攻防世界 reverse secret-string-400
secret-string-400 school-ctf-winter-2015
解压文件得到html和js文件
Task.html
<html>
<head>
<title>JSMachine</title>
<meta charset="UTF-8">
<script type='text/javascript' src='Machine.js'></script>
</head>
<body>
<h1>Secret key</h1><br/>
<h2>Test your luck! Enter valid string and you will know flag!</h2><br/>
<input type='text'></input><br/>
<br/>
<input type='button' onclick="check()" value='Проверить'></button>
</body>
</html>
Machine.js
function createRegisters(obj){
obj.registers = [];
for(i=0; i < 256; ++i){
obj.registers.push(0);
}
};
function Machine() {
createRegisters(this);
this.code = [0]
this.PC = 0;
this.callstack = [];
this.pow = Math.pow(2,32)
};
Machine.prototype = {
opcodesCount: 16,
run: run,
loadcode: function(code){this.code = code},
end: function(){this.code=[]}
};
function run(){
while(this.PC < this.code.length){
var command = parseCommand.call(this);
command.execute(this);
}
//this.end()
}
function getOpcodeObject(){
var opNum = (this.code[this.PC] % this.opcodesCount);
this.PC += 1;
return eval('new Opcode'+opNum);
}
function parseCommand(){
var opcode = getOpcodeObject.call(this);
opcode.consumeArgs(this);
return opcode;
}
var opcCreate = "";
for(i=0;i<16;++i){
opcCreate += "function Opcode"+i+"(){this.args=[]}\n";
}
eval(opcCreate);
function makeFromImm(obj) {
var res = obj.code[obj.PC + 2];
res <<=8;
res += obj.code[obj.PC + 1];
res <<=8;
res += obj.code[obj.PC];
res <<=8;
res += obj.code[obj.PC+3];
res = res >>> 0;
return res;
}
function getRegImm(obj){
this.args[0] = obj.code[obj.PC];
obj.PC += 1;
this.args[1] = makeFromImm(obj);
obj.PC += 4;
}
function getImm(obj){
this.args[0] = makeFromImm(obj);
obj.PC += 4;
}
function getTwoRegs(obj){
this.args[0] = obj.code[obj.PC];
obj.PC += 1;
this.args[1] = obj.code[obj.PC];
obj.PC += 1;
}
function getThreeRegs(obj){
this.args[0] = obj.code[obj.PC];
obj.PC += 1;
this.args[1] = obj.code[obj.PC];
obj.PC += 1;
this.args[2] = obj.code[obj.PC];
obj.PC += 1;
}
function getRegString(obj){
this.args[0] = obj.code[obj.PC];
obj.PC += 1;
this.args[1] = getString(obj);
}
function getRegRegString(obj){
this.args[0] = obj.code[obj.PC];
obj.PC += 1;
this.args[1] = obj.code[obj.PC];
obj.PC += 1;
this.args[2] = getString(obj);
}
function getRegTwoString(obj){
this.args[0] = obj.code[obj.PC];
obj.PC += 1;
this.args[1] = getString(obj);
this.args[2] = getString(obj);
}
function getString(obj){
var res = "";
while(obj.code[obj.PC] != 0) {
res += String.fromCharCode(obj.code[obj.PC]);
obj.PC += 1;
}
obj.PC += 1;
return res;
}
Opcode0.prototype = {
consumeArgs : function(obj){},
execute: function(){}
};
Opcode1.prototype = {
consumeArgs: getRegImm,
execute: function(obj){
obj.registers[this.args[0]] = (obj.registers[this.args[0]] + this.args[1]) % 0x100000000;
}
}
Opcode2.prototype = {
consumeArgs: getTwoRegs,
execute: function(obj){
obj.registers[this.args[0]] = (obj.registers[this.args[0]] + obj.registers[this.args[1]]) % 0x100000000;
}
}
Opcode3.prototype = {
consumeArgs: getRegImm,
execute: function(obj){
obj.registers[this.args[0]] = ((obj.registers[this.args[0]] - this.args[1]) % 0x100000000) >>> 0;
}
}
Opcode4.prototype = {
consumeArgs: getTwoRegs,
execute: function(obj){
obj.regsiters[this.args[0]] = ((obj.registers[this.args[0]] - this.registers[this.args[1]])%100000000) >>> 0
}
}
Opcode5.prototype = {
consumeArgs: getThreeRegs,
execute: function(obj){
var mult = obj.registers[this.args[0]] * obj.registers[this.args[1]];
console.log(mult.toString(16));
obj.registers[this.args[2]] = (mult / obj.pow) >>> 0;
obj.registers[this.args[2]+1] = (mult & 0xffffffff) >>> 0;
}
}
Opcode6.prototype = {
consumeArgs: getThreeRegs,
execute: function(obj){
var divs = obj.registers[this.args[0]] * obj.pow + obj.registers[this.args[0]+1];
obj.registers[this.args[2]] = (divs / obj.registers[this.args[1]]) >>> 0;
obj.registers[this.args[2]+1]= (divs % obj.registers[this.args[1]]) >>> 0;
}
}
Opcode7.prototype = {
consumeArgs: getRegImm,
execute: function(obj) {
obj.registers[this.args[0]] = this.args[1];
}
}
Opcode8.prototype = {
consumeArgs: getImm,
execute: function(obj){
obj.callstack.push(obj.PC);
obj.PC = this.args[0];
}
}
Opcode9.prototype = {
consumeArgs: getImm,
execute: function(obj){
obj.PC = (obj.PC + this.args[0]) % obj.code.length;
}
}
Opcode10.prototype = {
consumeArgs: function(){},
execute: function(obj){
obj.PC = obj.callstack.pop();
}
}
Opcode11.prototype = {
consumeArgs: getRegString,
execute: function(obj){
obj.registers[this.args[0]] = eval('new '+this.args[1]);
}
}
Opcode12.prototype = {
consumeArgs: getRegTwoString,
execute: function(obj){
obj.registers[this.args[0]][this.args[1]] = Function(this.args[2]);
}
}
Opcode13.prototype = {
consumeArgs: getRegRegString,
execute: function(obj){
obj.registers[this.args[0]] = obj.registers[this.args[1]][this.args[2]];
}
}
Opcode14.prototype = {
consumeArgs: getRegRegString,
execute: function(obj){
obj.registers[this.args[1]][this.args[2]] = obj.registers[this.args[0]];
}
}
Opcode15.prototype = {
consumeArgs: getRegRegString,
execute: function(obj){
obj.registers[this.args[0]] = obj.registers[this.args[1]][this.args[2]]();
}
}
function check(){
machine = new Machine;
machine.loadcode([11, 1, 79, 98, 106, 101, 99, 116, 0, 12, 1, 120, 0, 114, 101, 116, 117, 114, 110, 32, 100, 111, 99, 117, 109, 101, 110, 116, 46, 103, 101, 116, 69, 108, 101, 109, 101, 110, 116, 115, 66, 121, 84, 97, 103, 78, 97, 109, 101, 40, 39, 105, 110, 112, 117, 116, 39, 41, 91, 48, 93, 46, 118, 97, 108, 117, 101, 47, 47, 0, 15, 3, 1, 120, 0, 14, 3, 1, 117, 115, 101, 114, 105, 110, 112, 117, 116, 0, 12, 1, 121, 0, 119, 105, 110, 100, 111, 119, 46, 109, 97, 99, 104, 105, 110, 101, 46, 101, 110, 100, 32, 61, 32, 102, 117, 110, 99, 116, 105, 111, 110, 40, 41, 123, 116, 104, 105, 115, 46, 99, 111, 100, 101, 61, 91, 93, 59, 116, 104, 105, 115, 46, 80, 67, 61, 49, 55, 51, 125, 47, 47, 0, 15, 3, 1, 121, 0, 12, 1, 122, 0, 97, 108, 101, 114, 116, 40, 49, 41, 59, 47, 47, 11, 234, 79, 98, 106, 101, 99, 116, 255, 9, 255, 255, 255, 12, 10, 97, 108, 101, 114, 116, 40, 50, 41, 59, 47, 47, 12, 234, 120, 255, 118, 97, 114, 32, 102, 61, 119, 105, 110, 100, 111, 119, 46, 109, 97, 99, 104, 105, 110, 101, 46, 114, 101, 103, 105, 115, 116, 101, 114, 115, 91, 49, 93, 46, 117, 115, 101, 114, 105, 110, 112, 117, 116, 47, 47, 10, 118, 97, 114, 32, 105, 32, 61, 32, 102, 46, 108, 101, 110, 103, 116, 104, 47, 47, 10, 118, 97, 114, 32, 110, 111, 110, 99, 101, 32, 61, 32, 39, 103, 114, 111, 107, 101, 39, 59, 47, 47, 10, 118, 97, 114, 32, 106, 32, 61, 32, 48, 59, 47, 47, 10, 118, 97, 114, 32, 111, 117, 116, 32, 61, 32, 91, 93, 59, 47, 47, 10, 118, 97, 114, 32, 101, 113, 32, 61, 32, 116, 114, 117, 101, 59, 47, 47, 10, 119, 104, 105, 108, 101, 40, 106, 32, 60, 32, 105, 41, 123, 47, 47, 10, 111, 117, 116, 46, 112, 117, 115, 104, 40, 102, 46, 99, 104, 97, 114, 67, 111, 100, 101, 65, 116, 40, 106, 41, 32, 94, 32, 110, 111, 110, 99, 101, 46, 99, 104, 97, 114, 67, 111, 100, 101, 65, 116, 40, 106, 37, 53, 41, 41, 47, 47, 10, 106, 43, 43, 59, 47, 47, 10, 125, 47, 47, 10, 118, 97, 114, 32, 101, 120, 32, 61, 32, 32, 91, 49, 44, 32, 51, 48, 44, 32, 49, 52, 44, 32, 49, 50, 44, 32, 54, 57, 44, 32, 49, 52, 44, 32, 49, 44, 32, 56, 53, 44, 32, 55, 53, 44, 32, 53, 48, 44, 32, 52, 48, 44, 32, 51, 55, 44, 32, 52, 56, 44, 32, 50, 52, 44, 32, 49, 48, 44, 32, 53, 54, 44, 32, 53, 53, 44, 32, 52, 54, 44, 32, 53, 54, 44, 32, 54, 48, 93, 59, 47, 47, 10, 105, 102, 32, 40, 101, 120, 46, 108, 101, 110, 103, 116, 104, 32, 61, 61, 32, 111, 117, 116, 46, 108, 101, 110, 103, 116, 104, 41, 32, 123, 47, 47, 10, 106, 32, 61, 32, 48, 59, 47, 47, 10, 119, 104, 105, 108, 101, 40, 106, 32, 60, 32, 101, 120, 46, 108, 101, 110, 103, 116, 104, 41, 123, 47, 47, 10, 105, 102, 40, 101, 120, 91, 106, 93, 32, 33, 61, 32, 111, 117, 116, 91, 106, 93, 41, 47, 47, 10, 101, 113, 32, 61, 32, 102, 97, 108, 115, 101, 59, 47, 47, 10, 106, 32, 43, 61, 32, 49, 59, 47, 47, 10, 125, 47, 47, 10, 105, 102, 40, 101, 113, 41, 123, 47, 47, 10, 97, 108, 101, 114, 116, 40, 39, 89, 79, 85, 32, 87, 73, 78, 33, 39, 41, 59, 47, 47, 10, 125, 101, 108, 115, 101, 123, 10, 97, 108, 101, 114, 116, 40, 39, 78, 79, 80, 69, 33, 39, 41, 59, 10, 125, 125, 101, 108, 115, 101, 123, 97, 108, 101, 114, 116, 40, 39, 78, 79, 80, 69, 33, 39, 41, 59, 125, 47, 47, 255, 9, 255, 255, 255, 12, 10, 97, 108, 101, 114, 116, 40, 51, 41, 59, 47, 47, 15, 1, 234, 120, 255, 9, 255, 255, 255, 12, 10, 97, 108, 101, 114, 116, 40, 52, 41, 59, 47, 47, 10, 97, 108, 101, 114, 116, 40, 53, 41, 59, 47, 47, 10, 97, 108, 101, 114, 116, 40, 54, 41, 59, 47, 47, 10, 97, 108, 101, 114, 116, 40, 55, 41, 59, 47, 47, 0, 12, 1, 103, 0, 118, 97, 114, 32, 105, 32, 61, 48, 59, 119, 104, 105, 108, 101, 40, 105, 60, 119, 105, 110, 100, 111, 119, 46, 109, 97, 99, 104, 105, 110, 101, 46, 99, 111, 100, 101, 46, 108, 101, 110, 103, 116, 104, 41, 123, 105, 102, 40, 119, 105, 110, 100, 111, 119, 46, 109, 97, 99, 104, 105, 110, 101, 46, 99, 111, 100, 101, 91, 105, 93, 32, 61, 61, 32, 50, 53, 53, 32, 41, 32, 119, 105, 110, 100, 111, 119, 46, 109, 97, 99, 104, 105, 110, 101, 46, 99, 111, 100, 101, 91, 105, 93, 32, 61, 32, 48, 59, 105, 43, 43, 125, 47, 47, 0, 12, 1, 104, 0, 119, 105, 110, 100, 111, 119, 46, 109, 97, 99, 104, 105, 110, 101, 46, 80, 67, 61, 49, 55, 50, 47, 47, 0, 15, 0, 1, 103, 0, 15, 0, 1, 104, 0])
machine.run();
}
修改js文件,添加打印输出
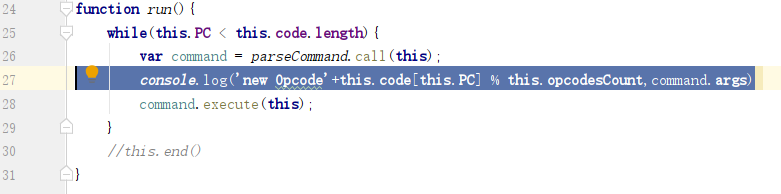
运行html
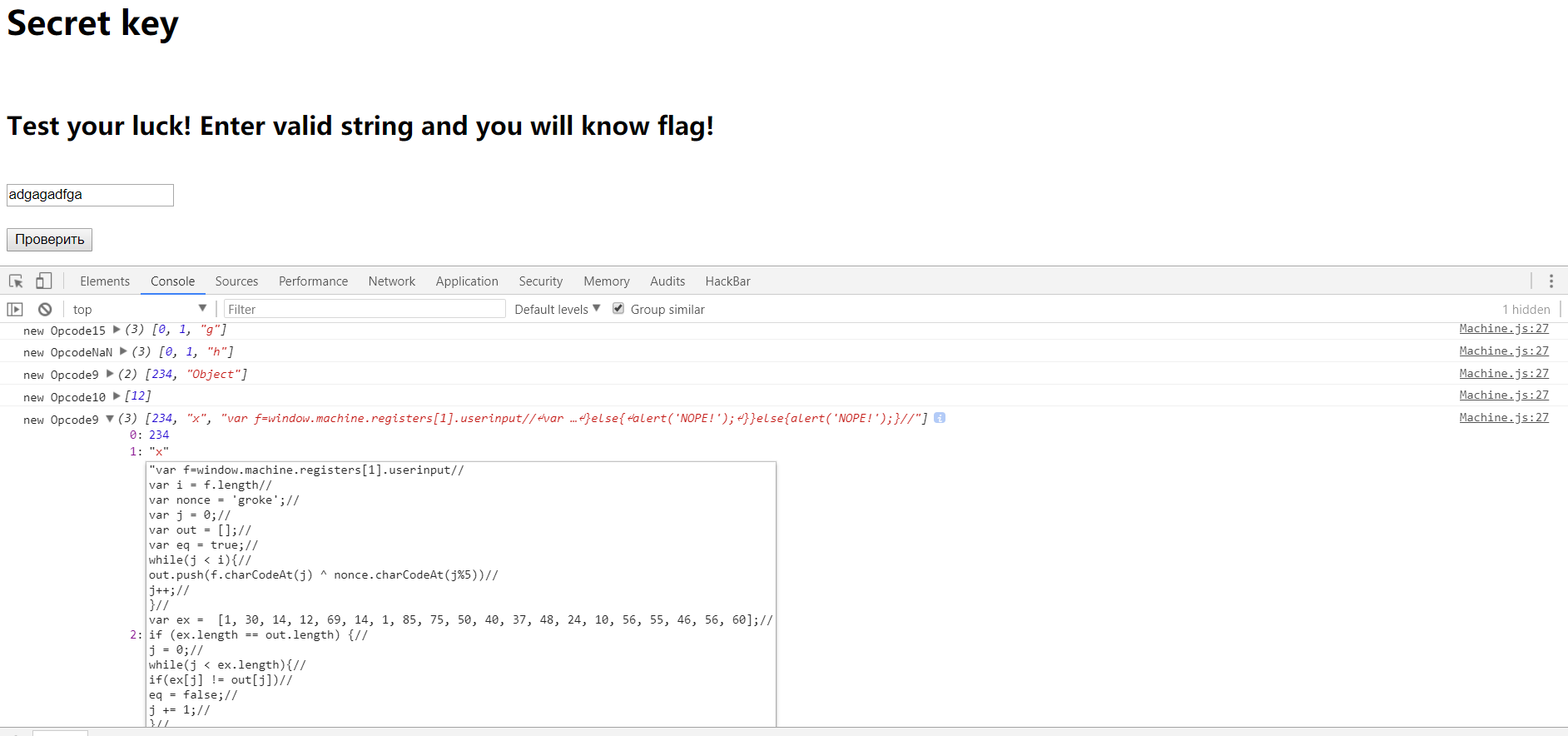
找到关键代码
1 var f=window.machine.registers[1].userinput//
2 var i = f.length//
3 var nonce = 'groke';//
4 var j = 0;//
5 var out = [];//
6 var eq = true;//
7 while(j < i){//
8 out.push(f.charCodeAt(j) ^ nonce.charCodeAt(j%5))//
9 j++;//
10 }//
11 var ex = [1, 30, 14, 12, 69, 14, 1, 85, 75, 50, 40, 37, 48, 24, 10, 56, 55, 46, 56, 60];//
12 if (ex.length == out.length) {//
13 j = 0;//
14 while(j < ex.length){//
15 if(ex[j] != out[j])//
16 eq = false;//
17 j += 1;//
18 }//
19 if(eq){//
20 alert('YOU WIN!');//
21 }else{
22 alert('NOPE!');
23 }}else{alert('NOPE!');}//
wp
ex = [1, 30, 14, 12, 69, 14, 1, 85, 75, 50, 40, 37, 48, 24, 10, 56, 55, 46, 56, 60];
nonce = 'groke';
flag=''
for i in range(len(ex)):
flag+=chr(ex[i]^ord(nonce[i%5]))
print(flag)
flag is: WOW_so_EASY
攻防世界 reverse secret-string-400的更多相关文章
- 攻防世界 reverse 进阶 APK-逆向2
APK-逆向2 Hack-you-2014 (看名以为是安卓逆向呢0.0,搞错了吧) 程序是.net写的,直接祭出神器dnSpy 1 using System; 2 using System.Diag ...
- 攻防世界 reverse 进阶 10 Reverse Box
攻防世界中此题信息未给全,题目来源为[TWCTF-2016:Reverse] Reverse Box 网上有很多wp是使用gdb脚本,这里找到一个本地还原关键算法,然后再爆破的 https://www ...
- 攻防世界 reverse evil
这是2017 ddctf的一道逆向题, 挑战:<恶意软件分析> 赛题背景: 员工小A收到了一封邮件,带一个文档附件,小A随手打开了附件.随后IT部门发现小A的电脑发出了异常网络访问请求,进 ...
- 攻防世界 reverse tt3441810
tt3441810 tinyctf-2014 附件给了一堆数据,将十六进制数据部分提取出来, flag应该隐藏在里面,(这算啥子re,) 保留可显示字符,然后去除填充字符(找规律 0.0) 处理脚本: ...
- 攻防世界 reverse leaked-license-64
mark一下,以后分析 原文:http://sibears.ru/labs/ASIS-CTF-Quals-2016-Leaked_License/ [ASIS CTF Quals 2016] - 泄露 ...
- 攻防世界 reverse Windows_Reverse2
Windows_Reverse2 2019_DDCTF 查壳: 寻找oep-->dump-->iat修复 便可成功脱壳 int __cdecl main(int argc, con ...
- 攻防世界 reverse easy_Maze
easy_Maze 从题目可得知是简单的迷宫问题 int __cdecl main(int argc, const char **argv, const char **envp) { __int64 ...
- 攻防世界 reverse BabyXor
BabyXor 2019_UNCTF 查壳 脱壳 dump 脱壳后 IDA静态分析 int main_0() { void *v0; // eax int v1; // ST5C_4 char ...
- 攻防世界 reverse Guess-the-Number
Guess-the-Number su-ctf-quals-2014 使用jd-gui 反编译jar import java.math.BigInteger; public class guess ...
随机推荐
- Watch the Wifi: Visually Stunning Look at the Digital World Invading Cities (video)
http://singularityhub.com/2011/04/01/watch-the-wifi-visually-stunning-look-at-the-digital-world-inva ...
- Axios 取消 Ajax 请求
Axios 取消 Ajax 请求 Axios XMLHttpRequest https://caniuse.com/?search=XMLHttpRequest https://developer.m ...
- Chrome DevTools & Slow 3G Network
Chrome DevTools & Slow 3G Network shortcuts https://developers.google.com/web/tools/chrome-devto ...
- server sent events
server sent events server push https://html5doctor.com/server-sent-events/ https://developer.mozilla ...
- Nodejs file path to url path
import * as path from 'path'; import * as url from 'url'; const savePath = path.join('public', 'imag ...
- 应该如何看待VAST的未来价格与价值?
提起数字货币的价格,很多币圈人士都是滔滔不绝,随口一举例,便是百倍千倍的数字货币.可是提起数字货币的价值,就很少有币圈人士能举出几个有力的例子,常常顾左右而言他,场面十分尴尬.之所以会这样,是因为很多 ...
- 「NGK每日快讯」2021.1.21日NGK公链第79期官方快讯!
- Chateau Renice酒庄 :忠于风味,尊重自然
Chateau Renice酒庄(公司编号:20151318780)凭借优良的葡萄栽培传统.卓越的酿酒技术以及独特风味的葡萄酒,近年来葡萄酒畅销至全球. Chateau Renice酒庄将葡萄酒出口至 ...
- Markdown简单语法的使用
Markdown简单语法的使用 目录 Markdown简单语法的使用 前言 标题的设置 字体的设置 1.字体加粗 2.斜体 3.字体加粗斜体 3.删除线 引用 列表的使用 插入图片 分割线 代码的书写 ...
- django学习-6.模板templates
1.前言 首先,我们要知道html是一门静态语言,里面没法传一些动态参数,也就是一个写死的html页面. 那么,如果我们想实现在一个html页面里传入不同的参数对应的参数值,这就可以用django框架 ...
