Understanding about numerical stability, convergence and consistency
In a computer simulation of the real world, physical quantities, which usually have continuous distributions governed by partial differential equations (PDEs), can be solved by numerical methods such as finite element method (FEM) and boundary element method (BEM). Whether the obtained solution is a good approximation of the reality and whether the numerical schemes can proceed properly under perturbations of different error sources, such as numerical quadrature error and round-off error, should be clarified before any code implementation. To answer these questions, this post will introduce the fundamental concepts of numerical stability, convergence and consistency according to the following figure.
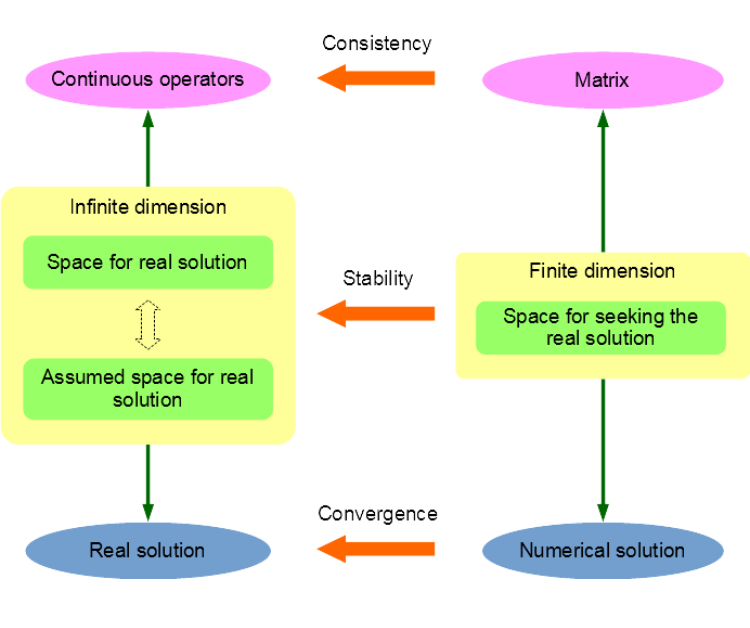
Let \(u\) be the real solution of the following general variational problem for a PDE:
\[
\text{Solve $u \in U$: } a(u, v) = (f, v) \quad (\forall v \in W),
\]
where both \(U\) and \(W\) are Hilbert spaces, \(a(\cdot, \cdot): U \times W \rightarrow \mathbb{K}\) with \(\mathbb{K} \in \{\mathbb{R}, \mathbb{C}\}\) is a sesquilinear or bilinear form and \(f: W \rightarrow \mathbb{K}\) is a continuous linear functional on \(W\). The solution \(u\) belongs to the space \(U\) of continuous functions with infinite dimension. For ease of further analysis, priori assumption is usually adopted for such function space thus we have the assumed function space \(V\). For example, the countably normed spaces \(V = B_{\varrho}(\Gamma)\) used in the \(hp\)-BEM is defined as
\[
B_{\varrho}(\Gamma) = \{ v \in L^2(\Gamma): v \circ \kappa_K \in B_{\varrho}(K_0) \},
\]
where
- \(\Gamma\) is the boundary manifold of the solution domain, which is covered by the mesh \(\{K_i\}_{i=1}^{N_M}\) with \(N_M\) as the number of mesh elements;
- \(K_0\) is the reference cell and \(K\) is the real cell which may be curved;
- \(\kappa_K: K_0 \rightarrow K\) is the mapping from the reference cell to the real cell;
- \(B_{\varrho}(K_0)\) is the countably normed space restricted on the reference cell, which has constraints on the norm of all the derivatives of \(v\). Its formulation is given as below:
\[
B_{\varrho}(K_0) = \big\{ v \in L^2(K_0): \Norm{r_X^{k - \varrho} \left( \Pd{}{r_X} \right)^k \left( \vartheta (\alpha_X - \vartheta_X) \right)^{l - \varrho} \left( \Pd{}{\vartheta_X} \right)^l v}_{L^2(U_X)} \leq C d^{k+l+1} k! l!\big\},
\]
for which I do not provide more explanation in this post, but just give you an impression that the construction of the assumed solution function space can be quite complicated.
To solve the PDE on a computer, a finite dimensional subspace \(V^L\) of \(V\) must be constructed, in which a solution is to be sought as an approximation of the real solution by using some sort of numerical method. Then the stability condition means, for any function \(u\) in the real space \(U\) or the assumed space \(V\) of infinite dimension, whether there exists a function \(v\) in the finite dimensional space \(V^L\), such that the norm of their difference can be controlled to be arbitrarily small as \(N_L\), the dimension of space \(V^L\), increases. For example, in the \(hp\)-BEM, a subspace \(V^L\) can be constructed to have the following exponential stability condition:
\[
\begin{equation}
\label{eq:stability-condition}
\forall u \in B_{\varrho}(\Gamma): \inf_{v \in V^L} \norm{u - v}_{L^2(\Gamma)} \leq C \exp(-b N_L^{1/4}).
\end{equation}
\]
Once the solution \(u^L \in V^L\) for the finite dimensional problem is obtained from a general method such as the Galerkin method, i.e.
\[
\text{Solve $u^L \in V^L$: } a(u^L, v) = (f, v) \quad (\forall v \in V^L),
\]
the concept of convergence comes into play, which ensures that the difference between this \(u^L\) and the real solution \(u\) can be controlled. For example, if the following condition can be satisfied:
\[
\Norm{P_L A u^L} \geq C_s \Norm{u^L} \quad (\forall u^L \in V^L),
\]
where \(P_L: V \rightarrow V^L\) is the projection operator, \(A: V^L \rightarrow (V^L)'\) is the associated operator of the sesquilinear or bilinear form \(a(\cdot, \cdot)\) and \(C_s > 0\) is a constant, it can be proved that the solution obtained from the Galerkin method satisfies
\[
\begin{equation}
\label{eq:convergence-condition}
\norm{u - u^L} \leq C \inf_{v \in V^L} \Norm{u - v}.
\end{equation}
\]
This means the real solution can be properly approximated by the Galerkin solution with the error norm controlled by the approximation capability of the adopted finite dimensional space \(V^L\), and we say the method is convergent. In addition, combing equation \eqref{eq:stability-condition} and \eqref{eq:convergence-condition}, we know the solution has the exponential convergence property:
\[
\begin{equation}
\label{eq:exponential-convergence}
\norm{u - u^L} \leq C \exp(-b N_L^{1/4}).
\end{equation}
\]
Finally, we introduce the concept of consistency. During the discretization of the problem, the sesquilinear or bilinear form \(a(\cdot, \cdot)\), or rather, its associated operator \(A\), is to be approximated by its discrete version, i.e. the stiffness matrix \(A^L\). The evaluation of \(A^L\)'s coefficients usually needs numerical quadrature techniques, which introduces additional numerical error. Even though there is an analytical formula for integration, round-off error limited by the finite computer byte length is unavoidable. Hence, an operator \(\tilde{A}^L\) is obtained being different from \(A^L\). The error between \(A^L\) and \(\tilde{A}^L\) will perturb the adopted numerical method. If the error between the real and numerical solutions \(\Norm{u - \tilde{u}^L}\) can still be controlled, we say the method is consistent. For example, in the \(hp\)-BEM, if the stiffness matrix coefficient error satisfies the following consistent condition
\[
\abs{A^L_{ij} - \tilde{A}^L_{ij}} < \Phi(L) \quad (i,j = 1, \cdots, N_L)
\]
with
\[
\lim_{L \rightarrow \infty} N_L \Phi(L) = 0 \; \text{and} \; \Phi(L) = N_L^{-1} L \sigma^{\varrho L},
\]
the exponential convergence as shown in \eqref{eq:exponential-convergence} can be preserved.
Understanding about numerical stability, convergence and consistency的更多相关文章
- Softmax vs. Softmax-Loss VS cross-entropy损失函数 Numerical Stability(转载)
http://freemind.pluskid.org/machine-learning/softmax-vs-softmax-loss-numerical-stability/ 卷积神经网络系列之s ...
- Softmax vs. Softmax-Loss: Numerical Stability
http://freemind.pluskid.org/machine-learning/softmax-vs-softmax-loss-numerical-stability/ softmax 在 ...
- Understanding Convolution in Deep Learning
Understanding Convolution in Deep Learning Convolution is probably the most important concept in dee ...
- [C4] Andrew Ng - Improving Deep Neural Networks: Hyperparameter tuning, Regularization and Optimization
About this Course This course will teach you the "magic" of getting deep learning to work ...
- 【转】Artificial Neurons and Single-Layer Neural Networks
原文:written by Sebastian Raschka on March 14, 2015 中文版译文:伯乐在线 - atmanic 翻译,toolate 校稿 This article of ...
- AP(affinity propagation)研究
待补充…… AP算法,即Affinity propagation,是Brendan J. Frey* 和Delbert Dueck于2007年在science上提出的一种算法(文章链接,维基百科) 现 ...
- 提高神经网络的学习方式Improving the way neural networks learn
When a golf player is first learning to play golf, they usually spend most of their time developing ...
- 【Caffe 测试】Training LeNet on MNIST with Caffe
Training LeNet on MNIST with Caffe We will assume that you have Caffe successfully compiled. If not, ...
- MR for Baum-Welch algorithm
The Baum-Welch algorithm is commonly used for training a Hidden Markov Model because of its superior ...
随机推荐
- tomcat apr 部署
背景 这还是为了高并发的事,网上说的天花乱坠的,加了apr怎么怎么好,我加了,扯淡.就是吹牛用.我还是认为,性能问题要考设计逻辑和代码解决,这些都是锦上添花的. 步骤 1 windows 部署简单,虽 ...
- zabbix3.0.4使用percona-monitoring-plugins插件来监控mysql5.6的详细实现过程
zabbix3.0.4使用percona-monitoring-plugins插件来监控mysql5.6的详细实现过程 因为Zabbix自带的MySQL监控没有提供可以直接使用的Key,所以一般不采用 ...
- 1-HTML Attributes
下表列举了常用的Html属性 Attribute Description alt Specifies an alternative text for an image, when the image ...
- mysql8:caching-sha2-password问题
参考文章:https://blog.csdn.net/u010026255/article/details/80062153 问题:caching-sha2-password 处理: ALTER US ...
- Netty学习4—NIO服务端报错:远程主机强迫关闭了一个现有的连接
1 发现问题 NIO编程中服务端会出现报错 Exception in thread "main" java.io.IOException: 远程主机强迫关闭了一个现有的连接. at ...
- SpringBoot和SpringCloud面试题
一. 什么是springboot 1.用来简化spring应用的初始搭建以及开发过程 使用特定的方式来进行配置(properties或yml文件) 2.创建独立的spring引用程序 main方法运行 ...
- android端 socket长连接 架构
看过包建强的<App研发录>之后对其中的基础Activity类封装感到惊讶,一直想找一种方式去解决关于app中使用socket长连接问题,如何实现简易的封装来达到主活动中涉及socket相 ...
- 数据结构HashMap(Android SparseArray 和ArrayMap)
HashMap也是我们使用非常多的Collection,它是基于哈希表的 Map 接口的实现,以key-value的形式存在.在HashMap中,key-value总是会当做一个整体来处理,系统会根据 ...
- spring mvc底层(DispacherServlet)的简单实现
使用过spring mvc的小伙伴都知道,mvc在使用的时候,我们只需要在controller上注解上@controller跟@requestMapping(“URL”),当我们访问对应的路径的时候, ...
- python(3):文件操作/os库
文件基本操作 r,以读模式打开, r+=r+w, w, 写模式(清空原来的内容), w+=w+r, a , 追加模式, a+=a+r, rb, wb, ab, b表示以二进制文件打开 想在一段文 ...
