CGANs
Introducation
1. intruduce the conditional version of GANs, which can be constructed by simply feeding the data , y.
2. the CGANs can be used to learn a multi-modal model.
3.GANs in order to sidestep the difficulty of approximating many intractable probabilistic computations.(为了避免许多难以处理的概率计算的近似困难)
4. Adversarial nets have the advantages that Markov chains are never needed, only backpropagation is used to obtain gradients, no inference is required during learning,
and a wide variety of factors and interactions can easily be incorporated into the model.(多种因素和相互作用可以很容易地纳入模型)
5.马尔可夫链(Markov Chain),描述了一种状态序列,其每个状态值取决于前面有限个状态。一般来说,其核心是满足条件期望和平稳的分布,保证在计算过程中能够得到想要的概率分布。而我们考虑的生成模型恰好可能有以下两种情况:
输入一个随机分布的数据(例如一张黑白像素夹杂的噪音图),输出期望的数据(一张头像)
输入含有噪音的数据(在原有的图像上添加噪点或缺损),输出除去噪点或补完后的数据(完整的原始图像),这种情况下的模型也可以叫做任意去噪的自编码器。
无论是哪种情况,我们都希望从模型输出的数据y的概率分布尽可能逼近训练数据集的概率分布。但是让计算机生成一段音乐,或者一张有意义的图片,这个分布是非常复杂,很难求解的;即使通过马尔可夫链取样,得到了一个生成模型,我们最终也很难对这个模型的效果进行评估,因为生成的音乐到底好不好听,不同的人会得到不同的答案。
6. GANs can produce state of the art log-likehood estimate and realistic samples.
7. but
Related Work
1. the challeage of scaling models to accommodate an extremely large number of predicted output categories (调整模型以适应非常多的预测输出类别的挑战), to adress this problem by leveraging additional information such as using natural language corpora.and even a simple linear mapping from image feature-space to word-representation-space can improve.
2. the challage of focusing on learning one-to-one mapping from input to output,but many interesting problems belong to a probabilistic one-to-many mapping.to adress this challege by using a conditional probabilistic generative model , for example, the input is taken to be the conditioning variable and the one-to-many mapping is instantiated(实例化)as a conditional predictive distribution.
Method
1. to specify that the G can capture the data distribution and the D can estimate the probability that a sample came from the training data rather than G.
2. the input is z, G and D are both trained simultaneously. we adjust the parameters for G to minimize $log(1-D(G(z)))$ and adjust the parameters for D to minimize $log(D(X))$
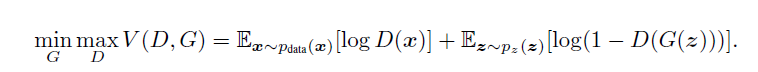
Import Details -----Conditional Adversarial Nets
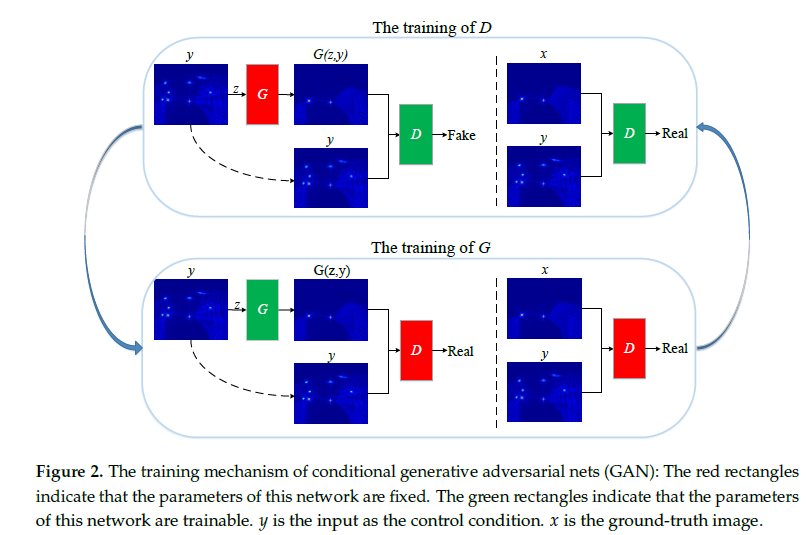
The training mechanism of CGANs.
1. GANs can be extended to a conditional model if both the G and D are conditioned on some extra information y.
2. y can be any kind of auxiliary information such as class label or data from other modalities.
3. feeding y into both discriminator and generator as additional input layer.
4. prior input noise and y are combined into joint hidden representation 对抗性训练框架允许在如何组成这种隐藏的表示方面具有相当大的灵活性。
5. In the discriminator and are presented as inputs and to a discriminative function (embodied x y again by a MLP in this case).
The formula of a objective function :
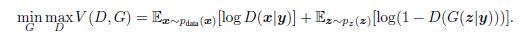
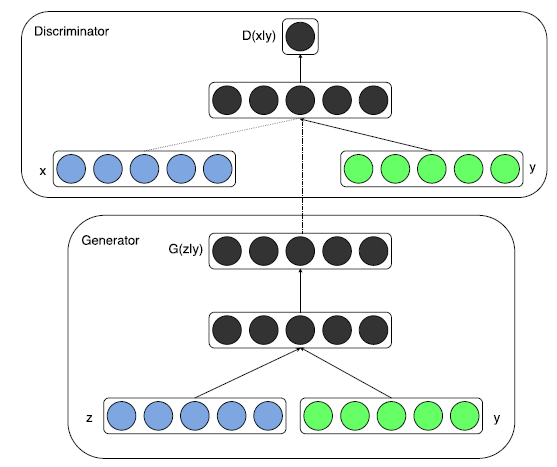
The framework of CGANs:
Experiment
1. this paper trained a CGANs on MNIST images conditioned on their class labels, encoded as one-hot vectors.
For G:
both z and y are mapped to hidden layers with RELU, with layer sizes 200 and 1000 respectively, then combined hidden ReLu layer of dimensionality 1200.
For D:
The discriminator maps to a maxout [6] layer with 240 units and 5 pieces, and to a maxout layer x y with 50 units and 5 pieces. Both of the hidden layers mapped to a joint maxout layer with 240 units and 4 pieces before being fed to the sigmoid layer
For Training:
and best estimate of log-likehood on the validation set was used as stopping point.(并以验证集的对数似然最优估计值作为停止点)。
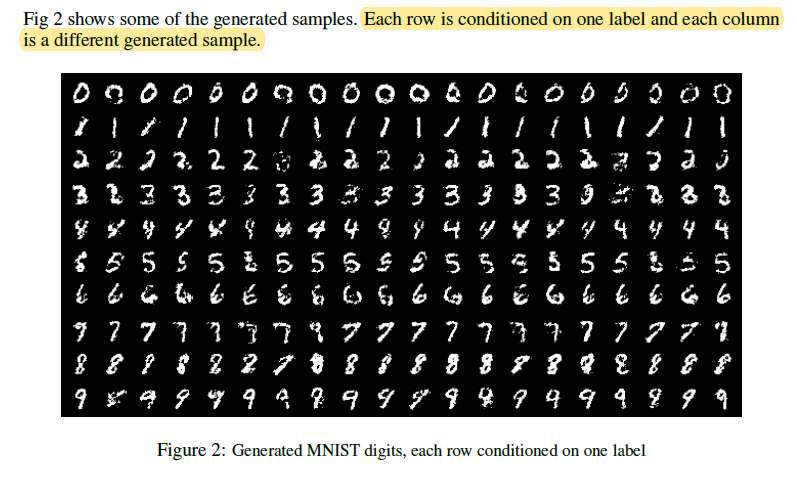
Summary
CGANs outperforms compared with original GANs, we can combine the class label or data from other modalities into the input of G and D, in order to achieve conditional probabilities distribution and controlling GANs.
CGANs的更多相关文章
- (转)Deep Learning Research Review Week 1: Generative Adversarial Nets
Adit Deshpande CS Undergrad at UCLA ('19) Blog About Resume Deep Learning Research Review Week 1: Ge ...
- Unsupervised Image-to-Image Translation Networks --- Reading Writing
Unsupervised Image-to-Image Translation Networks --- Reading Writing 2017.03.03 Motivations: most ex ...
- Face Aging with Conditional Generative Adversarial Network 论文笔记
Face Aging with Conditional Generative Adversarial Network 论文笔记 2017.02.28 Motivation: 本文是要根据最新的条件产 ...
- #论文笔记# [pix2pixHD] High-Resolution Image Synthesis and Semantic Manipulation with Conditional GANs
Ting-Chun Wang, Ming-Yu Liu, Jun-Yan Zhu, Andrew Tao, Jan Kautz, and Bryan Catanzaro. "High-Res ...
- StarGAN: Unified Generative Adversarial Networks for Multi-Domain Image-to-Image Translation - 1 - 多个域间的图像翻译论文学习
Abstract 最近在两个领域上的图像翻译研究取得了显著的成果.但是在处理多于两个领域的问题上,现存的方法在尺度和鲁棒性上还是有所欠缺,因为需要为每个图像域对单独训练不同的模型.为了解决该问题,我们 ...
- CSAGAN:LinesToFacePhoto: Face Photo Generation from Lines with Conditional Self-Attention Generative Adversarial Network - 1 - 论文学习
ABSTRACT 在本文中,我们探讨了从线条生成逼真的人脸图像的任务.先前的基于条件生成对抗网络(cGANs)的方法已经证明,当条件图像和输出图像共享对齐良好的结构时,它们能够生成视觉上可信的图像.然 ...
- Learning Face Age Progression: A Pyramid Architecture of GANs-1-实现人脸老化
Learning Face Age Progression: A Pyramid Architecture of GANs Abstract 人脸年龄发展有着两个重要的需求,即老化准确性和身份持久性, ...
- AT指令集之Call
1.//unsolicited result code,URC表示BP->AP+ESIPCPI:<call_id>,<dir>,<sip_msg_type>, ...
- mtk 的conferrence call建立流程
(重点看main_log与) 抓mtk log: 1.*#*#82533284#*#* 进入抓log UI 2.*#*#825364#*#* 进入工程模式 3.进入"Lo ...
随机推荐
- SpringMVC初始化阶段流程源码分析
1.都知道SpringMVC项目启动的时候都会初始化一个类:DispatcherServlet,看这个类的源码我们可以发现他其实就是一个servlet, 为什么这么说呢?请看: DispatcherS ...
- python-逻辑结构操作
0x01 大纲 逻辑结构 list dict 判断if else elif break continue while 0x02 添加 list = [i for i in range(0,10)] p ...
- JVM的整体结构
整个jvm的运行流程图如上所示,首先需要进行加载class文件,然后使用类加载子系统将class翻译解析导入内存,在内存中分别导入到对应的运行时数据区,然后执行引擎开始执行,对于需要的数据在对应的区域 ...
- springboot:This application has no explicit mapping for /erro
springboot启动没有报错,但是访问的时候返回如上图的错误.看报错内容感觉是没有这个mapping对应的接口.但是确实写了. 最终发现是因为springboot的启动类放的位置不对.启动类所在的 ...
- 使用 mysqld_safe 启动 mysqld 服务
目录 mysqld_safe 介绍 启动 停止 mysqld_safe 介绍 mysqld_safe is the recommended way to start a mysqld server o ...
- Linux 虚拟机绑定静态 IP
环境介绍 Machine: NUC8i5BEK OS: macOS Catalina 10.15.6 VirtualBox: 6.1.12 r139181 (Qt5.6.3) CentOS: 8.2. ...
- MySQL 8.0索引合并
简介 参考https://dev.mysql.com/doc/refman/8.0/en/index-merge-optimization.html#index-merge-intersection. ...
- 服务器备用远程-----Radmin客户端的操作指南(如何远程与传送文件)
一台服务器的寿命一般比较长可能会从几年到几十年,就会经历各个版本的更新与升级.再经过时间的历练后,可能windwos自带的远程连接有时候会拉胯,经常报错. 这时候就需要备选方案,有钱的单位会自己搭建堡 ...
- 《流畅的Python》第三部分 把函数视作对象 【一等函数】【使用一等函数实现设计模式】【函数装饰器和闭包】
第三部分 第5章 一等函数 一等对象 在运行时创建 能赋值给变量或数据结构中的元素 能作为参数传递给函数 能作为函数的返回结果 在Python中,所有函数都是一等对象 函数是对象 函数本身是 func ...
- 警惕char类型直接相加
今天在写某个程序需要对两个数字字符串进行相加操作,比如字符串1:12345,字符串2:23456.需要1和2相加.2和3相加.就是两个字符相同位置的数进行相加. 这个一看很好完成,写一个for,然后取 ...
