Python Ethical Hacking - TROJANS Analysis(5)
Spoofing File Extention - A trick.
Use the Kali Linux Program - Characters
1. Open the program.

2. Find Right-to-left Override.
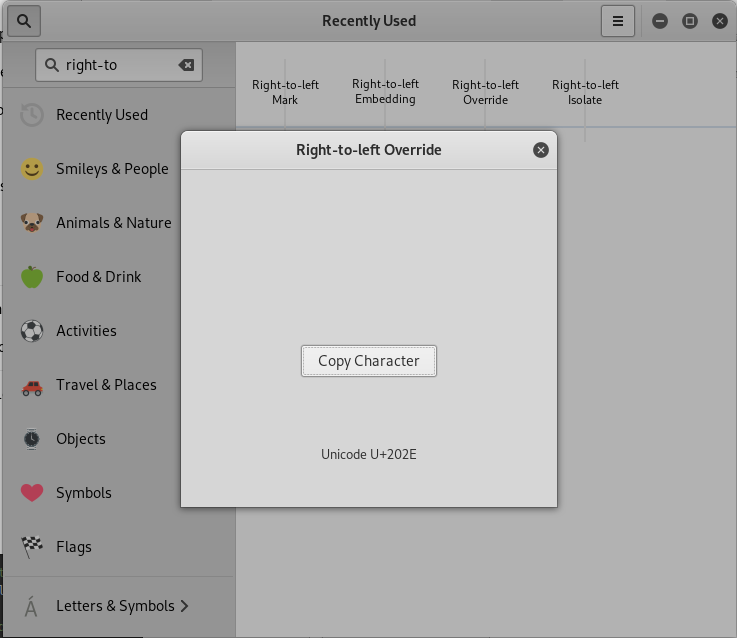
3. Copy Character and paste to the notepad.
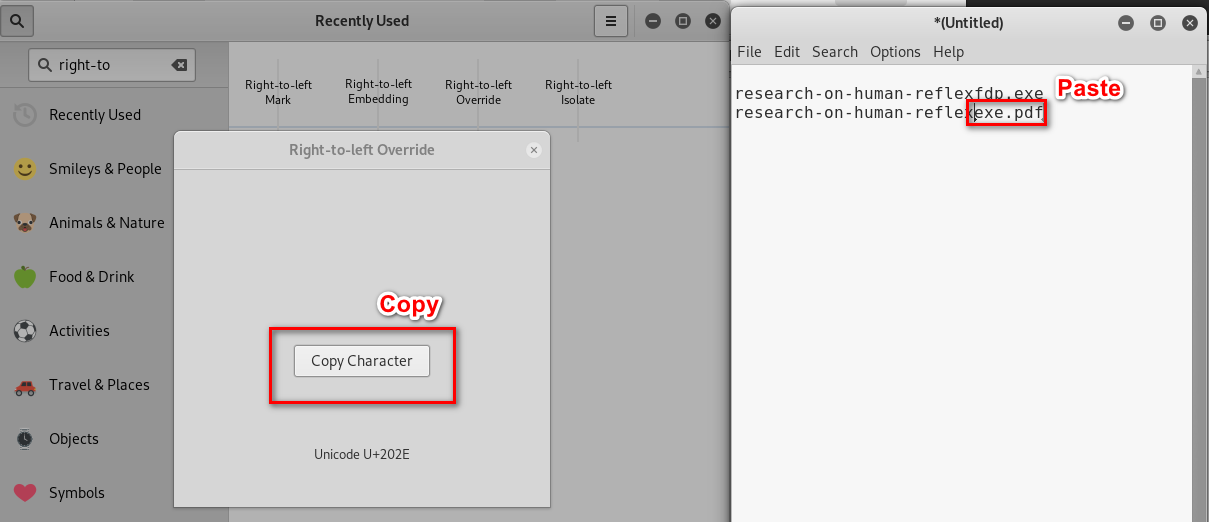
4. Rename the evil file.

5. Note: To avoid the browser replace the character, compress it.
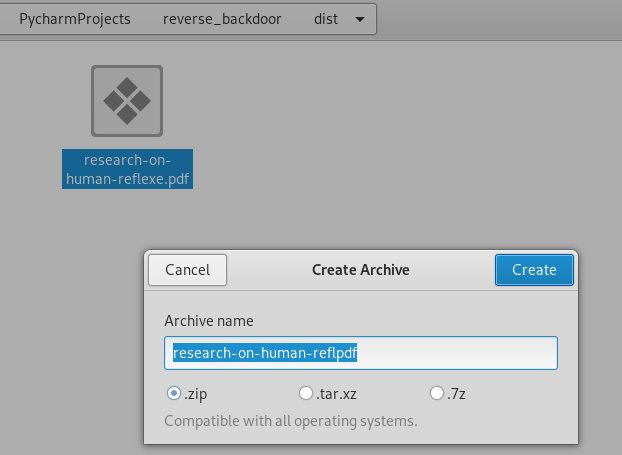
6. Download and extract to the Windows Folder.
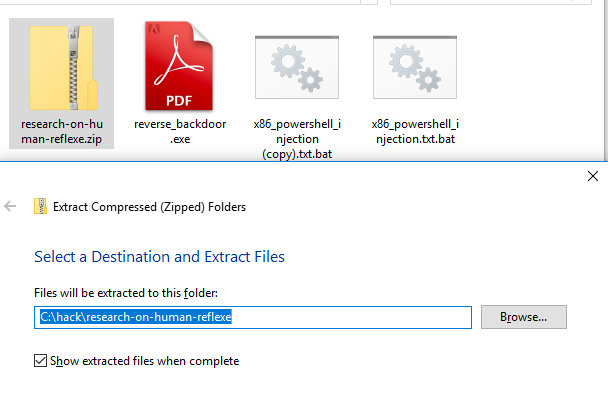

7. Open this "pdf" file and the communication is established.

Python Ethical Hacking - TROJANS Analysis(5)的更多相关文章
- Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD A generic executable that downloads & executes files. Disadvantag ...
- Python Ethical Hacking - TROJANS Analysis(1)
TROJANS A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc). When e ...
- Python Ethical Hacking - TROJANS Analysis(4)
Adding Icons to Generated Executables Prepare a proper icon file. https://www.iconfinder.com/ Conver ...
- Python Ethical Hacking - TROJANS Analysis(3)
BYPASSING ANTI-VIRUS PROGRAMS AV programs detect viruses based on: 1. Code - compare files to huge d ...
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - Malware Analysis(4)
DOWNLOAD_FILE Download files on a system. Once packaged properly will work on all operating systems. ...
- Python Ethical Hacking - Malware Analysis(3)
Stealing WiFi Password Saved on a Computer #!/usr/bin/env python import smtplib import subprocess im ...
- Python Ethical Hacking - Malware Analysis(2)
Filtering Command Output using Regex #!/usr/bin/env python import smtplib import subprocess import r ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- 百度文本编辑器的toolbars属性值描述
toolbars: [ [ 'anchor', //锚点 'undo', //撤销 'redo', //重做 'bold', //加粗 ...
- umi 调试
最近在umi. 设置一个layout字段, 结果左边菜单栏就出现了. 很神奇. 决定对这个库一探究竟. 我是一个喜欢看底层库的人,网上所有的启动方式都是yarn或者npm start 启动服务.然后 ...
- 学习 SQL Server (5) :视图,索引,事务和锁+T_SQL
--=============== 视图的创建 =================. --create view 视图名 as 查询语句--注意:视图查询中的字段不能重名-- 视图中的数据是‘假数据’ ...
- @PathVariable @RequestParam@RequestBody
@PathVariable 当使用@RequestMapping URI template 样式映射时, 即 someUrl/{paramId}, 这时的paramId可通过 @Pathvariabl ...
- Spring系列.SpEL表达式
Spring表达式语言 SpEL语言是一种强大的表达式语言,支持在运行时查询和操作对象.SpEL表达式不一定要创建IOC容器后才能使用.用户完全可以单独调用SpEL的API来独立的使用时SpEL表达式 ...
- Python三大器之装饰器
Python三大器之装饰器 开放封闭原则 一个良好的项目必定是遵守了开放封闭原则的,就比如一段好的Python代码必定是遵循PEP8规范一样.那么什么是开放封闭原则?具体表现在那些点? 开放封闭原则的 ...
- 入门大数据---Spring+Mybatis+Phoenix整合
一.前言 使用 Spring+Mybatis 操作 Phoenix 和操作其他的关系型数据库(如 Mysql,Oracle)在配置上是基本相同的,下面会分别给出 Spring/Spring Boot ...
- 近期Java高级开发岗面试总结
原文出处:公众号:编程大道 作者:walking 近期Java高级开发岗面试总结 哈喽大家好,我是walking,这是我的公众号:编程大道. 很久没和大家见面了,文章更新的速度略有延后.这个公众号断断 ...
- Oracle 存储过程中的临时表数据自动清空
问题叙述: 用 EXECUTE IMMEDIATE 动态往临时表插入数据,跟踪发现插入临时表后数据会立马清空,按理说等存储过程执行完才会清空临时表才对,现在是执行插入语句后下一步验证就发现临时表就没有 ...
- Spring中使用注解时启用<context:component-scan/>
在spring中使用注解方式时需要在spring配置文件中配置组件扫描器:http://blog.csdn.net/j080624/article/details/56277315 <conte ...
