Linux防火墙之iptables基本匹配条件和隐式扩展匹配条件
一、iptables的基本匹配条件
上一篇博文我们说到了iptables的基本工作原理、数据报文在内核的走向和管理链、管理规则、以及查看规则、导入和导出规则;回顾请参考https://www.cnblogs.com/qiuhom-1874/p/12237976.html,今天我们再来说说iptables的基本匹配条件。
iptables的基本匹配条件也叫通用匹配条件,是iptables/netfilter原生自带的,无需加载模块,通俗的讲就是iptables这个命令的原生选项。iptables基本匹配条件有以下几种
1、[!] -s,--source addresss[/mask][,…]:表示匹配报文段源ip地址或范围,它可以是一个ip地址,也可以是一个网段地址,网段地址需要写明子网掩码,其中子网掩码支持225.255.0.0的方式,也支持数字表示,比如192.168.0.0/24。同时它也支持取反。
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
461 33551 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
134 11256 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 14 packets, 1320 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 192.168.0.99 0.0.0.0/0 tcp spt:53
134 11256 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -A my_chain -s 192.168.1.0/24 -j ACCEPT
[root@test ~]# iptables -A my_chain -s 192.168.0.232 -d 192.168.0.99 -j ACCEPT
[root@test ~]# iptables -A my_chain -s 192.168.0.0/255.255.255.0 -j ACCEPT
[root@test ~]# iptables -nvL my_chain
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 192.168.1.0/24 0.0.0.0/0
0 0 ACCEPT all -- * * 192.168.0.232 192.168.0.99
0 0 ACCEPT all -- * * 192.168.0.0/24 0.0.0.0/0
[root@test ~]# iptables -A my_chain ! -s 192.168.10.0/24 -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
946 67475 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
134 11256 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 15 packets, 1396 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 192.168.0.99 0.0.0.0/0 tcp spt:53
134 11256 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 192.168.1.0/24 0.0.0.0/0
0 0 ACCEPT all -- * * 192.168.0.232 192.168.0.99
0 0 ACCEPT all -- * * 192.168.0.0/24 0.0.0.0/0
0 0 ACCEPT all -- * * !192.168.10.0/24 0.0.0.0/0
[root@test ~]#
2、-d,--destination address[/mask][,…]:表示匹配报文的目标ip地址或范围,它同-s的用法一样,支持单台主机或一个网段,网段需写明子网掩码,子网掩码支持数字表示,也支持子网掩码地址的方式表示。同时它也支持对匹配的条件取反。
[root@test ~]# iptables -F my_chain
[root@test ~]# iptables -nvL my_chain
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -A my_chain -d 192.168.0.99 -p tcp --dport 22 -j ACCEPT
[root@test ~]# iptables -A my_chain -d 192.168.0.10 -p tcp --dport 3306 -j DROP
[root@test ~]# iptables -A my_chain -d 192.168.10.0/24 -p tcp --dport 25 -j DROP
[root@test ~]# iptables -A my_chain ! -d 192.168.11.0/255.255.255.0 -p tcp --dport 123 -j DROP
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
1698 123K ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
134 11256 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 17 packets, 1580 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 192.168.0.99 0.0.0.0/0 tcp spt:53
134 11256 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:22
0 0 DROP tcp -- * * 0.0.0.0/0 192.168.0.10 tcp dpt:3306
0 0 DROP tcp -- * * 0.0.0.0/0 192.168.10.0/24 tcp dpt:25
0 0 DROP tcp -- * * 0.0.0.0/0 !192.168.11.0/24 tcp dpt:123
[root@test ~]#
3、[!] -p, --protocol protocol:指定协议,可使用数字如0(all);protocol: tcp, udp, icmp, icmpv6, udplite,esp, ah, sctp, mh or“all“ 参考:/etc/protocols
[root@test ~]# iptables -F my_chain
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
1752 126K ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
134 11256 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 13 packets, 1212 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 192.168.0.99 0.0.0.0/0 tcp spt:53
134 11256 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -A my_chain -s 192.168.0.232 -d 192.168.0.99 -p tcp --dport 80 -j DROP
[root@test ~]# iptables -A my_chain -s 192.168.0.232 -d 192.168.0.99 -p tcp --dport 23 -j DROP
[root@test ~]# iptables -A my_chain -d 192.168.0.99 -p tcp --sport 25 -j ACCEPT
[root@test ~]# iptables -A my_chain -d 192.168.0.99 -p icmp --icmp-type 0 -j ACCEPT
[root@test ~]# iptables -A my_chain -s 192.168.0.232 -d 192.168.0.99 -p icmp --icmp-type 8 -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2487 179K ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
134 11256 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 47 packets, 4340 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 192.168.0.99 0.0.0.0/0 tcp spt:53
134 11256 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 DROP tcp -- * * 192.168.0.232 192.168.0.99 tcp dpt:80
0 0 DROP tcp -- * * 192.168.0.232 192.168.0.99 tcp dpt:23
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp spt:25
0 0 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 0
0 0 ACCEPT icmp -- * * 192.168.0.232 192.168.0.99 icmptype 8
[root@test ~]# iptables -A my_chain ! -p udp -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2586 186K ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
134 11256 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 13 packets, 1212 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 192.168.0.99 0.0.0.0/0 tcp spt:53
134 11256 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 DROP tcp -- * * 192.168.0.232 192.168.0.99 tcp dpt:80
0 0 DROP tcp -- * * 192.168.0.232 192.168.0.99 tcp dpt:23
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp spt:25
0 0 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 0
0 0 ACCEPT icmp -- * * 192.168.0.232 192.168.0.99 icmptype 8
0 0 ACCEPT !udp -- * * 0.0.0.0/0 0.0.0.0/0
[root@test ~]#
提示:-p指定某一协议时,往往会有该协议的一些隐式扩展的选项,比如我们指定-p tcp 表示指定协议类型为tcp 后面指定的源端口或者目标端口 就是tcp模块的隐式。通俗讲就是我们指定了协议为tcp 可以不用明确的用-m 再指定其模块,这种机制我们叫隐式扩展。上面的例子用到了隐式扩展到有 tcp 的 --sport --dport ;icmp 协议的--icmp-type;当然-p指定协议的类型也可以用! 来对它取反,表示匹配除了指定的协议以为的所有协议的报文,如果不用-p 指定协议表示匹配所有协议的报文
4、[!] -i, --in-interface name:报文流入的接口;只能应用于数据报文流入环节,只应用于INPUT、FORWARD、PREROUTING链以及自定义链。
[root@test ~]# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp2s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:30:18:51:af:3c brd ff:ff:ff:ff:ff:ff
inet 192.168.0.99/24 brd 192.168.0.255 scope global noprefixroute enp2s0
valid_lft forever preferred_lft forever
inet 172.16.1.2/16 brd 172.16.255.255 scope global noprefixroute enp2s0:0
valid_lft forever preferred_lft forever
inet6 fe80::230:18ff:fe51:af3c/64 scope link
valid_lft forever preferred_lft forever
3: enp3s0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc pfifo_fast state DOWN group default qlen 1000
link/ether 00:30:18:51:af:3d brd ff:ff:ff:ff:ff:ff
4: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:63:ab:82:55 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 scope global docker0
valid_lft forever preferred_lft forever
[root@test ~]# iptables -F my_chain
[root@test ~]# iptables -nvL my_chain
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -A my_chain -s 192.168.0.0/24 -i enp2s0 -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2911 209K ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
134 11256 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 13 packets, 1212 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 192.168.0.99 0.0.0.0/0 tcp spt:53
134 11256 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- enp2s0 * 192.168.0.0/24 0.0.0.0/0
[root@test ~]# iptables -A OUTPUT -i enp2s0 -j ACCEPT
iptables v1.4.21: Can't use -i with OUTPUT Try `iptables -h' or 'iptables --help' for more information.
[root@test ~]#
提示:自定义添加到规则可以被任意主链所引用。不存在自定义链上的规则不适用主链,但主链上可以引用它的,只是说主链引用后,规则不生效,匹配不到报文。-i 表示指定网络报文流入的接口,所以这个基本匹配条件,只能用于报文能够进来的链上,比如PREROUTING、INPUT、FORWARD这三个主链,以及自定义链,通常情况,如果写到自定义链,都是被这三个主链所引用,除此之外,被OUTPUT、和POSTROUTING所引用,规则是无效的,不能匹配到报文。
5、[!] -o, --out-interface name:报文流出的接口;只能应用于数据报文流出的环节,只应用于FORWARD、OUTPUT、POSTROUTING链以及自定义链
[root@test ~]# ip a s
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp2s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:30:18:51:af:3c brd ff:ff:ff:ff:ff:ff
inet 192.168.0.99/24 brd 192.168.0.255 scope global noprefixroute enp2s0
valid_lft forever preferred_lft forever
inet 172.16.1.2/16 brd 172.16.255.255 scope global noprefixroute enp2s0:0
valid_lft forever preferred_lft forever
inet6 fe80::230:18ff:fe51:af3c/64 scope link
valid_lft forever preferred_lft forever
3: enp3s0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc pfifo_fast state DOWN group default qlen 1000
link/ether 00:30:18:51:af:3d brd ff:ff:ff:ff:ff:ff
4: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:63:ab:82:55 brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 scope global docker0
valid_lft forever preferred_lft forever
[root@test ~]# iptables -F my_chain
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
66 4512 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
0 0 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 13 packets, 1212 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -A my_chain -o enp2s0 -j ACCEPT
[root@test ~]# iptables -A INPUT -o enp2s0 -j DROP
iptables v1.4.21: Can't use -o with INPUT Try `iptables -h' or 'iptables --help' for more information.
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
238 16280 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
0 0 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 61 packets, 5724 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * enp2s0 0.0.0.0/0 0.0.0.0/0
[root@test ~]#
提示:同样-o表示匹配网络报文的出口接口,不能用于网络报文入口的链上。在iptables/netfilter框架中,报文的出口只经过FORWARD、OUTPUT和POSTROUTING这三个主链,即便我们在自定义链上用-o来指定匹配出口的网络接口,也只有被FORWARD、OUTPUT或者POSTROUTING这三个主链所引用才能生效,匹配到报文,用在INPUT或PREROUTING链上iptables是不允许的。可以看到FORWARD这个链上即可以匹配网络报文的入口接口和出口接口。
二、tcp/udp/icmp隐式扩展选项说明
iptables的匹配条件分基本匹配条件和扩展匹配条件,扩展匹配条件里有显示扩展和隐式扩展,从字面上很好理解,显示就是明确指定嘛 ,隐式就是不明确指定,通常扩展匹配条件是需要加载扩展模块(/usr/lib64/xtables/*.so)方可生效;隐式扩展我们可以理解为,当我们使用-p 去指定协议时无需再用-m再指定其模块,就可以使用其扩展模块中的选项,也就是说不需要我们手动的去加载模块,-p 所指定的协议,会帮我们加载。(这个仅个人理解哈)
1、tcp协议的隐式扩展选项说明
[!] --source-port, --sport port[:port]:匹配报文源端口,可为端口范围,当端口连续时可以用:来表示;比如21:25,表示匹配21,22,23,24,25这些连续的端口。
[root@test ~]# iptables -F my_chain
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
878 58520 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
0 0 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 13 packets, 1212 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -A my_chain -s 192.168.0.232 -d 192.168.0.99 -p tcp --sport 22 -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
1324 93312 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
0 0 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 34 packets, 3144 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 192.168.0.232 192.168.0.99 tcp spt:22
[root@test ~]#
提示:以上添加到规则表示匹配源地址为192.168.0.232 目标地址为192.168.0.99 的tcp报文,并且源端口为22 的报文,如果匹配到这样的报文,给予放行操作。当然如果是匹配一个连续的端口可以写成:来表示中间连续的端口,它也支持对源端口取反,表示匹配除了指定的端口以外的所有端口如下所示
[root@test ~]# iptables -A my_chain -s 192.168.0.232 -d 192.168.0.99 -p tcp --sport 23:30 -j ACCEPT
[root@test ~]# iptables -nvL my_chain
Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 192.168.0.232 192.168.0.99 tcp spt:22
0 0 ACCEPT tcp -- * * 192.168.0.232 192.168.0.99 tcp spts:23:30
[root@test ~]# iptables -A my_chain -s 192.168.0.232 -d 192.168.0.99 -p tcp ! --sport 40:50 -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
1519 107K ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:41319
0 0 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.99 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 13 packets, 1212 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT icmp -- * * 192.168.0.99 0.0.0.0/0 icmptype 0 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 192.168.0.232 192.168.0.99 tcp spt:22
0 0 ACCEPT tcp -- * * 192.168.0.232 192.168.0.99 tcp spts:23:30
0 0 ACCEPT tcp -- * * 192.168.0.232 192.168.0.99 tcp spts:!40:50
[root@test ~]#
[!] --destination-port,--dport port[:port]:匹配报文目标端口,可为范围,当端口连续是也可以用:来代替连续中间的端口,同--sport用法一样
[root@test ~]# iptables -F
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 19 packets, 1332 bytes)
pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 13 packets, 1212 bytes)
pkts bytes target prot opt in out source destination Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -A my_chain -d 192.168.0.99 -p tcp --dport 22 -j ACCEPT
[root@test ~]# iptables -A my_chain -d 192.168.0.99 -p tcp --dport 23:25 -j ACCEPT
[root@test ~]# iptables -A my_chain -d 192.168.0.99 -p tcp ! --dport 80 -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 19 packets, 1332 bytes)
pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 13 packets, 1212 bytes)
pkts bytes target prot opt in out source destination Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:22
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpts:23:25
0 0 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.99 tcp dpt:!80
[root@test ~]#
[!] --tcp-flags mask comp表示匹配符合指定标志的数据报文,mask表示需检查的标志为列表,用逗号分隔,例如SYN,ACK,FIN,RST;comp表示mask列表中必须为1的标志为列表,没有指定表示必须为0用逗号分隔
[root@test ~]# iptables -F
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 22 packets, 1556 bytes)
pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 15 packets, 1396 bytes)
pkts bytes target prot opt in out source destination Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -A my_chain -p tcp --tcp-flags SYN,ACK,FIN,RST SYN -j ACCEPT
[root@test ~]# iptables -A my_chain -p tcp --tcp-flags ALL ALL -j DROP
[root@test ~]# iptables -A my_chain -p tcp --tcp-flags ALL NONE -j DROP
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 47 packets, 3830 bytes)
pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 39 packets, 3630 bytes)
pkts bytes target prot opt in out source destination Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x17/0x02
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x3F
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x00
[root@test ~]#
提示:以上规则表示匹配tcp报文,syn=1 其他标志位为0的报文给予允许放行,匹配所有标志位为1的报文给予丢弃,匹配到所有标志为0的报文给予丢弃。这个扩展选项也支持取反,表示出了指定的标志位的所有报文。
[!] --syn:用于匹配TCP第一次握手报文,它相当于--tcp-flags SYN,ACK,FIN,RST SYN
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 73 packets, 5582 bytes)
pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 61 packets, 6538 bytes)
pkts bytes target prot opt in out source destination Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x17/0x02
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x3F
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x00
[root@test ~]# iptables -A INPUT -p tcp --syn -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 11 packets, 804 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x17/0x02 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 8 packets, 864 bytes)
pkts bytes target prot opt in out source destination Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x17/0x02
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x3F
0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x00
[root@test ~]#
2、udp协议的隐式扩展选项说明
[!] --source-port, --sport port[:port]:匹配报文的源端口或端口范围,当端口连续可以使用:来代替连续的中间端口
[root@test ~]# iptables -F
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 24 packets, 1636 bytes)
pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 15 packets, 1396 bytes)
pkts bytes target prot opt in out source destination Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -A OUTPUT -p udp --sport 928 -j ACCEPT
[root@test ~]# iptables -A OUTPUT -p udp --sport 111:123 -j ACCEPT
[root@test ~]# iptables -A OUTPUT -p udp ! --sport 323 -j DROP
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 14 packets, 1028 bytes)
pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 10 packets, 1144 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:928
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spts:111:123
0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:!323 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]#
[!] --destination-port,--dport port[:port]:匹配报文的目标端口或端口范围,当端口连续可以使用:来代替连续的中间端口
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 73 packets, 5156 bytes)
pkts bytes target prot opt in out source destination Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 54 packets, 6288 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:928
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spts:111:123
1 76 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:!323 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -A INPUT -p udp --dport 928 -j ACCEPT
[root@test ~]# iptables -A INPUT -p udp --dport 111:123 -j ACCEPT
[root@test ~]# iptables -A INPUT -p udp ! --dport 323 -j DROP
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 14 packets, 1028 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:928
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpts:111:123
0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:!323 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 10 packets, 1160 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:928
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spts:111:123
1 76 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:!323 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]#
3、icmp协议的隐式扩展选项
[!] --icmp-type {type[/code]|typename}
type/code 的值代表意义
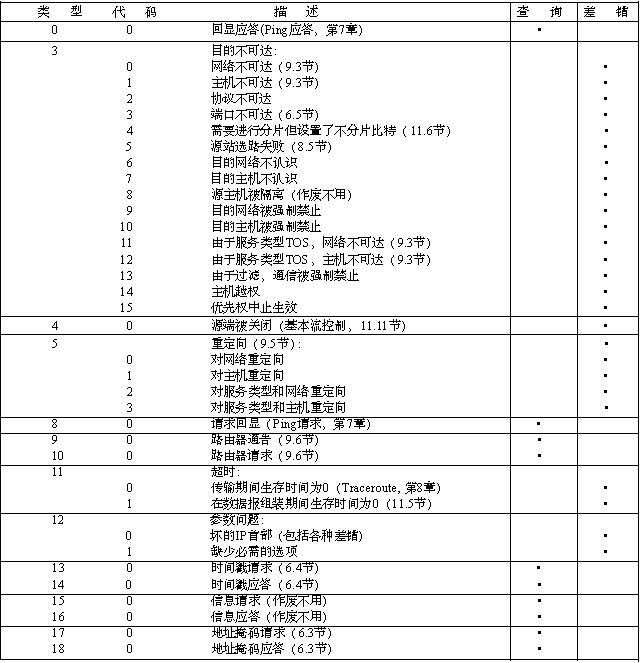
备注:此图片来源网络
从上面的表可以看到不同的type,所表达的意思不同,就拿icmp最常用的两个类型,0和8来说,0表示icmp的应答数据包类型,就好比我们去用ping工具去探测远端主机是否存活,可以向远端主机发送icmp协议的8号类型的数据包,对方收到这种类型的数据包,如果正常存活,它会回复一个icmp0号类型的消息,否则它会恢复一个其他类型的数据包(通常情况在对方主机没有设置任何针对icmp协议报文的控制时)
在iptables里允许我们去ping对方,不允许对方ping我们
[root@test ~]# iptables -F
[root@test ~]# iptables -A OUTPUT -p icmp --icmp-type 8 -j ACCEPT
[root@test ~]# iptables -A INPUT -p icmp --icmp-type 0 -j ACCEPT
[root@test ~]# iptables -A INPUT -p icmp --icmp-type 8 -j DROP
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 25 packets, 1780 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 0
0 0 DROP icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 17 packets, 1580 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]#
提示:把以上三条规则添加到iptabels中就可以实现我们本机发出去的icmp类型为8 的报文可以正常放行,从对方主机返回icmp类型为0的应答报文可以正常放行,同时明确指定发往本机icmp类型为8的请求报文给予丢弃操作
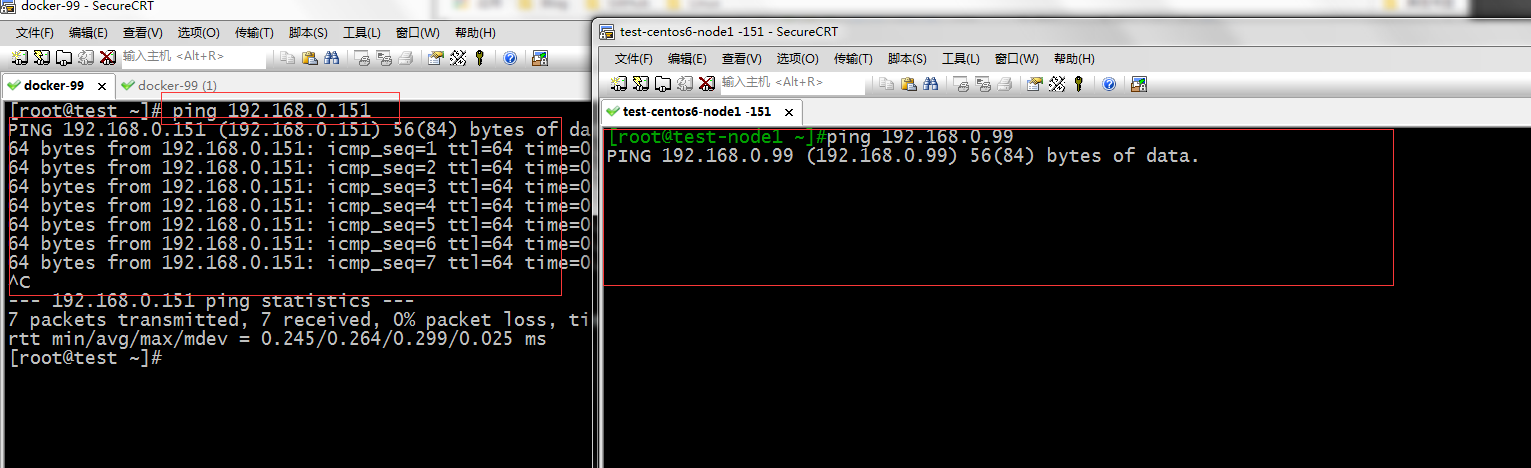
提示:这样是可以拒绝别人用ping工具来探测我们防火墙主机是否存活,当然这样设置后,我们自己想探测都不行了,要想设置自己可以探测,我们可以在规则里添加对应的规则。明确放行特定的icmp数据报文
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 30 packets, 2084 bytes)
pkts bytes target prot opt in out source destination
15 1260 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 0
35 2940 DROP icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 19 packets, 1780 bytes)
pkts bytes target prot opt in out source destination
36 3024 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]# iptables -I INPUT -s 192.168.0.151 -p icmp --icmp-type 8 -j ACCEPT
[root@test ~]# iptables -A OUTPUT -d 192.168.0.151 -p icmp --icmp-type 0 -j ACCEPT
[root@test ~]# iptables -nvL
Chain INPUT (policy ACCEPT 8 packets, 528 bytes)
pkts bytes target prot opt in out source destination
12 1008 ACCEPT icmp -- * * 192.168.0.151 0.0.0.0/0 icmptype 8
15 1260 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 0
46 3864 DROP icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8 Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 5 packets, 764 bytes)
pkts bytes target prot opt in out source destination
36 3024 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
0 0 ACCEPT icmp -- * * 0.0.0.0/0 192.168.0.151 icmptype 0 Chain my_chain (0 references)
pkts bytes target prot opt in out source destination
[root@test ~]#
提示:如果OUTPUT链的默认处理动作是DROP 需要配置以上两条规则,如果默认规则是ACCEPT 那么在INPUT链上添加一条允许指定源ip的报文允许就可以了

提示:可以看到添加了指定的源ip主机允许规则后,用对应的主机ping防火墙主机了。
以上就是tcp、udp、icmp这三种协议的常用隐式扩展选项。
Linux防火墙之iptables基本匹配条件和隐式扩展匹配条件的更多相关文章
- Linux防火墙配置(iptables, firewalld)
netfilter和底层实现 iptables firealld Linux中的防火墙 RHEL中有几种防火墙共存: iptables firewalld ip6tables ebtables 这些软 ...
- Linux防火墙之iptables常用扩展匹配条件(一)
上一篇博文讲了iptables的基本匹配条件和隐式匹配条件,回顾请参考https://www.cnblogs.com/qiuhom-1874/p/12269717.html:今天在来说说iptabel ...
- Linux防火墙(iptables/firewalld)
Linux防火墙(iptables/firewalld) 目录 Linux防火墙(iptables/firewalld) 一.iptables 1. iptables概述 2. netfilter和i ...
- Linux防火墙简介 – iptables配置策略
Linux防火墙简介 – iptables配置策略 Netfilter/iptables简介 要想真正掌握Linux防火墙体系,首先要搞清楚Netfilter和iptables的关系,Netfilte ...
- linux防火墙之iptables
linux防火墙之iptables 1.1.1 关于iptables简介 IPTABLES 是与最新的 3.5 版本 Linux 内核集成的 IP 信息包过滤系统.如果 Linux 系统连接到因特网或 ...
- Android隐式启动匹配:action,category,data
简介 Android开发中,Activity,Service 和 BroadcastReceiver 启动有两种方式,显示启动和隐式启动. 为方便下面描述,我以Activity启动为例. 显示启动便是 ...
- Linux防火墙之iptables常用扩展匹配条件(二)
上一篇博文我们讲到了iptables的一些常用的扩展匹配模块以及扩展模块的一些选项的说明,回顾请参考https://www.cnblogs.com/qiuhom-1874/p/12273755.htm ...
- Linux防火墙之iptables入门
一.防火墙的概念 什么是防火墙?防火墙是一台或一组设备,用以在网络间实施访问控制策略:事实上一个防火墙能够包含OSI模型中的很多层,并且可能会涉及进行数据包过滤的设备,它可以实施数据包检查和过滤,在更 ...
- Linux防火墙设置——iptables
防火墙用于监控往来流量,并根据用户定义的规则来过滤数据包以保证安全.iptables是Linux下设置防火墙规则的常用工具,它可以让你设置.维护以及查看防火墙的规则表.你可以定义多个表,每个表可以包含 ...
随机推荐
- leetcode.769旋转字符串
给定两个字符串, A 和 B. A 的旋转操作就是将 A 最左边的字符移动到最右边. 例如, 若 A = 'abcde',在移动一次之后结果就是'bcdea' .如果在若干次旋转操作之后,A 能变成B ...
- 洛谷$P3756\ [CQOI2017]$老$C$的方块 网络流
正解:网络流 解题报告: 传送门$QwQ$ 看到不能出现给定的讨厌的图形,简单来说就,特殊边两侧的方格不能同时再连方格. 所以如果出现,就相当于是四种方案?就分别炸四个格子. 然后冷静分析一波之后发现 ...
- Java中日期格式化YYYY-DD的坑
写这篇博文是记录下跨年的bug.去年隔壁组的小伙伴就是计算两个日期之间间隔的天数,因为跨年的原因计算有误. 当时测试组的小姐姐也没有模拟出来这种场景,导致上生产环境直接影响线上的数据. 今天逛技术论论 ...
- 洛谷P2602 [ZJOI2010]数字计数 题解 数位DP
题目链接:https://www.luogu.com.cn/problem/P2602 题目大意: 计算区间 \([L,R]\) 范围内 \(0 \sim 9\) 各出现了多少次? 解题思路: 使用 ...
- .Net Core 认证系统之基于Identity Server4 Token的JwtToken认证源码解析
介绍JwtToken认证之前,必须要掌握.Net Core认证系统的核心原理,如果你还不了解,请参考.Net Core 认证组件源码解析,且必须对jwt有基本的了解,如果不知道,请百度.最重要的是你还 ...
- Go合集,gRPC源码分析,算法合集
年初时,朋友圈见到的最多的就是新的一年新的FlAG,年末时朋友圈最多的也是xxxx就要过去了,你的FLAG实现了吗? 这个公众号2016就已经创建了,但截至今年之前从来没发表过文章,现在想想以前很忙, ...
- python3 三行代码基于HTTP2完美实现APNS推送【详解】
第一次做苹果APNS(Apple Push Notification service)推送,关于APNS推送原理以及证书的获取方式网上已经有许多资料,在此不做过多赘述,需要注意的是证书分为测试证书和正 ...
- MD5:js,java,C#三种语言加密结果不同解决办法
最近遇到前端js MD5加密与后端C#与Java MD5加密结果不一致的问题,所以写个关于此问题的解决办法 前端js引用的md5类库,类库地址:https://blueimp.github.io/Ja ...
- String类方法的使用
String类的判断功能: boolean equals(Object obj) //比较字符串内容是否相同(区分大小写). boolean equalsIgnoreCase(String str) ...
- java开源工作流引擎jflow的流程应用类型分类讲解
关键字: 驰骋工作流程快速开发平台 工作流程管理系统 工作流引擎 asp.net工作流引擎 java工作流引擎. 开发者表单 拖拽式表单 工作流系统CCBPM节点访问规则接收人规则 适配数据库: o ...
