附021.Traefik-ingress部署及使用
一 Helm部署
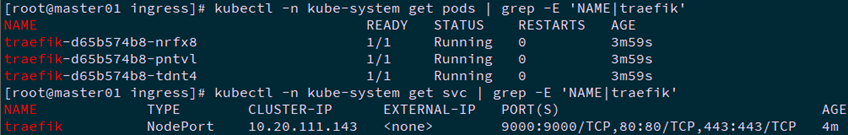
1.1 获取资源
1.2 配置traefik
1 deployment:
2 enabled: true
3 # Number of pods of the deployment
4 replicas: 3
5 ports:
6 traefik:
7 port: 9000
8 expose: true
9 nodePort: 9000
10 web:
11 port: 8000
12 expose: true
13 nodePort: 80
14 websecure:
15 port: 8443
16 expose: true
17 nodePort: 443
18 service:
19 enabled: true
20 type: NodePort
二 手动部署
2.1 创建CRD资源
1 ---
2 ## IngressRoute
3 apiVersion: apiextensions.k8s.io/v1beta1
4 kind: CustomResourceDefinition
5 metadata:
6 name: ingressroutes.traefik.containo.us
7
8 spec:
9 group: traefik.containo.us
10 version: v1alpha1
11 names:
12 kind: IngressRoute
13 plural: ingressroutes
14 singular: ingressroute
15 scope: Namespaced
16
17 ---
18 ## Middleware
19 apiVersion: apiextensions.k8s.io/v1beta1
20 kind: CustomResourceDefinition
21 metadata:
22 name: middlewares.traefik.containo.us
23
24 spec:
25 group: traefik.containo.us
26 version: v1alpha1
27 names:
28 kind: Middleware
29 plural: middlewares
30 singular: middleware
31 scope: Namespaced
32
33 ---
34 ## IngressRouteTCP
35 apiVersion: apiextensions.k8s.io/v1beta1
36 kind: CustomResourceDefinition
37 metadata:
38 name: ingressroutetcps.traefik.containo.us
39
40 spec:
41 group: traefik.containo.us
42 version: v1alpha1
43 names:
44 kind: IngressRouteTCP
45 plural: ingressroutetcps
46 singular: ingressroutetcp
47 scope: Namespaced
48
49 ---
50 ## IngressRouteUDP
51 apiVersion: apiextensions.k8s.io/v1beta1
52 kind: CustomResourceDefinition
53 metadata:
54 name: ingressrouteudps.traefik.containo.us
55
56 spec:
57 group: traefik.containo.us
58 version: v1alpha1
59 names:
60 kind: IngressRouteUDP
61 plural: ingressrouteudps
62 singular: ingressrouteudp
63 scope: Namespaced
64
65 ---
66 ## TLSOption
67 apiVersion: apiextensions.k8s.io/v1beta1
68 kind: CustomResourceDefinition
69 metadata:
70 name: tlsoptions.traefik.containo.us
71
72 spec:
73 group: traefik.containo.us
74 version: v1alpha1
75 names:
76 kind: TLSOption
77 plural: tlsoptions
78 singular: tlsoption
79 scope: Namespaced
80
81 ---
82 ## TLSStore
83 apiVersion: apiextensions.k8s.io/v1beta1
84 kind: CustomResourceDefinition
85 metadata:
86 name: tlsstores.traefik.containo.us
87
88 spec:
89 group: traefik.containo.us
90 version: v1alpha1
91 names:
92 kind: TLSStore
93 plural: tlsstores
94 singular: tlsstore
95 scope: Namespaced
96
97 ---
98 ## TraefikService
99 apiVersion: apiextensions.k8s.io/v1beta1
100 kind: CustomResourceDefinition
101 metadata:
102 name: traefikservices.traefik.containo.us
103
104 spec:
105 group: traefik.containo.us
106 version: v1alpha1
107 names:
108 kind: TraefikService
109 plural: traefikservices
110 singular: traefikservice
111 scope: Namespaced
2.2 创建账户RBAC
1 ---
2 ## ServiceAccount
3 apiVersion: v1
4 kind: ServiceAccount
5 metadata:
6 namespace: kube-system
7 name: traefik-ingress-controller
8 ---
9 ## ClusterRole
10 kind: ClusterRole
11 apiVersion: rbac.authorization.k8s.io/v1beta1
12 metadata:
13 name: traefik-ingress-controller
14
15 rules:
16 - apiGroups:
17 - ""
18 resources:
19 - services
20 - endpoints
21 - secrets
22 verbs:
23 - get
24 - list
25 - watch
26 - apiGroups:
27 - extensions
28 resources:
29 - ingresses
30 verbs:
31 - get
32 - list
33 - watch
34 - apiGroups:
35 - extensions
36 resources:
37 - ingresses/status
38 verbs:
39 - update
40 - apiGroups:
41 - traefik.containo.us
42 resources:
43 - middlewares
44 - ingressroutes
45 - traefikservices
46 - ingressroutetcps
47 - ingressrouteudps
48 - tlsoptions
49 - tlsstores
50 verbs:
51 - get
52 - list
53 - watch
54 ---
55 ## ClusterRoleBinding
56 kind: ClusterRoleBinding
57 apiVersion: rbac.authorization.k8s.io/v1beta1
58 metadata:
59 name: traefik-ingress-controller
60
61 roleRef:
62 apiGroup: rbac.authorization.k8s.io
63 kind: ClusterRole
64 name: traefik-ingress-controller
65 subjects:
66 - kind: ServiceAccount
67 name: traefik-ingress-controller
68 namespace: kube-system
2.3 创建Service
1 ---
2 apiVersion: v1
3 kind: Service
4 metadata:
5 name: traefik
6 namespace: kube-system
7
8 spec:
9 type: NodePort
10 ports:
11 - protocol: TCP
12 name: web
13 port: 8000
14 targetPort: 8000
15 nodePort: 80
16 - protocol: TCP
17 name: admin
18 port: 8080
19 targetPort: 8080
20 nodePort: 8080
21 - protocol: TCP
22 name: websecure
23 port: 4443
24 targetPort: 4443
25 nodePort: 443
26 selector:
27 app: traefik
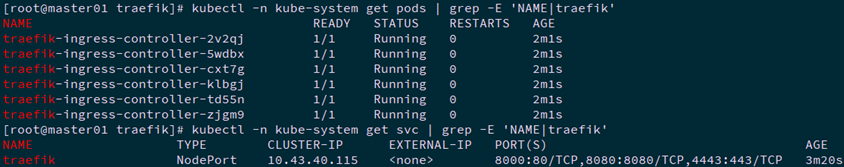
2.4 部署traefik
1 ## Static configuration
2 entryPoints:
3 web:
4 address: ":8000"
5
6 websecure:
7 address: ":4443"
8
9 certificatesResolvers:
10 myresolver:
11 acme:
12 tlschallenge: {}
13 email: xhy@itzgr.com
14 storage: acme.json
15 caserver: https://acme-staging-v02.api.letsencrypt.org/directory
16 tls:
17 certificates:
18 - certFile: /ssl/tls.crt
19 keyFile: /ssl/tls.key
20
21 api:
22 dashboard: true
23 insecure: true
24 ping: {}
25 metrics:
26 prometheus: {}
27 # Writing Logs to a File, in JSON
28 log:
29 filePath: "/var/traefik.log"
30 format: json
31 level: DEBUG
32 # Configuring a buffer of 100 lines
33 accessLog: {}
34 accessLog:
35 filePath: "/var/access.log"
36 format: json
37 providers:
38 kubernetesIngress: {}
39 kubernetescrd: {}
40 ## Static configuration
41 serversTransport:
42 insecureSkipVerify: true
1 ---
2 #kind: Deployment
3 kind: DaemonSet
4 apiVersion: apps/v1
5 metadata:
6 namespace: kube-system
7 name: traefik-ingress-controller
8 labels:
9 app: traefik
10
11 spec:
12 # replicas: 1
13 selector:
14 matchLabels:
15 app: traefik
16 template:
17 metadata:
18 labels:
19 app: traefik
20 spec:
21 serviceAccountName: traefik-ingress-controller
22 volumes:
23 - name: ssl
24 secret:
25 secretName: traefik-tls
26 - name: config
27 configMap:
28 name: traefik-config
29 containers:
30 - name: traefik
31 image: traefik:v2.2
32 volumeMounts:
33 - mountPath: "/ssl"
34 name: ssl
35 - mountPath: "/config"
36 name: config
37 args:
38 - --configfile=/config/traefik-cust.yaml
39 ports:
40 - name: web
41 containerPort: 8000
42 hostPort: 80
43 - name: websecure
44 containerPort: 4443
45 hostPort: 443
46 - name: admin
47 containerPort: 8080
48 hostPort: 8080
49 readinessProbe:
50 httpGet:
51 path: /ping
52 port: 8080
53 failureThreshold: 3
54 initialDelaySeconds: 10
55 periodSeconds: 10
56 successThreshold: 1
57 timeoutSeconds: 5
58 livenessProbe:
59 httpGet:
60 path: /ping
61 port: 8080
62 failureThreshold: 3
63 initialDelaySeconds: 10
64 periodSeconds: 10
65 successThreshold: 1
66 timeoutSeconds: 5
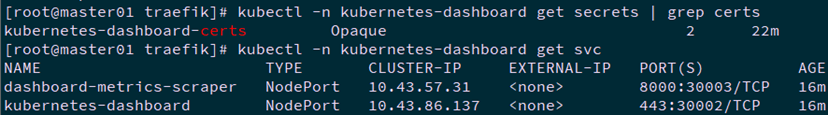
2.5 创建dashboard
三 traefik使用示例
3.1 route方式
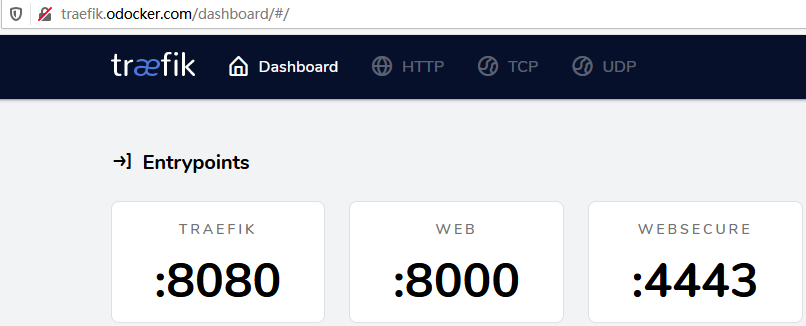
- route暴露http:以暴露traefik自身的UI为例
1 apiVersion: traefik.containo.us/v1alpha1
2 kind: IngressRoute
3 metadata:
4 name: traefik-dashboard-route-http
5 namespace: kube-system
6 spec:
7 entryPoints:
8 - web
9 routes:
10 - match: Host(`traefik.odocker.com`)
11 kind: Rule
12 services:
13 - name: traefik
14 port: 8080
- route暴露https:以暴露Kubernetes的dashboard为例
1 apiVersion: traefik.containo.us/v1alpha1
2 kind: IngressRoute
3 metadata:
4 name: kubernetes-dashboard-route-https
5 namespace: kubernetes-dashboard
6 spec:
7 entryPoints:
8 - websecure
9 tls:
10 secretName: kubernetes-dashboard-certs
11 routes:
12 - match: Host(`dashboard.odocker.com`)
13 kind: Rule
14 services:
15 - name: kubernetes-dashboard
16 port: 443
3.2 ingress方式
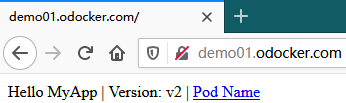
- ingress暴露http:创建一个用于测试的demo示例
1 apiVersion: v1
2 kind: Service
3 metadata:
4 name: traefikdemo01svc
5 namespace: default
6 spec:
7 selector:
8 app: traefikdemo01
9 ports:
10 - name: http
11 port: 80
12 targetPort: 80
13 ---
14 apiVersion: apps/v1
15 kind: Deployment
16 metadata:
17 name: traefikdemo01pod
18 spec:
19 replicas: 3
20 selector:
21 matchLabels:
22 app: traefikdemo01
23 template:
24 metadata:
25 labels:
26 app: traefikdemo01
27 spec:
28 containers:
29 - name: myapp
30 image: ikubernetes/myapp:v2
31 ports:
32 - name: httpd
33 containerPort: 80
1 ---
2 apiVersion: extensions/v1beta1
3 kind: Ingress
4 metadata:
5 name: traefik-ingress-demo01
6 namespace: default
7 annotations:
8 kubernetes.io/ingress.class: "traefik"
9 spec:
10 rules:
11 - host: demo01.odocker.com
12 http:
13 paths:
14 - path:
15 backend:
16 serviceName: traefikdemo01svc
17 servicePort: 80
- ingress暴露https:以暴露traefik的dashboard为例
1 apiVersion: extensions/v1beta1
2 kind: Ingress
3 metadata:
4 name: traefik-dashboard-ingress-https
5 namespace: kube-system
6 annotations:
7 kubernetes.io/ingress.class: "traefik"
8 spec:
9 tls:
10 - secretName: traefik-tls
11
12 rules:
13 - host: traefik.odocker.com
14 http:
15 paths:
16 - path:
17 backend:
18 serviceName: traefik
19 servicePort: 8080
3.3 自动调整
可通过配置自动调整,使http自动调整至https,本示例采用route方式实现,以暴露traefik dashboard为例。
[root@master01 traefik]# kubectl delete -f kubectl delete -f traefik-dashboard-ingress-https.yaml #删除3.1的route方式暴露的traefik dashboard
[root@master01 traefik]# vi traefik-cust.yaml
1 ……
2 entryPoints:
3 web:
4 address: ":80"
5 http:
6 redirections:
7 entryPoint:
8 to: websecure
9 scheme: https #追加重写至https配置
10 ……
[root@master01 traefik]# kubectl delete -n kube-system configmaps traefik-config
[root@master01 traefik]# kubectl create configmap traefik-config --from-file=traefik-cust.yaml -n kube-system
[root@master01 traefik]# kubectl apply -f traefik-deploy.yaml
[root@master01 traefik]# vi traefik-dashboard-route-http.yaml
[root@master01 traefik]# vi traefik-dashboard-route-https.yaml
1 apiVersion: traefik.containo.us/v1alpha1
2 kind: IngressRoute
3 metadata:
4 name: traefik-dashboard-route-https
5 namespace: kube-system
6 spec:
7 entryPoints:
8 - websecure
9 tls:
10 secretName: traefik-tls
11 routes:
12 - match: Host(`traefik.odocker.com`)
13 kind: Rule
14 services:
15 - name: traefik
16 port: 8080
[root@master01 traefik]# kubectl apply -f traefik-dashboard-route-http.yaml
[root@master01 traefik]# kubectl apply -f traefik-dashboard-route-https.yaml
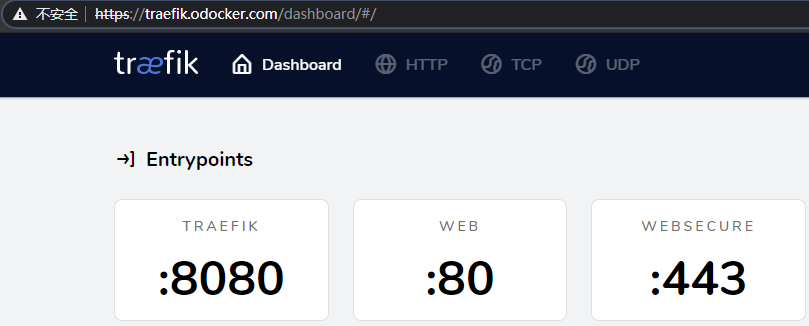
浏览器访问:http://traefik.odocker.com。
参考:https://docs.traefik.io/user-guides/crd-acme/。
http://www.mydlq.club/article/72/。
附021.Traefik-ingress部署及使用的更多相关文章
- 实操教程丨如何在K8S集群中部署Traefik Ingress Controller
注:本文使用的Traefik为1.x的版本 在生产环境中,我们常常需要控制来自互联网的外部进入集群中,而这恰巧是Ingress的职责. Ingress的主要目的是将HTTP和HTTPS从集群外部暴露给 ...
- Kubernets二进制安装(16)之安装部署traefik(ingress)
K8S的DNS实现了服务在集群"内"被自动发现,如何使得服务在Kuberneters集群"外"被使用和访问呢,有二种方法 1)使用NodePort型的Servi ...
- Kubernetes 服务入口管理 Traefik Ingress Controller
前面部署了 kubernetes/ingress-nginx 作为 Ingress Controller,使用 Nginx 反向代理与负载,通过 Ingress Controller 不断的跟 Kub ...
- kubernetes Traefik ingress配置详解
理解Ingress 简单的说,ingress就是从kubernetes集群外访问集群的入口,将用户的URL请求转发到不同的service上.Ingress相当于nginx.apache等负载均衡方向代 ...
- traefik ingress Controller使用
Kubernetes Ingress Kubernetes Ingress是路由规则的集合,这些规则控制外部用户如何访问Kubernetes集群中运行的服务. 在Kubernetes中,有三种方式可以 ...
- Kubernetes Ingress 部署
Kubernetes Ingress 部署 Pod与Ingress的关系• 通过service相关联• 通过Ingress Controller实现Pod的负载均衡- 支持TCP/UDP 4层和HTT ...
- K8S从入门到放弃系列-(15)Kubernetes集群Ingress部署
Ingress是kubernetes集群对外提供服务的一种方式.ingress部署相对比较简单,官方把相关资源配置文件,都已经集合到一个yml文件中(mandatory.yaml),镜像地址也修改为q ...
- k8s traefik ingress tls
使用下面的 openssl 命令生成 CA 证书: $ openssl req -newkey rsa:2048 -nodes -keyout tls.key -x509 -days 365 -out ...
- Kubernetes 系列(三):Kubernetes使用Traefik Ingress暴露服务
一.Kubernetes 服务暴露介绍 从 kubernetes 1.2 版本开始,kubernetes提供了 Ingress 对象来实现对外暴露服务:到目前为止 kubernetes 总共有三种暴露 ...
随机推荐
- 学习Vue第三节,事件修饰符stop、prevent、capture、self、once
事件修饰符: .stop 阻止冒泡 .prevent 阻止默认事件 .capture 添加事件侦听器时使用事件捕获模式 .self 只当事件在该元素本身(比如不是子元素)触发时触发回调 .once 事 ...
- 基于BasicRF点对点无线开发基础知识
BasicRF点对点概述 BasicRF软件包有四大部分: <1> 硬件层:Hardware Layer. <2> 硬件抽象层:Haware Abstraction Layer ...
- Spring官网阅读(十七)Spring中的数据校验
文章目录 Java中的数据校验 Bean Validation(JSR 380) 使用示例 Spring对Bean Validation的支持 Spring中的Validator 接口定义 UML类图 ...
- 3、Hive-sql优化,数据倾斜处理
一.Hive-sql优化 #增加reducer任务数量(拉取数量分流) ; #在同一个sql中的不同的job是否可以同时运行,默认为false set hive.exec.parallel=true; ...
- Day_12【集合】扩展案例2_键盘录入一个字符串,对其进行去重,并将去重后的字符串组成新数组
需求分析:键盘读取一行输入,去掉其中重复字符, 打印出不同的那些字符 思路: 1.键盘录入字符串 2.遍历字符串,将每个字符存储到集合中 3.将集合中重复的字符去掉 4.创建新集合,遍历老集合,获取老 ...
- Android 电池管理系统架构总结 Android power and battery management architecture summaries
文章目录 1 整体架构 2 设计构架 2.1 driver 2.1.1 Charger.ko 2.1.2 Battery.ko 2.2 power supply 2.2.1 基础架构 2.2.2 代码 ...
- 接口testing简介
一.基础介绍 1.什么是接口 我们常说的接口一般指2种1)API:应用程序编程接口 2)GUI:图形用户界面(接口) 这里我们主要说API——接口测试 2.接口测试的目的 测试接口的正确性和稳定性 ...
- POJ1321棋盘问题(DFS)
Description 在一个给定形状的棋盘(形状可能是不规则的)上面摆放棋子,棋子没有区别.要求摆放时任意的两个棋子不能放在棋盘中的同一行或者同一列,请编程求解对于给定形状和大小的棋盘,摆放k个棋子 ...
- 使用QQ同步助手备份同步手机数据
QQ同步助手官网:https://pim.qq.com/ QQ同步助手,由腾讯精心打造的云端备份工具.能实现手机之间传输文件,并备份文件.照片.视频.联系人.短信.通讯记录.应用程序到云端的换手机必备 ...
- 11.1 Go Http
11.0 Go Http http客户端 package main import ( "fmt" "net/http" "net/http/httpu ...