Codeforces Round #356 (Div. 2) C
1 second
256 megabytes
standard input
standard output
This is an interactive problem. In the output section below you will see the information about flushing the output.
Bear Limak thinks of some hidden number — an integer from interval [2, 100]. Your task is to say if the hidden number is prime or composite.
Integer x > 1 is called prime if it has exactly two distinct divisors, 1 and x. If integer x > 1 is not prime, it's called composite.
You can ask up to 20 queries about divisors of the hidden number. In each query you should print an integer from interval [2, 100]. The system will answer "yes" if your integer is a divisor of the hidden number. Otherwise, the answer will be "no".
For example, if the hidden number is 14 then the system will answer "yes" only if you print 2, 7 or 14.
When you are done asking queries, print "prime" or "composite" and terminate your program.
You will get the Wrong Answer verdict if you ask more than 20 queries, or if you print an integer not from the range [2, 100]. Also, you will get the Wrong Answer verdict if the printed answer isn't correct.
You will get the Idleness Limit Exceeded verdict if you don't print anything (but you should) or if you forget about flushing the output (more info below).
After each query you should read one string from the input. It will be "yes" if the printed integer is a divisor of the hidden number, and "no" otherwise.
Up to 20 times you can ask a query — print an integer from interval [2, 100] in one line. You have to both print the end-of-line character and flush the output. After flushing you should read a response from the input.
In any moment you can print the answer "prime" or "composite" (without the quotes). After that, flush the output and terminate your program.
To flush you can use (just after printing an integer and end-of-line):
- fflush(stdout) in C++;
- System.out.flush() in Java;
- stdout.flush() in Python;
- flush(output) in Pascal;
- See the documentation for other languages.
Hacking. To hack someone, as the input you should print the hidden number — one integer from the interval [2, 100]. Of course, his/her solution won't be able to read the hidden number from the input.
yes
no
yes
2
80
5
composite
no
yes
no
no
no
58
59
78
78
2
prime
The hidden number in the first query is 30. In a table below you can see a better form of the provided example of the communication process.
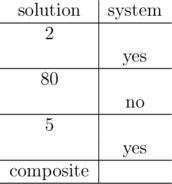
The hidden number is divisible by both 2 and 5. Thus, it must be composite. Note that it isn't necessary to know the exact value of the hidden number. In this test, the hidden number is 30.
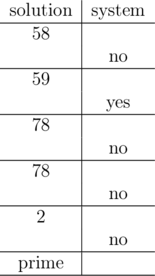
59 is a divisor of the hidden number. In the interval [2, 100] there is only one number with this divisor. The hidden number must be 59, which is prime. Note that the answer is known even after the second query and you could print it then and terminate. Though, it isn't forbidden to ask unnecessary queries (unless you exceed the limit of 20 queries).
题意:
题解:
#include<iostream>
#include<cstring>
#include<cstdio>
#include<bits/stdc++.h>
#include<algorithm>
#include<queue>
#define ll __int64
using namespace std;
int aa[]={,,,};
int pr[]={,,,,,,,,,,,,,,,,,,,,,,,,};
char a[];
int x,y=;
int n=,z,i,t=;
int main()
{
for(i=;i<;i++)
{
printf("%d\n",pr[i]);
fflush(stdout);
scanf("%s",a);
if(strcmp(a,"yes")==)
y++;
else
n++;
if(y>=)
break;
}
for(i=;i<;i++)
{
printf("%d\n",aa[i]);
fflush(stdout);
scanf("%s",a);
if(strcmp(a,"yes")==)
y++;
else
n++;
if(y>=)
break;
}
if(y>=)
{
printf("composite\n");
fflush(stdout);
}
else
{
printf("prime\n");
fflush(stdout);
}
return ;
}
Codeforces Round #356 (Div. 2) C的更多相关文章
- Codeforces Round #356 (Div. 2)-B
B. Bear and Finding Criminals 链接:http://codeforces.com/contest/680/problem/B There are n cities in B ...
- Codeforces Round #356 (Div. 2)-A
A. Bear and Five Cards 题目链接:http://codeforces.com/contest/680/problem/A A little bear Limak plays a ...
- Codeforces Round #356 (Div. 2) C. Bear and Prime 100(转)
C. Bear and Prime 100 time limit per test 1 second memory limit per test 256 megabytes input standar ...
- Codeforces Round #356 (Div. 2)B. Bear and Finding Criminals(水题)
B. Bear and Finding Criminals time limit per test 2 seconds memory limit per test 256 megabytes inpu ...
- Codeforces Round #356 (Div. 2)A. Bear and Five Cards(简单模拟)
A. Bear and Five Cards time limit per test 2 seconds memory limit per test 256 megabytes input stand ...
- 并查集+bfs+暴力滑窗 Codeforces Round #356 (Div. 2) E
http://codeforces.com/contest/680/problem/E 题目大意:给你一个n*n的图,然后图上的 . (我们下面都叫做‘点’)表示可以走,X表示不能走,你有如下的操作, ...
- dfs Codeforces Round #356 (Div. 2) D
http://codeforces.com/contest/680/problem/D 题目大意:给你一个大小为X的空间(X<=m),在该空间内,我们要尽量的放一个体积为a*a*a的立方体,且每 ...
- Codeforces Round #356 (Div. 1) D. Bear and Chase 暴力
D. Bear and Chase 题目连接: http://codeforces.com/contest/679/problem/D Description Bearland has n citie ...
- Codeforces Round #356 (Div. 2) E. Bear and Square Grid 滑块
E. Bear and Square Grid 题目连接: http://www.codeforces.com/contest/680/problem/E Description You have a ...
- Codeforces Round #356 (Div. 2) D. Bear and Tower of Cubes dfs
D. Bear and Tower of Cubes 题目连接: http://www.codeforces.com/contest/680/problem/D Description Limak i ...
随机推荐
- pycharm快捷键一览
编辑(Editing) Ctrl + Space 基本的代码完成(类.方法.属性)Ctrl + Alt + Space 快速导入任意类Ctrl + Shift + Enter 语句完成Ctrl + P ...
- python 一些基础知识
Python 注释的原理: 原理:根据对象的引用计数器,对象创建会给对象一个引用计数器属性.如果该属性的值为0,那么该对象会被释放.创建一个字符串对象,但是没有任何引用,计数器为0. Python小整 ...
- win7同时安装python2和python3
1.下载python2和python3版本. 2.安装python3 1>选择添加PATH路径到系统. 2>为所有用户安装python. 3.安装python2 1>为所 ...
- php面向对象(2)值传递
PHP中值传递方式,2中 值传递:传递的时候,拷贝的是数据本身.默认都是值传递 结果:传递完成,有了2份同样的数据,且2个变量“相互独立”,不会相互影响 引用传递:传递的时候,拷贝的是引用关系(数据的 ...
- Redis ---------- Sort Set排序集合类型
sortset是(list)和(set)的集中体现 与set的相同点: string类型元素的集合 不同点: sortset的元素:值+权 适合场合 获得最热门前5个帖子的信息 例如 select * ...
- HDU 3364 高斯消元
Lanterns Time Limit: 2000/1000 MS (Java/Others) Memory Limit: 65536/65536 K (Java/Others)Total Su ...
- C# 创建新线程
首先需要包含命名空间 using System.Threading; 然后创建进程 Thread th = new Thread(new ThreadStart(ThreadMethod)); //创 ...
- Numpy基础数据结构 python
Numpy基础数据结构 NumPy数组是一个多维数组对象,称为ndarray.其由两部分组成: 实际的数据 描述这些数据的元数据 1.一维数组 import numpy as np ar = np.a ...
- Oozie 实战之 Hive
1.编辑job.propertiers nameNode=hdfs://cen-ubuntu.cenzhongman.com:8020 jobTracker=localhost:8032 queueN ...
- 5 Post实现django表单
本节大纲 1.article-detail 评论页面的准备工作 (1)model层创建评论模型 class Comment(models.Model): """创建评论模 ...
