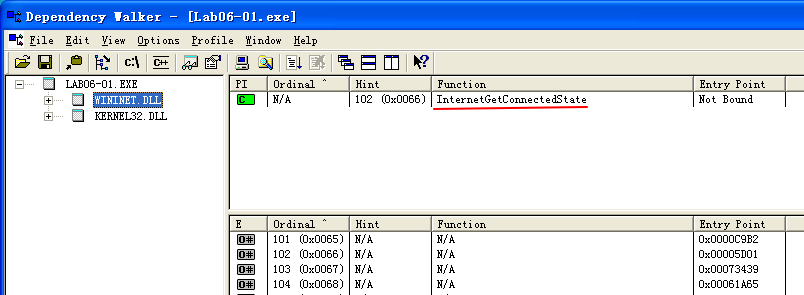
Using MSDN (InternetGetConnectedState), we learn this Windows API function checks the status of the Internet connection for the local system. The strings Error 1.1: No Internet and Success: Internet Connection hint that this program may check for an active Internet connection on the system.
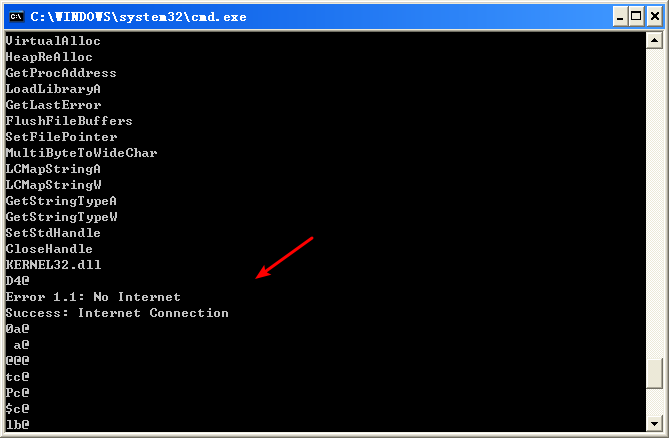
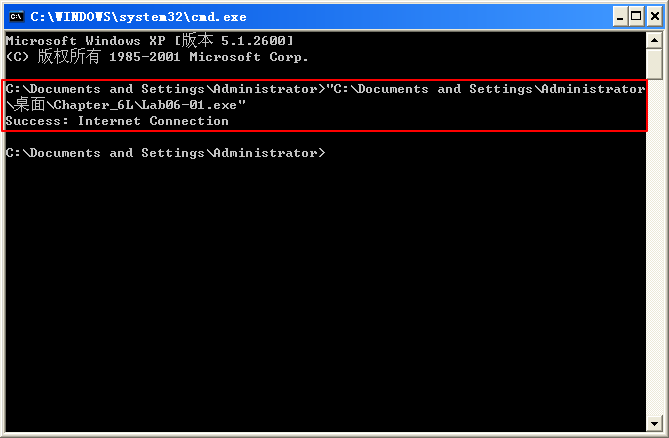
Next, we perform basic dynamic analysis on this executable. Nothing overly exciting happens when this executable is run from the command line. It simply prints “Success: Internet Connection” and then terminates.
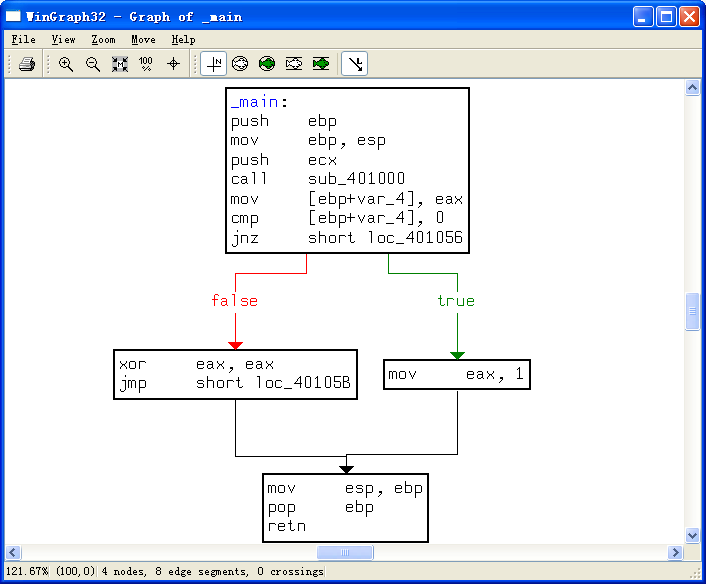
Finally, we load the file into IDA Pro for full analysis. Much of this disassembly is generated by the compiler, so we need to be careful to avoid going down rabbit holes of irrelevant code. Therefore, we start from the main function, which is typically where the code written by the malware author begins. In this case, the main function starts at 0x401040. The main function calls the function at 0x401000, which appears to be a key function of interest because it is the only one called by main. Figure 6-1L shows a flow graph of this function.
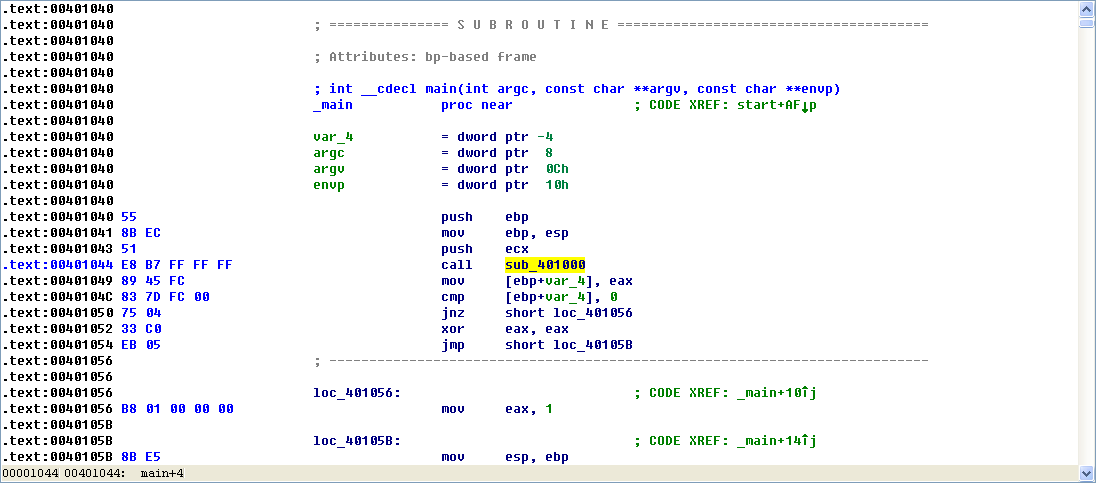
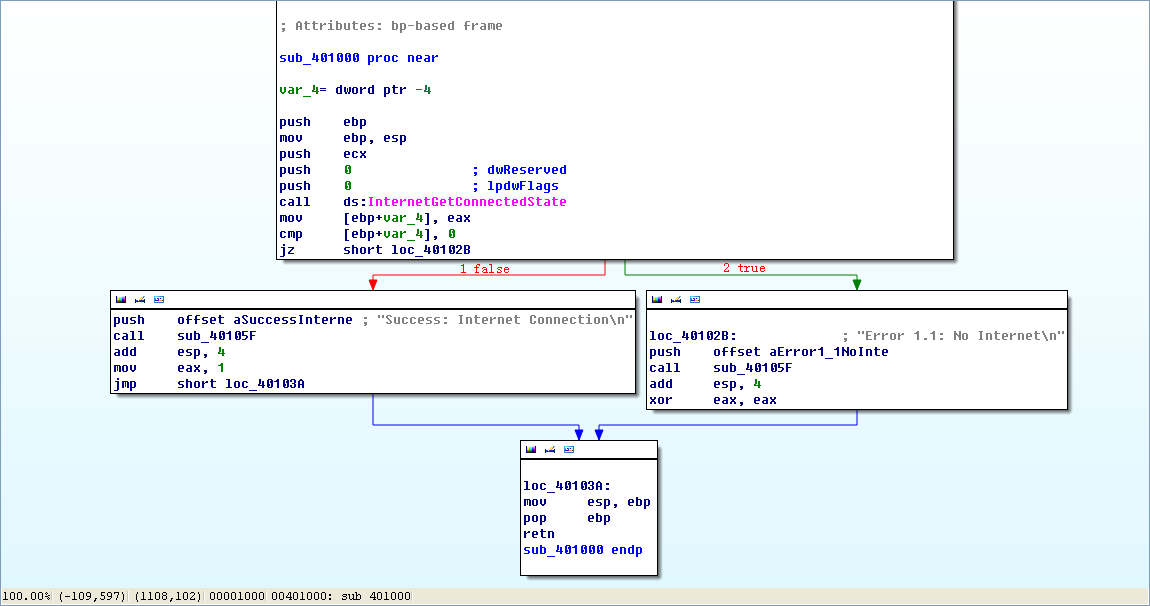
Figure 6-1L: Disassembly flow graph of the function at 0x401000
Now we graph this function in IDA Pro using View -> Graphs -> Flow chart. Looking at this graph and code, we see a common code construct: two different code paths depend on the result of the call to InternetGetConnectedState. The cmp instruction is used to compare the result contained in EAX to 0, and then the jz instruction is used to control the flow.
The MSDN page on InternetGetConnectedState further states that the function returns 1 if there is an active Internet connection; otherwise it returns 0. Therefore, the code will take the false branch at \({\color{red}1}\) if the result is 0 because the zero flag (ZF) will be clear; otherwise, it will take the true branch at \({\color{red}2}\). The code construct used in this function is an if statement.
The function calls the subroutine at 0x40105F in two locations, but if we dive into that function, we will quickly get lost in a rabbit hole. This function is printf. Surprisingly, both the IDA Pro commercial and freeware versions will not always recognize and label the printf function. Therefore, we must look for certain signals that hint at an unlabeled call to printf. One easy way to tell is by identifying parameters pushed onto the stack before the call to the subroutine. Here, in both cases, a format string is pushed onto the stack. The \n at the end of a string denotes a line feed. Also, given the context and the string itself, we can deduce that the function is printf. Therefore, we rename the function to printf, so that it is marked as such throughout the code, as shown in Figure 6-1L. Once the printf function is called, we see that EAX is set to either 1 or 0 before the function returns.
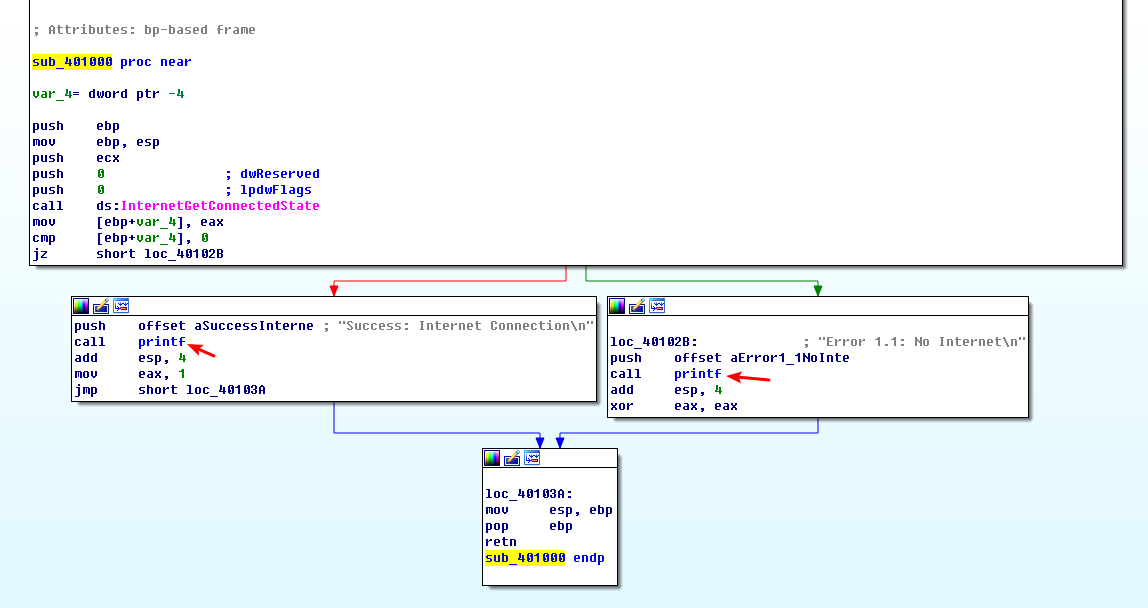
To summarize, this function checks for an active Internet connection, and then prints the result of its check, followed by returning a 1 if it is connected and 0 if it is not. Malware often performs a similar check for a valid Internet connection.
Preference
Lab 6-1的更多相关文章
- MIT 6.828 JOS学习笔记18. Lab 3.2 Part B: Page Faults, Breakpoints Exceptions, and System Calls
现在你的操作系统内核已经具备一定的异常处理能力了,在这部分实验中,我们将会进一步完善它,使它能够处理不同类型的中断/异常. Handling Page Fault 缺页中断是一个非常重要的中断,因为我 ...
- MIT 6.828 JOS学习笔记17. Lab 3.1 Part A User Environments
Introduction 在这个实验中,我们将实现操作系统的一些基本功能,来实现用户环境下的进程的正常运行.你将会加强JOS内核的功能,为它增添一些重要的数据结构,用来记录用户进程环境的一些信息:创建 ...
- MIT 6.828 JOS学习笔记16. Lab 2.2
Part 3 Kernel Address Space JOS把32位线性地址虚拟空间划分成两个部分.其中用户环境(进程运行环境)通常占据低地址的那部分,叫用户地址空间.而操作系统内核总是占据高地址的 ...
- MIT 6.828 JOS学习笔记15. Lab 2.1
Lab 2: Memory Management lab2中多出来的几个文件: inc/memlayout.h kern/pmap.c kern/pmap.h kern/kclock.h kern/k ...
- MIT 6.828 JOS学习笔记10. Lab 1 Part 3: The kernel
Lab 1 Part 3: The kernel 现在我们将开始具体讨论一下JOS内核了.就像boot loader一样,内核开始的时候也是一些汇编语句,用于设置一些东西,来保证C语言的程序能够正确的 ...
- MIT 6.828 JOS学习笔记7. Lab 1 Part 2.2: The Boot Loader
Lab 1 Part 2 The Boot Loader Loading the Kernel 我们现在可以进一步的讨论一下boot loader中的C语言的部分,即boot/main.c.但是在我们 ...
- python opencv 利用Lab空间把春天的场景改为秋天
前一段时间实现了Reinhard颜色迁移算法,感觉挺有意思的,然后在代码上随意做了一些更改,有了一些发现,把Lab通道的a通道值改为127左右,可以将绿色改为黄色,而对其他颜色的改动非常小,因此可以将 ...
- Acadia Lab 228 + Lab 222
又是一对串烧实验,布好线后非常方便就可以一起完成. 连线方案一模一样: Lab 228 数码管骰子 核心代码如下: def loop() : global cnt global btn_read,se ...
- Acadia Lab 203 + Lab 231
在做完 Lab 6 之后,惊觉选做实验缺口很大,于是遍历了一遍夏任务,找到了一条最省力的路线. 做完 Lab 6 的连线不用拆,可以接下来做以下两个实验: Lab 203 网络时钟 核心代码如下: v ...
- GJM : 【技术干货】给The Lab Renderer for Unity中地形添加阴影
感谢您的阅读.喜欢的.有用的就请大哥大嫂们高抬贵手"推荐一下"吧!你的精神支持是博主强大的写作动力以及转载收藏动力.欢迎转载! 版权声明:本文原创发表于 [请点击连接前往] ,未经 ...
随机推荐
- python ---16 初识面向对象
面向对象 一 .面向对象和面向过程比较 ①面向过程:一切以事物的发展流程为核心 优点:负责的问题流程化,编写相对简单 缺点:可扩展性差 ②面向对象:一切以对象为中心. 一切皆为对象. 具体的某一 ...
- Oracle使用——oracle 忘记用户密码登录
背景 有时候我们忘记了oracle登录的用户密码,甚至是用户名称都不确定,应该怎么登陆呢 操作系统 CentOS7 Oracle12c 操作步骤 使用sqlplus登录系统:sqlplus / a ...
- 自动化测试系列:Selenium UI自动化解决iframe定位问题
更多原创测试技术文章同步更新到微信公众号 :三国测,敬请扫码关注个人的微信号,感谢! 原文链接:http://www.cnblogs.com/zishi/p/6735116.html 一个阴雨霏霏 ...
- javaScript随机数取值方法
Math.random()方法返回0到1之间的一个随机数,不包括0和1 如若想取的一个范围的随机数可套用下面的公式: 一.X+开始数-1=结束数 二.Math.floor(Math.random()* ...
- Intellij IDEA 安装配置Gradle
1.安装 到官网链接下载最新的bin版本,解压到 D:\Program Files (x86)\JetBrains\IDEA Configuration And Cache\gradle 配置环境变量 ...
- RHEL7防火墙策略设置
注意查看firewall防火墙状态,并设置. 打开防火墙且没有放行端口的情况下rhel7这台机器是ping不通的. 放行端口需要永久放行,加--permernant,否则重启后失效,仍然无法访问该端口 ...
- (转)Understanding, generalisation, and transfer learning in deep neural networks
Understanding, generalisation, and transfer learning in deep neural networks FEBRUARY 27, 2017 Thi ...
- ZooKeeper分布式过程协同技术详解2——了解ZooKeeper
这个服务如何实现这些协作方面的原语? ZooKeeper基础
- sql server数据库自动备份
SqlServer 数据库自动备份的两种解决方案 SQL Server中的角色(服务器级别和数据库级别角色) SqlServer服务器角色和数据库角色相关操作
- Leetcode121-Best Time to Buy and Sell Stock I - Easy
I Say you have an array for which the ith element is the price of a given stock on day i. If you wer ...
