Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark
WIreshark is a network protocol analyser that is designed to help network administartors to keep track of what is happening in their network and analyse all the packtes.
Wireshark works by logging each packet that flows through the device.
Usage:
python2 mitmf.py --arp --spoof -i wlan0 --gateway 10.0.0.1 --target 10.0.0.22 wireshark
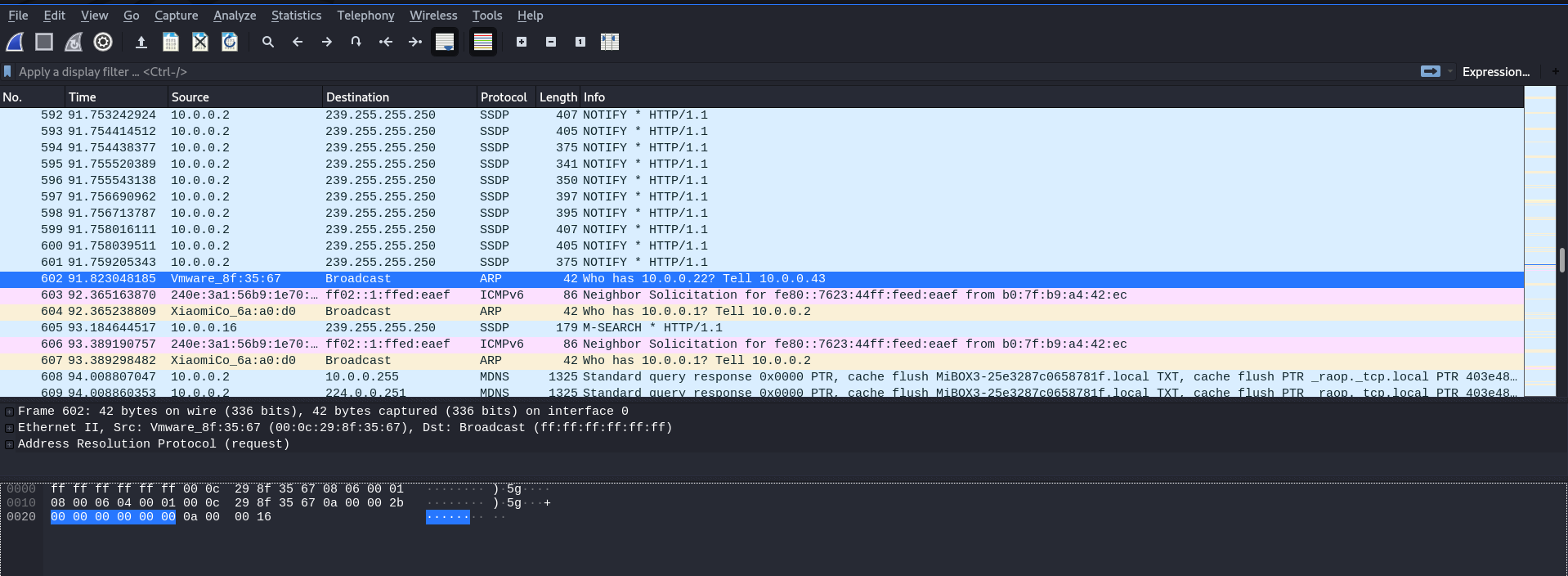
The wireshark can analysis the packages from target machine.
Ethical Hacking - NETWORK PENETRATION TESTING(22)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(21)
MITM - Code Injection Inject javascript or HTML code into pages. Code gets executed on target machin ...
- Ethical Hacking - NETWORK PENETRATION TESTING(20)
MITM - Capturing Screen Of Target & Injecting a Keylogger ScreenShotter Plugin: ScreenShotter: U ...
- Ethical Hacking - NETWORK PENETRATION TESTING(19)
MITM-DNS Spoofing DNS Spoofing allows us to redirect any request to a certain domain to another doma ...
- Ethical Hacking - NETWORK PENETRATION TESTING(17)
MITM - bypassing HTTPS Most websites use https in their login pages, this means that these pages are ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
随机推荐
- go 项目目录结构
网上有很多误人子弟的教程, 说项目下必须要有src, 傻逼玩意. 正确的路径应该是这样的: 所有go项目路径 src 项目1 项目2 项目N pkg bin 不是所有项目下必须建src, pk ...
- Kafka源码解析(二)---Log分析
上一篇文章讲了LogSegment和Log的初始化,这篇来讲讲Log的主要操作有哪些. 一般来说Log 的常见操作分为 4 大部分. 高水位管理操作 日志段管理 关键位移值管理 读写操作 其中关键位移 ...
- maven依赖冲突以及解决方法
什么是依赖冲突 依赖冲突是指项目依赖的某一个jar包,有多个不同的版本,因而造成类包版本冲突 依赖冲突的原因 依赖冲突很经常是类包之间的间接依赖引起的.每个显式声明的类包都会依赖于一些其它的隐式类包, ...
- [ C++ ] 勿在浮沙筑高台 —— 内存管理(18~31p) std::alloc
部分内容个人感觉不是特别重要,所以没有记录了.其实还是懒 embedded pointers 把对象的前四字节当指针用. struct obj{ struct obj *free_list_link; ...
- Idea激活JRebel
选择license激活 UUID 生成地址: http://www.uuid.online 激活地址 http://jrebel-license.jiweichengzhu.com/ UUID
- Object.defineProperty()更改对象中的函数
这个方法可以修改javascript中的对象的属性值,但是例子只讲了如何修改对象中的属性值,却没有讲如何修改对象里面的方法,所以这里补充下: 例子代码如下: <!DOCTYPE html> ...
- C#数据结构与算法系列(十九):选择排序算法(SelectSort)
1.介绍 选择排序算法属于内部排序算法,是从欲排序的数据中,按指定的规则选出某一元素,再依规定交换位置达到排序的目的 时间复杂度:O(n^2) 双层for 2.思想 选择排序(select sorti ...
- python黑帽子之tcp客户端
在渗透测试过程中,我们经常会需要创建一个tcp客户端来连接服务,发送垃圾数据,进行模糊测试等任务,所以我们来用python创建一个简单的tcp客户端. import sockettarget_host ...
- IDEA创建SpringBoot的多模块项目教程
最近在写一个多模块的SpringBoot项目,基于过程总了一些总结,故把SpringBoot多个模块的项目创建记录下来. 首先,先建立一个父工程: (1)在IDEA工具栏选择File->New- ...
- 《HelloGitHub》第 51 期
兴趣是最好的老师,HelloGitHub 就是帮你找到兴趣! 简介 分享 GitHub 上有趣.入门级的开源项目. 这是一个面向编程新手.热爱编程.对开源社区感兴趣 人群的月刊,月刊的内容包括:各种编 ...
