Nikto
https://cirt.net/nikto2
Fire Up Kali & Open Nikto
Let's fire up Kali and get started with nikto. Once we have Kali up and running, go to Kali Linux -> Vulnerability Analysis -> Misc Scanners -> nikto, like in the screenshot below.
Image via wonderhowto.com
Although there are many options in using nikto, we will limit ourselves here to the basic syntax, such as this:
- nikto -h <IP or hostname>
Step 2Scan the Web Server
Let's start with a safe web server on our own network. In this case, I have started the http service on another machine on my network. There is not a website hosted by this machine, just the web server. Let's scan it for vulnerabilities by typing:
- nikto -h 192.168.1.104
Nikto responds with a lot of information, as you can see below.
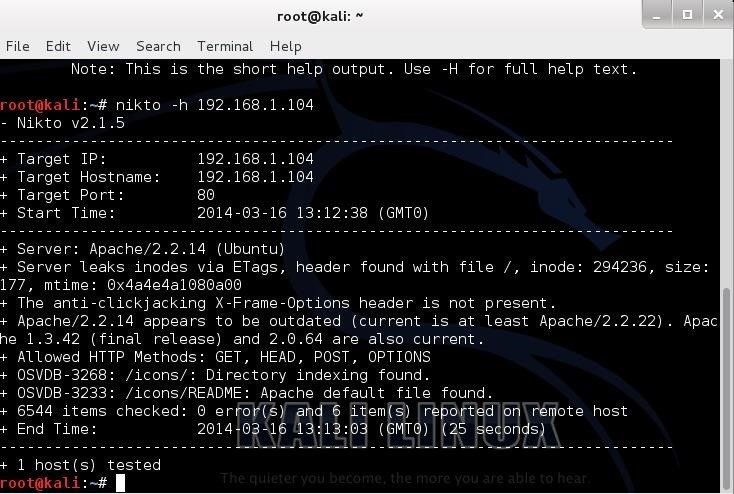
First, it tells us the server is Apache 2.2.14, probably on Ubuntu. It nailed this info and gives up more information on other potential vulnerabilities on this web server.
Note near the bottom that it identifies some vulnerabilities with the OSVDB prefix. This is the Open Source Vulnerability Database. This is a database maintained of known vulnerabilities at www.osvdb.org, in addition to other databases I covered, such as SecurityFocus and Microsoft's Technet.
Step 3Scan the Site
Let's try another site. In an earlier tutorial, we had hacked a web server named webscantest.com. Let's see what nikto can tell us about this site.
- nikto -h webscantest.com
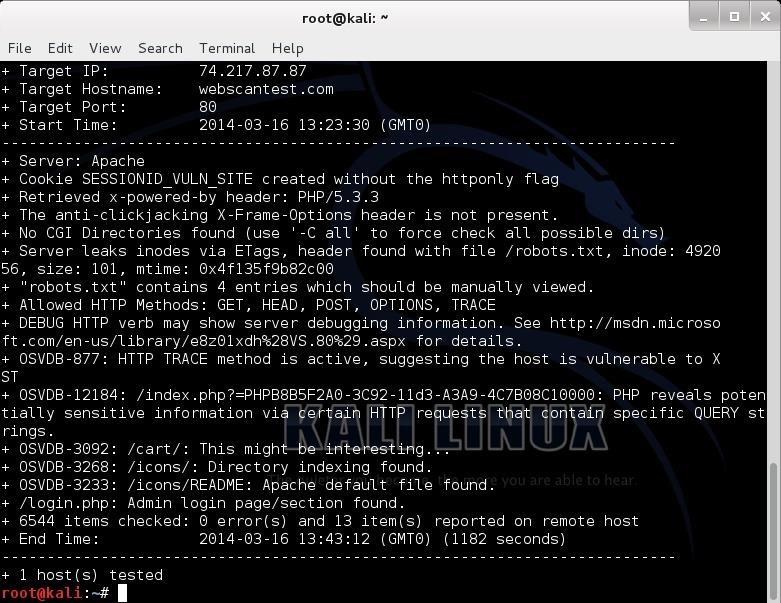
Once again, it identifies the server (Apache) and then proceeds to identify numerous potential vulnerabilities pre-fixed with OSVDB. We can take a look at that website at www.osvdb.org to learn more about these vulnerabilities.
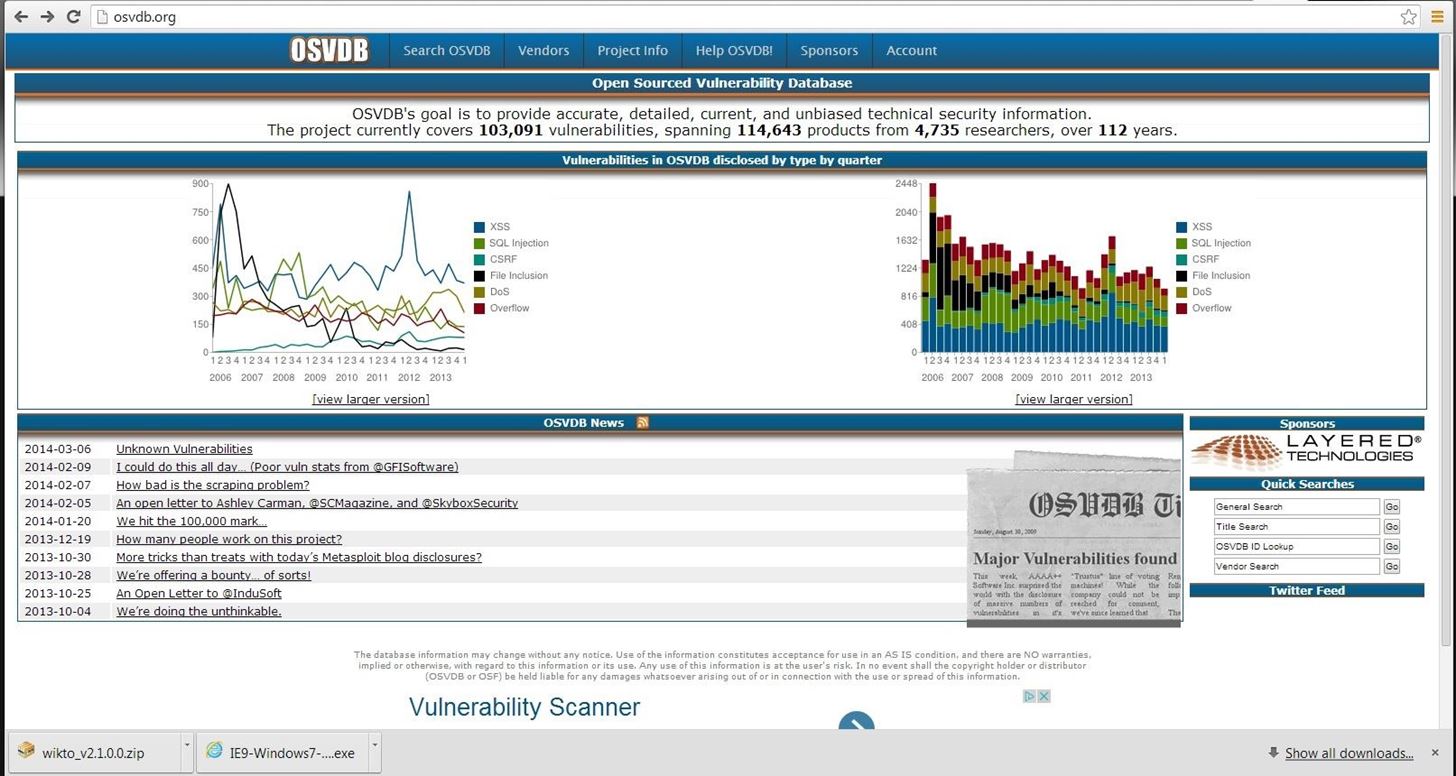
Now, let's use this site to find information on one of the vulnerabilities identified by nikto as OSVDB-877. We can put that reference number into the search function and it retrieves the following page.
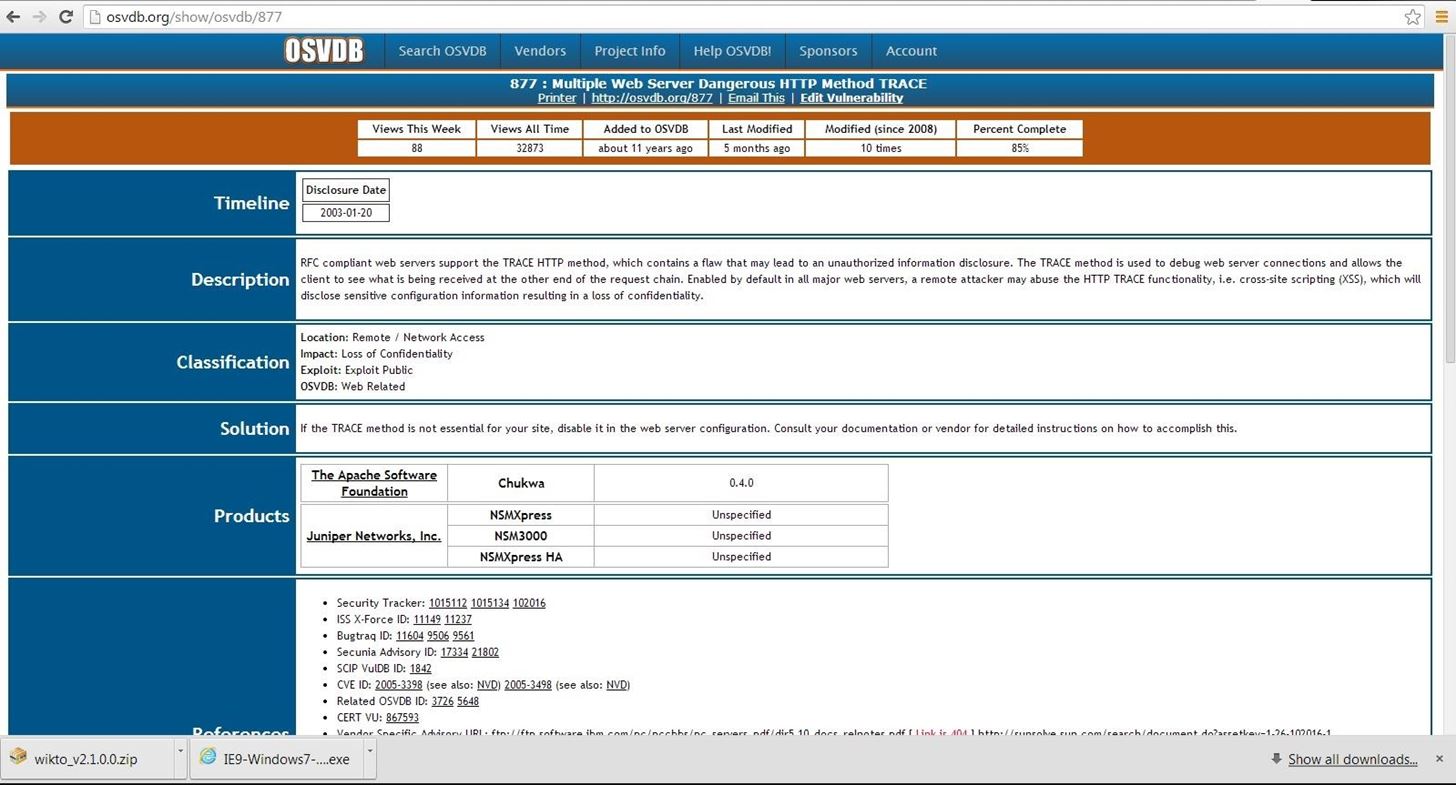
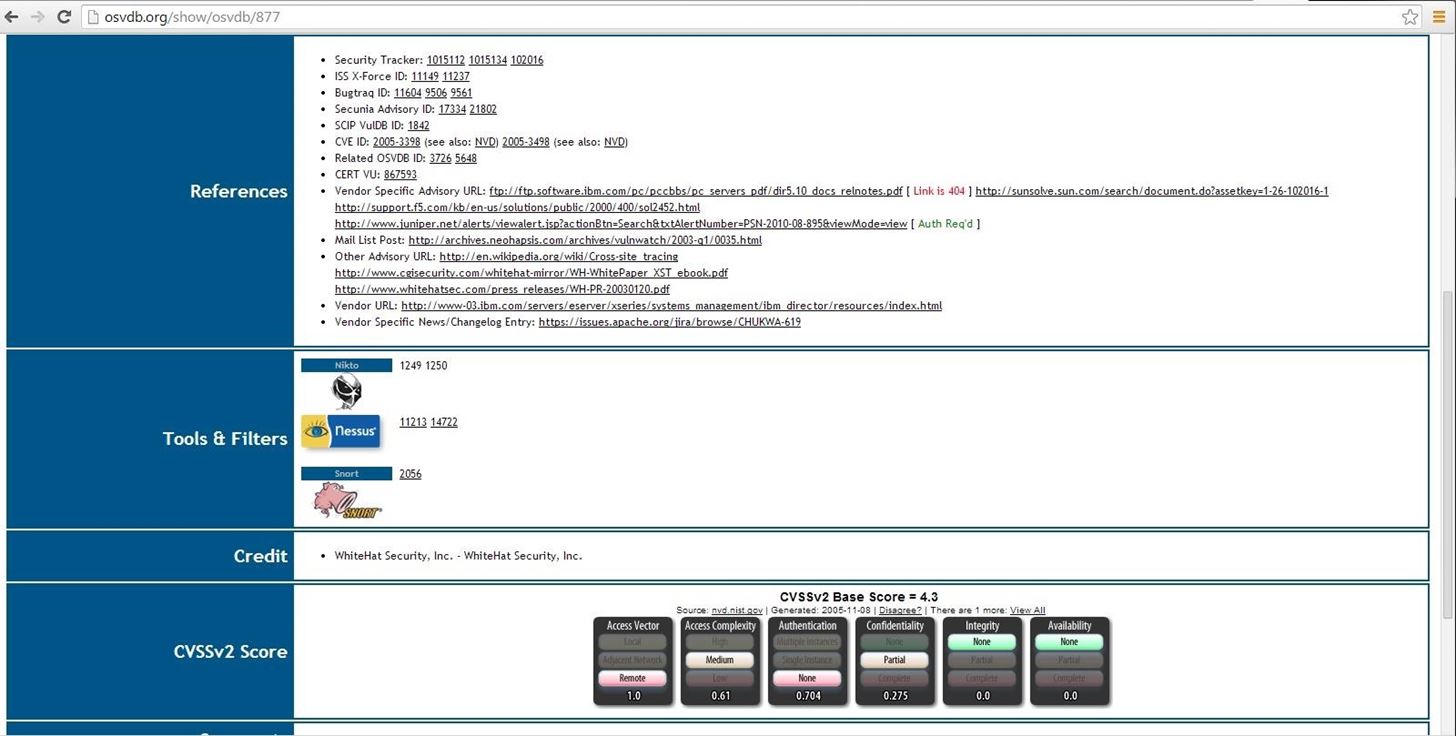
Note, in lower half of this page there are cross-references to the various information sources about this vulnerability, as well as references to tools and filters such as Nikto, Nessus, and Snort.
Scan WonderHowTo
Let's scan a few more sites and see what it can tell us about these sites. Let's see what we can find out about our own website, www.wonderhowto.com.
- nikto -h wonderhowto.com
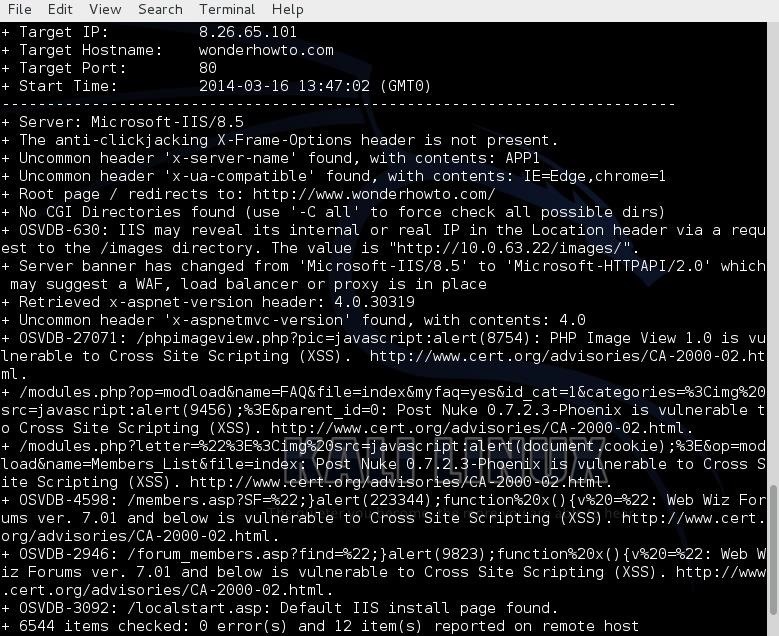
As you can see, it tells us that WonderHowTo is using Microsoft's IIS 8.5 as a web server and then lists numerous potential vulnerabilities.
However, any attempt to exploit the vulnerabilities listed will reveal that they're all false-positives, as WonderHowTo simply returns a harmless 404 page. This is because WonderHowTo is not built on php or asp as the noted exploits expect.
False positives like this can appear because the scan does not actually execute each of the possible vulnerabilities, but rather scans to see if the server responds without error to known exploitable URLs.
Scan Facebook
Finally, lets point nikto at www.facebook.com.
- nikto -h facebook.com

As you can see, Facebook is tightly secured with few vulnerabilities. As you can imagine, if Facebook weren't secure, every script-kiddie on the planet would be hacking it to see who his true love is chatting with online.
Nikto的更多相关文章
- 用Nikto探测一个网站所用到的技术
Nikto是一款开源的(GPL)网页服务器扫描器,它可以对网页服务器进行全面的多种扫描,包含超过3300种有潜在危险的文件/CGIs:超过 625种服务器版本:超过230种特定服务器问题,包括多种有潜 ...
- Nikto是一款Web安全扫描工具,可以扫描指定主机的web类型,主机名,特定目录,cookie,特定CGI漏洞,XSS漏洞,SQL注入漏洞等,非常强大滴说。。。
Nikto是一款Web安全扫描工具,可以扫描指定主机的web类型,主机名,特定目录,cookie,特定CGI漏洞,XSS漏洞,SQL注入漏洞等,非常强大滴说... root@xi4ojin:~# cd ...
- 小白日记28:kali渗透测试之Web渗透-扫描工具-Nikto
扫描工具-Nikto #WEB渗透 靶机:metasploitable 靶场:DVWA[默认账号/密码:admin/password] #新手先将DVWA的安全性,调到最低,可容易发现漏洞 侦察[减少 ...
- New ipad安装Perl支持安装nikto
Title:New ipad安装Perl支持安装nikto --2012-11-15 09:47 New Ipad 越了后. ssh new ipad 进入目录 cd /tmp 下载Key文件 wge ...
- Nikto and whatweb
root@kali:~# nikto -host www.baidu.com- Nikto v2.1.6------------------------------------------------ ...
- Nikto主动扫描神器!!!
Perl语言开发的开源web安全扫描器 Nikto只支持主动扫描:可扫描web服务器类型是不是最新版本(分析先版本与新版相比有哪些漏洞) 针对:1.软件版本.2.搜索存在安全隐患的文件.3.服务器配置 ...
- Nikto学习点
一.使用Nikto扫描https站点 nikto.pl -output myhost.html -g -ssl -Format HTM -host www.test.com -port 443 二.使 ...
- Kali学习笔记24:Nikto、Skipfish
文章的格式也许不是很好看,也没有什么合理的顺序 完全是想到什么写一些什么,但各个方面都涵盖到了 能耐下心看的朋友欢迎一起学习,大牛和杠精们请绕道 实验环境: Kali机器IP:192.168.163. ...
- web扫描工具-Nikto介绍与使用
Nikto Perl语言开发的开源Web安全扫描器 web扫描模式:截断代理主动扫描 可以扫描的方面:软件版本搜索存在安全隐患的文件服务器配置漏洞WEB Application层面的安全隐患避免404 ...
随机推荐
- 第一章 HTML基本标签
1.HTML:HTML:超文本标签语言(标签又称标记.元素).浏览器:“解释和执行”HTML源码的工具 (运行网页的工具APP).客户端:享受服务的计算机服务器:提供服务的计算机 2.基本框架(网页最 ...
- (转)Hashtable与ConcurrentHashMap区别
ConcurrentHashMap融合了hashtable和hashmap二者的优势. hashtable是做了同步的,hashmap未考虑同步.所以hashmap在单线程情况下效率较高.hashta ...
- TP父类及模板继承
一.TP父类方法继承 session用法 用登录页面做例子 <?php namespace Home\Controller; use Think\Controller; class LoginC ...
- 3.GDScript(1)概览
GDScript 是上面提到的用于Godot的主要语言.和其他语言相比,它与Godot高度整合,有许多优点: 简单,优雅,设计上为Lua.Python.Squirrel等语言用户所熟悉. 加载和编译速 ...
- javascript(一):javascript基本介绍及基本语法
什么是javascript? javascript是一种直译型脚本语言,是一种动态类型.弱类型.基于原型的语言.(所谓“脚本语言”:指的是它不具有开发操作系统的能力,只是用来编写大型运用程序的脚本!) ...
- CSS选择符-----伪类选择符
Element:hover E:hover { sRules } 设置元素在其鼠标悬停时的样式 <!DOCTYPE html> <html> <head> < ...
- maven工程的common模块jar上传至仓库并被其它模块依赖
.parent pom和common pom 都需要添加 <distributionManagement> <repository> <id>nexus</i ...
- Failed to start component [StandardEngine[Tomcat].StandardHost[localhost]]
1.问题场景描述:一个maven项目启动时候,偶尔会报tomcat的这个错误(如图:) 随机报错,有时频率很高,要一直重新启动很多次可能还是启动不了,有时不报错.. 2.解决过程:网上各种寻找解决办法 ...
- 初探AngularJs框架(二)
一.创建Components组件 直接使用AngularCLI即可很方便的创建component组件,使用如下指令: ng g component components/news 这样就会在compo ...
- Linux基础命令---chsh
chsh 改变用户登录时使用的shell,默认使用bash.如果命令行上没有给出shell,chsh将提示输入一个shell.chsh将接受系统上任何可执行文件的完整路径名.但是,如果shell未在“ ...
