Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(1)
Address Objects and Groups
- Creating address objects.
- Organizing address objects with address groups
- Limiting the human error and complexity thanks to address groups.

Add a new address:
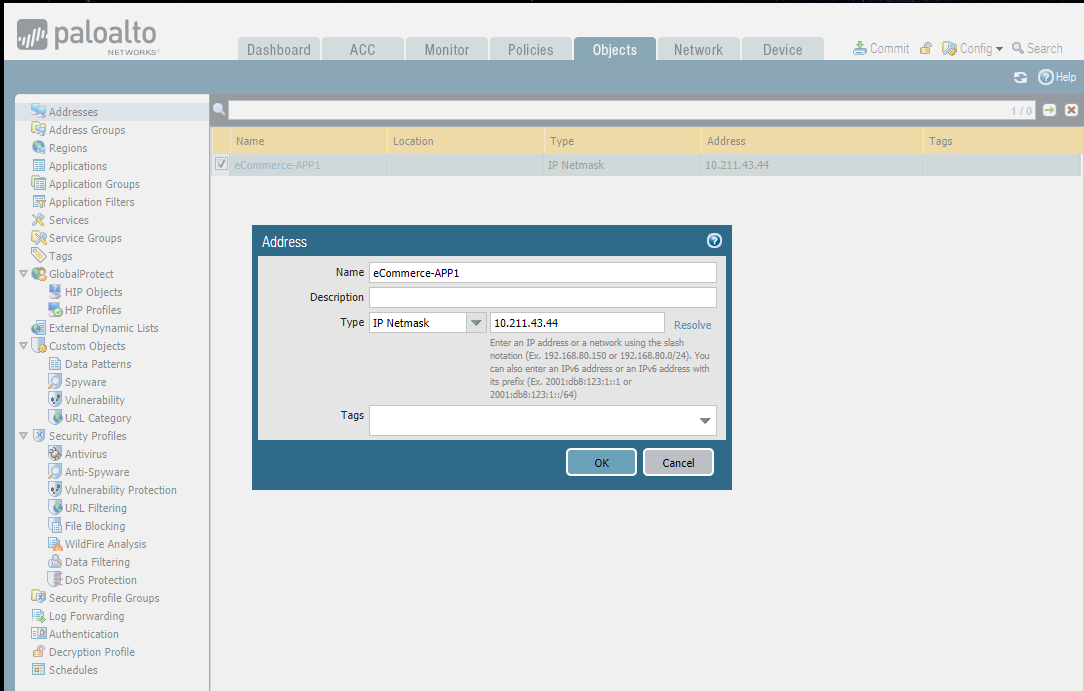
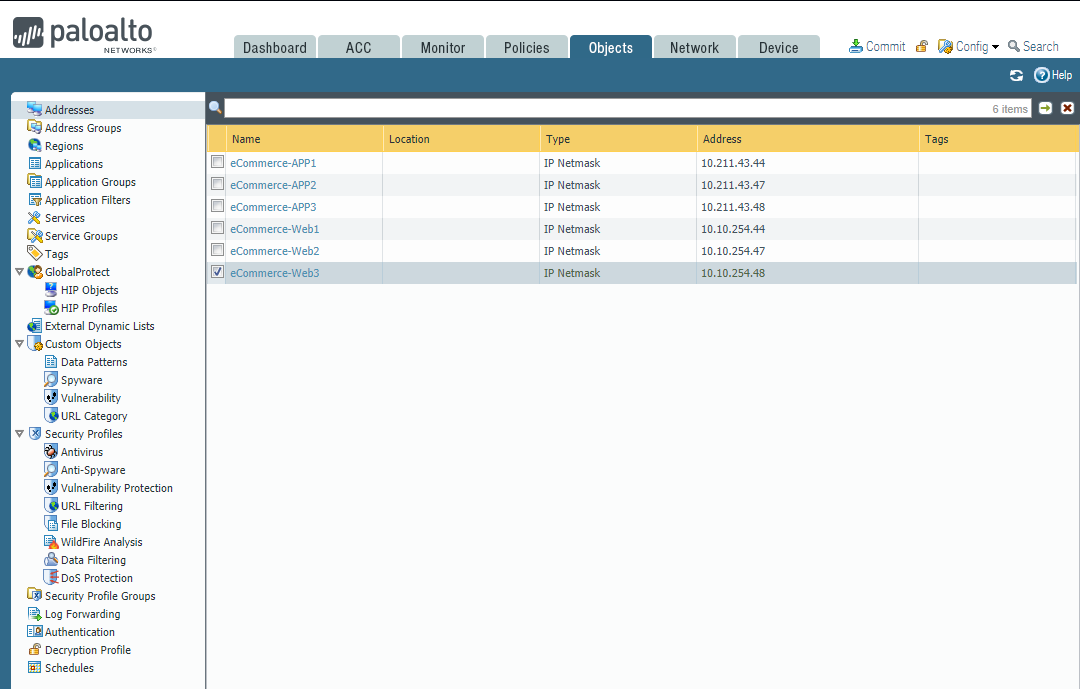
Add new Address Groups:


Service Objects and Groups
- Creating service objects.
- Organizing service objects with service groups
- Using service groups to avoid long and complex security policy tables.
Add services:
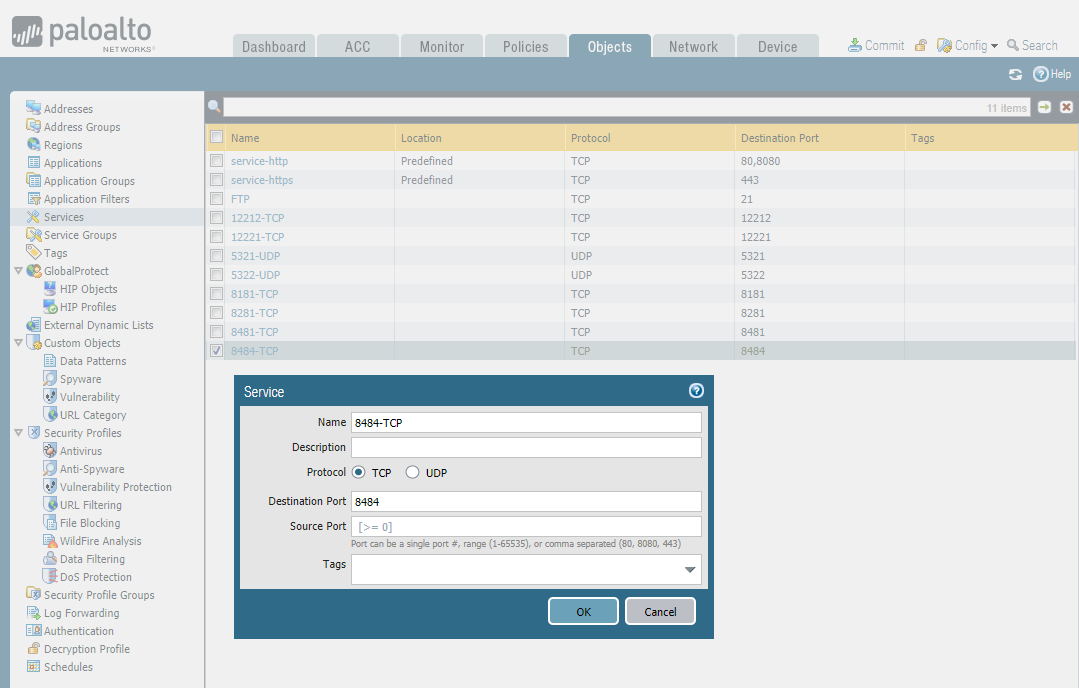
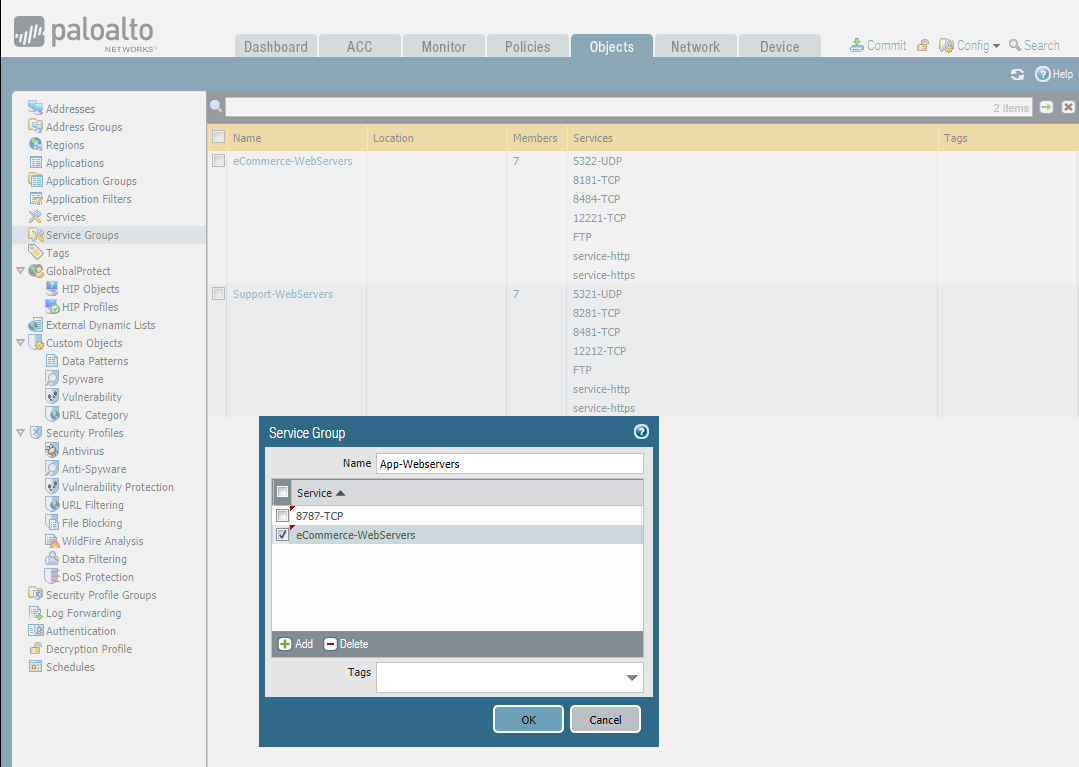
Add Service Groups:
Application Objects and Groups
- Creating application objects.
- Classify application objects in groups.

Add applications:
Add a new Clinical system:



Add a new application group:
Search the PAN Application Research Center before adding an application group. Identifying any required dependencies when applying application-specific rules and taking advantage of Palo Alto's application portal. https://applipedia.paloaltonetworks.com/

Then add the Youtube-Group.

Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(1)的更多相关文章
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(3)
LDAP Authentication and Remote Users and Groups Create Remote User Objects and LDAP Integration: sam ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(2)
Users Objects and Groups Creating local user objects. Creating local user groups. https://docs.paloa ...
- Cyber Security - Palo Alto Firewall Interface Types
Multiple options to integrate the Palo Alto Firewall into your: Network Layer 2 interfaces and VLAN ...
- Cyber Security - Palo Alto Firewall V-Wires
Leveraging V-Wires Bridge two physical connections and apply security Policies without influencing a ...
- Cyber Security - Palo Alto Firewall Security Zones
Firewall Security Zones Zones: The foundational aspect of every Firewall. Police network traffic Enf ...
- Cyber Security - Palo Alto Basic Introduction
Preparation of the Lab Environment: Download and Install Pan-OS from the following website https://d ...
- Cyber Security - Palo Alto Security Policies(1)
Security policies: Enforcing network traffic by configuring rules of what is allowed or denied to co ...
- Cyber Security - Palo Alto Security Policies(2)
Task 3 The SOC(Security Operation Center) monitoring team dashboard reported more 1,000 requests to ...
- Palo Alto GlobalProtect上的PreAuth RCE
0x00 前言 SSL VPN虽然可以保护企业资产免受互联网被攻击的风险影响,但如果SSL VPN本身容易受到攻击呢?它们暴露在互联网上,可以可靠并安全地连接到内网中.一旦SSL VPN服务器遭到入侵 ...
随机推荐
- vue 深度拷贝 除去空的参数
// 去除数组里面为空的属性及子数组 export function deepCopy (source) { var result = [] //var result = {} for (var ke ...
- Jenkins入门教程之linux下安装配置jenkins(一)
https://blog.csdn.net/zjh_746140129/article/details/80835866
- Apollo配置中心的实战
31.携程 Apollo 配置中心介绍~1.mp4 32.Apollo核心概念~1.mp4 32.Apollo核心概念~1.mp4 每个应用需要有一个唯一的AppID 要在指定的机器上的server. ...
- laravel生成key失败
laravel生成key失败 生成KEY失败.原因是没有复制.env文件 In KeyGenerateCommand.php line 96: file_get_contents(D:\project ...
- Spark HA搭建
正文 下载Spark版本,这版本又要求必须和jdk与hadoop版本对应. http://spark.apache.org/downloads.html tar -zxvf 解压到指定目录,进入con ...
- JFinal 开箱评测,这次我是认真的
引言 昨天在看服务器容器的时候意外的遇到了 JFinal ,之前我对 JFinal 的印象仅停留在这是一款国人开发的集成 Spring 全家桶的一个框架. 后来我查了一下,好像事情并没有这么简单. J ...
- 深度学习“四大名著”发布!Python、TensorFlow、机器学习、深度学习四件套!
Python 程序员深度学习的"四大名著": 这四本书着实很不错!我们都知道现在机器学习.深度学习的资料太多了,面对海量资源,往往陷入到"无从下手"的困惑出境. ...
- 在Ubuntu上实现人脸识别登录
安装Howdy: howdy项目地址 sudo add-apt-repository ppa:boltgolt/howdy sudo apt update sudo apt install howdy ...
- Docker编写镜像 发布个人网站
推荐国内镜像中心:网易云镜像----> https://c.163.com/hub#/home 或者歪果镜像---> https://hub.docker.com/ 博客地址:http: ...
- Flask项目实战:创建电影网站(2)
flask网站制作后台时候常见流程总结 安利一个神神器: 百度脑图PC版 创建数据库 下面是创建User数据库,需要导入db库 #coding:utf8 from flask import Flask ...
