实际中可能遇到的NAT问题(IPsec)
一、背景介绍:
一般我们在实际网络中不是IPSec VPN的时候,都是边界设备连接Internet,然后两个边界设备通过Internet去实现互通,建立VPN,但是,有的运营商在分配IP地址的时候,给我们使用的地址可能会在运营商的设备上再完成一次NAT,这样将会导致我们的IPSec VPN无法建立,我做了一个测试,简单搭建的拓扑图如下: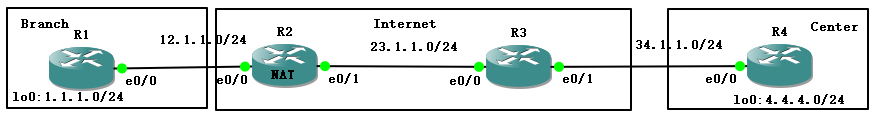
R1作为一个分支站点的边界路由去,R2和R3是作为运营商的设备,R4是总部的一个边界路由器,但是在R2上针对R1的12.1.1.0/24做了NAT。
二、基本配置:
R1:
R1#sho run int lo0
Building configuration...
Current configuration : 61 bytes
!
interface Loopback0
ip address 1.1.1.1 255.255.255.0
end
R1#sho run int e0/0
Building configuration...
Current configuration : 95 bytes
!
interface Ethernet0/0
ip address 12.1.1.1 255.255.255.0
half-duplex
crypto map cisco
end
R1#sho run | s ip route
ip route 0.0.0.0 0.0.0.0 12.1.1.2
R2:
R2#sho run int e0/0
Building configuration...
Current configuration : 115 bytes
!
interface Ethernet0/0
ip address 12.1.1.2 255.255.255.0
ip nat inside
ip virtual-reassembly
half-duplex
end
R2#sho run int e0/1
Building configuration...
Current configuration : 116 bytes
!
interface Ethernet0/1
ip address 23.1.1.2 255.255.255.0
ip nat outside
ip virtual-reassembly
half-duplex
end
R2#sho run | s ip route
ip route 0.0.0.0 0.0.0.0 23.1.1.3
R2#sho run | s ip nat
ip nat inside
ip nat outside
ip nat pool cisco 23.1.1.100 23.1.1.200 netmask 255.255.255.0
ip nat inside source list nat pool cisco
R3:
R3#sho run int e0/0
Building configuration...
Current configuration : 77 bytes
!
interface Ethernet0/0
ip address 23.1.1.3 255.255.255.0
half-duplex
end
R3#sho run int e0/1
Building configuration...
Current configuration : 77 bytes
!
interface Ethernet0/1
ip address 34.1.1.3 255.255.255.0
half-duplex
end
R3#sho run | s ip route
ip route 12.1.1.0 255.255.255.0 23.1.1.2
R4:
R4#sho run int e0/0
Building configuration...
Current configuration : 95 bytes
!
interface Ethernet0/0
ip address 34.1.1.4 255.255.255.0
half-duplex
crypto map cisco
end
R4#sho run int l0
Building configuration...
Current configuration : 61 bytes
!
interface Loopback0
ip address 4.4.4.4 255.255.255.0
end
R4#sho run | s ip route
ip route 0.0.0.0 0.0.0.0 34.1.1.3
如此实现R1和R4站点之间的可达性:
R1#ping 34.1.1.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 34.1.1.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 44/60/92 ms
三、在R1和R4配置IPSec VPN
R1:
R1#sho run | s crypto
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
lifetime 28800
crypto isakmp key cisco address 34.1.1.4
crypto ipsec transform-set Trans esp-3des esp-sha-hmac
mode transport
crypto map cisco 10 ipsec-isakmp
set peer 34.1.1.4
set transform-set Trans
set pfs group2
match address vpn
crypto map cisco
R1#sho run int e0/0
Building configuration...
Current configuration : 95 bytes
!
interface Ethernet0/0
ip address 12.1.1.1 255.255.255.0
half-duplex
crypto map cisco
End
R1#sho run | s ip access
ip access-list extended vpn
permit ip 1.1.1.0 0.0.0.255 4.4.4.0 0.0.0.255
R4:
R4#sho run | s crypto
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
lifetime 28800
crypto isakmp key cisco address 12.1.1.1
crypto ipsec transform-set Trans esp-3des esp-sha-hmac
mode transport
crypto map cisco 10 ipsec-isakmp
set peer 12.1.1.1
set transform-set Trans
set pfs group2
match address vpn
crypto map cisco
R4#sho run int e0/0
Building configuration...
Current configuration : 95 bytes
!
interface Ethernet0/0
ip address 34.1.1.4 255.255.255.0
half-duplex
crypto map cisco
end
R4#sh run | s ip access
ip access-list extended vpn
permit ip 4.4.4.0 0.0.0.255 1.1.1.0 0.0.0.255
四、测试尝试建立的IPSec VPN,从R4的内部流量到R1的内部流量(模拟为4.4.4.0/24到1.1.1.0/24)为触发流量。
过程中开启debug信息:
R1/R4#debug crypto isakmp
Crypto ISAKMP debugging is on
R1#debug crypto ipsec
Crypto IPSEC debugging is on
DEBUG过程:
R4#ping 1.1.1.1 so 4.4.4.4 re 100
R1上的debug:
R1#
//收到了R4发来的SA信息:
*Mar 1 00:43:58.955: ISAKMP (0:0): received packet from 34.1.1.4 dport 500 sport 500 Global (N) NEW SA
*Mar 1 00:43:58.955: ISAKMP: Created a peer struct for 34.1.1.4, peer port 500
*Mar 1 00:43:58.955: ISAKMP: New peer created peer = 0x646C2A90 peer_handle = 0x8000000C
*Mar 1 00:43:58.959: ISAKMP: Locking peer struct 0x646C2A90, IKE refcount 1 for crypto_isakmp_process_block
*Mar 1 00:43:58.959: ISAKMP: local port 500, remote port 500
*Mar 1 00:43:58.959: insert sa successfully sa = 643C4DB8
*Mar 1 00:43:58.963: ISAKMP:(0:0:N/A:0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 1 00:43:58.963: ISAKMP:(0:0:N/A:0):Old State = IKE_READY New State = IKE_R_MM1
*Mar 1 00:43:58.967: ISAKMP:(0:0:N/A:0): processing SA payload. message ID = 0
*Mar 1 00:43:58.967: ISAKMP:(0:0:N/A:0): processing vendor id payload
*Mar 1 00:43:58.971: ISAKMP:(0:0:N/A:0): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 1 00:43:58.971: ISAKMP (0:0): vendor ID is NAT-T v7
*Mar 1 00:43:58.971: ISAKMP:(0:0:N/A:0): processing vendor id payload
*Mar 1 00:43:58.971: ISAKMP:(0:0:N/A:0): vendor ID seems Unity/DPD but major 157 mismatch
*Mar 1 00:43:58.975: ISAKMP:(0:0:N/A:0): vendor ID is NAT-T v3
*Mar 1 00:43:58.975: ISAKMP:(0:0:N/A:0): processing vendor id payload
*Mar 1 00:43:58.975: ISAKMP:(0:0:N/A:0): vendor ID seems Unity/DPD but major 123 mismatch
*Mar 1 00:43:58.975: ISAKMP:(0:0:N/A:0): vendor ID is NAT-T v2
*Mar 1 00:43:58.979: ISAKMP:(0:0:N/A:0):found peer pre-shared key matching 34.1.1.4
*Mar 1 00:43:58.979: ISAKMP:(0:0:N/A:0): local preshared key found
*Mar 1 00:43:58.979: ISAKMP : Scanning profiles for xauth …
//开始检查IKE第一阶段的策略
*Mar 1 00:43:58.979: ISAKMP:(0:0:N/A:0):Checking ISAKMP transform 1 against priority 10 policy
*Mar 1 00:43:58.979: ISAKMP: encryption 3DES-CBC
*Mar 1 00:43:58.983: ISAKMP: hash MD5
*Mar 1 00:43:58.983: ISAKMP: default group 2
*Mar 1 00:43:58.983: ISAKMP: auth pre-share
*Mar 1 00:43:58.983: ISAKMP: life type in seconds
*Mar 1 00:43:58.983: ISAKMP: life duration (basic) of 28800
*Mar 1 00:43:58.983: ISAKMP:(0:0:N/A:0):atts are acceptable. Next payload is 0
*Mar 1 00:43:59.023: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 00:43:59.023: ISAKMP:(0:1:SW:1): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 1 00:43:59.023: ISAKMP (0:134217729): vendor ID is NAT-T v7
*Mar 1 00:43:59.023: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 00:43:59.023: ISAKMP:(0:1:SW:1): vendor ID seems Unity/DPD but major 157 mismatch
*Mar 1 00:43:59.023: ISAKMP:(0:1:SW:1): vendor ID is NAT-T v3
*Mar 1 00:43:59.027: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 00:43:59.027: ISAKMP:(0:1:SW:1): vendor ID seems Unity/DPD but major 123 mismatch
*Mar 1 00:43:59.027: ISAKMP:(0:1:SW:1): vendor ID is NAT-T v2
*Mar 1 00:43:59.027: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 1 00:43:59.027: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM1 New State = IKE_R_MM1
//本端和对端继续交互SA协商报文,但是发出没有收到回复
*Mar 1 00:43:59.027: ISAKMP:(0:1:SW:1): constructed NAT-T vendor-07 ID
*Mar 1 00:43:59.031: ISAKMP:(0:1:SW:1): sending packet to 34.1.1.4 my_port 500 peer_port 500 (R) MM_SA_SETUP
*Mar 1 00:43:59.031: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 1 00:43:59.031: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM1 New State = IKE_R_MM2
//本端没有收到回复,继续重传5次,删除准备协商的SA
*Mar 1 00:44:08.971: ISAKMP (0:134217729): received packet from 34.1.1.4 dport 500 sport 500 Global (R) MM_SA_SETUP
*Mar 1 00:44:08.975: ISAKMP:(0:1:SW:1): phase 1 packet is a duplicate of a previous packet.
*Mar 1 00:44:08.975: ISAKMP:(0:1:SW:1): retransmitting due to retransmit phase 1
*Mar 1 00:44:09.475: ISAKMP:(0:1:SW:1): retransmitting phase 1 MM_SA_SETUP...
*Mar 1 00:44:09.475: ISAKMP (0:134217729): incrementing error counter on sa, attempt 1 of 5: retransmit phase 1
*Mar 1 00:44:09.475: ISAKMP:(0:1:SW:1): retransmitting phase 1 MM_SA_SETUP
*Mar 1 00:44:09.475: ISAKMP:(0:1:SW:1): sending packet to 34.1.1.4 my_port 500 peer_port 500 (R) MM_SA_SETUP
R1#
*Mar 1 00:44:18.979: ISAKMP (0:134217729): received packet from 34.1.1.4 dport 500 sport 500 Global (R) MM_SA_SETUP
*Mar 1 00:44:18.983: ISAKMP:(0:1:SW:1): phase 1 packet is a duplicate of a previous packet.
*Mar 1 00:44:18.983: ISAKMP:(0:1:SW:1): retransmitting due to retransmit phase 1
*Mar 1 00:44:19.483: ISAKMP:(0:1:SW:1): retransmitting phase 1 MM_SA_SETUP...
*Mar 1 00:44:19.483: ISAKMP (0:134217729): incrementing error counter on sa, attempt 2 of 5: retransmit phase 1
*Mar 1 00:44:19.483: ISAKMP:(0:1:SW:1): retransmitting phase 1 MM_SA_SETUP
*Mar 1 00:44:19.483: ISAKMP:(0:1:SW:1): sending packet to 34.1.1.4 my_port 500 peer_port 500 (R) MM_SA_SETUP
R1#
*Mar 1 00:44:28.967: ISAKMP (0:134217729): received packet from 34.1.1.4 dport 500 sport 500 Global (R) MM_SA_SETUP
*Mar 1 00:44:28.967: ISAKMP:(0:1:SW:1): phase 1 packet is a duplicate of a previous packet.
*Mar 1 00:44:28.967: ISAKMP:(0:1:SW:1): retransmitting due to retransmit phase 1
*Mar 1 00:44:29.471: ISAKMP:(0:1:SW:1): retransmitting phase 1 MM_SA_SETUP...
*Mar 1 00:44:29.471: ISAKMP (0:134217729): incrementing error counter on sa, attempt 3 of 5: retransmit phase 1
*Mar 1 00:44:29.471: ISAKMP:(0:1:SW:1): retransmitting phase 1 MM_SA_SETUP
*Mar 1 00:44:29.471: ISAKMP:(0:1:SW:1): sending packet to 34.1.1.4 my_port 500 peer_port 500 (R) MM_SA_SETUP
R1#
*Mar 1 00:44:39.019: ISAKMP (0:134217729): received packet from 34.1.1.4 dport 500 sport 500 Global (R) MM_SA_SETUP
*Mar 1 00:44:39.019: ISAKMP:(0:1:SW:1): phase 1 packet is a duplicate of a previous packet.
*Mar 1 00:44:39.019: ISAKMP:(0:1:SW:1): retransmitting due to retransmit phase 1
*Mar 1 00:44:39.523: ISAKMP:(0:1:SW:1): retransmitting phase 1 MM_SA_SETUP...
*Mar 1 00:44:39.523: ISAKMP (0:134217729): incrementing error counter on sa, attempt 4 of 5: retransmit phase 1
*Mar 1 00:44:39.523: ISAKMP:(0:1:SW:1): retransmitting phase 1 MM_SA_SETUP
*Mar 1 00:44:39.523: ISAKMP:(0:1:SW:1): sending packet to 34.1.1.4 my_port 500 peer_port 500 (R) MM_SA_SETUP
R1#
*Mar 1 00:44:48.987: ISAKMP (0:134217729): received packet from 34.1.1.4 dport 500 sport 500 Global (R) MM_SA_SETUP
*Mar 1 00:44:48.987: ISAKMP:(0:1:SW:1): phase 1 packet is a duplicate of a previous packet.
*Mar 1 00:44:48.987: ISAKMP:(0:1:SW:1): retransmitting due to retransmit phase 1
*Mar 1 00:44:49.491: ISAKMP:(0:1:SW:1): retransmitting phase 1 MM_SA_SETUP...
*Mar 1 00:44:49.491: ISAKMP (0:134217729): incrementing error counter on sa, attempt 5 of 5: retransmit phase 1
*Mar 1 00:44:49.491: ISAKMP:(0:1:SW:1): retransmitting phase 1 MM_SA_SETUP
*Mar 1 00:44:49.491: ISAKMP:(0:1:SW:1): sending packet to 34.1.1.4 my_port 500 peer_port 500 (R) MM_SA_SETUP
R1#
*Mar 1 00:44:59.495: ISAKMP:(0:1:SW:1): retransmitting phase 1 MM_SA_SETUP...
*Mar 1 00:44:59.495: ISAKMP:(0:1:SW:1):peer does not do paranoid keepalives.
*Mar 1 00:44:59.495: ISAKMP:(0:1:SW:1):deleting SA reason "Death by retransmission P1" state (R) MM_SA_SETUP (peer 34.1.1.4)
*Mar 1 00:44:59.499: ISAKMP:(0:1:SW:1):deleting SA reason "Death by retransmission P1" state (R) MM_SA_SETUP (peer 34.1.1.4)
*Mar 1 00:44:59.503: ISAKMP: Unlocking IKE struct 0x646C2A90 for isadb_mark_sa_deleted(), count 0
*Mar 1 00:44:59.503: ISAKMP: Deleting peer node by peer_reap for 34.1.1.4: 646C2A90
*Mar 1 00:44:59.507: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
R1#
*Mar 1 00:44:59.507: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM2 New State = IKE_DEST_SA
//开始重复上述过程
*Mar 1 00:44:59.507: IPSEC(key_engine): got a queue event with 1 kei messages
*Mar 1 00:45:00.971: ISAKMP (0:0): received packet from 34.1.1.4 dport 500 sport 500 Global (N) NEW SA
R4上的debug:
//发出SA协商报文,开始尝试建立第一阶段
*Mar 1 00:43:54.987: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 34.1.1.4, remote= 12.1.1.1,
local_proxy= 4.4.4.0/255.255.255.0/0/0 (type=4),
remote_proxy= 1.1.1.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x924045A9(2453685673), conn_id= 0, keysize= 0, flags= 0x400F
*Mar 1 00:43:54.991: ISAKMP: received ke message (1/1)
*Mar 1 00:43:54.995: ISAKMP:(0:0:N/A:0): SA request profile is (NULL)
*Mar 1 00:43:54.995: ISAKMP: Created a peer struct for 12.1.1.1, peer port 500
*Mar 1 00:43:54.995: ISAKMP: New peer created peer = 0x649A497C peer_handle = 0x8000000C
*Mar 1 00:43:54.995: ISAKMP: Locking peer struct 0x649A497C, IKE refcount 1 for isakmp_initiator
*Mar 1 00:43:54.999: ISAKMP: local port 500, remote port 500
*Mar 1 00:43:54.999: ISAKMP: set new node 0 to QM_IDLE
*Mar 1 00:43:54.999: insert sa successfully sa = 64278AD0
*Mar 1 00:43:55.003: ISAKMP:(0:0:N/A:0):Can not start Aggressive mode, trying Main mode.
*Mar 1 00:43:55.003: ISAKMP:(0:0:N/A:0):found peer pre-shared key matching 12.1.1.1
*Mar 1 00:43:55.003: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-07 ID
*Mar 1 00:43:55.007: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-03 ID
*Mar 1 00:43:55.007: ISAKMP:(0:0:N/A:0): constructed NAT-T vendor-02 ID
*Mar 1 00:43:55.007: ISAKMP:(0:0:N/A:0):Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
*Mar 1 00:43:55.007: ISAKMP:(0:0:N/A:0):Old State = IKE_READY New State = IKE_I_MM1
//向对端12.1.1.1发起协商,但是回复的是NAT之后的地址23.1.1.100。本端认为协商出错
*Mar 1 00:43:55.011: ISAKMP:(0:0:N/A:0): beginning Main Mode exchange
*Mar 1 00:43:55.011: ISAKMP:(0:0:N/A:0): sending packet to 12.1.1.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Mar 1 00:43:55.131: ISAKMP (0:0): received p.acket from 23.1.1.100 dport 500 sport 500 Global (N) NEW SA
*Mar 1 00:43:55.135: %CRYPTO-4-IKMP_NO_SA: IKE message from 23.1.1.100 has no SA and is not an initialization offer....
*Mar 1 00:44:05.011: ISAKMP:(0:0:N/A:0): retransmitting phase 1 MM_NO_STATE...
*Mar 1 00:44:05.011: ISAKMP (0:0): incrementing error counter on sa, attempt 1 of 5: retransmit phase 1
*Mar 1 00:44:05.011: ISAKMP:(0:0:N/A:0): retransmitting phase 1 MM_NO_STATE
*Mar 1 00:44:05.015: ISAKMP:(0:0:N/A:0): sending packet to 12.1.1.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Mar 1 00:44:05.595: ISAKMP (0:0): received packet from 23.1.1.100 dport 500 sport 500 Global (N) NEW SA.....
*Mar 1 00:44:15.015: ISAKMP:(0:0:N/A:0): retransmitting phase 1 MM_NO_STATE...
*Mar 1 00:44:15.015: ISAKMP (0:0): incrementing error counter on sa, attempt 2 of 5: retransmit phase 1
*Mar 1 00:44:15.015: ISAKMP:(0:0:N/A:0): retransmitting phase 1 MM_NO_STATE
*Mar 1 00:44:15.019: ISAKMP:(0:0:N/A:0): sending packet to 12.1.1.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Mar 1 00:44:15.591: ISAKMP (0:0): received packet from 23.1.1.100 dport 500 sport 500 Global (N) NEW SA.....
*Mar 1 00:44:24.987: IPSEC(key_engine): request timer fired: count = 1,
(identity) local= 34.1.1.4, remote= 12.1.1.1,
local_proxy= 4.4.4.0/255.255.255.0/0/0 (type=4),
remote_proxy= 1.1.1.0/255.255.255.0/0/0 (type=4)
*Mar 1 00:44:24.991: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 34.1.1.4, remote= 12.1.1.1,
local_proxy= 4.4.4.0/255.255.255.0/0/0 (type=4),
remote_proxy= 1.1.1.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-3des esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x393ADF7B(960159611), conn_id= 0, keysize= 0, flags= 0x400F
*Mar 1 00:44:24.995: ISAKMP: received ke message (1/1)
*Mar 1 00:44:24.995: ISAKMP: set new node 0 to QM_IDLE
*Mar 1 00:44:24.999: ISAKMP:(0:0:N/A:0):SA is still budding. Attached new ipsec request to it. (local 34.1.1.4, remote 12.1.1.1)
*Mar 1 00:44:25.019: ISAKMP:(0:0:N/A:0): retransmitting phase 1 MM_NO_STATE...
*Mar 1 00:44:25.019: ISAKMP (0:0): incrementing error counter on sa, attempt 3 of 5: retransmit phase 1
*Mar 1 00:44:25.019: ISAKMP:(0:0:N/A:0): retransmitting phase 1 MM_NO_STATE
*Mar 1 00:44:25.019: ISAKMP:(0:0:N/A:0): sending packet to 12.1.1.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Mar 1 00:44:25.575: ISAKMP (0:0): received packet from 23.1.1.100 dport 500 sport 500 Global (N) NEW SA.....
*Mar 1 00:44:35.023: ISAKMP:(0:0:N/A:0): retransmitting phase 1 MM_NO_STATE...
*Mar 1 00:44:35.023: ISAKMP (0:0): incrementing error counter on sa, attempt 4 of 5: retransmit phase 1
*Mar 1 00:44:35.023: ISAKMP:(0:0:N/A:0): retransmitting phase 1 MM_NO_STATE
*Mar 1 00:44:35.027: ISAKMP:(0:0:N/A:0): sending packet to 12.1.1.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Mar 1 00:44:35.659: ISAKMP (0:0): received packet from 23.1.1.100 dport 500 sport 500 Global (N) NEW SA.....
*Mar 1 00:44:45.027: ISAKMP:(0:0:N/A:0): retransmitting phase 1 MM_NO_STATE...
*Mar 1 00:44:45.027: ISAKMP (0:0): incrementing error counter on sa, attempt 5 of 5: retransmit phase 1
*Mar 1 00:44:45.027: ISAKMP:(0:0:N/A:0): retransmitting phase 1 MM_NO_STATE
*Mar 1 00:44:45.031: ISAKMP:(0:0:N/A:0): sending packet to 12.1.1.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Mar 1 00:44:45.599: ISAKMP (0:0): received packet from 23.1.1.100 dport 500 sport 500 Global (N) NEW SA.....
*Mar 1 00:44:54.991: IPSEC(key_engine): request timer fired: count = 2,
(identity) local= 34.1.1.4, remote= 12.1.1.1,
local_proxy= 4.4.4.0/255.255.255.0/0/0 (type=4),
remote_proxy= 1.1.1.0/255.255.255.0/0/0 (type=4)
*Mar 1 00:44:54.995: ISAKMP: received ke message (3/1)
*Mar 1 00:44:54.995: ISAKMP:(0:0:N/A:0):peer does not do paranoid keepalives.
//重传5次后,删除准备协商的SA
*Mar 1 00:44:54.999: ISAKMP:(0:0:N/A:0):deleting SA reason "P1 delete notify (in)" state (I) MM_NO_STATE (peer 12.1.1.1)
*Mar 1 00:44:55.003: ISAKMP:(0:0:N/A:0):deleting SA reason "P1 delete notify (in)" state (I) MM_NO_STATE (peer 12.1.1.1)
*Mar 1 00:44:55.003: ISAKMP: Unlocking IKE struct 0x649A497C for isadb_mark_sa_deleted(), count 0
*Mar 1 00:44:55.003: ISAKMP: Deleting peer node by peer_reap for 12.1.1.1: 649A497C
*Mar 1 00:44:55.007: ISAKMP:(0:0:N/A:0):deleting node 210980541 error FALSE reason "IKE deleted"
*Mar 1 00:44:55.007: ISAKMP:(0:0:N/A:0):deleting node -132879272 error FALSE reason "IKE deleted"
*Mar 1 00:44:55.007: ISAKMP:(0:0:N/A:0):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
*Mar 1 00:44:55.011: ISAKMP:(0:0:N/A:0):Old State = IKE_I_MM1 New State = IKE_DEST_SA
五、解决方法:
R4(config)#no crypto isakmp key 0 cisco address 12.1.1.1
R4(config)#crypto isakmp key 0 cisco address 23.1.1.100 255.255.255.0
R4(config)#crypto map cisco 10 ipsec-isakmp
R4(config-crypto-map)#no set peer 12.1.1.1
R4(config-crypto-map)#set peer 23.1.1.100
实际中可能遇到的NAT问题(IPsec)的更多相关文章
- 加密设备NAT对IPSec的影响
加密设备NAT对IPSec VPN的影响:我们先配置好经典的IPSec VPN,然后在R3上做PAT看会对IPSec VPN产生什么影响(不会对有隧道的IPSec VPN技术产生影响). 现在默认配置 ...
- UITableView使用过程中可能遇到的问题
前言:记录一些UITableView使用过程中可能遇到的问题 环境:Xcode9 解决UITableViewStyleGrouped类型的TableView的cell距离顶部有距离的问题: table ...
- virtualbox中centos系统配置nat+host only上网
以前一直使用的是virtualbox的桥接模式,桥接模式的特点: 虚拟机和宿主机处于同等地位,就像是一台真实主机一样存在于局域网中,可以分配到一个网络中独立的IP. 虚拟机和宿主机之间能够互访. 如果 ...
- virtualbox中centos系统配置nat+host only上网(zhuan)
http://www.cnblogs.com/leezhxing/p/4482659.html **************************************************** ...
- 单点登陆CAS安装过程中可能遇到的问题
可能遇到的问题: 错误: java.security.cert.CertificateException: No name matching localhost found 原因: keystore里 ...
- VM12中CentOS7以NAT方式连接网络的方法
解决问题:centos网络连不上,连不上主机,ifconfig等命令不能用(配完有网了,安装上就好了)等问题 前提:安装vm12,centos7(最小安装) 注意:以下以192开头的,你都要替换成自 ...
- 使用路由和远程访问服务为Hyper-V中虚拟机实现NAT上网
众所周知,在微软的Hyper-V环境中的网络环境中没有VMware Workstation中的NAT功能,所以Hyper-V环境中虚拟机上网一般情况下需要通过设置为外部网络方可访问网络,当然也可设置为 ...
- VMWare中桥接、NAT、Host-only
1.概述 2.bridged(桥接模式) 3.NAT(网络地址转换模式) 4.host-only(主机模式) 5.replicate physical network connection state ...
- vmware12中centos7以NAT连接网络
1.第一步当然是安装VM和安装CentOS,我用的是VM12和64位的CentOS7,怎么安装在我的其他文中有写到: http://www.cnblogs.com/wuyx/p/7246675.htm ...
随机推荐
- command failed: npm install --loglevel error --registry=https://registry.npm 用vue-cli 4.0 新建项目总是报错
昨天新买的本本,今天布环境,一安装vue-cli发现都4.0+的版本了,没管太多,就开始新建个项目感受哈,一切运行顺利,输入 "vue create app" 的时候,一切貌似进展 ...
- 浅谈Power Signoff
Power Analysis是芯片设计实现中极重要的一环,因为它直接关系到芯片的性能和可靠性.Power Analysis 需要Timing Analysis 产生包含频率.transition 等时 ...
- jQuery 源码解析(三十) 动画模块 $.animate()详解
jQuery的动画模块提供了包括隐藏显示动画.渐显渐隐动画.滑入划出动画,同时还支持构造复杂自定义动画,动画模块用到了之前讲解过的很多其它很多模块,例如队列.事件等等, $.animate()的用法如 ...
- Codeforces Round #599 (Div. 2) A. Maximum Square
Ujan decided to make a new wooden roof for the house. He has nn rectangular planks numbered from 11 ...
- DVWA全级别之Brute Force(暴力破解)
Brute Force Brute Force,即暴力(破解),是指黑客利用密码字典,使用穷举法猜解出用户口令. 首先我们登录DVWA(admin,password),之后我们看网络是否为无代理,: ...
- 多对多三种创建方式、forms组件、cookies与session
多对多三种创建方式.forms组件.cookies与session 一.多对多三种创建方式 1.全自动 # 优势:不需要你手动创建第三张表 # 不足:由于第三张表不是你手动创建的,也就意味着第三张表字 ...
- 推荐几个c/c++语言编写的游戏源码下载网站
在游戏开发的学习或工作中,利用完好的游戏源码可以事半功倍,不仅可以逆向学习开拓思维,也可以大大减少设计周期.自己浏览了很游戏源码下载的网站,发现大多数质量都良莠不齐,且大部分需要消费才能下载,下面整理 ...
- Spring5 of WebClient(转载)
前言 Spring5带来了新的响应式web开发框架WebFlux,同时,也引入了新的HttpClient框架WebClient.WebClient是Spring5中引入的执行 HTTP 请求的非阻塞. ...
- 红帽RHCE培训-课程3笔记内容2
9 NFS 9.1 NFS基础 目标 .使用NFS将文件系统连接到客户端,并使用IP 地址控制访问 .使用NFS将文件系统连接到客户端,并使用kerberos 来控制访问 .配置用户名和密码控制访问的 ...
- 洛谷P1734 最大约数和(01背包)
题目描述 选取和不超过S的若干个不同的正整数,使得所有数的约数(不含它本身)之和最大. 输入格式 输入一个正整数S. 输出格式 输出最大的约数之和. 输入输出样例 输入 #1 11 输出 #1 9 说 ...
