.Net Core 3.0 Api json web token 中间件签权验证和 Cors 中间件处理跨域请求
第一步:在Nuget上安装"Microsoft.AspNet.WebApi.Cors"包,并对api controller使用[EnableCors]特性以及Microsoft.AspNetCore.Authentication.JwtBearer包
第二步:创建.netcore API项目 /控制器:AuthenticateController
using System;
using System.Collections.Generic;
using System.Linq;
using System.Text;
using System.Threading.Tasks;
using Microsoft.AspNetCore.Authorization;
using Microsoft.AspNetCore.Cors;
using Microsoft.AspNetCore.Mvc;
using Microsoft.Extensions.Options;
using Microsoft.IdentityModel.Tokens;
using static JSON_WEB_Token.Helper; namespace JSON_WEB_Token.Controllers
{ //跨域标签
[EnableCors("anyPolicy")]
//API接口打上Authorize标签
[Authorize]
[ApiController]
//路由配置
[Route("api/[controller]/[action]")]
public class AuthenticateController : ControllerBase
{
private JwtSettingsModel _jwtSettings;
public AuthenticateController(IOptions<JwtSettingsModel> jwtSetting)
{
_jwtSettings = jwtSetting.Value;
} [HttpPost]
public IActionResult Token([FromBody]PasswordModel request)
{
var key = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(_jwtSettings.SecetKey)); string userId = request.UserName == null ? request.UserName : request.UserNo;
if (request.UserName != "test" && request.PassWord != "" )
{
return BadRequest();
} var tokenModel = Helper.GetAccessTokenModel
(new UserData()
{
UserGid = strUserGid,
UserNo = "test"
},
*
); return Ok(tokenModel);
} } public class PasswordModel
{
public string UserName { get; set; }
public string PassWord { get; set; }
public string UserNo { get; set; }
public string ClientSecret { get; set; } }
}
第三步: Helper
using Microsoft.Extensions.Configuration;
using Microsoft.IdentityModel.Tokens;
using System;
using System.Collections.Generic;
using System.ComponentModel.DataAnnotations;
using System.IdentityModel.Tokens.Jwt;
using System.IO;
using System.Linq;
using System.Security.Claims;
using System.Text;
using System.Threading.Tasks; namespace JSON_WEB_Token
{
public class Helper
{
public static AccessTokenResponse GetAccessTokenModel(UserData userData, int hours = , DateTime? expireTimeSpan = null)
{
JwtSettingsModel _jwtSettings = GetAppsettings<JwtSettingsModel>("JwtSettings");
//创建claim
var claim = new Claim[]{
new Claim(ClaimTypes.Sid,userData.UserGid.ToString()),
new Claim(ClaimTypes.Name,userData.UserNo),
new Claim(ClaimTypes.Role,TokenRoleType.UserApp), };
//对称秘钥 签名秘钥
var key = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(_jwtSettings.SecetKey));
//签名证书(秘钥,加密算法)
var creds = new SigningCredentials(key, SecurityAlgorithms.HmacSha256);
//生成token
DateTime expiresDate = expireTimeSpan ?? System.DateTime.Now.AddHours(hours); var token = new JwtSecurityToken(_jwtSettings.Issuer, _jwtSettings.Audience, claim, DateTime.Now, expiresDate, creds); //保存token
var accessTokenModel = new AccessTokenResponse();
accessTokenModel.TokenType = "Bearer";
accessTokenModel.UserNo = userData.UserNo;
accessTokenModel.ExpiresDate = DateTimeToTimestamp(expiresDate);
accessTokenModel.AccessToken = new JwtSecurityTokenHandler().WriteToken(token);
return accessTokenModel; } public static long DateTimeToTimestamp(DateTime dateTime)
{
var start = new DateTime(, , , , , , dateTime.Kind);
return Convert.ToInt64((dateTime - start).TotalSeconds);
}
public class UserData
{
public Guid UserGid { get; set; }
public string UserNo { get; set; }
[Required]
public string UserName { get; set; }
public string PassWord { get; set; } } public class AccessTokenResponse
{
public string TokenType { get; set; } = "Bearer";
public string UserNo { get; set; }
public string AccessToken { get; set; }
public long ExpiresDate { get; set; } }
/// <summary>
/// 获取配置文件信息
/// </summary>
/// <typeparam name="T"></typeparam>
/// <param name="setKey"></param>
/// <returns></returns>
public static T GetAppsettings<T>(string setKey)
{ var builder = new Microsoft.Extensions.Configuration.ConfigurationBuilder()
.SetBasePath(Directory.GetCurrentDirectory())
.AddJsonFile("appsettings.json").Build();
return builder.GetSection(setKey).Get<T>();
} /// <summary>
/// Token用户类型
/// </summary>
public class TokenRoleType
{
/// <summary>
/// 匿名Token
/// </summary>
public const string GuoWaiApp = "国外渠道"; /// <summary>
/// 用户Token
/// </summary>
public const string UserApp = "国内渠道"; } } }
第四:JwtSettingsModel
using System;
using System.Collections.Generic;
using System.Linq;
using System.Threading.Tasks; namespace JSON_WEB_Token
{
public class JwtSettingsModel
{
//token是谁颁发的
public string Issuer { get; set; }
//token可以给哪些客户端使用
public string Audience { get; set; }
//加密的key 必须是16个字符以上,要大于128个字节
public string SecetKey { get; set; }
} public class AccessTokenErrModel
{
public string AppId { get; set; } public string errcode { get; set; }
public string errmsg { get; set; } public Guid UserGid { get; set; } }
}
第五:appsettings
{
"Logging": {
"LogLevel": {
"Default": "Information",
"Microsoft": "Warning",
"Microsoft.Hosting.Lifetime": "Information"
}
},
"AllowedHosts": "*",
"JwtSettings": {
"Issuer": "http://localhost:44305",
"Audience": "http://localhost:44305",
"SecetKey": "HelloWorldHelloWorldHelloWorld"
}
}
第六:Startup
using System;
using System.Collections.Generic;
using System.Linq;
using System.Text;
using System.Threading.Tasks;
using Microsoft.AspNetCore.Authentication.JwtBearer;
using Microsoft.AspNetCore.Builder;
using Microsoft.AspNetCore.Hosting;
using Microsoft.AspNetCore.HttpsPolicy;
using Microsoft.AspNetCore.Mvc;
using Microsoft.Extensions.Configuration;
using Microsoft.Extensions.DependencyInjection;
using Microsoft.Extensions.Hosting;
using Microsoft.Extensions.Logging;
using Microsoft.IdentityModel.Tokens; namespace JSON_WEB_Token
{
public class Startup
{
public Startup(IConfiguration configuration)
{
Configuration = configuration;
} public IConfiguration Configuration { get; } // This method gets called by the runtime. Use this method to add services to the container.
public void ConfigureServices(IServiceCollection services)
{
services.AddControllers(); #region json web token 添加认证服务
//将appsettings.json中的JwtSettings部分文件读取到JwtSettings中
services.Configure<JwtSettingsModel>(Configuration.GetSection("JwtSettings")); //使用Bind的方式读取配置
//将配置绑定到JwtSettings实例中
var jwtSettings = new JwtSettingsModel();
Configuration.Bind("JwtSettings", jwtSettings); services.AddAuthentication(options => {
//认证middleware配置
options.DefaultAuthenticateScheme = JwtBearerDefaults.AuthenticationScheme;
options.DefaultChallengeScheme = JwtBearerDefaults.AuthenticationScheme;
options.DefaultScheme = JwtBearerDefaults.AuthenticationScheme;
}).AddJwtBearer(options =>
{
//options.SaveToken = true;
//options.RequireHttpsMetadata = false;
//主要是jwt token参数设置
options.TokenValidationParameters = new TokenValidationParameters
{ //Token颁发机构
ValidIssuer = jwtSettings.Issuer,
//颁发给谁
ValidAudience = jwtSettings.Audience,
//这里的key要进行加密
IssuerSigningKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(jwtSettings.SecetKey)) };
});
#endregion #region 注册跨域请求服务 CORS 中间件处理跨域请求
//注册跨域请求服务 允许所有来源、所有方法、所有请求标头、允许请求凭据
services.AddCors(options =>
{
//注册默认策略
options.AddDefaultPolicy( builder =>
{
builder.AllowAnyOrigin()
.AllowAnyMethod()
.AllowAnyHeader()
// .AllowCredentials()
;
});
//注册一个策略名称
options.AddPolicy("anyPolicy", builder =>
{
builder.WithOrigins("http://127.0.0.1:9102", "https://www.baidu.com")
.AllowAnyMethod()
.AllowAnyHeader()
// .AllowCredentials()
;
});
});
services.AddMvc().SetCompatibilityVersion(CompatibilityVersion.Version_3_0);
#endregion
} // This method gets called by the runtime. Use this method to configure the HTTP request pipeline.
public void Configure(IApplicationBuilder app, IWebHostEnvironment env)
{
if (env.IsDevelopment())
{
app.UseDeveloperExceptionPage();
}
else
{
app.UseExceptionHandler("/Home/Error");
}
app.UseHttpsRedirection();
/////////////////////////////////////////////
//授权(Authorization)
app.UseAuthorization();
///添加中间件(Middleware) 启用验证
app.UseAuthentication();
/////////////////////////////////////////////////
app.UseCors("anyPolicy"); // 设置全局跨域
app.UseRouting(); app.UseEndpoints(endpoints =>
{
endpoints.MapControllers();
endpoints.MapControllerRoute(
name: "default",
pattern: "{controller=Authenticate}/{action=Index}/{id?}");
});
}
}
}
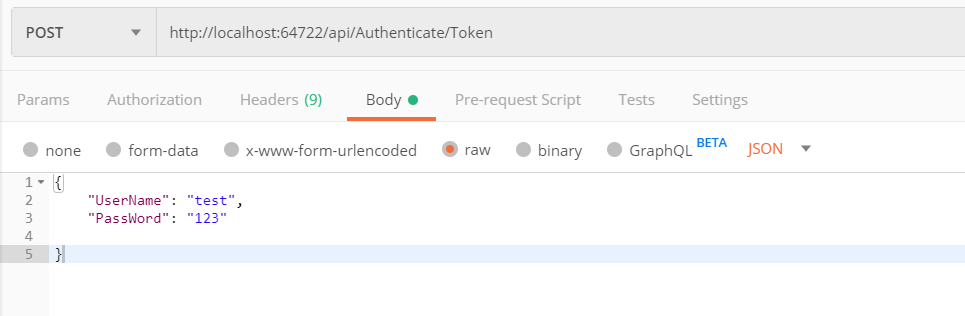
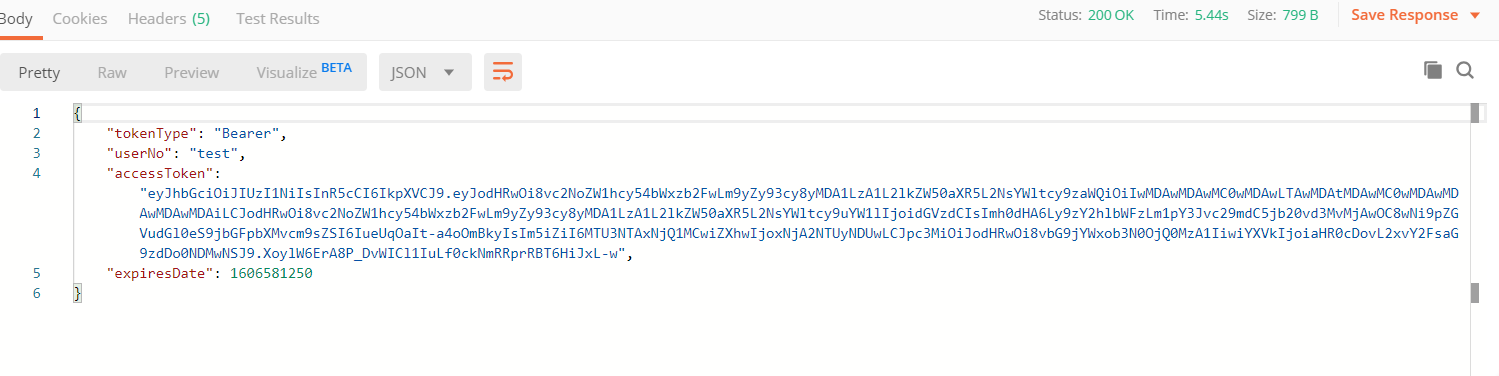
第七:postman请求
.Net Core 3.0 Api json web token 中间件签权验证和 Cors 中间件处理跨域请求的更多相关文章
- Handle Refresh Token Using ASP.NET Core 2.0 And JSON Web Token
来源: https://www.c-sharpcorner.com/article/handle-refresh-token-using-asp-net-core-2-0-and-json-web ...
- JSON Web Token(缩写 JWT) 目前最流行的跨域认证解决方案
一.跨域认证的问题 互联网服务离不开用户认证.一般流程是下面这样. 1.用户向服务器发送用户名和密码. 2.服务器验证通过后,在当前对话(session)里面保存相关数据,比如用户角色.登录时间等等. ...
- JWT(JSON Web Token) 【转载】
JWT(JSON Web Token) 什么叫JWTJSON Web Token(JWT)是目前最流行的跨域身份验证解决方案. 一般来说,互联网用户认证是这样子的. 1.用户向服务器发送用户名和密码. ...
- JSON Web Token(JWT)原理和用法介绍
JSON Web Token(JWT)是目前最流行的跨域身份验证解决方案.今天给大家介绍一下JWT的原理和用法. 官网地址:https://jwt.io/ 一.跨域身份验证 Internet服务无法与 ...
- JSON Web Token (JWT) 实现与使用方法
1. JSON Web Token是什么 JSON Web Token (JWT)是一个开放标准(RFC 7519),它定义了一种紧凑的.自包含的方式,用于作为JSON对象在各方之间安全地传输信息.该 ...
- 一分钟简单了解 JSON Web Token
JSON Web Token(JWT)是一个开放的标准(RFC 7519),它定义了一个紧凑且自包含的方式,用于在各方之间作为 JSON 对象安全地传输信息.由于此信息是经过数字签名的,因此可以被验证 ...
- ASP.NET Core 启用跨域请求
本文翻译整理自:https://docs.microsoft.com/en-us/aspnet/core/security/cors?view=aspnetcore-3.1 一 .Cross-Orig ...
- 把旧系统迁移到.Net Core 2.0 日记 (18) --JWT 认证(Json Web Token)
我们最常用的认证系统是Cookie认证,通常用一般需要人工登录的系统,用户访问授权范围的url时,会自动Redirect到Account/Login,登录后把认证结果存在cookie里. 系统只要找到 ...
- [转] JSON Web Token in ASP.NET Web API 2 using Owin
本文转自:http://bitoftech.net/2014/10/27/json-web-token-asp-net-web-api-2-jwt-owin-authorization-server/ ...
随机推荐
- Ubuntu 18.04 + Gtx 1660 安装Nvidia 显卡驱动
1.UEFI禁用secure boot(我的系统是win10主系统,引导ubuntu,安装驱动前电脑存在win10 uefi引导问题) Make sure the "OS Type" ...
- 【转】如何把变量或者数组定义到SDRAM及任意位置
我们开发软件的时候,经常会遇到到一个问题,就是内存不够,这个时候就纠结了,怎么办,有两种方法,第一种是扩展内存,外加SRAM或者SDRAM:第二种应该就是优化代码,也就是通常所说的把数组大小减一减,代 ...
- SaltStack--接口salt-api
SaltStack接口salt-api 介绍 参考官档参考官档 SaltStack官方提供有REST API格式的salt-api项目,将使salt与第三方系统集成变得更加简单. salt-api安装 ...
- font-awesome图标显示问题解决方案
font-awesome一个很强大的字体图标库.下载链接:http://fontawesome.dashgame.com/刚开始使用font-awesome的新手往往容易只引入一个css文件,这样就会 ...
- 201671030114 马秀丽 实验十四 团队项目评审&课程学习总结
项目 内容 作业所属课程 所属课程 作业要求 作业要求 课程学习目标 (1)掌握软件项目评审会流程:(2)反思总结课程学习内容 任务一:团队项目审核已完成.项目验收过程意见表已上交. 任务二:课程学习 ...
- 项目Beta冲刺(团队7/7)
项目Beta冲刺(团队) --7/7 作业要求: 项目Beta冲刺(团队) 1.团队信息 团队名 :男上加男 成员信息 : 队员学号 队员姓名 个人博客地址 备注 221600427 Alicesft ...
- Spring Boot 之:接口参数校验
Spring Boot 之:接口参数校验,学习资料 网址 SpringBoot(八) JSR-303 数据验证(写的比较好) https://qq343509740.gitee.io/2018/07/ ...
- Nginx——跨域造成的504问题
前言 前台域名和后台域名是两个不同不同的二级域名,访问的时候造成了跨域,出现了504错误 解决 修改Nginx配置,将超时的时间设置为1200秒 keepalive_timeout 1200; pro ...
- js的原型与模板类型
原型处于复用(原型)链上: 模版类型属于构造概念: 对象复用原型的数据和函数: 对象由模版类型+原型构造而成: 模版类型属于构造对象的临时变量,包含了对象空间的所有信息: 原型包含了对象所引用的原型空 ...
- 金融类openapi
股市URL解析 http://money.finance.sina.com.cn/moneyflow/?stockName=上证指数&symbol=sh000001&stockSymb ...
