攻防世界CRYPTO新手练习
0x01 base64
直接base64 Decode 得到flag cyberpeace{Welcome_to_new_World!}
0x02 Caesar
key为12 的恺撒密码,解密德flag cyberpeace{you_have_learned_caesar_encryption}
Tools:http://www.zjslove.com/3.decode/kaisa/index.html
0x03 Morse
摩斯密码 1替换成-,0替换成.,直接解密
11 111 010 000 0 1010 111 100 0 00 000 000 111 00 10 1 0 010 0 000 1 00 10 110
-- --- .-. ... . -.-. --- -.. . .. ... ... --- .. -. - . .-. . ... - .. -. --.
解密得到flag cyberpeace{morsecodeissointeresting}
贴出大佬的代码
# python3
# -*- coding:utf-8 -*-
CODE_TABLE = {
# 26 个英文字符
'A': '.-', 'B': '-...', 'C': '-.-.',
'D': '-..', 'E': '.', 'F': '..-.',
'G': '--.', 'H': '....', 'I': '..',
'J': '.---', 'K': '-.-', 'L': '.-..',
'M': '--', 'N': '-.', 'O': '---',
'P': '.--.', 'Q': '--.-', 'R': '.-.',
'S': '...', 'T': '-', 'U': '..-',
'V': '...-', 'W': '.--', 'X': '-..-',
'Y': '-.--', 'Z': '--..',
# 10 个数字
'0': '-----', '1': '.----', '2': '..---',
'3': '...--', '4': '....-', '5': '.....',
'6': '-....', '7': '--...', '8': '---..',
'9': '----.',
# 16 个特殊字符
',': '--..--', '.': '.-.-.-', ':': '---...', ';': '-.-.-.',
'?': '..--..', '=': '-...-', "'": '.----.', '/': '-..-.',
'!': '-.-.--', '-': '-....-', '_': '..--.-', '(': '-.--.',
')': '-.--.-', '$': '...-..-', '&': '. . . .', '@': '.--.-.'
# 你还可以自定义
}
def morsedecode(morse):
msg =''
codes = morse.split(' ')
for code in codes:
if code =='':
msg += ' '
else:
UNCODE =dict(map(lambda t:(t[1],t[0]),CODE_TABLE.items()))
msg += UNCODE[code]
return msg
a = open(r'crypto3.txt','r')
ciphertext = a.read()
ciphertext = ciphertext.replace('1','-')
ciphertext = ciphertext.replace('0','.')
FLAG = morsedecode(ciphertext)
flag = FLAG.lower()
flag = 'cyberpeace{'+flag+'}'
print('flag is ',flag)
0x04 Railfence
栅栏密码,栏数为5,解出来flag为 cyberpeace{railfence_cipher_gogogo}0
网上很多人都在这里遇到了问题,表示无法得出答案,其实这里主要的原因是国内外对栅栏密码的加密原理相同当实际过程有些不同,这道题就需要用国外的解密方法来解密
贴张网图了解一下
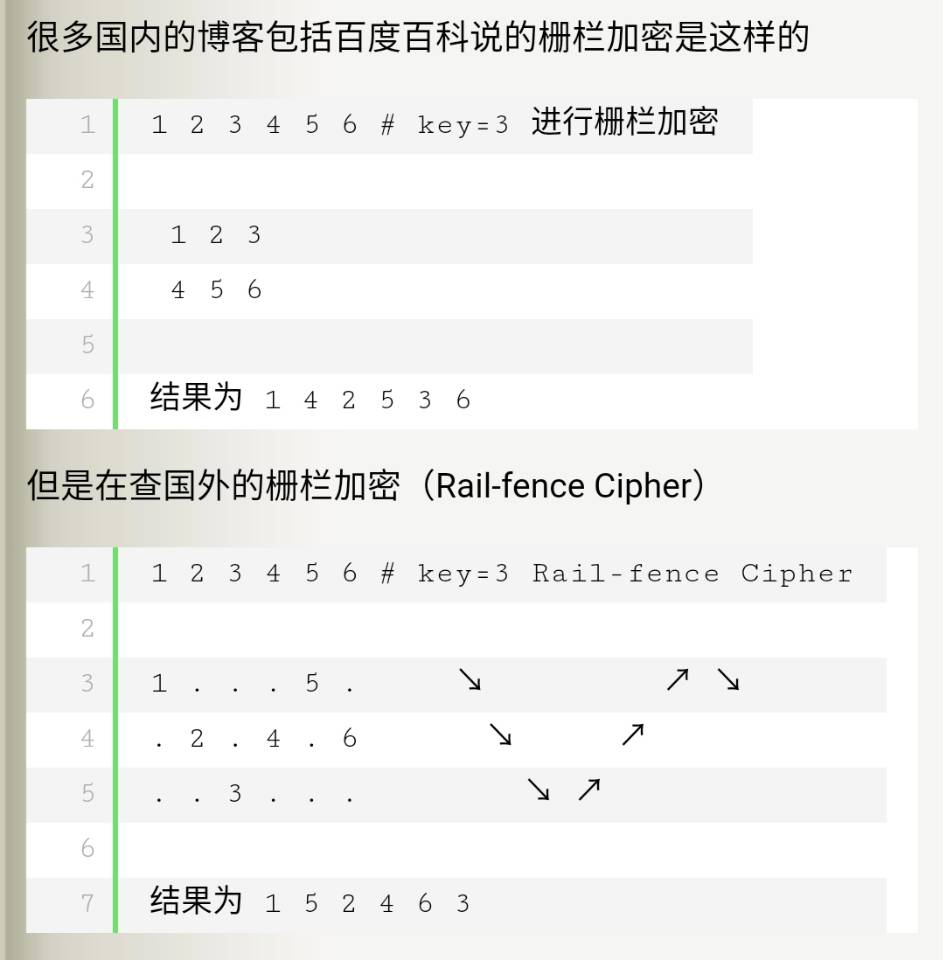
国内解密 https://www.qqxiuzi.cn/bianma/zhalanmima.php
国外解密 http://www.atoolbox.net/Tool.php?Id=777
0x05 easy RSA
一个RSA加密,直接贴出代码
import gmpy2
p = 473398607161
q = 4511491
e = 17
s = (p-1)*(q-1)
d = gmpy2.invert(e,s)
print('flag is :',d)
得flag : cyberpeace{125631357777427553}
0X06 不仅仅是Morse
下载得文件是这样的
--/.-/-.--/..--.-/-..././..--.-/..../.-/...-/./..--.-/.-/-./---/-/...././.-./..--.-/-.././-.-./---/-.././..../..../..../..../.-/.-/.-/.-/.-/-.../.-/.-/-.../-.../-.../.-/.-/-.../-.../.-/.-/.-/.-/.-/.-/.-/.-/-.../.-/.-/-.../.-/-.../.-/.-/.-/.-/.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../-.../.-/.-/.-/-.../-.../.-/.-/-.../.-/.-/.-/.-/-.../.-/-.../.-/.-/-.../.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/-.../-.../.-/.-/-.../-.../-.../.-/-.../.-/.-/.-/-.../.-/-.../.-/-.../-.../.-/.-/.-/-.../-.../.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/.-/.-/.-/-.../-.../.-/-.../-.../.-/.-/-.../-.../.-/.-/-.../.-/.-/-.../.-/.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/.-/-.../.-/-.../.-/.-/-.../-.../.-/-.../.-/.-/.-/.-/-.../-.../.-/-.../.-/.-/-.../-.../.-
讲/替换成空格,可得到一串摩斯密码,解密后
AAAAABAABBBAABBAAAAAAAABAABABAAAAAAABBABAAABBAAABBAABAAAABABAABAAABBABAAABAAABAABABBAABBBABAAABABABBAAABBABAAABAABAABAAAABBABBAABBAABAABAAABAABAABAABABAABBABAAAABBABAABBA
培根密码,贴出(大佬的)解密代码
import re
# 密文转化为指定格式
s = 'AAAAABAABBBAABBAAAAAAAABAABABAAAAAAABBABAAABBAAABBAABAAAABABAABAAABBABAAABAAABAABABBAABBBABAAABABABBAAABBABAAABAABAABAAAABBABBAABBAABAABAAABAABAABAABABAABBABAAAABBABAABBA'
a = s.lower()
# 字典
CODE_TABLE = {
'a':'aaaaa','b':'aaaab','c':'aaaba','d':'aaabb','e':'aabaa','f':'aabab','g':'aabba',
'h':'aabbb','i':'abaaa','j':'abaab','k':'ababa','l':'ababb','m':'abbaa','n':'abbab',
'o':'abbba','p':'abbbb','q':'baaaa','r':'baaab','s':'baaba','t':'baabb','u':'babaa',
'v':'babab','w':'babba','x':'babbb','y':'bbaaa','z':'bbaab'
}
# 5个一组进行切割并解密
def peigendecode(peigen):
msg =''
codes = re.findall(r'.{5}', a)
for code in codes:
if code =='':
msg += ' '
else:
UNCODE =dict(map(lambda t:(t[1],t[0]),CODE_TABLE.items()))
msg += UNCODE[code]
return msg
flag = peigendecode(a)
print('flag is ',flag)
得到flag cyberpeace{attackanddefenceworldisinteresting}
0x07 混合编码
先base64 Decode 解得
LzExOS8xMDEvMTA4Lzk5LzExMS8xMDkvMTAxLzExNi8xMTEvOTcvMTE2LzExNi85Ny85OS8xMDcvOTcvMTEwLzEwMC8xMDAvMTAxLzEwMi8xMDEvMTEwLzk5LzEwMS8xMTkvMTExLzExNC8xMDgvMTAw
更具ASCII转成字符串可得
LzExOS8xMDEvMTA4Lzk5LzExMS8xMDkvMTAxLzExNi8xMTEvOTcvMTE2LzExNi85Ny85OS8xMDcvOTcvMTEwLzEwMC8xMDAvMTAxLzEwMi8xMDEvMTEwLzk5LzEwMS8xMTkvMTExLzExNC8xMDgvMTAw
在进行一次base64 Decode
/119/101/108/99/111/109/101/116/111/97/116/116/97/99/107/97/110/100/100/101/102/101/110/99/101/119/111/114/108/100
去掉/再转一次字符串得到答案welcometoattackanddefenceworld
顺便贴一个大佬的代码
#!/usr/bin/env python3
# -*- coding:utf-8 -*- import base64 a = open(r'crypto8.txt','r')
s = a.read() # base64解密一下
b = base64.b64decode(s).decode('ascii')
# 对解密后的字符串进行处理
b = b.strip('&#;')
c = []
c = b.split(';&#')
# unicode解密
d = ''
for i in c:
d += chr(int(i))
# base64再次解密
e = base64.b64decode(d).decode('ascii')
# 对字符进行处理
e = e.strip('/')
f = []
f = e.split('/')
# 转化为ascii码
flag =''
for i in f:
flag += chr(int(i))
print('flag is ',flag)
flag : cyberpeace{welcometoattackanddefenceworld}
0x08 Normal RSA
这道题主要考察得是RSAtool的使用,我都在kail里操作
先准备rsatool
git clone https://github.com/ius/rsatool
下载文件解压后得到flag.enc和pubkey.pem两个文件
openssl提取出pubkey.pem中的参数;
openssl rsa -pubin -text -modulus -in warmup -in pubkey.pem
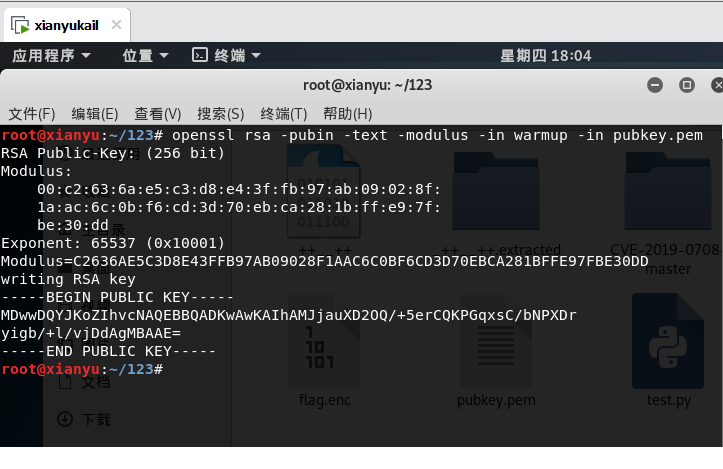
将得到的Modulus 16进制转为10进制,得到
87924348264132406875276140514499937145050893665602592992418171647042491658461
使用kail的factor()将这个数分解成两个素数的乘积时,直接报错了,应该是太长了,所以使用在线工具进行分解
在线:http://www.factordb.com/ 分解得:
275127860351348928173285174381581152299
319576316814478949870590164193048041239
知道两个素数,随机定义大素数e,求出密钥文件
python rsatool.py -o private.pem -e 65537 -p 275127860351348928173285174381581152299 -q 319576316814478949870590164193048041239
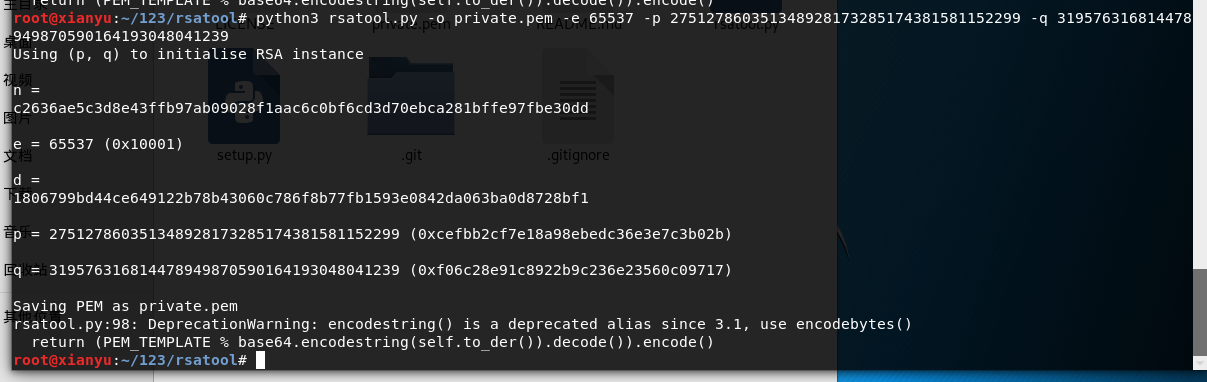
这时候我们会得到一个private.pem文件,利用这个文件进行解密
openssl rsautl -decrypt -in flag.enc -inkey private.pem
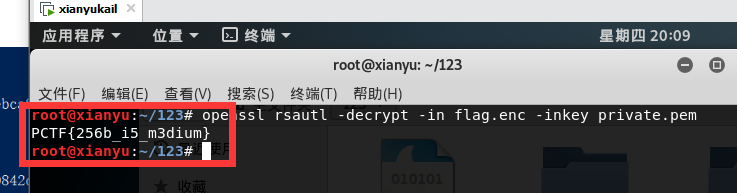
得到flag : PCTF{256b_i5_m3dium}
0x09 轮转机加密
题目如此,轮转机加密
1: < ZWAXJGDLUBVIQHKYPNTCRMOSFE <
2: < KPBELNACZDTRXMJQOYHGVSFUWI <
3: < BDMAIZVRNSJUWFHTEQGYXPLOCK <
4: < RPLNDVHGFCUKTEBSXQYIZMJWAO <
5: < IHFRLABEUOTSGJVDKCPMNZQWXY <
6: < AMKGHIWPNYCJBFZDRUSLOQXVET <
7: < GWTHSPYBXIZULVKMRAFDCEONJQ <
8: < NOZUTWDCVRJLXKISEFAPMYGHBQ <
9: < XPLTDSRFHENYVUBMCQWAOIKZGJ <
10: < UDNAJFBOWTGVRSCZQKELMXYIHP <
11: < MNBVCXZQWERTPOIUYALSKDJFHG <
12: < LVNCMXZPQOWEIURYTASBKJDFHG <
13: < JZQAWSXCDERFVBGTYHNUMKILOP < 密钥为:2,3,7,5,13,12,9,1,8,10,4,11,6
密文为:NFQKSEVOQOFNP
直接贴出大佬的代码
#!/usr/bin/env python3
# -*- coding:utf-8 -*- import re sss = '1: < ZWAXJGDLUBVIQHKYPNTCRMOSFE < 2: < KPBELNACZDTRXMJQOYHGVSFUWI < 3: < BDMAIZVRNSJUWFHTEQGYXPLOCK < 4: < RPLNDVHGFCUKTEBSXQYIZMJWAO < 5: < IHFRLABEUOTSGJVDKCPMNZQWXY < 6: < AMKGHIWPNYCJBFZDRUSLOQXVET < 7: < GWTHSPYBXIZULVKMRAFDCEONJQ < 8: < NOZUTWDCVRJLXKISEFAPMYGHBQ < 9: < XPLTDSRFHENYVUBMCQWAOIKZGJ < 10: < UDNAJFBOWTGVRSCZQKELMXYIHP < 11 < MNBVCXZQWERTPOIUYALSKDJFHG < 12 < LVNCMXZPQOWEIURYTASBKJDFHG < 13 < JZQAWSXCDERFVBGTYHNUMKILOP <'
m = 'NFQKSEVOQOFNP'
# 将sss转化为列表形式
content=re.findall(r'< (.*?) <',sss,re.S)
# re.S:DOTALL,此模式下,"."的匹配不受限制,可匹配任何字符,包括换行符
iv=[2,3,7,5,13,12,9,1,8,10,4,11,6]
print(content)
vvv=[]
for i in range(13):
index=content[iv[i]-1].index(m[i])
vvv.append(index)
print(vvv) for i in range(0,26):
flag=""
for j in range(13):
flag += content[iv[j]-1][(vvv[j]+i)%26]
print(flag.lower())
得到flag cyberpeace{fireinthehole}
0x10 easychallenge
pyc时是将python的py程序编译成的中间式文件,这道题我们需要将其反编译成我们可读的py代码
反编译结果
#!/usr/bin/env python
# encoding: utf-8
# 如果觉得不错,可以推荐给你的朋友!http://tool.lu/pyc
import base64 def encode1(ans):
s = ''
for i in ans:
x = ord(i) ^ 36
x = x + 25
s += chr(x)
return s def encode2(ans):
s = ''
for i in ans:
x = ord(i) + 36
x = x ^ 36
s += chr(x)
return s def encode3(ans):
return base64.b32encode(ans) flag = ' '
print 'Please Input your flag:'
flag = raw_input()
final = 'UC7KOWVXWVNKNIC2XCXKHKK2W5NLBKNOUOSK3LNNVWW3E==='
if encode3(encode2(encode1(flag))) == final:
print 'correct'
else:
print 'wrong'
分析代码,输入的flag需要进行三次加密(??),想求答案,写段代码
import base64 key = 'UC7KOWVXWVNKNIC2XCXKHKK2W5NLBKNOUOSK3LNNVWW3E==='
temp = base64.b32decode(key)
#可得temp为'\xa0\xbe\xa7Z\xb7\xb5Z\xa6\xa0Z\xb8\xae\xa3\xa9Z\xb7Z\xb0\xa9\xae\xa3\xa4\xad\xad\xad\xad\xad\xb2'
#手动赋值进行接下来的解密
b = "\xa0\xbe\xa7Z\xb7\xb5Z\xa6\xa0Z\xb8\xae\xa3\xa9Z\xb7Z\xb0\xa9\xae\xa3\xa4\xad\xad\xad\xad\xad\xb2"
s = ''
for i in b:
s += chr((ord(i) ^ 36) - 36)
l = ''
for i in s:
l += chr((ord(i) - 25) ^ 36)
print ('flag is ',l)
得到flag :cyberpeace{interestinghhhhh}
0x11 幂数加密
下载下来分析后,式云影密码
8842101220480224404014224202480122
88421 122 48 2244 4 142242 248 122
23 5 12 12 4 15 14 5
w e l l d o n e
就这样,以0为分界,每组加起来,去对应顺序字母
贴一段大佬的代码
#!/user/bin/env python
# -*-coding:utf-8 -*- a = open(r'crypto11.txt','r')
ciphertext = a.read() s = ciphertext.split('0') flag = ''
for i in range(len(s)):
list = []
for j in s[i]:
list.append(j)
b = 0
for k in list:
b += int(k)
# 字母ascii值与字母顺序相差为96
flag += chr(b+96)
print('flag is ',flag)
flag : cyberpeace{welldone}
0x12 easy ECC
ECC(椭圆曲线加密)
椭圆曲线加密原理 ECC椭圆曲线详解 ECC加密算法入门介绍
我现在还是一脸懵逼,只能用着大佬的脚本,苟延残喘
#!/usr/bin/env python3
# -*- coding:utf-8 -*- def get_inverse(mu, p):
"""
获取y的负元
"""
for i in range(1, p):
if (i*mu)%p == 1:
return i
return -1 def get_gcd(zi, mu):
"""
获取最大公约数
"""
if mu:
return get_gcd(mu, zi%mu)
else:
return zi def get_np(x1, y1, x2, y2, a, p):
"""
获取n*p,每次+p,直到求解阶数np=-p
"""
flag = 1 # 定义符号位(+/-) # 如果 p=q k=(3x2+a)/2y1mod p
if x1 == x2 and y1 == y2:
zi = 3 * (x1 ** 2) + a # 计算分子 【求导】
mu = 2 * y1 # 计算分母 # 若P≠Q,则k=(y2-y1)/(x2-x1) mod p
else:
zi = y2 - y1
mu = x2 - x1
if zi* mu < 0:
flag = 0 # 符号0为-(负数)
zi = abs(zi)
mu = abs(mu) # 将分子和分母化为最简
gcd_value = get_gcd(zi, mu) # 最大公約數
zi = zi // gcd_value # 整除
mu = mu // gcd_value
# 求分母的逆元 逆元: ∀a ∈G ,ョb∈G 使得 ab = ba = e
# P(x,y)的负元是 (x,-y mod p)= (x,p-y) ,有P+(-P)= O∞
inverse_value = get_inverse(mu, p)
k = (zi * inverse_value) if flag == 0: # 斜率负数 flag==0
k = -k
k = k % p
# 计算x3,y3 P+Q
x3 = (k ** 2 - x1 - x2) % p
y3 = (k * (x1 - x3) - y1) % p
return x3,y3 def get_rank(x0, y0, a, b, p):
"""
获取椭圆曲线的阶
"""
x1 = x0 #-p的x坐标
y1 = (-1*y0)%p #-p的y坐标
tempX = x0
tempY = y0
n = 1
while True:
n += 1
# 求p+q的和,得到n*p,直到求出阶
p_x,p_y = get_np(tempX, tempY, x0, y0, a, p)
# 如果 == -p,那么阶数+1,返回
if p_x == x1 and p_y == y1:
return n+1
tempX = p_x
tempY = p_y def get_param(x0, a, b, p):
"""
计算p与-p
"""
y0 = -1
for i in range(p):
# 满足取模约束条件,椭圆曲线Ep(a,b),p为质数,x,y∈[0,p-1]
if i**2%p == (x0**3 + a*x0 + b)%p:
y0 = i
break # 如果y0没有,返回false
if y0 == -1:
return False # 计算-y(负数取模)
x1 = x0
y1 = (-1*y0) % p
return x0,y0,x1,y1 def get_ng(G_x, G_y, key, a, p):
"""
计算nG
"""
temp_x = G_x
temp_y = G_y
while key != 1:
temp_x,temp_y = get_np(temp_x,temp_y, G_x, G_y, a, p)
key -= 1
return temp_x,temp_y def ecc_main():
while True:
a = int(input("请输入椭圆曲线参数a(a>0)的值:"))
b = int(input("请输入椭圆曲线参数b(b>0)的值:"))
p = int(input("请输入椭圆曲线参数p(p为素数)的值:")) #用作模运算 # 条件满足判断
if (4*(a**3)+27*(b**2))%p == 0:
print("您输入的参数有误,请重新输入!!!\n")
else:
break # 选点作为G点
print("在如上坐标系中选一个值为G的坐标")
G_x = int(input("请输入选取的x坐标值:"))
G_y = int(input("请输入选取的y坐标值:")) # 获取椭圆曲线的阶
n = get_rank(G_x, G_y, a, b, p) # user1生成私钥,小key
key = int(input("请输入私钥小key(<{}):".format(n))) # user1生成公钥,大KEY
KEY_x,kEY_y = get_ng(G_x, G_y, key, a, p)
print('flag is ',KEY_,KEY_Y) if __name__ == "__main__":
ecc_main()
然而题目的给的数值貌似太大,这个脚本的跑不出来,悲伤.jpg
等以后看有没有机会补上(咕咕咕)
20191021,今天突然想起来了,找到了其他大佬的py代码,于是补上
import collections
import random
EllipticCurve = collections.namedtuple('EllipticCurve', 'name p a b g n h')
curve = EllipticCurve(
'secp256k1',
# Field characteristic.
p=int(input('p=')),
# Curve coefficients.
a=int(input('a=')),
b=int(input('b=')),
# Base point.
g=(int(input('Gx=')),
int(input('Gy='))),
# Subgroup order.
n=int(input('k=')),
# Subgroup cofactor.
h=1,
)
# Modular arithmetic ##########################################################
def inverse_mod(k, p):
"""Returns the inverse of k modulo p.
This function returns the only integer x such that (x * k) % p == 1.
k must be non-zero and p must be a prime.
"""
if k == 0:
raise ZeroDivisionError('division by zero')
if k < 0:
# k ** -1 = p - (-k) ** -1 (mod p)
return p - inverse_mod(-k, p)
# Extended Euclidean algorithm.
s, old_s = 0, 1
t, old_t = 1, 0
r, old_r = p, k
while r != 0:
quotient = old_r // r
old_r, r = r, old_r - quotient * r
old_s, s = s, old_s - quotient * s
old_t, t = t, old_t - quotient * t
gcd, x, y = old_r, old_s, old_t
assert gcd == 1
assert (k * x) % p == 1
return x % p
# Functions that work on curve points #########################################
def is_on_curve(point):
"""Returns True if the given point lies on the elliptic curve."""
if point is None:
# None represents the point at infinity.
return True
x, y = point
return (y * y - x * x * x - curve.a * x - curve.b) % curve.p == 0
def point_neg(point):
"""Returns -point."""
assert is_on_curve(point)
if point is None:
# -0 = 0
return None
x, y = point
result = (x, -y % curve.p)
assert is_on_curve(result)
return result
def point_add(point1, point2):
"""Returns the result of point1 + point2 according to the group law."""
assert is_on_curve(point1)
assert is_on_curve(point2)
if point1 is None:
# 0 + point2 = point2
return point2
if point2 is None:
# point1 + 0 = point1
return point1
x1, y1 = point1
x2, y2 = point2
if x1 == x2 and y1 != y2:
# point1 + (-point1) = 0
return None
if x1 == x2:
# This is the case point1 == point2.
m = (3 * x1 * x1 + curve.a) * inverse_mod(2 * y1, curve.p)
else:
# This is the case point1 != point2.
m = (y1 - y2) * inverse_mod(x1 - x2, curve.p)
x3 = m * m - x1 - x2
y3 = y1 + m * (x3 - x1)
result = (x3 % curve.p,
-y3 % curve.p)
assert is_on_curve(result)
return result
def scalar_mult(k, point):
"""Returns k * point computed using the double and point_add algorithm."""
assert is_on_curve(point)
if k < 0:
# k * point = -k * (-point)
return scalar_mult(-k, point_neg(point))
result = None
addend = point
while k:
if k & 1:
# Add.
result = point_add(result, addend)
# Double.
addend = point_add(addend, addend)
k >>= 1
assert is_on_curve(result)
return result
# Keypair generation and ECDHE ################################################
def make_keypair():
"""Generates a random private-public key pair."""
private_key = curve.n
public_key = scalar_mult(private_key, curve.g)
return private_key, public_key
private_key, public_key = make_keypair()
print("private key:", hex(private_key))
print("public key: (0x{:x}, 0x{:x})".format(*public_key))
3个月过去了,我还是一样的菜啊!!!

攻防世界CRYPTO新手练习的更多相关文章
- CTF -攻防世界-crypto新手区(5~11)
easy_RSA 首先如果你没有密码学基础是得去恶补一下的 然后步骤是先算出欧拉函数 之后提交注意是cyberpeace{********}这样的 ,博主以为是flag{}耽误了很长时间 明明没算错 ...
- CTF -攻防世界-crypto新手区(1~4)
题目已经提示用base64直接解密就行 base64解密网址 http://tool.oschina.net/encrypt?type=3 题目提示是凯撒密码 http://www.zjslove.c ...
- 攻防世界web新手区
攻防世界web新手区 第一题view_source 第二题get_post 第三题robots 第四题Backup 第五题cookie 第六题disabled_button 第七题simple_js ...
- 攻防世界 Misc 新手练习区 stegano CONFidence-DS-CTF-Teaser Writeup
攻防世界 Misc 新手练习区 stegano CONFidence-DS-CTF-Teaser Writeup 题目介绍 题目考点 隐写术 摩斯密码 Writeup 下载附件是PDF文件打开,研究一 ...
- 攻防世界 Misc 新手练习区 ext3 bugku Writeup
攻防世界 Misc 新手练习区 ext3 bugku Writeup 题目介绍 题目考点 WinHex工具的使用 linux磁盘挂载mount命令 Writeup 下载附件拖进winhex分析一下,查 ...
- 攻防世界 Misc 新手练习区 gif Writeup
攻防世界 Misc 新手练习区 gif Writeup 题目介绍 题目考点 仔细联想 字符转换 Writeup 下载附件并打开 104张黑白图 发现是一堆黑色和白色的图片,按某种规律排列,猜想flag ...
- 攻防世界 Misc 新手练习区 坚持60s Writeup
攻防世界 Misc 新手练习区 坚持60s Writeup 题目介绍 题目考点 java反编译 jd-gui 的使用 Writeup 下载附件并打开 kali执行命令 java -jar 9dc125 ...
- 攻防世界 Misc 新手练习区 give_you_flag Writeup
攻防世界 Misc 新手练习区 give_you_flag Writeup 题目介绍 题目考点 gif图片分离 细心的P图 二维码解码 Writeup 下载附件打开,发现是一张gif图片,打开看了一下 ...
- 攻防世界 Misc 新手练习区 如来十三掌 Writeup
攻防世界 Misc 新手练习区 如来十三掌 Writeup 题目介绍 题目考点 佛曰加密.base64.Rot13等加密方法的了解 Writeup 下载并打开附件 联想到佛曰加密,复制内容到 佛曰加密 ...
随机推荐
- 2019HDU多校第五场A fraction —— 辗转相除法|类欧几里得
题目 设 $ab^{-1} = x(mod \ p)$,给出 $x,p$,要求最小的 $b$,其中 $0< a < b, \ 1 < x<p,\ 3 \leq x\leq {1 ...
- C# IFormattable 接口重写
public class Racer : IComparable<Racer>, IFormattable { public int Id { get; private set; } pu ...
- 通过德鲁伊druid给系统增加监控
系统在线上运行了一段时间后,比如一年半载的,我们发现系统可能存在某些问题,比如执行系统变慢了,比如某些spring的bean无法监控各种调用情况. 触发到db的各种执行情况,这个时候,我们就需要一个工 ...
- 15、生命周期-BeanPostProcessor-后置处理器
15.生命周期-BeanPostProcessor-后置处理器 BeanPostProcessor 接口 package org.springframework.beans.factory.confi ...
- MySQL Bug#67718 浅谈B+树索引的分裂优化
原文链接:http://hedengcheng.com/?p=525 问题背景 今天,看到Twitter的DBA团队发布了其最新的MySQL分支:Changes in Twitter MySQL 5. ...
- CRT小键盘输入乱码
Options --> Session Options --> Terminal --> Emulation --> Modes 去选中 Enable keypad mode ...
- redis详解之cluster模式部署
一.环境说明 1.Operation OS:CentOS7.22.ruby version >= 2.2.23.openssl zlib gcc>=4.8.5 二.开始部署 1.安装rub ...
- Chisel-LLDB命令插件,让调试更Easy
http://blog.cnbluebox.com/blog/2015/03/05/chisel/ LLDB 是一个有着 REPL 的特性和 C++ ,Python 插件的开源调试器.LLDB 绑定在 ...
- 我的新书,ArcGIS从0到1,京东接受预定,有160个视频,851分钟
我的新书,ArcGIS从0到1,京东接受预定,8月08日至08月16日发货https://item.jd.com/53669213250.html当当网 http://product.dangdan ...
- C# Under the Hood: async/await (Marko Papic)
https://www.markopapic.com/csharp-under-the-hood-async-await/ Async and await keywords came with C# ...
