Suricata的规则解读(默认和自定义)
不多说,直接上干货!
见suricata官网
https://suricata.readthedocs.io/en/latest/rules/index.html
一、Suricata的规则所放位置
下面,是我使用的SELKS里安装的Suricata默认自带规则。
见博客
Stamus Networks的产品SELKS(Suricata IDPS、Elasticsearch 、Logstash 、Kibana 和 Scirius )的下载和安装(带桌面版和不带桌面版)(图文详解)
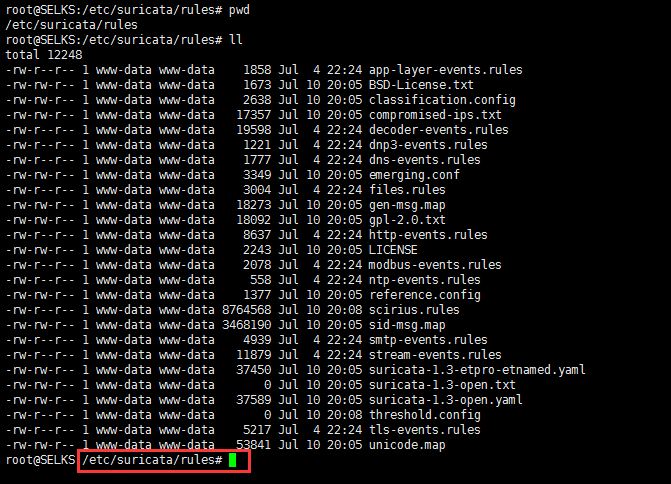
root@SELKS:/etc/suricata/rules# ll
total
-rw-r--r-- www-data www-data Jul : app-layer-events.rules
-rw-rw-r-- www-data www-data Jul : BSD-License.txt
-rw-rw-r-- www-data www-data Jul : classification.config
-rw-rw-r-- www-data www-data Jul : compromised-ips.txt
-rw-r--r-- www-data www-data Jul : decoder-events.rules
-rw-r--r-- www-data www-data Jul : dnp3-events.rules
-rw-r--r-- www-data www-data Jul : dns-events.rules
-rw-rw-r-- www-data www-data Jul : emerging.conf
-rw-r--r-- www-data www-data Jul : files.rules
-rw-rw-r-- www-data www-data Jul : gen-msg.map
-rw-rw-r-- www-data www-data Jul : gpl-2.0.txt
-rw-r--r-- www-data www-data Jul : http-events.rules
-rw-rw-r-- www-data www-data Jul : LICENSE
-rw-r--r-- www-data www-data Jul : modbus-events.rules
-rw-r--r-- www-data www-data Jul : ntp-events.rules
-rw-rw-r-- www-data www-data Jul : reference.config
-rw-r--r-- www-data www-data Jul : scirius.rules
-rw-rw-r-- www-data www-data Jul : sid-msg.map
-rw-r--r-- www-data www-data Jul : smtp-events.rules
-rw-r--r-- www-data www-data Jul : stream-events.rules
-rw-rw-r-- www-data www-data Jul : suricata-1.3-etpro-etnamed.yaml
-rw-rw-r-- www-data www-data Jul : suricata-1.3-open.txt
-rw-rw-r-- www-data www-data Jul : suricata-1.3-open.yaml
-rw-r--r-- www-data www-data Jul : threshold.config
-rw-r--r-- www-data www-data Jul : tls-events.rules
-rw-rw-r-- www-data www-data Jul : unicode.map
root@SELKS:/etc/suricata/rules#
下面,是我源码编译安装的Suricata默认自带规则。
见博客
基于CentOS6.5下Suricata(一款高性能的网络IDS、IPS和网络安全监控引擎)的搭建(图文详解)(博主推荐)
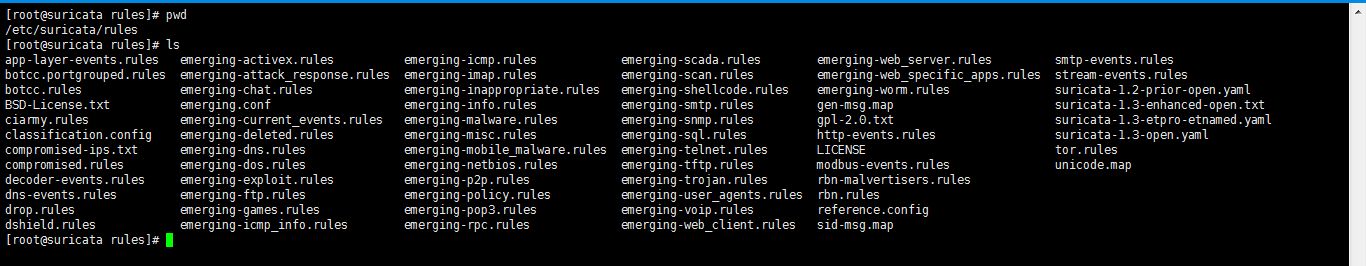
[root@suricata rules]# pwd
/etc/suricata/rules
[root@suricata rules]# ls
app-layer-events.rules emerging-activex.rules emerging-icmp.rules emerging-scada.rules emerging-web_server.rules smtp-events.rules
botcc.portgrouped.rules emerging-attack_response.rules emerging-imap.rules emerging-scan.rules emerging-web_specific_apps.rules stream-events.rules
botcc.rules emerging-chat.rules emerging-inappropriate.rules emerging-shellcode.rules emerging-worm.rules suricata-1.2-prior-open.yaml
BSD-License.txt emerging.conf emerging-info.rules emerging-smtp.rules gen-msg.map suricata-1.3-enhanced-open.txt
ciarmy.rules emerging-current_events.rules emerging-malware.rules emerging-snmp.rules gpl-2.0.txt suricata-1.3-etpro-etnamed.yaml
classification.config emerging-deleted.rules emerging-misc.rules emerging-sql.rules http-events.rules suricata-1.3-open.yaml
compromised-ips.txt emerging-dns.rules emerging-mobile_malware.rules emerging-telnet.rules LICENSE tor.rules
compromised.rules emerging-dos.rules emerging-netbios.rules emerging-tftp.rules modbus-events.rules unicode.map
decoder-events.rules emerging-exploit.rules emerging-p2p.rules emerging-trojan.rules rbn-malvertisers.rules
dns-events.rules emerging-ftp.rules emerging-policy.rules emerging-user_agents.rules rbn.rules
drop.rules emerging-games.rules emerging-pop3.rules emerging-voip.rules reference.config
dshield.rules emerging-icmp_info.rules emerging-rpc.rules emerging-web_client.rules sid-msg.map
[root@suricata rules]#
二、Suricata的自定义规则所放位置和书写(重点)
这里,为了规范,我们一般是将自定义的规则也同默认规则在一个目录下。
源码编译安装的Suricata,我这里写了个小例子,见
使用 Suricata 进行入侵监控(一个简单小例子访问百度)
我这里呢,重点使用的是SELKS里的Suricata。(重点)
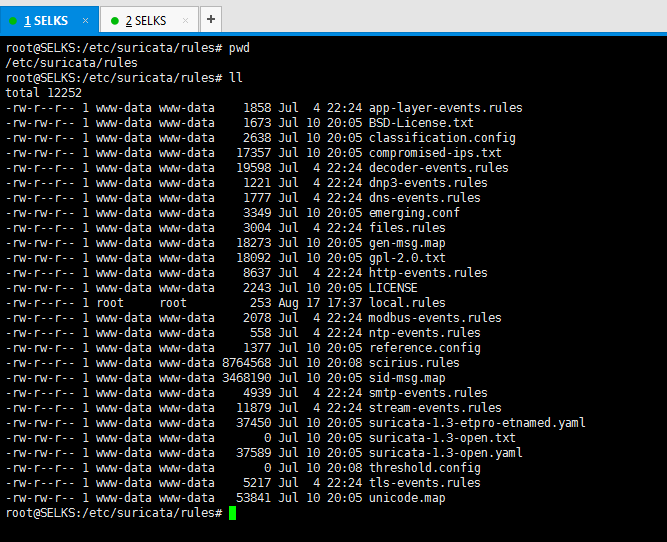
root@SELKS:/etc/suricata/rules# pwd
/etc/suricata/rules
root@SELKS:/etc/suricata/rules# ll
total
-rw-r--r-- www-data www-data Jul : app-layer-events.rules
-rw-rw-r-- www-data www-data Jul : BSD-License.txt
-rw-rw-r-- www-data www-data Jul : classification.config
-rw-rw-r-- www-data www-data Jul : compromised-ips.txt
-rw-r--r-- www-data www-data Jul : decoder-events.rules
-rw-r--r-- www-data www-data Jul : dnp3-events.rules
-rw-r--r-- www-data www-data Jul : dns-events.rules
-rw-rw-r-- www-data www-data Jul : emerging.conf
-rw-r--r-- www-data www-data Jul : files.rules
-rw-rw-r-- www-data www-data Jul : gen-msg.map
-rw-rw-r-- www-data www-data Jul : gpl-2.0.txt
-rw-r--r-- www-data www-data Jul : http-events.rules
-rw-rw-r-- www-data www-data Jul : LICENSE
-rw-r--r-- root root Aug : local.rules
-rw-r--r-- www-data www-data Jul : modbus-events.rules
-rw-r--r-- www-data www-data Jul : ntp-events.rules
-rw-rw-r-- www-data www-data Jul : reference.config
-rw-r--r-- www-data www-data Jul : scirius.rules
-rw-rw-r-- www-data www-data Jul : sid-msg.map
-rw-r--r-- www-data www-data Jul : smtp-events.rules
-rw-r--r-- www-data www-data Jul : stream-events.rules
-rw-rw-r-- www-data www-data Jul : suricata-1.3-etpro-etnamed.yaml
-rw-rw-r-- www-data www-data Jul : suricata-1.3-open.txt
-rw-rw-r-- www-data www-data Jul : suricata-1.3-open.yaml
-rw-r--r-- www-data www-data Jul : threshold.config
-rw-r--r-- www-data www-data Jul : tls-events.rules
-rw-rw-r-- www-data www-data Jul : unicode.map
root@SELKS:/etc/suricata/rules#
下面,我将逐个进行解释。
1、 SELKS里的suricata的app-layer-events.rules(非常重要)
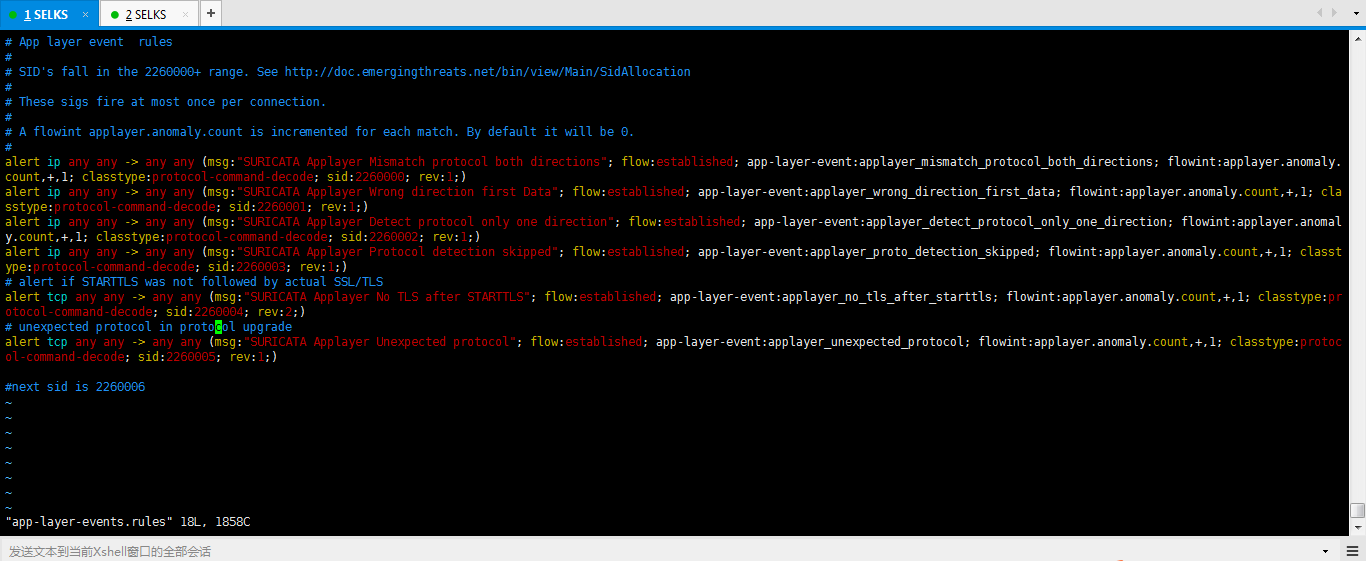
# App layer event rules
#
# SID's fall in the 2260000+ range. See http://doc.emergingthreats.net/bin/view/Main/SidAllocation
#
# These sigs fire at most once per connection.
#
# A flowint applayer.anomaly.count is incremented for each match. By default it will be .
#
alert ip any any -> any any (msg:"SURICATA Applayer Mismatch protocol both directions"; flow:established; app-layer-event:applayer_mismatch_protocol_both_directions; flowint:applayer.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert ip any any -> any any (msg:"SURICATA Applayer Wrong direction first Data"; flow:established; app-layer-event:applayer_wrong_direction_first_data; flowint:applayer.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert ip any any -> any any (msg:"SURICATA Applayer Detect protocol only one direction"; flow:established; app-layer-event:applayer_detect_protocol_only_one_direction; flowint:applayer.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert ip any any -> any any (msg:"SURICATA Applayer Protocol detection skipped"; flow:established; app-layer-event:applayer_proto_detection_skipped; flowint:applayer.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
# alert if STARTTLS was not followed by actual SSL/TLS
alert tcp any any -> any any (msg:"SURICATA Applayer No TLS after STARTTLS"; flow:established; app-layer-event:applayer_no_tls_after_starttls; flowint:applayer.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
# unexpected protocol in protocol upgrade
alert tcp any any -> any any (msg:"SURICATA Applayer Unexpected protocol"; flow:established; app-layer-event:applayer_unexpected_protocol; flowint:applayer.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;) #next sid is
2、 SELKS里的suricata的 BSD-License.txt (非常重要)
#*************************************************************
# Copyright (c) -, Emerging Threats
# All rights reserved.
#
# Redistribution and use in source and binary forms, with or without modification, are permitted provided that the
# following conditions are met:
#
# * Redistributions of source code must retain the above copyright notice, this list of conditions and the following
# disclaimer.
# * Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the
# following disclaimer in the documentation and/or other materials provided with the distribution.
# * Neither the name of the nor the names of its contributors may be used to endorse or promote products derived
# from this software without specific prior written permission.
#
# THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS AS IS AND ANY EXPRESS OR IMPLIED WARRANTIES,
# INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
# DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
# SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
# SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
# WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE
# USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
#
#*************************************************************
3、 SELKS里的suricata的 classification.config (非常重要)
#
# config classification:shortname,short description,priority
# #Traditional classifications. These will be replaced soon config classification: not-suspicious,Not Suspicious Traffic,
config classification: unknown,Unknown Traffic,
config classification: bad-unknown,Potentially Bad Traffic,
config classification: attempted-recon,Attempted Information Leak,
config classification: successful-recon-limited,Information Leak,
config classification: successful-recon-largescale,Large Scale Information Leak,
config classification: attempted-dos,Attempted Denial of Service,
config classification: successful-dos,Denial of Service,
config classification: attempted-user,Attempted User Privilege Gain,
config classification: unsuccessful-user,Unsuccessful User Privilege Gain,
config classification: successful-user,Successful User Privilege Gain,
config classification: attempted-admin,Attempted Administrator Privilege Gain,
config classification: successful-admin,Successful Administrator Privilege Gain,
config classification: rpc-portmap-decode,Decode of an RPC Query,
config classification: shellcode-detect,Executable Code was Detected,
config classification: string-detect,A Suspicious String was Detected,
config classification: suspicious-filename-detect,A Suspicious Filename was Detected,
config classification: suspicious-login,An Attempted Login Using a Suspicious Username was Detected,
config classification: system-call-detect,A System Call was Detected,
config classification: tcp-connection,A TCP Connection was Detected,
config classification: trojan-activity,A Network Trojan was Detected,
config classification: unusual-client-port-connection,A Client was Using an Unusual Port,
config classification: network-scan,Detection of a Network Scan,
config classification: denial-of-service,Detection of a Denial of Service Attack,
config classification: non-standard-protocol,Detection of a Non-Standard Protocol or Event,
config classification: protocol-command-decode,Generic Protocol Command Decode,
config classification: web-application-activity,Access to a Potentially Vulnerable Web Application,
config classification: web-application-attack,Web Application Attack,
config classification: misc-activity,Misc activity,
config classification: misc-attack,Misc Attack,
config classification: icmp-event,Generic ICMP event,
config classification: inappropriate-content,Inappropriate Content was Detected,
config classification: policy-violation,Potential Corporate Privacy Violation,
config classification: default-login-attempt,Attempt to Login By a Default Username and Password,
4、SELKS里的suricata的compromised-ips.txt (非常重要)
100.16.27.26
101.100.146.142
101.204.128.115
101.230.12.55
101.6.130.81
101.68.109.167
101.95.184.150
103.14.182.59
103.205.14.7
103.207.36.103
103.207.37.170
103.207.37.187
103.207.37.20
103.207.37.73
103.207.37.80
103.207.38.191
103.207.38.195
103.207.39.127
103.207.39.16
103.207.39.188
103.207.39.30
103.207.39.38
103.216.120.245
103.227.81.239
103.249.205.50
103.28.121.90
103.29.16.163
103.31.80.190
103.45.9.244
103.47.137.57
103.53.231.51
103.54.219.210
103.62.239.76
103.74.120.72
103.74.120.73
103.89.124.190
103.89.88.118
103.89.88.119
103.89.88.120
103.89.88.128
103.89.88.130
103.89.88.147
103.89.88.163
103.89.88.168
103.89.88.172
103.89.88.188
103.89.88.66
103.89.91.28
103.9.159.39
104.131.127.81
104.192.2.34
104.205.178.202
104.225.103.87
104.236.48.163
104.237.202.199
104.40.85.167
104.52.24.81
106.112.55.176
106.14.143.238
106.2.20.94
106.36.45.37
106.36.45.43
106.38.159.104
106.39.13.237
106.39.44.0
106.75.152.115
107.10.163.103
107.15.32.114
107.167.189.114
107.173.60.101
108.170.31.119
108.61.157.119
109.132.131.123
109.167.202.71
109.192.8.180
109.195.86.76
109.23.142.139
109.236.82.106
109.90.139.235
110.12.38.93
110.170.131.150
110.182.183.41
110.190.90.207
110.249.217.82
110.51.153.228
110.77.143.2
111.118.204.98
111.121.192.6
111.144.112.36
111.183.102.97
111.204.101.254
111.217.148.102
111.246.121.202
111.73.45.39
112.101.161.63
112.101.167.29
112.104.100.106
112.104.32.32
112.119.236.159
112.120.148.181
112.193.245.64
112.193.247.154
112.216.232.227
112.216.44.115
112.218.76.12
112.25.212.208
112.254.199.190
112.72.98.210
112.90.72.70
113.122.147.60
113.122.35.107
113.122.49.237
113.122.7.181
113.13.186.32
113.135.193.217
113.16.204.156
113.162.109.135
113.186.220.228
113.190.2.38
113.22.109.221
113.23.75.66
113.240.250.144
113.252.218.224
113.5.255.22
113.62.127.254
113.96.134.2
114.113.126.3
114.113.150.181
114.199.67.92
114.241.70.201
114.245.104.205
114.252.208.77
114.32.139.3
114.84.3.17
114.99.241.22
115.114.142.210
115.124.127.209
115.171.31.159
115.230.90.25
115.233.220.100
115.68.24.156
115.73.57.123
115.85.82.90
115.95.160.87
116.100.100.139
116.104.63.185
116.111.226.194
116.115.217.6
116.228.114.206
116.228.132.254
116.228.205.125
116.236.218.66
116.36.229.93
1.164.123.2
1.164.128.251
116.54.193.37
116.62.135.243
116.8.5.182
116.88.115.98
117.0.198.87
117.172.232.12
117.21.210.214
117.240.14.98
117.27.136.49
117.4.26.238
118.131.109.51
118.140.120.26
118.144.127.206
118.151.209.235
118.163.193.82
118.175.21.170
118.189.205.197
118.216.167.18
1.182.168.130
118.217.181.8
1.182.224.153
118.97.55.250
119.163.193.23
119.165.33.24
119.176.42.69
119.185.200.120
119.193.140.157
119.193.140.216
119.207.21.229
119.23.236.141
119.23.255.43
119.254.146.86
119.27.36.79
119.29.234.179
119.29.248.124
119.29.59.125
119.31.210.68
119.36.212.26
119.44.217.222
119.61.27.244
119.74.39.39
119.81.208.88
119.82.68.254
119.95.61.69
120.210.193.101
1.202.187.81
1.202.187.82
120.236.232.18
120.52.120.193
120.52.179.95
120.92.43.223
120.92.76.234
120.92.79.81
120.92.89.63
120.92.93.181
121.141.169.112
121.143.236.90
121.14.7.244
121.148.151.227
121.148.151.230
121.157.84.171
121.160.248.210
121.194.2.247
121.194.2.251
121.194.2.252
121.201.78.13
1.212.241.37
122.112.216.210
122.112.221.12
122.112.225.205
122.114.35.226
122.156.234.148
122.160.88.127
122.224.144.131
122.224.144.133
122.226.68.146
122.55.48.35
1.226.131.20
123.114.35.124
123.119.171.87
123.150.103.3
123.150.108.253
123.158.91.190
123.16.150.39
123.166.29.86
123.168.101.173
123.169.197.127
123.169.198.185
123.169.216.22
123.169.230.16
123.207.219.54
123.207.9.150
123.235.154.212
123.249.4.86
124.127.110.135
124.13.235.12
124.160.103.92
124.18.92.170
124.193.236.138
124.205.190.173
124.207.144.181
124.237.78.183
124.243.216.102
124.6.224.23
124.89.48.33
125.131.127.45
125.132.230.113
125.147.33.73
125.209.165.183
125.212.253.46
125.227.185.1
125.24.65.152
125.253.123.137
125.253.123.140
125.34.78.210
126.24.181.207
126.85.40.39
128.199.66.191
129.232.252.140
130.211.229.196
130.91.248.238
131.100.205.26
1.32.113.71
132.248.141.236
134.249.19.226
137.111.92.27
137.135.46.74
137.74.114.225
137.74.47.82
137.99.1.209
138.197.100.132
138.197.34.203
138.197.83.17
138.36.22.14
138.68.49.247
139.159.220.147
139.159.236.242
139.198.189.26
139.199.178.38
139.201.164.118
139.208.185.163
139.217.1.157
139.219.108.38
139.219.195.206
139.219.196.11
139.219.227.153
139.219.235.54
13.93.151.203
13.94.154.107
139.59.231.14
140.119.170.163
140.250.96.11
140.250.99.110
140.255.75.45
14.153.196.30
14.162.54.218
14.169.27.142
14.175.16.207
14.186.237.216
14.190.134.17
142.0.39.185
143.239.87.19
144.217.201.226
144.76.38.71
145.132.52.248
14.55.206.77
148.251.250.75
149.202.65.164
149.56.109.232
150.244.82.44
151.80.149.14
151.80.42.176
152.101.90.161
152.204.13.242
152.204.21.180
153.122.66.77
153.37.150.197
153.99.185.99
154.0.162.41
1.54.189.78
154.66.40.91
155.133.82.12
155.4.119.5
155.4.186.213
155.4.255.138
157.0.78.2
157.119.184.66
157.7.243.224
159.224.62.130
159.8.107.23
160.16.93.205
160.238.104.2
161.105.179.2
161.202.16.71
162.157.248.168
162.208.50.18
162.254.148.49
163.172.113.171
163.172.130.189
163.172.132.168
163.172.146.104
163.172.164.45
163.172.166.56
163.172.176.183
163.172.204.238
163.172.226.199
163.172.227.51
164.132.194.50
164.160.28.133
166.62.122.86
167.205.108.156
167.61.87.250
168.144.9.15
168.195.182.25
169.38.70.148
170.210.5.57
170.80.33.24
171.212.142.0
171.212.143.29
171.214.178.58
171.231.152.124
171.234.230.135
171.244.18.197
173.193.189.206
173.199.124.23
173.212.218.230
173.212.219.234
173.212.230.79
173.233.59.68
173.244.207.14
173.61.183.188
175.101.12.123
175.137.191.97
175.140.199.193
175.156.164.162
175.210.26.232
175.45.85.70
176.104.176.150
176.119.63.71
176.37.206.64
176.53.86.110
176.74.154.44
176.8.88.176
176.8.88.35
176.9.99.131
177.103.173.122
177.124.247.194
177.130.63.102
177.135.210.130
177.136.40.50
177.23.58.55
177.39.209.11
177.55.191.60
177.55.98.244
177.82.80.9
178.132.216.166
178.132.219.203
178.140.247.238
178.150.0.231
178.157.80.138
178.166.26.215
178.211.55.56
178.213.174.220
178.251.228.77
178.33.167.144
178.57.81.210
178.66.117.238
178.71.217.105
179.107.107.123
179.125.52.114
179.184.37.124
179.35.32.13
180.150.176.70
180.150.5.202
180.151.56.246
180.164.158.184
180.164.38.174
180.183.245.182
180.218.142.20
180.76.160.239
180.97.69.63
181.209.194.181
181.21.10.185
181.223.168.212
182.150.27.203
182.18.61.151
182.18.76.248
182.18.77.199
182.23.28.250
182.23.66.165
182.23.66.166
182.23.66.167
182.23.66.168
182.23.66.170
182.23.66.171
182.243.91.32
182.33.211.130
182.37.90.234
182.61.39.158
182.86.189.237
182.93.77.124
183.129.170.182
183.131.180.83
183.136.132.23
183.140.251.251
183.151.176.168
183.152.90.44
183.240.8.11
183.250.89.39
184.154.43.242
184.62.8.235
185.100.222.110
185.13.202.222
185.141.26.245
185.165.29.111
185.165.29.112
185.165.29.26
185.165.29.38
185.165.29.41
185.165.29.46
185.165.29.50
185.165.29.67
185.165.29.69
185.165.29.76
185.165.29.84
185.177.23.111
185.188.6.128
185.198.56.26
185.206.147.45
185.2.100.72
185.26.147.162
185.29.11.214
185.30.232.10
185.40.31.134
185.92.221.2
186.121.240.62
186.18.14.160
186.203.237.176
186.237.128.194
186.24.37.179
186.58.141.52
187.115.165.204
187.141.143.180
187.18.116.47
187.20.255.169
187.210.228.6
187.33.2.56
188.132.244.89
188.171.12.51
188.171.3.105
188.194.29.193
188.19.56.25
188.212.103.10
188.213.166.191
188.94.241.5
189.16.207.227
189.200.76.241
189.254.234.244
189.4.22.196
189.43.82.194
189.59.220.74
189.89.73.26
190.102.140.100
190.128.255.62
190.15.206.203
190.156.238.131
190.166.159.211
190.17.241.165
190.185.128.228
190.205.54.150
190.210.1.169
190.215.97.65
190.219.110.45
190.25.228.170
190.90.191.18
190.90.191.20
191.103.251.1
191.232.252.181
191.253.110.165
191.7.218.98
191.98.220.10
192.186.133.90
192.187.114.122
192.241.135.35
193.105.134.187
193.151.197.110
193.164.108.28
193.194.69.155
193.58.196.146
1.93.64.252
194.122.166.86
194.132.238.207
194.28.115.112
194.85.90.167
195.14.163.214
195.146.59.167
195.154.102.207
195.154.200.88
195.154.39.188
195.154.48.85
195.154.51.223
195.154.57.131
195.154.59.73
195.158.12.77
195.207.179.90
195.223.245.106
195.242.80.68
195.25.17.198
195.3.147.132
195.3.147.133
195.87.93.143
195.94.212.90
196.24.44.21
197.14.54.201
197.245.234.118
198.167.140.39
198.175.126.128
198.23.161.126
198.244.107.112
198.61.190.203
199.180.133.135
200.105.195.186
200.107.156.229
200.110.172.2
200.111.164.27
200.150.207.82
200.195.139.102
200.206.177.135
200.2.127.242
200.246.136.193
200.57.73.170
200.71.34.59
201.130.203.232
201.16.140.128
201.16.140.73
201.20.73.3
201.217.142.186
201.76.129.116
202.100.182.250
202.107.104.119
202.112.23.245
202.114.159.186
202.120.32.226
202.168.151.118
202.169.44.69
202.201.255.200
202.58.104.46
202.70.34.27
202.71.25.248
202.73.98.66
202.83.111.94
202.85.212.231
203.112.149.73
203.122.27.186
203.142.65.20
203.145.171.58
203.146.107.42
203.185.22.28
203.19.35.67
203.205.40.11
203.205.40.15
203.223.143.116
203.253.207.72
203.35.91.97
204.44.81.206
206.221.188.106
208.52.168.215
209.124.225.135
209.133.208.103
209.190.64.57
210.12.110.7
210.14.152.58
210.18.5.67
210.209.68.130
210.211.100.187
210.212.210.86
210.38.136.92
210.42.72.158
210.72.24.15
210.73.195.79
210.94.133.40
211.110.184.231
211.149.209.32
211.157.114.92
211.228.102.83
211.72.254.202
211.81.48.246
211.88.76.174
211.95.17.4
211.98.64.174
211.98.64.176
211.99.191.106
212.112.41.201
212.129.13.110
212.129.24.71
212.129.27.112
212.129.37.229
212.129.56.220
212.129.61.39
212.147.119.2
212.156.72.102
212.237.21.208
212.237.25.50
212.237.2.97
212.237.38.113
212.237.53.179
212.237.53.247
212.237.54.30
212.237.60.77
212.237.8.216
212.251.54.10
212.47.241.246
212.47.254.117
212.83.142.45
212.86.120.100
213.112.202.186
213.136.65.5
213.136.73.49
213.14.64.98
213.151.96.2
213.167.35.219
213.229.73.111
216.165.71.227
216.198.226.109
216.241.87.179
216.243.62.206
216.41.104.45
216.55.176.225
217.182.205.118
217.182.252.161
217.182.69.217
217.182.73.91
217.182.79.218
217.182.94.32
217.23.13.51
217.61.20.159
217.61.2.24
217.61.6.27
217.72.49.24
217.92.20.95
218.104.144.250
218.108.6.186
218.109.3.220
218.16.209.182
218.240.43.26
218.247.171.20
218.249.154.130
218.61.208.160
218.63.248.173
218.88.177.151
218.88.236.249
218.91.232.26
219.128.72.130
219.129.216.133
219.141.189.4
219.141.189.41
219.141.189.57
219.152.27.1
219.216.72.139
219.217.90.222
219.217.90.224
219.84.169.97
219.92.16.253
220.130.104.108
220.132.66.88
220.134.115.11
220.247.201.40
220.72.81.117
220.89.8.131
221.167.253.208
221.195.48.116
221.203.75.210
221.204.48.155
221.215.160.138
221.229.166.44
221.229.166.74
221.7.177.36
222.117.96.6
222.124.175.86
222.161.20.182
222.161.211.18
222.179.189.206
222.186.169.212
222.186.169.234
222.186.169.235
222.196.36.11
222.252.124.15
222.47.26.138
222.47.26.139
222.47.26.140
222.54.132.162
222.88.213.214
223.100.3.209
223.16.203.95
223.166.207.144
223.18.205.191
223.202.57.237
223.68.8.160
223.84.204.10
223.87.10.205
223.99.167.27
23.225.207.210
23.233.116.163
23.235.161.41
2.32.82.130
24.145.70.60
24.180.131.65
24.202.112.126
24.21.167.65
24.4.27.91
24.5.154.198
24.93.199.243
27.102.66.189
27.115.36.78
27.122.190.83
27.125.145.80
27.132.120.160
27.191.224.130
27.254.63.96
27.50.23.147
31.131.19.111
31.14.128.160
31.169.80.239
31.201.59.186
31.207.47.63
31.221.7.90
34.208.141.173
34.226.202.79
34.252.62.166
34.253.172.174
35.154.166.1
35.160.161.108
35.161.227.4
35.184.143.12
35.196.13.66
36.107.239.163
36.231.31.72
36.234.215.5
36.250.77.36
36.32.128.97
36.49.86.82
36.66.242.91
36.81.203.227
37.114.62.70
37.120.168.194
37.120.169.222
37.187.109.46
37.200.63.88
37.204.121.150
37.222.150.238
37.229.178.24
37.233.101.211
37.49.224.100
37.49.224.115
37.49.224.194
37.52.29.2
38.130.227.70
39.118.158.229
40.69.44.170
40.83.144.161
40.83.145.134
40.83.15.249
41.160.117.170
41.193.67.67
41.33.25.54
42.103.110.93
42.103.96.94
42.112.161.5
42.115.168.174
42.115.168.176
42.115.169.244
42.115.237.85
42.117.120.43
42.117.13.194
42.159.205.6
42.159.251.248
42.202.140.221
42.236.73.149
42.236.73.151
42.87.12.149
43.240.117.234
45.32.120.14
45.32.120.8
45.32.17.241
45.32.68.8
45.32.80.163
45.32.80.174
45.55.200.114
45.56.39.191
45.63.41.172
45.76.130.158
45.76.180.51
45.76.32.127
45.76.38.65
45.77.29.192
45.77.30.134
45.77.68.12
45.77.75.92
46.101.171.182
46.118.179.59
46.139.206.243
46.140.157.157
46.146.223.66
46.166.185.33
46.183.222.167
46.189.228.170
46.228.192.158
46.228.192.200
46.242.28.239
46.246.36.45
46.246.45.145
46.38.248.155
46.44.234.78
46.59.14.223
46.61.132.15
4.71.171.180
47.74.0.40
47.92.101.157
47.92.136.153
47.93.193.200
49.143.252.40
49.231.238.218
50.115.165.160
50.199.55.109
50.200.99.19
50.235.200.138
50.63.167.21
5.101.40.10
51.15.131.72
51.15.140.183
51.15.140.54
51.15.143.76
51.15.45.206
51.15.49.172
51.15.55.67
51.15.59.93
51.15.69.161
51.15.69.204
51.15.70.155
51.15.74.36
51.254.126.89
5.141.219.63
5.141.98.150
5.172.111.125
5.175.40.188
5.1.81.165
5.187.245.239
52.10.188.3
52.164.208.219
52.166.76.165
52.168.166.245
52.172.209.6
52.173.143.114
52.174.36.99
52.178.134.151
52.178.45.144
52.179.17.135
52.203.74.121
52.229.119.21
52.231.201.37
52.237.246.189
52.242.35.99
5.230.131.185
5.249.150.189
52.58.184.59
52.58.71.63
52.66.7.114
54.166.187.96
54.171.155.0
54.215.184.159
54.237.199.84
54.88.207.172
54.93.60.87
58.101.149.217
58.187.173.199
58.187.199.38
58.213.99.251
58.216.51.73
58.218.200.5
58.240.202.16
58.240.26.2
58.240.52.76
58.247.246.36
58.42.228.170
58.55.127.254
59.111.92.32
59.115.120.165
59.127.229.12
59.41.103.97
59.45.142.199
59.49.111.146
59.53.67.84
59.57.13.165
59.63.161.252
60.12.229.225
60.174.195.41
60.190.226.162
60.216.75.138
60.253.214.115
60.255.146.182
60.28.235.147
60.5.255.112
61.144.105.236
61.158.120.253
61.159.182.140
61.161.182.158
61.163.32.197
61.180.33.102
61.183.52.39
61.185.27.34
61.216.145.154
61.222.152.156
61.234.156.69
61.51.192.243
61.72.97.52
61.79.81.73
61.85.7.206
62.112.9.25
62.146.13.85
62.163.155.31
62.168.44.238
62.210.169.42
62.210.211.212
62.210.24.141
62.210.24.142
62.210.247.81
62.210.48.192
62.210.48.193
62.210.48.196
62.232.121.238
62.233.149.138
62.75.210.207
64.244.204.50
64.55.104.2
65.52.181.50
66.113.15.230
66.210.180.50
66.31.24.189
67.137.119.10
67.189.16.174
67.204.212.159
67.207.94.17
67.210.105.196
67.8.107.41
68.102.147.186
68.118.181.247
69.159.244.95
69.162.73.83
69.249.103.229
69.4.91.92
69.61.125.189
69.70.245.30
71.42.243.226
72.2.170.24
72.248.114.133
73.115.68.110
73.130.68.239
73.168.47.138
73.203.31.15
73.207.128.189
73.217.158.187
73.29.49.121
74.118.114.202
74.208.202.74
74.208.47.253
74.222.20.43
74.74.132.156
75.146.136.114
75.185.32.119
76.110.252.120
76.12.191.22
77.107.237.51
77.166.11.186
77.174.233.198
77.222.139.15
77.222.155.252
77.243.188.150
77.244.211.2
77.34.115.49
77.34.132.210
77.53.124.27
77.72.82.171
77.72.82.187
77.81.225.108
77.81.225.18
77.81.225.37
77.81.225.9
77.81.226.120
78.111.124.240
78.111.2.25
78.187.47.157
78.192.107.9
78.233.101.180
78.40.108.231
78.58.187.40
79.1.210.39
79.137.0.35
79.137.86.3
79.142.66.169
79.171.75.25
79.174.32.164
79.7.209.216
79.98.155.170
80.112.141.195
80.11.28.118
80.195.199.74
80.241.38.36
80.55.15.30
80.56.46.52
80.59.61.107
80.82.64.21
80.82.77.46
81.136.157.167
81.136.189.195
81.138.11.109
81.138.86.225
81.142.80.97
81.142.98.129
81.149.154.58
81.149.211.134
81.171.53.7
81.171.58.111
81.174.255.65
81.184.253.49
81.196.221.96
82.10.59.165
82.216.39.35
82.225.6.33
82.253.111.241
82.69.94.219
82.74.122.154
82.81.139.73
83.121.255.250
83.233.5.167
83.234.168.65
83.255.117.130
83.52.18.255
84.10.18.150
84.198.184.38
84.216.211.76
85.114.132.32
85.150.101.113
85.150.79.226
85.184.149.94
85.194.166.198
85.195.42.225
85.195.48.240
85.214.116.182
85.222.46.201
85.232.156.4
85.92.220.96
86.100.68.209
86.171.57.227
86.205.119.160
86.57.164.109
86.57.168.86
86.97.49.101
87.81.240.178
87.98.185.8
88.103.112.229
88.159.153.152
88.177.168.133
88.177.205.141
88.186.249.54
88.188.177.186
88.190.183.18
88.190.235.84
88.198.65.205
88.215.4.114
88.87.20.126
88.99.133.232
88.99.3.195
88.99.39.105
89.163.209.162
89.163.255.165
89.218.73.54
89.239.149.7
89.248.160.2
89.34.237.72
89.36.211.8
89.40.70.128
89.46.196.206
91.102.225.109
91.112.18.170
91.120.21.57
91.134.133.251
91.134.177.237
91.160.90.59
91.161.102.62
91.195.103.171
91.197.232.109
91.197.232.15
91.200.12.1
91.200.205.119
91.218.105.28
91.218.114.137
91.225.78.26
91.236.116.245
91.236.116.75
91.236.116.78
91.73.236.133
92.100.166.228
92.100.211.180
92.207.194.177
92.222.216.160
92.222.74.167
92.27.4.189
92.43.113.177
92.45.30.225
93.114.42.188
93.152.165.147
93.174.89.103
93.176.213.222
93.186.245.104
93.186.245.119
93.186.245.160
93.186.245.241
93.187.16.70
93.61.95.172
93.63.247.0
93.63.4.77
93.76.199.84
93.85.82.92
94.125.120.23
94.156.20.219
94.158.166.207
94.177.167.240
94.177.180.80
94.177.189.75
94.177.197.113
94.177.205.214
94.177.205.52
94.177.205.87
94.177.206.227
94.177.206.46
94.177.217.113
94.177.217.184
94.180.250.74
94.188.164.58
94.210.83.227
94.23.216.99
94.29.109.131
94.74.81.27
94.99.138.196
95.110.174.19
95.110.174.43
95.110.174.52
95.110.186.242
95.123.201.228
95.123.84.219
95.138.190.191
95.211.209.213
95.30.227.173
95.55.108.201
95.67.46.46
95.9.109.6
96.239.59.131
96.57.82.166
96.88.170.121
98.126.20.18
99.225.59.47
5、SELKS里的suricata的decoder-events.rules (非常重要)
# Decoder event signatures for Suricata.
# SID's fall in the 2200000+ range. See http://doc.emergingthreats.net/bin/view/Main/SidAllocation
alert pkthdr any any -> any any (msg:"SURICATA IPv4 packet too small"; decode-event:ipv4.pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv4 header size too small"; decode-event:ipv4.hlen_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv4 total length smaller than header size"; decode-event:ipv4.iplen_smaller_than_hlen; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv4 truncated packet"; decode-event:ipv4.trunc_pkt; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv4 invalid option"; decode-event:ipv4.opt_invalid; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv4 invalid option length"; decode-event:ipv4.opt_invalid_len; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv4 malformed option"; decode-event:ipv4.opt_malformed; classtype:protocol-command-decode; sid:; rev:;)
#alert pkthdr any any -> any any (msg:"SURICATA IPv4 padding required "; decode-event:ipv4.opt_pad_required; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv4 with ICMPv6 header"; decode-event:ipv4.icmpv6; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv4 option end of list required"; decode-event:ipv4.opt_eol_required; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv4 duplicated IP option"; decode-event:ipv4.opt_duplicate; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv4 unknown IP option"; decode-event:ipv4.opt_unknown; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv4 wrong IP version"; decode-event:ipv4.wrong_ip_version; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv6 packet too small"; decode-event:ipv6.pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv6 truncated packet"; decode-event:ipv6.trunc_pkt; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv6 truncated extension header"; decode-event:ipv6.trunc_exthdr; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv6 duplicated Fragment extension header"; decode-event:ipv6.exthdr_dupl_fh; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv6 useless Fragment extension header"; decode-event:ipv6.exthdr_useless_fh; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv6 duplicated Routing extension header"; decode-event:ipv6.exthdr_dupl_rh; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv6 duplicated Hop-By-Hop Options extension header"; decode-event:ipv6.exthdr_dupl_hh; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv6 duplicated Destination Options extension header"; decode-event:ipv6.exthdr_dupl_dh; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv6 duplicated Authentication Header extension header"; decode-event:ipv6.exthdr_dupl_ah; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv6 duplicate ESP extension header"; decode-event:ipv6.exthdr_dupl_eh; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv6 invalid option lenght in header"; decode-event:ipv6.exthdr_invalid_optlen; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv6 wrong IP version"; decode-event:ipv6.wrong_ip_version; classtype:protocol-command-decode; sid:; rev:;)
# RFC states the reserved field should be .
alert pkthdr any any -> any any (msg:"SURICATA IPv6 AH reserved field not 0"; decode-event:ipv6.exthdr_ah_res_not_null; classtype:protocol-command-decode; sid:; rev:;)
# HOP option that we don't understand
alert pkthdr any any -> any any (msg:"SURICATA IPv6 HOPOPTS unknown option"; decode-event:ipv6.hopopts_unknown_opt; classtype:protocol-command-decode; sid:; rev:;)
# HOP header with only padding, covert channel?
alert pkthdr any any -> any any (msg:"SURICATA IPv6 HOPOPTS only padding"; decode-event:ipv6.hopopts_only_padding; classtype:protocol-command-decode; sid:; rev:;)
# DST option that we don't understand
alert pkthdr any any -> any any (msg:"SURICATA IPv6 DSTOPTS unknown option"; decode-event:ipv6.dstopts_unknown_opt; classtype:protocol-command-decode; sid:; rev:;)
# DST header with only padding, covert channel?
alert pkthdr any any -> any any (msg:"SURICATA IPv6 DSTOPTS only padding"; decode-event:ipv6.dstopts_only_padding; classtype:protocol-command-decode; sid:; rev:;)
# Type Routing header deprecated per RFC
alert ipv6 any any -> any any (msg:"SURICATA RH Type 0"; decode-event:ipv6.rh_type_0; classtype:protocol-command-decode; sid:; rev:;)
# padN option with zero length field
alert ipv6 any any -> any any (msg:"SURICATA zero length padN option"; decode-event:ipv6.zero_len_padn; classtype:protocol-command-decode; sid:; rev:;)
# Frag Header 'length' field is reserved and should be
alert ipv6 any any -> any any (msg:"SURICATA reserved field in Frag Header not zero"; decode-event:ipv6.fh_non_zero_reserved_field; classtype:protocol-command-decode; sid:; rev:;)
# Data after the 'none' header () is suspicious.
alert ipv6 any any -> any any (msg:"SURICATA data after none (59) header"; decode-event:ipv6.data_after_none_header; classtype:protocol-command-decode; sid:; rev:;)
# unknown/unsupported next header / protocol. Valid protocols are not yet supported, so disabling by default
#alert ipv6 any any -> any any (msg:"SURICATA unknown next header / protocol"; decode-event:ipv6.unknown_next_header; classtype:protocol-command-decode; sid:; rev:;)
alert ipv6 any any -> any any (msg:"SURICATA IPv6 with ICMPv4 header"; decode-event:ipv6.icmpv4; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA ICMPv4 packet too small"; decode-event:icmpv4.pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA ICMPv4 unknown type"; decode-event:icmpv4.unknown_type; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA ICMPv4 unknown code"; decode-event:icmpv4.unknown_code; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA ICMPv4 truncated packet"; decode-event:icmpv4.ipv4_trunc_pkt; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA ICMPv4 unknown version"; decode-event:icmpv4.ipv4_unknown_ver; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA ICMPv6 packet too small"; decode-event:icmpv6.pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
# uncomment the following sginature if you plan to update suricata code to support more ICMPv6 type
#alert pkthdr any any -> any any (msg:"SURICATA ICMPv6 unknown type"; decode-event:icmpv6.unknown_type; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA ICMPv6 unknown code"; decode-event:icmpv6.unknown_code; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA ICMPv6 truncated packet"; decode-event:icmpv6.ipv6_trunc_pkt; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA ICMPv6 unknown version"; decode-event:icmpv6.ipv6_unknown_version; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA ICMPv6 MLD hop limit not 1"; decode-event:icmpv6.mld_message_with_invalid_hl; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA ICMPv6 unassigned type"; decode-event:icmpv6.unassigned_type; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA ICMPv6 private experimentation type"; decode-event:icmpv6.experimentation_type; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA TCP packet too small"; decode-event:tcp.pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA TCP header length too small"; decode-event:tcp.hlen_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA TCP invalid option length"; decode-event:tcp.invalid_optlen; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA TCP option invalid length"; decode-event:tcp.opt_invalid_len; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA TCP duplicated option"; decode-event:tcp.opt_duplicate; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA UDP packet too small"; decode-event:udp.pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA UDP header length too small"; decode-event:udp.hlen_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA UDP invalid header length"; decode-event:udp.hlen_invalid; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA SLL packet too small"; decode-event:sll.pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA Ethernet packet too small"; decode-event:ethernet.pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA PPP packet too small"; decode-event:ppp.pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA PPP VJU packet too small"; decode-event:ppp.vju_pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA PPP IPv4 packet too small"; decode-event:ppp.ip4_pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA PPP IPv6 too small"; decode-event:ppp.ip6_pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA PPP wrong type"; decode-event:ppp.wrong_type; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA PPP unsupported protocol"; decode-event:ppp.unsup_proto; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA PPPOE packet too small"; decode-event:pppoe.pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA PPPOE wrong code"; decode-event:pppoe.wrong_code; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA PPPOE malformed tags"; decode-event:pppoe.malformed_tags; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE packet too small"; decode-event:gre.pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE wrong version"; decode-event:gre.wrong_version; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE v0 recursion control"; decode-event:gre.version0_recur; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE v0 flags"; decode-event:gre.version0_flags; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE v0 header too big"; decode-event:gre.version0_hdr_too_big; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE v1 checksum present"; decode-event:gre.version1_chksum; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE v1 routing present"; decode-event:gre.version1_route; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE v1 strict source route"; decode-event:gre.version1_ssr; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE v1 recursion control"; decode-event:gre.version1_recur; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE v1 flags"; decode-event:gre.version1_flags; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE v1 no key present"; decode-event:gre.version1_no_key; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE v1 wrong protocol"; decode-event:gre.version1_wrong_protocol; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE v1 malformed Source Route Entry header"; decode-event:gre.version1_malformed_sre_hdr; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA GRE v1 header too big"; decode-event:gre.version1_hdr_too_big; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA VLAN header too small "; decode-event:vlan.header_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA VLAN unknown type"; decode-event:vlan.unknown_type; classtype:protocol-command-decode; sid:; rev:;)
# more than vlan layers in the packet
alert pkthdr any any -> any any (msg:"SURICATA VLAN too many layers"; decode-event:vlan.too_many_layers; classtype:protocol-command-decode; sid:; rev:;) alert pkthdr any any -> any any (msg:"SURICATA IP raw invalid IP version "; decode-event:ipraw.invalid_ip_version; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA FRAG IPv4 Packet size too large"; decode-event:ipv4.frag_pkt_too_large; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA FRAG IPv4 Fragmentation overlap"; decode-event:ipv4.frag_overlap; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA FRAG IPv6 Packet size too large"; decode-event:ipv6.frag_pkt_too_large; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA FRAG IPv6 Fragmentation overlap"; decode-event:ipv6.frag_overlap; classtype:protocol-command-decode; sid:; rev:;) # checksum rules
alert ip any any -> any any (msg:"SURICATA IPv4 invalid checksum"; ipv4-csum:invalid; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA TCPv4 invalid checksum"; tcpv4-csum:invalid; classtype:protocol-command-decode; sid:; rev:;)
alert udp any any -> any any (msg:"SURICATA UDPv4 invalid checksum"; udpv4-csum:invalid; classtype:protocol-command-decode; sid:; rev:;)
alert icmp any any -> any any (msg:"SURICATA ICMPv4 invalid checksum"; icmpv4-csum:invalid; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA TCPv6 invalid checksum"; tcpv6-csum:invalid; classtype:protocol-command-decode; sid:; rev:;)
alert udp any any -> any any (msg:"SURICATA UDPv6 invalid checksum"; udpv6-csum:invalid; classtype:protocol-command-decode; sid:; rev:;)
alert icmp any any -> any any (msg:"SURICATA ICMPv6 invalid checksum"; icmpv6-csum:invalid; classtype:protocol-command-decode; sid:; rev:;) # IPv4 in IPv6 rules
alert pkthdr any any -> any any (msg:"SURICATA IPv4-in-IPv6 packet too short"; decode-event:ipv6.ipv4_in_ipv6_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv4-in-IPv6 invalid protocol"; decode-event:ipv6.ipv4_in_ipv6_wrong_version; classtype:protocol-command-decode; sid:; rev:;)
# IPv6 in IPv6 rules
alert pkthdr any any -> any any (msg:"SURICATA IPv6-in-IPv6 packet too short"; decode-event:ipv6.ipv6_in_ipv6_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA IPv6-in-IPv6 invalid protocol"; decode-event:ipv6.ipv6_in_ipv6_wrong_version; classtype:protocol-command-decode; sid:; rev:;) # MPLS rules
alert pkthdr any any -> any any (msg:"SURICATA MPLS header too small"; decode-event:mpls.header_too_small; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA MPLS bad router alert label"; decode-event:mpls.bad_label_router_alert; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA MPLS bad implicit null label"; decode-event:mpls.bad_label_implicit_null; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA MPLS reserved label"; decode-event:mpls.bad_label_reserved; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA MPLS unknown payload type"; decode-event:mpls.unknown_payload_type; classtype:protocol-command-decode; sid:; rev:;) # linktype null
alert pkthdr any any -> any any (msg:"SURICATA NULL pkt too small"; decode-event:ltnull.pkt_too_small; classtype:protocol-command-decode; sid:; rev:;)
# packet has type not supported by Suricata's decoders
alert pkthdr any any -> any any (msg:"SURICATA NULL unsupported type"; decode-event:ltnull.unsupported_type; classtype:protocol-command-decode; sid:; rev:;) # ERSPAN
alert pkthdr any any -> any any (msg:"SURICATA ERSPAN pkt too small"; decode-event:erspan.header_too_small; classtype:protocol-command-decode; sid:; rev:;)
# packet has type not supported by Suricata's decoders
alert pkthdr any any -> any any (msg:"SURICATA ERSPAN unsupported version"; decode-event:erspan.unsupported_version; classtype:protocol-command-decode; sid:; rev:;)
alert pkthdr any any -> any any (msg:"SURICATA ERSPAN too many vlan layers"; decode-event:erspan.too_many_vlan_layers; classtype:protocol-command-decode; sid:; rev:;) # Cisco Fabric Path/DCE
alert pkthdr any any -> any any (msg:"SURICATA DCE packet too small"; decode-event:dce.pkt_too_small; classtype:protocol-command-decode; sid:; rev:;) # next sid is
6、SELKS里的suricata的dnp3-events.rules(非常重要)
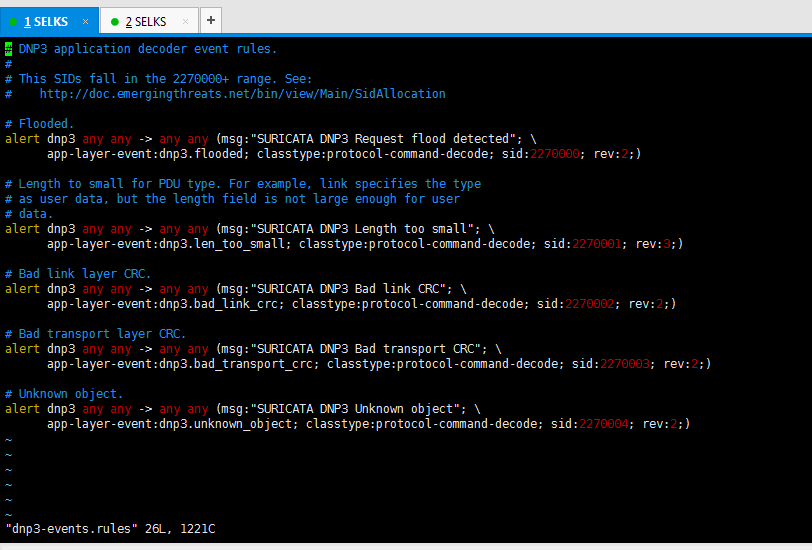
# DNP3 application decoder event rules.
#
# This SIDs fall in the + range. See:
# http://doc.emergingthreats.net/bin/view/Main/SidAllocation # Flooded.
alert dnp3 any any -> any any (msg:"SURICATA DNP3 Request flood detected"; \
app-layer-event:dnp3.flooded; classtype:protocol-command-decode; sid:; rev:;) # Length to small for PDU type. For example, link specifies the type
# as user data, but the length field is not large enough for user
# data.
alert dnp3 any any -> any any (msg:"SURICATA DNP3 Length too small"; \
app-layer-event:dnp3.len_too_small; classtype:protocol-command-decode; sid:; rev:;) # Bad link layer CRC.
alert dnp3 any any -> any any (msg:"SURICATA DNP3 Bad link CRC"; \
app-layer-event:dnp3.bad_link_crc; classtype:protocol-command-decode; sid:; rev:;) # Bad transport layer CRC.
alert dnp3 any any -> any any (msg:"SURICATA DNP3 Bad transport CRC"; \
app-layer-event:dnp3.bad_transport_crc; classtype:protocol-command-decode; sid:; rev:;) # Unknown object.
alert dnp3 any any -> any any (msg:"SURICATA DNP3 Unknown object"; \
app-layer-event:dnp3.unknown_object; classtype:protocol-command-decode; sid:; rev:;)
7、SELKS里的suricata的dns-events.rules(非常重要)
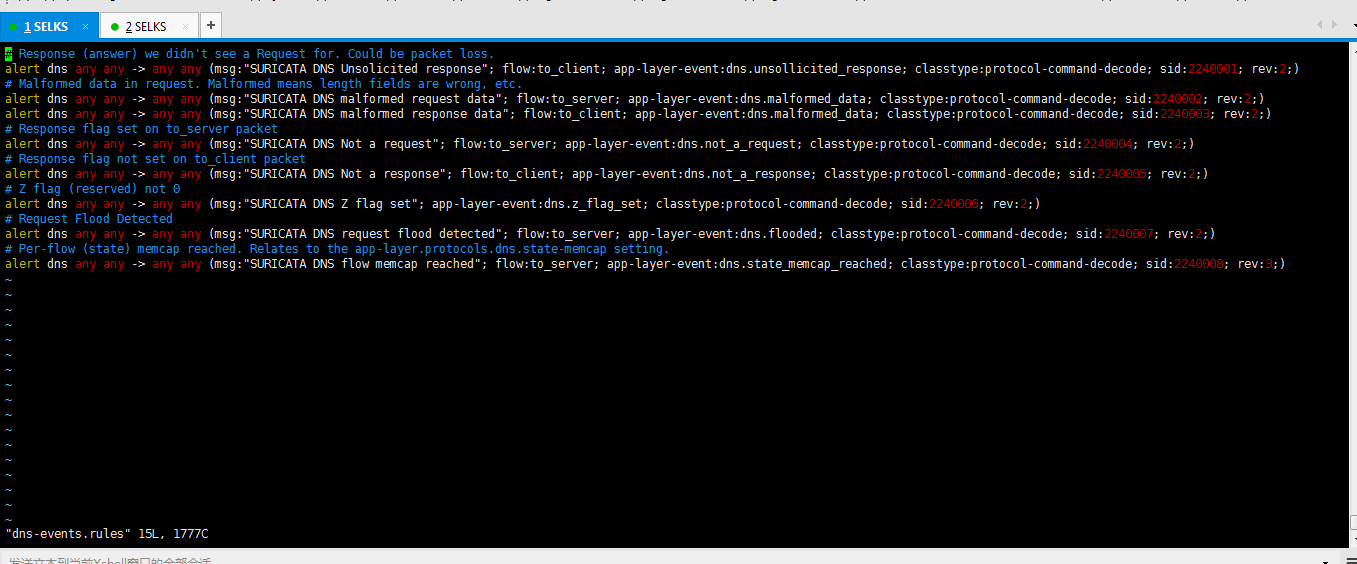
# Response (answer) we didn't see a Request for. Could be packet loss.
alert dns any any -> any any (msg:"SURICATA DNS Unsolicited response"; flow:to_client; app-layer-event:dns.unsollicited_response; classtype:protocol-command-decode; sid:; rev:;)
# Malformed data in request. Malformed means length fields are wrong, etc.
alert dns any any -> any any (msg:"SURICATA DNS malformed request data"; flow:to_server; app-layer-event:dns.malformed_data; classtype:protocol-command-decode; sid:; rev:;)
alert dns any any -> any any (msg:"SURICATA DNS malformed response data"; flow:to_client; app-layer-event:dns.malformed_data; classtype:protocol-command-decode; sid:; rev:;)
# Response flag set on to_server packet
alert dns any any -> any any (msg:"SURICATA DNS Not a request"; flow:to_server; app-layer-event:dns.not_a_request; classtype:protocol-command-decode; sid:; rev:;)
# Response flag not set on to_client packet
alert dns any any -> any any (msg:"SURICATA DNS Not a response"; flow:to_client; app-layer-event:dns.not_a_response; classtype:protocol-command-decode; sid:; rev:;)
# Z flag (reserved) not
alert dns any any -> any any (msg:"SURICATA DNS Z flag set"; app-layer-event:dns.z_flag_set; classtype:protocol-command-decode; sid:; rev:;)
# Request Flood Detected
alert dns any any -> any any (msg:"SURICATA DNS request flood detected"; flow:to_server; app-layer-event:dns.flooded; classtype:protocol-command-decode; sid:; rev:;)
# Per-flow (state) memcap reached. Relates to the app-layer.protocols.dns.state-memcap setting.
alert dns any any -> any any (msg:"SURICATA DNS flow memcap reached"; flow:to_server; app-layer-event:dns.state_memcap_reached; classtype:protocol-command-decode; sid:; rev:;)
8、SELKS里的suricata的emerging.conf(非常重要)
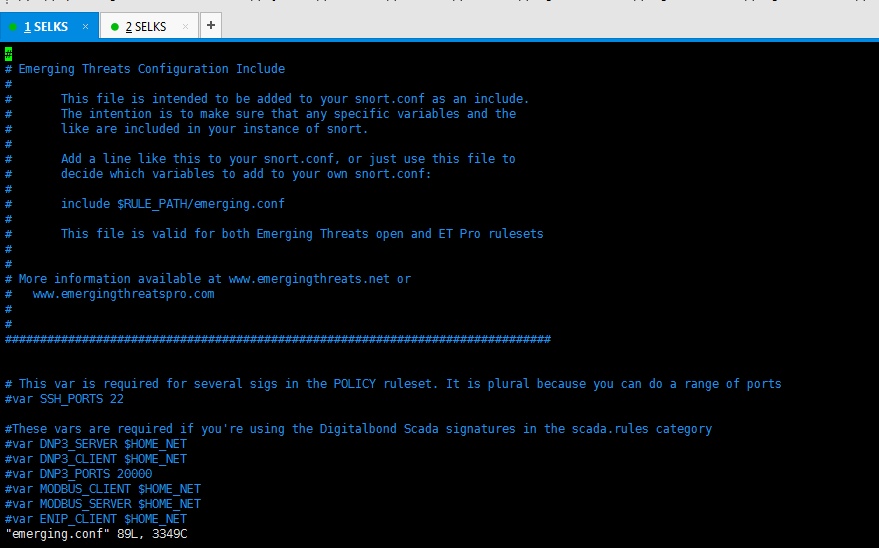
#
# Emerging Threats Configuration Include
#
# This file is intended to be added to your snort.conf as an include.
# The intention is to make sure that any specific variables and the
# like are included in your instance of snort.
#
# Add a line like this to your snort.conf, or just use this file to
# decide which variables to add to your own snort.conf:
#
# include $RULE_PATH/emerging.conf
#
# This file is valid for both Emerging Threats open and ET Pro rulesets
#
#
# More information available at www.emergingthreats.net or
# www.emergingthreatspro.com
#
#
############################################################################## # This var is required for several sigs in the POLICY ruleset. It is plural because you can do a range of ports
#var SSH_PORTS #These vars are required if you're using the Digitalbond Scada signatures in the scada.rules category
#var DNP3_SERVER $HOME_NET
#var DNP3_CLIENT $HOME_NET
#var DNP3_PORTS
#var MODBUS_CLIENT $HOME_NET
#var MODBUS_SERVER $HOME_NET
#var ENIP_CLIENT $HOME_NET
#var ENIP_SERVER $HOME_NET #include $RULE_PATH/classification.config
#include $RULE_PATH/reference.config #include $RULE_PATH/emerging-ftp.rules
#include $RULE_PATH/emerging-policy.rules
#include $RULE_PATH/emerging-trojan.rules
#include $RULE_PATH/emerging-games.rules
#include $RULE_PATH/emerging-pop3.rules
#include $RULE_PATH/emerging-user_agents.rules
##include $RULE_PATH/emerging-activex.rules
#include $RULE_PATH/emerging-rpc.rules
#include $RULE_PATH/emerging-attack_response.rules
#include $RULE_PATH/emerging-icmp.rules
#include $RULE_PATH/emerging-scan.rules
#include $RULE_PATH/emerging-scada.rules
#include $RULE_PATH/emerging-voip.rules
#include $RULE_PATH/emerging-chat.rules
##include $RULE_PATH/emerging-icmp_info.rules
##include $RULE_PATH/emerging-shellcode.rules
##include $RULE_PATH/emerging-web_client.rules
#include $RULE_PATH/emerging-imap.rules
#include $RULE_PATH/emerging-web_server.rules
#include $RULE_PATH/emerging-current_events.rules
##include $RULE_PATH/emerging-inappropriate.rules
#include $RULE_PATH/emerging-smtp.rules
##include $RULE_PATH/emerging-web_specific_apps.rules
##include $RULE_PATH/emerging-deleted.rules
#include $RULE_PATH/emerging-malware.rules
#include $RULE_PATH/emerging-snmp.rules
#include $RULE_PATH/emerging-worm.rules
#include $RULE_PATH/emerging-dns.rules
#include $RULE_PATH/emerging-misc.rules
#include $RULE_PATH/emerging-sql.rules
#include $RULE_PATH/emerging-dos.rules
#include $RULE_PATH/emerging-netbios.rules
#include $RULE_PATH/emerging-telnet.rules
#include $RULE_PATH/emerging-exploit.rules
#include $RULE_PATH/emerging-p2p.rules
#include $RULE_PATH/emerging-tftp.rules
#include $RULE_PATH/emerging-mobile_malware.rules
#include $RULE_PATH/emerging-info.rules #include $RULE_PATH/emerging-botcc.rules
#include $RULE_PATH/emerging-botcc-BLOCK.rules
#include $RULE_PATH/emerging-compromised.rules
#include $RULE_PATH/emerging-compromised-BLOCK.rules
#include $RULE_PATH/emerging-drop.rules
#include $RULE_PATH/emerging-drop-BLOCK.rules
#include $RULE_PATH/emerging-dshield.rules
#include $RULE_PATH/emerging-dshield-BLOCK.rules
#include $RULE_PATH/emerging-tor.rules
#include $RULE_PATH/emerging-tor-BLOCK.rules
#include $RULE_PATH/emerging-ciarmy.rules
9、SELKS里的suricata的files.rules(非常重要)
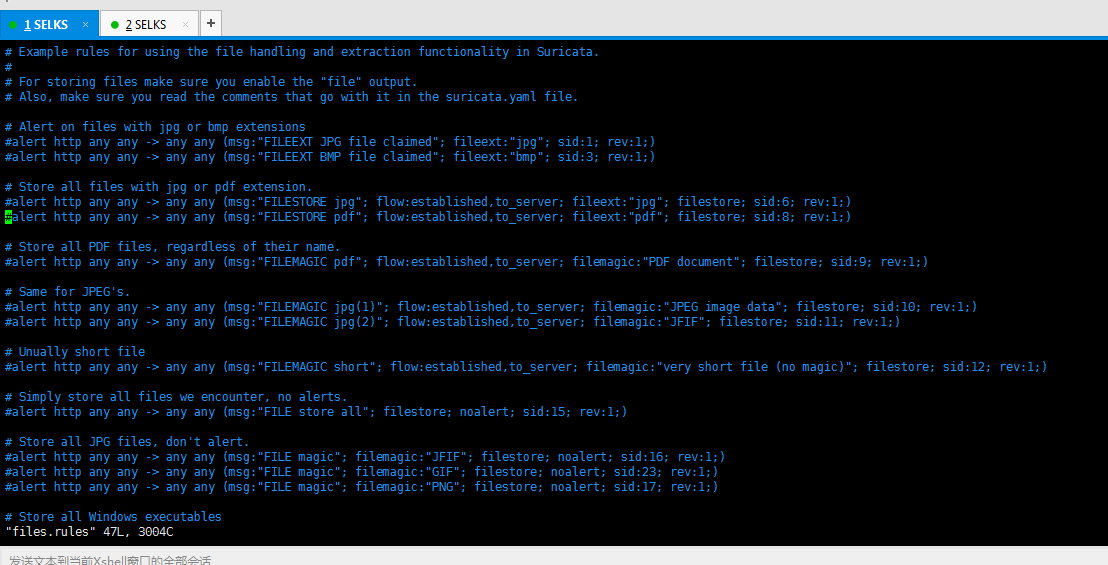
# Example rules for using the file handling and extraction functionality in Suricata.
#
# For storing files make sure you enable the "file" output.
# Also, make sure you read the comments that go with it in the suricata.yaml file. # Alert on files with jpg or bmp extensions
#alert http any any -> any any (msg:"FILEEXT JPG file claimed"; fileext:"jpg"; sid:; rev:;)
#alert http any any -> any any (msg:"FILEEXT BMP file claimed"; fileext:"bmp"; sid:; rev:;) # Store all files with jpg or pdf extension.
#alert http any any -> any any (msg:"FILESTORE jpg"; flow:established,to_server; fileext:"jpg"; filestore; sid:; rev:;)
#alert http any any -> any any (msg:"FILESTORE pdf"; flow:established,to_server; fileext:"pdf"; filestore; sid:; rev:;) # Store all PDF files, regardless of their name.
#alert http any any -> any any (msg:"FILEMAGIC pdf"; flow:established,to_server; filemagic:"PDF document"; filestore; sid:; rev:;) # Same for JPEG's.
#alert http any any -> any any (msg:"FILEMAGIC jpg(1)"; flow:established,to_server; filemagic:"JPEG image data"; filestore; sid:; rev:;)
#alert http any any -> any any (msg:"FILEMAGIC jpg(2)"; flow:established,to_server; filemagic:"JFIF"; filestore; sid:; rev:;) # Unually short file
#alert http any any -> any any (msg:"FILEMAGIC short"; flow:established,to_server; filemagic:"very short file (no magic)"; filestore; sid:; rev:;) # Simply store all files we encounter, no alerts.
#alert http any any -> any any (msg:"FILE store all"; filestore; noalert; sid:; rev:;) # Store all JPG files, don't alert.
#alert http any any -> any any (msg:"FILE magic"; filemagic:"JFIF"; filestore; noalert; sid:; rev:;)
#alert http any any -> any any (msg:"FILE magic"; filemagic:"GIF"; filestore; noalert; sid:; rev:;)
#alert http any any -> any any (msg:"FILE magic"; filemagic:"PNG"; filestore; noalert; sid:; rev:;) # Store all Windows executables
#alert http any any -> any any (msg:"FILE magic -- windows"; flow:established,to_client; filemagic:"executable for MS Windows"; filestore; sid:; rev:;) # Alert on PNG with 1x1 pixels (tracking)
#alert http any any -> any any (msg:"FILE tracking PNG (1x1 pixel) (1)"; filemagic:"PNG image data, 1 x 1,"; sid:; rev:;)
#alert http any any -> any any (msg:"FILE tracking PNG (1x1 pixel) (2)"; filemagic:"PNG image data, 1 x 1|00|"; sid:; rev:;) # Alert on GIT with 1x1 pixels (tracking)
# The pattern matches on || which is the end of the magic buffer, this way we won't match on 1 x 128.
#alert http any any -> any any (msg:"FILE tracking GIF (1x1 pixel)"; filemagic:"GIF image data, version 89a, 1 x 1|00|"; sid:; rev:;) # Alert and store pdf attachment but not pdf file
#alert http any any -> any any (msg:"FILE pdf claimed, but not pdf"; flow:established,to_client; fileext:"pdf"; filemagic:!"PDF document"; filestore; sid:; rev:;) # Alert and store files over SMTP
#alert smtp any any -> any any (msg:"File Found over SMTP and stored"; filestore; sid:; rev:;)
10、SELKS里的suricata的gen-msg.map(非常重要)

# $Id: gen-msg.map,v 1.8 // :: mwatchinski Exp $
# GENERATORS -> msg map
# Format: generatorid || alertid || MSG || || snort general alert
|| || tag: Tagged Packet
|| || snort dynamic alert
|| || spp_portscan: Portscan Detected
|| || spp_portscan: Portscan Status
|| || spp_portscan: Portscan Ended
|| || spp_minfrag: minfrag alert
|| || http_decode: Unicode Attack
|| || http_decode: CGI NULL Byte Attack
|| || http_decode: large method attempted
|| || http_decode: missing uri
|| || http_decode: double encoding detected
|| || http_decode: illegal hex values detected
|| || http_decode: overlong character detected
|| || spp_defrag: Fragmentation Overflow Detected
|| || spp_defrag: Stale Fragments Discarded
|| || spp_anomsensor: SPADE Anomaly Threshold Exceeded
|| || spp_anomsensor: SPADE Anomaly Threshold Adjusted
|| || spp_bo: Back Orifice Traffic Detected
|| || spp_bo: Back Orifice Client Traffic Detected
|| || spp_bo: Back Orifice Server Traffic Detected
|| || spp_bo: Back Orifice Snort Buffer Attack
|| || spp_rpc_decode: Fragmented RPC Records
|| || spp_rpc_decode: Multiple Records in one packet
|| || spp_rpc_decode: Large RPC Record Fragment
|| || spp_rpc_decode: Incomplete RPC segment
|| || spp_rpc_decode: Zero-length RPC Fragment
|| || spp_unidecode: CGI NULL Attack
|| || spp_unidecode: Directory Traversal
|| || spp_unidecode: Unknown Mapping
|| || spp_unidecode: Invalid Mapping
|| || spp_stream4: Stealth Activity Detected
|| || spp_stream4: Evasive Reset Packet
|| || spp_stream4: Retransmission
|| || spp_stream4: Window Violation
|| || spp_stream4: Data on SYN Packet
|| || spp_stream4: Full XMAS Stealth Scan
|| || spp_stream4: SAPU Stealth Scan
|| || spp_stream4: FIN Stealth Scan
|| || spp_stream4: NULL Stealth Scan
|| || spp_stream4: NMAP XMAS Stealth Scan
|| || spp_stream4: VECNA Stealth Scan
|| || spp_stream4: NMAP Fingerprint Stateful Detection
|| || spp_stream4: SYN FIN Stealth Scan
|| || spp_stream4: TCP forward overlap detected
|| || spp_stream4: TTL Evasion attempt
|| || spp_stream4: Evasive retransmitted data attempt
|| || spp_stream4: Evasive retransmitted data with the data split attempt
|| || spp_stream4: Multiple acked
|| || spp_stream4: Shifting to Emergency Session Mode
|| || spp_stream4: Shifting to Suspend Mode
|| || spp_stream4: TCP Timestamp option has value of zero
|| || spp_stream4: Too many overlapping TCP packets
|| || spp_stream4: Packet in established TCP stream missing ACK
|| || spp_stream4: Evasive FIN Packet
|| || spp_stream4: SYN on established
|| || spp_arpspoof: Directed ARP Request
|| || spp_arpspoof: Etherframe ARP Mismatch SRC
|| || spp_arpspoof: Etherframe ARP Mismatch DST
|| || spp_arpspoof: ARP Cache Overwrite Attack
|| || spp_frag2: Oversized Frag
|| || spp_frag2: Teardrop/Fragmentation Overlap Attack
|| || spp_frag2: TTL evasion detected
|| || spp_frag2: overlap detected
|| || spp_frag2: Duplicate first fragments
|| || spp_frag2: memcap exceeded
|| || spp_frag2: Out of order fragments
|| || spp_frag2: IP Options on Fragmented Packet
|| || spp_frag2: Shifting to Emegency Session Mode
|| || spp_frag2: Shifting to Suspend Mode
|| || spp_fnord: Possible Mutated GENERIC NOP Sled detected
|| || spp_fnord: Possible Mutated IA32 NOP Sled detected
|| || spp_fnord: Possible Mutated HPPA NOP Sled detected
|| || spp_fnord: Possible Mutated SPARC NOP Sled detected
|| || spp_asn1: Indefinite ASN. length encoding
|| || spp_asn1: Invalid ASN. length encoding
|| || spp_asn1: ASN. oversized item, possible overflow
|| || spp_asn1: ASN. spec violation, possible overflow
|| || spp_asn1: ASN. Attack: Datum length > packet length
|| || snort_decoder: Not IPv4 datagram!
|| || snort_decoder: WARNING: hlen < IP_HEADER_LEN!
|| || snort_decoder: WARNING: IP dgm len < IP Hdr len!
|| || snort_decoder: Bad IPv4 Options
|| || snort_decoder: Truncated IPv4 Options
|| || snort_decoder: WARNING: IP dgm len > captured len!
|| || snort_decoder: TCP packet len is smaller than bytes!
|| || snort_decoder: TCP Data Offset is less than !
|| || snort_decoder: TCP Data Offset is longer than payload!
|| || snort_decoder: Tcp Options found with bad lengths
|| || snort_decoder: Truncated Tcp Options
|| || snort_decoder: T/TCP Detected
|| || snort_decoder: Obsolete TCP options
|| || snort_decoder: Experimental TCP options
|| || snort_decoder: TCP Window Scale Option Scale Invalid (> )
|| || snort_decoder: Truncated UDP Header!
|| || snort_decoder: Invalid UDP header, length field <
|| || snort_decoder: Short UDP packet, length field > payload length
|| || snort_decoder: Long UDP packet, length field < payload length
|| || snort_decoder: ICMP Header Truncated!
|| || snort_decoder: ICMP Timestamp Header Truncated!
|| || snort_decoder: ICMP Address Header Truncated!
|| || snort_decoder: Unknown Datagram decoding problem!
|| || snort_decoder: Truncated ARP Packet!
|| || snort_decoder: Truncated EAP Header!
|| || snort_decoder: EAP Key Truncated!
|| || snort_decoder: EAP Header Truncated!
|| || snort_decoder: WARNING: Bad PPPOE frame detected!
|| || snort_decoder: WARNING: Bad VLAN Frame!
|| || snort_decoder: WARNING: Bad LLC header!
|| || snort_decoder: WARNING: Bad Extra LLC Info!
|| || snort_decoder: WARNING: Bad 802.11 LLC header!
|| || snort_decoder: WARNING: Bad 802.11 Extra LLC Info!
|| || snort_decoder: WARNING: Bad Token Ring Header!
|| || snort_decoder: WARNING: Bad Token Ring ETHLLC Header!
|| || snort_decoder: WARNING: Bad Token Ring MRLEN Header!
|| || snort_decoder: WARNING: Bad Token Ring MR Header!
|| || snort_decoder: Bad Traffic Loopback IP!
|| || snort_decoder: Bad Traffic Same Src/Dst IP!
|| || snort_decoder: WARNING: GRE header length > payload length
|| || snort_decoder: WARNING: Multiple encapsulations in packet
|| || snort_decoder: WARNING: Invalid GRE version
|| || snort_decoder: WARNING: Invalid GRE v. header
|| || snort_decoder: WARNING: Invalid GRE v. PPTP header
|| || snort_decoder: WARNING: GRE Trans header length > payload length
|| || snort_decoder: Bad MPLS Frame
|| || snort_decoder: MPLS Label Appears in Nonbottom Header
|| || snort_decoder: MPLS Label Appears in Bottom Header
|| || snort_decoder: MPLS Label Appears in Nonbottom Header
|| || snort_decoder: Bad use of label
|| || snort_decoder: MPLS Label , ,.. or Appears in Header
|| || snort_decoder: Too Many MPLS headers
|| || snort_decoder: WARNING: ICMP Original IP Header Truncated!
|| || snort_decoder: WARNING: ICMP Original IP Header Not IPv4!
|| || snort_decoder: WARNING: ICMP Original Datagram Length < Original IP Header Length!
|| || snort_decoder: WARNING: ICMP Original IP Payload < bits!
|| || snort_decoder: WARNING: ICMP Original IP Payload > bytes!
|| || snort_decoder: WARNING: ICMP Original IP Fragmented and Offset Not !
|| || snort_decoder: WARNING: IPV6 packet exceeded TTL limit
|| || snort_decoder: WARNING: IPv6 header claims to not be IPv6
|| || snort_decoder: WARNING: IPV6 truncated extension header
|| || snort_decoder: WARNING: IPV6 truncated header
|| || snort_decoder: WARNING: IPV6 dgm len < IPV6 Hdr len!
|| || snort_decoder: WARNING: IPV6 dgm len > captured len!
|| || snort_decoder: IPV6 tunneled over IPv4, IPv6 header truncated, possible Linux Kernel attack
|| || snort_decoder: WARNING: XMAS Attack Detected!
|| || snort_decoder: WARNING: Nmap XMAS Attack Detected!
|| || snort_decoder: DOS NAPTHA Vulnerability Detected!
|| || snort_decoder: Bad Traffic SYN to multicast address
|| || snort_decoder: WARNING: IPV4 packet with zero TTL
|| || snort_decoder: WARNING: IPV4 packet with bad frag bits (Both MF and DF set)
|| || snort_decoder: Invalid IPv6 UDP packet, checksum zero
|| || spp_portscan2: Portscan detected!
|| || spp_conversation: Bad IP protocol!
|| || http_inspect: ASCII ENCODING
|| || http_inspect: DOUBLE DECODING ATTACK
|| || http_inspect: U ENCODING
|| || http_inspect: BARE BYTE UNICODE ENCODING
|| || http_inspect: BASE36 ENCODING
|| || http_inspect: UTF- ENCODING
|| || http_inspect: IIS UNICODE CODEPOINT ENCODING
|| || http_inspect: MULTI_SLASH ENCODING
|| || http_inspect: IIS BACKSLASH EVASION
|| || http_inspect: SELF DIRECTORY TRAVERSAL
|| || http_inspect: DIRECTORY TRAVERSAL
|| || http_inspect: APACHE WHITESPACE (TAB)
|| || http_inspect: NON-RFC HTTP DELIMITER
|| || http_inspect: NON-RFC DEFINED CHAR
|| || http_inspect: OVERSIZE REQUEST-URI DIRECTORY
|| || http_inspect: OVERSIZE CHUNK ENCODING
|| || http_inspect: UNAUTHORIZED PROXY USE DETECTED
|| || http_inspect: WEBROOT DIRECTORY TRAVERSAL
|| || http_inspect: LONG HEADER
|| || http_inspect: MAX HEADERS
|| || http_inspect: MULTIPLE CONTENT LENGTH HEADER FIELDS
|| || http_inspect: CHUNK SIZE MISMATCH DETECTED
|| || http_inspect: ANOMALOUS HTTP SERVER ON UNDEFINED HTTP PORT
|| || flow-portscan: Fixed Scale Scanner Limit Exceeded
|| || flow-portscan: Sliding Scale Scanner Limit Exceeded
|| || flow-portscan: Fixed Scale Talker Limit Exceeded
|| || flow-portscan: Sliding Scale Talker Limit Exceeded
|| || portscan: TCP Portscan
|| || portscan: TCP Decoy Portscan
|| || portscan: TCP Portsweep
|| || portscan: TCP Distributed Portscan
|| || portscan: TCP Filtered Portscan
|| || portscan: TCP Filtered Decoy Portscan
|| || portscan: TCP Filtered Portsweep
|| || portscan: TCP Filtered Distributed Portscan
|| || portscan: IP Protocol Scan
|| || portscan: IP Decoy Protocol Scan
|| || portscan: IP Protocol Sweep
|| || portscan: IP Distributed Protocol Scan
|| || portscan: IP Filtered Protocol Scan
|| || portscan: IP Filtered Decoy Protocol Scan
|| || portscan: IP Filtered Protocol Sweep
|| || portscan: IP Filtered Distributed Protocol Scan
|| || portscan: UDP Portscan
|| || portscan: UDP Decoy Portscan
|| || portscan: UDP Portsweep
|| || portscan: UDP Distributed Portscan
|| || portscan: UDP Filtered Portscan
|| || portscan: UDP Filtered Decoy Portscan
|| || portscan: UDP Filtered Portsweep
|| || portscan: UDP Filtered Distributed Portscan
|| || portscan: ICMP Sweep
|| || portscan: ICMP Filtered Sweep
|| || portscan: Open Port
|| || frag3: IP Options on fragmented packet
|| || frag3: Teardrop attack
|| || frag3: Short fragment, possible DoS attempt
|| || frag3: Fragment packet ends after defragmented packet
|| || frag3: Zero-byte fragment
|| || frag3: Bad fragment size, packet size is negative
|| || frag3: Bad fragment size, packet size is greater than
|| || frag3: Fragmentation overlap
|| || frag3: IPv6 BSD mbufs remote kernel buffer overflow
|| || frag3: Bogus fragmentation packet. Possible BSD attack
|| || frag3: TTL value less than configured minimum, not using for reassembly
|| || frag3: Number of overlapping fragments exceed configured limit
|| || frag3: Fragments smaller than configured min_fragment_length
|| || smtp: Attempted command buffer overflow
|| || smtp: Attempted data header buffer overflow
|| || smtp: Attempted response buffer overflow
|| || smtp: Attempted specific command buffer overflow
|| || smtp: Unknown command
|| || smtp: Illegal command
|| || smtp: Attempted header name buffer overflow
|| || smtp: Attempted X-Link2State command buffer overflow
|| || ftp_pp: Telnet command on FTP command channel
|| || ftp_pp: Invalid FTP command
|| || ftp_pp: FTP parameter length overflow
|| || ftp_pp: FTP malformed parameter
|| || ftp_pp: Possible string format attempt in FTP command/parameter
|| || ftp_pp: FTP response length overflow
|| || ftp_pp: FTP command channel encrypted
|| || ftp_pp: FTP bounce attack
|| || ftp_pp: Evasive Telnet command on FTP command channel
|| || telnet_pp: Telnet consecutive AYT overflow
|| || telnet_pp: Telnet data encrypted
|| || telnet_pp: Subnegotiation Begin without matching Subnegotiation End
|| || ssh: Gobbles exploit
|| || ssh: SSH1 CRC32 exploit
|| || ssh: Server version string overflow
|| || ssh: Protocol mismatch
|| || ssh: Bad message direction
|| || ssh: Payload size incorrect for the given payload
|| || ssh: Failed to detect SSH version string
|| || stream5: SYN on established session
|| || stream5: Data on SYN packet
|| || stream5: Data sent on stream not accepting data
|| || stream5: TCP Timestamp is outside of PAWS window
|| || stream5: Bad segment, overlap adjusted size less than/equal
|| || stream5: Window size (after scaling) larger than policy allows
|| || stream5: Limit on number of overlapping TCP packets reached
|| || stream5: Data sent on stream after TCP Reset
|| || stream5: TCP Client possibly hijacked, different Ethernet Address
|| || stream5: TCP Server possibly hijacked, different Ethernet Address
|| || stream5: TCP Data with no TCP Flags set
|| || stream5: TCP Small Segment Threshold Exceeded
|| || stream5: TCP -way handshake detected
|| || stream5: TCP Timestamp is missing
|| || dcerpc: Maximum memory usage reached
|| || dns: Obsolete DNS RData Type
|| || dns: Experimental DNS RData Type
|| || dns: Client RData TXT Overflow
|| || dcerpc2: Memory cap exceeded
|| || dcerpc2: SMB - Bad NetBIOS Session Service session type
|| || dcerpc2: SMB - Bad SMB message type
|| || dcerpc2: SMB - Bad SMB Id (not \xffSMB)
|| || dcerpc2: SMB - Bad word count for command
|| || dcerpc2: SMB - Bad byte count for command
|| || dcerpc2: SMB - Bad format type for command
|| || dcerpc2: SMB - Bad AndX or data offset in command
|| || dcerpc2: SMB - Zero total data count in command
|| || dcerpc2: SMB - NetBIOS data length less than SMB header length
|| || dcerpc2: SMB - Remaining NetBIOS data length less than command length
|| || dcerpc2: SMB - Remaining NetBIOS data length less than command byte count
|| || dcerpc2: SMB - Remaining NetBIOS data length less than command data size
|| || dcerpc2: SMB - Remaining total data count less than this command data size
|| || dcerpc2: SMB - Total data sent greater than command total data expected
|| || dcerpc2: SMB - Byte count less than command data size
|| || dcerpc2: SMB - Invalid command data size for byte count
|| || dcerpc2: SMB - Excessive Tree Connect requests with pending Tree Connect responses
|| || dcerpc2: SMB - Excessive Read requests with pending Read responses
|| || dcerpc2: SMB - Excessive command chaining
|| || dcerpc2: SMB - Multiple chained login requests
|| || dcerpc2: SMB - Multiple chained tree connect requests
|| || dcerpc2: SMB - Chained login followed by logoff
|| || dcerpc2: SMB - Chained tree connect followed by tree disconnect
|| || dcerpc2: SMB - Chained open pipe followed by close pipe
|| || dcerpc2: SMB - Invalid share access
|| || dcerpc2: Connection-oriented DCE/RPC - Invalid major version
|| || dcerpc2: Connection-oriented DCE/RPC - Invalid minor version
|| || dcerpc2: Connection-oriented DCE/RPC - Invalid pdu type
|| || dcerpc2: Connection-oriented DCE/RPC - Fragment length less than header size
|| || dcerpc2: Connection-oriented DCE/RPC - Remaining fragment length less than size needed
|| || dcerpc2: Connection-oriented DCE/RPC - No context items specified
|| || dcerpc2: Connection-oriented DCE/RPC - No transfer syntaxes specified
|| || dcerpc2: Connection-oriented DCE/RPC - Fragment length on non-last fragment less than maximum negotiated fragment transmit size for client
|| || dcerpc2: Connection-oriented DCE/RPC - Fragment length greater than maximum negotiated fragment transmit size
|| || dcerpc2: Connection-oriented DCE/RPC - Alter Context byte order different from Bind
|| || dcerpc2: Connection-oriented DCE/RPC - Call id of non first/last fragment different from call id established for fragmented request
|| || dcerpc2: Connection-oriented DCE/RPC - Opnum of non first/last fragment different from opnum established for fragmented request
|| || dcerpc2: Connection-oriented DCE/RPC - Context id of non first/last fragment different from context id established for fragmented request
|| || dcerpc2: Connectionless DCE/RPC - Invalid major version
|| || dcerpc2: Connectionless DCE/RPC - Invalid pdu type
|| || dcerpc2: Connectionless DCE/RPC - Data length less than header size
|| || dcerpc2: Connectionless DCE/RPC - Bad sequence number
|| || ppm: rule tree disabled
|| || ppm: rule tree enabled
|| || internal: syn received
|| || internal: session established
|| || internal: session cleared
|| || sensitive_data: sensitive data global threshold exceeded
11、SELKS里的suricata的gpl-2.0.txt(非常重要)
GNU GENERAL PUBLIC LICENSE
Version , June Copyright (C) , Free Software Foundation, Inc.,
Franklin Street, Fifth Floor, Boston, MA - USA
Everyone is permitted to copy and distribute verbatim copies
of this license document, but changing it is not allowed. Preamble The licenses for most software are designed to take away your
freedom to share and change it. By contrast, the GNU General Public
License is intended to guarantee your freedom to share and change free
software--to make sure the software is free for all its users. This
General Public License applies to most of the Free Software
Foundation's software and to any other program whose authors commit to
using it. (Some other Free Software Foundation software is covered by
the GNU Lesser General Public License instead.) You can apply it to
your programs, too. When we speak of free software, we are referring to freedom, not
price. Our General Public Licenses are designed to make sure that you
have the freedom to distribute copies of free software (and charge for
this service if you wish), that you receive source code or can get it
if you want it, that you can change the software or use pieces of it
in new free programs; and that you know you can do these things. To protect your rights, we need to make restrictions that forbid
anyone to deny you these rights or to ask you to surrender the rights.
These restrictions translate to certain responsibilities for you if you
distribute copies of the software, or if you modify it. For example, if you distribute copies of such a program, whether
gratis or for a fee, you must give the recipients all the rights that
you have. You must make sure that they, too, receive or can get the
source code. And you must show them these terms so they know their
rights. We protect your rights with two steps: () copyright the software, and
() offer you this license which gives you legal permission to copy,
distribute and/or modify the software. Also, for each author's protection and ours, we want to make certain
that everyone understands that there is no warranty for this free
software. If the software is modified by someone else and passed on, we
want its recipients to know that what they have is not the original, so
that any problems introduced by others will not reflect on the original
authors' reputations. Finally, any free program is threatened constantly by software
patents. We wish to avoid the danger that redistributors of a free
program will individually obtain patent licenses, in effect making the
program proprietary. To prevent this, we have made it clear that any
patent must be licensed for everyone's free use or not licensed at all. The precise terms and conditions for copying, distribution and
modification follow. GNU GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION . This License applies to any program or other work which contains
a notice placed by the copyright holder saying it may be distributed
under the terms of this General Public License. The "Program", below,
refers to any such program or work, and a "work based on the Program"
means either the Program or any derivative work under copyright law:
that is to say, a work containing the Program or a portion of it,
either verbatim or with modifications and/or translated into another
language. (Hereinafter, translation is included without limitation in
the term "modification".) Each licensee is addressed as "you". Activities other than copying, distribution and modification are not
covered by this License; they are outside its scope. The act of
running the Program is not restricted, and the output from the Program
is covered only if its contents constitute a work based on the
Program (independent of having been made by running the Program).
Whether that is true depends on what the Program does. . You may copy and distribute verbatim copies of the Program's
source code as you receive it, in any medium, provided that you
conspicuously and appropriately publish on each copy an appropriate
copyright notice and disclaimer of warranty; keep intact all the
notices that refer to this License and to the absence of any warranty;
and give any other recipients of the Program a copy of this License
along with the Program. You may charge a fee for the physical act of transferring a copy, and
you may at your option offer warranty protection in exchange for a fee. . You may modify your copy or copies of the Program or any portion
of it, thus forming a work based on the Program, and copy and
distribute such modifications or work under the terms of Section
above, provided that you also meet all of these conditions: a) You must cause the modified files to carry prominent notices
stating that you changed the files and the date of any change. b) You must cause any work that you distribute or publish, that in
whole or in part contains or is derived from the Program or any
part thereof, to be licensed as a whole at no charge to all third
parties under the terms of this License. c) If the modified program normally reads commands interactively
when run, you must cause it, when started running for such
interactive use in the most ordinary way, to print or display an
announcement including an appropriate copyright notice and a
notice that there is no warranty (or else, saying that you provide
a warranty) and that users may redistribute the program under
these conditions, and telling the user how to view a copy of this
License. (Exception: if the Program itself is interactive but
does not normally print such an announcement, your work based on
the Program is not required to print an announcement.) These requirements apply to the modified work as a whole. If
identifiable sections of that work are not derived from the Program,
and can be reasonably considered independent and separate works in
themselves, then this License, and its terms, do not apply to those
sections when you distribute them as separate works. But when you
distribute the same sections as part of a whole which is a work based
on the Program, the distribution of the whole must be on the terms of
this License, whose permissions for other licensees extend to the
entire whole, and thus to each and every part regardless of who wrote it. Thus, it is not the intent of this section to claim rights or contest
your rights to work written entirely by you; rather, the intent is to
exercise the right to control the distribution of derivative or
collective works based on the Program. In addition, mere aggregation of another work not based on the Program
with the Program (or with a work based on the Program) on a volume of
a storage or distribution medium does not bring the other work under
the scope of this License. . You may copy and distribute the Program (or a work based on it,
under Section ) in object code or executable form under the terms of
Sections and above provided that you also do one of the following: a) Accompany it with the complete corresponding machine-readable
source code, which must be distributed under the terms of Sections
and above on a medium customarily used for software interchange; or, b) Accompany it with a written offer, valid for at least three
years, to give any third party, for a charge no more than your
cost of physically performing source distribution, a complete
machine-readable copy of the corresponding source code, to be
distributed under the terms of Sections and above on a medium
customarily used for software interchange; or, c) Accompany it with the information you received as to the offer
to distribute corresponding source code. (This alternative is
allowed only for noncommercial distribution and only if you
received the program in object code or executable form with such
an offer, in accord with Subsection b above.) The source code for a work means the preferred form of the work for
making modifications to it. For an executable work, complete source
code means all the source code for all modules it contains, plus any
associated interface definition files, plus the scripts used to
control compilation and installation of the executable. However, as a
special exception, the source code distributed need not include
anything that is normally distributed (in either source or binary
form) with the major components (compiler, kernel, and so on) of the
operating system on which the executable runs, unless that component
itself accompanies the executable. If distribution of executable or object code is made by offering
access to copy from a designated place, then offering equivalent
access to copy the source code from the same place counts as
distribution of the source code, even though third parties are not
compelled to copy the source along with the object code. . You may not copy, modify, sublicense, or distribute the Program
except as expressly provided under this License. Any attempt
otherwise to copy, modify, sublicense or distribute the Program is
void, and will automatically terminate your rights under this License.
However, parties who have received copies, or rights, from you under
this License will not have their licenses terminated so long as such
parties remain in full compliance. . You are not required to accept this License, since you have not
signed it. However, nothing else grants you permission to modify or
distribute the Program or its derivative works. These actions are
prohibited by law if you do not accept this License. Therefore, by
modifying or distributing the Program (or any work based on the
Program), you indicate your acceptance of this License to do so, and
all its terms and conditions for copying, distributing or modifying
the Program or works based on it. . Each time you redistribute the Program (or any work based on the
Program), the recipient automatically receives a license from the
original licensor to copy, distribute or modify the Program subject to
these terms and conditions. You may not impose any further
restrictions on the recipients' exercise of the rights granted herein.
You are not responsible for enforcing compliance by third parties to
this License. . If, as a consequence of a court judgment or allegation of patent
infringement or for any other reason (not limited to patent issues),
conditions are imposed on you (whether by court order, agreement or
otherwise) that contradict the conditions of this License, they do not
excuse you from the conditions of this License. If you cannot
distribute so as to satisfy simultaneously your obligations under this
License and any other pertinent obligations, then as a consequence you
may not distribute the Program at all. For example, if a patent
license would not permit royalty-free redistribution of the Program by
all those who receive copies directly or indirectly through you, then
the only way you could satisfy both it and this License would be to
refrain entirely from distribution of the Program. If any portion of this section is held invalid or unenforceable under
any particular circumstance, the balance of the section is intended to
apply and the section as a whole is intended to apply in other
circumstances. It is not the purpose of this section to induce you to infringe any
patents or other property right claims or to contest validity of any
such claims; this section has the sole purpose of protecting the
integrity of the free software distribution system, which is
implemented by public license practices. Many people have made
generous contributions to the wide range of software distributed
through that system in reliance on consistent application of that
system; it is up to the author/donor to decide if he or she is willing
to distribute software through any other system and a licensee cannot
impose that choice. This section is intended to make thoroughly clear what is believed to
be a consequence of the rest of this License. . If the distribution and/or use of the Program is restricted in
certain countries either by patents or by copyrighted interfaces, the
original copyright holder who places the Program under this License
may add an explicit geographical distribution limitation excluding
those countries, so that distribution is permitted only in or among
countries not thus excluded. In such case, this License incorporates
the limitation as if written in the body of this License. . The Free Software Foundation may publish revised and/or new versions
of the General Public License from time to time. Such new versions will
be similar in spirit to the present version, but may differ in detail to
address new problems or concerns. Each version is given a distinguishing version number. If the Program
specifies a version number of this License which applies to it and "any
later version", you have the option of following the terms and conditions
either of that version or of any later version published by the Free
Software Foundation. If the Program does not specify a version number of
this License, you may choose any version ever published by the Free Software
Foundation. . If you wish to incorporate parts of the Program into other free
programs whose distribution conditions are different, write to the author
to ask for permission. For software which is copyrighted by the Free
Software Foundation, write to the Free Software Foundation; we sometimes
make exceptions for this. Our decision will be guided by the two goals
of preserving the free status of all derivatives of our free software and
of promoting the sharing and reuse of software generally. NO WARRANTY . BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY
FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN
OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES
PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED
OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS
TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE
PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING,
REPAIR OR CORRECTION. . IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING
WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR
REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES,
INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING
OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED
TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY
YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER
PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE
POSSIBILITY OF SUCH DAMAGES. END OF TERMS AND CONDITIONS How to Apply These Terms to Your New Programs If you develop a new program, and you want it to be of the greatest
possible use to the public, the best way to achieve this is to make it
free software which everyone can redistribute and change under these terms. To do so, attach the following notices to the program. It is safest
to attach them to the start of each source file to most effectively
convey the exclusion of warranty; and each file should have at least
the "copyright" line and a pointer to where the full notice is found. <one line to give the program's name and a brief idea of what it does.>
Copyright (C) <year> <name of author> This program is free software; you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation; either version of the License, or
(at your option) any later version. This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details. You should have received a copy of the GNU General Public License along
with this program; if not, write to the Free Software Foundation, Inc.,
Franklin Street, Fifth Floor, Boston, MA - USA. Also add information on how to contact you by electronic and paper mail. If the program is interactive, make it output a short notice like this
when it starts in an interactive mode: Gnomovision version , Copyright (C) year name of author
Gnomovision comes with ABSOLUTELY NO WARRANTY; for details type `show w'.
This is free software, and you are welcome to redistribute it
under certain conditions; type `show c' for details. The hypothetical commands `show w' and `show c' should show the appropriate
parts of the General Public License. Of course, the commands you use may
be called something other than `show w' and `show c'; they could even be
mouse-clicks or menu items--whatever suits your program. You should also get your employer (if you work as a programmer) or your
school, if any, to sign a "copyright disclaimer" for the program, if
necessary. Here is a sample; alter the names: Yoyodyne, Inc., hereby disclaims all copyright interest in the program
`Gnomovision' (which makes passes at compilers) written by James Hacker. <signature of Ty Coon>, April
Ty Coon, President of Vice This General Public License does not permit incorporating your program into
proprietary programs. If your program is a subroutine library, you may
consider it more useful to permit linking proprietary applications with the
library. If this is what you want to do, use the GNU Lesser General
Public License instead of this License.
12、SELKS里的suricata的http-events.rules(非常重要)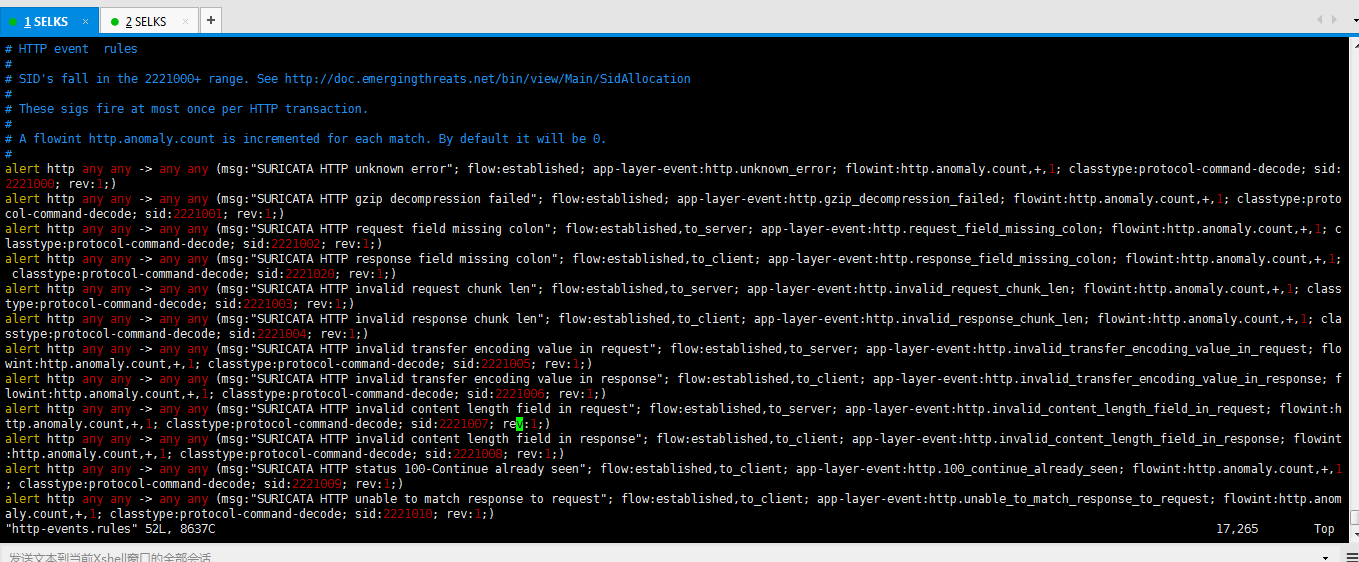
# HTTP event rules
#
# SID's fall in the 2221000+ range. See http://doc.emergingthreats.net/bin/view/Main/SidAllocation
#
# These sigs fire at most once per HTTP transaction.
#
# A flowint http.anomaly.count is incremented for each match. By default it will be .
#
alert http any any -> any any (msg:"SURICATA HTTP unknown error"; flow:established; app-layer-event:http.unknown_error; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP gzip decompression failed"; flow:established; app-layer-event:http.gzip_decompression_failed; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP request field missing colon"; flow:established,to_server; app-layer-event:http.request_field_missing_colon; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP response field missing colon"; flow:established,to_client; app-layer-event:http.response_field_missing_colon; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP invalid request chunk len"; flow:established,to_server; app-layer-event:http.invalid_request_chunk_len; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP invalid response chunk len"; flow:established,to_client; app-layer-event:http.invalid_response_chunk_len; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP invalid transfer encoding value in request"; flow:established,to_server; app-layer-event:http.invalid_transfer_encoding_value_in_request; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP invalid transfer encoding value in response"; flow:established,to_client; app-layer-event:http.invalid_transfer_encoding_value_in_response; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP invalid content length field in request"; flow:established,to_server; app-layer-event:http.invalid_content_length_field_in_request; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP invalid content length field in response"; flow:established,to_client; app-layer-event:http.invalid_content_length_field_in_response; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP status 100-Continue already seen"; flow:established,to_client; app-layer-event:http.100_continue_already_seen; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP unable to match response to request"; flow:established,to_client; app-layer-event:http.unable_to_match_response_to_request; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP invalid server port in request"; flow:established,to_server; app-layer-event:http.invalid_server_port_in_request; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP invalid authority port"; flow:established; app-layer-event:http.invalid_authority_port; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP request header invalid"; flow:established,to_server; app-layer-event:http.request_header_invalid; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP response header invalid"; flow:established,to_client; app-layer-event:http.response_header_invalid; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP missing Host header"; flow:established,to_server; app-layer-event:http.missing_host_header; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
# Alert if hostname is both part of URL and Host header and they are not the same.
alert http any any -> any any (msg:"SURICATA HTTP Host header ambiguous"; flow:established,to_server; app-layer-event:http.host_header_ambiguous; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP invalid request field folding"; flow:established,to_server; app-layer-event:http.invalid_request_field_folding; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP invalid response field folding"; flow:established,to_client; app-layer-event:http.invalid_response_field_folding; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP request buffer too long"; flow:established,to_server; app-layer-event:http.request_field_too_long; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert http any any -> any any (msg:"SURICATA HTTP response buffer too long"; flow:established,to_client; app-layer-event:http.response_field_too_long; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
# Multipart parser detected generic error.
alert http any any -> any any (msg:"SURICATA HTTP multipart generic error"; flow:established,to_server; app-layer-event:http.multipart_generic_error; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
# Multipart header claiming a file to present, but no actual filedata available.
alert http any any -> any any (msg:"SURICATA HTTP multipart no filedata"; flow:established,to_server; app-layer-event:http.multipart_no_filedata; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
# Multipart header invalid.
alert http any any -> any any (msg:"SURICATA HTTP multipart invalid header"; flow:established,to_server; app-layer-event:http.multipart_invalid_header; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
# Warn when the port in the Host: header doesn't match the actual TCP Server port.
alert http any any -> any any (msg:"SURICATA HTTP request server port doesn't match TCP port"; flow:established,to_server; app-layer-event:http.request_server_port_tcp_port_mismatch; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
# Host part of URI is invalid
alert http any any -> any any (msg:"SURICATA HTTP Host part of URI is invalid"; flow:established,to_server; app-layer-event:http.request_uri_host_invalid; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
# Host header is invalid
alert http any any -> any any (msg:"SURICATA HTTP Host header invalid"; flow:established,to_server; app-layer-event:http.request_header_host_invalid; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
# URI is terminated by non-compliant characters. RFC allows for space (0x20), but many implementations permit others like tab and more.
alert http any any -> any any (msg:"SURICATA HTTP URI terminated by non-compliant character"; flow:established,to_server; app-layer-event:http.uri_delim_non_compliant; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
# Method is terminated by non-compliant characters. RFC allows for space (0x20), but many implementations permit others like tab and more.
alert http any any -> any any (msg:"SURICATA HTTP METHOD terminated by non-compliant character"; flow:established,to_server; app-layer-event:http.method_delim_non_compliant; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
# Request line started with whitespace
alert http any any -> any any (msg:"SURICATA HTTP Request line with leading whitespace"; flow:established,to_server; app-layer-event:http.request_line_leading_whitespace; flowint:http.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;) # next sid
13、SELKS里的suricata的LICENSE(非常重要)

# Emerging Threats
#
# This distribution may contain rules under three different licenses.
#
# Rules with sids through , and through are under the GPLv2.
# A copy of that license is available at http://www.gnu.org/licenses/gpl-2.0.html
#
# Rules with sids through are from Emerging Threats and are covered under the BSD License
# as follows:
#
#*************************************************************
# Copyright (c) -, Emerging Threats
# All rights reserved.
#
# Redistribution and use in source and binary forms, with or without modification, are permitted provided that the
# following conditions are met:
#
# * Redistributions of source code must retain the above copyright notice, this list of conditions and the following
# disclaimer.
# * Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the
# following disclaimer in the documentation and/or other materials provided with the distribution.
# * Neither the name of the nor the names of its contributors may be used to endorse or promote products derived
# from this software without specific prior written permission.
#
# THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS AS IS AND ANY EXPRESS OR IMPLIED WARRANTIES,
# INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
# DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,
# SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR
# SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY,
# WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE
# USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
#
#*************************************************************
#
#
# Rules with sids through are provided by Emerging Threats Pro and are covered by the license
# provided in this distribution titled ETPRO-License.txt
#
#
14、SELKS里的suricata的local.rules(非常重要)
15、SELKS里的suricata的modbus-events.rules(非常重要)
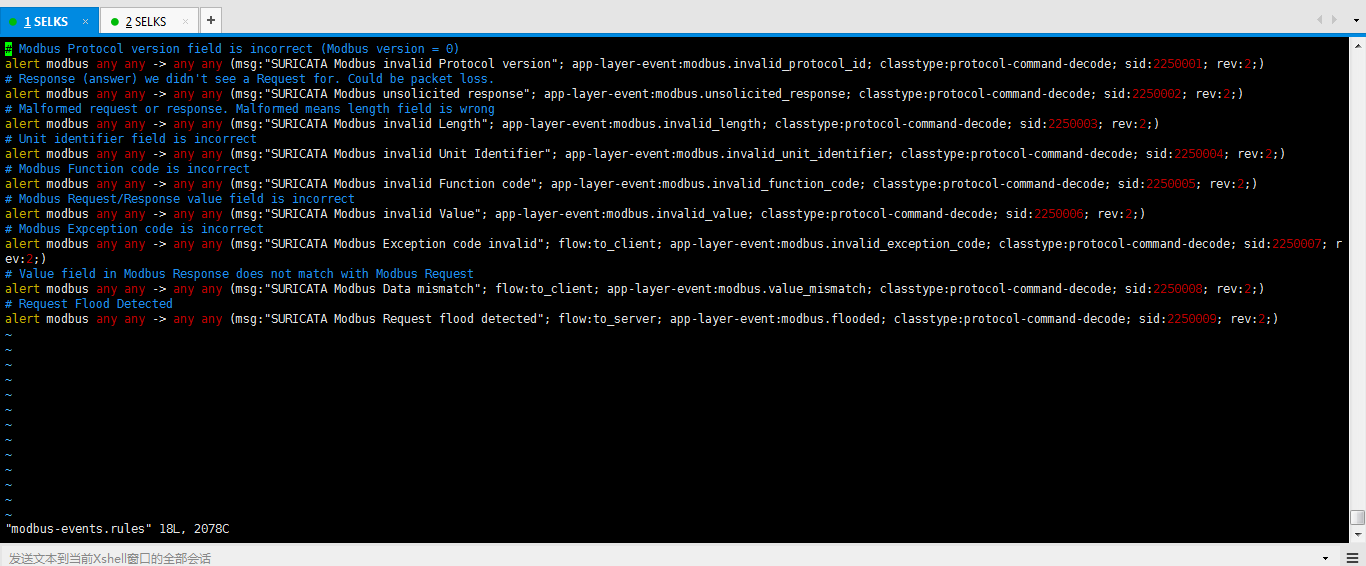
# Modbus Protocol version field is incorrect (Modbus version = )
alert modbus any any -> any any (msg:"SURICATA Modbus invalid Protocol version"; app-layer-event:modbus.invalid_protocol_id; classtype:protocol-command-decode; sid:; rev:;)
# Response (answer) we didn't see a Request for. Could be packet loss.
alert modbus any any -> any any (msg:"SURICATA Modbus unsolicited response"; app-layer-event:modbus.unsolicited_response; classtype:protocol-command-decode; sid:; rev:;)
# Malformed request or response. Malformed means length field is wrong
alert modbus any any -> any any (msg:"SURICATA Modbus invalid Length"; app-layer-event:modbus.invalid_length; classtype:protocol-command-decode; sid:; rev:;)
# Unit identifier field is incorrect
alert modbus any any -> any any (msg:"SURICATA Modbus invalid Unit Identifier"; app-layer-event:modbus.invalid_unit_identifier; classtype:protocol-command-decode; sid:; rev:;)
# Modbus Function code is incorrect
alert modbus any any -> any any (msg:"SURICATA Modbus invalid Function code"; app-layer-event:modbus.invalid_function_code; classtype:protocol-command-decode; sid:; rev:;)
# Modbus Request/Response value field is incorrect
alert modbus any any -> any any (msg:"SURICATA Modbus invalid Value"; app-layer-event:modbus.invalid_value; classtype:protocol-command-decode; sid:; rev:;)
# Modbus Expception code is incorrect
alert modbus any any -> any any (msg:"SURICATA Modbus Exception code invalid"; flow:to_client; app-layer-event:modbus.invalid_exception_code; classtype:protocol-command-decode; sid:; rev:;)
# Value field in Modbus Response does not match with Modbus Request
alert modbus any any -> any any (msg:"SURICATA Modbus Data mismatch"; flow:to_client; app-layer-event:modbus.value_mismatch; classtype:protocol-command-decode; sid:; rev:;)
# Request Flood Detected
alert modbus any any -> any any (msg:"SURICATA Modbus Request flood detected"; flow:to_server; app-layer-event:modbus.flooded; classtype:protocol-command-decode; sid:; rev:;)
16、SELKS里的suricata的ntp-events.rules(非常重要)
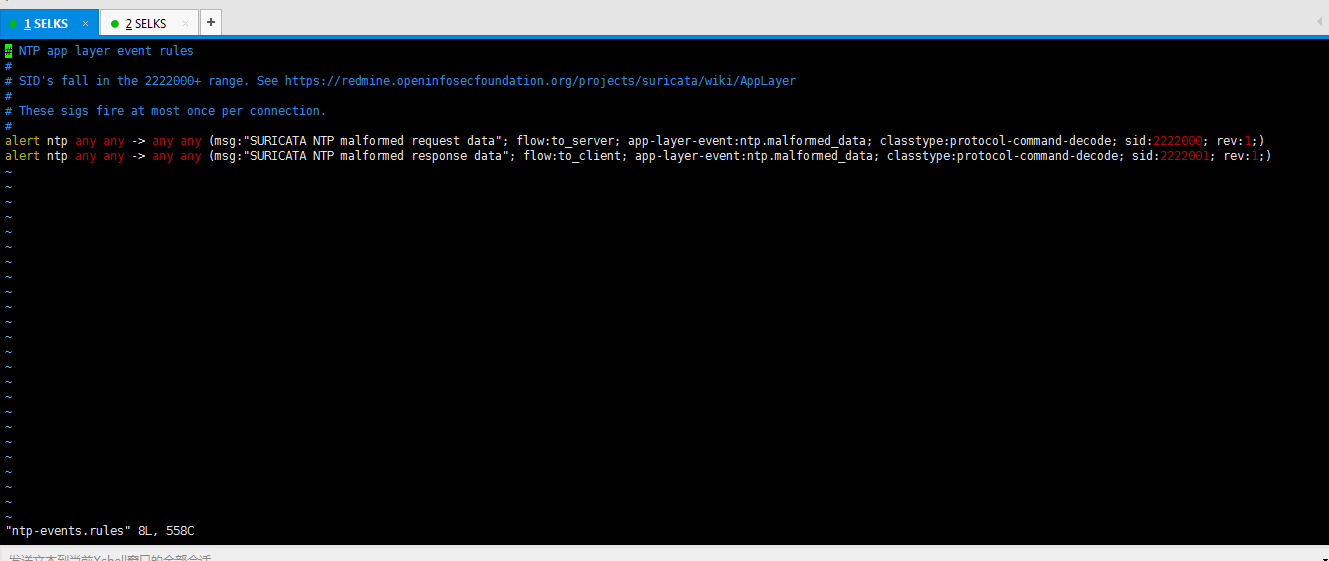
# NTP app layer event rules
#
# SID's fall in the 2222000+ range. See https://redmine.openinfosecfoundation.org/projects/suricata/wiki/AppLayer
#
# These sigs fire at most once per connection.
#
alert ntp any any -> any any (msg:"SURICATA NTP malformed request data"; flow:to_server; app-layer-event:ntp.malformed_data; classtype:protocol-command-decode; sid:; rev:;)
alert ntp any any -> any any (msg:"SURICATA NTP malformed response data"; flow:to_client; app-layer-event:ntp.malformed_data; classtype:protocol-command-decode; sid:; rev:;)
17、SELKS里的suricata的reference.config(非常重要)
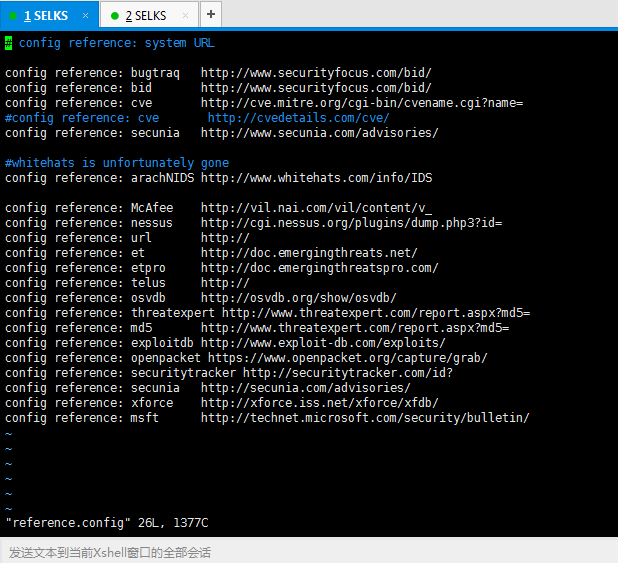
# config reference: system URL config reference: bugtraq http://www.securityfocus.com/bid/
config reference: bid http://www.securityfocus.com/bid/
config reference: cve http://cve.mitre.org/cgi-bin/cvename.cgi?name=
#config reference: cve http://cvedetails.com/cve/
config reference: secunia http://www.secunia.com/advisories/ #whitehats is unfortunately gone
config reference: arachNIDS http://www.whitehats.com/info/IDS config reference: McAfee http://vil.nai.com/vil/content/v_
config reference: nessus http://cgi.nessus.org/plugins/dump.php3?id=
config reference: url http://
config reference: et http://doc.emergingthreats.net/
config reference: etpro http://doc.emergingthreatspro.com/
config reference: telus http://
config reference: osvdb http://osvdb.org/show/osvdb/
config reference: threatexpert http://www.threatexpert.com/report.aspx?md5=
config reference: md5 http://www.threatexpert.com/report.aspx?md5=
config reference: exploitdb http://www.exploit-db.com/exploits/
config reference: openpacket https://www.openpacket.org/capture/grab/
config reference: securitytracker http://securitytracker.com/id?
config reference: secunia http://secunia.com/advisories/
config reference: xforce http://xforce.iss.net/xforce/xfdb/
config reference: msft http://technet.microsoft.com/security/bulletin/
18、SELKS里的suricata的scirius.rules(非常重要)
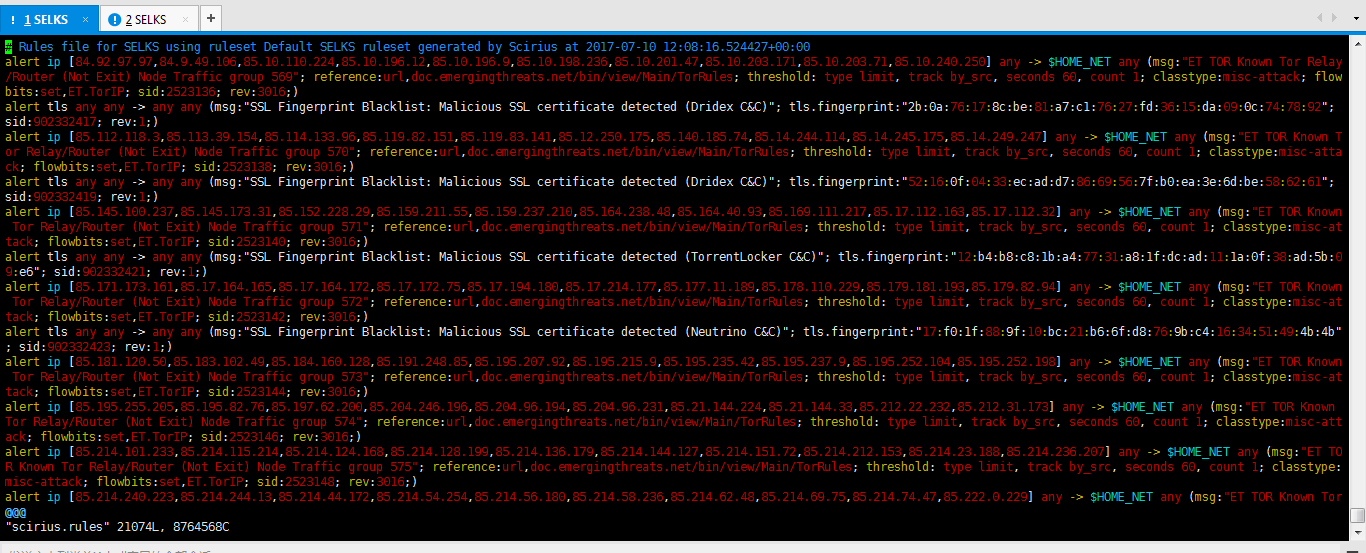
这里由于太长,未粘贴了。
19、SELKS里的suricata的sid-msg.map(非常重要)

因为太长,所以未粘贴了。
20、SELKS里的suricata的smtp-events.rules(非常重要)
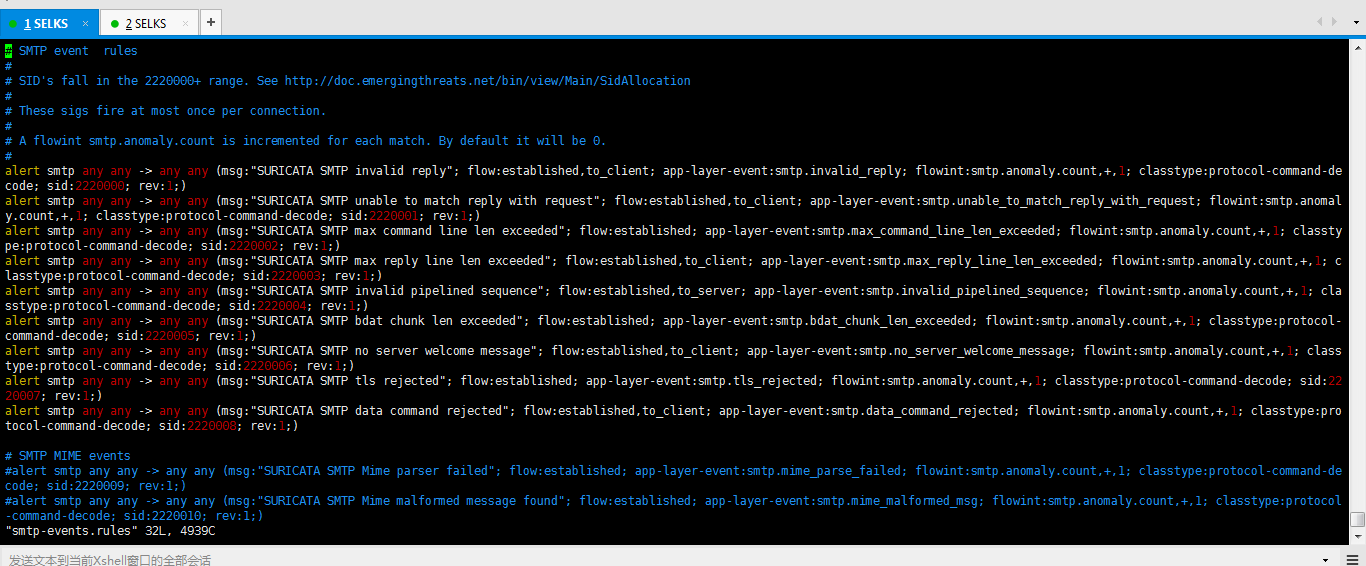
# SMTP event rules
#
# SID's fall in the 2220000+ range. See http://doc.emergingthreats.net/bin/view/Main/SidAllocation
#
# These sigs fire at most once per connection.
#
# A flowint smtp.anomaly.count is incremented for each match. By default it will be .
#
alert smtp any any -> any any (msg:"SURICATA SMTP invalid reply"; flow:established,to_client; app-layer-event:smtp.invalid_reply; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert smtp any any -> any any (msg:"SURICATA SMTP unable to match reply with request"; flow:established,to_client; app-layer-event:smtp.unable_to_match_reply_with_request; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert smtp any any -> any any (msg:"SURICATA SMTP max command line len exceeded"; flow:established; app-layer-event:smtp.max_command_line_len_exceeded; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert smtp any any -> any any (msg:"SURICATA SMTP max reply line len exceeded"; flow:established,to_client; app-layer-event:smtp.max_reply_line_len_exceeded; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert smtp any any -> any any (msg:"SURICATA SMTP invalid pipelined sequence"; flow:established,to_server; app-layer-event:smtp.invalid_pipelined_sequence; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert smtp any any -> any any (msg:"SURICATA SMTP bdat chunk len exceeded"; flow:established; app-layer-event:smtp.bdat_chunk_len_exceeded; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert smtp any any -> any any (msg:"SURICATA SMTP no server welcome message"; flow:established,to_client; app-layer-event:smtp.no_server_welcome_message; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert smtp any any -> any any (msg:"SURICATA SMTP tls rejected"; flow:established; app-layer-event:smtp.tls_rejected; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert smtp any any -> any any (msg:"SURICATA SMTP data command rejected"; flow:established,to_client; app-layer-event:smtp.data_command_rejected; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;) # SMTP MIME events
#alert smtp any any -> any any (msg:"SURICATA SMTP Mime parser failed"; flow:established; app-layer-event:smtp.mime_parse_failed; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
#alert smtp any any -> any any (msg:"SURICATA SMTP Mime malformed message found"; flow:established; app-layer-event:smtp.mime_malformed_msg; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
#alert smtp any any -> any any (msg:"SURICATA SMTP Mime base64-decoding failed"; flow:established; app-layer-event:smtp.mime_invalid_base64; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
#alert smtp any any -> any any (msg:"SURICATA SMTP Mime header name len exceeded"; flow:established; app-layer-event:smtp.mime_long_header_name; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
#alert smtp any any -> any any (msg:"SURICATA SMTP Mime header value len exceeded"; flow:established; app-layer-event:smtp.mime_long_header_value; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
#alert smtp any any -> any any (msg:"SURICATA SMTP Mime quoted-printable-decoding failed"; flow:established; app-layer-event:smtp.mime_invalid_qp; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
#alert smtp any any -> any any (msg:"SURICATA SMTP Mime line len exceeded"; flow:established; app-layer-event:smtp.mime_long_line; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
#alert smtp any any -> any any (msg:"SURICATA SMTP Mime encoded line len exceeded"; flow:established; app-layer-event:smtp.mime_long_enc_line; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert smtp any any -> any any (msg:"SURICATA SMTP Mime boundary length exceeded"; flow:established,to_server; app-layer-event:smtp.mime_long_boundary; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;) alert smtp any any -> any any (msg:"SURICATA SMTP duplicate fields"; flow:established,to_server; app-layer-event:smtp.duplicate_fields; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert smtp any any -> any any (msg:"SURICATA SMTP unparsable content"; flow:established,to_server; app-layer-event:smtp.unparsable_content; flowint:smtp.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
# next sid
21、SELKS里的suricata的stream-events.rules(非常重要)

# Stream events -- rules for matching on TCP stream engine events.
#
# SID's fall in the 2210000+ range. See http://doc.emergingthreats.net/bin/view/Main/SidAllocation
#
alert tcp any any -> any any (msg:"SURICATA STREAM 3way handshake with ack in wrong dir"; stream-event:3whs_ack_in_wrong_dir; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 3way handshake async wrong sequence"; stream-event:3whs_async_wrong_seq; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 3way handshake right seq wrong ack evasion"; stream-event:3whs_right_seq_wrong_ack_evasion; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 3way handshake SYNACK in wrong direction"; stream-event:3whs_synack_in_wrong_direction; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 3way handshake SYNACK resend with different ack"; stream-event:3whs_synack_resend_with_different_ack; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 3way handshake SYNACK resend with different seq"; stream-event:3whs_synack_resend_with_diff_seq; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 3way handshake SYNACK to server on SYN recv"; stream-event:3whs_synack_toserver_on_syn_recv; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 3way handshake SYNACK with wrong ack"; stream-event:3whs_synack_with_wrong_ack; classtype:protocol-command-decode; sid:; rev:;)
# Excessive SYN/ACKs within a session. Limit is set in stream engine, "stream.max-synack-queued".
alert tcp any any -> any any (msg:"SURICATA STREAM 3way handshake excessive different SYN/ACKs"; stream-event:3whs_synack_flood; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 3way handshake SYN resend different seq on SYN recv"; stream-event:3whs_syn_resend_diff_seq_on_syn_recv; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 3way handshake SYN to client on SYN recv"; stream-event:3whs_syn_toclient_on_syn_recv; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 3way handshake wrong seq wrong ack"; stream-event:3whs_wrong_seq_wrong_ack; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 4way handshake SYNACK with wrong ACK"; stream-event:4whs_synack_with_wrong_ack; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 4way handshake SYNACK with wrong SYN"; stream-event:4whs_synack_with_wrong_syn; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 4way handshake wrong seq"; stream-event:4whs_wrong_seq; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM 4way handshake invalid ack"; stream-event:4whs_invalid_ack; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM CLOSEWAIT ACK out of window"; stream-event:closewait_ack_out_of_window; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM CLOSEWAIT FIN out of window"; stream-event:closewait_fin_out_of_window; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM CLOSEWAIT invalid ACK"; stream-event:closewait_invalid_ack; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM CLOSING ACK wrong seq"; stream-event:closing_ack_wrong_seq; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM CLOSING invalid ACK"; stream-event:closing_invalid_ack; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM ESTABLISHED packet out of window"; stream-event:est_packet_out_of_window; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM ESTABLISHED SYNACK resend"; stream-event:est_synack_resend; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM ESTABLISHED SYNACK resend with different ACK"; stream-event:est_synack_resend_with_different_ack; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM ESTABLISHED SYNACK resend with different seq"; stream-event:est_synack_resend_with_diff_seq; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM ESTABLISHED SYNACK to server"; stream-event:est_synack_toserver; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM ESTABLISHED SYN resend"; stream-event:est_syn_resend; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM ESTABLISHED SYN resend with different seq"; stream-event:est_syn_resend_diff_seq; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM ESTABLISHED SYN to client"; stream-event:est_syn_toclient; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM ESTABLISHED invalid ack"; stream-event:est_invalid_ack; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM FIN invalid ack"; stream-event:fin_invalid_ack; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM FIN1 ack with wrong seq"; stream-event:fin1_ack_wrong_seq; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM FIN1 FIN with wrong seq"; stream-event:fin1_fin_wrong_seq; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM FIN1 invalid ack"; stream-event:fin1_invalid_ack; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM FIN2 ack with wrong seq"; stream-event:fin2_ack_wrong_seq; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM FIN2 FIN with wrong seq"; stream-event:fin2_fin_wrong_seq; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM FIN2 invalid ack"; stream-event:fin2_invalid_ack; classtype:protocol-command-decode; sid:; rev:;)
# very common when looking at midstream traffic after IDS started
#alert tcp any any -> any any (msg:"SURICATA STREAM FIN recv but no session"; stream-event:fin_but_no_session; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM FIN out of window"; stream-event:fin_out_of_window; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM Last ACK with wrong seq"; stream-event:lastack_ack_wrong_seq; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM Last ACK invalid ACK"; stream-event:lastack_invalid_ack; classtype:protocol-command-decode; sid:; rev:;)
# very common when looking at midstream traffic after IDS started
#alert tcp any any -> any any (msg:"SURICATA STREAM RST recv but no session"; stream-event:rst_but_no_session; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM TIMEWAIT ACK with wrong seq"; stream-event:timewait_ack_wrong_seq; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM TIMEWAIT invalid ack"; stream-event:timewait_invalid_ack; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM Packet with invalid timestamp"; stream-event:pkt_invalid_timestamp; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM Packet with invalid ack"; stream-event:pkt_invalid_ack; classtype:protocol-command-decode; sid:; rev:;)
# Broken TCP: ack field non , but ACK flag not set. http://ask.wireshark.org/questions/3183/acknowledgment-number-broken-tcp-the-acknowledge-field-is-nonzero-while-the-ack-flag-is-not-set
# Often result of broken load balancers, firewalls and such.
#alert tcp any any -> any any (msg:"SURICATA STREAM Packet with broken ack"; stream-event:pkt_broken_ack; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM SHUTDOWN RST invalid ack"; stream-event:rst_invalid_ack; classtype:protocol-command-decode; sid:; rev:;)
# SYN (re)send during shutdown (closing, closewait, finwait1, finwait2, lastack, timewait states)
#alert tcp any any -> any any (msg:"SURICATA STREAM SYN resend"; stream-event:shutdown_syn_resend; classtype:protocol-command-decode; sid:; rev:;)
# Sequence gap: missing data in the reassembly engine. Usually due to packet loss. Will be very noisy on a overloaded link / sensor.
#alert tcp any any -> any any (msg:"SURICATA STREAM reassembly sequence GAP -- missing packet(s)"; stream-event:reassembly_seq_gap; classtype:protocol-command-decode; sid:; rev:;)
alert tcp any any -> any any (msg:"SURICATA STREAM reassembly overlap with different data"; stream-event:reassembly_overlap_different_data; classtype:protocol-command-decode; sid:; rev:;)
# Bad Window Update: see bug for an explanation
alert tcp any any -> any any (msg:"SURICATA STREAM bad window update"; stream-event:pkt_bad_window_update; classtype:protocol-command-decode; sid:; rev:;) # retransmission detection
#
# The rules below match on retransmissions detected in various stages of the
# stream engine. They are all "noalert" rules that increment the counter
# tcp.retransmission.count. The last rule sid: matches if the counter
# reaches . Increase this number if the rule is too noisy.
#
# "regular" retransmissions, only count
alert tcp any any -> any any (msg:"SURICATA STREAM ESTABLISHED retransmission packet before last ack"; stream-event:est_pkt_before_last_ack; flowint:tcp.retransmission.count,+,; noalert; classtype:protocol-command-decode; sid:; rev:;)
# retransmission, only count
alert tcp any any -> any any (msg:"SURICATA STREAM CLOSEWAIT retransmission packet before last ack"; stream-event:closewait_pkt_before_last_ack; flowint:tcp.retransmission.count,+,; noalert; classtype:protocol-command-decode; sid:; rev:;)
# retransmission of pkt before reassembly window, only count
alert tcp any any -> any any (msg:"SURICATA STREAM reassembly segment before base seq (retransmission)"; stream-event:reassembly_segment_before_base_seq; flowint:tcp.retransmission.count,+,; noalert; classtype:protocol-command-decode; sid:; rev:;)
# count "general" retransmissions
alert tcp any any -> any any (msg:"SURICATA STREAM Packet is retransmission"; stream-event:pkt_retransmission; flowint:tcp.retransmission.count,+,; noalert; classtype:protocol-command-decode; sid:; rev:;)
# rule to alert if a stream has excessive retransmissions
alert tcp any any -> any any (msg:"SURICATA STREAM excessive retransmissions"; flowbits:isnotset,tcp.retransmission.alerted; flowint:tcp.retransmission.count,>=,; flowbits:set,tcp.retransmission.alerted; classtype:protocol-command-decode; sid:; rev:;) # next sid
22、SELKS里的suricata的suricata-1.3-etpro-etnamed.yaml(非常重要)

%YAML 1.1
--- # Suricata configuration file. In addition to the comments describing all
# options in this file, full documentation can be found at:
# https://redmine.openinfosecfoundation.org/projects/suricata/wiki/Suricatayaml # NOTE: This version of the Suricata.yaml file is modified by the Emerging Threats
# Pro Team to reflect the default assumptions on inspection depths. Comments have been
# added to note where users may tune defaults back where performance is a
# concern. The default stance of this config is maximum detection.
# Decisions on features such as file extraction and pcap logging must be made
# locally. These are left at defaults. # Number of packets allowed to be processed simultaneously. Default is a
# conservative . A higher number will make sure CPU's/CPU cores will be
# more easily kept busy, but may negatively impact caching.
#
# If you are using the CUDA pattern matcher (b2g_cuda below), different rules
# apply. In that case try something like or more. This is because the CUDA
# pattern matcher scans many packets in parallel.
max-pending-packets: # Runmode the engine should use. Please check --list-runmodes to get the available
# runmodes for each packet acquisition method. Defaults to "autofp" (auto flow pinned
# load balancing).
#runmode: autofp # Specifies the kind of flow load balancer used by the flow pinned autofp mode.
#
# Supported schedulers are:
#
# round-robin - Flows assigned to threads in a round robin fashion.
# active-packets - Flows assigned to threads that have the lowest number of
# unprocessed packets (default).
# hash - Flow alloted usihng the address hash. More of a random
# technique. Was the default in Suricata 1.2. and older.
#
#autofp-scheduler: active-packets # Default pid file.
# Will use this file if no --pidfile in command options.
#pid-file: /var/run/suricata.pid # Preallocated size for packet. Default is which is the classical
# size for pcap on ethernet. You should adjust this value to the highest
# packet size (MTU + hardware header) on your system.
#default-packet-size: # The default logging directory. Any log or output file will be
# placed here if its not specified with a full path name. This can be
# overridden with the -l command line parameter.
default-log-dir: /var/log/suricata/ # Unix command socket can be used to pass commands to suricata.
# An external tool can then connect to get information from suricata
# or trigger some modification of the engine.
#unix-command: yes # Configure the type of alert (and other) logging you would like.
outputs: # a line based alerts log similar to Snort's fast.log
- fast:
enabled: yes
filename: fast.log
append: yes
#filetype: regular # 'regular', 'unix_stream' or 'unix_dgram' # alert output for use with Barnyard2
- unified2-alert:
enabled: yes
filename: unified2.alert # File size limit. Can be specified in kb, mb, gb. Just a number
# is parsed as bytes.
#limit: 32mb # a line based log of HTTP requests (no alerts)
- http-log:
enabled: yes
filename: http.log
append: yes
#extended: yes # enable this for extended logging information
#custom: yes # enabled the custom logging format (defined by customformat)
#customformat: "%{%D-%H:%M:%S}t.%z %{X-Forwarded-For}i %H %m %h %u %s %B %a:%p -> %A:%P"
#filetype: regular # 'regular', 'unix_stream' or 'unix_dgram' # a line based log of TLS handshake parameters (no alerts)
- tls-log:
enabled: yes # Log TLS connections.
filename: tls.log # File to store TLS logs.
extended: yes # Log extended information like fingerprint
certs-log-dir: certs # directory to store the certificates files # a line based log to used with pcap file study.
# this module is dedicated to offline pcap parsing (empty output
# if used with another kind of input). It can interoperate with
# pcap parser like wireshark via the suriwire plugin.
- pcap-info:
enabled: no # Packet log... log packets in pcap format. modes of operation: "normal"
# and "sguil".
#
# In normal mode a pcap file "filename" is created in the default-log-dir,
# or are as specified by "dir". In Sguil mode "dir" indicates the base directory.
# In this base dir the pcaps are created in th directory structure Sguil expects:
#
# $sguil-base-dir/YYYY-MM-DD/$filename.<timestamp>
#
# By default all packets are logged except:
# - TCP streams beyond stream.reassembly.depth
# - encrypted streams after the key exchange
#
- pcap-log:
enabled: no
filename: log.pcap # File size limit. Can be specified in kb, mb, gb. Just a number
# is parsed as bytes.
limit: 1000mb # If set to a value will enable ring buffer mode. Will keep Maximum of "max-files" of size "limit"
max-files: mode: normal # normal or sguil.
#sguil-base-dir: /nsm_data/
#ts-format: usec # sec or usec second format (default) is filename.sec usec is filename.sec.usec
use-stream-depth: no #If set to "yes" packets seen after reaching stream inspection depth are ignored. "no" logs all packets # a full alerts log containing much information for signature writers
# or for investigating suspected false positives.
- alert-debug:
enabled: no
filename: alert-debug.log
append: yes
#filetype: regular # 'regular', 'unix_stream' or 'unix_dgram' # alert output to prelude (http://www.prelude-technologies.com/) only
# available if Suricata has been compiled with --enable-prelude
- alert-prelude:
enabled: no
profile: suricata
log-packet-content: no
log-packet-header: yes # Stats.log contains data from various counters of the suricata engine.
# The interval field (in seconds) tells after how long output will be written
# on the log file.
- stats:
enabled: yes
filename: stats.log
interval: # a line based alerts log similar to fast.log into syslog
- syslog:
enabled: yes
# reported identity to syslog. If ommited the program name (usually
# suricata) will be used.
#identity: "suricata"
facility: local5
#level: Info ## possible levels: Emergency, Alert, Critical,
## Error, Warning, Notice, Info, Debug # a line based information for dropped packets in IPS mode
- drop:
enabled: no
filename: drop.log
append: yes
#filetype: regular # 'regular', 'unix_stream' or 'unix_dgram' # output module to store extracted files to disk
#
# The files are stored to the log-dir in a format "file.<id>" where <id> is
# an incrementing number starting at . For each file "file.<id>" a meta
# file "file.<id>.meta" is created.
#
# File extraction depends on a lot of things to be fully done:
# - stream reassembly depth. For optimal results, set this to (unlimited)
# - http request / response body sizes. Again set to for optimal results.
# - rules that contain the "filestore" keyword.
- file-store:
enabled: no # set to yes to enable
log-dir: files # directory to store the files
force-magic: no # force logging magic on all stored files
force-md5: no # force logging of md5 checksums
#waldo: file.waldo # waldo file to store the file_id across runs # output module to log files tracked in a easily parsable json format
- file-log:
enabled: no
filename: files-json.log
append: yes
#filetype: regular # 'regular', 'unix_stream' or 'unix_dgram' force-magic: no # force logging magic on all logged files
force-md5: no # force logging of md5 checksums # Magic file. The extension .mgc is added to the value here.
#magic-file: /usr/share/file/magic
magic-file: /usr/share/file/magic # When running in NFQ inline mode, it is possible to use a simulated
# non-terminal NFQUEUE verdict.
# This permit to do send all needed packet to suricata via this a rule:
# iptables -I FORWARD -m mark ! --mark $MARK/$MASK -j NFQUEUE
# And below, you can have your standard filtering ruleset. To activate
# this mode, you need to set mode to 'repeat'
# If you want packet to be sent to another queue after an ACCEPT decision
# set mode to 'route' and set next-queue value.
# On linux >= 3.6, you can set the fail-open option to yes to have the kernel
# accept the packet if suricata is not able to keep pace.
nfq:
# mode: accept
# repeat-mark:
# repeat-mask:
# route-queue:
# fail-open: yes # af-packet support
# Set threads to > to use PACKET_FANOUT support
af-packet:
- interface: eth0
# Number of receive threads (> will enable experimental flow pinned
# runmode)
threads:
# Default clusterid. AF_PACKET will load balance packets based on flow.
# All threads/processes that will participate need to have the same
# clusterid.
cluster-id:
# Default AF_PACKET cluster type. AF_PACKET can load balance per flow or per hash.
# This is only supported for Linux kernel > 3.1
# possible value are:
# * cluster_round_robin: round robin load balancing
# * cluster_flow: all packets of a given flow are send to the same socket
# * cluster_cpu: all packets treated in kernel by a CPU are send to the same socket
cluster-type: cluster_flow
# In some fragmentation case, the hash can not be computed. If "defrag" is set
# to yes, the kernel will do the needed defragmentation before sending the packets.
defrag: yes
# To use the ring feature of AF_PACKET, set 'use-mmap' to yes
use-mmap: yes
# Ring size will be computed with respect to max_pending_packets and number
# of threads. You can set manually the ring size in number of packets by setting
# the following value. If you are using flow cluster-type and have really network
# intensive single-flow you could want to set the ring-size independantly of the number
# of threads:
#ring-size:
# On busy system, this could help to set it to yes to recover from a packet drop
# phase. This will result in some packets (at max a ring flush) being non treated.
#use-emergency-flush: yes
# recv buffer size, increase value could improve performance
# buffer-size:
# Set to yes to disable promiscuous mode
# disable-promisc: no
# Choose checksum verification mode for the interface. At the moment
# of the capture, some packets may be with an invalid checksum due to
# offloading to the network card of the checksum computation.
# Possible values are:
# - kernel: use indication sent by kernel for each packet (default)
# - yes: checksum validation is forced
# - no: checksum validation is disabled
# - auto: suricata uses a statistical approach to detect when
# checksum off-loading is used.
# Warning: 'checksum-validation' must be set to yes to have any validation
#checksum-checks: kernel
# BPF filter to apply to this interface. The pcap filter syntax apply here.
#bpf-filter: port or udp
# You can use the following variables to activate AF_PACKET tap od IPS mode.
# If copy-mode is set to ips or tap, the traffic coming to the current
# interface will be copied to the copy-iface interface. If 'tap' is set, the
# copy is complete. If 'ips' is set, the packet matching a 'drop' action
# will not be copied.
#copy-mode: ips
#copy-iface: eth1
- interface: eth1
threads:
cluster-id:
cluster-type: cluster_flow
defrag: yes
# buffer-size:
# disable-promisc: no # You can specify a threshold config file by setting "threshold-file"
# to the path of the threshold config file:
# threshold-file: /etc/suricata/threshold.config # The detection engine builds internal groups of signatures. The engine
# allow us to specify the profile to use for them, to manage memory on an
# efficient way keeping a good performance. For the profile keyword you
# can use the words "low", "medium", "high" or "custom". If you use custom
# make sure to define the values at "- custom-values" as your convenience.
# Usually you would prefer medium/high/low.
#
# "sgh mpm-context", indicates how the staging should allot mpm contexts for
# the signature groups. "single" indicates the use of a single context for
# all the signature group heads. "full" indicates a mpm-context for each
# group head. "auto" lets the engine decide the distribution of contexts
# based on the information the engine gathers on the patterns from each
# group head.
#
# The option inspection-recursion-limit is used to limit the recursive calls
# in the content inspection code. For certain payload-sig combinations, we
# might end up taking too much time in the content inspection code.
# If the argument specified is , the engine uses an internally defined
# default limit. On not specifying a value, we use no limits on the recursion.
detect-engine:
- profile: medium
- custom-values:
toclient-src-groups:
toclient-dst-groups:
toclient-sp-groups:
toclient-dp-groups:
toserver-src-groups:
toserver-dst-groups:
toserver-sp-groups:
toserver-dp-groups:
- sgh-mpm-context: auto
- inspection-recursion-limit:
# When rule-reload is enabled, sending a USR2 signal to the Suricata process
# will trigger a live rule reload. Experimental feature, use with care.
#- rule-reload: true
# If set to yes, the loading of signatures will be made after the capture
# is started. This will limit the downtime in IPS mode.
#- delayed-detect: yes # Suricata is multi-threaded. Here the threading can be influenced.
threading:
# On some cpu's/architectures it is beneficial to tie individual threads
# to specific CPU's/CPU cores. In this case all threads are tied to CPU0,
# and each extra CPU/core has one "detect" thread.
#
# On Intel Core2 and Nehalem CPU's enabling this will degrade performance.
#
set-cpu-affinity: no
# Tune cpu affinity of suricata threads. Each family of threads can be bound
# on specific CPUs.
cpu-affinity:
- management-cpu-set:
cpu: [ ] # include only these cpus in affinity settings
- receive-cpu-set:
cpu: [ ] # include only these cpus in affinity settings
- decode-cpu-set:
cpu: [ , ]
mode: "balanced"
- stream-cpu-set:
cpu: [ "0-1" ]
- detect-cpu-set:
cpu: [ "all" ]
mode: "exclusive" # run detect threads in these cpus
# Use explicitely threads and don't compute number by using
# detect-thread-ratio variable:
# threads:
prio:
low: [ ]
medium: [ "1-2" ]
high: [ ]
default: "medium"
- verdict-cpu-set:
cpu: [ ]
prio:
default: "high"
- reject-cpu-set:
cpu: [ ]
prio:
default: "low"
- output-cpu-set:
cpu: [ "all" ]
prio:
default: "medium"
#
# By default Suricata creates one "detect" thread per available CPU/CPU core.
# This setting allows controlling this behaviour. A ratio setting of will
# create detect threads for each CPU/CPU core. So for a dual core CPU this
# will result in detect threads. If values below are used, less threads
# are created. So on a dual core CPU a setting of 0.5 results in detect
# thread being created. Regardless of the setting at a minimum detect
# thread will always be created.
#
detect-thread-ratio: 1.5 # Cuda configuration.
cuda:
# The "mpm" profile. On not specifying any of these parameters, the engine's
# internal default values are used, which are same as the ones specified here.
- mpm:
# Threshold limit for no of packets buffered to the GPU. Once we hit this
# limit, we pass the buffer to the gpu.
packet-buffer-limit:
# The maximum length for a packet that we would buffer to the gpu.
# Anything over this is MPM'ed on the CPU. All entries > 0 are valid.
# Can be specified in kb, mb, gb. Just a number indicates it's in bytes.
packet-size-limit:
# No of packet buffers we initialize. All entries > are valid.
packet-buffers:
# The timeout limit for batching of packets in secs. If we don't fill the
# buffer within this timeout limit, we pass the currently filled buffer to the gpu.
# All entries > are valid.
batching-timeout:
# Specifies whether to use page-locked memory whereever possible. Accepted values
# are "enabled" and "disabled".
page-locked: enabled
# The device to use for the mpm. Currently we don't support load balancing
# on multiple gpus. In case you have multiple devices on your system, you
# can specify the device to use, using this conf. By default we hold , to
# specify the first device cuda sees. To find out device-id associated with
# the card(s) on the system run "suricata --list-cuda-cards".
device-id:
# No of Cuda streams used for asynchronous processing. All values > are valid.
# For this option you need a device with Compute Capability > 1.0 and
# page-locked enabled to have any effect.
cuda-streams: # Select the multi pattern algorithm you want to run for scan/search the
# in the engine. The supported algorithms are b2g, b2gc, b2gm, b3g, wumanber,
# ac and ac-gfbs.
#
# The mpm you choose also decides the distribution of mpm contexts for
# signature groups, specified by the conf - "detect-engine.sgh-mpm-context".
# Selecting "ac" as the mpm would require "detect-engine.sgh-mpm-context"
# to be set to "single", because of ac's memory requirements, unless the
# ruleset is small enough to fit in one's memory, in which case one can
# use "full" with "ac". Rest of the mpms can be run in "full" mode.
#
# There is also a CUDA pattern matcher (only available if Suricata was
# compiled with --enable-cuda: b2g_cuda. Make sure to update your
# max-pending-packets setting above as well if you use b2g_cuda. mpm-algo: ac # The memory settings for hash size of these algorithms can vary from lowest
# () - low () - medium () - high () - higher () - max
# (). The bloomfilter sizes of these algorithms can vary from low () -
# medium () - high ().
#
# For B2g/B3g algorithms, there is a support for two different scan/search
# algorithms. For B2g the scan algorithms are B2gScan & B2gScanBNDMq, and
# search algorithms are B2gSearch & B2gSearchBNDMq. For B3g scan algorithms
# are B3gScan & B3gScanBNDMq, and search algorithms are B3gSearch &
# B3gSearchBNDMq.
#
# For B2g the different scan/search algorithms and, hash and bloom
# filter size settings. For B3g the different scan/search algorithms and, hash
# and bloom filter size settings. For wumanber the hash and bloom filter size
# settings. pattern-matcher:
- b2gc:
search-algo: B2gSearchBNDMq
hash-size: low
bf-size: medium
- b2gm:
search-algo: B2gSearchBNDMq
hash-size: low
bf-size: medium
- b2g:
search-algo: B2gSearchBNDMq
hash-size: low
bf-size: medium
- b3g:
search-algo: B3gSearchBNDMq
hash-size: low
bf-size: medium
- wumanber:
hash-size: low
bf-size: medium # Defrag settings: defrag:
trackers: # number of defragmented flows to follow
max-frags: # number of fragments to keep (higher than trackers)
prealloc: yes
timeout: # Flow settings:
# By default, the reserved memory (memcap) for flows is 32MB. This is the limit
# for flow allocation inside the engine. You can change this value to allow
# more memory usage for flows.
# The hash-size determine the size of the hash used to identify flows inside
# the engine, and by default the value is .
# At the startup, the engine can preallocate a number of flows, to get a better
# performance. The number of flows preallocated is by default.
# emergency-recovery is the percentage of flows that the engine need to
# prune before unsetting the emergency state. The emergency state is activated
# when the memcap limit is reached, allowing to create new flows, but
# prunning them with the emergency timeouts (they are defined below).
# If the memcap is reached, the engine will try to prune flows
# with the default timeouts. If it doens't find a flow to prune, it will set
# the emergency bit and it will try again with more agressive timeouts.
# If that doesn't work, then it will try to kill the last time seen flows
# not in use.
# The memcap can be specified in kb, mb, gb. Just a number indicates it's
# in bytes. flow:
memcap: 32mb
hash-size:
prealloc:
emergency-recovery: # Specific timeouts for flows. Here you can specify the timeouts that the
# active flows will wait to transit from the current state to another, on each
# protocol. The value of "new" determine the seconds to wait after a hanshake or
# stream startup before the engine free the data of that flow it doesn't
# change the state to established (usually if we don't receive more packets
# of that flow). The value of "established" is the amount of
# seconds that the engine will wait to free the flow if it spend that amount
# without receiving new packets or closing the connection. "closed" is the
# amount of time to wait after a flow is closed (usually zero).
#
# There's an emergency mode that will become active under attack circumstances,
# making the engine to check flow status faster. This configuration variables
# use the prefix "emergency-" and work similar as the normal ones.
# Some timeouts doesn't apply to all the protocols, like "closed", for udp and
# icmp. flow-timeouts: default:
new:
established:
closed:
emergency-new:
emergency-established:
emergency-closed:
tcp:
new:
established:
closed:
emergency-new:
emergency-established:
emergency-closed:
udp:
new:
established:
emergency-new:
emergency-established:
icmp:
new:
established:
emergency-new:
emergency-established: # Stream engine settings. Here the TCP stream tracking and reaasembly
# engine is configured.
#
# stream:
# memcap: 32mb # Can be specified in kb, mb, gb. Just a
# # number indicates it's in bytes.
# checksum-validation: yes # To validate the checksum of received
# # packet. If csum validation is specified as
# # "yes", then packet with invalid csum will not
# # be processed by the engine stream/app layer.
# # Warning: locally generated trafic can be
# # generated without checksum due to hardware offload
# # of checksum. You can control the handling of checksum
# # on a per-interface basis via the 'checksum-checks'
# # option
# max-sessions: # 256k concurrent sessions
# prealloc-sessions: # 32k sessions prealloc'd
# midstream: false # don't allow midstream session pickups
# async-oneside: false # don't enable async stream handling
# inline: no # stream inline mode
#
# reassembly:
# memcap: 64mb # Can be specified in kb, mb, gb. Just a number
# # indicates it's in bytes.
# depth: 1mb # Can be specified in kb, mb, gb. Just a number
# # indicates it's in bytes.
# toserver-chunk-size: # inspect raw stream in chunks of at least
# # this size. Can be specified in kb, mb,
# # gb. Just a number indicates it's in bytes.
# toclient-chunk-size: # inspect raw stream in chunks of at least
# # this size. Can be specified in kb, mb,
# # gb. Just a number indicates it's in bytes. stream:
memcap: 32mb
checksum-validation: yes # reject wrong csums
inline: no # no inline mode
reassembly:
memcap: 64mb
depth: 1mb # reassemble 1mb into a stream
toserver-chunk-size:
toclient-chunk-size: # Host table:
#
# Host table is used by tagging and per host thresholding subsystems.
#
host:
hash-size:
prealloc:
memcap: # Logging configuration. This is not about logging IDS alerts, but
# IDS output about what its doing, errors, etc.
logging: # The default log level, can be overridden in an output section.
# Note that debug level logging will only be emitted if Suricata was
# compiled with the --enable-debug configure option.
#
# This value is overriden by the SC_LOG_LEVEL env var.
default-log-level: info # The default output format. Optional parameter, should default to
# something reasonable if not provided. Can be overriden in an
# output section. You can leave this out to get the default.
#
# This value is overriden by the SC_LOG_FORMAT env var.
#default-log-format: "[%i] %t - (%f:%l) <%d> (%n) -- " # A regex to filter output. Can be overridden in an output section.
# Defaults to empty (no filter).
#
# This value is overriden by the SC_LOG_OP_FILTER env var.
default-output-filter: # Define your logging outputs. If none are defined, or they are all
# disabled you will get the default - console output.
outputs:
- console:
enabled: yes
- file:
enabled: yes
filename: /var/log/suricata.log
- syslog:
enabled: yes
facility: local5
format: "[%i] <%d> -- " # PF_RING configuration. for use with native PF_RING support
# for more info see http://www.ntop.org/PF_RING.html
pfring:
- interface: eth0
# Number of receive threads (> will enable experimental flow pinned
# runmode)
threads: # Default clusterid. PF_RING will load balance packets based on flow.
# All threads/processes that will participate need to have the same
# clusterid.
cluster-id: # Default PF_RING cluster type. PF_RING can load balance per flow or per hash.
# This is only supported in versions of PF_RING > 4.1..
cluster-type: cluster_round_robin
# bpf filter for this interface
#bpf-filter: tcp
# Choose checksum verification mode for the interface. At the moment
# of the capture, some packets may be with an invalid checksum due to
# offloading to the network card of the checksum computation.
# Possible values are:
# - rxonly: only compute checksum for packets received by network card.
# - yes: checksum validation is forced
# - no: checksum validation is disabled
# - auto: suricata uses a statistical approach to detect when
# checksum off-loading is used. (default)
# Warning: 'checksum-validation' must be set to yes to have any validation
#checksum-checks: auto
# Second interface
#- interface: eth1
# threads:
# cluster-id:
# cluster-type: cluster_flow pcap:
- interface: eth0
#buffer-size:
#bpf-filter: "tcp and port 25"
# Choose checksum verification mode for the interface. At the moment
# of the capture, some packets may be with an invalid checksum due to
# offloading to the network card of the checksum computation.
# Possible values are:
# - yes: checksum validation is forced
# - no: checksum validation is disabled
# - auto: suricata uses a statistical approach to detect when
# checksum off-loading is used. (default)
# Warning: 'checksum-validation' must be set to yes to have any validation
#checksum-checks: auto # For FreeBSD ipfw() divert() support.
# Please make sure you have ipfw_load="YES" and ipdivert_load="YES"
# in /etc/loader.conf or kldload'ing the appropriate kernel modules.
# Additionally, you need to have an ipfw rule for the engine to see
# the packets from ipfw. For Example:
#
# ipfw add divert ip from any to any
#
# The above should be the same number you passed on the command
# line, i.e. -d
#
ipfw: # Reinject packets at the specified ipfw rule number. This config
# option is the ipfw rule number AT WHICH rule processing continues
# in the ipfw processing system after the engine has finished
# inspecting the packet for acceptance. If no rule number is specified,
# accepted packets are reinjected at the divert rule which they entered
# and IPFW rule processing continues. No check is done to verify
# this will rule makes sense so care must be taken to avoid loops in ipfw.
#
## The following example tells the engine to reinject packets
# back into the ipfw firewall AT rule number :
#
# ipfw-reinjection-rule-number: # Set the default rule path here to search for the files.
# if not set, it will look at the current working dir
default-rule-path: /etc/suricata/rules/
rule-files: #Malware/trojan oriented rules
- etpro-trojan.rules
- etpro-malware.rules
- etpro-mobile_malware.rules
- etpro-worm.rules
- etpro-user_agents.rules
- etpro-current_events.rules #important but relatively low load rules you'll likely want to keep on
- etpro-ftp.rules
- etpro-pop3.rules
- etpro-rpc.rules
- etpro-attack_response.rules
# - etpro-icmp.rules
- etpro-scan.rules
- etpro-voip.rules
- etpro-imap.rules
- etpro-web_server.rules
- etpro-smtp.rules
- etpro-dns.rules
- etpro-misc.rules
- etpro-snmp.rules
- etpro-sql.rules
- etpro-dos.rules
- etpro-telnet.rules
- etpro-exploit.rules
- etpro-tftp.rules #useful but often high load rules. Look here for performance tuning
- etpro-web_client.rules
- etpro-netbios.rules #things you'll want to look through and consider policy needs
- etpro-policy.rules
# - etpro-games.rules
- etpro-p2p.rules
- etpro-chat.rules #informational, not recommended for high speed nets
# - etpro-icmp_info.rules
# - etpro-info.rules
# - etpro-shellcode.rules
# - etpro-inappropriate.rules
# - etpro-web_specific_apps.rules
# - etpro-activex.rules #ip based rules
- botcc.rules
- ciarmy.rules
- compromised.rules
- drop.rules
- dshield.rules
- tor.rules #only use the scada_special if you have the scada extensions compiled int
# - etpro-scada_special.rules
# - etpro-scada.rules classification-file: /etc/suricata/classification.config
reference-config-file: /etc/suricata/reference.config # Holds variables that would be used by the engine.
vars: # Holds the address group vars that would be passed in a Signature.
# These would be retrieved during the Signature address parsing stage.
address-groups: HOME_NET: "[192.168.0.0/16,10.0.0.0/8,172.16.0.0/12]" EXTERNAL_NET: "any" HTTP_SERVERS: "$HOME_NET" SMTP_SERVERS: "$HOME_NET" SQL_SERVERS: "$HOME_NET" DNS_SERVERS: "$HOME_NET" TELNET_SERVERS: "$HOME_NET" AIM_SERVERS: "$EXTERNAL_NET" DNP3_SERVER: "$HOME_NET" DNP3_CLIENT: "$HOME_NET" MODBUS_CLIENT: "$HOME_NET" MODBUS_SERVER: "$HOME_NET" ENIP_CLIENT: "$HOME_NET" ENIP_SERVER: "$HOME_NET" # Holds the port group vars that would be passed in a Signature.
# These would be retrieved during the Signature port parsing stage.
port-groups: HTTP_PORTS: "[80,81,311,591,593,901,1220,1414,1830,2301,2381,2809,3128,3702,4343,5250,7001,7145,7510,7777,7779,8000,8008,8014,8028,8080,8088,8118,8123,8180,8181,8243,8280,8800,8888,8899,9080,9090,9091,9443,9999,11371,55555]" SHELLCODE_PORTS: "!80" ORACLE_PORTS: SSH_PORTS: DNP3_PORTS: # Set the order of alerts bassed on actions
# The default order is pass, drop, reject, alert
action-order:
- pass
- drop
- reject
- alert # Host specific policies for defragmentation and TCP stream
# reassembly. The host OS lookup is done using a radix tree, just
# like a routing table so the most specific entry matches.
host-os-policy:
# Make the default policy windows.
windows: [0.0.0.0/]
bsd: []
bsd-right: []
old-linux: []
linux: []
old-solaris: []
solaris: []
hpux10: []
hpux11: []
irix: []
macos: []
vista: []
windows2k3: [] # Limit for the maximum number of asn1 frames to decode (default )
asn1-max-frames: # When run with the option --engine-analysis, the engine will read each of
# the parameters below, and print reports for each of the enabled sections
# and exit. The reports are printed to a file in the default log dir
# given by the parameter "default-log-dir", with engine reporting
# subsection below printing reports in its own report file.
engine-analysis:
# enables printing reports for fast-pattern for every rule.
rules-fast-pattern: yes
# enables printing reports for each rule
rules: yes #recursion and match limits for PCRE where supported
pcre:
match-limit:
match-limit-recursion: ###########################################################################
# Configure libhtp.
#
#
# default-config: Used when no server-config matches
# personality: List of personalities used by default
# request-body-limit: Limit reassembly of request body for inspection
# by http_client_body & pcre /P option.
# response-body-limit: Limit reassembly of response body for inspection
# by file_data, http_server_body & pcre /Q option.
# double-decode-path: Double decode path section of the URI
# double-decode-query: Double decode query section of the URI
#
# server-config: List of server configurations to use if address matches
# address: List of ip addresses or networks for this block
# personalitiy: List of personalities used by this block
# request-body-limit: Limit reassembly of request body for inspection
# by http_client_body & pcre /P option.
# response-body-limit: Limit reassembly of response body for inspection
# by file_data, http_server_body & pcre /Q option.
# double-decode-path: Double decode path section of the URI
# double-decode-query: Double decode query section of the URI
#
# Currently Available Personalities:
# Minimal
# Generic
# IDS (default)
# IIS_4_0
# IIS_5_0
# IIS_5_1
# IIS_6_0
# IIS_7_0
# IIS_7_5
# Apache
# Apache_2_2
###########################################################################
libhtp: default-config:
personality: IDS
# Can be specified in kb, mb, gb. Just a number indicates
# it's in bytes.
request-body-limit:
response-body-limit:
double-decode-path: no
double-decode-query: no ##### Set proper personality for your net #######
# server-config:
# - apache:
# address: [192.168.1.0/, 127.0.0.0/, "::1"]
# personality: Apache_2_2
# # Can be specified in kb, mb, gb. Just a number indicates
# # it's in bytes.
# request-body-limit:
# response-body-limit:
# double-decode-path: no
# double-decode-query: no
#
# - iis7:
# address:
# - 192.168.0.0/
# - 192.168.10.0/
# personality: IIS_7_0
# # Can be specified in kb, mb, gb. Just a number indicates
# # it's in bytes.
# request-body-limit:
# response-body-limit:
# double-decode-path: no
# double-decode-query: no # Profiling settings. Only effective if Suricata has been built with the
# the --enable-profiling configure flag.
#
profiling: # rule profiling
rules: # Profiling can be disabled here, but it will still have a
# performance impact if compiled in.
enabled: yes
filename: rule_perf.log
append: yes # Sort options: ticks, avgticks, checks, matches, maxticks
sort: avgticks # Limit the number of items printed at exit.
#limit: # packet profiling
packets: # Profiling can be disabled here, but it will still have a
# performance impact if compiled in.
enabled: yes
filename: packet_stats.log
append: yes # per packet csv output
csv: # Output can be disabled here, but it will still have a
# performance impact if compiled in.
enabled: no
filename: packet_stats.csv # profiling of locking. Only available when Suricata was built with
# --enable-profiling-locks.
locks:
enabled: no
filename: lock_stats.log
append: yes # Suricata core dump configuration. Limits the size of the core dump file to
# approximately max-dump. The actual core dump size will be a multiple of the
# page size. Core dumps that would be larger than max-dump are truncated. On
# Linux, the actual core dump size may be a few pages larger than max-dump.
# Setting max-dump to disables core dumping.
# Setting max-dump to 'unlimited' will give the full core dump file.
# On -bit Linux, a max-dump value >= ULONG_MAX may cause the core dump size
# to be 'unlimited'. coredump:
max-dump: unlimited
23、SELKS里的suricata的suricata-1.3-open.txt(非常重要)
这里面,默认是为空的。
24、SELKS里的suricata的suricata-1.3-open.yaml(非常重要)

%YAML 1.1
--- # Suricata configuration file. In addition to the comments describing all
# options in this file, full documentation can be found at:
# https://redmine.openinfosecfoundation.org/projects/suricata/wiki/Suricatayaml # NOTE: This version of the Suricata.yaml file is modified by the Emerging Threats
# Pro Team to reflect the default assumptions on inspection depths. Comments have been
# added to note where users may tune defaults back where performance is a
# concern. The default stance of this config is maximum detection.
# Decisions on features such as file extraction and pcap logging must be made
# locally. These are left at defaults. # Number of packets allowed to be processed simultaneously. Default is a
# conservative . A higher number will make sure CPU's/CPU cores will be
# more easily kept busy, but may negatively impact caching.
#
# If you are using the CUDA pattern matcher (b2g_cuda below), different rules
# apply. In that case try something like or more. This is because the CUDA
# pattern matcher scans many packets in parallel.
max-pending-packets: # Runmode the engine should use. Please check --list-runmodes to get the available
# runmodes for each packet acquisition method. Defaults to "autofp" (auto flow pinned
# load balancing).
#runmode: autofp # Specifies the kind of flow load balancer used by the flow pinned autofp mode.
#
# Supported schedulers are:
#
# round-robin - Flows assigned to threads in a round robin fashion.
# active-packets - Flows assigned to threads that have the lowest number of
# unprocessed packets (default).
# hash - Flow alloted usihng the address hash. More of a random
# technique. Was the default in Suricata 1.2. and older.
#
#autofp-scheduler: active-packets # Default pid file.
# Will use this file if no --pidfile in command options.
#pid-file: /var/run/suricata.pid # Preallocated size for packet. Default is which is the classical
# size for pcap on ethernet. You should adjust this value to the highest
# packet size (MTU + hardware header) on your system.
#default-packet-size: # The default logging directory. Any log or output file will be
# placed here if its not specified with a full path name. This can be
# overridden with the -l command line parameter.
default-log-dir: /var/log/suricata/ # Unix command socket can be used to pass commands to suricata.
# An external tool can then connect to get information from suricata
# or trigger some modification of the engine.
#unix-command: yes # Configure the type of alert (and other) logging you would like.
outputs: # a line based alerts log similar to Snort's fast.log
- fast:
enabled: yes
filename: fast.log
append: yes
#filetype: regular # 'regular', 'unix_stream' or 'unix_dgram' # alert output for use with Barnyard2
- unified2-alert:
enabled: yes
filename: unified2.alert # File size limit. Can be specified in kb, mb, gb. Just a number
# is parsed as bytes.
#limit: 32mb # a line based log of HTTP requests (no alerts)
- http-log:
enabled: yes
filename: http.log
append: yes
#extended: yes # enable this for extended logging information
#custom: yes # enabled the custom logging format (defined by customformat)
#customformat: "%{%D-%H:%M:%S}t.%z %{X-Forwarded-For}i %H %m %h %u %s %B %a:%p -> %A:%P"
#filetype: regular # 'regular', 'unix_stream' or 'unix_dgram' # a line based log of TLS handshake parameters (no alerts)
- tls-log:
enabled: yes # Log TLS connections.
filename: tls.log # File to store TLS logs.
extended: yes # Log extended information like fingerprint
certs-log-dir: certs # directory to store the certificates files # a line based log to used with pcap file study.
# this module is dedicated to offline pcap parsing (empty output
# if used with another kind of input). It can interoperate with
# pcap parser like wireshark via the suriwire plugin.
- pcap-info:
enabled: no # Packet log... log packets in pcap format. modes of operation: "normal"
# and "sguil".
#
# In normal mode a pcap file "filename" is created in the default-log-dir,
# or are as specified by "dir". In Sguil mode "dir" indicates the base directory.
# In this base dir the pcaps are created in th directory structure Sguil expects:
#
# $sguil-base-dir/YYYY-MM-DD/$filename.<timestamp>
#
# By default all packets are logged except:
# - TCP streams beyond stream.reassembly.depth
# - encrypted streams after the key exchange
#
- pcap-log:
enabled: no
filename: log.pcap # File size limit. Can be specified in kb, mb, gb. Just a number
# is parsed as bytes.
limit: 1000mb # If set to a value will enable ring buffer mode. Will keep Maximum of "max-files" of size "limit"
max-files: mode: normal # normal or sguil.
#sguil-base-dir: /nsm_data/
#ts-format: usec # sec or usec second format (default) is filename.sec usec is filename.sec.usec
use-stream-depth: no #If set to "yes" packets seen after reaching stream inspection depth are ignored. "no" logs all packets # a full alerts log containing much information for signature writers
# or for investigating suspected false positives.
- alert-debug:
enabled: no
filename: alert-debug.log
append: yes
#filetype: regular # 'regular', 'unix_stream' or 'unix_dgram' # alert output to prelude (http://www.prelude-technologies.com/) only
# available if Suricata has been compiled with --enable-prelude
- alert-prelude:
enabled: no
profile: suricata
log-packet-content: no
log-packet-header: yes # Stats.log contains data from various counters of the suricata engine.
# The interval field (in seconds) tells after how long output will be written
# on the log file.
- stats:
enabled: yes
filename: stats.log
interval: # a line based alerts log similar to fast.log into syslog
- syslog:
enabled: yes
# reported identity to syslog. If ommited the program name (usually
# suricata) will be used.
#identity: "suricata"
facility: local5
#level: Info ## possible levels: Emergency, Alert, Critical,
## Error, Warning, Notice, Info, Debug # a line based information for dropped packets in IPS mode
- drop:
enabled: no
filename: drop.log
append: yes
#filetype: regular # 'regular', 'unix_stream' or 'unix_dgram' # output module to store extracted files to disk
#
# The files are stored to the log-dir in a format "file.<id>" where <id> is
# an incrementing number starting at . For each file "file.<id>" a meta
# file "file.<id>.meta" is created.
#
# File extraction depends on a lot of things to be fully done:
# - stream reassembly depth. For optimal results, set this to (unlimited)
# - http request / response body sizes. Again set to for optimal results.
# - rules that contain the "filestore" keyword.
- file-store:
enabled: no # set to yes to enable
log-dir: files # directory to store the files
force-magic: no # force logging magic on all stored files
force-md5: no # force logging of md5 checksums
#waldo: file.waldo # waldo file to store the file_id across runs # output module to log files tracked in a easily parsable json format
- file-log:
enabled: no
filename: files-json.log
append: yes
#filetype: regular # 'regular', 'unix_stream' or 'unix_dgram' force-magic: no # force logging magic on all logged files
force-md5: no # force logging of md5 checksums # Magic file. The extension .mgc is added to the value here.
#magic-file: /usr/share/file/magic
magic-file: /usr/share/file/magic # When running in NFQ inline mode, it is possible to use a simulated
# non-terminal NFQUEUE verdict.
# This permit to do send all needed packet to suricata via this a rule:
# iptables -I FORWARD -m mark ! --mark $MARK/$MASK -j NFQUEUE
# And below, you can have your standard filtering ruleset. To activate
# this mode, you need to set mode to 'repeat'
# If you want packet to be sent to another queue after an ACCEPT decision
# set mode to 'route' and set next-queue value.
# On linux >= 3.6, you can set the fail-open option to yes to have the kernel
# accept the packet if suricata is not able to keep pace.
nfq:
# mode: accept
# repeat-mark:
# repeat-mask:
# route-queue:
# fail-open: yes # af-packet support
# Set threads to > to use PACKET_FANOUT support
af-packet:
- interface: eth0
# Number of receive threads (> will enable experimental flow pinned
# runmode)
threads:
# Default clusterid. AF_PACKET will load balance packets based on flow.
# All threads/processes that will participate need to have the same
# clusterid.
cluster-id:
# Default AF_PACKET cluster type. AF_PACKET can load balance per flow or per hash.
# This is only supported for Linux kernel > 3.1
# possible value are:
# * cluster_round_robin: round robin load balancing
# * cluster_flow: all packets of a given flow are send to the same socket
# * cluster_cpu: all packets treated in kernel by a CPU are send to the same socket
cluster-type: cluster_flow
# In some fragmentation case, the hash can not be computed. If "defrag" is set
# to yes, the kernel will do the needed defragmentation before sending the packets.
defrag: yes
# To use the ring feature of AF_PACKET, set 'use-mmap' to yes
use-mmap: yes
# Ring size will be computed with respect to max_pending_packets and number
# of threads. You can set manually the ring size in number of packets by setting
# the following value. If you are using flow cluster-type and have really network
# intensive single-flow you could want to set the ring-size independantly of the number
# of threads:
#ring-size:
# On busy system, this could help to set it to yes to recover from a packet drop
# phase. This will result in some packets (at max a ring flush) being non treated.
#use-emergency-flush: yes
# recv buffer size, increase value could improve performance
# buffer-size:
# Set to yes to disable promiscuous mode
# disable-promisc: no
# Choose checksum verification mode for the interface. At the moment
# of the capture, some packets may be with an invalid checksum due to
# offloading to the network card of the checksum computation.
# Possible values are:
# - kernel: use indication sent by kernel for each packet (default)
# - yes: checksum validation is forced
# - no: checksum validation is disabled
# - auto: suricata uses a statistical approach to detect when
# checksum off-loading is used.
# Warning: 'checksum-validation' must be set to yes to have any validation
#checksum-checks: kernel
# BPF filter to apply to this interface. The pcap filter syntax apply here.
#bpf-filter: port or udp
# You can use the following variables to activate AF_PACKET tap od IPS mode.
# If copy-mode is set to ips or tap, the traffic coming to the current
# interface will be copied to the copy-iface interface. If 'tap' is set, the
# copy is complete. If 'ips' is set, the packet matching a 'drop' action
# will not be copied.
#copy-mode: ips
#copy-iface: eth1
- interface: eth1
threads:
cluster-id:
cluster-type: cluster_flow
defrag: yes
# buffer-size:
# disable-promisc: no # You can specify a threshold config file by setting "threshold-file"
# to the path of the threshold config file:
# threshold-file: /etc/suricata/threshold.config # The detection engine builds internal groups of signatures. The engine
# allow us to specify the profile to use for them, to manage memory on an
# efficient way keeping a good performance. For the profile keyword you
# can use the words "low", "medium", "high" or "custom". If you use custom
# make sure to define the values at "- custom-values" as your convenience.
# Usually you would prefer medium/high/low.
#
# "sgh mpm-context", indicates how the staging should allot mpm contexts for
# the signature groups. "single" indicates the use of a single context for
# all the signature group heads. "full" indicates a mpm-context for each
# group head. "auto" lets the engine decide the distribution of contexts
# based on the information the engine gathers on the patterns from each
# group head.
#
# The option inspection-recursion-limit is used to limit the recursive calls
# in the content inspection code. For certain payload-sig combinations, we
# might end up taking too much time in the content inspection code.
# If the argument specified is , the engine uses an internally defined
# default limit. On not specifying a value, we use no limits on the recursion.
detect-engine:
- profile: medium
- custom-values:
toclient-src-groups:
toclient-dst-groups:
toclient-sp-groups:
toclient-dp-groups:
toserver-src-groups:
toserver-dst-groups:
toserver-sp-groups:
toserver-dp-groups:
- sgh-mpm-context: auto
- inspection-recursion-limit:
# When rule-reload is enabled, sending a USR2 signal to the Suricata process
# will trigger a live rule reload. Experimental feature, use with care.
#- rule-reload: true
# If set to yes, the loading of signatures will be made after the capture
# is started. This will limit the downtime in IPS mode.
#- delayed-detect: yes # Suricata is multi-threaded. Here the threading can be influenced.
threading:
# On some cpu's/architectures it is beneficial to tie individual threads
# to specific CPU's/CPU cores. In this case all threads are tied to CPU0,
# and each extra CPU/core has one "detect" thread.
#
# On Intel Core2 and Nehalem CPU's enabling this will degrade performance.
#
set-cpu-affinity: no
# Tune cpu affinity of suricata threads. Each family of threads can be bound
# on specific CPUs.
cpu-affinity:
- management-cpu-set:
cpu: [ ] # include only these cpus in affinity settings
- receive-cpu-set:
cpu: [ ] # include only these cpus in affinity settings
- decode-cpu-set:
cpu: [ , ]
mode: "balanced"
- stream-cpu-set:
cpu: [ "0-1" ]
- detect-cpu-set:
cpu: [ "all" ]
mode: "exclusive" # run detect threads in these cpus
# Use explicitely threads and don't compute number by using
# detect-thread-ratio variable:
# threads:
prio:
low: [ ]
medium: [ "1-2" ]
high: [ ]
default: "medium"
- verdict-cpu-set:
cpu: [ ]
prio:
default: "high"
- reject-cpu-set:
cpu: [ ]
prio:
default: "low"
- output-cpu-set:
cpu: [ "all" ]
prio:
default: "medium"
#
# By default Suricata creates one "detect" thread per available CPU/CPU core.
# This setting allows controlling this behaviour. A ratio setting of will
# create detect threads for each CPU/CPU core. So for a dual core CPU this
# will result in detect threads. If values below are used, less threads
# are created. So on a dual core CPU a setting of 0.5 results in detect
# thread being created. Regardless of the setting at a minimum detect
# thread will always be created.
#
detect-thread-ratio: 1.5 # Cuda configuration.
cuda:
# The "mpm" profile. On not specifying any of these parameters, the engine's
# internal default values are used, which are same as the ones specified here.
- mpm:
# Threshold limit for no of packets buffered to the GPU. Once we hit this
# limit, we pass the buffer to the gpu.
packet-buffer-limit:
# The maximum length for a packet that we would buffer to the gpu.
# Anything over this is MPM'ed on the CPU. All entries > 0 are valid.
# Can be specified in kb, mb, gb. Just a number indicates it's in bytes.
packet-size-limit:
# No of packet buffers we initialize. All entries > are valid.
packet-buffers:
# The timeout limit for batching of packets in secs. If we don't fill the
# buffer within this timeout limit, we pass the currently filled buffer to the gpu.
# All entries > are valid.
batching-timeout:
# Specifies whether to use page-locked memory whereever possible. Accepted values
# are "enabled" and "disabled".
page-locked: enabled
# The device to use for the mpm. Currently we don't support load balancing
# on multiple gpus. In case you have multiple devices on your system, you
# can specify the device to use, using this conf. By default we hold , to
# specify the first device cuda sees. To find out device-id associated with
# the card(s) on the system run "suricata --list-cuda-cards".
device-id:
# No of Cuda streams used for asynchronous processing. All values > are valid.
# For this option you need a device with Compute Capability > 1.0 and
# page-locked enabled to have any effect.
cuda-streams: # Select the multi pattern algorithm you want to run for scan/search the
# in the engine. The supported algorithms are b2g, b2gc, b2gm, b3g, wumanber,
# ac and ac-gfbs.
#
# The mpm you choose also decides the distribution of mpm contexts for
# signature groups, specified by the conf - "detect-engine.sgh-mpm-context".
# Selecting "ac" as the mpm would require "detect-engine.sgh-mpm-context"
# to be set to "single", because of ac's memory requirements, unless the
# ruleset is small enough to fit in one's memory, in which case one can
# use "full" with "ac". Rest of the mpms can be run in "full" mode.
#
# There is also a CUDA pattern matcher (only available if Suricata was
# compiled with --enable-cuda: b2g_cuda. Make sure to update your
# max-pending-packets setting above as well if you use b2g_cuda. mpm-algo: ac # The memory settings for hash size of these algorithms can vary from lowest
# () - low () - medium () - high () - higher () - max
# (). The bloomfilter sizes of these algorithms can vary from low () -
# medium () - high ().
#
# For B2g/B3g algorithms, there is a support for two different scan/search
# algorithms. For B2g the scan algorithms are B2gScan & B2gScanBNDMq, and
# search algorithms are B2gSearch & B2gSearchBNDMq. For B3g scan algorithms
# are B3gScan & B3gScanBNDMq, and search algorithms are B3gSearch &
# B3gSearchBNDMq.
#
# For B2g the different scan/search algorithms and, hash and bloom
# filter size settings. For B3g the different scan/search algorithms and, hash
# and bloom filter size settings. For wumanber the hash and bloom filter size
# settings. pattern-matcher:
- b2gc:
search-algo: B2gSearchBNDMq
hash-size: low
bf-size: medium
- b2gm:
search-algo: B2gSearchBNDMq
hash-size: low
bf-size: medium
- b2g:
search-algo: B2gSearchBNDMq
hash-size: low
bf-size: medium
- b3g:
search-algo: B3gSearchBNDMq
hash-size: low
bf-size: medium
- wumanber:
hash-size: low
bf-size: medium # Defrag settings: defrag:
trackers: # number of defragmented flows to follow
max-frags: # number of fragments to keep (higher than trackers)
prealloc: yes
timeout: # Flow settings:
# By default, the reserved memory (memcap) for flows is 32MB. This is the limit
# for flow allocation inside the engine. You can change this value to allow
# more memory usage for flows.
# The hash-size determine the size of the hash used to identify flows inside
# the engine, and by default the value is .
# At the startup, the engine can preallocate a number of flows, to get a better
# performance. The number of flows preallocated is by default.
# emergency-recovery is the percentage of flows that the engine need to
# prune before unsetting the emergency state. The emergency state is activated
# when the memcap limit is reached, allowing to create new flows, but
# prunning them with the emergency timeouts (they are defined below).
# If the memcap is reached, the engine will try to prune flows
# with the default timeouts. If it doens't find a flow to prune, it will set
# the emergency bit and it will try again with more agressive timeouts.
# If that doesn't work, then it will try to kill the last time seen flows
# not in use.
# The memcap can be specified in kb, mb, gb. Just a number indicates it's
# in bytes. flow:
memcap: 32mb
hash-size:
prealloc:
emergency-recovery: # Specific timeouts for flows. Here you can specify the timeouts that the
# active flows will wait to transit from the current state to another, on each
# protocol. The value of "new" determine the seconds to wait after a hanshake or
# stream startup before the engine free the data of that flow it doesn't
# change the state to established (usually if we don't receive more packets
# of that flow). The value of "established" is the amount of
# seconds that the engine will wait to free the flow if it spend that amount
# without receiving new packets or closing the connection. "closed" is the
# amount of time to wait after a flow is closed (usually zero).
#
# There's an emergency mode that will become active under attack circumstances,
# making the engine to check flow status faster. This configuration variables
# use the prefix "emergency-" and work similar as the normal ones.
# Some timeouts doesn't apply to all the protocols, like "closed", for udp and
# icmp. flow-timeouts: default:
new:
established:
closed:
emergency-new:
emergency-established:
emergency-closed:
tcp:
new:
established:
closed:
emergency-new:
emergency-established:
emergency-closed:
udp:
new:
established:
emergency-new:
emergency-established:
icmp:
new:
established:
emergency-new:
emergency-established: # Stream engine settings. Here the TCP stream tracking and reaasembly
# engine is configured.
#
# stream:
# memcap: 32mb # Can be specified in kb, mb, gb. Just a
# # number indicates it's in bytes.
# checksum-validation: yes # To validate the checksum of received
# # packet. If csum validation is specified as
# # "yes", then packet with invalid csum will not
# # be processed by the engine stream/app layer.
# # Warning: locally generated trafic can be
# # generated without checksum due to hardware offload
# # of checksum. You can control the handling of checksum
# # on a per-interface basis via the 'checksum-checks'
# # option
# max-sessions: # 256k concurrent sessions
# prealloc-sessions: # 32k sessions prealloc'd
# midstream: false # don't allow midstream session pickups
# async-oneside: false # don't enable async stream handling
# inline: no # stream inline mode
#
# reassembly:
# memcap: 64mb # Can be specified in kb, mb, gb. Just a number
# # indicates it's in bytes.
# depth: 1mb # Can be specified in kb, mb, gb. Just a number
# # indicates it's in bytes.
# toserver-chunk-size: # inspect raw stream in chunks of at least
# # this size. Can be specified in kb, mb,
# # gb. Just a number indicates it's in bytes.
# toclient-chunk-size: # inspect raw stream in chunks of at least
# # this size. Can be specified in kb, mb,
# # gb. Just a number indicates it's in bytes. stream:
memcap: 32mb
checksum-validation: yes # reject wrong csums
inline: no # no inline mode
reassembly:
memcap: 64mb
depth: 1mb # reassemble 1mb into a stream
toserver-chunk-size:
toclient-chunk-size: # Host table:
#
# Host table is used by tagging and per host thresholding subsystems.
#
host:
hash-size:
prealloc:
memcap: # Logging configuration. This is not about logging IDS alerts, but
# IDS output about what its doing, errors, etc.
logging: # The default log level, can be overridden in an output section.
# Note that debug level logging will only be emitted if Suricata was
# compiled with the --enable-debug configure option.
#
# This value is overriden by the SC_LOG_LEVEL env var.
default-log-level: info # The default output format. Optional parameter, should default to
# something reasonable if not provided. Can be overriden in an
# output section. You can leave this out to get the default.
#
# This value is overriden by the SC_LOG_FORMAT env var.
#default-log-format: "[%i] %t - (%f:%l) <%d> (%n) -- " # A regex to filter output. Can be overridden in an output section.
# Defaults to empty (no filter).
#
# This value is overriden by the SC_LOG_OP_FILTER env var.
default-output-filter: # Define your logging outputs. If none are defined, or they are all
# disabled you will get the default - console output.
outputs:
- console:
enabled: yes
- file:
enabled: yes
filename: /var/log/suricata.log
- syslog:
enabled: yes
facility: local5
format: "[%i] <%d> -- " # PF_RING configuration. for use with native PF_RING support
# for more info see http://www.ntop.org/PF_RING.html
pfring:
- interface: eth0
# Number of receive threads (> will enable experimental flow pinned
# runmode)
threads: # Default clusterid. PF_RING will load balance packets based on flow.
# All threads/processes that will participate need to have the same
# clusterid.
cluster-id: # Default PF_RING cluster type. PF_RING can load balance per flow or per hash.
# This is only supported in versions of PF_RING > 4.1..
cluster-type: cluster_round_robin
# bpf filter for this interface
#bpf-filter: tcp
# Choose checksum verification mode for the interface. At the moment
# of the capture, some packets may be with an invalid checksum due to
# offloading to the network card of the checksum computation.
# Possible values are:
# - rxonly: only compute checksum for packets received by network card.
# - yes: checksum validation is forced
# - no: checksum validation is disabled
# - auto: suricata uses a statistical approach to detect when
# checksum off-loading is used. (default)
# Warning: 'checksum-validation' must be set to yes to have any validation
#checksum-checks: auto
# Second interface
#- interface: eth1
# threads:
# cluster-id:
# cluster-type: cluster_flow pcap:
- interface: eth0
#buffer-size:
#bpf-filter: "tcp and port 25"
# Choose checksum verification mode for the interface. At the moment
# of the capture, some packets may be with an invalid checksum due to
# offloading to the network card of the checksum computation.
# Possible values are:
# - yes: checksum validation is forced
# - no: checksum validation is disabled
# - auto: suricata uses a statistical approach to detect when
# checksum off-loading is used. (default)
# Warning: 'checksum-validation' must be set to yes to have any validation
#checksum-checks: auto # For FreeBSD ipfw() divert() support.
# Please make sure you have ipfw_load="YES" and ipdivert_load="YES"
# in /etc/loader.conf or kldload'ing the appropriate kernel modules.
# Additionally, you need to have an ipfw rule for the engine to see
# the packets from ipfw. For Example:
#
# ipfw add divert ip from any to any
#
# The above should be the same number you passed on the command
# line, i.e. -d
#
ipfw: # Reinject packets at the specified ipfw rule number. This config
# option is the ipfw rule number AT WHICH rule processing continues
# in the ipfw processing system after the engine has finished
# inspecting the packet for acceptance. If no rule number is specified,
# accepted packets are reinjected at the divert rule which they entered
# and IPFW rule processing continues. No check is done to verify
# this will rule makes sense so care must be taken to avoid loops in ipfw.
#
## The following example tells the engine to reinject packets
# back into the ipfw firewall AT rule number :
#
# ipfw-reinjection-rule-number: # Set the default rule path here to search for the files.
# if not set, it will look at the current working dir
default-rule-path: /etc/suricata/rules/
rule-files: #Malware/trojan oriented rules
- emerging-trojan.rules
- emerging-malware.rules
- emerging-mobile_malware.rules
- emerging-worm.rules
- emerging-user_agents.rules
- emerging-current_events.rules #important but relatively low load rules you'll likely want to keep on
- emerging-ftp.rules
- emerging-pop3.rules
- emerging-rpc.rules
- emerging-attack_response.rules
# - emerging-icmp.rules
- emerging-scan.rules
- emerging-voip.rules
- emerging-imap.rules
- emerging-web_server.rules
- emerging-smtp.rules
- emerging-dns.rules
- emerging-misc.rules
- emerging-snmp.rules
- emerging-sql.rules
- emerging-dos.rules
- emerging-telnet.rules
- emerging-exploit.rules
- emerging-tftp.rules #useful but often high load rules. Look here for performance tuning
- emerging-web_client.rules
- emerging-netbios.rules #things you'll want to look through and consider policy needs
- emerging-policy.rules
# - emerging-games.rules
- emerging-p2p.rules
- emerging-chat.rules #informational, not recommended for high speed nets
# - emerging-icmp_info.rules
# - emerging-info.rules
# - emerging-shellcode.rules
# - emerging-inappropriate.rules
# - emerging-web_specific_apps.rules
# - emerging-activex.rules #ip based rules
- botcc.rules
# - botcc.portgrouped.rules
- ciarmy.rules
- compromised.rules
- drop.rules
- dshield.rules
- tor.rules #only use the scada_special if you have the scada extensions compiled int
# - emerging-scada_special.rules
# - emerging-scada.rules classification-file: /etc/suricata/classification.config
reference-config-file: /etc/suricata/reference.config # Holds variables that would be used by the engine.
vars: # Holds the address group vars that would be passed in a Signature.
# These would be retrieved during the Signature address parsing stage.
address-groups: HOME_NET: "[192.168.0.0/16,10.0.0.0/8,172.16.0.0/12]" EXTERNAL_NET: "any" HTTP_SERVERS: "$HOME_NET" SMTP_SERVERS: "$HOME_NET" SQL_SERVERS: "$HOME_NET" DNS_SERVERS: "$HOME_NET" TELNET_SERVERS: "$HOME_NET" AIM_SERVERS: "$EXTERNAL_NET" DNP3_SERVER: "$HOME_NET" DNP3_CLIENT: "$HOME_NET" MODBUS_CLIENT: "$HOME_NET" MODBUS_SERVER: "$HOME_NET" ENIP_CLIENT: "$HOME_NET" ENIP_SERVER: "$HOME_NET" # Holds the port group vars that would be passed in a Signature.
# These would be retrieved during the Signature port parsing stage.
port-groups: HTTP_PORTS: "80,81,311,591,593,901,1220,1414,1830,2301,2381,2809,3128,3702,4343,5250,7001,7145,7510,7777,7779,8000,8008,8014,8028,8080,8088,8118,8123,8180,8181,8243,8280,8800,8888,8899,9080,9090,9091,9443,9999,11371,55555" SHELLCODE_PORTS: "!80" ORACLE_PORTS: SSH_PORTS: DNP3_PORTS: # Set the order of alerts bassed on actions
# The default order is pass, drop, reject, alert
action-order:
- pass
- drop
- reject
- alert # Host specific policies for defragmentation and TCP stream
# reassembly. The host OS lookup is done using a radix tree, just
# like a routing table so the most specific entry matches.
host-os-policy:
# Make the default policy windows.
windows: [0.0.0.0/]
bsd: []
bsd-right: []
old-linux: []
linux: []
old-solaris: []
solaris: []
hpux10: []
hpux11: []
irix: []
macos: []
vista: []
windows2k3: [] # Limit for the maximum number of asn1 frames to decode (default )
asn1-max-frames: # When run with the option --engine-analysis, the engine will read each of
# the parameters below, and print reports for each of the enabled sections
# and exit. The reports are printed to a file in the default log dir
# given by the parameter "default-log-dir", with engine reporting
# subsection below printing reports in its own report file.
engine-analysis:
# enables printing reports for fast-pattern for every rule.
rules-fast-pattern: yes
# enables printing reports for each rule
rules: yes #recursion and match limits for PCRE where supported
pcre:
match-limit:
match-limit-recursion: ###########################################################################
# Configure libhtp.
#
#
# default-config: Used when no server-config matches
# personality: List of personalities used by default
# request-body-limit: Limit reassembly of request body for inspection
# by http_client_body & pcre /P option.
# response-body-limit: Limit reassembly of response body for inspection
# by file_data, http_server_body & pcre /Q option.
# double-decode-path: Double decode path section of the URI
# double-decode-query: Double decode query section of the URI
#
# server-config: List of server configurations to use if address matches
# address: List of ip addresses or networks for this block
# personalitiy: List of personalities used by this block
# request-body-limit: Limit reassembly of request body for inspection
# by http_client_body & pcre /P option.
# response-body-limit: Limit reassembly of response body for inspection
# by file_data, http_server_body & pcre /Q option.
# double-decode-path: Double decode path section of the URI
# double-decode-query: Double decode query section of the URI
#
# Currently Available Personalities:
# Minimal
# Generic
# IDS (default)
# IIS_4_0
# IIS_5_0
# IIS_5_1
# IIS_6_0
# IIS_7_0
# IIS_7_5
# Apache
# Apache_2_2
###########################################################################
libhtp: default-config:
personality: IDS
# Can be specified in kb, mb, gb. Just a number indicates
# it's in bytes.
request-body-limit:
response-body-limit:
double-decode-path: no
double-decode-query: no ##### Set proper personality for your net #######
# server-config:
#
# - apache:
# address: [192.168.1.0/, 127.0.0.0/, "::1"]
# personality: Apache_2_2
# # Can be specified in kb, mb, gb. Just a number indicates
# # it's in bytes.
# request-body-limit:
# response-body-limit:
# double-decode-path: no
# double-decode-query: no
#
# - iis7:
# address:
# - 192.168.0.0/
# - 192.168.10.0/
# personality: IIS_7_0
# # Can be specified in kb, mb, gb. Just a number indicates
# # it's in bytes.
# request-body-limit:
# response-body-limit:
# double-decode-path: no
# double-decode-query: no # Profiling settings. Only effective if Suricata has been built with the
# the --enable-profiling configure flag.
#
profiling: # rule profiling
rules: # Profiling can be disabled here, but it will still have a
# performance impact if compiled in.
enabled: yes
filename: rule_perf.log
append: yes # Sort options: ticks, avgticks, checks, matches, maxticks
sort: avgticks # Limit the number of items printed at exit.
#limit: # packet profiling
packets: # Profiling can be disabled here, but it will still have a
# performance impact if compiled in.
enabled: yes
filename: packet_stats.log
append: yes # per packet csv output
csv: # Output can be disabled here, but it will still have a
# performance impact if compiled in.
enabled: no
filename: packet_stats.csv # profiling of locking. Only available when Suricata was built with
# --enable-profiling-locks.
locks:
enabled: no
filename: lock_stats.log
append: yes # Suricata core dump configuration. Limits the size of the core dump file to
# approximately max-dump. The actual core dump size will be a multiple of the
# page size. Core dumps that would be larger than max-dump are truncated. On
# Linux, the actual core dump size may be a few pages larger than max-dump.
# Setting max-dump to disables core dumping.
# Setting max-dump to 'unlimited' will give the full core dump file.
# On -bit Linux, a max-dump value >= ULONG_MAX may cause the core dump size
# to be 'unlimited'. coredump:
max-dump: unlimited
25、SELKS里的suricata的threshold.config(非常重要)
这根,默认为空。
26、SELKS里的suricata的tls-events.rules(非常重要)
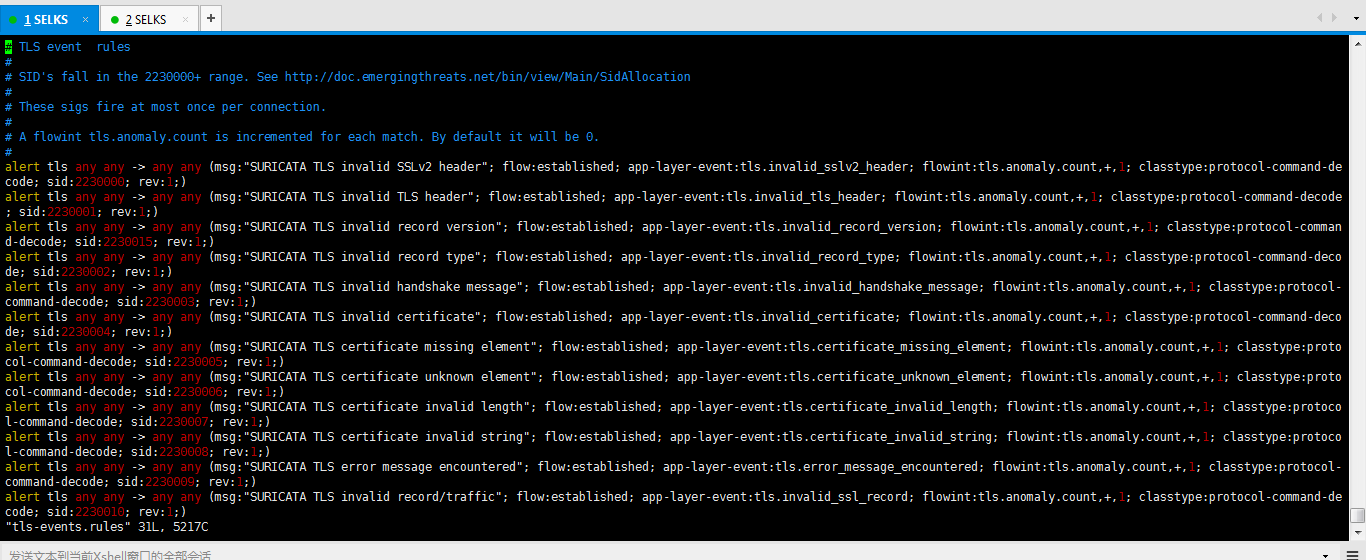
# TLS event rules
#
# SID's fall in the 2230000+ range. See http://doc.emergingthreats.net/bin/view/Main/SidAllocation
#
# These sigs fire at most once per connection.
#
# A flowint tls.anomaly.count is incremented for each match. By default it will be .
#
alert tls any any -> any any (msg:"SURICATA TLS invalid SSLv2 header"; flow:established; app-layer-event:tls.invalid_sslv2_header; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS invalid TLS header"; flow:established; app-layer-event:tls.invalid_tls_header; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS invalid record version"; flow:established; app-layer-event:tls.invalid_record_version; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS invalid record type"; flow:established; app-layer-event:tls.invalid_record_type; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS invalid handshake message"; flow:established; app-layer-event:tls.invalid_handshake_message; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS invalid certificate"; flow:established; app-layer-event:tls.invalid_certificate; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS certificate missing element"; flow:established; app-layer-event:tls.certificate_missing_element; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS certificate unknown element"; flow:established; app-layer-event:tls.certificate_unknown_element; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS certificate invalid length"; flow:established; app-layer-event:tls.certificate_invalid_length; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS certificate invalid string"; flow:established; app-layer-event:tls.certificate_invalid_string; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS error message encountered"; flow:established; app-layer-event:tls.error_message_encountered; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS invalid record/traffic"; flow:established; app-layer-event:tls.invalid_ssl_record; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS heartbeat encountered"; flow:established; app-layer-event:tls.heartbeat_message; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS overflow heartbeat encountered, possible exploit attempt (heartbleed)"; flow:established; app-layer-event:tls.overflow_heartbeat_message; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; reference:cve,-; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS invalid heartbeat encountered, possible exploit attempt (heartbleed)"; flow:established; app-layer-event:tls.invalid_heartbeat_message; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; reference:cve,-; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS invalid encrypted heartbeat encountered, possible exploit attempt (heartbleed)"; flow:established; app-layer-event:tls.dataleak_heartbeat_mismatch; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; reference:cve,-; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS multiple SNI extensions"; flow:established,to_server; app-layer-event:tls.multiple_sni_extensions; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS invalid SNI type"; flow:established,to_server; app-layer-event:tls.invalid_sni_type; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS invalid SNI length"; flow:established,to_server; app-layer-event:tls.invalid_sni_length; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS handshake invalid length"; flow:established; app-layer-event:tls.handshake_invalid_length; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;)
alert tls any any -> any any (msg:"SURICATA TLS too many records in packet"; flow:established; app-layer-event:tls.too_many_records_in_packet; flowint:tls.anomaly.count,+,; classtype:protocol-command-decode; sid:; rev:;) #next sid is
27、SELKS里的suricata的unicode.map(非常重要)

# Windows Version: 5.00.
# OEM codepage:
# ACP codepage: # INSTALLED CODEPAGES
(MAC - Roman) (MAC - Icelandic) (ANSI - Central Europe)
00a1: 00a2: 00a3:4c 00a5: 00aa: 00b2: 00b3: 00b9: 00ba:6f 00bc: 00bd: 00be: 00c0: 00c3: 00c5: 00c6: 00c8: 00ca: 00cc: 00cf: 00d1:4e 00d2:4f 00d5:4f 00d8:4f 00d9: 00db: 00e0: 00e3: 00e5: 00e6: 00e8: 00ea: 00ec: 00ef: 00f1:6e 00f2:6f 00f5:6f 00f8:6f 00f9: 00fb: 00ff: : : : : 010a: 010b: : : : : : : 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : : :4a :6a :4b :6b 013b:4c 013c:6c :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f : : 015c: 015d: : : : : 016a: 016b: 016c: 016d: : : : : : : : : : : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01b6:7a 01c0:7c 01c3: 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a : 02b9: 02ba: 02bc: 02c4:5e 02c6:5e 02c8: 02cb: 02cd:5f 02dc:7e : :5e :7e 030e: :5f :5f 037e:3b 04bb: :3a 066a: : : : : : : : :2d :2d : : 203c: :2f : : : : : : : : : : : : : : : : : 210a: 210b: 210c: 210d: 210e: : : :4c :6c :4e : : 211a: 211b: 211c: 211d: :5a :5a 212a:4b 212c: 212d: 212e: 212f: : : :4d :6f :5e :2d :7c 21a8:7c :2d :2f :5c :2a 221f:4c :7c :3a 223c:7e :5e :3c 232a:3e :2d 250c:2d :4c :2d 251c:2b :2b 252c: :2b 253c:2b :3d :2d 255a:4c 255d:2d : 256c:2b :2d :2d :2d :2d :2d :2d 25ac:2d 25b2:5e 25ba:3e 25c4:3c 25cb: 25d9: 263c: :2b :3e 266a: 266b: :7c : :3c :3e 301a:5b 301b:5d ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (ANSI - Cyrillic)
00c0: 00c1: 00c2: 00c3: 00c4: 00c5: 00c7: 00c8: 00c9: 00ca: 00cb: 00cc: 00cd: 00ce: 00cf: 00d1:4e 00d2:4f 00d3:4f 00d4:4f 00d5:4f 00d6:4f 00d8:4f 00d9: 00da: 00db: 00dc: 00dd: 00e0: 00e1: 00e2: 00e3: 00e4: 00e5: 00e7: 00e8: 00e9: 00ea: 00eb: 00ec: 00ed: 00ee: 00ef: 00f1:6e 00f2:6f 00f3:6f 00f4:6f 00f5:6f 00f6:6f 00f8:6f 00f9: 00fa: 00fb: 00fc: 00fd: 00ff: : : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : : : 011a: 011b: 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : :4a :6a :4b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: 015e: 015f: : : : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : : :5a 017b:5a 017c:7a 017d:5a 017e:7a : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a 203c: :3c :5e :3e : :2d 221a: 221f:4c :2d 250c:2d :4c :2d 251c:2b :2b 252c: :2b 253c:2b :3d :2d :4c :4c 255a:4c 255b:2d 255c:2d 255d:2d : : : 256a:2b 256b:2b 256c:2b :2d :2d :2d :2d :2d :2d 25ac:2d 25b2:5e 25ba:3e 25c4:3c 25cb: 25d9: 263a:4f 263b:4f 263c: :2b :3e 266a: 266b: ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (ANSI - Latin I)
: : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : : 011a: 011b: 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : : :4a :6a :4b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: 015e: 015f: : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : :5a 017b:5a 017c:7a : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01b6:7a 01c0:7c 01c3: 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a : 02b9: 02ba: 02bc: 02c4:5e 02c8: 02cb: 02cd:5f : :5e :7e 030e: :5f :5f 037e:3b : : 03a3: 03a6: 03a9:4f 03b1: 03b4: 03b5: 03c0: 03c3: 03c4: 03c6: 04bb: :3a 066a: : : : : : : : :2d :2d :3d : : :2f : : : : : 207f:6e : : : : : : : : : : 20a7: : : 210a: 210b: 210c: 210d: 210e: : : :4c :6c :4e : : 211a: 211b: 211c: 211d: :5a :5a 212a:4b 212c: 212d: 212e: 212f: : : :4d :6f :2d :2f :5c :2a 221a: 221e: :7c :6e :3a 223c:7e :3d :3d :3d :5e : : :3c 232a:3e :2d 250c:2b :2b :2b :2b 251c:2b 252c:2d :2d 253c:2b :2d :2b :2b :2b :2b :2b :2b :2b :2b 255a:2b 255b:2b 255c:2b 255d:2b :2d :2d :2d :2d :2d :2d 256a:2b 256b:2b 256c:2b :5f :7c : :3c :3e 301a:5b 301b:5d ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (ANSI - Greek)
00b4:2f 00c0: 00c1: 00c2: 00c3: 00c4: 00c5: 00c7: 00c8: 00c9: 00ca: 00cb: 00cc: 00cd: 00ce: 00cf: 00d1:4e 00d2:4f 00d3:4f 00d4:4f 00d5:4f 00d6:4f 00d8:4f 00d9: 00da: 00db: 00dc: 00dd: 00e0: 00e1: 00e2: 00e3: 00e4: 00e5: 00e7: 00e8: 00e9: 00ea: 00eb: 00ec: 00ed: 00ee: 00ef: 00f1:6e 00f2:6f 00f3:6f 00f4:6f 00f5:6f 00f6:6f 00f8:6f 00f9: 00fa: 00fb: 00fc: 00fd: 00ff: : : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : : : 011a: 011b: 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : :4a :6a :4b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: 015e: 015f: : : : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : : :5a 017b:5a 017c:7a 017d:5a 017e:7a : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a 037e:3b 203c: :3c :5e :3e : :2d 221f:4c :2d 250c:2d :4c :2d 251c:2b :2b 252c: :2b 253c:2b :3d :2d 255a:4c 255d:2d : 256c:2b :2d :2d :2d :2d :2d :2d 25ac:2d 25b2:5e 25ba:3e 25c4:3c 25cb: 25d9: 263a:4f 263b:4f 263c: :2b :3e 266a: 266b: ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (ANSI - Turkish)
00dd: 00fd: : : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : : : 011a: 011b: 011c: 011d: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: :4a :6a :4b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : :5a 017b:5a 017c:7a 017d:5a 017e:7a : : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01b6:7a 01c0:7c 01c3: 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a : 02b9: 02ba: 02bc: 02c4:5e 02c7:5e 02c8: 02cb: 02cd:5f 02d8:5e 02d9: : :5e :5f :5f 04bb: :3a 066a: : : : : : : : :2d :2d : : 203c: :2f : : : : : : : : : : : : : : 210a: 210b: 210c: 210d: 210e: : : :4c :6c :4e : : 211a: 211b: 211c: 211d: :5a :5a 212a:4b 212c: 212d: 212e: 212f: : : :4d :6f :5e : :2d :7c 21a8:7c :2d :2f :5c :2a 221f:4c :7c :3a 223c:7e :5e :3c 232a:3e :2d 250c:2d :4c :2d 251c:2b :2b 252c: :2b 253c:2b :3d :2d 255a:4c 255d:2d : 256c:2b :2d :2d :2d :2d :2d :2d 25ac:2d 25b2:5e 25ba:3e 25c4:3c 25cb: 25d9: 263a:4f 263b:4f 263c: :2b :3e 266a: 266b: :7c : :3c :3e 301a:5b 301b:3d 301d: 301e: ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (ANSI - Hebrew)
: ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (ANSI - Arabic)
00c0: 00c2: 00c7: 00c8: 00c9: 00ca: 00cb: 00ce: 00cf: 00d4:4f 00d9: 00db: 00dc: : ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (ANSI - Baltic)
ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (ANSI/OEM - Viet Nam)
ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e #INVALID CODEPAGE:
(US-ASCII)
00a0: 00a1: 00a2: 00a4: 00a5: 00a6:7c 00a9: 00aa: 00ab:3c 00ad:2d 00ae: 00b2: 00b3: 00b7:2e 00b8:2c 00b9: 00ba:6f 00bb:3e 00c0: 00c1: 00c2: 00c3: 00c4: 00c5: 00c6: 00c7: 00c8: 00c9: 00ca: 00cb: 00cc: 00cd: 00ce: 00cf: 00d0: 00d1:4e 00d2:4f 00d3:4f 00d4:4f 00d5:4f 00d6:4f 00d8:4f 00d9: 00da: 00db: 00dc: 00dd: 00e0: 00e1: 00e2: 00e3: 00e4: 00e5: 00e6: 00e7: 00e8: 00e9: 00ea: 00eb: 00ec: 00ed: 00ee: 00ef: 00f1:6e 00f2:6f 00f3:6f 00f4:6f 00f5:6f 00f6:6f 00f8:6f 00f9: 00fa: 00fb: 00fc: 00fd: 00ff: : : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : : : 011a: 011b: 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : : :4a :6a :4b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: 015e: 015f: : : : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : : :5a 017b:5a 017c:7a 017d:5a 017e:7a : : : : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01b6:7a 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a : 02b9: 02ba: 02bc: 02c4:5e 02c6:5e 02c8: 02cb: 02cd:5f 02dc:7e : :5e :7e 030e: :5f :5f : : : : : : : :2d :2d :2d :2d : : 201a:2c 201c: 201d: 201e: :2e :2e : : :3c 203a:3e : ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (T.)
f8dd:5c f8de:5e f8df: f8e0:7b f8fc:7d f8fd:7e f8fe:7f (Russian - KOI8)
00a7: 00ab:3c 00ad:2d 00ae: 00b1:2b 00b6: 00bb:3e 00c0: 00c1: 00c2: 00c3: 00c4: 00c5: 00c7: 00c8: 00c9: 00ca: 00cb: 00cc: 00cd: 00ce: 00cf: 00d1:4e 00d2:4f 00d3:4f 00d4:4f 00d5:4f 00d6:4f 00d8:4f 00d9: 00da: 00db: 00dc: 00dd: 00e0: 00e1: 00e2: 00e3: 00e4: 00e5: 00e7: 00e8: 00e9: 00ea: 00eb: 00ec: 00ed: 00ee: 00ef: 00f1:6e 00f2:6f 00f3:6f 00f4:6f 00f5:6f 00f6:6f 00f8:6f 00f9: 00fa: 00fb: 00fc: 00fd: 00ff: : : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : : : 011a: 011b: 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : :4a :6a :4b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: 015e: 015f: : : : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : : :5a 017b:5a 017c:7a 017d:5a 017e:7a : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a :2d :2d : : 201a: 201c: 201d: 201e: : :3a : :3c 203a:3e 203c: : :1b : :1a : :1d : 21a8: 221f:1c :7f 25ac: 25b2:1e 25ba: 25bc:1f 25c4: 25cb: 25d8: 25d9:0a 263a: 263b: 263c:0f :0c :0b : : : : 266a:0d 266b:0e (ISO - Latin I)
: : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : : : 011a: 011b: 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : : :4a :6a :4b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: 015e: 015f: : : : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : : :5a 017b:5a 017c:7a 017d:5a 017e:7a : : : : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01b6:7a 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a : 02b9: 02ba: 02bc: 02c4:5e 02c6:5e 02c8: 02cb: 02cd:5f 02dc:7e : :5e :7e 030e: :5f :5f : : : : : : : :2d :2d :2d :2d : : 201a:2c 201c: 201d: 201e: :2e :2e : : :3c 203a:3e : ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (ISO - Central Europe)
00a1: 00a2: 00a5: 00a6:7c 00a9: 00aa: 00ab:3c 00ae: 00b2: 00b3: 00b7:2e 00b9: 00ba:6f 00bb:3e 00c0: 00c3: 00c5: 00c6: 00c8: 00ca: 00cc: 00cf: 00d0: 00d1:4e 00d2:4f 00d5:4f 00d8:4f 00d9: 00db: 00e0: 00e3: 00e5: 00e6: 00e8: 00ea: 00ec: 00ef: 00f1:6e 00f2:6f 00f5:6f 00f8:6f 00f9: 00fb: 00ff: : : : : 010a: 010b: : : : : : : 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : : :4a :6a :4b :6b 013b:4c 013c:6c :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f : : 015c: 015d: : : : : 016a: 016b: 016c: 016d: : : : : : : : : : : : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01b6:7a 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a : 02b9: 02ba: 02bc: 02c4:5e 02c6:5e 02c8: 02cb: 02cd:5f 02dc:7e : :5e :7e 030e: :5f :5f : : : : : : : :2d :2d :2d :2d : : 201a:2c 201c: 201d: 201e: :2e :2e : : :3c 203a:3e : ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e #INVALID CODEPAGE:
#INVALID CODEPAGE:
(ISO - Latin )
00a6:7c : : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : 011a: 011b: 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : : :4a :6a :4b :6b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014a:4e 014b:6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: 015e: 015f: : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : :5a 017b:5a 017c:7a : : : : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01b6:7a 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a : 02b9: 02ba: 02bc: 02c4:5e 02c6:5e 02c8: 02cb: 02cd:5f 02dc:7e : :5e :7e 030e: :5f :5f : : : : : : : :2d :2d :2d :2d : : 201a:2c 201c: 201d: 201e: :2e :2e : : :3c 203a:3e : ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (IBM EBCDIC - U.S./Canada)
: :2d :2e :2f : : 000a: :3c :3d : : 001a:3f 001b: : :5a :7f :7b :5b :6c : :7d :4d :5d 002a:5c 002b:4e 002c:6b 002d: 002e:4b 002f: 003a:7a 003b:5e 003c:4c 003d:7e 003e:6e 003f:6f :7c 005f:6d : 007c:4f 007f: : : : : : : : : : : 008a:2a 008b:2b 008c:2c 008d: 008e:0a 008f:1b : : :1a : : : : : : : 009a:3a 009b:3b 009c: 009d: 009e:3e 00a0: 00a2:4a 00a6:6a 00ac:5f 00c0: 00c1: 00c2: 00c3: 00c4: 00c5: 00c7: 00c8: 00c9: 00ca: 00cb: 00cc: 00cd: 00ce: 00cf: 00d1: 00df: 00e0: 00e1: 00e2: 00e3: 00e4: 00e5: 00e7: 00e8: 00e9: 00ea: 00eb: 00ec: 00ed: 00ee: 00ef: 00f1: 00f8: ff01:5a ff02:7f ff03:7b ff04:5b ff05:6c ff06: ff07:7d ff08:4d ff09:5d ff0a:5c ff0b:4e ff0c:6b ff0d: ff0e:4b ff0f: ff1a:7a ff1b:5e ff1c:4c ff1d:7e ff1e:6e ff20:7c ff3f:6d ff40: ff5c:4f (OEM - United States)
00a4:0f 00a7: 00a8: 00a9: 00ad:2d 00ae: 00af:5f 00b3: 00b4: 00b6: 00b8:2c 00b9: 00be:5f 00c0: 00c1: 00c2: 00c3: 00c8: 00ca: 00cb: 00cc: 00cd: 00ce: 00cf: 00d0: 00d2:4f 00d3:4f 00d4:4f 00d5:4f 00d7: 00d8:4f 00d9: 00da: 00db: 00dd: 00de:5f 00e3: 00f0: 00f5:6f 00f8:6f 00fd: 00fe:5f : : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : : : 011a: 011b: 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : : :4a :6a :4b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: 015e: 015f: : : : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : : :5a 017b:5a 017c:7a 017d:5a 017e:7a : : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01b6:7a 01c0:7c 01c3: 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a : 02b9: 02ba: 02bc: 02c4:5e 02c6:5e 02c8: 02ca: 02cb: 02cd:5f 02dc:7e : : :5e :7e : 030e: :2c :5f :5f 037e:3b 04bb: :3a 066a: : : : : : : : :2d :2d :2d :2d :5f : : 201a:2c 201c: 201d: 201e:2c :2b : :2e : : : :3c 203a:3e 203c: :2f : : : : : : : : : : : : : : : 20dd: : : 210a: 210b: 210c: 210d: 210e: : : :4c :6c :4e : : 211a: 211b: 211c: 211d: : :5a :5a 212a:4b 212c: 212d: 212e: 212f: : : :4d :6f :1b : :1a : :1d : 21a8: :2d :2f :5c :2a 221f:1c :7c :3a 223c:7e :7f :5e :3c 232a:3e 25ac: 25b2:1e 25ba: 25bc:1f 25c4: 25cb: 25d8: 25d9:0a 263a: 263b: 263c:0f :0c :0b : : : : 266a:0d 266b:0e :7c : : :3c :3e 301a:5b 301b:5d ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (IBM EBCDIC - International)
: :2d :2e :2f : : 000a: :3c :3d : : 001a:3f 001b: : :4f :7f :7b :5b :6c : :7d :4d :5d 002a:5c 002b:4e 002c:6b 002d: 002e:4b 002f: 003a:7a 003b:5e 003c:4c 003d:7e 003e:6e 003f:6f :7c 005b:4a 005d:5a 005e:5f 005f:6d : 007f: : : : : : : : : : : 008a:2a 008b:2b 008c:2c 008d: 008e:0a 008f:1b : : :1a : : : : : : : 009a:3a 009b:3b 009c: 009d: 009e:3e 00a0: 00a6:6a 00c0: 00c1: 00c2: 00c3: 00c4: 00c5: 00c7: 00c8: 00c9: 00ca: 00cb: 00cc: 00cd: 00ce: 00cf: 00d1: 00df: 00e0: 00e1: 00e2: 00e3: 00e4: 00e5: 00e7: 00e8: 00e9: 00ea: 00eb: 00ec: 00ed: 00ee: 00ef: 00f1: 00f8: ff01:4f ff02:7f ff03:7b ff04:5b ff05:6c ff06: ff07:7d ff08:4d ff09:5d ff0a:5c ff0b:4e ff0c:6b ff0d: ff0e:4b ff0f: ff1a:7a ff1b:5e ff1c:4c ff1d:7e ff1e:6e ff20:7c ff3b:4a ff3d:5a ff3e:5f ff3f:6d ff40: (OEM - Multilingual Latin I)
: : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : : : 011a: 011b: 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : :4a :6a :4b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: 015e: 015f: : : : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : : :5a 017b:5a 017c:7a 017d:5a 017e:7a : : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01a9: 01ab: 01ae: 01af: 01b0: 01b6:5a 01c3: 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a : 02ba: 02bc: 02c4:5e 02c6:5e 02c8: 02cb: 02cd:5f 02dc:7e : :5e :7e 030e: :5f :5f 037e:3b : 03a3: 03a6: 03a9:4f 03b1: 03b4: 03b5: 03c0: 03c3: 03c4: 03c6: 04bb: :3a 066a: : : : : : : : :2d :2d :2d :2d : : 201a: 201c: 201d: 201e: : : :2e : :3c 203a:3e 203c: :2f : : : : : : 207f:6e : : : : : : : 20a7: 20dd:4f : : 210a: 210b: 210c: 210d: 210e: : : :4c :6c :4e : : 211a: 211b: 211c: 211d: : :5a :4f :5a 212a:4b 212c: 212d: 212e: 212f: : : :4d :6f :1b : :1a : :1d : 21a8: : :2d :2f :2f :2a : 221a: 221e: 221f:1c :6e :3a 223c:7e :7e :3d :3d :3d :7f :5e : : :3c 232a:3e 25ac: 25b2:1e 25ba: 25bc:1f 25c4: 25cb: 25d8: 25d9:0a 263a: 263b: 263c:0f :0c :0b : : : : 266a:0d 266b:0e : : :4f :3c :3e 301a:5b 301b:5d ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (OEM - Portuguese)
00a4:0f 00a5: 00a7: 00a8: 00a9: 00ad:5f 00ae: 00af: 00b3: 00b4:2f 00b6: 00b8:2c 00b9: 00be: 00c4: 00c5: 00c6: 00cb: 00ce: 00cf: 00d0: 00d6:4f 00d7: 00d8:4f 00db: 00dd: 00de: 00e4: 00e5: 00e6: 00eb: 00ee: 00ef: 00f0: 00f6:6f 00f8:6f 00fb: 00fd: 00fe: 00ff: : : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : : : 011a: 011b: 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : : :4a :6a :4b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: 015e: 015f: :5c :7c : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : : :5a 017b:5a 017c:7a 017d:5a 017e:7a : : : : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01b6:7a 01c0:7c 01c3: 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a : : 02b9: 02ba: 02bc: 02c4:5e 02c6:5e 02c8: 02c9: 02ca:2f 02cb: 02cd:5f 02dc:7e : :2f :5e :7e : : : 030e: :2c :5f :5f 037e:3b 04bb: :3a 066a: : : : : : : : :5f :5f :5f :5f :5f : : 201a:2c 201c: 201d: 201e: : : :2e : : : :3c 203a:3e 203c: :2f : : : : : : : : : : : : : : : 20dd:4f : : 210a: 210b: 210c: 210d: 210e: : : :4c :6c :4e : : 211a: 211b: 211c: 211d: : :5a :5a 212a:4b 212b: 212c: 212d: 212e: 212f: : : :4d :6f :1b : :1a : :1d : 21a8: :4f :5f :2f :5c :2a 221f:1c :7c :3a 223c:7e 22c5: :7f :5e :3c 232a:3e 25ac: 25b2:1e 25ba: 25bc:1f 25c4: 25cb: 25d8: 25d9:0a 263a: 263b: 263c:0f :0c :0b : : : : 266a:0d 266b:0e : :4f :3c :3e 301a:5b 301b:5d 30fb: (OEM - Icelandic)
00a2: 00a4:0f 00a5: 00a7: 00a8: 00a9: 00aa: 00ad:5f 00ae: 00af: 00b3: 00b4:2f 00b6: 00b8:2c 00b9: 00ba:6f 00be: 00c0: 00c2: 00c3: 00c8: 00ca: 00cb: 00cc: 00ce: 00cf: 00d1:4e 00d2:4f 00d4:4f 00d5:4f 00d7: 00d9: 00db: 00e3: 00ec: 00ee: 00ef: 00f1:6e 00f2:6f 00f5:6f 00f9: 00ff: : : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : : 011a: 011b: 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : : :4a :6a :4b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: 015e: 015f: : : : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : : :5a 017b:5a 017c:7a 017d:5a 017e:7a : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01b6:7a 01c3: 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a : : 02b9: 02ba: 02bc: 02c4:5e 02c6:5e 02c8: 02c9: 02ca:2f 02cb: 02cd:5f 02dc:7e : :2f :5e :7e : : : 030e: :2c :5f :5f 037e:3b 04bb: :3a 066a: : : : : : : : :2d :2d :2d :2d :5f : : 201a: 201c: 201d: 201e: : : : : : : :3c 203a:3e 203c: :2f : : : : : : : : : : : : : : : 20dd:4f : : 210a: 210b: 210c: 210d: 210e: : : :4c :6c :4e : : 211a: 211b: 211c: 211d: : :5a :5a 212a:4b 212c: 212d: 212e: 212f: : : :4d :6f :1b : :1a : :1d : 21a8: :4f :5f :2f :5c :2a 221f:1c :7c :3a 223c:7e 22c5: :7f :5e :3c 232a:3e 25ac: 25b2:1e 25ba: 25bc:1f 25c4: 25cb: 25d8: 25d9:0a 263a: 263b: 263c:0f :0c :0b : : : : 266a:0d 266b:0e : :4f :3c :3e 301a:5b 301b:5d 30fb: (OEM - Canadian French)
00a1: 00a5: 00a9: 00aa: 00ad: 00ae: 00b9: 00ba:6f 00c1: 00c3: 00c4: 00c5: 00c6: 00cc: 00cd: 00d0: 00d1:4e 00d2:4f 00d3:4f 00d5:4f 00d6:4f 00d7: 00d8:4f 00da: 00dd: 00de: 00e1: 00e3: 00e4: 00e5: 00e6: 00ec: 00ed: 00f0: 00f1:6e 00f2:6f 00f5:6f 00f6:6f 00f8:6f 00fd: 00fe: 00ff: : : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : : : 011a: 011b: 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : : :4a :6a :4b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: 015e: 015f: : : : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : : :5a 017b:5a 017c:7a 017d:5a 017e:7a : : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01b6:7a 01c3: 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a : 02b9: 02ba: 02bc: 02c4:5e 02c6:5e 02c8: 02c9: 02cb: 02cd:5f 02dc:7e : :5e :7e : : :5f :5f 037e:3b 04bb: :3a 066a: : : : : : : : :2d :2d :2d :2d : : 201a: 201c: 201d: 201e: : : : : : : :3c 203a:3e 203c: :2f : : : : : : : : : : : : : : 20a7: 20dd:4f : : 210a: 210b: 210c: 210d: 210e: : : :4c :6c :4e : : 211a: 211b: 211c: 211d: : :5a :5a 212a:4b 212b: 212c: 212d: 212e: 212f: : : :4d :6f :1b : :1a : :1d : 21a8: :4f :5f :2f :5c :2a 221f:1c :7c :3a 223c:7e 22c5: :7f :5e :3c 232a:3e 25ac: 25b2:1e 25ba: 25bc:1f 25c4: 25cb: 25d8: 25d9:0a 263a: 263b: 263c:0f :0c :0b : : : : 266a:0d 266b:0e : :4f :3c :3e 301a:5b 301b:5d 30fb: (OEM - Nordic)
00a2: 00a5: 00a7: 00a8: 00a9: 00ad:5f 00ae: 00af: 00b3: 00b4:2f 00b6: 00b8:2c 00b9: 00bb:3e 00be: 00c0: 00c1: 00c2: 00c3: 00c8: 00ca: 00cb: 00cc: 00cd: 00ce: 00cf: 00d0: 00d2:4f 00d3:4f 00d4:4f 00d5:4f 00d7: 00d9: 00da: 00db: 00dd: 00de: 00e3: 00f0: 00f5:6f 00fd: 00fe: : : : : : : : : : : 010a: 010b: 010c: 010d: 010e: 010f: : : : : : : : : : : 011a: 011b: 011c: 011d: 011e: 011f: : : : : : : : : : : 012a: 012b: 012c: 012d: 012e: 012f: : : :4a :6a :4b :6b :4c 013a:6c 013b:4c 013c:6c 013d:4c 013e:6c :4c :6c :4e :6e :4e :6e :4e :6e 014c:4f 014d:6f 014e:4f 014f:6f :4f :6f :4f :6f : : : : : : 015a: 015b: 015c: 015d: 015e: 015f: : : : : : : : : : : 016a: 016b: 016c: 016d: 016e: 016f: : : : : : : : : : :5a 017b:5a 017c:7a 017d:5a 017e:7a : : : 019a:6c 019f:4f 01a0:4f 01a1:6f 01ab: 01ae: 01af: 01b0: 01b6:7a 01c3: 01cd: 01ce: 01cf: 01d0: 01d1:4f 01d2:6f 01d3: 01d4: 01d5: 01d6: 01d7: 01d8: 01d9: 01da: 01db: 01dc: 01de: 01df: 01e4: 01e5: 01e6: 01e7: 01e8:4b 01e9:6b 01ea:4f 01eb:6f 01ec:4f 01ed:6f 01f0:6a : 02b9: 02ba: 02bc: 02c4:5e 02c6:5e 02c8: 02c9: 02ca:2f 02cb: 02cd:5f 02dc:7e : :2f :5e :7e : : : 030e: :2c :5f :5f 037e:3b 04bb: :3a 066a: : : : : : : : :2d :2d :2d :2d :5f : : 201a: 201c: 201d: 201e: : : : : : : :3c 203a:3e 203c: :2f : : : : : : : : : : : : : : : 20dd:4f : : 210a: 210b: 210c: 210d: 210e: : : :4c :6c :4e : : 211a: 211b: 211c: 211d: : :5a :5a 212a:4b 212c: 212d: 212e: 212f: : : :4d :6f :1b : :1a : :1d : 21a8: :4f :5f :2f :5c :2a 221f:1c :7c :3a 223c:7e 226b:3c 22c5: :7f :5e :3c 232a:3e 25ac: 25b2:1e 25ba: 25bc:1f 25c4: 25cb: 25d8: 25d9:0a 263a: 263b: 263c:0f :0c :0b : : : : 266a:0d 266b:0e : :4f :3c :3e 300b:3e 301a:5b 301b:5d 30fb: (ANSI/OEM - Thai)
00a7: 00b6: 203c: :1b : :1a : :1d : 21a8: 221f:1c :7f 25ac: 25b2:1e 25ba: 25bc:1f 25c4: 25cb: 25d8: 25d9:0a 263a: 263b: 263c:0f :0c :0b : : : : 266a:0d 266b:0e ff01: ff02: ff03: ff04: ff05: ff06: ff07: ff08: ff09: ff0a:2a ff0b:2b ff0c:2c ff0d:2d ff0e:2e ff0f:2f ff10: ff11: ff12: ff13: ff14: ff15: ff16: ff17: ff18: ff19: ff1a:3a ff1b:3b ff1c:3c ff1d:3d ff1e:3e ff20: ff21: ff22: ff23: ff24: ff25: ff26: ff27: ff28: ff29: ff2a:4a ff2b:4b ff2c:4c ff2d:4d ff2e:4e ff2f:4f ff30: ff31: ff32: ff33: ff34: ff35: ff36: ff37: ff38: ff39: ff3a:5a ff3b:5b ff3c:5c ff3d:5d ff3e:5e ff3f:5f ff40: ff41: ff42: ff43: ff44: ff45: ff46: ff47: ff48: ff49: ff4a:6a ff4b:6b ff4c:6c ff4d:6d ff4e:6e ff4f:6f ff50: ff51: ff52: ff53: ff54: ff55: ff56: ff57: ff58: ff59: ff5a:7a ff5b:7b ff5c:7c ff5d:7d ff5e:7e (ANSI/OEM - Japanese Shift-JIS)
00a1: 00a5:5c 00a6:7c 00a9: 00aa: 00ad:2d 00ae: 00b2: 00b3: 00b9: 00ba:6f 00c0: 00c1: 00c2: 00c3: 00c4: 00c5: 00c6: 00c7: 00c8: 00c9: 00ca: 00cb: 00cc: 00cd: 00ce: 00cf: 00d0: 00d1:4e 00d2:4f 00d3:4f 00d4:4f 00d5:4f 00d6:4f 00d8:4f 00d9: 00da: 00db: 00dc: 00dd: 00de: 00df: 00e0: 00e1: 00e2: 00e3: 00e4: 00e5: 00e6: 00e7: 00e8: 00e9: 00ea: 00eb: 00ec: 00ed: 00ee: 00ef: 00f0: 00f1:6e 00f2:6f 00f3:6f 00f4:6f 00f5:6f 00f6:6f 00f8:6f 00f9: 00fa: 00fb: 00fc: 00fd: 00fe: 00ff: (ANSI/OEM - Simplified Chinese GBK)
00a6:7c 00aa: 00ad:2d 00b2: 00b3: 00b9: 00ba:6f 00d0: 00dd: 00de: 00e2: 00f0: 00fd: 00fe: (ANSI/OEM - Korean)
00a6:7c 00c0: 00c1: 00c2: 00c3: 00c4: 00c5: 00c7: 00c8: 00c9: 00ca: 00cb: 00cc: 00cd: 00ce: 00cf: 00d1:4e 00d2:4f 00d3:4f 00d4:4f 00d5:4f 00d6:4f 00d9: 00da: 00db: 00dc: 00dd: 00e0: 00e1: 00e2: 00e3: 00e4: 00e5: 00e7: 00e8: 00e9: 00ea: 00eb: 00ec: 00ed: 00ee: 00ef: 00f1:6e 00f2:6f 00f3:6f 00f4:6f 00f5:6f 00f6:6f 00f9: 00fa: 00fb: 00fc: 00fd: 00ff: 20a9:5c (ANSI/OEM - Traditional Chinese Big5)
00a1: 00a6:7c 00a9: 00aa: 00ad:2d 00ae: 00b2: 00b3: 00b9: 00ba:6f 00c0: 00c1: 00c2: 00c3: 00c4: 00c5: 00c6: 00c7: 00c8: 00c9: 00ca: 00cb: 00cc: 00cd: 00ce: 00cf: 00d0: 00d1:4e 00d2:4f 00d3:4f 00d4:4f 00d5:4f 00d6:4f 00d8:4f 00d9: 00da: 00db: 00dc: 00dd: 00de: 00df: 00e0: 00e1: 00e2: 00e3: 00e4: 00e5: 00e6: 00e7: 00e8: 00e9: 00ea: 00eb: 00ec: 00ed: 00ee: 00ef: 00f0: 00f1:6e 00f2:6f 00f3:6f 00f4:6f 00f5:6f 00f6:6f 00f8:6f 00f9: 00fa: 00fb: 00fc: 00fd: 00fe: 00ff: (UTF-) (UTF-)
同时,大家,可以去配置文件里看
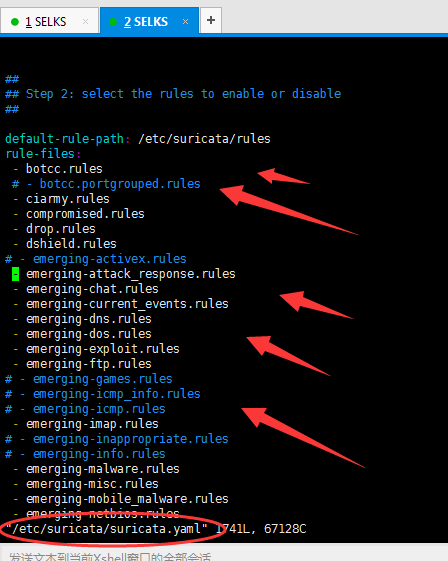
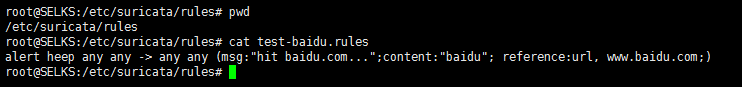
root@SELKS:/etc/suricata/rules# pwd
/etc/suricata/rules
root@SELKS:/etc/suricata/rules# cat test-baidu.rules
alert heep any any -> any any (msg:"hit baidu.com...";content:"baidu"; reference:url, www.baidu.com;)
root@SELKS:/etc/suricata/rules#
然后 ,再启动suricata
注意,SELKS里的suricata启动脚本是在
有兴趣的朋友们,可以跟我这样粘贴出来,研究研究
root@SELKS:/etc/init.d# cat suricata
#!/bin/sh -e
#
### BEGIN INIT INFO
# Provides: suricata
# Required-Start: $time $network $local_fs $remote_fs
# Required-Stop: $remote_fs
# Default-Start:
# Default-Stop:
# Short-Description: Next Generation IDS/IPS
# Description: Intrusion detection system that will
# capture traffic from the network cards and will
# match against a set of known attacks.
### END INIT INFO . /lib/lsb/init-functions # Source function library.
if test -f /etc/default/suricata; then
. /etc/default/suricata
else
echo "/etc/default/suricata is missing... bailing out!"
fi # We'll add up all the options above and use them
NAME=suricata
DAEMON=/usr/bin/$NAME # Use this if you want the user to explicitly set 'RUN' in
# /etc/default/
if [ "x$RUN" != "xyes" ] ; then
log_failure_msg "$NAME disabled, please adjust the configuration to your needs "
log_failure_msg "and then set RUN to 'yes' in /etc/default/$NAME to enable it."
exit
fi check_root() {
if [ "$(id -u)" != "" ]; then
log_failure_msg "You must be root to start, stop or restart $NAME."
exit
fi
} check_nfqueue() {
if [ ! -e /proc/net/netfilter/nf_queue ]; then
log_failure_msg "NFQUEUE support not found !"
log_failure_msg "Please ensure the nfnetlink_queue module is loaded or built in kernel"
exit
fi
} check_run_dir() {
if [ ! -d /var/run/suricata ]; then
mkdir /var/run/suricata
chmod /var/run/suricata
fi
} check_root case "$LISTENMODE" in
nfqueue)
IDMODE="IPS (nfqueue)"
LISTEN_OPTIONS=" $NFQUEUE"
check_nfqueue
;;
pcap)
IDMODE="IDS (pcap)"
LISTEN_OPTIONS=" -i $IFACE"
;;
af-packet)
IDMODE="IDS (af-packet)"
LISTEN_OPTIONS=" --af-packet"
;;
*)
echo "Unsupported listen mode $LISTENMODE, aborting"
exit
;;
esac SURICATA_OPTIONS=" -c $SURCONF --pidfile $PIDFILE $LISTEN_OPTIONS -D -v" # See how we were called.
case "$1" in
start)
if [ -f $PIDFILE ]; then
PID1=`cat $PIDFILE`
if kill - "$PID1" >/dev/null; then
echo "$NAME is already running with PID $PID1"
exit
fi
fi
check_run_dir
if [ -z "$RUN_AS_USER" ]; then
USER_SWITCH=
else
USER_SWITCH=--user=${RUN_AS_USER}
chown ${RUN_AS_USER}:${RUN_AS_USER} /var/run/suricata
fi
echo -n "Starting suricata in $IDMODE mode..."
if [ -f /usr/lib/libtcmalloc_minimal.so. ] && [ "x$TCMALLOC" = "xYES" ]; then
export LD_PRELOAD="/usr/lib/libtcmalloc_minimal.so.0"
#echo "Using googles tcmalloc for minor performance boost!?!"
fi
$DAEMON $SURICATA_OPTIONS $USER_SWITCH > /var/log/suricata/suricata-start.log >& &
echo " done."
;;
stop)
echo -n "Stopping suricata: "
if [ -f $PIDFILE ]; then
PID2=`cat $PIDFILE`
else
echo " No PID file found; not running?"
exit ;
fi
start-stop-daemon --oknodo --stop --quiet --pidfile=$PIDFILE --exec $DAEMON
if [ -n "$PID2" ]; then
kill "$PID2"
ret=$?
sleep
if kill - "$PID2" >/dev/null; then
ret=$?
echo -n "Waiting . "
cnt=
while kill - "$PID2" >/dev/null; do
ret=$?
cnt=`expr "$cnt" + `
if [ "$cnt" -gt ]; then
kill - "$PID2"
break
fi
sleep
echo -n ". "
done
fi
fi
if [ -e $PIDFILE ]; then
rm $PIDFILE > /dev/null >&
fi
echo " done."
;;
status)
# Check if running...
if [ -s $PIDFILE ]; then
PID3=`cat $PIDFILE`
if kill - "$PID3" >/dev/null; then
echo "$NAME is running with PID $PID3"
exit
else
echo "PID file $PIDFILE exists, but process not running!"
fi
else
echo "$NAME not running!"
fi
;;
restart)
$ stop
$ start
;;
force-reload)
$ stop
$ start
;;
*)
echo "Usage: $0 {start|stop|restart|status}"
exit
esac exit
root@SELKS:/etc/init.d#
然而,我们需要如下来启动
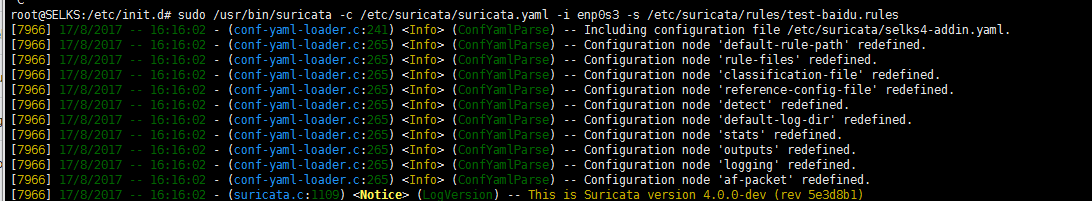
root@SELKS:/etc/init.d# sudo /usr/bin/suricata -c /etc/suricata/suricata.yaml -i enp0s3 -s /etc/suricata/rules/test-baidu.rules
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Including configuration file /etc/suricata/selks4-addin.yaml.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'default-rule-path' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'rule-files' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'classification-file' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'reference-config-file' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'detect' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'default-log-dir' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'stats' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'outputs' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'logging' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'af-packet' redefined.
[] // -- :: - (suricata.c:) <Notice> (LogVersion) -- This is Suricata version 4.0.-dev (rev 5e3d8b1)
或者这么来写自定义规则(为了遵循官网的习惯,命名为local.rules)
见官网
https://suricata.readthedocs.io/en/latest/rule-management/adding-your-own-rules.html
比如
alert http any any -> any any (msg:"Do not read gossip during work";
content:"Scarlett"; nocase; classtype:policy-violation; sid:; rev:;)
然后,还要将自定义规则文件,加载到配置文件里

然后,执行
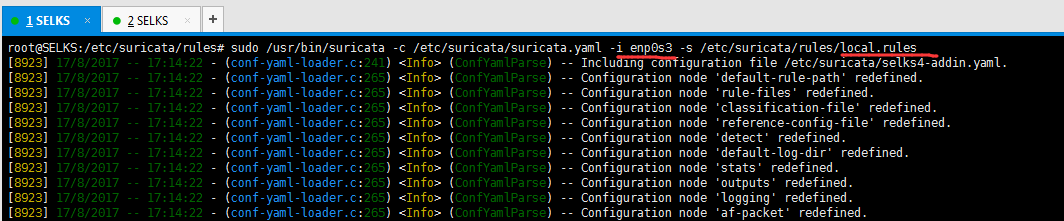
root@SELKS:/etc/suricata/rules# sudo /usr/bin/suricata -c /etc/suricata/suricata.yaml -i enp0s3 -s /etc/suricata/rules/local.rules
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Including configuration file /etc/suricata/selks4-addin.yaml.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'default-rule-path' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'rule-files' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'classification-file' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'reference-config-file' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'detect' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'default-log-dir' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'stats' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'outputs' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'logging' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'af-packet' redefined.
[] // -- :: - (suricata.c:) <Notice> (LogVersion) -- This is Suricata version 4.0.-dev (rev 5e3d8b1)
或者这么来写自定义规则(模拟产生更多的数据)
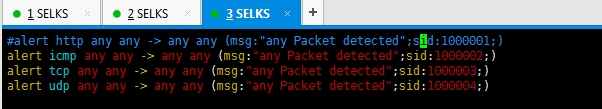
root@SELKS:/etc/suricata/rules# cat local.rules
#alert http any any -> any any (msg:"any Packet detected";sid:;)
alert icmp any any -> any any (msg:"any Packet detected";sid:;)
alert tcp any any -> any any (msg:"any Packet detected";sid:;)
alert udp any any -> any any (msg:"any Packet detected";sid:;)
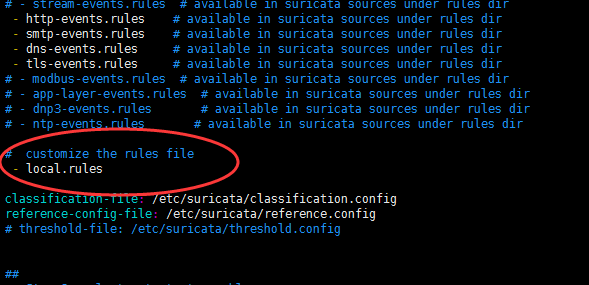
然后,执行
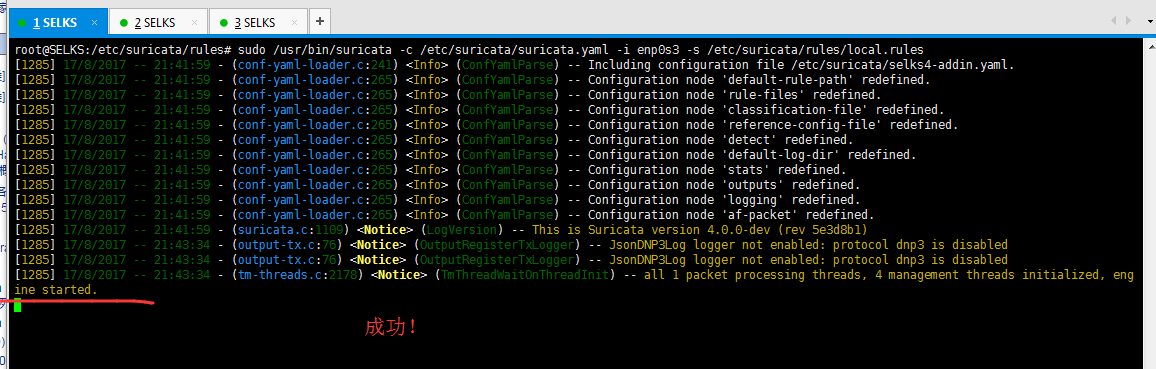
root@SELKS:/etc/suricata/rules# sudo /usr/bin/suricata -c /etc/suricata/suricata.yaml -i enp0s3 -s /etc/suricata/rules/local.rules
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Including configuration file /etc/suricata/selks4-addin.yaml.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'default-rule-path' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'rule-files' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'classification-file' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'reference-config-file' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'detect' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'default-log-dir' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'stats' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'outputs' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'logging' redefined.
[] // -- :: - (conf-yaml-loader.c:) <Info> (ConfYamlParse) -- Configuration node 'af-packet' redefined.
[] // -- :: - (suricata.c:) <Notice> (LogVersion) -- This is Suricata version 4.0.-dev (rev 5e3d8b1)
[] // -- :: - (output-tx.c:) <Notice> (OutputRegisterTxLogger) -- JsonDNP3Log logger not enabled: protocol dnp3 is disabled
[] // -- :: - (output-tx.c:) <Notice> (OutputRegisterTxLogger) -- JsonDNP3Log logger not enabled: protocol dnp3 is disabled
[] // -- :: - (tm-threads.c:) <Notice> (TmThreadWaitOnThreadInit) -- all packet processing threads, management threads initialized, engine started.
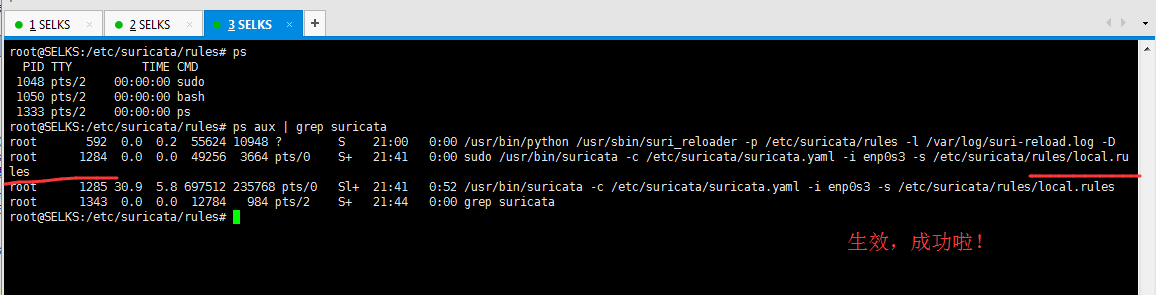
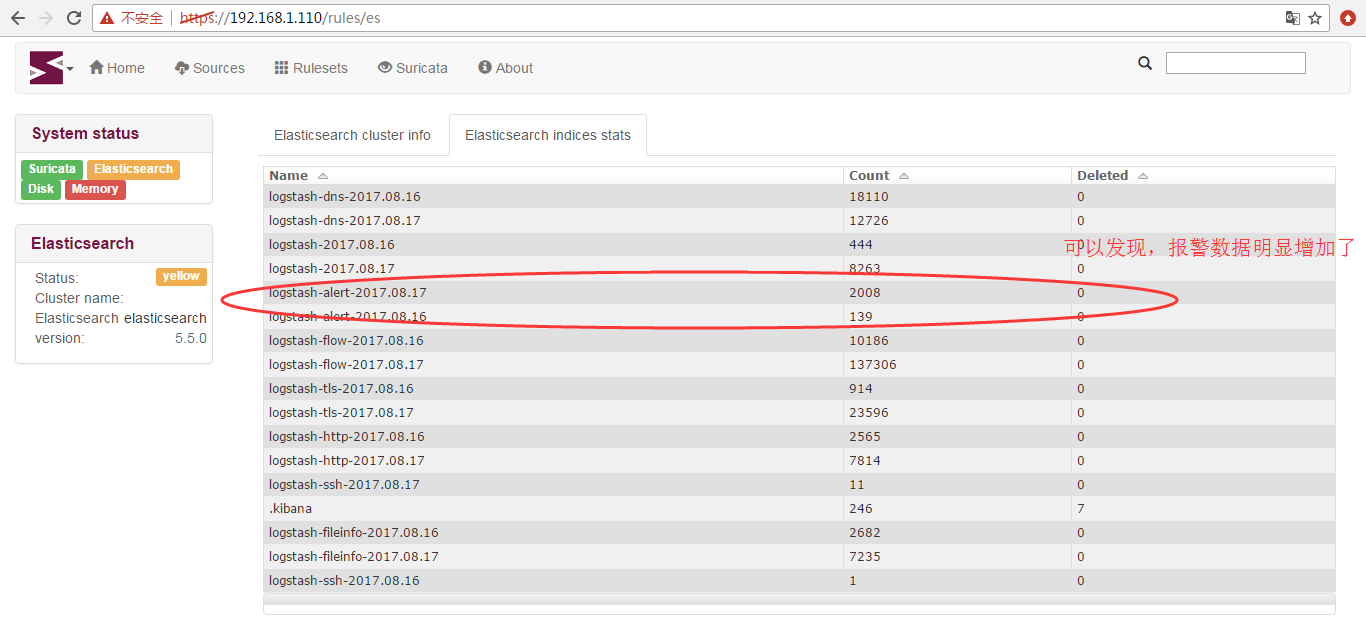
Suricata的规则解读(默认和自定义)的更多相关文章
- Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库之后的切换到指定的工作空间
不多说,直接上干货! 为什么要这么做? 答: 方便我们将扫描不同的目标或目标的不同段,进行归类.为了更好的后续工作! 前期博客 Kali linux 2016.2(Rolling)里Metasploi ...
- WordPress发布文章/页面时自动添加默认的自定义字段
如果你每篇文章或页面都需要插入同一个自定义字段和值,可以考虑在WordPress发布文章/页面时,自动添加默认的自定义字段.将下面的代码添加到当前主题的 functions.php 即可: 1 2 3 ...
- 建立标准编码规则(一)-自定义C#代码分析器
1.下载Roslyn的Visual Studio分析器模板插件(VS2015 或VS2017) https://marketplace.visualstudio.com/items?itemName= ...
- 20. Spring Boot 默认、自定义数据源 、配置多个数据源 jdbcTemplate操作DB
Spring-Boot-2.0.0-M1版本将默认的数据库连接池从tomcat jdbc pool改为了hikari,这里主要研究下hikari的默认配置 0. 创建Spring Boot项目,选中 ...
- Cognos开发自定义排序规则的报表和自定义排名报表
场景:有一个简单的销售数据分析,可以按照日期,按照商品类型来分析订单笔数和订单金额. 目的:用户可以自定义查看按照不同指标排序的数据,用户可以查看按照不同指标排名的前N名数据 一:功能及效果展示 效果 ...
- VISIO 2007 修改形状默认字体 自定义模具
visio 2007的形状的默认字体为8号,比较小,怎样改成默认10号? 首先将一个流程图中所要用的形状都拖到绘图区,然后全选,设置字体为10号,全选,再拖动到形状区,如下图: 点击‘是’,确认修改模 ...
- 利用Sonar定制自定义JS扫描规则(二)——自定义JS扫描规则
在上一篇blog中,我们将sonar几个需要的环境都搭建好了,包括sonar的服务器,sonar runner,sonar的javascript插件.现在我们就来讲如何自定义JS扫描规则. 实际上有3 ...
- java编程排序之内置引用类型的排序规则实现,和自定义规则实现+冒泡排序运用
第一种排序:[冒泡排序]基本数据类型的排序. [1]最简易的冒泡排序.效率低.因为比较的次数和趟数最多. /** * 最原始的冒泡排序. * 效率低. * 因为趟数和次数最多.都是按最大化的循环次数进 ...
- Spring data JPA 理解(默认查询 自定义查询 分页查询)及no session 三种处理方法
简介:Spring Data JPA 其实就是JDK方式(还有一种cglib的方式需要Class)的动态代理 (需要一个接口 有一大堆接口最上边的是Repository接口来自org.springfr ...
随机推荐
- Deep Learning 33:读论文“Densely Connected Convolutional Networks”-------DenseNet 简单理解
一.读前说明 1.论文"Densely Connected Convolutional Networks"是现在为止效果最好的CNN架构,比Resnet还好,有必要学习一下它为什么 ...
- (23) java web的struts2框架的使用-struts动态调用和通配符
一,动态查找 1,配置允许动态调用 <!-- 允许动态方法调用 --> <constant name="struts.enable.DynamicMethodInvocat ...
- EventStore文件存储设计
背景 ENode是一个CQRS+Event Sourcing架构的开发框架,Event Sourcing需要持久化事件,事件可以持久化在DB,但是DB由于面向的是CRUD场景,是针对数据会不断修改或删 ...
- (C)strcpy ,strncpy与strlcpy
1. 背景 好多人已经知道利用strncpy替代strcpy来防止缓冲区越界. 但是如果还要考虑运行效率的话,也许strlcpy是一个更好的方式. 2. strcpy strcpy 是依据 /0 作为 ...
- CSS中的那点事儿(一)--- CSS中的单位2
在上篇博客提到了%.px.em三个单位,其中最复杂的是em,因为要计算当前元素内的font-size,必须知道其父元素的font-size,层层累积,容易出错.现在CSS3中引入了新的单位rem,改变 ...
- POJ1077 Eight —— 反向BFS
主页面:http://www.cnblogs.com/DOLFAMINGO/p/7538588.html 代码一:以数组充当队列,利用结构体中的pre追溯上一个状态在数组(队列)中的下标: #incl ...
- MYSQL进阶学习笔记五:MySQL函数的创建!(视频序号:进阶_13)
知识点六:MySQL函数的创建(13) 内置函数: 自定义函数: 首先查看是否已经开启了创建函数的功能: SHOW VARIABLES LIKE ‘%fun%’; 如果变量的值是OFF,那么需要开启 ...
- android之View坐标系(view获取自身坐标的方法和点击事件中坐标的获取)
在做一个view背景特效的时候被坐标的各个获取方法搞晕了,几篇抄来抄去的博客也没弄很清楚. 现在把整个总结一下. 其实只要把下面这张图看明白就没问题了. 涉及到的方法一共有下面几个: view获取自身 ...
- 一步一步学Silverlight 2系列(23):Silverlight与HTML混合之无窗口模式
概述 Silverlight 2 Beta 1版本发布了,无论从Runtime还是Tools都给我们带来了很多的惊喜,如支持框架语言Visual Basic, Visual C#, IronRuby, ...
- skynet源码阅读<4>--定时器实现
昨天和三石公聊天,他提到timer的实现原理,我当时迟疑了一下,心想timer不是系统底层时钟中断驱动上层进程/线程,累积计时实现的么?他简述了timer的实现,什么堆排序,优先级队列等,与我想象的不 ...
