nProtect APPGuard安卓反外挂分析
工具与环境:
IDA7.0
JEB2.2.5
Nexus 5
Android 4.4
目录:
一:app简单分析与java层反编译
二: compatible.so反调试与反反调试
三: compatible.so注册jni函数分析
四: stub.so反调试与反反调试
五: stub.so注册jni函数分析
六: Assembly-CSharp.dll解密分析
七: libengine模块分析
八:总结
一:app简单分析与java层反编译
整体图:
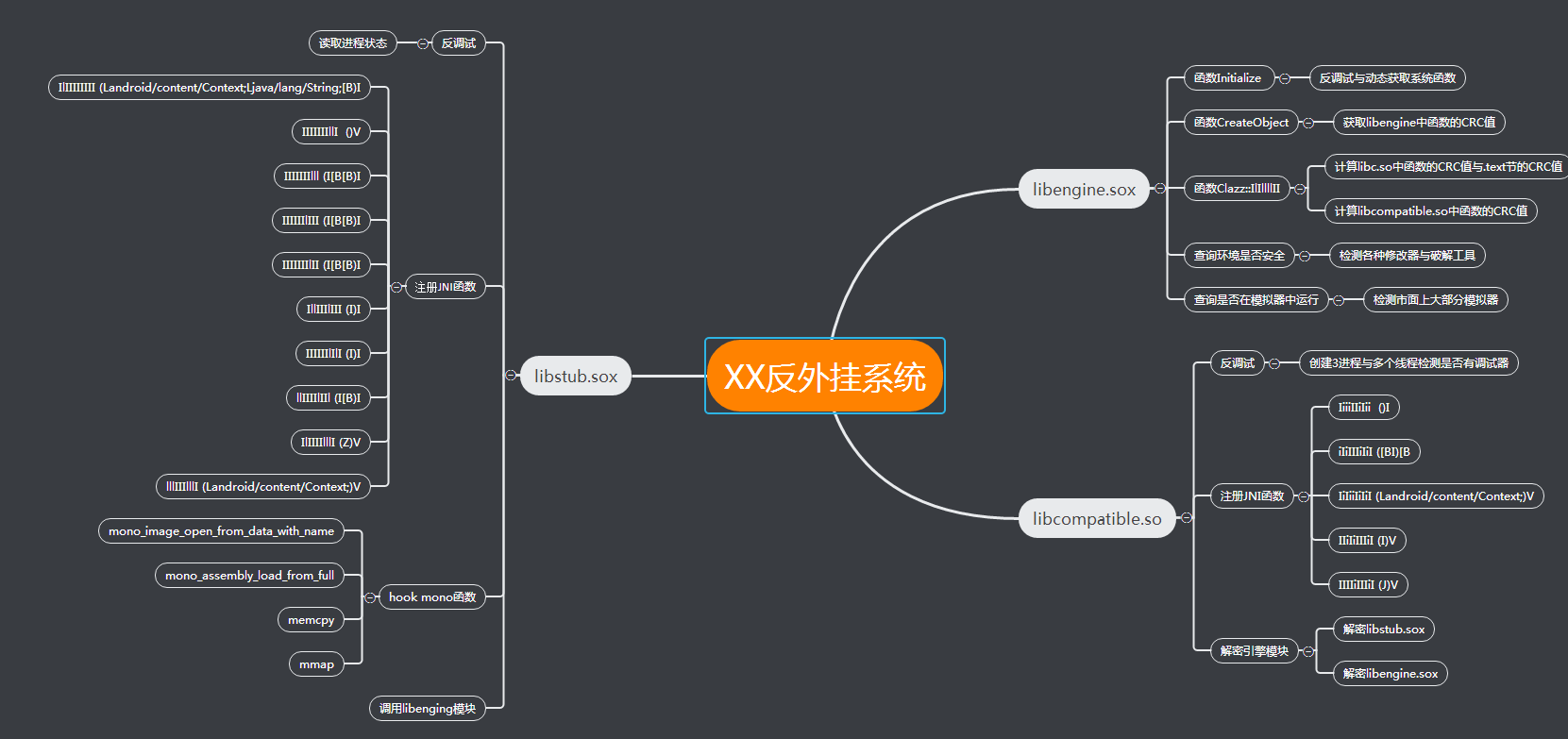
1.最近在学习手游保护方面的技术,本文是学习过程中分析某反外挂的一点记录,高手莫要见笑,有不对的地方还请指教,首先简单通过资源目录中文件名做基本了解,
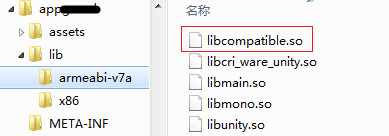
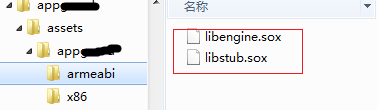
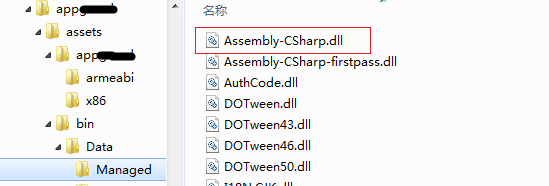
在lib目录中有libmono.so、libunity.so,资源目录中存在(assets\bin\Data\Managed\Assembly-CSharp.dll),应该是unity 3D编写,通过反编译发现该文件己被加密,在资源目录下armeabi文件夹中还存放着libengine.sox与libstub.sox文件,看名字猜测很可能这两个文件就是反外挂其中的一些模块了,在看看lib目录下只有libcompatible.so模块比较可疑。如下图所示:
当我们用调试器附加游戏程进时会有如下提示:
被发现有调试器附加,下节我们将分析它的反调试机制。
2.通过JEB反编译来看看大致流程,反编译后先找到application类,代码如下图:
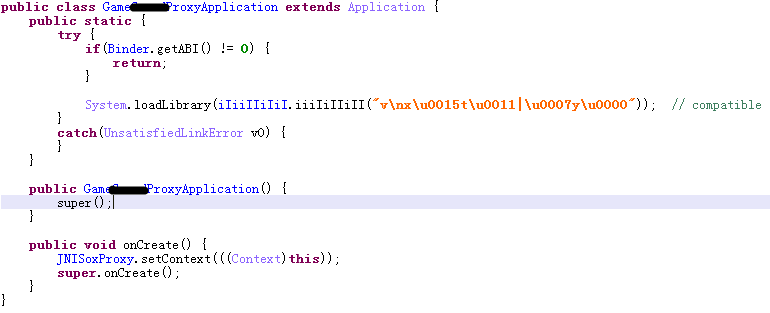
主要是加载so模块,so名称字符串被加密了,解密出来后so名称"compatible",将compatible.so放到IDA中反编译发现函数名被混淆了,字符串己加密,如下图:
通过以上简单分析,我们主要关注的重点关注的模块主要有lib目录下的libcompatible.so与资源目录中的libengine.sox与libstub.sox,还有就是发现java层的字符串与函数名都被混淆,so模块中的字符串也函数名也被混淆。
3.拷贝资源,解密libstub.sox并加载 。
在Lcom/inca/security/Core/AppGuardEngine初始函数<init>(Landroid/content/Context;Lcom/inca/security/AppGuard/AppGuardEventListener;Z)V中将判断X86或ARM平台并将对应的\assets\appguard中的libengine.sox、libstub.sox、update.dat拷贝到程序安装目录。JEB未能正常反编译出java代码,看smali代码。
- :1946
- 00001946 const/4 v9, 3
- 00001948 if-ge v6, v9, :1C16
- :194C
- 0000194C invoke-static Binder->getABI()I
- 00001952 move-result v6
- 00001954 move-object/from16 v0, p0
- 00001958 move-object/from16 v1, p1
- 0000195C invoke-virtual AppGuardEngine->iiIIIiiiIi(Context, I)Z, v0, v1, v6 # 拷贝资源
- 00001962 move-result v6
- 00001964 if-eqz v6, :1BE0
- :1968
- 00001968 new-instance v6, qb
- 0000196C invoke-static JNISoxProxy->getContext()Context
- 00001972 move-result-object v9
- 00001974 invoke-direct qb-><init>(Context)V, v6, v9
- 0000197A const-string v9, "fChY~_h\u0004yEr" # libstub.sox
- 0000197E invoke-virtual qb->iiIIIiiiIi([B)V, v6, v8
- 00001984 invoke-static b->iiIIIiiiIi(String)String, v9
- 0000198A move-result-object v9
- 0000198C const-string v10, "j\u000Fd\u0015r\u0013dHu\t" # libstub.so
- 00001990 invoke-static yb->iiIIIiiiIi(String)String, v10
- 00001996 move-result-object v10
- 00001998 const/4 v11, 0
- 0000199A invoke-virtual qb->iiIIIiiiIi(String, String, [B)Z, v6, v9, v10, v11 # 解密libstub.sox((最终传入so层解密private static native byte[] iIiIIIiIiI(byte[] arg0, int arg1)))
- 000019A0 move-result v6
- 000019A2 if-eqz v6, :1BE0
- :19A6
- 000019A6 new-instance v6, File
- 000019AA new-instance v9, StringBuilder
- 000019AE invoke-direct StringBuilder-><init>()V, v9
- 000019B4 const/4 v10, 0
- 000019B6 invoke-static JNISoxProxy->getContext()Context
- 000019BC move-result-object v11
- 000019BE invoke-virtual Context->getFilesDir()File, v11
- 000019C4 move-result-object v11
- 000019C6 invoke-virtual File->getAbsolutePath()String, v11
- 000019CC move-result-object v11
- 000019CE invoke-virtual StringBuilder->insert(I, String)StringBuilder, v9, v10, v11
- 000019D4 move-result-object v9
- 000019D6 const-string v10, "%FcHy^\u007FH$Ye" # /libstub.so
- 000019DA invoke-static b->iiIIIiiiIi(String)String, v10
- 000019E0 move-result-object v10
- 000019E2 invoke-virtual StringBuilder->append(String)StringBuilder, v9, v10
- 000019E8 move-result-object v9
- 000019EA invoke-virtual StringBuilder->toString()String, v9
- 000019F0 move-result-object v9
- 000019F2 invoke-direct File-><init>(String)V, v6, v9
- 000019F8 invoke-virtual File->exists()Z, v6
- :19FE
- 000019FE move-result v9
- 00001A00 if-eqz v9, :1BE0
- :1A04
- 00001A04 invoke-virtual File->getAbsolutePath()String, v6
- 00001A0A move-result-object v9
- 00001A0C invoke-static System->load(String)V, v9 # 加载指定路径的SO
- 00001A12 invoke-direct/range AppGuardEngine->lllIIIlllI(Context)V, p0 .. p1 # 调用Native
- :1A18
- 00001A18 invoke-virtual File->delete()Z, v6
- 00001A1E new-instance v6, File
- 00001A22 new-instance v9, StringBuilder
- 00001A26 invoke-direct StringBuilder-><init>()V, v9
- 00001A2C const/4 v10, 0
- 00001A2E invoke-static JNISoxProxy->getContext()Context
- 00001A34 move-result-object v11
- 00001A36 invoke-virtual Context->getFilesDir()File, v11
- 00001A3C move-result-object v11
- 00001A3E invoke-virtual File->getAbsolutePath()String, v11
- 00001A44 move-result-object v11
- 00001A46 invoke-virtual StringBuilder->insert(I, String)StringBuilder, v9, v10, v11
- 00001A4C move-result-object v9
- 00001A4E const-string v10, ")\no\u0004u\u0012s\u0004(\u0015i\u001E" # /libstub.sox
- 00001A52 invoke-static yb->iiIIIiiiIi(String)String, v10
- 00001A58 move-result-object v10
- 00001A5A invoke-virtual StringBuilder->append(String)StringBuilder, v9, v10
- 00001A60 move-result-object v9
- 00001A62 invoke-virtual StringBuilder->toString()String, v9
- 00001A68 move-result-object v9
- 00001A6A invoke-direct File-><init>(String)V, v6, v9
- 00001A70 invoke-virtual File->delete()Z, v6
4. 解密libstub.sox模块。
解密函数在类com/inca/security/qb中iiIIIiiiIi函数,代码如下:
- @SuppressLint(value={"SdCardPath"}) public boolean iiIIIiiiIi(String arg25, String arg26, byte[] arg27) throws IOException, InvalidKeyException {
- Object v18;
- Object v5_2;
- long v16_1;
- Method v8_3;
- Class v11_2;
- Object v7_2;
- Object v4_7;
- Method v15; // doFinal
- Method v14_1; // init java.security.Key
- Object v13_1; // RSA/ECB/PKCS1Padding
- int v8_1;
- int v7;
- FileInputStream v13;
- Method v4_6;
- byte[] v7_1;
- boolean v4_2;
- Method v5_1; // read
- byte[] v12;
- byte[] v11;
- Object v10; // /
- Class v9; // java.io.FileInputStream
- try {
- v9 = Class.forName(vb.iiIIIiiiIi("&3:3b;#|\n; 7\u0005<<\'8\u00018 )3!")); // java.io.FileInputStream
- Constructor v4_1 = v9.getConstructor(String.class);
- v10 = v4_1.newInstance(arg25.indexOf(yb.iiIIIiiiIi("I")) == 0 ? arg25 : new StringBuilder().insert(0, this.iiIiiiIIIi).append(arg25).toString()); // /
- v11 = new byte[16];
- v12 = new byte[4];
- v5_1 = v9.getMethod(vb.iiIIIiiiIi(" )3("), byte[].class, Integer.TYPE, Integer.TYPE); // read
- v5_1.invoke(v10, v11, Integer.valueOf(0), Integer.valueOf(3));
- if(v11[0] == 83 && v11[1] == 79 && v11[2] == 88) { // 判断开头是否为SOX
- goto label_82;
- }
- v4_2 = false;
- return v4_2;
- }
- catch(Exception v4) {
- goto label_78;
- }
- label_82:
- int v4_3 = 3;
- try {
- v5_1.invoke(v10, v11, Integer.valueOf(0), Integer.valueOf(2));
- if((((short)((((short)v11[0])) | (((short)v11[1])) << 8))) != 1) {
- return false;
- }
- v5_1.invoke(v10, v11, Integer.valueOf(0), Integer.valueOf(1));
- v5_1.invoke(v10, v11, Integer.valueOf(0), Integer.valueOf(2));
- v5_1.invoke(v10, v11, Integer.valueOf(0), Integer.valueOf(2));
- v5_1.invoke(v10, v11, Integer.valueOf(0), Integer.valueOf(4));
- v5_1.invoke(v10, v11, Integer.valueOf(0), Integer.valueOf(4));
- v5_1.invoke(v10, v12, Integer.valueOf(0), Integer.valueOf(4));
- v5_1.invoke(v10, v11, Integer.valueOf(0), Integer.valueOf(12));
- v5_1.invoke(v10, v11, Integer.valueOf(0), Integer.valueOf(16));
- v5_1.invoke(v10, v11, Integer.valueOf(0), Integer.valueOf(16));
- byte[] v4_5 = null;
- if(v11[0] == 0 || v11[1] == 0 || v11[14] == 0 || v11[15] == 0) {
- v7_1 = v4_5;
- v4_6 = v5_1;
- goto label_291;
- label_276:
- while(v7 < 64) {
- v13.read(v11);
- if(v8_1 == v14) {
- v4_5 = new byte[16];
- System.arraycopy(v11, 0, v4_5, 0, 16);
- }
- v7 = v8_1 + 1;
- v8_1 = v7;
- }
- v13.close();
- v7_1 = v4_5;
- v4_6 = v5_1;
- }
- else {
- File v8 = new File(String.format(yb.iiIIIiiiIi("CuI#\u0015(\u0012v\r"), arg25.substring(0, arg25.lastIndexOf(47)), qb.iiIIIiiiIi(v11))); // %s/%s.tpk
- if(v8.exists()) {
- v13 = new FileInputStream(v8);
- v13.read(v11);
- int v14 = (Math.abs(v11[0] << 24 | v11[4] << 16 | v11[8] << 8 | v11[12]) + 1) % 64;
- v7 = 1;
- v8_1 = 1;
- goto label_276;
- }
- else {
- return false;
- }
- }
- label_291:
- v4_6.invoke(v10, v11, Integer.valueOf(0), Integer.valueOf(4));
- v4_5 = new byte[(v11[3] & 255) << 24 | 0 | (v11[2] & 255) << 16 | (v11[1] & 255) << 8 | v11[0] & 255];
- v5_1 = v9.getMethod(vb.iiIIIiiiIi(" )3("), byte[].class); // read
- v5_1.invoke(v10, v4_5);
- Class v8_2 = Class.forName(yb.iiIIIiiiIi("\fg\u0010g\u001E(\u0005t\u001Fv\u0012iHE\u000Fv\u000Ec\u0014")); // javax.crypto.Cipher
- Method v11_1 = v8_2.getMethod(vb.iiIIIiiiIi("+78\u001B\"!83\"1)"), String.class); // getInstance
- v13_1 = v11_1.invoke(null, yb.iiIIIiiiIi("T5GIC%DIV-E576g\u0002b\u000Fh\u0001")); // RSA/ECB/PKCS1Padding
- v14_1 = v8_2.getMethod(vb.iiIIIiiiIi(";\";8"), Integer.TYPE, Class.forName(yb.iiIIIiiiIi("\fg\u0010gHu\u0003e\u0013t\u000Fr\u001F(-c\u001F"))); // init java.security.Key
- v14_1.invoke(v13_1, Integer.valueOf(2), this.iIiIIiIiIi);
- v15 = v8_2.getMethod(vb.iiIIIiiiIi("(=\n;\"3 "), byte[].class); // doFinal
- v4_7 = v15.invoke(v13_1, v4_5);
- if(v7_1 != null) {
- v13_1 = v11_1.invoke(null, yb.iiIIIiiiIi("\'C5")); // AES
- v14_1.invoke(v13_1, Integer.valueOf(2), Class.forName(vb.iiIIIiiiIi("&3:34|/ 5\"8=b!<7/|\u001F7/ )&\u000775\u0001<7/")).getConstructor(byte[].class, String.class).newInstance(v7_1, yb.iiIIIiiiIi("\'C5"))); // javax.crypto.spec.SecretKeySpec AES
- v4_7 = v15.invoke(v13_1, v4_7);
- }
- v7_2 = null;
- v7_2 = v11_1.invoke(v7_2, vb.iiIIIiiiIi("\r\u0017\u001F"));
- v14_1.invoke(v7_2, Integer.valueOf(2), Class.forName(yb.iiIIIiiiIi("\fg\u0010g\u001E(\u0005t\u001Fv\u0012iHu\u0016c\u0005(5c\u0005t\u0003r-c\u001FU\u0016c\u0005")).getConstructor(byte[].class, String.class).newInstance(v4_7, vb.iiIIIiiiIi("\r\u0017\u001F")));
- v11_2 = Class.forName(yb.iiIIIiiiIi("\fg\u0010gHo\t($\u007F\u0012c\'t\u0014g\u001FI\u0013r\u0016s\u0012U\u0012t\u0003g\u000B"));
- v13_1 = v11_2.getConstructor(null).newInstance(null);
- byte[] v14_2 = new byte[1024];
- v15 = v8_2.getMethod(vb.iiIIIiiiIi("\'<6-&)"), byte[].class, Integer.TYPE, Integer.TYPE);
- Method v16 = v11_2.getMethod(yb.iiIIIiiiIi("\u0011t\u000Fr\u0003"), byte[].class);
- for(v4_6 = v5_1; true; v4_6 = v5_1) {
- v4_3 = v4_6.invoke(v10, v14_2).intValue();
- if(v4_3 == -1) {
- break;
- }
- v16.invoke(v13_1, v15.invoke(v7_2, v14_2, Integer.valueOf(0), Integer.valueOf(v4_3)));
- }
- v16.invoke(v13_1, v8_2.getMethod(vb.iiIIIiiiIi("(=\n;\"3 "), null).invoke(v7_2, null));
- v4_7 = v11_2.getMethod(yb.iiIIIiiiIi("\u0012i$\u007F\u0012c\'t\u0014g\u001F"), null).invoke(v13_1, null);
- if(arg25.indexOf(vb.iiIIIiiiIi("c")) != 0) {
- arg26 = new StringBuilder().insert(0, this.iiIiiiIIIi).append(arg26).toString();
- }
- Class v7_3 = Class.forName(yb.iiIIIiiiIi("l\u0007p\u0007(\u000FiH@\u000Fj\u0003I\u0013r\u0016s\u0012U\u0012t\u0003g\u000B"));
- v8_3 = v7_3.getMethod(vb.iiIIIiiiIi("; %&)"), byte[].class);
- v14_1 = v7_3.getMethod(yb.iiIIIiiiIi("\u0005j\tu\u0003"), null);
- v15 = v7_3.getMethod(vb.iiIIIiiiIi("*>9!$"), null);
- v7_2 = v7_3.getConstructor(String.class).newInstance(arg26);
- v16_1 = na.iIIIiiiIII(((byte[])v4_7), 5);
- v5_2 = null;
- }
- catch(Exception v4) {
- goto label_78;
- }
- try {
- v18 = Binder.getReserved1();
- if(v18 == null) {
- goto label_761;
- }
- }
- catch(Exception v4) {
- goto label_760;
- }
- try {
- v5_2 = v18.getClass().getMethod(yb.iiIIIiiiIi("o/o/O\u000Fo/o/"), byte[].class, Integer.TYPE).invoke(v18, v4_7, Integer.valueOf(((int)v16_1)));
- }
- catch(Exception v4) {
- try {
- v4.printStackTrace();
- goto label_659;
- label_761:
- byte[] v5_3 = AppGuardEngine.iiIIIiiiIi(((byte[])v4_7), ((int)v16_1)); // 传入SO层解密 (该Native函数在compatible.so进行动态注册)
- label_760:
- }
- catch(Exception v4) {
- goto label_760;
- }
- }
- label_659:
- v4_3 = 3;
- try {
- int v12_1 = v12[0] & 255 | ((v12[v4_3] & 255) << 24 | 0 | (v12[2] & 255) << 16 | (v12[1] & 255) << 8);
- Class v16_2 = Class.forName(vb.iiIIIiiiIi("&3:3b\'8; |6;<|\r6 7>a~"));
- Object v17 = v16_2.getConstructor(null).newInstance(null);
- v16_2.getMethod(yb.iiIIIiiiIi("s\u0016b\u0007r\u0003"), byte[].class, Integer.TYPE, Integer.TYPE).invoke(v17, v5_2, Integer.valueOf(0), Integer.valueOf(v5_2.length));
- v16_1 = v16_2.getMethod(vb.iiIIIiiiIi("5)&\u001A3 \')"), null).invoke(v17, null).longValue();
- if(v12_1 != 0 && v12_1 != (((int)v16_1))) {
- v14_1.invoke(v7_2, null);
- v4_2 = false;
- }
- else {
- v8_3.invoke(v7_2, v5_2);
- v15.invoke(v7_2, null);
- v14_1.invoke(v7_2, null);
- v9.getMethod(yb.iiIIIiiiIi("\u0005j\tu\u0003"), null).invoke(v10, null);
- v11_2.getMethod(vb.iiIIIiiiIi("/>#!)"), null).invoke(v13_1, null);
- v9.getMethod(yb.iiIIIiiiIi("\u0005j\tu\u0003"), null).invoke(v10, null);
- v4_2 = true;
- }
- return v4_2;
- }
- catch(Exception v4) {
- label_78:
- Exception v5_4 = v4;
- v4_2 = false;
- v5_4.printStackTrace();
- return v4_2;
- }
- }
java层AES解密再传入传入so层解密private static native byte[] iIiIIIiIiI(byte[] arg0, int arg1)。
5. 解密libengine.sox模块
在Lcom/inca/security/Core/AppGuardEngine;->iiIIIiiiIi([B)Z生成一个随机数后SHA1后字会串做为解密后的文件名存放在/data/data/包名/files/目录下,解密函数与上一步相同。
生成随机数代码:
- .method private synthetic iiIIIiiiIi([B)Z
- .registers 12
- .annotation build SuppressLint
- value = {
- "TrulyRandom"
- }
- .end annotation
- .annotation system Throws
- value = {
- AppGuardException
- }
- .end annotation
- 00000000 const/4 v9, 2
- 00000002 const/16 v8, -0x007E
- 00000006 const/16 v7, 0x0030
- 0000000A const/4 v2, 0
- 0000000C const/4 v3, 1
- :E
- 0000000E const-string v1, "U.GW" # SHA1
- 00000012 invoke-static yb->iiIIIiiiIi(String)String, v1
- 00000018 move-result-object v1
- 0000001A invoke-static MessageDigest->getInstance(String)MessageDigest, v1
- :20
- 00000020 move-result-object v1
- :22
- 00000022 new-instance v4, SecureRandom
- 00000026 invoke-direct SecureRandom-><init>()V, v4
- 0000002C const/16 v5, 0x0100
- 00000030 new-array v5, v5, [B
- 00000034 const/16 v6, 0x0126
- 00000038 invoke-virtual SecureRandom->nextBytes([B)V, v4, v5
- 0000003E invoke-virtual MessageDigest->update([B)V, v1, v5
- 00000044 invoke-virtual SecureRandom->nextBytes([B)V, v4, v5
- 0000004A invoke-virtual MessageDigest->update([B)V, v1, v5
- 00000050 new-instance v4, BigInteger
- 00000054 invoke-virtual MessageDigest->digest()[B, v1
- 0000005A move-result-object v1
- 0000005C invoke-direct BigInteger-><init>(I, [B)V, v4, v3, v1
- 00000062 const/16 v1, 0x0010
- 00000066 invoke-virtual BigInteger->toString(I)String, v4, v1 # 随机数后SHA1值
- 0000006C move-result-object v1
- 0000006E iput-object v1, p0, AppGuardEngine->IiIIiiiiii_Random_SHA1:String # 解密后文件名
- //解密并调用
- 00000D7A new-instance v4, qb
- 00000D7E invoke-static JNISoxProxy->getContext()Context
- 00000D84 move-result-object v5
- 00000D86 invoke-direct qb-><init>(Context)V, v4, v5
- 00000D8C const-string v5, "fChOdMcDo\u0004yEr" # libengine.sox
- 00000D90 invoke-virtual qb->iiIIIiiiIi([B)V, v4, v1
- 00000D96 invoke-static b->iiIIIiiiIi(String)String, v5
- 00000D9C move-result-object v1
- 00000D9E iget-object v5, p0, AppGuardEngine->IiIIiiiiii_Random_SHA1:String
- 00000DA2 const/4 v6, 0
- 00000DA4 invoke-virtual qb->iiIIIiiiIi(String, String, [B)Z, v4, v1, v5, v6 # 解密libengine.sox(最终传入so层解密private static native byte[] iIiIIIiIiI(byte[] arg0, int arg1))
- :DAA
- 00000DAA move-object v0, p0
- :DAC
- 00000DAC invoke-static JNISoxProxy->getContext()Context
- 00000DB2 move-result-object v1
- 00000DB4 new-instance v4, StringBuilder
- 00000DB8 invoke-direct StringBuilder-><init>()V, v4
- 00000DBE invoke-static JNISoxProxy->getContext()Context
- 00000DC4 move-result-object v5
- 00000DC6 invoke-virtual Context->getFilesDir()File, v5
- 00000DCC move-result-object v5
- 00000DCE invoke-virtual File->getAbsolutePath()String, v5
- 00000DD4 move-result-object v5
- 00000DD6 invoke-virtual StringBuilder->insert(I, String)StringBuilder, v4, v2, v5
- 00000DDC move-result-object v4
- 00000DDE const-string v5, "%" # /
- 00000DE2 invoke-static b->iiIIIiiiIi(String)String, v5
- 00000DE8 move-result-object v5
- 00000DEA invoke-virtual StringBuilder->append(String)StringBuilder, v4, v5
- 00000DF0 move-result-object v4
- 00000DF2 iget-object v5, p0, AppGuardEngine->IiIIiiiiii_Random_SHA1:String
- 00000DF6 invoke-virtual StringBuilder->append(String)StringBuilder, v4, v5
- 00000DFC move-result-object v4
- 00000DFE invoke-virtual StringBuilder->toString()String, v4
- 00000E04 move-result-object v4
- 00000E06 invoke-direct AppGuardEngine->IIIIIIIlIl(Context, String, [B)I, v0, v1, v4, p1 # 将解密后将libengine文件路径传入该Native函数中调用
- 00000E0C move-result v1
- 00000E0E if-gez v1, :E9A
解密后的so会在Native函数中通过dlopen、dlsym来调用。
二: compatible.so反调试与反反调试
1. 反调试 (文件偏移 13284)
- /data/app-lib/com.digitalsky.girlsfrontline.cn-/libcompatible.so 757C8000 0005F000
- .text:757DB284 loc_757DB284 ; CODE XREF: JNI_OnLoad+254↑j
- .text:757DB284 5C E3 CMP R12, #
- .text:757DB288 BA BLT loc_757DB2F0
- .text:757DB28C E2 RSB R3, R8, #
- .text:757DB290 E0 EOR R0, R0, R3
- .text:757DB294 E0 ADD R8, R0, R8
- .text:757DB298 0D E3 CMP R8, #0xD ; 判断SDK版本
- .text:757DB29C 9F FF FF DA BLE loc_757DB120
- .text:757DB2A0
- .text:757DB2A0 loc_757DB2A0 ; CODE XREF: JNI_OnLoad+2E4↓j
- .text:757DB2A0 7D 2B EB BL _Z11lIlIlIIIIIIv ; 创建3进程和多线程反调试
- .text:757DB2A4 E2 SUBS R2, R0, # ; char *
如果SDK大于0XD时就创建3进程与多线程反调试:
- .text:756F84B0 EXPORT _Z11IIIIIIIllllv
- .text:756F84B0 _Z11IIIIIIIllllv ; CODE XREF: JNI_OnLoad:loc_756EE6E4↑p
- .text:756F84B0
- .text:756F84B0 var_2C= -0x2C
- .text:756F84B0 var_28= -0x28
- .text:756F84B0 var_24= -0x24
- .text:756F84B0 var_20= -0x20
- .text:756F84B0
- .text:756F84B0 ; __unwind {
- .text:756F84B0 F0 2D E9 STMFD SP!, {R4-R9,LR}
- .text:756F84B4 C0 9F E5 LDR R4, =(_GLOBAL_OFFSET_TABLE_ - 0x756F84C8)
- .text:756F84B8 C0 9F E5 LDR R2, =(__stack_chk_guard_ptr - 0x7572FED0)
- .text:756F84BC C0 9F E5 LDR R3, =(_ZN6Global10lIlIIllIIlE_ptr - 0x7572FED0)
- .text:756F84C0 8F E0 ADD R4, PC, R4 ; _GLOBAL_OFFSET_TABLE_
- .text:756F84C4 E7 LDR R7, [R4,R2]
- .text:756F84C8 D0 4D E2 SUB SP, SP, #0x14
- .text:756F84CC E5 LDR R2, [R7]
- .text:756F84D0 0C 8D E5 STR R2, [SP,#0x30+var_24]
- .text:756F84D4 E7 LDR R6, [R4,R3]
- .text:756F84D8 A0 E1 MOV R0, R6 ; int *
- .text:756F84DC F2 FF EB BL pipi
- .text:756F84E0 E3 CMP R0, #
- .text:756F84E4 BA BLT loc_756F8538
- .text:756F84E8 E2 ADD R0, R6, # ; int *
- .text:756F84EC 6E F2 FF EB BL pipi
- .text:756F84F0 E3 CMP R0, #
- .text:756F84F4 0F BA BLT loc_756F8538
- .text:756F84F8 E2 ADD R0, R6, #0x48 ; int *
- .text:756F84FC 6A F2 FF EB BL pipi
- .text:756F8500 E3 CMP R0, #
- .text:756F8504 0B BA BLT loc_756F8538
- .text:756F8508 E2 ADD R0, R6, #0x30 ; int *
- .text:756F850C F2 FF EB BL pipi
- .text:756F8510 E3 CMP R0, #
- .text:756F8514 BA BLT loc_756F8538
- .text:756F8518 E2 ADD R0, R6, #0x38 ; int *
- .text:756F851C F2 FF EB BL pipi
- .text:756F8520 E3 CMP R0, #
- .text:756F8524 BA BLT loc_756F8538
- .text:756F8528 E2 ADD R0, R6, #0x40 ; int *
- .text:756F852C 5E F2 FF EB BL pipi
- .text:756F8530 E3 CMP R0, #
- .text:756F8534 AA BGE loc_756F8540
- .text:756F8538
- .text:756F8538 loc_756F8538 ; CODE XREF: IIIIIIIllll(void)+34↑j
- .text:756F8538 ; IIIIIIIllll(void)+44↑j ...
- .text:756F8538 A0 E3 MOV R0, # ; int
- .text:756F853C 4E F2 FF EB BL _Z10llIIlIIIlli ; llIIlIIIll(int)
- .text:756F8540
- .text:756F8540 loc_756F8540 ; CODE XREF: IIIIIIIllll(void)+84↑j
- .text:756F8540 A0 E3 MOV R1, #
- .text:756F8544 A0 E3 MOV R0, # ; option
- .text:756F8548 AF CB FF EB BL prctl
- .text:756F854C F2 FF EB BL getpid_0
- .text:756F8550 9F E5 LDR R3, =(_ZN6Global10lIllllIllIE_ptr - 0x7572FED0)
- .text:756F8554 E7 LDR R5, [R4,R3]
- .text:756F8558 E5 STR R0, [R5] ; Global::lIllllIllI
- .text:756F855C F2 FF EB BL fork
- .text:756F8560 E3 CMN R0, #
- .text:756F8564 E5 STR R0, [R5,#(dword_757309F4 - 0x757309F0)]
- .text:756F8568 0A BEQ loc_756F87B8
- .text:756F856C
- .text:756F856C loc_756F856C ; CODE XREF: IIIIIIIllll(void)+314↓j
- .text:756F856C E3 CMP R0, #
- .text:756F8570 DA BLE loc_756F8648
- .text:756F8574 A0 E3 MOV R8, #
- .text:756F8578 A0 E3 MOV R9, #
- .text:756F857C 9F E5 LDR R3, =(_ZN6Global10IIlIIlIIlIE_ptr - 0x7572FED0)
- .text:756F8580 8D E2 ADD R1, SP, #0x30+var_20
- .text:756F8584 E5 LDR R0, [R6,#(dword_75730EBC - 0x75730E84)] ; int
- .text:756F8588 E7 LDR R3, [R4,R3]
- .text:756F858C A0 E3 MOV R2, # ; unsigned int
- .text:756F8590 E5 STR R8, [R1,#-0x10]!
- .text:756F8594 C3 E5 STRB R9, [R3] ; Global::IIlIIlIIlI
- .text:756F8598 7B F2 FF EB BL read
- .text:756F859C EC 9F E5 LDR R1, =(_ZN6Global6ThreadE_ptr - 0x7572FED0)
- .text:756F85A0 EC 9F E5 LDR R2, =(_Z10IlIIlllIIlPv_ptr - 0x7572FED0)
- .text:756F85A4 E2 ADD R3, R5, # ; void *
- .text:756F85A8 E7 LDR R6, [R4,R1]
- .text:756F85AC E7 LDR R2, [R4,R2] ; void *(__cdecl *)(void *)
- .text:756F85B0 A0 E1 MOV R1, R8 ; pthread_attr_t *
- .text:756F85B4 A0 E1 MOV R0, R6 ; int *
- .text:756F85B8 6D F1 FF EB BL pthread_create_0
- .text:756F85BC E1 CMP R0, R8
- .text:756F85C0 BA BLT loc_756F87C8
- .text:756F85C4
- .text:756F85C4 loc_756F85C4 ; CODE XREF: IIIIIIIllll(void)+334↓j
- .text:756F85C4 CC 9F E5 LDR R3, =(_Z10IIlIlllllIPv_ptr - 0x7572FED0)
- .text:756F85C8 E2 ADD R0, R6, # ; int *
- .text:756F85CC A0 E3 MOV R1, # ; pthread_attr_t *
- .text:756F85D0 E7 LDR R2, [R4,R3] ; void *(__cdecl *)(void *)
- .text:756F85D4 A0 E3 MOV R3, # ; void *
- .text:756F85D8 F1 FF EB BL pthread_create_0
- .text:756F85DC E3 CMP R0, #
- .text:756F85E0 6C BA BLT loc_756F8798
- .text:756F85E4
- .text:756F85E4 loc_756F85E4 ; CODE XREF: IIIIIIIllll(void)+304↓j
- .text:756F85E4 A0 E3 MOV R1, # ; pthread_attr_t *
- .text:756F85E8 AC 9F E5 LDR R2, =(_Z11IIIlllIIIIIPv_ptr - 0x7572FED0)
- .text:756F85EC A0 E1 MOV R3, R1 ; void *
- .text:756F85F0 E7 LDR R2, [R4,R2] ; void *(__cdecl *)(void *)
- .text:756F85F4 E2 ADD R0, R6, #0x10 ; int *
- .text:756F85F8 5D F1 FF EB BL pthread_create_0
- .text:756F85FC A0 E3 MOV R1, # ; pthread_attr_t *
- .text:756F8600 9F E5 LDR R2, =(_Z11IIIlIIlIllIPv_ptr - 0x7572FED0)
- .text:756F8604 A0 E1 MOV R3, R1 ; void *
- .text:756F8608 E7 LDR R2, [R4,R2] ; void *(__cdecl *)(void *)
- .text:756F860C 8D E2 ADD R0, SP, #0x30+var_2C ; int *
- .text:756F8610 F1 FF EB BL pthread_create_0
- .text:756F8614 9F E5 LDR R3, =(_Z10IIllIIlIlIPv_ptr - 0x7572FED0)
- .text:756F8618 8D E2 ADD R0, SP, #0x30+var_28 ; int *
- .text:756F861C A0 E3 MOV R1, # ; pthread_attr_t *
- .text:756F8620 E7 LDR R2, [R4,R3] ; void *(__cdecl *)(void *)
- .text:756F8624 A0 E3 MOV R3, # ; void *
- .text:756F8628 F1 FF EB BL pthread_create_0
- .text:756F862C
- .text:756F862C loc_756F862C ; CODE XREF: IIIIIIIllll(void)+250↓j
- .text:756F862C 0C 9D E5 LDR R2, [SP,#0x30+var_24]
- .text:756F8630 E5 LDR R3, [R7]
- .text:756F8634 A0 E3 MOV R0, #
- .text:756F8638 E1 CMP R2, R3
- .text:756F863C 8D 1A BNE loc_756F8878
- .text:756F8640 D0 8D E2 ADD SP, SP, #0x14
- .text:756F8644 F0 BD E8 LDMFD SP!, {R4-R9,PC}
- .text:756F8648 ; ---------------------------------------------------------------------------
- .text:756F8648
- .text:756F8648 loc_756F8648 ; CODE XREF: IIIIIIIllll(void)+C0↑j
- .text:756F8648 CB FF EB BL getpid
- .text:756F864C E5 STR R0, [R5,#(dword_757309F4 - 0x757309F0)]
- .text:756F8650 F2 FF EB BL fork
- .text:756F8654 E2 ADD R1, R5, # ; void *
- .text:756F8658 E5 STR R0, [R5,#(dword_757309F8 - 0x757309F0)]
- .text:756F865C A0 E3 MOV R2, # ; unsigned int
- .text:756F8660 3C E5 LDR R0, [R6,#(dword_75730EC0 - 0x75730E84)] ; int
- .text:756F8664 F2 FF EB BL write_0
- .text:756F8668 E5 LDR R3, [R5,#(dword_757309F8 - 0x757309F0)]
- .text:756F866C E3 CMN R3, #
- .text:756F8670 0A BEQ loc_756F8808
- .text:756F8674
- .text:756F8674 loc_756F8674 ; CODE XREF: IIIIIIIllll(void)+364↓j
- .text:756F8674 E3 CMP R3, #
- .text:756F8678 A0 E3 MOV R0, # ; option
- .text:756F867C A0 E3 MOV R1, #
- .text:756F8680 1F DA BLE loc_756F8704
- .text:756F8684 CB FF EB BL prctl
- .text:756F8688 9F E5 LDR R1, =(_ZN6Global6ThreadE_ptr - 0x7572FED0)
- .text:756F868C 9F E5 LDR R2, =(_Z10IlIIlllIIlPv_ptr - 0x7572FED0)
- .text:756F8690 E2 ADD R3, R5, # ; void *
- .text:756F8694 E7 LDR R6, [R4,R1]
- .text:756F8698 E7 LDR R2, [R4,R2] ; void *(__cdecl *)(void *)
- .text:756F869C A0 E3 MOV R1, # ; pthread_attr_t *
- .text:756F86A0 A0 E1 MOV R0, R6 ; int *
- .text:756F86A4 F1 FF EB BL pthread_create_0
- .text:756F86A8 E3 CMP R0, #
- .text:756F86AC BA BLT loc_756F8818
- .text:756F86B0
- .text:756F86B0 loc_756F86B0 ; CODE XREF: IIIIIIIllll(void)+384↓j
- .text:756F86B0 E0 9F E5 LDR R3, =(_Z10IIlIlllllIPv_ptr - 0x7572FED0)
- .text:756F86B4 E2 ADD R0, R6, # ; int *
- .text:756F86B8 A0 E3 MOV R1, # ; pthread_attr_t *
- .text:756F86BC E7 LDR R2, [R4,R3] ; void *(__cdecl *)(void *)
- .text:756F86C0 A0 E3 MOV R3, # ; void *
- .text:756F86C4 2A F1 FF EB BL pthread_create_0
- .text:756F86C8 E3 CMP R0, #
- .text:756F86CC BA BLT loc_756F87E8
- .text:756F86D0
- .text:756F86D0 loc_756F86D0 ; CODE XREF: IIIIIIIllll(void)+354↓j
- .text:756F86D0 CC 9F E5 LDR R3, =(_Z10IIllIIlIlIPv_ptr - 0x7572FED0)
- .text:756F86D4 A0 E3 MOV R1, # ; pthread_attr_t *
- .text:756F86D8 E7 LDR R2, [R4,R3] ; void *(__cdecl *)(void *)
- .text:756F86DC A0 E3 MOV R3, # ; void *
- .text:756F86E0 8D E2 ADD R0, SP, #0x30+var_28 ; int *
- .text:756F86E4
- .text:756F86E4 loc_756F86E4 ; CODE XREF: IIIIIIIllll(void)+2E4↓j
- .text:756F86E4 F1 FF EB BL pthread_create_0
- .text:756F86E8 9D E5 LDR R0, [SP,#0x30+var_28] ; int
- .text:756F86EC A0 E3 MOV R1, # ; void **
- .text:756F86F0 A9 F1 FF EB BL pthread_join
- .text:756F86F4 E5 LDR R0, [R6] ; int
- .text:756F86F8 A0 E3 MOV R1, # ; void **
- .text:756F86FC A6 F1 FF EB BL pthread_join
- .text:756F8700 C9 FF FF EA B loc_756F862C
- .text:756F8704 ; ---------------------------------------------------------------------------
- .text:756F8704
- .text:756F8704 loc_756F8704 ; CODE XREF: IIIIIIIllll(void)+1D0↑j
- .text:756F8704 CB FF EB BL prctl
- .text:756F8708 F2 FF EB BL getpid_0
- .text:756F870C A0 E1 MOV R1, R5
- .text:756F8710 A0 E3 MOV R2, # ; unsigned int
- .text:756F8714 A1 E5 STR R0, [R1,#(dword_757309F8 - 0x757309F0)]!
- .text:756F8718 E5 LDR R0, [R6,#(dword_75730EB8 - 0x75730E84)] ; int
- .text:756F871C F2 FF EB BL write_0
- .text:756F8720 9F E5 LDR R2, =(_ZN6Global6ThreadE_ptr - 0x7572FED0)
- .text:756F8724 9F E5 LDR R3, =(_Z10IlIIlllIIlPv_ptr - 0x7572FED0)
- .text:756F8728 A0 E3 MOV R1, # ; pthread_attr_t *
- .text:756F872C E7 LDR R6, [R4,R2]
- .text:756F8730 E7 LDR R2, [R4,R3] ; void *(__cdecl *)(void *)
- .text:756F8734 A0 E1 MOV R3, R5 ; void *
- .text:756F8738 A0 E1 MOV R0, R6 ; int *
- .text:756F873C 0C F1 FF EB BL pthread_create_0
- .text:756F8740 E3 CMP R0, #
- .text:756F8744 BA BLT loc_756F8858
- .text:756F8748
- .text:756F8748 loc_756F8748 ; CODE XREF: IIIIIIIllll(void)+3C4↓j
- .text:756F8748 A0 E3 MOV R1, # ; pthread_attr_t *
- .text:756F874C 9F E5 LDR R2, =(_Z10IIlIlllllIPv_ptr - 0x7572FED0)
- .text:756F8750 A0 E1 MOV R3, R1 ; void *
- .text:756F8754 E7 LDR R2, [R4,R2] ; void *(__cdecl *)(void *)
- .text:756F8758 E2 ADD R0, R6, # ; int *
- .text:756F875C F1 FF EB BL pthread_create_0
- .text:756F8760 E3 CMP R0, #
- .text:756F8764 BA BLT loc_756F8838
- .text:756F8768
- .text:756F8768 loc_756F8768 ; CODE XREF: IIIIIIIllll(void)+3A4↓j
- .text:756F8768 A0 E3 MOV R1, # ; pthread_attr_t *
- .text:756F876C 9F E5 LDR R2, =(_Z10IIllIIlIlIPv_ptr - 0x7572FED0)
- .text:756F8770 A0 E1 MOV R3, R1 ; void *
- .text:756F8774 E7 LDR R2, [R4,R2] ; void *(__cdecl *)(void *)
- .text:756F8778 8D E2 ADD R0, SP, #0x30+var_28 ; int *
- .text:756F877C FC F0 FF EB BL pthread_create_0
- .text:756F8780 9F E5 LDR R2, =(_Z11IlIIllIIlIlPv_ptr - 0x7572FED0)
- .text:756F8784 A0 E1 MOV R3, R5
- .text:756F8788 E7 LDR R2, [R4,R2]
- .text:756F878C A0 E1 MOV R0, R6
- .text:756F8790 A0 E3 MOV R1, #
- .text:756F8794 D2 FF FF EA B loc_756F86E4
- .text:756F8798 ; ---------------------------------------------------------------------------
- .text:756F8798
- .text:756F8798 loc_756F8798 ; CODE XREF: IIIIIIIllll(void)+130↑j
- .text:756F8798 A0 E3 MOV R0, # ; int
- .text:756F879C 0E A0 E3 MOV R1, #0xE ; int
- .text:756F87A0 A0 E1 MOV R3, R0 ; int
- .text:756F87A4 A0 E3 MOV R2, # ; char *
- .text:756F87A8 DB EB BL _Z10IIIIIllIIliiPKci ; IIIIIllIIl(int,int,char const*,int)
- .text:756F87AC A0 E3 MOV R0, # ; int
- .text:756F87B0 B1 F1 FF EB BL _Z10llIIlIIIlli ; llIIlIIIll(int)
- .text:756F87B4 8A FF FF EA B loc_756F85E4
- .text:756F87B8 ; ---------------------------------------------------------------------------
- .text:756F87B8
- .text:756F87B8 loc_756F87B8 ; CODE XREF: IIIIIIIllll(void)+B8↑j
- .text:756F87B8 A0 E3 MOV R0, # ; int
- .text:756F87BC AE F1 FF EB BL _Z10llIIlIIIlli ; llIIlIIIll(int)
- .text:756F87C0 E5 LDR R0, [R5,#(dword_757309F4 - 0x757309F0)]
- .text:756F87C4 FF FF EA B loc_756F856C
- .text:756F87C8 ; ---------------------------------------------------------------------------
- .text:756F87C8
- .text:756F87C8 loc_756F87C8 ; CODE XREF: IIIIIIIllll(void)+110↑j
- .text:756F87C8 A0 E1 MOV R0, R9 ; int
- .text:756F87CC A0 E1 MOV R2, R8 ; char *
- .text:756F87D0 0D A0 E3 MOV R1, #0xD ; int
- .text:756F87D4 A0 E1 MOV R3, R9 ; int
- .text:756F87D8 CF EB BL _Z10IIIIIllIIliiPKci ; IIIIIllIIl(int,int,char const*,int)
- .text:756F87DC A0 E1 MOV R0, R9 ; int
- .text:756F87E0 A5 F1 FF EB BL _Z10llIIlIIIlli ; llIIlIIIll(int)
- .text:756F87E4 FF FF EA B loc_756F85C4
- .text:756F87E8 ; ---------------------------------------------------------------------------
- .text:756F87E8
- .text:756F87E8 loc_756F87E8 ; CODE XREF: IIIIIIIllll(void)+21C↑j
- .text:756F87E8 A0 E3 MOV R0, # ; int
- .text:756F87EC 0E A0 E3 MOV R1, #0xE ; int
- .text:756F87F0 A0 E1 MOV R3, R0 ; int
- .text:756F87F4 A0 E3 MOV R2, # ; char *
- .text:756F87F8 C7 EB BL _Z10IIIIIllIIliiPKci ; IIIIIllIIl(int,int,char const*,int)
- .text:756F87FC A0 E3 MOV R0, # ; int
- .text:756F8800 9D F1 FF EB BL _Z10llIIlIIIlli ; llIIlIIIll(int)
- .text:756F8804 B1 FF FF EA B loc_756F86D0
- .text:756F8808 ; ---------------------------------------------------------------------------
- .text:756F8808
- .text:756F8808 loc_756F8808 ; CODE XREF: IIIIIIIllll(void)+1C0↑j
- .text:756F8808 A0 E3 MOV R0, # ; int
- .text:756F880C 9A F1 FF EB BL _Z10llIIlIIIlli ; llIIlIIIll(int)
- .text:756F8810 E5 LDR R3, [R5,#(dword_757309F8 - 0x757309F0)]
- .text:756F8814 FF FF EA B loc_756F8674
- .text:756F8818 ; ---------------------------------------------------------------------------
- .text:756F8818
- .text:756F8818 loc_756F8818 ; CODE XREF: IIIIIIIllll(void)+1FC↑j
- .text:756F8818 A0 E3 MOV R0, # ; int
- .text:756F881C 0D A0 E3 MOV R1, #0xD ; int
- .text:756F8820 A0 E1 MOV R3, R0 ; int
- .text:756F8824 A0 E3 MOV R2, # ; char *
- .text:756F8828 BB EB BL _Z10IIIIIllIIliiPKci ; IIIIIllIIl(int,int,char const*,int)
- .text:756F882C A0 E3 MOV R0, # ; int
- .text:756F8830 F1 FF EB BL _Z10llIIlIIIlli ; llIIlIIIll(int)
- .text:756F8834 9D FF FF EA B loc_756F86B0
- .text:756F8838 ; ---------------------------------------------------------------------------
- .text:756F8838
- .text:756F8838 loc_756F8838 ; CODE XREF: IIIIIIIllll(void)+2B4↑j
- .text:756F8838 A0 E3 MOV R0, # ; int
- .text:756F883C 0E A0 E3 MOV R1, #0xE ; int
- .text:756F8840 A0 E1 MOV R3, R0 ; int
- .text:756F8844 A0 E3 MOV R2, # ; char *
- .text:756F8848 B3 EB BL _Z10IIIIIllIIliiPKci ; IIIIIllIIl(int,int,char const*,int)
- .text:756F884C A0 E3 MOV R0, # ; int
- .text:756F8850 F1 FF EB BL _Z10llIIlIIIlli ; llIIlIIIll(int)
- .text:756F8854 C3 FF FF EA B loc_756F8768
- .text:756F8858 ; ---------------------------------------------------------------------------
- .text:756F8858
- .text:756F8858 loc_756F8858 ; CODE XREF: IIIIIIIllll(void)+294↑j
- .text:756F8858 A0 E3 MOV R0, # ; int
- .text:756F885C 0D A0 E3 MOV R1, #0xD ; int
- .text:756F8860 A0 E1 MOV R3, R0 ; int
- .text:756F8864 A0 E3 MOV R2, # ; char *
- .text:756F8868 AB EB BL _Z10IIIIIllIIliiPKci ; IIIIIllIIl(int,int,char const*,int)
- .text:756F886C A0 E3 MOV R0, # ; int
- .text:756F8870 F1 FF EB BL _Z10llIIlIIIlli ; llIIlIIIll(int)
- .text:756F8874 B3 FF FF EA B loc_756F8748
2.反反调试
过3进程互相调试我是通过hook ptrace直接让它返回0,多线程循环读取进程状态判断是否有调试器,我是通过hook open 函数过虑掉,还有就是直接让SDK版本小于0XD,或者直接NOP掉函数。
- int new_ptrace(int request, int pid, int addr, int data){
- //LOGD("new_ptrace..");
- return ;
- }
- int new_open(char *pathname, int oflag, mode_t mode)
- {
- char* anit = "stat";
- char* tmp = "";
- if (NULL == pathname)
- {
- goto exitret;
- }
- //LOGD("new_open..%s", pathname);
- if(strstr(pathname, anit) != NULL)
- {
- return -;
- }
- exitret:
- return old_open(pathname, oflag, mode);
- }
三: compatible.so注册jni函数分析
1.获取动态jni注册函数
通过在dvmUseJNIBridge函数下好断点,来获取注册的jni函数地址,最后注册完后对照表:
注册类名com/inca/security/Core/AppGuardEngine
/data/app-lib/com.digitalsky.girlsfrontline.cn-1/libcompatible.so 757C8000 0005F000
Number 内存地址 函数名 文件偏移 签名
第1个函数 .text:757D9AF8 IiiiIIiIii (文件偏移 11AF8) ()I
第2个函数 .text:757DA058 iIiIIIiIiI (文件偏移 12058) ([BI)[B
第3个函数 .text:757DC268 IiIiiIiIiI (文件偏移 14268) (Landroid/content/Context;)V
第4个函数 .text:757D9914 IIiIiIIIiI (文件偏移 11914) (I)V
第5个函数 .text:757D8A28 IIIIiIIIiI (文件偏移 10A28) (J)V
2. jni函数功能分析
当JNI_OnLoad函数执行完后第一个执行的jni函数是上面注册的第3个函数, 反射获取包名与签名等。
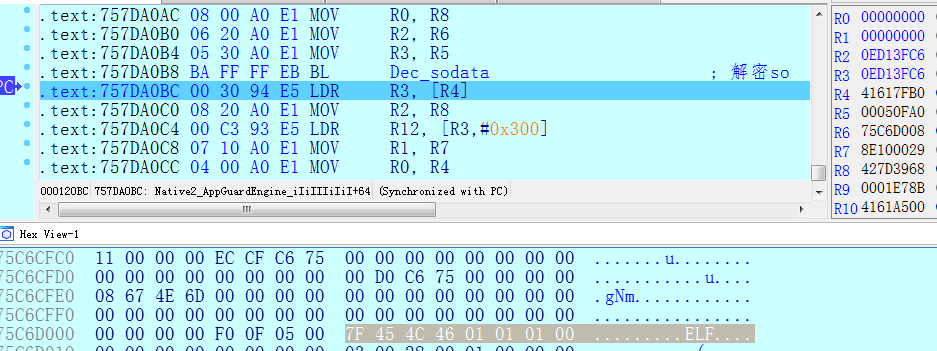
第2个jni函数就是解密libengine.sox与libstub.sox,(assets\appguard\armeabi\)先在上面java层分析时AES解密后数据传入的就是这个函数 (文件偏移 12058)。
- .text:757DA058 ; __unwind {
- .text:757DA058 F0 2D E9 STMFD SP!, {R4-R9,LR}
- .text:757DA05C A0 E1 MOV R7, R2
- .text:757DA060 E5 LDR R2, [R0]
- .text:757DA064 A0 E1 MOV R4, R0
- .text:757DA068 0C D0 4D E2 SUB SP, SP, #0xC
- .text:757DA06C A0 E1 MOV R1, R7
- .text:757DA070 AC E5 LDR R2, [R2,#0x2AC]
- .text:757DA074 A0 E1 MOV R5, R3
- .text:757DA078 FF 2F E1 BLX R2
- .text:757DA07C E5 LDR R3, [R4]
- .text:757DA080 A0 E1 MOV R1, R7
- .text:757DA084 A0 E1 MOV R9, R0
- .text:757DA088 E0 E5 LDR R3, [R3,#0x2E0]
- .text:757DA08C A0 E3 MOV R2, #
- .text:757DA090 A0 E1 MOV R0, R4
- .text:757DA094 FF 2F E1 BLX R3
- .text:757DA098 A0 E1 MOV R8, R0
- .text:757DA09C A0 E1 MOV R0, R5 ; unsigned int
- .text:757DA0A0 1E EB BL malloc_0 ; 分配存放空间存放解密后so数据
- .text:757DA0A4 A0 E1 MOV R6, R0
- .text:757DA0A8 A0 E1 MOV R1, R9
- .text:757DA0AC A0 E1 MOV R0, R8
- .text:757DA0B0 A0 E1 MOV R2, R6
- .text:757DA0B4 A0 E1 MOV R3, R5
- .text:757DA0B8 BA FF FF EB BL Dec_sodata ; 解密so
- .text:757DA0BC E5 LDR R3, [R4]
- .text:757DA0C0 A0 E1 MOV R2, R8
- .text:757DA0C4 C3 E5 LDR R12, [R3,#0x300]
- .text:757DA0C8 A0 E1 MOV R1, R7
- .text:757DA0CC A0 E1 MOV R0, R4
- .text:757DA0D0 A0 E3 MOV R3, #
- .text:757DA0D4 3C FF 2F E1 BLX R12
- .text:757DA0D8 E5 LDR R3, [R4]
- .text:757DA0DC A0 E1 MOV R1, R5
- .text:757DA0E0 A0 E1 MOV R0, R4
- .text:757DA0E4 C0 E5 LDR R3, [R3,#0x2C0]
- .text:757DA0E8 FF 2F E1 BLX R3
- .text:757DA0EC A0 E1 MOV R7, R0
- .text:757DA0F0 E5 LDR R2, [R4]
- .text:757DA0F4 8D E5 STR R6, [SP,#0x28+var_28]
- .text:757DA0F8 A0 E1 MOV R3, R5
- .text:757DA0FC C3 E5 LDR R12, [R2,#0x340]
- .text:757DA100 A0 E1 MOV R0, R4
- .text:757DA104 A0 E1 MOV R1, R7
- .text:757DA108 A0 E3 MOV R2, #
- .text:757DA10C 3C FF 2F E1 BLX R12
- .text:757DA110 A0 E1 MOV R0, R6 ; ptr
- .text:757DA114 DD F6 FF EB BL free
- .text:757DA118 A0 E1 MOV R0, R7
- .text:757DA11C 0C D0 8D E2 ADD SP, SP, #0xC
- .text:757DA120 F0 BD E8 LDMFD SP!, {R4-R9,PC}
- 解密完后R5是大小,R6基址,将其dump出来,如下图所示:
- static main(void)
- {
- auto fp, begin, end, dexbyte;
- fp = fopen("d:\\libstub.so", "wb"); //打开或创建一个文件
- begin = R6; //so基址
- end = begin + R5; //so基址 + so文件大小
- for ( dexbyte = begin; dexbyte < end;dexbyte ++ )
- {
- fputc(Byte(dexbyte), fp); //按字节将其dump到本地文件中
- }
- }
libstub.sox解密后将最终的明文写到/data/data/包名/files/libstub.so目录下,后然加载,接下来分析libstub.so。
四: stub.so反调试与反反调试
1.反调试在JNI_onLoad中读取进程状态,前面通过hook open函数己过了反调试。
五: stub.so注册jni函数分析
1.注册jni
通过在dvmUseJNIBridge函数下好断点,来获取注册的jni函数地址,最后注册完后对照表:
注册类名com/inca/security/Core/UnsafeDexLoader
/data/data/com.digitalsky.girlsfrontline.cn/files/libstub.so 75C6E000 00052000
Number 内存地址 函数名 文件偏移 签名
第1个函数 .text:75C80704 IlIIIIIIII (文件偏移 12704) (Ljava/lang/String;Ljava/lang/String;I)I
第2个函数 .text:75C808C4 IIIIIIIIIl (文件偏移 128C4) ([B)I
第3个函数 .text:75C80A7C IIIIIIIIlI (文件偏移 12A7C) (Ljava/lang/String;Ljava/lang/ClassLoader;I)Ljava/lang/Class;
第4个函数 .text:75C80C3C IIIIIIIIll (文件偏移 12C3C) (I)[Ljava/lang/String;
第5个函数 .text:75C80DF4 IIIIIIIlII (文件偏移 12DF4) (I)V
//
注册类名com/inca/security/Core/AppGuardEngine
/data/data/com.digitalsky.girlsfrontline.cn/files/libstub.so 75C6E000 00052000
Number 内存地址 函数名 文件偏移 签名
第1个函数 .text:75C81168 IlIIIIIIII (文件偏移 13168) (Landroid/content/Context;Ljava/lang/String;[B)I
第2个函数 .text:75C814AC IIIIIIIllI (文件偏移 134AC) ()V
第3个函数 .text:75C81618 IIIIIIIlll (文件偏移 13618) (I[B[B)I
第4个函数 .text:75C81724 IIIIIIlIII (文件偏移 13724) (I[B[B)I
第5个函数 .text:75C817CC IIIIIIIlII (文件偏移 137CC) (I[B[B)I
第6个函数 .text:75C8186C IllIIIlIII (文件偏移 1386C) (I)I
第7个函数 .text:75C818AC IIIIIIlIlI (文件偏移 138AC) (I)I
第8个函数 .text:75C81810 llIIIIlIIl (文件偏移 13810) (I[B)I
第9个函数 .text:75C81844 IlIIIIlllI (文件偏移 13844) (Z)V
第10个函数 .text:75C81D10 lllIIIlllI (文件偏移 13D10) (Landroid/content/Context;)V
注册类名com/inca/security/AppGuard/TestCase
/data/data/com.digitalsky.girlsfrontline.cn/files/libstub.so 75C6E000 00052000
第1个函数 .text:75C82608 IIIIIIlIll (文件偏移 14608) (Landroid/content/Context;Z)Z
第2个函数 .text:75C8267C IIIIIIllII (文件偏移 1467C) (Landroid/content/Context;)Z
第3个函数 .text:75C826F0 IIIIIIllIl (文件偏移 146F0) (Landroid/content/Context;)Z
第4个函数 .text:75C82764 IIIIIIlllI (文件偏移 14764) (Landroid/content/Context;)Z
2.在com/inca/security/Core/AppGuardEngine类中第10个函数jni函数中hook mono函数 (文件偏移 18D04)
- /data/data/com.digitalsky.girlsfrontline.cn/files/libstub.so 75C6E000
- .text:75C86D04 EXPORT hook_mono_func
- .text:75C86D04 hook_mono_func ; CODE XREF: Hook_Thread+4↑p
- .text:75C86D04
- .text:75C86D04 var_280= -0x280
- .text:75C86D04 var_27C= -0x27C
- .text:75C86D04 var_278= -0x278
- .text:75C86D04 format= -0x274
- .text:75C86D04 var_26C= -0x26C
- .text:75C86D04 var_24C= -0x24C
- .text:75C86D04 s= -0x22C
- .text:75C86D04 var_12C= -0x12C
- .text:75C86D04 var_2C= -0x2C
- .text:75C86D04
- .text:75C86D04 ; __unwind { // 75C9B220
- .text:75C86D04 F0 4F 2D E9 STMFD SP!, {R4-R11,LR}
- .text:75C86D08 9F E5 LDR R5, =(_GLOBAL_OFFSET_TABLE_ - 0x75C86D1C)
- .text:75C86D0C 9F E5 LDR R3, =(__stack_chk_guard_ptr - 0x75CBEEC0)
- .text:75C86D10 DF 4D E2 SUB SP, SP, #0x25C
- .text:75C86D14 8F E0 ADD R5, PC, R5 ; _GLOBAL_OFFSET_TABLE_
- .text:75C86D18 A0 E7 LDR R10, [R5,R3]
- .text:75C86D1C 8D E2 ADD R8, SP, #0x280+s
- .text:75C86D20 A0 E3 MOV R1, # ; c
- .text:75C86D24 9A E5 LDR R3, [R10]
- .text:75C86D28 FF A0 E3 MOV R2, #0xFF ; n
- .text:75C86D2C A0 E1 MOV R0, R8 ; s
- .text:75C86D30 8D E5 STR R3, [SP,#0x280+var_2C]
- .text:75C86D34 D7 FF EB BL memset
- .text:75C86D38 E0 9F E5 LDR R1, =(unk_75CB8B70 - 0x75C86D4C)
- .text:75C86D3C 8D E2 ADD R4, SP, #0x280+var_24C
- .text:75C86D40 A0 E1 MOV R0, R4 ; this
- .text:75C86D44 8F E0 ADD R1, PC, R1 ; unk_75CB8B70
- .text:75C86D48 F0 E2 ADD R1, R1, #0xF0 ; char *
- .text:75C86D4C F8 FF EB BL DecString
- .text:75C86D50 A0 E1 MOV R0, R4
- .text:75C86D54 F7 FF EB BL _ZN10lIIIlIlIIlcvPcEv ; lIIIlIlIIl::operator char *(void)
- .text:75C86D58 A0 E3 MOV R1, # ; mode
- .text:75C86D5C D7 FF EB BL dlopen
- .text:75C86D60 A0 E1 MOV R6, R0
- .text:75C86D64 A0 E1 MOV R0, R4 ; this
- .text:75C86D68 F7 FF EB BL _ZN10lIIIlIlIIlD2Ev ; lIIIlIlIIl::~lIIIlIlIIl()
- .text:75C86D6C B0 9F E5 LDR R1, =(unk_75CB8B70 - 0x75C86D80)
- .text:75C86D70 E3 CMP R6, #
- .text:75C86D74 A0 E1 MOV R0, R4 ; this
- .text:75C86D78 8F E0 ADD R1, PC, R1 ; unk_75CB8B70
- .text:75C86D7C 1D E2 ADD R1, R1, #0x140 ; char *
- .text:75C86D80 E0 MOVEQ R6, #0xFFFFFFFF
- .text:75C86D84 F8 FF EB BL DecString
- .text:75C86D88 A0 E1 MOV R0, R4
- .text:75C86D8C F7 FF EB BL _ZN10lIIIlIlIIlcvPcEv ; lIIIlIlIIl::operator char *(void)
- .text:75C86D90 A0 E1 MOV R1, R0 ; name
- .text:75C86D94 A0 E1 MOV R0, R6 ; handle
- .text:75C86D98 F8 D6 FF EB BL dlsym
- .text:75C86D9C A0 E1 MOV R6, R0
- .text:75C86DA0 A0 E1 MOV R0, R4 ; this
- .text:75C86DA4 F7 FF EB BL _ZN10lIIIlIlIIlD2Ev ; lIIIlIlIIl::~lIIIlIlIIl()
- .text:75C86DA8 E3 CMP R6, #
- .text:75C86DAC 0A BEQ loc_75C86DB8
- .text:75C86DB0 FF 2F E1 BLX R6
- .text:75C86DB4 A0 E1 MOV R6, R0
- .text:75C86DB8
- .text:75C86DB8 loc_75C86DB8 ; CODE XREF: hook_mono_func+A8↑j
- .text:75C86DB8 A0 E1 MOV R0, R6 ; unsigned int
- .text:75C86DBC EB BL _Z11llllIIlllIlj ; libil2cpp.so没有
- .text:75C86DC0 9F E5 LDR R1, =(unk_75CB8B70 - 0x75C86DD4)
- .text:75C86DC4 8D E2 ADD R7, SP, #0x280+var_26C
- .text:75C86DC8 A0 E1 MOV R0, R7 ; this
- .text:75C86DCC 8F E0 ADD R1, PC, R1 ; unk_75CB8B70
- .text:75C86DD0 1E E2 ADD R1, R1, #0x190 ; char *
- .text:75C86DD4 F8 FF EB BL DecString
- .text:75C86DD8 A0 E1 MOV R0, R7
- .text:75C86DDC F7 FF EB BL _ZN10lIIIlIlIIlcvPcEv ; lIIIlIlIIl::operator char *(void)
- .text:75C86DE0 9F E5 LDR R1, =(unk_75CB8B70 - 0x75C86DF0)
- .text:75C86DE4 A0 E1 MOV R9, R0
- .text:75C86DE8 8F E0 ADD R1, PC, R1 ; unk_75CB8B70
- .text:75C86DEC A0 E1 MOV R0, R4 ; this
- .text:75C86DF0 1E 1E E2 ADD R1, R1, #0x1E0 ; char *
- .text:75C86DF4 F8 FF EB BL DecString
- .text:75C86DF8 A0 E1 MOV R0, R4
- .text:75C86DFC 3D F7 FF EB BL _ZN10lIIIlIlIIlcvPcEv ; lIIIlIlIIl::operator char *(void)
- .text:75C86E00 9F E5 LDR R2, =(_ZN6Global10llIllllIlIE_ptr - 0x75CBEEC0)
- .text:75C86E04 A0 E1 MOV R3, R0
- .text:75C86E08 E7 LDR R2, [R5,R2]
- .text:75C86E0C A0 E1 MOV R1, R9 ; format
- .text:75C86E10 A0 E1 MOV R0, R8 ; s
- .text:75C86E14 8D E5 STR R2, [SP,#0x280+var_280]
- .text:75C86E18 F9 D6 FF EB BL sprintf
- .text:75C86E1C A0 E1 MOV R0, R4 ; this
- .text:75C86E20 F7 FF EB BL _ZN10lIIIlIlIIlD2Ev ; lIIIlIlIIl::~lIIIlIlIIl()
- .text:75C86E24 A0 E1 MOV R0, R7 ; this
- .text:75C86E28 F7 FF EB BL _ZN10lIIIlIlIIlD2Ev ; lIIIlIlIIl::~lIIIlIlIIl()
- .text:75C86E2C A0 E1 MOV R0, R8 ; file
- .text:75C86E30 A0 E3 MOV R1, # ; mode
- .text:75C86E34 DD D6 FF EB BL dlopen ; 打开libmono.so
- .text:75C86E38 E2 SUBS R9, R0, #
- .text:75C86E3C 5B 0A BEQ loc_75C86FB0
- .text:75C86E40 EC 9F E5 LDR R1, =(unk_75CB8B70 - 0x75C86E50)
- .text:75C86E44 A0 E1 MOV R0, R4 ; this
- .text:75C86E48 8F E0 ADD R1, PC, R1 ; unk_75CB8B70
- .text:75C86E4C 1E E2 ADD R1, R1, #0x230 ; char *
- .text:75C86E50 F8 FF EB BL DecString
- .text:75C86E54 A0 E1 MOV R0, R4
- .text:75C86E58 F7 FF EB BL _ZN10lIIIlIlIIlcvPcEv ; lIIIlIlIIl::operator char *(void)
- .text:75C86E5C A0 E1 MOV R1, R0 ; name
- .text:75C86E60 A0 E1 MOV R0, R9 ; handle
- .text:75C86E64 C5 D6 FF EB BL dlsym ; 获取mono_assembly_load_from_full地址
- .text:75C86E68 C8 9F E5 LDR R3, =(IIlIlIIllll_ptr - 0x75CBEEC0)
- .text:75C86E6C C8 9F E5 LDR R2, =(dword_75CC0068 - 0x75C86E7C)
- .text:75C86E70 E7 LDR R3, [R5,R3]
- .text:75C86E74 8F E0 ADD R2, PC, R2 ; dword_75CC0068
- .text:75C86E78 E2 ADD R2, R2, #0x10 ; void **
- .text:75C86E7C A0 E1 MOV R1, R3 ; void *
- .text:75C86E80 8D E5 STR R3, [SP,#0x280+var_278]
- .text:75C86E84 F8 FF EB BL hook ; hook mono_assembly_load_from_full
- .text:75C86E88 A0 E1 MOV R0, R4 ; this
- .text:75C86E8C F7 F6 FF EB BL _ZN10lIIIlIlIIlD2Ev ; lIIIlIlIIl::~lIIIlIlIIl()
- .text:75C86E90 A8 9F E5 LDR R1, =(unk_75CB8B70 - 0x75C86EA0)
- .text:75C86E94 A0 E1 MOV R0, R4 ; this
- .text:75C86E98 8F E0 ADD R1, PC, R1 ; unk_75CB8B70
- .text:75C86E9C 0A 1D E2 ADD R1, R1, #0x280 ; char *
- .text:75C86EA0 2E F8 FF EB BL DecString
- .text:75C86EA4 A0 E1 MOV R0, R4
- .text:75C86EA8 F7 FF EB BL _ZN10lIIIlIlIIlcvPcEv ; lIIIlIlIIl::operator char *(void)
- .text:75C86EAC A0 E1 MOV R1, R0 ; name
- .text:75C86EB0 A0 E1 MOV R0, R9 ; handle
- .text:75C86EB4 B1 D6 FF EB BL dlsym ; 获取mono_image_open_from_data_with_name地址
- .text:75C86EB8 9F E5 LDR R3, =(lIlIllIllIl_ptr - 0x75CBEEC0)
- .text:75C86EBC 9F E5 LDR R2, =(dword_75CC0068 - 0x75C86ECC)
- .text:75C86EC0 E7 LDR R3, [R5,R3]
- .text:75C86EC4 8F E0 ADD R2, PC, R2 ; dword_75CC0068
- .text:75C86EC8 E2 ADD R2, R2, # ; void **
- .text:75C86ECC A0 E1 MOV R1, R3 ; void *
- .text:75C86ED0 8D E5 STR R3, [SP,#0x280+var_27C]
- .text:75C86ED4 F8 FF EB BL hook ; hook mono_image_open_from_data_with_name
- .text:75C86ED8 A0 E1 MOV R0, R4 ; this
- .text:75C86EDC E3 F6 FF EB BL _ZN10lIIIlIlIIlD2Ev ; lIIIlIlIIl::~lIIIlIlIIl()
- .text:75C86EE0 9F E5 LDR R3, =(dword_75CC0068 - 0x75C86EEC)
- .text:75C86EE4 8F E0 ADD R3, PC, R3 ; dword_75CC0068
- .text:75C86EE8 E5 LDR R2, [R3,#(dword_75CC0078 - 0x75CC0068)]
- .text:75C86EEC E3 CMP R2, #
- .text:75C86EF0 0A BEQ loc_75C86FC8
- .text:75C86EF4 E5 LDR R3, [R3,#(dword_75CC0070 - 0x75CC0068)]
- .text:75C86EF8 E3 CMP R3, #
- .text:75C86EFC 0A BEQ loc_75C86FC8
- .text:75C86F00
- .text:75C86F00 loc_75C86F00 ; CODE XREF: hook_mono_func+364↓j
- .text:75C86F00 ; hook_mono_func+38C↓j ...
- .text:75C86F00 E3 CMP R6, #0x17
- .text:75C86F04 9A BLS loc_75C86F1C
- .text:75C86F08 9F E5 LDR R3, =(_ZN6Global10lIlllIIllIE_ptr - 0x75CBEEC0)
- .text:75C86F0C E7 LDR R3, [R5,R3]
- .text:75C86F10 E5 LDR R3, [R3] ; Global::lIlllIIllI
- .text:75C86F14 E3 CMP R3, #0x17
- .text:75C86F18 6E CA BGT loc_75C870D8
- .text:75C86F1C
- .text:75C86F1C loc_75C86F1C ; CODE XREF: hook_mono_func+200↑j
- .text:75C86F1C 9F E5 LDR R1, =(unk_75CB8B70 - 0x75C86F2C)
- .text:75C86F20 A0 E1 MOV R0, R4 ; this
- .text:75C86F24 8F E0 ADD R1, PC, R1 ; unk_75CB8B70
- .text:75C86F28 1E E2 ADD R1, R1, #0x320 ; char *
- .text:75C86F2C 0B F8 FF EB BL DecString
- .text:75C86F30 A0 E1 MOV R0, R4
- .text:75C86F34 EF F6 FF EB BL _ZN10lIIIlIlIIlcvPcEv ; lIIIlIlIIl::operator char *(void)
- .text:75C86F38 9F E5 LDR R3, =(dword_75CC0068 - 0x75C86F4C)
- .text:75C86F3C 9F E5 LDR R2, =(lIIIlIIlII_ptr - 0x75CBEEC0)
- .text:75C86F40 A0 E1 MOV R1, R0 ; char *
- .text:75C86F44 8F E0 ADD R3, PC, R3 ; dword_75CC0068
- .text:75C86F48 E7 LDR R2, [R5,R2] ; void *
- .text:75C86F4C E2 ADD R3, R3, # ; void **
- .text:75C86F50 A0 E1 MOV R0, R9 ; void *
- .text:75C86F54 F8 FF EB BL IAT_HOOK ; hook memcpy
- .text:75C86F58 A0 E1 MOV R0, R4 ; this
- .text:75C86F5C C3 F6 FF EB BL _ZN10lIIIlIlIIlD2Ev ; lIIIlIlIIl::~lIIIlIlIIl()
- .text:75C86F60 F8 9F E5 LDR R1, =(unk_75CB8B70 - 0x75C86F70)
- .text:75C86F64 A0 E1 MOV R0, R4 ; this
- .text:75C86F68 8F E0 ADD R1, PC, R1 ; unk_75CB8B70
- .text:75C86F6C 1E E2 ADD R1, R1, #0x370 ; char *
- .text:75C86F70 FA F7 FF EB BL DecString
- .text:75C86F74 A0 E1 MOV R0, R4
- .text:75C86F78 DE F6 FF EB BL _ZN10lIIIlIlIIlcvPcEv ; lIIIlIlIIl::operator char *(void)
- .text:75C86F7C E0 9F E5 LDR R3, =(IlIIIlIIlI_ptr - 0x75CBEEC0)
- .text:75C86F80 A0 E1 MOV R1, R0 ; char *
- .text:75C86F84 E7 LDR R2, [R5,R3] ; void *
- .text:75C86F88 D8 9F E5 LDR R3, =(dword_75CC0068 - 0x75C86F98)
- .text:75C86F8C A0 E1 MOV R0, R9 ; void *
- .text:75C86F90 8F E0 ADD R3, PC, R3 ; dword_75CC0068 ; void **
- .text:75C86F94 F8 FF EB BL IAT_HOOK ; hook mmap
- .text:75C86F98
- .text:75C86F98 loc_75C86F98 ; CODE XREF: hook_mono_func+4C0↓j
- .text:75C86F98 A0 E1 MOV R0, R4 ; this
- .text:75C86F9C B3 F6 FF EB BL _ZN10lIIIlIlIIlD2Ev ; lIIIlIlIIl::~lIIIlIlIIl()
- .text:75C86FA0
- .text:75C86FA0 loc_75C86FA0 ; CODE XREF: hook_mono_func+484↓j
- .text:75C86FA0 A0 E3 MOV R2, #
- .text:75C86FA4 C0 9F E5 LDR R3, =(_ZN6Global10lllllllIIIE_ptr - 0x75CBEEC0)
- .text:75C86FA8 E7 LDR R3, [R5,R3]
- .text:75C86FAC C3 E5 STRB R2, [R3] ; Global::lllllllIII
- .text:75C86FB0
- .text:75C86FB0 loc_75C86FB0 ; CODE XREF: hook_mono_func+138↑j
- .text:75C86FB0 9D E5 LDR R2, [SP,#0x280+var_2C]
- .text:75C86FB4 9A E5 LDR R3, [R10]
- .text:75C86FB8 E1 CMP R2, R3
- .text:75C86FBC A4 1A BNE loc_75C87254
- .text:75C86FC0 DF 8D E2 ADD SP, SP, #0x25C
- .text:75C86FC4 F0 8F BD E8 LDMFD SP!, {R4-R11,PC}
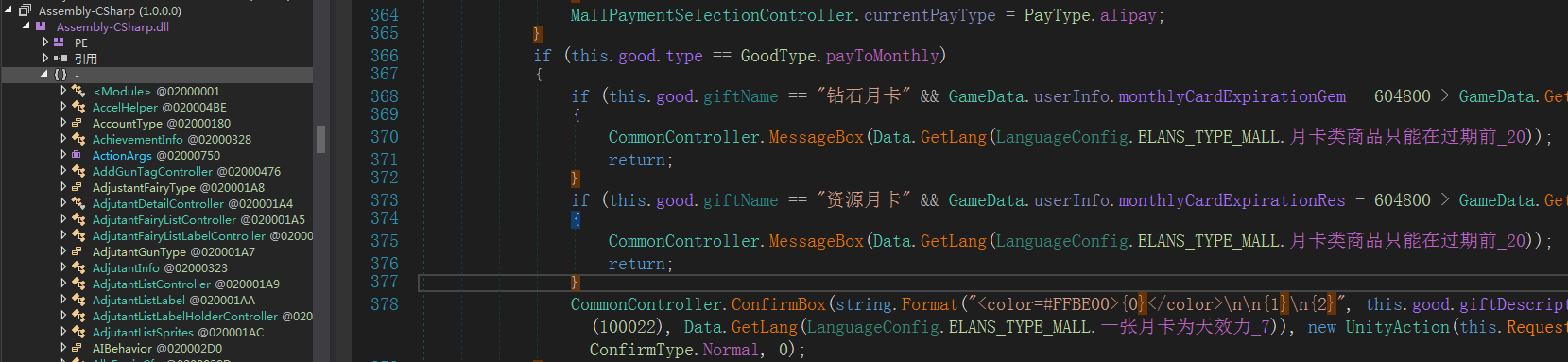
六: Assembly-CSharp.dll解密分析
1. 在mono的hook函数中解密Assembly-CSharp.dll,代码如下:
- .text:75C7A138 EXPORT hook_mono_image_open_from_data_with_name
- .text:75C7A138 hook_mono_image_open_from_data_with_name
- .text:75C7A138 ; DATA XREF: .got:lIlIllIllIl_ptr↓o
- .text:75C7A138
- .text:75C7A138 var_4F0= -0x4F0
- .text:75C7A138 var_4EC= -0x4EC
- .text:75C7A138 var_4E8= -0x4E8
- .text:75C7A138 var_4E4= -0x4E4
- .text:75C7A138 var_4DC= -0x4DC
- .text:75C7A138 var_4D8= -0x4D8
- .text:75C7A138 var_4D4= -0x4D4
- .text:75C7A138 var_4D0= -0x4D0
- .text:75C7A138 var_4CC= -0x4CC
- .text:75C7A138 var_4C8= -0x4C8
- .text:75C7A138 var_4C4= -0x4C4
- .text:75C7A138 var_60= -0x60
- .text:75C7A138 var_54= -0x54
- .text:75C7A138 var_50= -0x50
- .text:75C7A138 var_4C= -0x4C
- .text:75C7A138 var_48= -0x48
- .text:75C7A138 var_44= -0x44
- .text:75C7A138 var_43= -0x43
- .text:75C7A138 var_42= -0x42
- .text:75C7A138 var_41= -0x41
- .text:75C7A138 var_40= -0x40
- .text:75C7A138 var_3F= -0x3F
- .text:75C7A138 var_3E= -0x3E
- .text:75C7A138 var_3D= -0x3D
- .text:75C7A138 var_2C= -0x2C
- .text:75C7A138 arg_0=
- .text:75C7A138 arg_4=
- .text:75C7A138
- .text:75C7A138 ; __unwind { // 75C8F220
- .text:75C7A138 F0 4F 2D E9 STMFD SP!, {R4-R11,LR}
- .text:75C7A13C DD 4D E2 SUB SP, SP, #0x4C0
- .text:75C7A140 0C D0 4D E2 SUB SP, SP, #0xC
- .text:75C7A144 F4 9D E5 LDR R7, [SP,#0x4F0+arg_4]
- .text:75C7A148 9F E5 LDR R8, =(_GLOBAL_OFFSET_TABLE_ - 0x75C7A168)
- .text:75C7A14C C4 9F E5 LDR R12, =(__stack_chk_guard_ptr - 0x75CB2EC0)
- .text:75C7A150 E2 MOVS R6, R7
- .text:75C7A154 A0 MOVNE R6, #
- .text:75C7A158 E3 CMP R7, #
- .text:75C7A15C FF CMPNE R1, #0xFF
- .text:75C7A160 8F E0 ADD R8, PC, R8 ; _GLOBAL_OFFSET_TABLE_
- .text:75C7A164 0C C0 E7 LDR R12, [R8,R12]
- .text:75C7A168 A0 E1 MOV R5, R1
- .text:75C7A16C C0 8D E5 STR R12, [SP,#0x4F0+var_4E8]
- .text:75C7A170 C0 9C E5 LDR R12, [R12]
- .text:75C7A174 A0 E1 MOV R4, R0
- .text:75C7A178 0C 8D E5 STR R2, [SP,#0x4F0+var_4E4]
- .text:75C7A17C C4 C4 8D E5 STR R12, [SP,#0x4F0+var_2C]
- .text:75C7A180 DE 9A BLS loc_75C7A500
- .text:75C7A184 9F E5 LDR R1, =(unk_75CACB70 - 0x75C7A198)
- .text:75C7A188 2C 8D E2 ADD R6, SP, #0x4F0+var_4C4
- .text:75C7A18C A0 E1 MOV R0, R6 ; this
- .text:75C7A190 8F E0 ADD R1, PC, R1 ; unk_75CACB70 ; char *
- .text:75C7A194 A0 E1 MOV R9, R3
- .text:75C7A198 FB FF EB BL DecString
- .text:75C7A19C A0 E1 MOV R0, R6
- .text:75C7A1A0 FA FF EB BL _ZN10lIIIlIlIIlcvPcEv ; lIIIlIlIIl::operator char *(void)
- .text:75C7A1A4 A0 E1 MOV R1, R0 ; needle
- .text:75C7A1A8 A0 E1 MOV R0, R7 ; haystack
- .text:75C7A1AC DA FF EB BL strstr ; 判断是否加载Assembly-CSharp.dll
- .text:75C7A1B0 A0 A0 E1 MOV R10, R0
- .text:75C7A1B4 A0 E1 MOV R0, R6 ; this
- .text:75C7A1B8 2C FA FF EB BL _ZN10lIIIlIlIIlD2Ev ; lIIIlIlIIl::~lIIIlIlIIl()
- .text:75C7A1BC 5A E3 CMP R10, #
- .text:75C7A1C0 A5 0A BEQ loc_75C7A45C
- .text:75C7A1C4 E4 A3 9F E5 LDR R10, =unk_49F54EEB ; 准备解密
- .text:75C7A1C8 E4 E3 9F E5 LDR LR, =0x8B3BE89F
- .text:75C7A1CC E4 C3 9F E5 LDR R12, =0xC6EF3720
- .text:75C7A1D0 0A A0 E1 MOV R3, R10
- .text:75C7A1D4
- .text:75C7A1D4 loc_75C7A1D4 ; CODE XREF: hook_mono_image_open_from_data_with_name+104↓j
- .text:75C7A1D4 E0 9F E5 LDR R1, =0x815AA0CD
- .text:75C7A1D8 E0 9F E5 LDR R2, =0xA1C489F7
- .text:75C7A1DC B2 A0 E1 MOV R11, R3,LSL#
- .text:75C7A1E0 A3 A0 E1 MOV R0, R3,LSR#
- .text:75C7A1E4 8B E0 ADD R1, R11, R1
- .text:75C7A1E8 E0 ADD R2, R0, R2
- .text:75C7A1EC 8C E0 ADD R3, R12, R3
- .text:75C7A1F0 E0 EOR R2, R2, R1
- .text:75C7A1F4 E0 EOR R2, R2, R3
- .text:75C7A1F8 C4 9F E5 LDR R1, =0x95A8882C
- .text:75C7A1FC C4 9F E5 LDR R3, =0x9D2CC113
- .text:75C7A200 0E E0 E0 RSB LR, R2, LR
- .text:75C7A204 0C 8E E0 ADD R2, LR, R12
- .text:75C7A208 0E B2 A0 E1 MOV R11, LR,LSL#
- .text:75C7A20C AE A0 E1 MOV R0, LR,LSR#
- .text:75C7A210 C4 8C E2 ADD R12, R12, #0x61000000
- .text:75C7A214 8B E0 ADD R1, R11, R1
- .text:75C7A218 E0 ADD R3, R0, R3
- .text:75C7A21C C7 8C E2 ADD R12, R12, #0xC80000
- .text:75C7A220 E0 EOR R3, R3, R1
- .text:75C7A224 CC 8C E2 ADD R12, R12, #0x8600
- .text:75C7A228 E0 EOR R3, R3, R2
- .text:75C7A22C C0 8C E2 ADD R12, R12, #0x47
- .text:75C7A230 0A E0 RSB R3, R3, R10
- .text:75C7A234 5C E3 CMP R12, #
- .text:75C7A238 A0 A0 E1 MOV R10, R3
- .text:75C7A23C E4 FF FF 1A BNE loc_75C7A1D4
- .text:75C7A240 D4 E5 LDRB R1, [R4]
- .text:75C7A244 FF E2 AND R2, R3, #0xFF
- .text:75C7A248 E0 8D E5 STR LR, [SP,#0x4F0+var_4C8]
- .text:75C7A24C E1 CMP R1, R2
- .text:75C7A250 8D E5 STR R3, [SP,#0x4F0+var_4CC]
- .text:75C7A254 1A BNE loc_75C7A45C
- .text:75C7A258 D4 E5 LDRB R2, [R4,#]
- .text:75C7A25C DD E5 LDRB R3, [SP,#0x4F0+var_4CC+]
- .text:75C7A260 E1 CMP R2, R3
- .text:75C7A264 7C 1A BNE loc_75C7A45C
- .text:75C7A268 D4 E5 LDRB R2, [R4,#]
- .text:75C7A26C DD E5 LDRB R3, [SP,#0x4F0+var_4CC+]
- .text:75C7A270 E1 CMP R2, R3
- .text:75C7A274 1A BNE loc_75C7A45C
- .text:75C7A278 D4 E5 LDRB R2, [R4,#]
- .text:75C7A27C DD E5 LDRB R3, [SP,#0x4F0+var_4CC+]
- .text:75C7A280 E1 CMP R2, R3
- .text:75C7A284 1A BNE loc_75C7A45C
- .text:75C7A288 D4 E5 LDRB R2, [R4,#]
- .text:75C7A28C DD E5 LDRB R3, [SP,#0x4F0+var_4C8]
- .text:75C7A290 E1 CMP R2, R3
- .text:75C7A294 1A BNE loc_75C7A45C
- .text:75C7A298 2C 9F E5 LDR R3, =(_ZN6Global10IIlllllllIE_ptr - 0x75CB2EC0)
- .text:75C7A29C 9C C4 8D E5 STR R12, [SP,#0x4F0+var_54]
- .text:75C7A2A0 A0 C4 8D E5 STR R12, [SP,#0x4F0+var_50]
- .text:75C7A2A4 E7 LDR R3, [R8,R3]
- .text:75C7A2A8 D3 E5 LDRB R3, [R3] ; Global::IIlllllllI
- .text:75C7A2AC E3 CMP R3, #
- .text:75C7A2B0 A7 0A BEQ loc_75C7A554
- .text:75C7A2B4 9F E5 LDR R3, =(_ZN6Global10IllIlIIllIE_ptr - 0x75CB2EC0)
- .text:75C7A2B8 E7 LDR R3, [R8,R3]
- .text:75C7A2BC E5 LDR R3, [R3] ; Global::IllIlIIllI
- .text:75C7A2C0 A0 D3 E5 LDRB R10, [R3]
- .text:75C7A2C4 D3 E5 LDRB R8, [R3,#]
- .text:75C7A2C8 E0 D3 E5 LDRB LR, [R3,#]
- .text:75C7A2CC C0 D3 E5 LDRB R12, [R3,#]
- .text:75C7A2D0 D3 E5 LDRB R0, [R3,#]
- .text:75C7A2D4 D3 E5 LDRB R1, [R3,#]
- .text:75C7A2D8 D3 E5 LDRB R2, [R3,#]
- .text:75C7A2DC D3 E5 LDRB R3, [R3,#]
- .text:75C7A2E0 9C A4 CD E5 STRB R10, [SP,#0x4F0+var_54]
- .text:75C7A2E4 9D CD E5 STRB R8, [SP,#0x4F0+var_54+]
- .text:75C7A2E8 9E E4 CD E5 STRB LR, [SP,#0x4F0+var_54+]
- .text:75C7A2EC 9F C4 CD E5 STRB R12, [SP,#0x4F0+var_54+]
- .text:75C7A2F0 A0 CD E5 STRB R0, [SP,#0x4F0+var_50]
- .text:75C7A2F4 A1 CD E5 STRB R1, [SP,#0x4F0+var_50+]
- .text:75C7A2F8 A2 CD E5 STRB R2, [SP,#0x4F0+var_50+]
- .text:75C7A2FC A3 CD E5 STRB R3, [SP,#0x4F0+var_50+]
- .text:75C7A300
- .text:75C7A300 loc_75C7A300 ; CODE XREF: hook_mono_image_open_from_data_with_name+440↓j
- .text:75C7A300 A0 E1 MOV R0, R6 ; this
- .text:75C7A304 2E F1 FF EB BL _ZN10llIlIlIlllC2Ev ; llIlIlIlll::llIlIlIlll(void)
- .text:75C7A308 A0 E3 MOV R3, #0x10 ; int
- .text:75C7A30C C0 D4 E5 LDRB R12, [R4,#]
- .text:75C7A310 9C E4 9D E5 LDR LR, [SP,#0x4F0+var_54]
- .text:75C7A314 D4 E5 LDRB R1, [R4,#]
- .text:75C7A318 D4 E5 LDRB R2, [R4,#]
- .text:75C7A31C D4 E5 LDRB R0, [R4,#]
- .text:75C7A320 A0 D4 E5 LDRB R10, [R4,#]
- .text:75C7A324 8D E5 STR R3, [SP,#0x4F0+var_4F0] ; int
- .text:75C7A328 A0 B4 9D E5 LDR R11, [SP,#0x4F0+var_50]
- .text:75C7A32C A4 E4 8D E5 STR LR, [SP,#0x4F0+var_4C]
- .text:75C7A330 0A D4 E5 LDRB R8, [R4,#0xA]
- .text:75C7A334 0B E0 D4 E5 LDRB LR, [R4,#0xB]
- .text:75C7A338 AC C4 CD E5 STRB R12, [SP,#0x4F0+var_44]
- .text:75C7A33C 0C C0 D4 E5 LDRB R12, [R4,#0xC]
- .text:75C7A340 AF CD E5 STRB R1, [SP,#0x4F0+var_41]
- .text:75C7A344 B0 CD E5 STRB R2, [SP,#0x4F0+var_40]
- .text:75C7A348 4A 1E 8D E2 ADD R1, SP, #0x4F0+var_50
- .text:75C7A34C 4B 2E 8D E2 ADD R2, SP, #0x4F0+var_40
- .text:75C7A350 AE CD E5 STRB R0, [SP,#0x4F0+var_42]
- .text:75C7A354 E2 ADD R1, R1, # ; char *
- .text:75C7A358 A0 E1 MOV R0, R6 ; this
- .text:75C7A35C E2 ADD R2, R2, # ; char *
- .text:75C7A360 A8 B4 8D E5 STR R11, [SP,#0x4F0+var_48]
- .text:75C7A364 AD A4 CD E5 STRB R10, [SP,#0x4F0+var_43]
- .text:75C7A368 B1 CD E5 STRB R8, [SP,#0x4F0+var_3F]
- .text:75C7A36C B2 E4 CD E5 STRB LR, [SP,#0x4F0+var_3E]
- .text:75C7A370 B3 C4 CD E5 STRB R12, [SP,#0x4F0+var_3D]
- .text:75C7A374 F1 FF EB BL _ZN10llIlIlIlll10lIIIIlIlIIEPKcS1_ii ; llIlIlIlll::lIIIIlIlII(char const*,char const*,int,int)
- .text:75C7A378 0F D4 E5 LDRB R2, [R4,#0xF]
- .text:75C7A37C D4 E5 LDRB R3, [R4,#0x10]
- .text:75C7A380 0D D4 E5 LDRB R0, [R4,#0xD]
- .text:75C7A384 0E D4 E5 LDRB R1, [R4,#0xE]
- .text:75C7A388 CD E5 STRB R2, [SP,#0x4F0+var_4DC+]
- .text:75C7A38C CD E5 STRB R3, [SP,#0x4F0+var_4DC+]
- .text:75C7A390 D4 E5 LDRB R2, [R4,#0x11]
- .text:75C7A394 D4 E5 LDRB R3, [R4,#0x12]
- .text:75C7A398 CD E5 STRB R0, [SP,#0x4F0+var_4DC]
- .text:75C7A39C CD E5 STRB R1, [SP,#0x4F0+var_4DC+]
- .text:75C7A3A0 A0 9D E5 LDR R10, [SP,#0x4F0+var_4DC]
- .text:75C7A3A4 D4 E5 LDRB R8, [R4,#0x13]
- .text:75C7A3A8 E0 D4 E5 LDRB LR, [R4,#0x14]
- .text:75C7A3AC C0 D4 E5 LDRB R12, [R4,#0x15]
- .text:75C7A3B0 D4 E5 LDRB R1, [R4,#0x16]
- .text:75C7A3B4 CD E5 STRB R2, [SP,#0x4F0+var_4D8]
- .text:75C7A3B8 CD E5 STRB R3, [SP,#0x4F0+var_4D8+]
- .text:75C7A3BC D4 E5 LDRB R2, [R4,#0x17]
- .text:75C7A3C0 D4 E5 LDRB R3, [R4,#0x18]
- .text:75C7A3C4 0A A0 E1 MOV R0, R10 ; unsigned int
- .text:75C7A3C8 1A CD E5 STRB R8, [SP,#0x4F0+var_4D8+]
- .text:75C7A3CC 1B E0 CD E5 STRB LR, [SP,#0x4F0+var_4D8+]
- .text:75C7A3D0 1C C0 CD E5 STRB R12, [SP,#0x4F0+var_4D4]
- .text:75C7A3D4 1D CD E5 STRB R1, [SP,#0x4F0+var_4D4+]
- .text:75C7A3D8 1E CD E5 STRB R2, [SP,#0x4F0+var_4D4+]
- .text:75C7A3DC 1F CD E5 STRB R3, [SP,#0x4F0+var_4D4+]
- .text:75C7A3E0 9C E0 FF EB BL malloc_0
- .text:75C7A3E4 A0 E3 MOV R1, #
- .text:75C7A3E8 A0 E1 MOV R8, R0
- .text:75C7A3EC A0 E1 MOV R2, R0 ; char *
- .text:75C7A3F0 8D E5 STR R1, [SP,#0x4F0+var_4F0] ; int
- .text:75C7A3F4 0A A0 E1 MOV R3, R10 ; unsigned int
- .text:75C7A3F8 A0 E1 MOV R0, R6 ; this
- .text:75C7A3FC E2 ADD R1, R4, #0x19 ; char *
- .text:75C7A400 F9 FF EB BL _ZN10llIlIlIlll10lllIIIllIIEPKcPcji ; llIlIlIlll::lllIIIllII(char const*,char *,uint,int)
- .text:75C7A404 1C B0 9D E5 LDR R11, [SP,#0x4F0+var_4D4]
- .text:75C7A408 0B A0 E1 MOV R0, R11 ; unsigned int
- .text:75C7A40C E0 FF EB BL malloc_0 ; 分配内存放解密后数据
- .text:75C7A410 C0 A0 E3 MOV R12, #
- .text:75C7A414 8D E2 ADD R3, SP, #0x4F0+var_4D0
- .text:75C7A418 A0 A0 E1 MOV R10, R0
- .text:75C7A41C 8D E5 STR R3, [SP,#0x4F0+var_4EC]
- .text:75C7A420 9D E5 LDR R2, [SP,#0x4F0+var_4D8]
- .text:75C7A424 A0 E1 MOV R3, R0
- .text:75C7A428 B0 8D E5 STR R11, [SP,#0x4F0+var_4F0]
- .text:75C7A42C A0 E3 MOV R0, #
- .text:75C7A430 A0 E1 MOV R1, R8
- .text:75C7A434 C0 8D E5 STR R12, [SP,#0x4F0+var_4D0]
- .text:75C7A438 1E EB BL _Z10IlllIIIIll10IIlIlIlllIPKhjPhjPj ; 解密出明文dll
- .text:75C7A43C E3 CMP R0, #
- .text:75C7A440 3A 0A BEQ loc_75C7A530
- .text:75C7A444
- .text:75C7A444 loc_75C7A444 ; CODE XREF: hook_mono_image_open_from_data_with_name+418↓j
- .text:75C7A444 0A A0 E1 MOV R0, R10 ; void *
- .text:75C7A448 E0 FF EB BL _Z10IIIIIllIIlPv ; IIIIIllIIl(void *)
- .text:75C7A44C A0 E1 MOV R0, R8 ; void *
- .text:75C7A450 8E E0 FF EB BL _Z10IIIIIllIIlPv ; IIIIIllIIl(void *)
- .text:75C7A454 A0 E1 MOV R0, R6 ; this
- .text:75C7A458 DC F0 FF EB BL _ZN10llIlIlIlllD2Ev ; llIlIlIlll::~llIlIlIlll()
- .text:75C7A45C
- .text:75C7A45C loc_75C7A45C ; CODE XREF: hook_mono_image_open_from_data_with_name+88↑j
- .text:75C7A45C ; hook_mono_image_open_from_data_with_name+11C↑j ...
- .text:75C7A45C F0 9D E5 LDR R3, [SP,#0x4F0+arg_0]
- .text:75C7A460 6C 9F E5 LDR R1, =(dword_75CB4068 - 0x75C7A474)
- .text:75C7A464 8D E5 STR R7, [SP,#0x4F0+var_4EC]
- .text:75C7A468 8D E5 STR R3, [SP,#0x4F0+var_4F0]
- .text:75C7A46C 8F E0 ADD R1, PC, R1 ; dword_75CB4068
- .text:75C7A470 C0 E5 LDR R12, [R1,#(dword_75CB4070 - 0x75CB4068)]
- .text:75C7A474 0C 9D E5 LDR R2, [SP,#0x4F0+var_4E4]
- .text:75C7A478 A0 E1 MOV R3, R9
- .text:75C7A47C A0 E1 MOV R0, R4
- .text:75C7A480 A0 E1 MOV R1, R5
- .text:75C7A484 3C FF 2F E1 BLX R12
- .text:75C7A488 A0 E1 MOV R8, R0
- .text:75C7A48C
- .text:75C7A48C loc_75C7A48C ; CODE XREF: hook_mono_image_open_from_data_with_name+3F4↓j
- .text:75C7A48C 9F E5 LDR R1, =(unk_75CACB70 - 0x75C7A49C)
- .text:75C7A490 A0 E1 MOV R0, R6 ; this
- .text:75C7A494 8F E0 ADD R1, PC, R1 ; unk_75CACB70 ; char *
- .text:75C7A498 B0 FA FF EB BL DecString
- .text:75C7A49C A0 E1 MOV R0, R6
- .text:75C7A4A0 F9 FF EB BL _ZN10lIIIlIlIIlcvPcEv ; lIIIlIlIIl::operator char *(void)
- .text:75C7A4A4 A0 E1 MOV R1, R0 ; needle
- .text:75C7A4A8 A0 E1 MOV R0, R7 ; haystack
- .text:75C7A4AC D9 FF EB BL strstr
- .text:75C7A4B0 A0 E1 MOV R7, R0
- .text:75C7A4B4 A0 E1 MOV R0, R6 ; this
- .text:75C7A4B8 6C F9 FF EB BL _ZN10lIIIlIlIIlD2Ev ; lIIIlIlIIl::~lIIIlIlIIl()
- .text:75C7A4BC E3 CMP R7, #
- .text:75C7A4C0 CMPNE R5, #
- .text:75C7A4C4 0A BEQ loc_75C7A4DC
- .text:75C7A4C8 A0 E3 MOV R3, #
- .text:75C7A4CC E0 ADD R5, R4, R5
- .text:75C7A4D0
- .text:75C7A4D0 loc_75C7A4D0 ; CODE XREF: hook_mono_image_open_from_data_with_name+3A0↓j
- .text:75C7A4D0 C4 E4 STRB R3, [R4],#
- .text:75C7A4D4 E1 CMP R4, R5
- .text:75C7A4D8 FC FF FF 1A BNE loc_75C7A4D0
- .text:75C7A4DC
- .text:75C7A4DC loc_75C7A4DC ; CODE XREF: hook_mono_image_open_from_data_with_name+38C↑j
- .text:75C7A4DC ; hook_mono_image_open_from_data_with_name+3EC↓j
- .text:75C7A4DC 9D E5 LDR R3, [SP,#0x4F0+var_4E8]
- .text:75C7A4E0 C4 9D E5 LDR R2, [SP,#0x4F0+var_2C]
- .text:75C7A4E4 A0 E1 MOV R0, R8
- .text:75C7A4E8 E5 LDR R3, [R3]
- .text:75C7A4EC E1 CMP R2, R3
- .text:75C7A4F0 1A BNE loc_75C7A588
- .text:75C7A4F4 DD 8D E2 ADD SP, SP, #0x4C0
- .text:75C7A4F8 0C D0 8D E2 ADD SP, SP, #0xC
- .text:75C7A4FC F0 8F BD E8 LDMFD SP!, {R4-R11,PC}
- 解密后 dump dll R10是基址,R11是大小,如下图:

- static main(void)
- {
- auto fp, begin, end, dexbyte;
- fp = fopen("d:\\dump.dll", "wb"); //打开或创建一个文件
- begin = R10; //dll基址
- end = begin + R11; //dll基址 + dll文件大小
- for ( dexbyte = begin; dexbyte < end;dexbyte ++ )
- {
- fputc(Byte(dexbyte), fp); //按字节将其dump到本地文件中
- }
- }
将dump出来的dll反编后如下图:
3.在hook_mono_assembly_load_from_full主要是计算将解密dll的PE头清楚后的计算crc值。
七: libengine模块分析
1. 在com/inca/security/Core/AppGuardEngine类中注册的第一个Native函数中通过dlopen、dlsym调用libengine.sox解密的so
JNI比函数 .text:75C81168 IlIIIIIIII (文件偏移 13168) (Landroid/content/Context;Ljava/lang/String;[B)I
2.通过dlopen、dlsym获取下面3个函数。
以下这几个函数被调用
Initialize (文件偏移27144)
CreateObject (文件偏移2A2F4)
Clazz::IlIllllIIl (文件偏移2B1B0)
3. Initialize函数
- //反调试
- /data/data/com.digitalsky.girlsfrontline.cn/files/95c72528dc4c1ef12d2bf750585fed56eca973a8 7CE87000
- .text:7CEAE17A loc_7CEAE17A ; CODE XREF: Initialize+32↑j
- .text:7CEAE17A CC 4B LDR R3, =(_ZN10lllllIIIll11IIlIlIIIlllE_ptr - 0x7CF87D44)
- .text:7CEAE17C EB LDR R3, [R5,R3]
- .text:7CEAE17E 1E STR R6, [R3] ; lllllIIIll::IIlIlIIIlll
- .text:7CEAE180 F0 B6 FD BL Anit_Dbg ; 反调试(读进程状态)
- .text:7CEAE184 B8 CMP R0, R7
- .text:7CEAE186 D0 BEQ loc_7CEAE18A
- .text:7CEAE188 D4 E1 B loc_7CEAE534
- //动态获取函数
- .text:7CEAE33A loc_7CEAE33A ; CODE XREF: Initialize+1F2↑j
- .text:7CEAE33A 1A STR R2, [R3] ; Global::llIlIllllI
- .text:7CEAE33C 1E F0 DA FC BL GetlibcFunc
- .text:7CEAE340 1F F0 FD BL GetlibdvmFunc
- .text:7CEAE344 CMP R0, #
- .text:7CEAE346 D0 BEQ loc_7CEAE352
- .text:7CEAE348 4B LDR R3, =(_ZN6Global11llllIIlIlIIE_ptr - 0x7CF87D44)
- .text:7CEAE34A EB LDR R3, [R5,R3]
- .text:7CEAE34C STR R3, [SP,#0x1A8+var_198]
- .text:7CEAE34E MOVS R3, #
- .text:7CEAE350 1E E0 B loc_7CEAE390
4. CreateObject函数
计算libengine.sox解密后的函数crc (文件偏移 2A1F6)
- /data/data/com.digitalsky.girlsfrontline.cn/files/95c72528dc4c1ef12d2bf750585fed56eca973a8 7CF7A000
- .text:7CFA41F6 loc_7CFA41F6 ; CODE XREF: IlllIIIlll::IlllIIIlll(_JNIEnv *,void *)+324↓j
- .text:7CFA41F6 4B LDR R3, =(_ZN6Global11lIIIIIIIIIIE_ptr - 0x7D07AD44)
- .text:7CFA41F8 9A LDR R2, [SP,#0xF8+var_DC]
- .text:7CFA41FA F3 LDR R3, [R6,R3]
- .text:7CFA41FC 1C MOVS R0, R2 ; void *
- .text:7CFA41FE 1A STR R2, [R3] ; Global::lIIIIIIIIII
- .text:7CFA4200 F0 F8 BL GetCrc32 ; 计算libengine.sox解密后的函数crc
- .text:7CFA4204 4B LDR R3, =(_ZN6Global11lIIlIlIIIlIE_ptr - 0x7D07AD44)
- 计算CRC函数代码如下:
- .text:7CFD8250 EXPORT GetCrc32
- .text:7CFD8250 GetCrc32 ; CODE XREF: IlllIIIlll::IlllIIIlll(_JNIEnv *,void *)+2E4↑p
- .text:7CFD8250 ; IlllIllIll::lIIIllIlIll(lIIIllIlllII *,int,IIlIllIlllll *,bool *,char *,bool)+88↑p ...
- .text:7CFD8250 ; __unwind {
- .text:7CFD8250 F8 B5 PUSH {R3-R7,LR}
- .text:7CFD8252 4B LDR R3, =(_ZN6Global10lIIllIllIlE_ptr - 0x7CFD825A)
- .text:7CFD8254 MOVS R5, #
- .text:7CFD8256 7B ADD R3, PC ; _ZN6Global10lIIllIllIlE_ptr
- .text:7CFD8258 1B LDR R3, [R3] ; Global::lIIllIllIl
- .text:7CFD825A 1B LDR R3, [R3] ; Global::lIIllIllIl
- .text:7CFD825C 2B CMP R3, #0x17
- .text:7CFD825E 3B DC BGT loc_7CFD82D8
- .text:7CFD8260 1C MOVS R4, R0
- .text:7CFD8262 2B CMP R3, #0x17
- .text:7CFD8264 D1 BNE loc_7CFD8278
- .text:7CFD8266 1E LDR R0, =(_ZN6Global11IlIIIIlllllE_ptr - 0x7CFD826E)
- .text:7CFD8268 1E LDR R1, =(aN - 0x7CFD8272)
- .text:7CFD826A ADD R0, PC ; _ZN6Global11IlIIIIlllllE_ptr
- .text:7CFD826C LDR R0, [R0] ; Global::IlIIIIlllll
- .text:7CFD826E ADD R1, PC ; "N"
- .text:7CFD8270 F0 BE FB BL j_strcmp
- .text:7CFD8274 A8 CMP R0, R5
- .text:7CFD8276 2F D0 BEQ loc_7CFD82D8
- .text:7CFD8278
- .text:7CFD8278 loc_7CFD8278 ; CODE XREF: GetCrc32+14↑j
- .text:7CFD8278 MOVS R6, #
- .text:7CFD827A 1C MOVS R3, R4
- .text:7CFD827C 1C MOVS R0, R6 ; this
- .text:7CFD827E B0 ADDS R3, #0xB0
- .text:7CFD8280 1F LDR R7, [R3]
- .text:7CFD8282
- .text:7CFD8282 loc_7CFD8282 ; CODE XREF: GetCrc32+84↓j
- .text:7CFD8282 1C MOVS R3, R4
- .text:7CFD8284 B4 ADDS R3, #0xB4
- .text:7CFD8286 1B LDR R3, [R3]
- .text:7CFD8288 9E CMP R6, R3 ; 判断是否结束
- .text:7CFD828A D2 BCS loc_7CFD82D6
- .text:7CFD828C 1C MOVS R3, R4
- .text:7CFD828E BC ADDS R3, #0xBC
- .text:7CFD8290 1B LDR R3, [R3]
- .text:7CFD8292 B2 LSLS R2, R6, #
- .text:7CFD8294 D5 LDR R5, [R2,R3]
- .text:7CFD8296
- .text:7CFD8296 loc_7CFD8296 ; CODE XREF: GetCrc32+80↓j
- .text:7CFD8296 2D CMP R5, #
- .text:7CFD8298 1B D0 BEQ loc_7CFD82D2
- .text:7CFD829A 2B LSLS R3, R5, #
- .text:7CFD829C FB ADDS R3, R7, R3 ; unsigned int
- .text:7CFD829E 7B LDRB R1, [R3,#0xC]
- .text:7CFD82A0 0A ASRS R2, R1, #
- .text:7CFD82A2 3A SUBS R2, #
- .text:7CFD82A4 2A CMP R2, #
- .text:7CFD82A6 0E D8 BHI loc_7CFD82C6
- .text:7CFD82A8 DA LDRH R2, [R3,#0xE]
- .text:7CFD82AA 2A CMP R2, #
- .text:7CFD82AC 0B D0 BEQ loc_7CFD82C6
- .text:7CFD82AE 0F MOVS R2, #0xF
- .text:7CFD82B0 0A ANDS R2, R1
- .text:7CFD82B2 2A CMP R2, #
- .text:7CFD82B4 D1 BNE loc_7CFD82C6
- .text:7CFD82B6 1C MOVS R2, R4
- .text:7CFD82B8 8C ADDS R2, #0x8C
- .text:7CFD82BA LDR R1, [R2]
- .text:7CFD82BC 5A LDR R2, [R3,#]
- .text:7CFD82BE ADDS R1, R2, R1 ; unsigned int
- .text:7CFD82C0 9A LDR R2, [R3,#] ; unsigned __int8 *
- .text:7CFD82C2 E5 F7 F1 FF BL adler_adler32 ; R1函数首地址,R2函数大小
- .text:7CFD82C6
- .text:7CFD82C6 loc_7CFD82C6 ; CODE XREF: GetCrc32+56↑j
- .text:7CFD82C6 ; GetCrc32+5C↑j ...
- .text:7CFD82C6 1C MOVS R3, R4
- .text:7CFD82C8 C0 ADDS R3, #0xC0
- .text:7CFD82CA 1B LDR R3, [R3]
- .text:7CFD82CC AD LSLS R5, R5, #
- .text:7CFD82CE 5D LDR R5, [R3,R5]
- .text:7CFD82D0 E1 E7 B loc_7CFD8296
- .text:7CFD82D2 ; ---------------------------------------------------------------------------
- .text:7CFD82D2
- .text:7CFD82D2 loc_7CFD82D2 ; CODE XREF: GetCrc32+48↑j
- .text:7CFD82D2 ADDS R6, #
- .text:7CFD82D4 D5 E7 B loc_7CFD8282
- .text:7CFD82D6 ; ---------------------------------------------------------------------------
- .text:7CFD82D6
- .text:7CFD82D6 loc_7CFD82D6 ; CODE XREF: GetCrc32+3A↑j
- .text:7CFD82D6 1C ADDS R5, R0, #
- .text:7CFD82D8
- .text:7CFD82D8 loc_7CFD82D8 ; CODE XREF: GetCrc32+E↑j
- .text:7CFD82D8 ; GetCrc32+26↑j
- .text:7CFD82D8 1C MOVS R0, R5
- .text:7CFD82DA F8 BD POP {R3-R7,PC}
5. IlIllllIIl 函数
计算libc.so代码节的crc值 与.text节的CRC(文件偏移398AE)
- /data/data/com.digitalsky.girlsfrontline.cn/files/95c72528dc4c1ef12d2bf750585fed56eca973a8
- .text:7779C8AE LDR R1, [R3,#]
- .text:7779C8B0 LDR R3, [R6,#0x10] ; unsigned int
- .text:7779C8B2 C9 ADDS R1, R1, R3 ; unsigned int
- .text:7779C8B4 0A F0 F8 FC BL _ZN5adler7adler32EmPKhj ; 计算libc.so代码节的crc值 AA4AC826
6.计算libcompatible.so函数的Crc与.text节的CRC
- .text:7C88BAB2
- .text:7C88BAB2 ; IlllIIIIlIl(IlIIlIIIll *)
- .text:7C88BAB2 EXPORT _Z11IlllIIIIlIlP10IlIIlIIIll
- .text:7C88BAB2 _Z11IlllIIIIlIlP10IlIIlIIIll ; CODE XREF: IlllIllIll::IlIllIllll(lIIIllIlllII *,int,IIlIllIlllll *,bool *,char *,bool)+196↑p
- .text:7C88BAB2 ; IlllIllIll::IlllIllIll(_jobject *,int,long long,long long,uint,char **,char **,char **,char **,char **)+80C↑p
- .text:7C88BAB2 ; __unwind {
- .text:7C88BAB2 F8 B5 PUSH {R3-R7,LR}
- .text:7C88BAB4 MOVS R6, #
- .text:7C88BAB6 FC ADDS R0, #0xFC
- .text:7C88BAB8 1C MOVS R4, R0
- .text:7C88BABA 6C LDR R7, [R0,#0x48]
- .text:7C88BABC 1C ADDS R0, R6, # ; this
- .text:7C88BABE
- .text:7C88BABE loc_7C88BABE ; CODE XREF: IlllIIIIlIl(IlIIlIIIll *)+4E↓j
- .text:7C88BABE A3 6A LDR R3, [R4,#0x28]
- .text:7C88BAC0 9E CMP R6, R3 ; 判断函数个数是否结束
- .text:7C88BAC2 1E D2 BCS locret_7C88BB02
- .text:7C88BAC4 6B LDR R2, [R4,#0x30]
- .text:7C88BAC6 B3 LSLS R3, R6, #
- .text:7C88BAC8 9D LDR R5, [R3,R2]
- .text:7C88BACA
- .text:7C88BACA loc_7C88BACA ; CODE XREF: IlllIIIIlIl(IlIIlIIIll *)+4A↓j
- .text:7C88BACA 2D CMP R5, #
- .text:7C88BACC D0 BEQ loc_7C88BAFE ; i++
- .text:7C88BACE 2B LSLS R3, R5, #
- .text:7C88BAD0 FB ADDS R3, R7, R3 ; unsigned int
- .text:7C88BAD2 7B LDRB R1, [R3,#0xC]
- .text:7C88BAD4 0A ASRS R2, R1, #
- .text:7C88BAD6 3A SUBS R2, #
- .text:7C88BAD8 2A CMP R2, #
- .text:7C88BADA 0C D8 BHI loc_7C88BAF6
- .text:7C88BADC DA LDRH R2, [R3,#0xE]
- .text:7C88BADE 2A CMP R2, #
- .text:7C88BAE0 D0 BEQ loc_7C88BAF6
- .text:7C88BAE2 0F MOVS R2, #0xF
- .text:7C88BAE4 0A ANDS R2, R1
- .text:7C88BAE6 2A CMP R2, #
- .text:7C88BAE8 D1 BNE loc_7C88BAF6
- .text:7C88BAEA 5A LDR R2, [R3,#]
- .text:7C88BAEC 6A LDR R1, [R4,#0x20]
- .text:7C88BAEE ADDS R1, R2, R1 ; unsigned int
- .text:7C88BAF0 9A LDR R2, [R3,#] ; unsigned __int8 *
- .text:7C88BAF2 E5 F7 D9 FB BL adler_adler32 ; 计算crc32
- .text:7C88BAF6
- .text:7C88BAF6 loc_7C88BAF6 ; CODE XREF: IlllIIIIlIl(IlIIlIIIll *)+28↑j
- .text:7C88BAF6 ; IlllIIIIlIl(IlIIlIIIll *)+2E↑j ...
- .text:7C88BAF6 6B LDR R3, [R4,#0x34]
- .text:7C88BAF8 AD LSLS R5, R5, #
- .text:7C88BAFA 5D LDR R5, [R3,R5]
- .text:7C88BAFC E5 E7 B loc_7C88BACA
- .text:7C88BAFE ; ---------------------------------------------------------------------------
- .text:7C88BAFE
- .text:7C88BAFE loc_7C88BAFE ; CODE XREF: IlllIIIIlIl(IlIIlIIIll *)+1A↑j
- .text:7C88BAFE ADDS R6, # ; i++
- .text:7C88BB00 DD E7 B loc_7C88BABE
- .text:7C88BB02 ; ---------------------------------------------------------------------------
- .text:7C88BB02
- .text:7C88BB02 locret_7C88BB02 ; CODE XREF: IlllIIIIlIl(IlIIlIIIll *)+10↑j
- .text:7C88BB02 F8 BD POP {R3-R7,PC}
- 计算so的.text节代码的crc值 (文件偏移 )
- ,text:7C866860 ; IlllIllIll::IlllIllIll(_jobject *,int,long long,long long,uint,char **,char **,char **,char **,char **)+8E2↑j
- .text:7C866860 MOVS R3, #
- .text:7C866862 STR R3, [SP,#0xB20+var_B08]
- .text:7C866864 9B LDR R3, [SP,#0xB20+var_B14]
- .text:7C866866 2B CMP R3, #
- .text:7C866868 2C D0 BEQ loc_7C8668C4 ; 结束
- .text:7C86686A
- .text:7C86686A loc_7C86686A ; CODE XREF: IlllIllIll::IlllIllIll(_jobject *,int,long long,long long,uint,char **,char **,char **,char **,char **)+94A↓j
- .text:7C86686A 9B LDR R3, [SP,#0xB20+var_B08]
- .text:7C86686C 9A LDR R2, [SP,#0xB20+var_AFC]
- .text:7C86686E CMP R3, R2 ; 判断是否结束
- .text:7C866870 D0 BEQ loc_7C8668C4 ; 结束
- .text:7C866872 1C MOVS R0, R5 ; this
- .text:7C866874 LDR R1, [SP,#0xB20+var_B08] ; unsigned int
- .text:7C866876 1C F0 FE BL _ZN10lIIIIllIII10lIlIIlIIll10IlIIlIlIllEj ; lIIIIllIII::lIlIIlIIll::IlIIlIlIll(uint)
- .text:7C86687A 9B LDR R3, [SP,#0xB20+var_B14]
- .text:7C86687C LDR R2, [R0]
- .text:7C86687E 1C MOVS R6, R0
- .text:7C866880 ADDS R0, R3, R2
- .text:7C866882 2B LDR R3, [R5]
- .text:7C866884 5A LDR R2, [R3,#]
- .text:7C866886 9B LDR R3, [R3,#]
- .text:7C866888 D3 ADDS R3, R2, R3
- .text:7C86688A CMP R0, R3
- .text:7C86688C 1C D8 BHI loc_7C8668C8
- .text:7C86688E LDR R1, =(aText - 0x7C866896)
- .text:7C866890 MOVS R2, #
- .text:7C866892 ADD R1, PC ; ".text"
- .text:7C866894 6C F0 FE BL j_strncmp ; 判断是否为.text
- .text:7C866898 CMP R0, #
- .text:7C86689A 0F D1 BNE loc_7C8668BC
- .text:7C86689C D7 MOVS R3, #0xD7
- .text:7C86689E LDR R2, [R6,#0x14] ; unsigned __int8 *
- .text:7C8668A0 9B LSLS R3, R3, #
- .text:7C8668A2 FA STR R2, [R7,R3]
- .text:7C8668A4 D8 MOVS R3, #0xD8
- .text:7C8668A6 LDR R1, [R6,#0x10]
- .text:7C8668A8 9B LSLS R3, R3, #
- .text:7C8668AA F9 STR R1, [R7,R3]
- .text:7C8668AC 2B LDR R3, [R5]
- .text:7C8668AE LDR R1, [R3,#]
- .text:7C8668B0 LDR R3, [R6,#0x10] ; unsigned int
- .text:7C8668B2 C9 ADDS R1, R1, R3 ; unsigned int
- .text:7C8668B4 0A F0 F8 FC BL adler_adler32 ; 计算libc.so代码节的crc值
- .text:7C8668B8 0A 9B LDR R3, [SP,#0xB20+var_AF8]
- .text:7C8668BA F8 STR R0, [R7,R3]
- .text:7C8668BC
- .text:7C8668BC loc_7C8668BC ; CODE XREF: IlllIllIll::IlllIllIll(_jobject *,int,long long,long long,uint,char **,char **,char **,char **,char **)+922↑j
- .text:7C8668BC 9B LDR R3, [SP,#0xB20+var_B08]
- .text:7C8668BE ADDS R3, #
7.判断是否有种破解工具与是否在模拟器中运行,创建线程检测比较CRC值。
检测是否有的非法工具部分字符串如下:
- LuckyPatcher v4..(幸运破解器)
- LuckyPatcher v5..
- gamehacker (烧饼游戏修改器)
- com.cih.game_cih:*(金手指)
- (com.huluxia.gametools)葫芦侠
- Cheat Engine修改器
- tcpdump
- GenyMotion(模拟器)
- Windroy
- BlueStacks
- org.sbtools.gamespeed燒餅修改器
- org.game.master 游戏修改大师
- 在线程中比较CRC值。
- .text:7D34674C Cmp_Crc32 ; CODE XREF: IlllIllIll::IIIlllIlllII(lIIIllIlllII *,IIlIllIlllll *)+40A↓p
- .text:7D34674C ; IlllIllIll::lIllllllIlII(lIIIllIlllII *,IIlIllIlllll *)+4EA↓p ...
- .text:7D34674C
- .text:7D34674C var_20 = -0x20
- .text:7D34674C var_1C = -0x1C
- .text:7D34674C arg_0 =
- .text:7D34674C arg_8 =
- .text:7D34674C
- .text:7D34674C ; __unwind {
- .text:7D34674C F7 B5 PUSH {R0-R2,R4-R7,LR}
- .text:7D34674E 0A AC ADD R4, SP, #0x20+arg_8
- .text:7D346750 LDRB R4, [R4]
- .text:7D346752 STR R4, [SP,#0x20+var_20]
- .text:7D346754 CMP R1, #
- .text:7D346756 D0 BEQ loc_7D346764
- .text:7D346758 MOVS R5, #
- .text:7D34675A D4 LSLS R4, R2, #
- .text:7D34675C 0C ADDS R4, R1, R4
- .text:7D34675E STR R5, [R4,#]
- .text:7D346760 MOVS R5, #
- .text:7D346762 A5 STR R5, [R4,#]
- .text:7D346764
- .text:7D346764 loc_7D346764 ; CODE XREF: Cmp_Crc32+A↑j
- .text:7D346764 9C LDR R4, [SP,#0x20+var_20]
- .text:7D346766 2C CMP R4, #
- .text:7D346768 D1 BNE loc_7D34677A
- .text:7D34676A 8C E4 MOVS R4, #0x460
- .text:7D34676E ADDS R4, R0, R4
- .text:7D346770 LDR R4, [R4]
- .text:7D346772 A4 LSLS R4, R4, #0x16
- .text:7D346774 D5 BPL loc_7D34677A
- .text:7D346776
- .text:7D346776 loc_7D346776 ; CODE XREF: Cmp_Crc32+38↓j
- .text:7D346776 ; Cmp_Crc32+58↓j
- .text:7D346776 MOVS R0, #
- .text:7D346778 E0 B locret_7D346808
- .text:7D34677A ; ---------------------------------------------------------------------------
- .text:7D34677A
- .text:7D34677A loc_7D34677A ; CODE XREF: Cmp_Crc32+1C↑j
- .text:7D34677A ; Cmp_Crc32+28↑j
- .text:7D34677A 4C LDR R4, =(_ZN6Global10llIIIlIlIIE_ptr - 0x7D346780)
- .text:7D34677C 7C ADD R4, PC ; _ZN6Global10llIIIlIlIIE_ptr
- .text:7D34677E LDR R4, [R4] ; Global::llIIIlIlII
- .text:7D346780 LDRB R6, [R4] ; Global::llIIIlIlII
- .text:7D346782 2E CMP R6, #
- .text:7D346784 F7 D1 BNE loc_7D346776
- .text:7D346786 1D 1C MOVS R5, R3
- .text:7D346788 4B LDR R3, =(_ZN6Global11lIIIIIIIIIIE_ptr - 0x7D346790)
- .text:7D34678A 1C MOVS R4, R0
- .text:7D34678C 7B ADD R3, PC ; _ZN6Global11lIIIIIIIIIIE_ptr
- .text:7D34678E 1B LDR R3, [R3] ; Global::lIIIIIIIIII
- .text:7D346790 STR R2, [SP,#0x20+var_1C]
- .text:7D346792 0F 1C MOVS R7, R1
- .text:7D346794 LDR R0, [R3] ; void *
- .text:7D346796 F0 5B FD BL GetCrc32
- .text:7D34679A 1E 4B LDR R3, =(_ZN6Global11lIIlIlIIIlIE_ptr - 0x7D3467A0)
- .text:7D34679C 7B ADD R3, PC ; _ZN6Global11lIIlIlIIIlIE_ptr
- .text:7D34679E 1B LDR R3, [R3] ; Crc32Dword_E13E1FA9
- .text:7D3467A0 1B LDR R3, [R3]
- .text:7D3467A2 CMP R0, R3 ; 比较crc32值
- .text:7D3467A4 E7 D0 BEQ loc_7D346776
- .text:7D3467A6 1C 4A LDR R2, =(_ZN10IlllIllIll11llllIllIIIlE - 0x7D3467AC)
- .text:7D3467A8 7A ADD R2, PC ; IlllIllIll::llllIllIIIl
- .text:7D3467AA LDR R3, [R2] ; IlllIllIll::llllIllIIIl
- .text:7D3467AC ADDS R3, #
- .text:7D3467AE STR R3, [R2] ; IlllIllIll::llllIllIIIl
- .text:7D3467B0 2D CMP R5, #
- .text:7D3467B2 1D D0 BEQ loc_7D3467F0
- .text:7D3467B4 MOVS R1, #
- .text:7D3467B6 2A LDR R2, [R5]
- .text:7D3467B8 LSLS R3, R2, #
- .text:7D3467BA EB ADDS R3, R5, R3
- .text:7D3467BC STR R1, [R3,#]
- .text:7D3467BE 0A MOVS R1, #0xA
- .text:7D3467C0 DE STR R6, [R3,#0xC]
- .text:7D3467C2 STR R1, [R3,#]
- .text:7D3467C4 1E STR R6, [R3,#0x10]
- .text:7D3467C6 9B LDR R3, [SP,#0x20+arg_0]
- .text:7D3467C8 ADDS R2, #
- .text:7D3467CA 2A STR R2, [R5]
- .text:7D3467CC 2B CMP R3, #
- .text:7D3467CE D0 BEQ loc_7D3467D6
- .text:7D3467D0 MOVS R3, #
- .text:7D3467D2 9A LDR R2, [SP,#0x20+arg_0]
- .text:7D3467D4 STRB R3, [R2]
- .text:7D3467D6
- .text:7D3467D6 loc_7D3467D6 ; CODE XREF: Cmp_Crc32+82↑j
- .text:7D3467D6 9B LDR R3, [SP,#0x20+var_20]
- .text:7D3467D8 2B CMP R3, #
- .text:7D3467DA D1 BNE loc_7D3467F0
- .text:7D3467DC 8D DB MOVS R3, #0x468
- .text:7D3467E0 E3 ADDS R3, R4, R3
- .text:7D3467E2 1B LDR R3, [R3]
- .text:7D3467E4 9B LSLS R3, R3, #0x16
- .text:7D3467E6 D4 BMI loc_7D3467F0
- .text:7D3467E8 0C 4A LDR R2, =0x49C
- .text:7D3467EA A3 LDR R3, [R4,R2]
- .text:7D3467EC ADDS R3, #
- .text:7D3467EE A3 STR R3, [R4,R2]
- .text:7D3467F0
- .text:7D3467F0 loc_7D3467F0 ; CODE XREF: Cmp_Crc32+66↑j
- .text:7D3467F0 ; Cmp_Crc32+8E↑j ...
- .text:7D3467F0 2F CMP R7, #
- .text:7D3467F2 D0 BEQ loc_7D3467FE
- .text:7D3467F4 9B LDR R3, [SP,#0x20+var_1C]
- .text:7D3467F6 DA LSLS R2, R3, #
- .text:7D3467F8 AA MOVS R3, #0xAA
- .text:7D3467FA BA ADDS R2, R7, R2
- .text:7D3467FC STR R3, [R2,#]
- .text:7D3467FE
- .text:7D3467FE loc_7D3467FE ; CODE XREF: Cmp_Crc32+A6↑j
- .text:7D3467FE MOVS R0, #
- .text:7D346800 4B LDR R3, =(_ZN6Global10lIlIIllIIlE_ptr - 0x7D346806)
- .text:7D346802 7B ADD R3, PC ; _ZN6Global10lIlIIllIIlE_ptr
- .text:7D346804 1B LDR R3, [R3] ; Global::lIlIIllIIl
- .text:7D346806 STRB R0, [R3,#(byte_7D413581 - 0x7D413578)]
- .text:7D346808
- .text:7D346808 locret_7D346808 ; CODE XREF: Cmp_Crc32+2C↑j
- .text:7D346808 FE BD POP {R1-R7,PC}
截图监控
- .text:7D34B944 2A LDR R1, =(unk_7D3E51F8 - 0x7D34B94E)
- .text:7D34B946 3D LDR R5, [R7,R4]
- .text:7D34B948 7F AC ADD R4, SP, #0xB20+var_924
- .text:7D34B94A ADD R1, PC ; unk_7D3E51F8
- .text:7D34B94C 1C MOVS R0, R4 ; this
- .text:7D34B94E 4C ADDS R1, #0x4C ; 'L' ; char *
- .text:7D34B950 0A F0 F8 BL DecString
- .text:7D34B954 1C MOVS R0, R4
- .text:7D34B956 F0 FF BL _ZN10IIllIIlIIIcvPcEv ; IIllIIlIII::operator char *(void)
- .text:7D34B95A 1C MOVS R1, R0
- .text:7D34B95C MOVS R2, #
- .text:7D34B95E 1C MOVS R0, R5
- .text:7D34B960 6D F0 9E F8 BL j_inotify_add_watch ; 截图监控
- .text:7D34B964 E0 AD MOVS R5, #0x380
- .text:7D34B968 STR R0, [R7,R5]
- .text:7D34B96A 1C MOVS R0, R4 ; this
- .text:7D34B96C F0 FF BL _ZN10IIllIIlIIID2Ev ; IIllIIlIII::~IIllIIlIII()
- .text:7D34B970 7B LDR R3, [R7,R5]
- .text:7D34B972 2B CMP R3, #
- .text:7D34B974 DA BGE loc_7D34B998
- .text:7D34B976 MOVS R3, #
- .text:7D34B978 1E 4A LDR R2, =(a5eddcc418cda8d - 0x7D34B988)
八:总结
1.该反外挂系统主要有字符串加密保护,客户端完整性检查(CRC+签
名),函数及变量、反调试保护,系统so文件校验, 自身so文件校验,U3D防护,画面截屏保护,内存防修改保护,但是so本身只做了函数名混淆与字符串加密,代码没有做保护处理,逆向起来还是比较容易。
样本:链接: https://pan.baidu.com/s/1dFPbyLj 密码: 7h2r
欢迎关注公众号:

nProtect APPGuard安卓反外挂分析的更多相关文章
- 帧同步(LockStep)该如何反外挂
在中国的游戏环境下,反挂已经成为了游戏开发的重中之重,甚至能决定一款游戏的生死,吃鸡就是一个典型的案例.目前参与了了一款动作射击的MOBA类游戏的开发,同步方案上选择了帧同步技术(LockStep而非 ...
- 基于御安全APK加固的游戏反外挂方案
一. 前言 随着移动互联网的兴起,移动游戏市场近几年突然爆发,收入规模快速增长.根据第三方数据统计,国内移动游戏2015年市场规模已达514.6亿.由于手游市场强势兴起,而且后续增长势头会愈加猛烈.火 ...
- 一文了解安卓APP逆向分析与保护机制
"知物由学"是网易云易盾打造的一个品牌栏目,词语出自汉·王充<论衡·实知>.人,能力有高下之分,学习才知道事物的道理,而后才有智慧,不去求问就不会知道."知物 ...
- Android敲诈者病毒“安卓性能激活”分析(2015年9月版)
一.情况简介 前几天分析了论坛里的一个Android敲诈者病毒,感觉还是很有收获,后面有空多研究研究Android病毒.说句题外话, 根据前面分析的Android敲诈者病毒的隐藏手法,应该可以实现&q ...
- CNN卷积核反传分析
CNN(卷积神经网络)的误差反传(error back propagation)中有一个非常关键的的步骤就是将某个卷积(Convolve)层的误差传到前一层的池化(Pool)层上,因为在CNN中是2D ...
- 安卓脱壳&&协议分析&&burp辅助分析插件编写
前言 本文由 本人 首发于 先知安全技术社区: https://xianzhi.aliyun.com/forum/user/5274 前言 本文以一个 app 为例,演示对 app脱壳,然后分析其 协 ...
- 163music 反爬分析
# 网易163 音乐的 mp3下载 .mp3 下载的一个API吧 封 IP 的一种报错 网易云就给我返回了一个{"code":-460,"msg":" ...
- 唯品会安卓版app分析
.................................................................................................... ...
- 安卓动态逆向分析工具--Andbug&Androguard
工具使用方法: 转自: http://bbs.pediy.com/showthread.php?t=183412 https://testerhome.com/topics/3542 安装andbug ...
随机推荐
- 2019.2.10考试T2, 多项式求exp+生成函数
\(\color{#0066ff}{ 题目描述 }\) 为了减小文件大小,这里不写一堆题目背景了. 请写一个程序,输入一个数字N,输出N个点的森林的数量.点有标号. 森林是一种无向图,要求图中不能存在 ...
- http 与 TCP 与 socket 定义,区别
http://blog.csdn.net/jenminzhang/article/details/47017741 http协议:处于互联网协议的应用层,角色是规定数据传输的格式,http是建立在so ...
- 解决maven项目中有小红叉的问题
首先在window--perferences--showview中显示problems中查看出错的原因
- MySql8最新配置方式(完美)
下载MYSQL8 地址:https://www.mysql.com/downloads/ 1.滑动网页到最下面,选择Community (GPL) Downloads » 2.选择MySQL Comm ...
- P3800 Power收集
传送门 DP每次向下一格,显然是DP方程也十分显然:设$f[i][j]$为到第$i$行第$j$列时能得到的最大价值显然$f[i][j]=max(f[i-1][k]+v[i][j]),( max(0,j ...
- HDU 1565 方格取数(简单状态压缩DP)
http://acm.hdu.edu.cn/showproblem.php?pid=1565 对于每一个数,取或者不取,用0表示不取,1表示取,那么对于每一行的状态,就可以用一个二进制的数来表示.比如 ...
- day22 正则表达式 re
1. 正则表达式 正则表达式是对字符串操作的一种逻辑公式. 我们一般使用正则表达式对字符串进行匹配和过滤. 工具: 各大文本编辑器⼀般都有正则匹配功能. 我们也可以去http://tool.china ...
- Appium自动化—浅谈iOS自动化测试环境搭建
在日常的测试工作中,我们会发现有些测试工作重复率极高,测试人员需要花费大量的时间进行这些重复性的测试,浪费了大量的人力与时间.若能够将常用的测试场景进行自动化,那必定能节省许多的人力与时间.作为一个初 ...
- 阿里云 Ubuntu16.04 部署 LAMP
1.更新软件源 sudo apt-get update 2.安装Apache sudo apt-get install apache2 3.查看Apache是否安装成功 apache2 –v 如下所示 ...
- Spring实现AOP
转载: https://blog.csdn.net/tolcf/article/details/49133119 [框架][Spring]XML配置实现AOP拦截-切点:JdkRegexpMethod ...
